Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
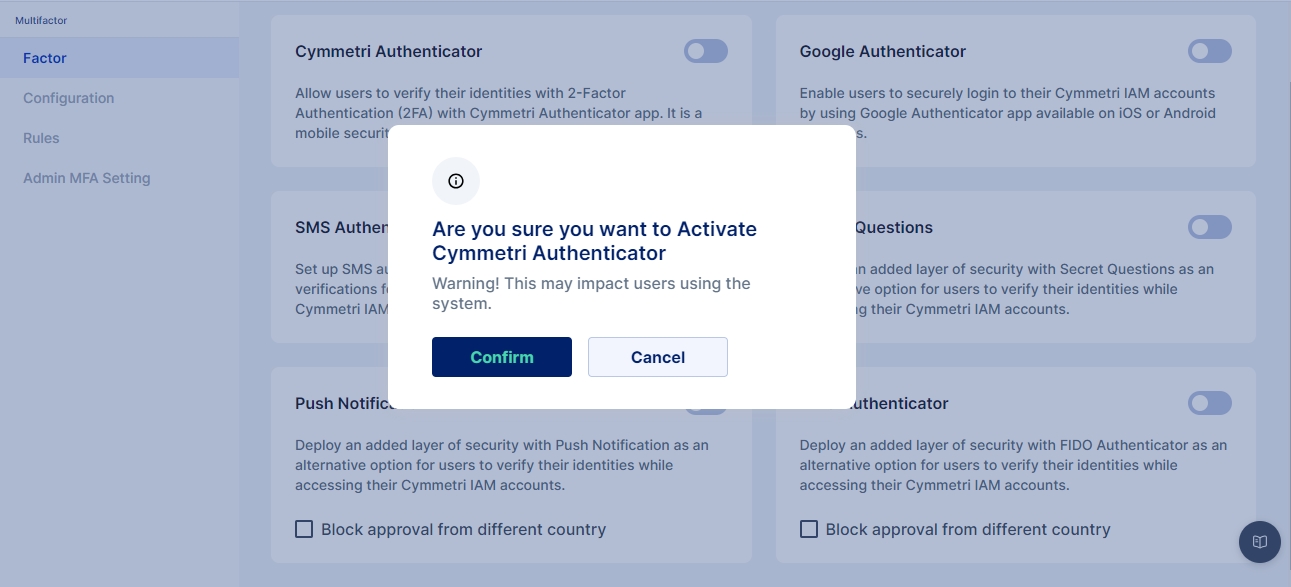
The Cymmetri Authenticator is a robust multi-factor authentication (MFA) mechanism. This mechanism enhances digital security by adding an additional layer of authentication to verify user identity, using a time based OTP (TOTP)
The Cymmetri Authenticator uses the Cymmetri Verifier App that generates time-based one-time passwords (TOTPs) that expire after a short time window. Users must enter these constantly changing codes along with their regular passwords to gain access to their accounts, ensuring that even if a malicious actor obtains their password, access remains highly restricted.
The Cymmetri Authenticator App is user-friendly and easy to set up, often by scanning QR codes provided by the service requiring authentication. It's a valuable tool for businesses and individuals looking to protect their sensitive data effectively.
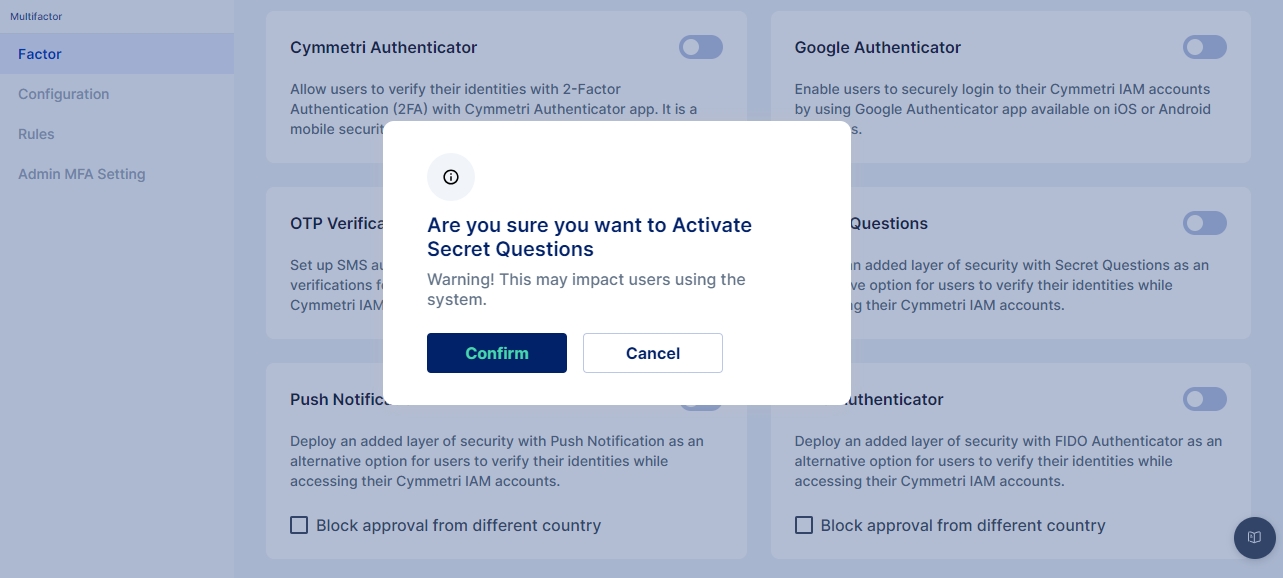
For configuring the Cymmetri Authenticator, select the Cymmetri Authenticator (Time based OTP) toggle button and click confirm to setup Cymmetri Authenticator as an MFA option
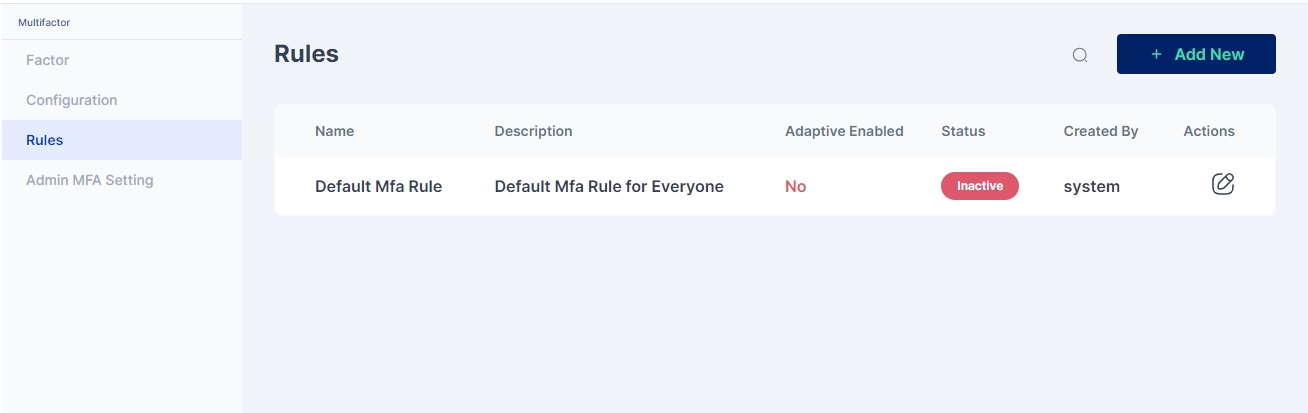
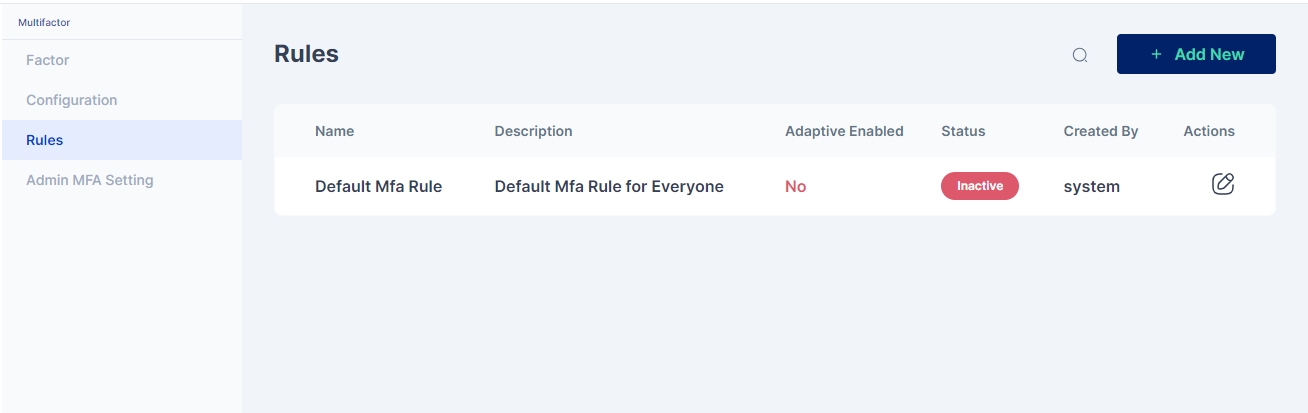
Next we move to configure the rules for Multi-factor authentication policy for login
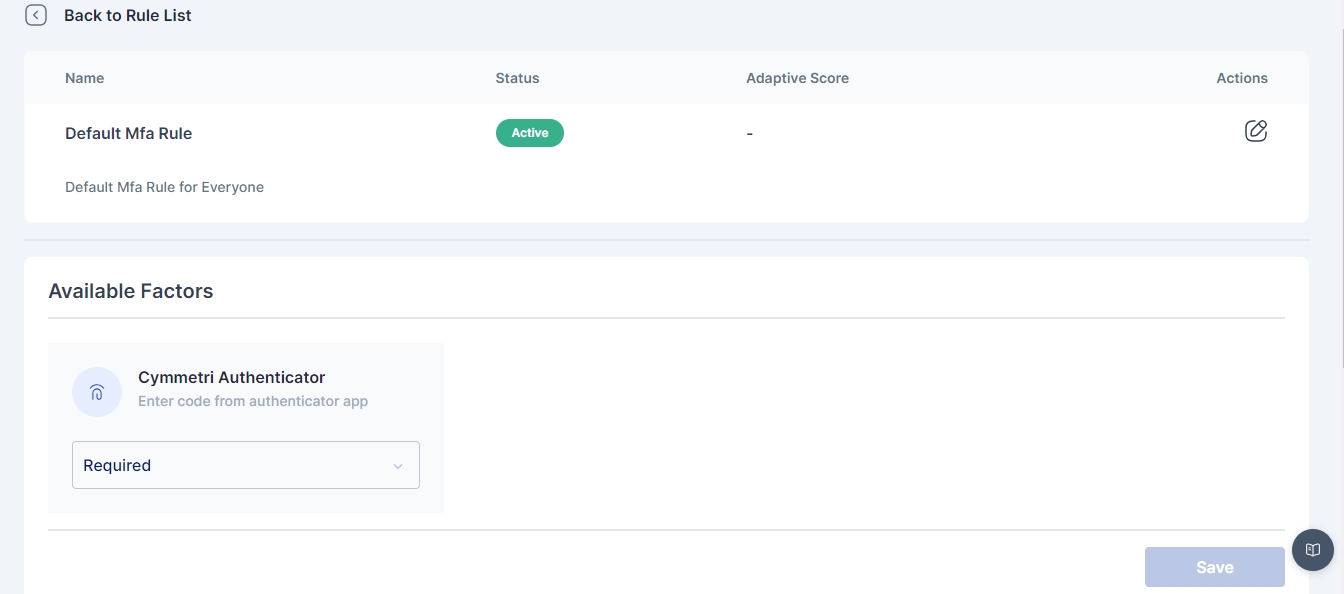
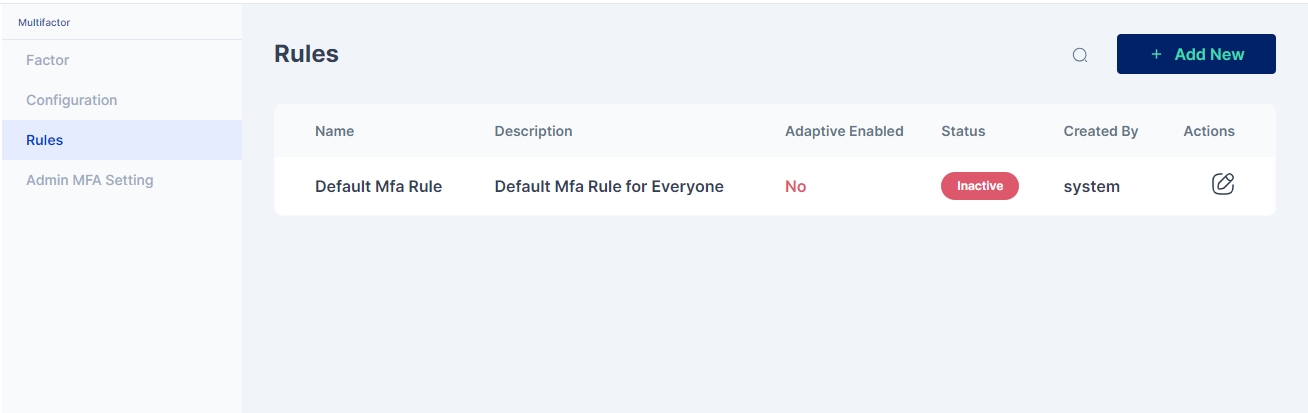
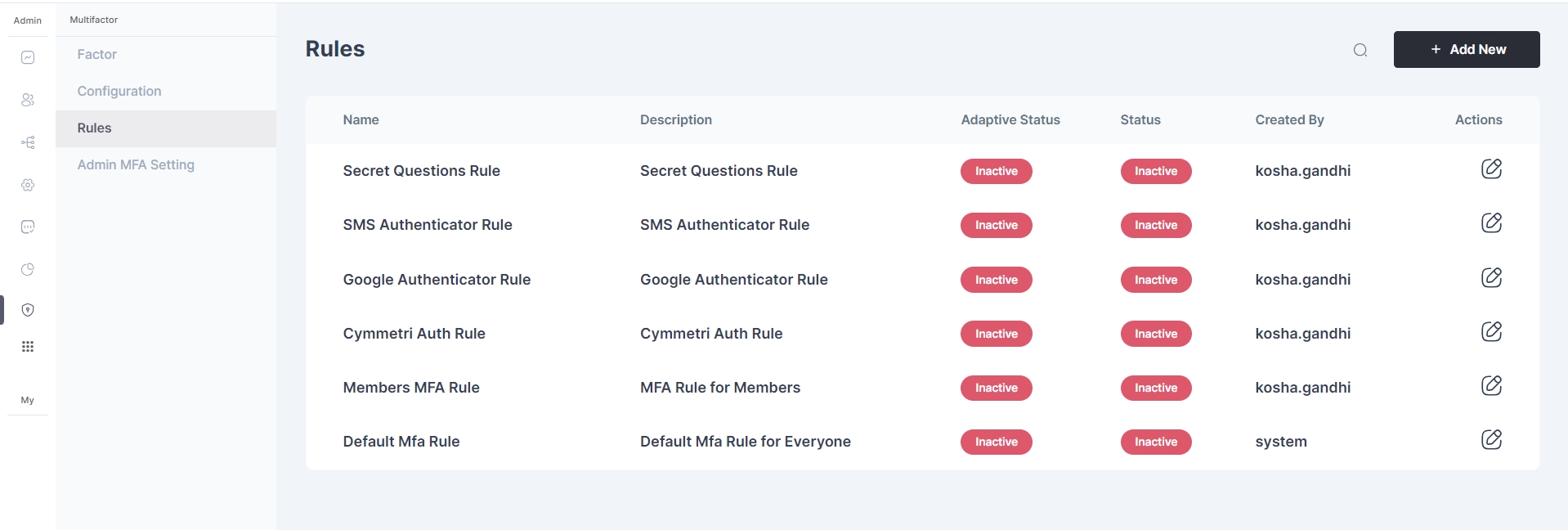
Click on the pencil icon to start editing the rule.
To enable this rule click on the pencil icon in the upper box to toggle on this rule.
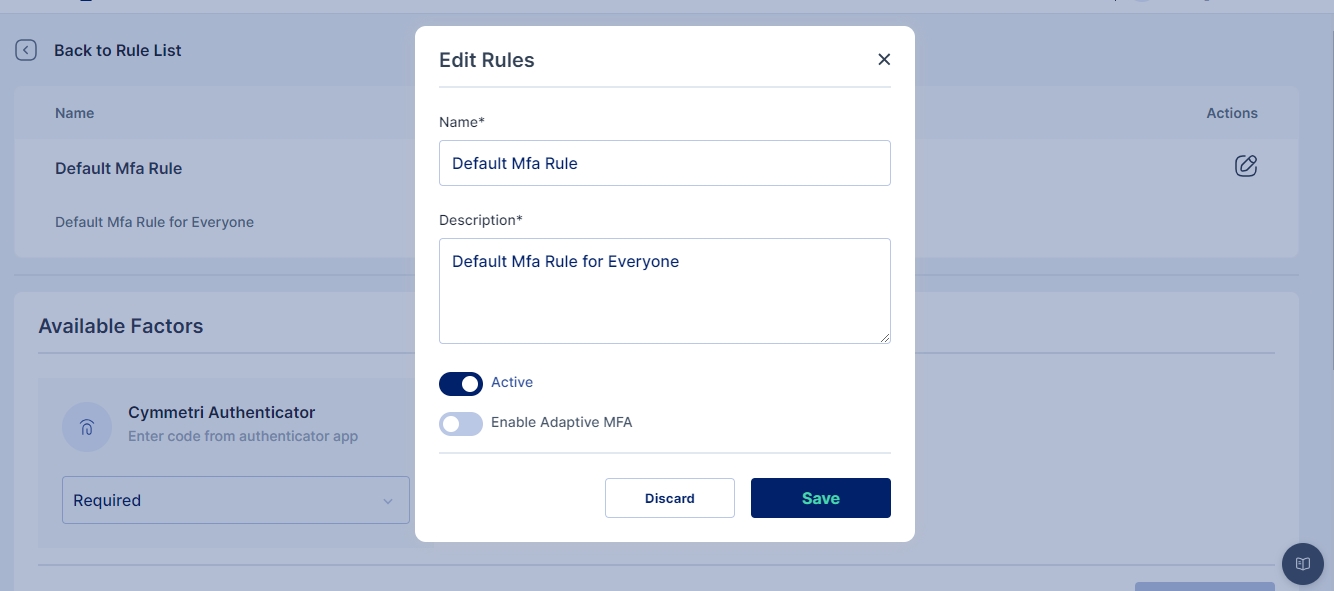
Change the dropdown of the Cymmetri Authenticator factor to indicate that it is mandatory (required).
The options available for each factor are:
Required: This setting means that the corresponding factor is required to be enabled for each user, and every user must set up this factor in their next login.
Optional: This setting means that the corresponding factor is not required to be enabled for each user, and they may configure this option from their "My Workspace". Once the user configures it, they may use it for the purpose of second level of authentication during authentication. Disabled: This settings means that the corresponding factor is not required or enabled for each user, and the user may not configure or use it for authentication into the Cymmetri platform.
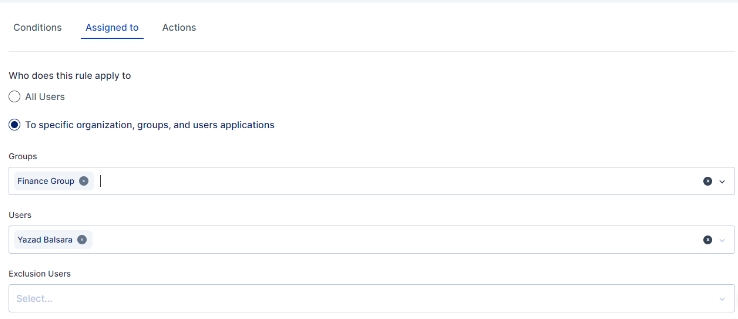
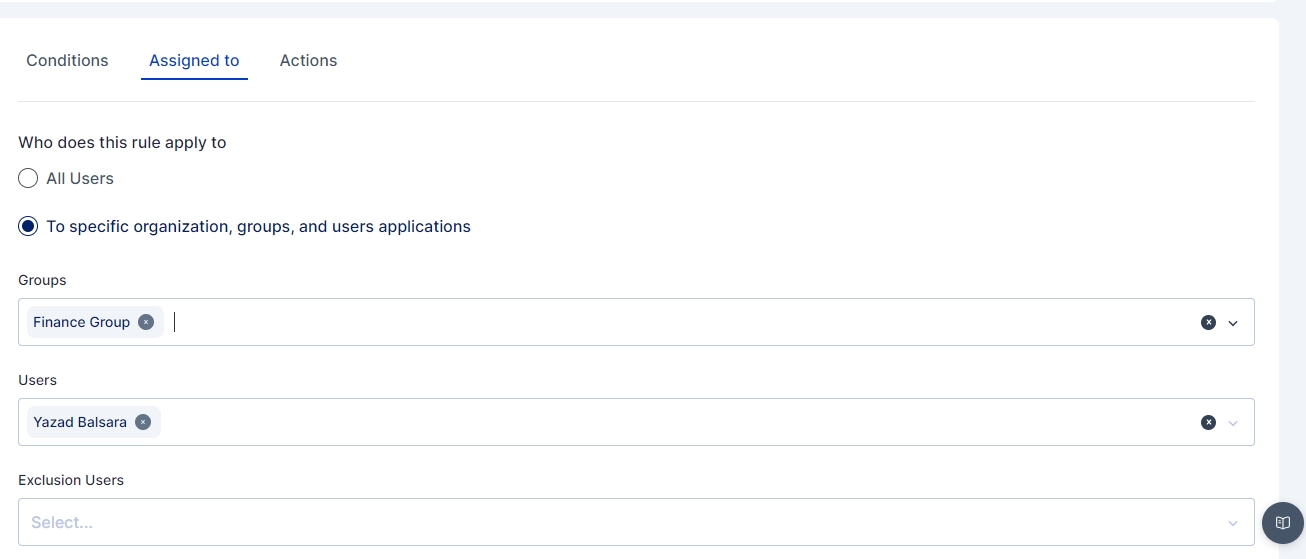
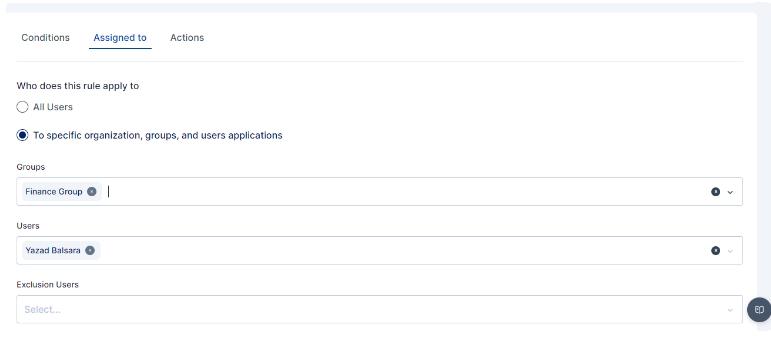
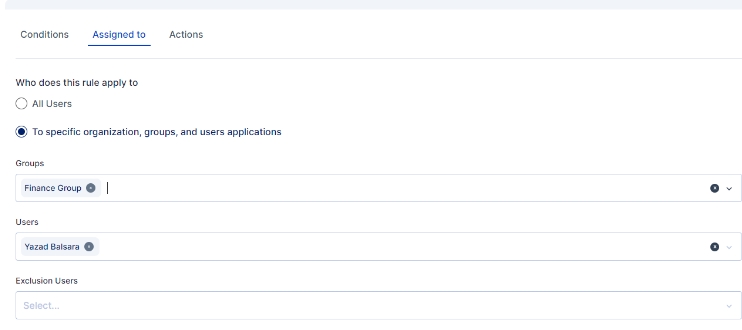
An administrator can further customize to whom the rule would be applicable by selecting user(s) or group of users in the "Assigned to" Tab, If the rule is to be applied to all the users then the "All Users" option need to be selected
All subsequent logins of any user on the Cymmetri platform will now require the use of the Cymmetri Authenticator Code.
The user needs to setup the Cymmetri Authenticator, for which the user needs to download the Cymmetri Verifier app. The links below can be used to download the Cymmetri Verifier App on Android or IOS:
IOS- https://apps.apple.com/in/app/cymmetri-verify/id6455987489
Android - https://play.google.com/store/apps/details?id=com.cymmetri.verify
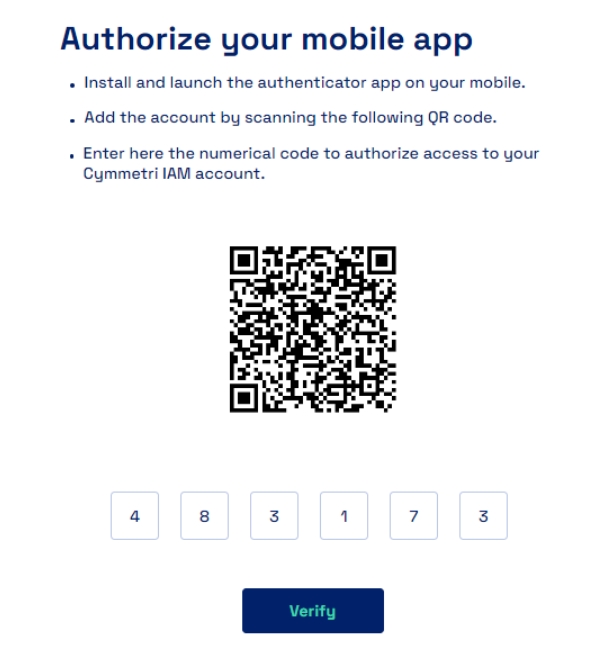
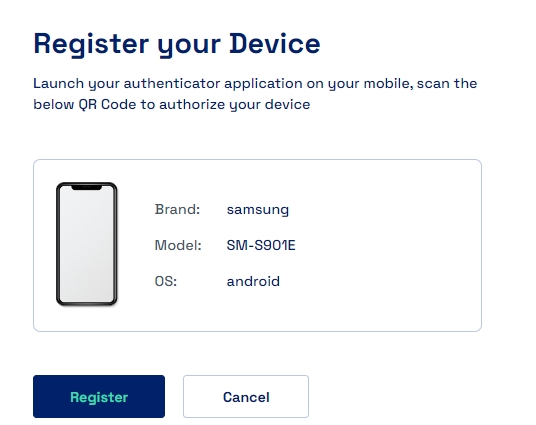
Once downloaded we need to scan the QR Code as shown below in the Cymmetri Verifier App and obtain a 6 digit code which needs to be entered in the space provided below and verify the user login.
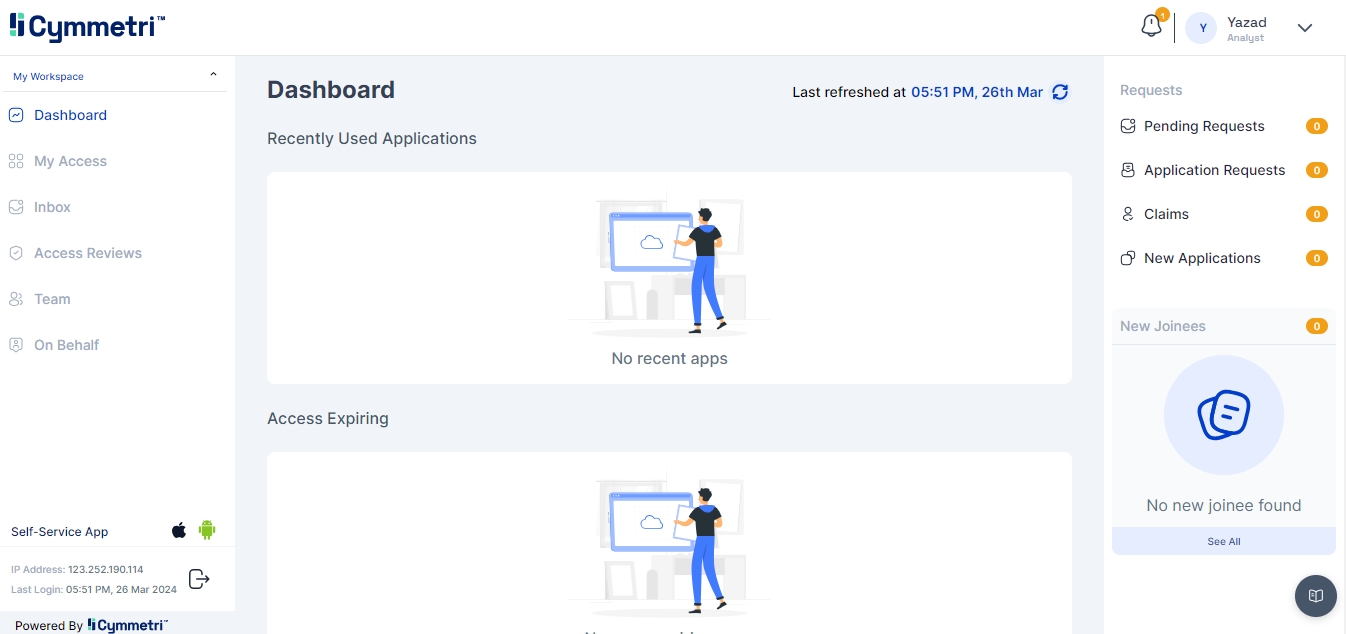
Once successfully verified the user is redirected to the Dashboard
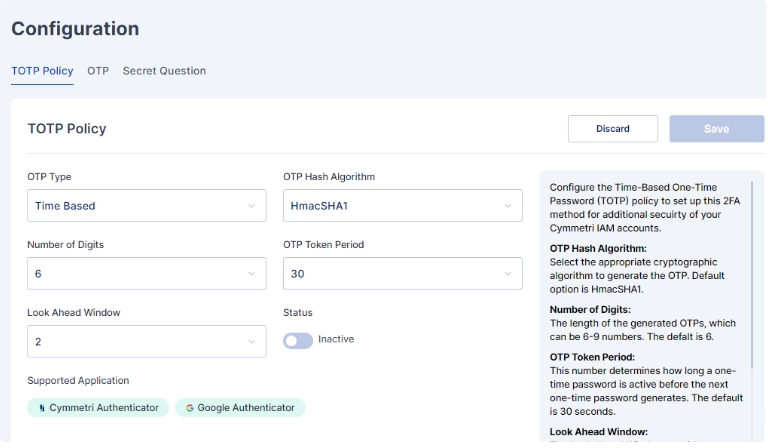
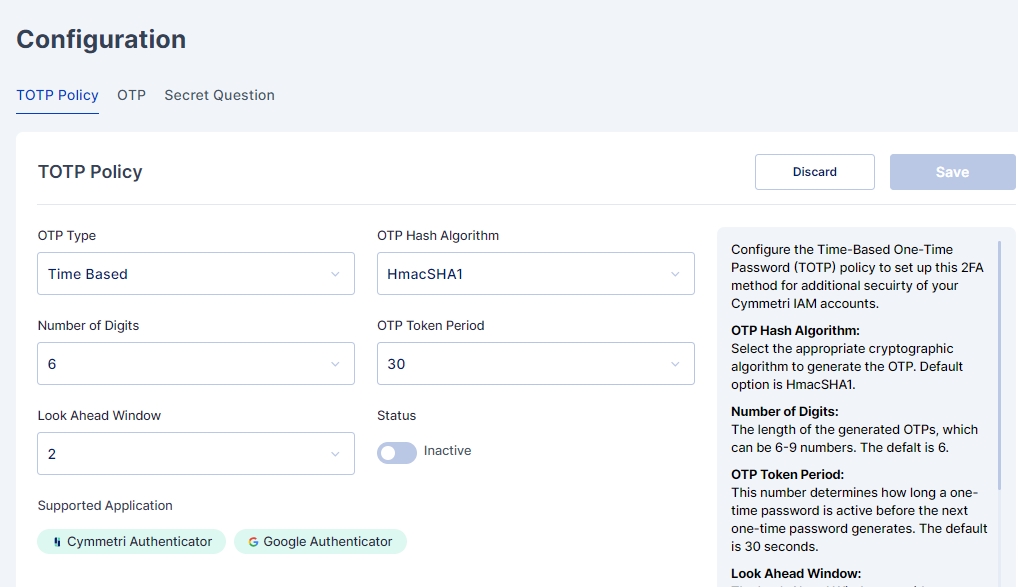
Cymmetri also allow you to customize the Cymmetri Authenticator parameters using the Configuration section. Here you may configure the values as shown below:
OTP Type: Select the OTP Type to be implemented.Time Based is the default value here.
OTP Hash Algorithm: Select the appropriate cryptographic algorithm to generate the OTP. Default option is HmacSHA1.
Number of Digits: The length of the generated OTPs, which can be 6-9 numbers. The default is 6.
OTP Token Period: This number determines how long a one-time password is active before the next one-time password generates. The default is 30 seconds.
Look Ahead Window: The Look Ahead Window considers any possible synchronization delay between the server and the client that generates the one-time password. Default value is 2.
Supported Applications: Two-Factor Authentication apps that can be used by users to secure their Cymmetri IAM accounts.
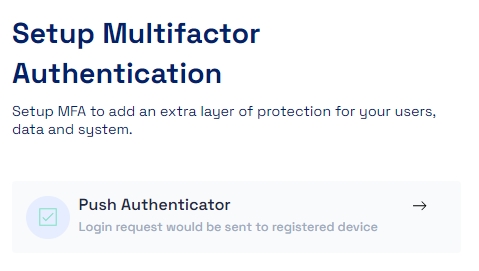
Push Authenticator is a modern and highly convenient multi-factor authentication (MFA) mechanism of Cymmetri's Multi-factor Authentication mechanisms designed to bolster security while offering a user-friendly experience. This authentication method simplifies the process of verifying one's identity, reducing the reliance on traditional methods like SMS codes or hardware tokens.
With Push Authenticator, users receive authentication requests directly on their registered mobile devices. A push notification is sent to the user's device in the Cymmetri Authenticator App, prompting them to approve or deny the login attempt. This approval process occurs with a simple tap.
The advantages of Push Authenticator are twofold. First, it enhances security by reducing the risk of intercepted codes or phishing attacks. Second, it streamlines the user experience, making MFA more accessible and less intrusive.
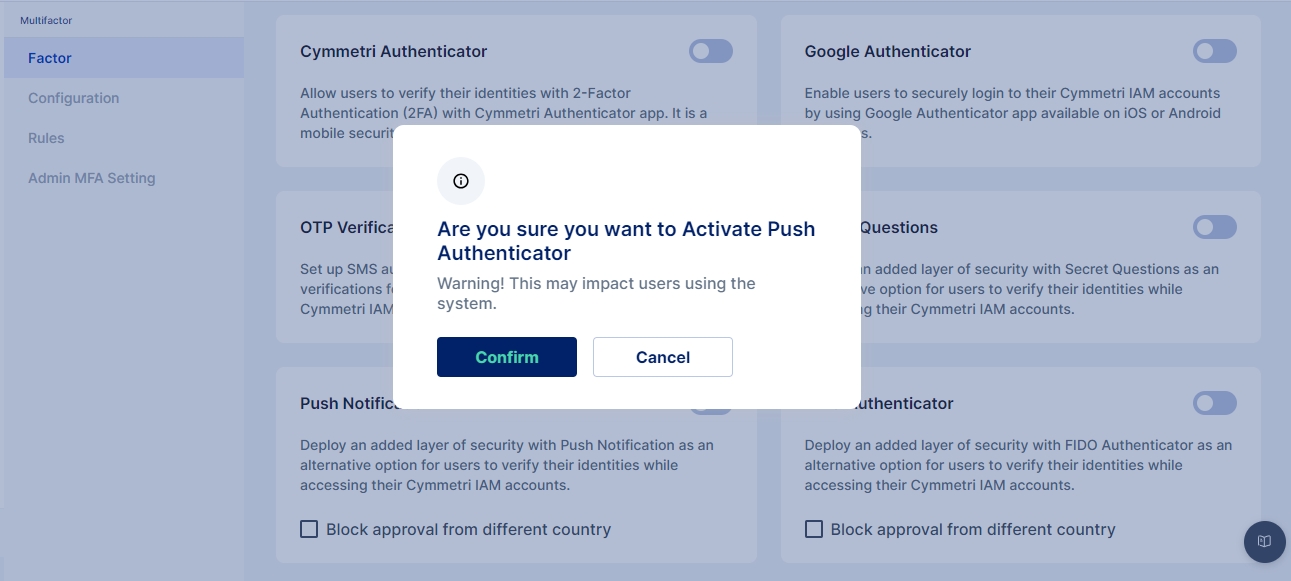
For configuring the Push Authenticator, select the Push Notification toggle button and click confirm to setup Push Authenticator as an MFA option
And click confirm to setup Push Authenticator as an MFA option
Next we move to configure the rules for Multi-factor authentication policy for login
Click on the pencil icon to start editing the rule.Optionally you may also add a new rule by clicking on the "+ Add New" button.
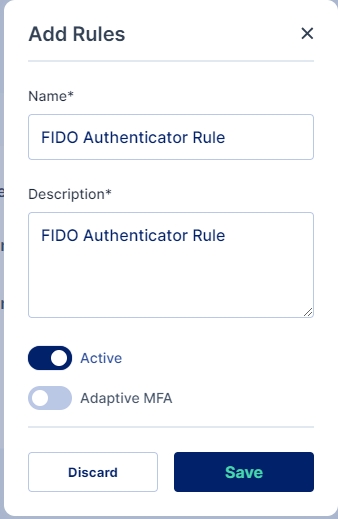
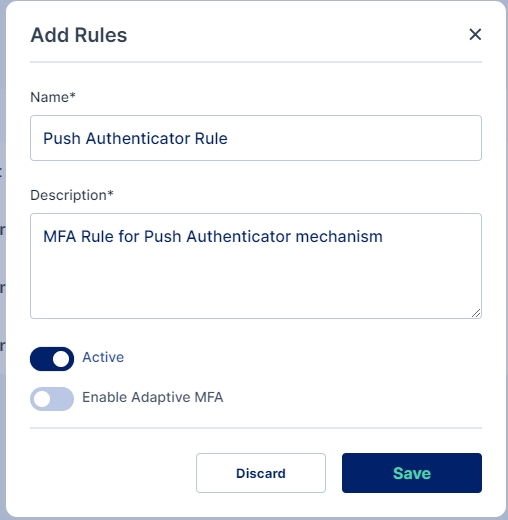
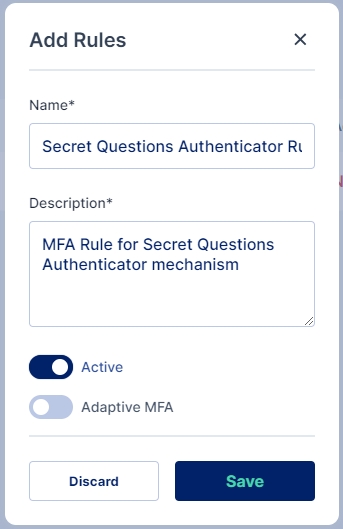
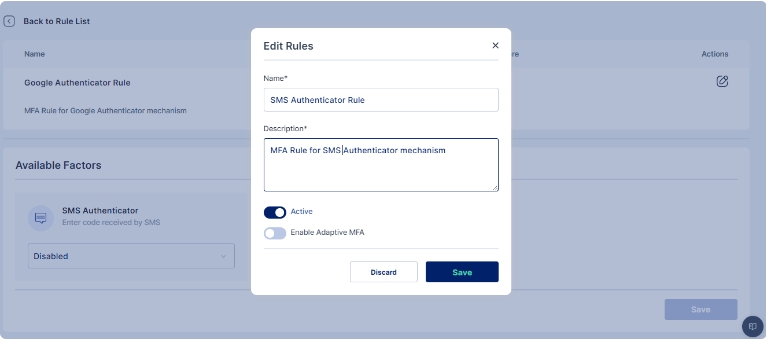
For adding a New Rule enter Name of the Rule and Description also Enable the rule; you may optionally select whether you want to enable Adaptive MFA and the click on the Save button to add the rule
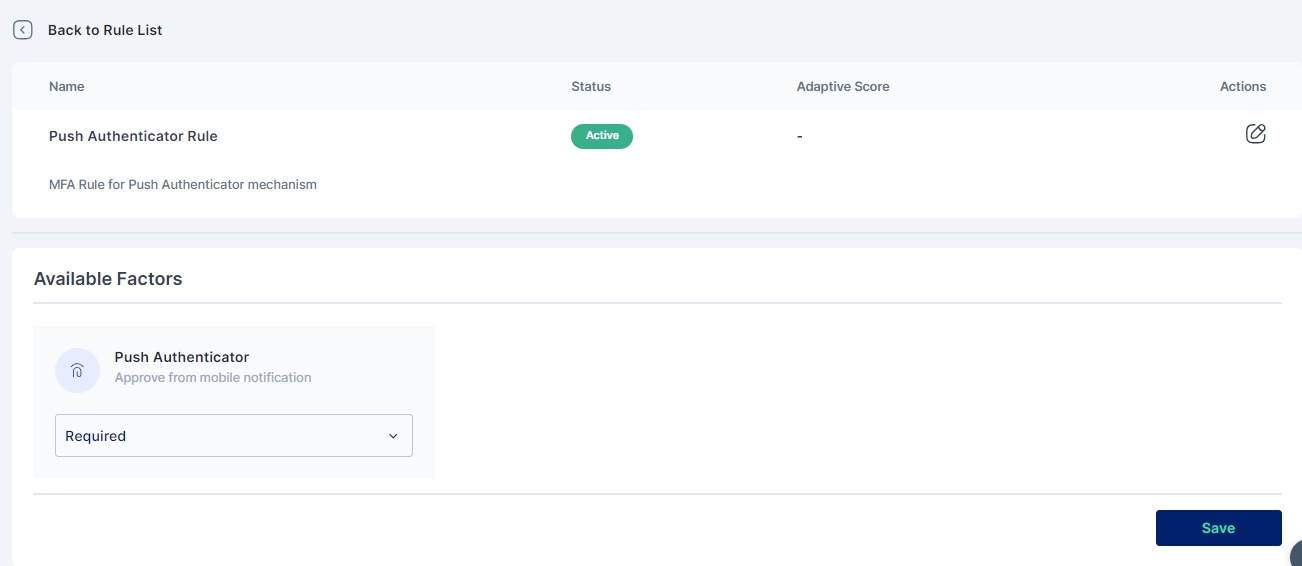
Once added you need to configure the rule to select the Push Authenticator mechanism as Required and enable it.
The other options that can be selected are as explained below:
Required: This setting means that the corresponding factor is required to be enabled for each user, and every user must set up this factor in their next login.
Optional: This setting means that the corresponding factor is not required to be enabled for each user, and they may configure this option from their "My Workspace". Once the user configures it, they may use it for the purpose of second level of authentication during authentication. Disabled: This settings means that the corresponding factor is not required or enabled for each user, and the user may not configure or use it for authentication into the Cymmetri platform.
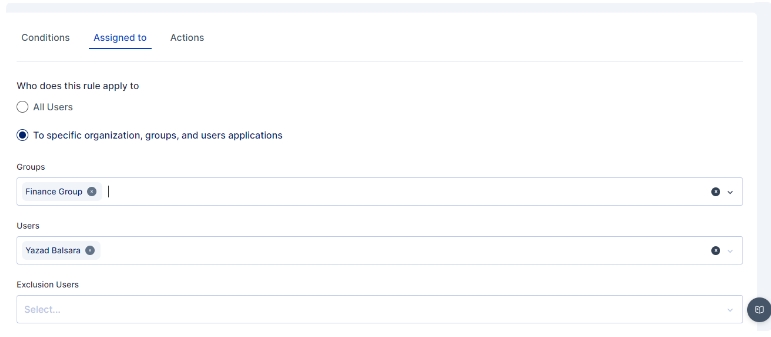
An administrator can further customize to whom the rule would be applicable by selecting user(s) or group of users in the "Assigned to" Tab, If the rule is to be applied to all the users then the "All Users" option need to be selected
All subsequent logins of any user on the Cymmetri Identity platform will now require the use of the Push Authenticator mechanism.
The user needs to setup the Cymmetri Authenticator for receiving the push notification on the device, for which the user needs to download the Cymmetri Verifier app. The links below can be used to download the Cymmetri Verifier App on Android or IOS:
IOS- https://apps.apple.com/in/app/cymmetri-verify/id6455987489
Android - https://play.google.com/store/apps/details?id=com.cymmetri.verify
Once downloaded we need to scan the QR Code in the Cymmetri Verifier App to register the device
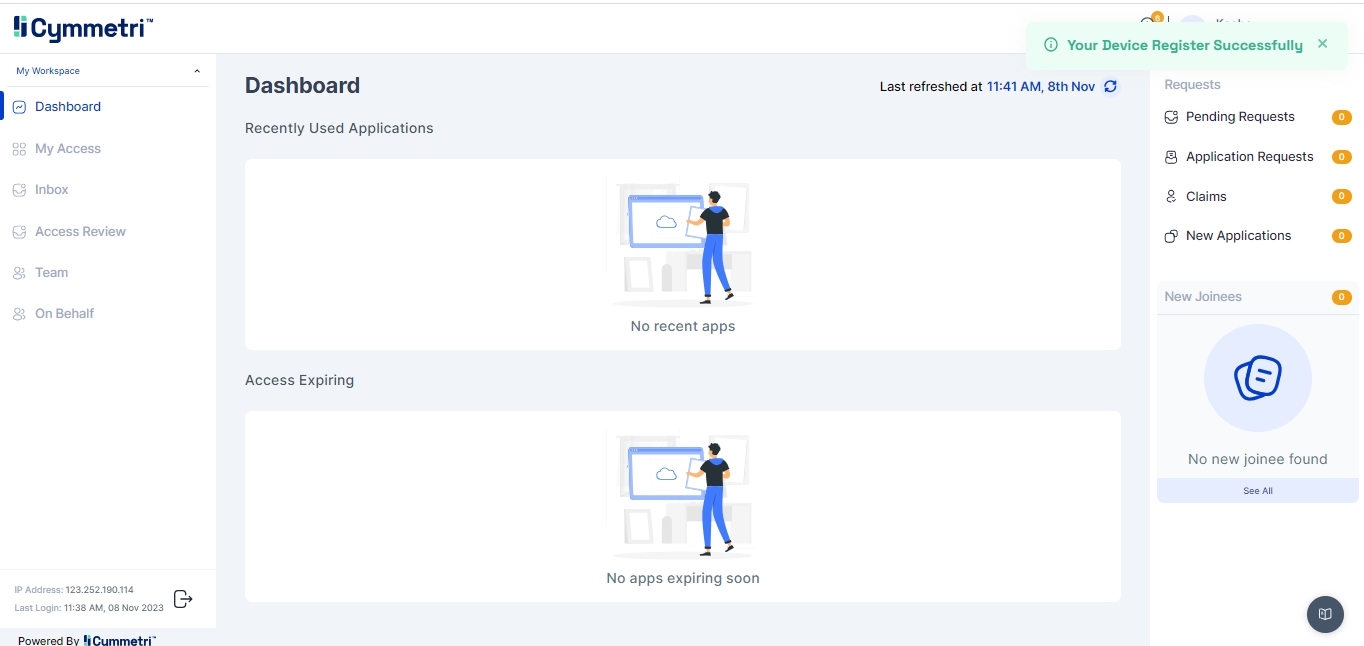
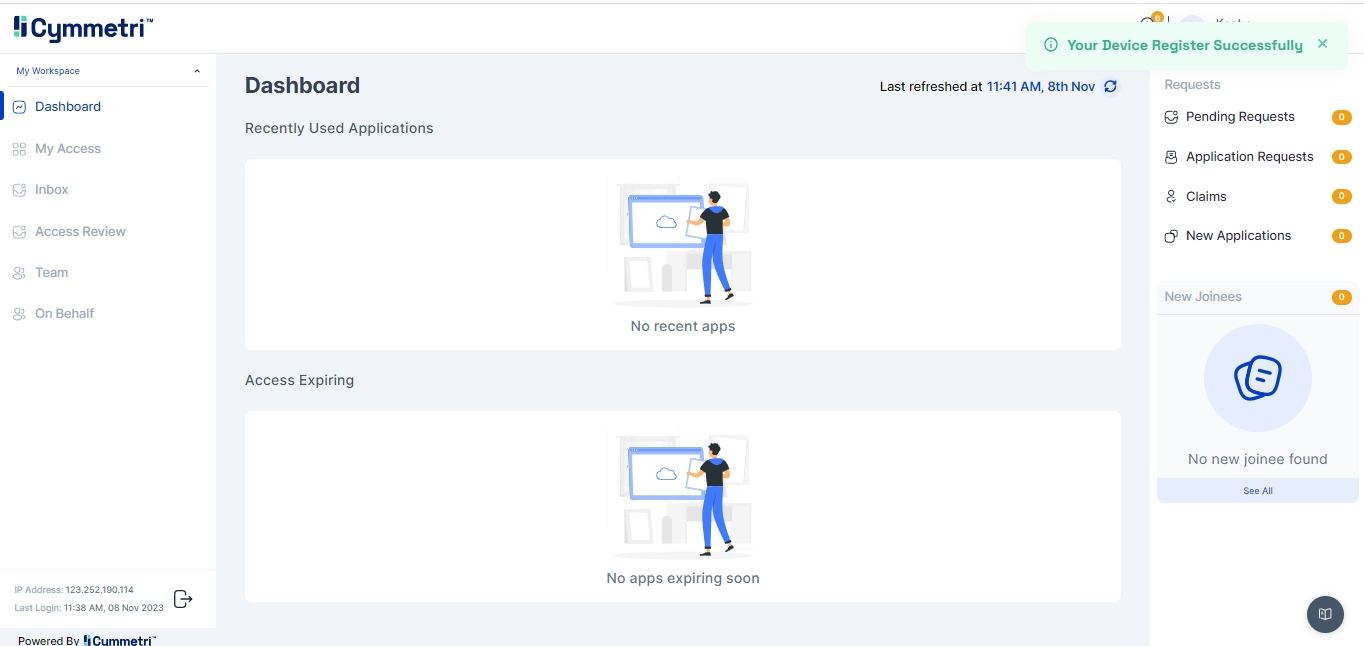
Once the device is registered successfully a notification is show on the dashboard
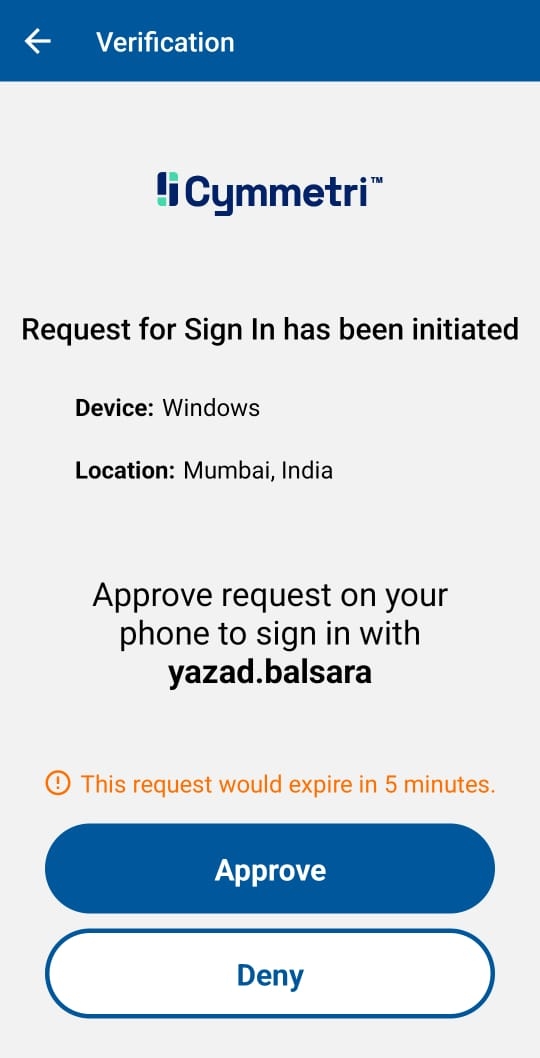
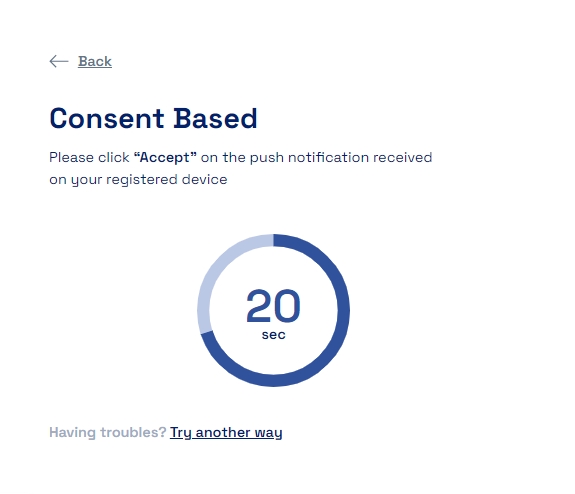
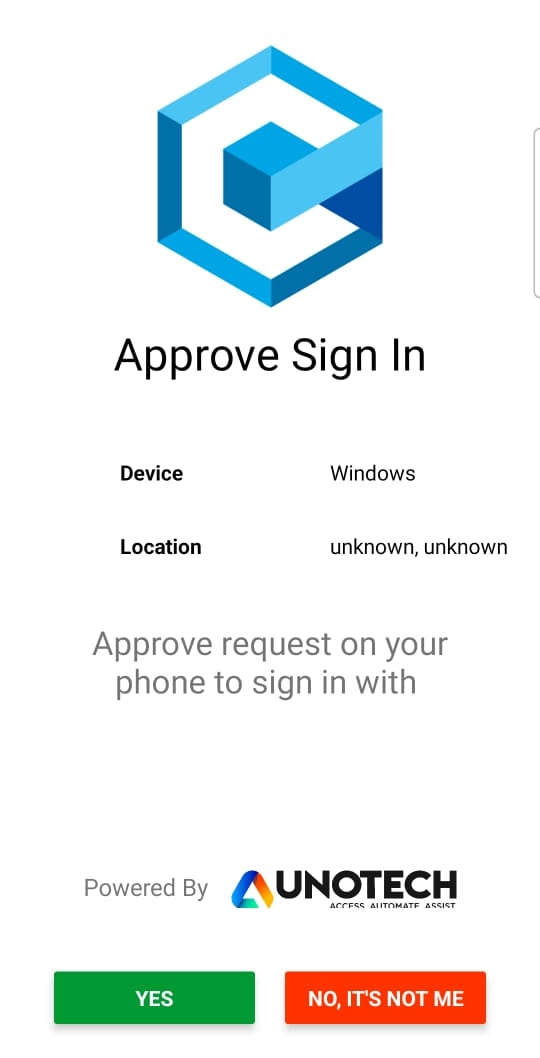
Now when the user selects Push Authenticator as an MFA mechanism and consent notification is sent to the mobile device and the user needs to accept the consent in the stipulated time to be allowed to login.
A notification like as shown below appears on the mobile device where the user needs to click on Yes button to allow login
Once successfully verified the user is redirected to the Dashboard
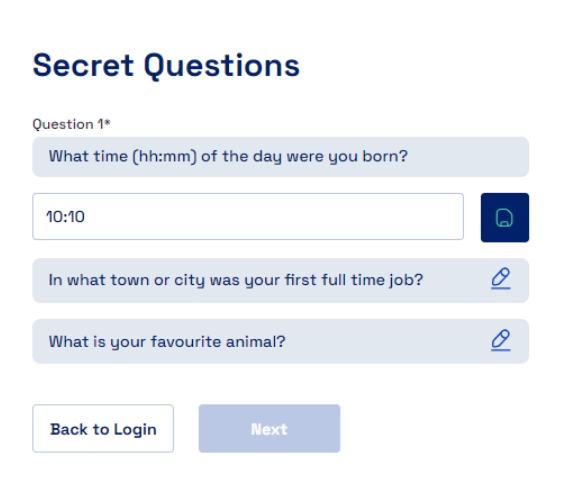
Secret questions are a form of knowledge-based authentication where users set up personalized questions and provide answers during the account setup. These questions might serve as an additional layer of identity verification. Users are prompted to answer these questions during login or account recovery processes, supplementing other authentication methods.
For configuring the Secret Questions Authenticator, select the Secret Questions Authenticator toggle button and click confirm to setup Secret Questions Authenticator as an MFA option
Next we move to configure the rules for Multi-factor authentication policy for login
You may either click on the pencil icon to start editing the rule, or create a new rule
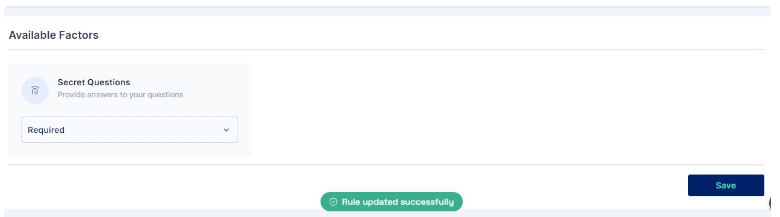
Once you have either created a new rule or edited an existing one, change the dropdown of the Secret Questions Authenticator factor to indicate that it is mandatory (required).
The options available for each factor are:
Required: This setting means that the corresponding factor is required to be enabled for each user, and every user must set up this factor in their next login.
Optional: This setting means that the corresponding factor is not required to be enabled for each user, and they may configure this option from their "My Workspace". Once the user configures it, they may use it for the purpose of second level of authentication during authentication. Disabled: This settings means that the corresponding factor is not required or enabled for each user, and the user may not configure or use it for authentication into the Cymmetri platform.
An administrator can further customize to whom the rule would be applicable by selecting user(s) or group of users in the "Assigned to" Tab, If the rule is to be applied to all the users then the "All Users" option need to be selected
Once the changes are saved this is how the rule appears:
All subsequent logins of any user on the Cymmetri platform will now require the use of the Secret Questions Authenticator and answer the configured questions.
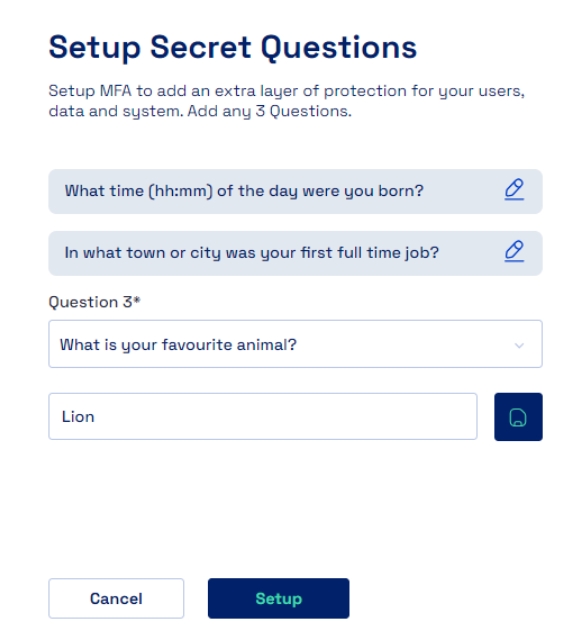
The user needs to setup the Secret Questions, for which the user needs to select the questions from a predefined set of questions and provide their relevant answers which the user can answer later when logging into the system.
When the user logs in the next time user needs to answer these questions to be able to successfully login into Cymmetri
Once successfully verified the user is redirected to the Dashboard
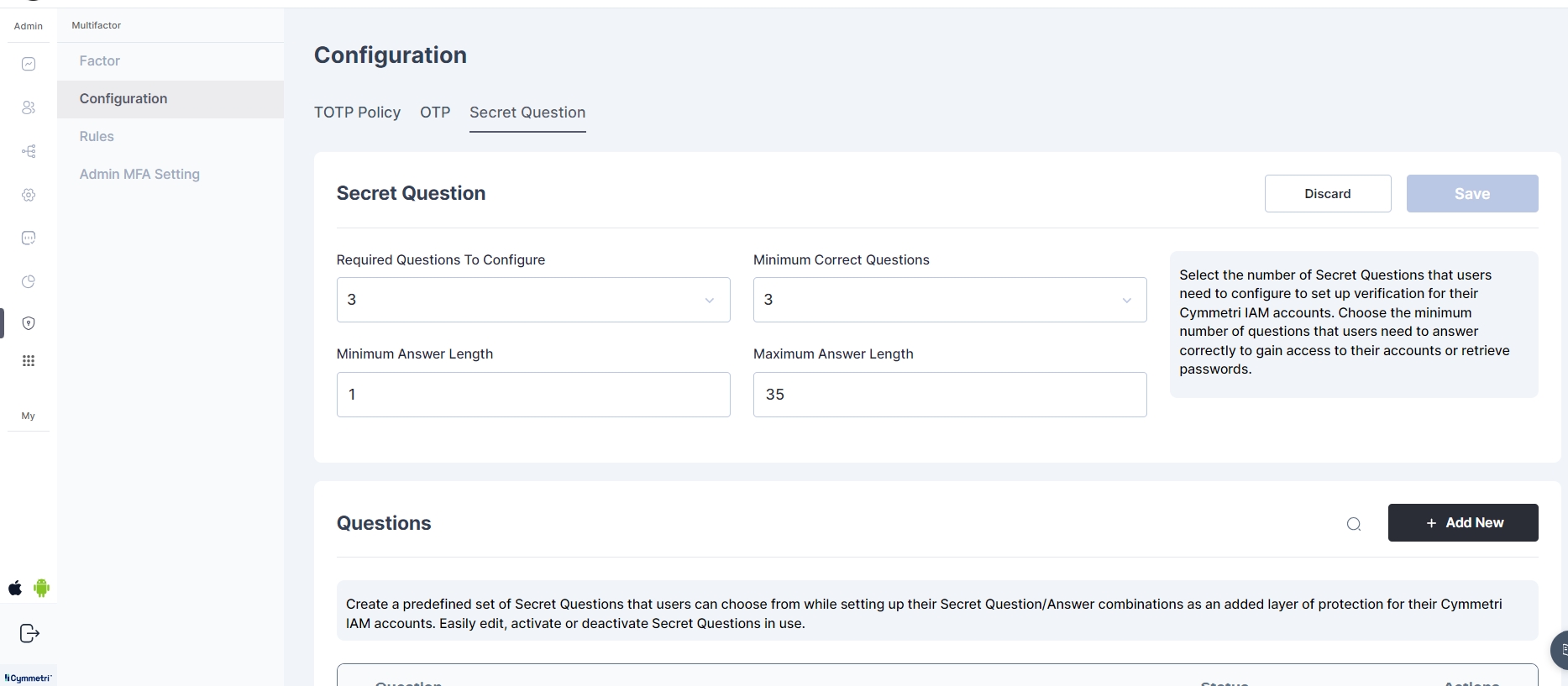
Cymmetri also allow you to customize the Secret Questions parameters using the Configuration section. Here you may configure the values as shown below:
Required Questions To Configure: Select the number of Secret Questions that users need to configure to set up for verifying the account. Default is 3.
Minimum Correct Questions: Choose the minimum number of questions that users need to answer correctly to gain access to their accounts or retrieve passwords. Default is 3.
Minimum Answer Length: Choose the minimum number of characters for the answer to these questions. Default is 2.
Maximum Answer Length: Choose the maximum number of characters for the answer to these questions. Default is 35.
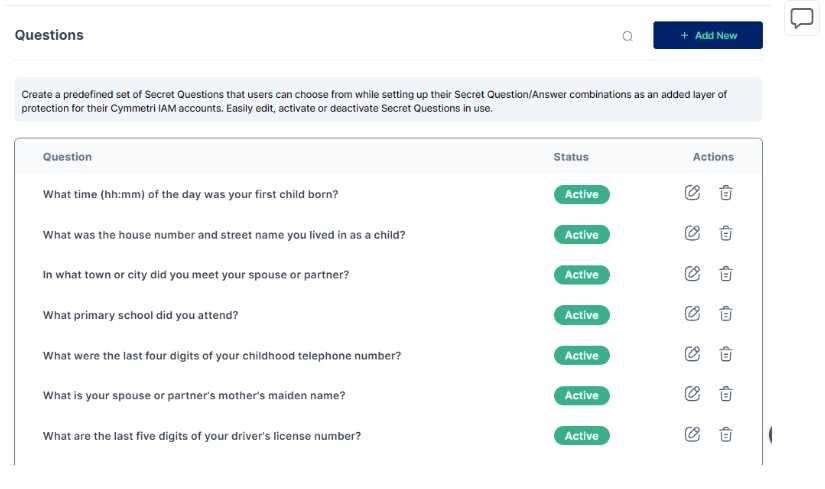
Administrators can create a predefined set of Secret Questions that users can choose from while setting up their Secret Question/Answer combinations as an added layer of protection for their Cymmetri accounts.
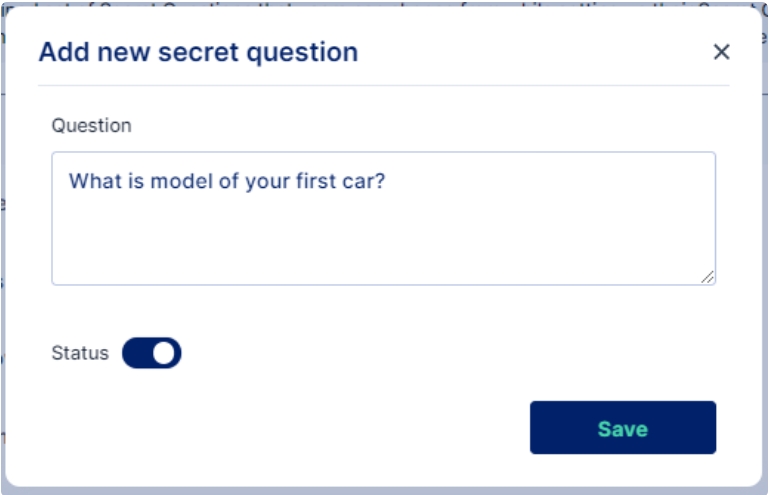
To a new question Administrator needs to click on the "Add New" button and enter the following details:
Question: The question that the administrator wants to add
Status: needs to be enabled for the question to appear in the list
Administrators can easily edit, delete, activate or deactivate Secret Questions in use.
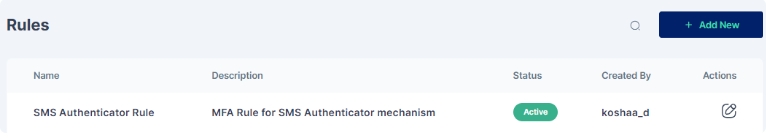
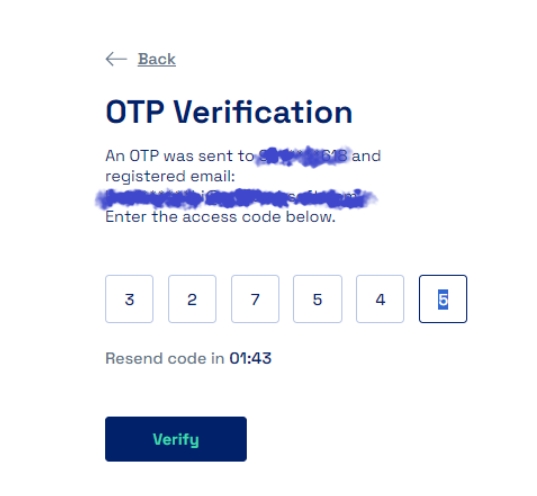
SMS Authenticator involves sending a unique verification code to the user's mobile device via SMS and/ or to the user's email. The user then enters this code along with their password to complete the login process.
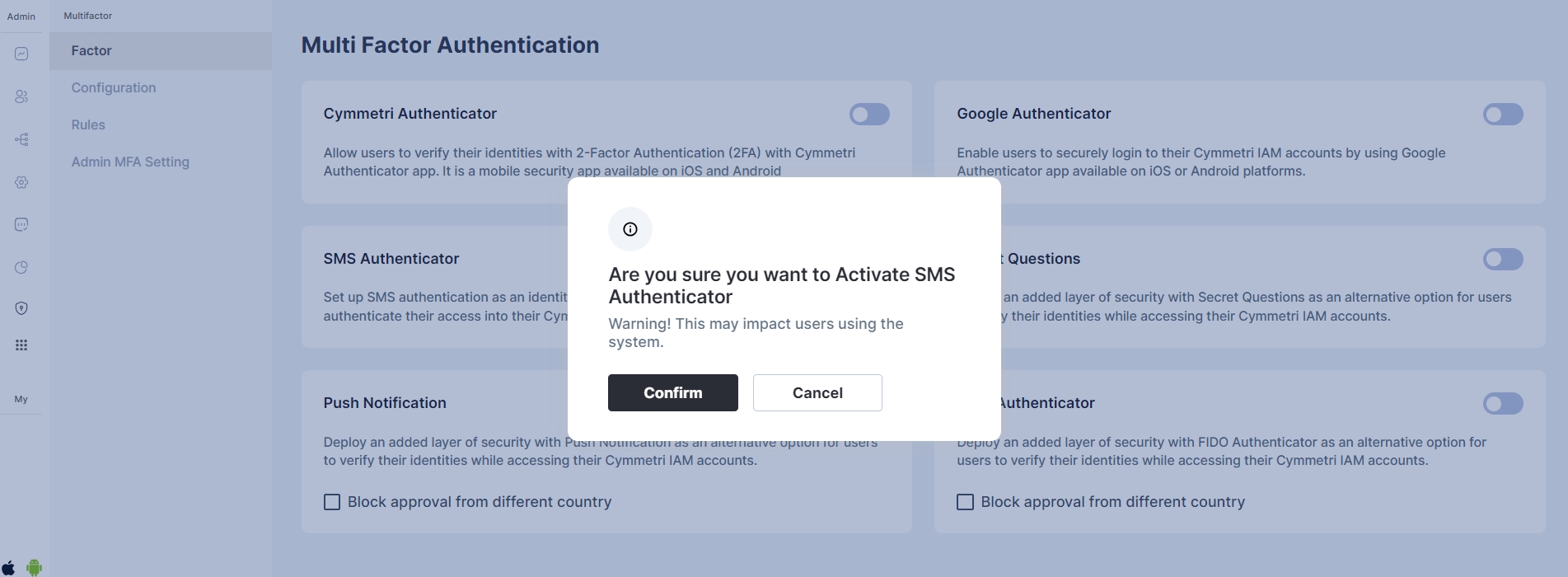
For configuring the SMS Authenticator, select the SMS Authenticator toggle button and click confirm to setup SMS Authenticator as an MFA option
Next we move to configure the rules for Multi-factor authentication policy for login
You may either click on the pencil icon to start editing the rule, or create a new rule
Once you have either created a new rule or edited an existing one, change the dropdown of the SMS Authenticator factor to indicate that it is mandatory (required).
The options available for each factor are:
Required: This setting means that the corresponding factor is required to be enabled for each user, and every user must set up this factor in their next login.
Optional: This setting means that the corresponding factor is not required to be enabled for each user, and they may configure this option from their "My Workspace". Once the user configures it, they may use it for the purpose of second level of authentication during authentication. Disabled: This settings means that the corresponding factor is not required or enabled for each user, and the user may not configure or use it for authentication into the Cymmetri platform.
An administrator can further customize to whom the rule would be applicable by selecting user(s) or group of users in the "Assigned to" Tab, If the rule is to be applied to all the users then the "All Users" option need to be selected
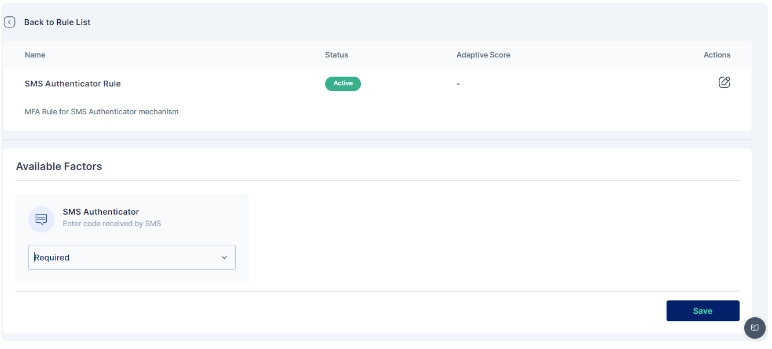
Once the changes are saved this is how the rule appears:
All subsequent logins of any user on the Cymmetri platform will now require the use of sms received on the mobile device as an SMS or email.
Once successfully verified the user is redirected to the Dashboard
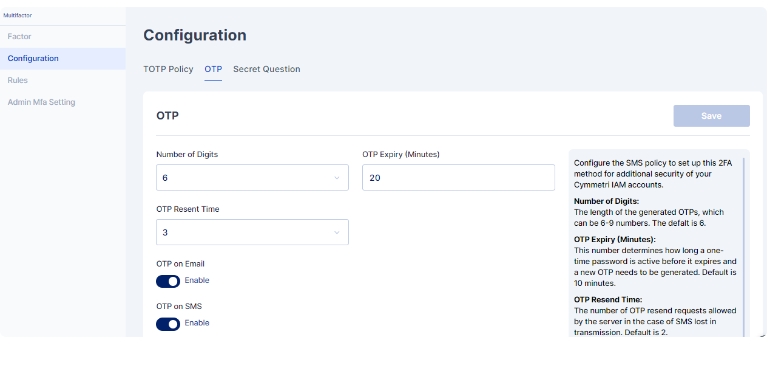
Cymmetri also allow you to customize the SMS Authenticator parameters using the Configuration section. Here you may configure the values as shown below:
Number of Digits: The length of the generated OTPs, which can be 4-6 numbers. Default is 6.
OTP Expiry (Minutes): This number determines how long a one-time password is active before it expires and a new OTP needs to be generated. Default is 10 minutes.
OTP Resent Time: The number of OTP resend requests allowed by the server in the case of SMS lost in transmission. Default is 2.
OTP on Email: when enabled OTP is sent on email.
OTP on SMS: when enabled OTP is sent as an SMS on user's mobile device
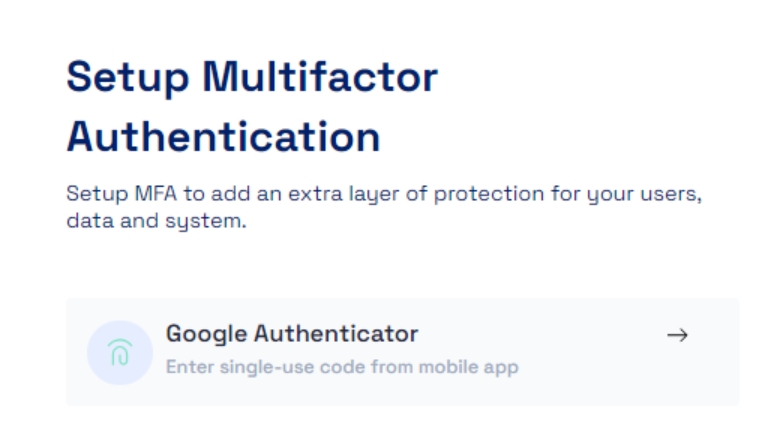
Google Authenticator is a widely used two-factor authentication app developed by Google. It generates time-based one-time passcodes (TOTPs) on users' mobile devices, providing an additional layer of security beyond passwords. Users typically scan QR codes presented by online services to set up two-factor authentication.
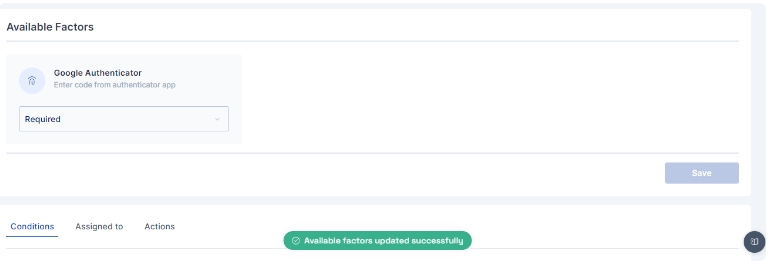
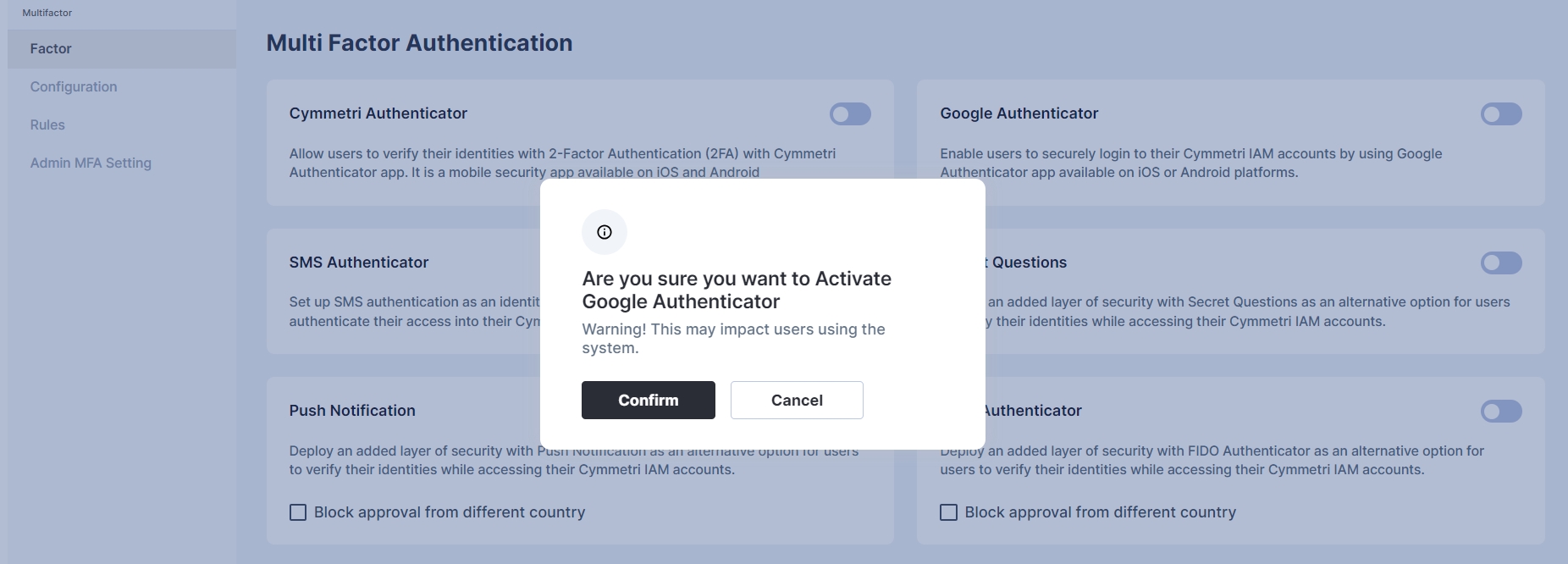
For configuring the Google Authenticator, select the Google Authenticator toggle button and click confirm to setup Google Authenticator as an MFA option
Next we move to configure the rules for Multi-factor authentication policy for login
You may either click on the pencil icon to start editing the rule, or create a new rule
Once you have either created a new rule or edited an existing one, change the dropdown of the Google Authenticator factor to indicate that it is mandatory (required).
The options available for each factor are:
Required: This setting means that the corresponding factor is required to be enabled for each user, and every user must set up this factor in their next login.
Optional: This setting means that the corresponding factor is not required to be enabled for each user, and they may configure this option from their "My Workspace". Once the user configures it, they may use it for the purpose of second level of authentication during authentication. Disabled: This settings means that the corresponding factor is not required or enabled for each user, and the user may not configure or use it for authentication into the Cymmetri platform.
An administrator can further customize to whom the rule would be applicable by selecting user(s) or group of users in the "Assigned to" Tab, If the rule is to be applied to all the users then the "All Users" option need to be selected
Once the changes are saved this is how the rule appears:
All subsequent logins of any user on the Cymmetri platform will now require the use of the Google Authenticator Code.
The user needs to setup the Google Authenticator, for which the user needs to download the Google Authenticator App. The links below can be used to download the Google Authenticator App on Android or IOS:
IOS: https://apps.apple.com/gb/app/google-authenticator/id388497605
Once downloaded we need to scan the QR Code as shown below in the Google Authenticator App and obtain a 6 digit code which needs to be entered in the space provided below and verify the user login.
Once successfully verified the user is redirected to the Dashboard
Cymmetri also allow you to customize the Cymmetri Authenticator parameters using the Configuration section. Here you may configure the values as shown below:
OTP Type: Select the OTP Type to be implemented.Time Based is the default value here.
OTP Hash Algorithm: Select the appropriate cryptographic algorithm to generate the OTP. Default option is HmacSHA1.
Number of Digits: The length of the generated OTPs, which can be 6-9 numbers. The default is 6.
OTP Token Period: This number determines how long a one-time password is active before the next one-time password generates. The default is 30 seconds.
Look Ahead Window: The Look Ahead Window considers any possible synchronization delay between the server and the client that generates the one-time password. Default value is 2.
Supported Applications: Two-Factor Authentication apps that can be used by users to secure their Cymmetri IAM accounts.
The FIDO (“Fast IDentity Online”) Authenticator is a hardware device or software solution designed to provide secure access to services and applications through robust, user-friendly authentication methods. FIDO Authenticators support multiple authentication technologies including biometrics (such as fingerprint recognition, facial recognition), security keys, and mobile devices.
Strong Authentication: By using cryptographic techniques, FIDO Authenticator ensure a high level of security, making unauthorized access significantly more difficult.
Privacy-Focused: Biometric data, when used, does not leave the device. This ensures that personal information is kept secure and private.
Ease of Use: FIDO authentication simplifies the user experience by allowing a single gesture, like a fingerprint swipe or facial recognition, to quickly access services without remembering passwords.
Versatility: These authenticators are designed to work across a wide range of devices and platforms, ensuring seamless integration into users’ digital lives.
Phishing Resistant: Because authentication is tied to the user’s device and uses cryptographic keys, it is virtually impossible for attackers to replicate or steal credentials through phishing attacks.
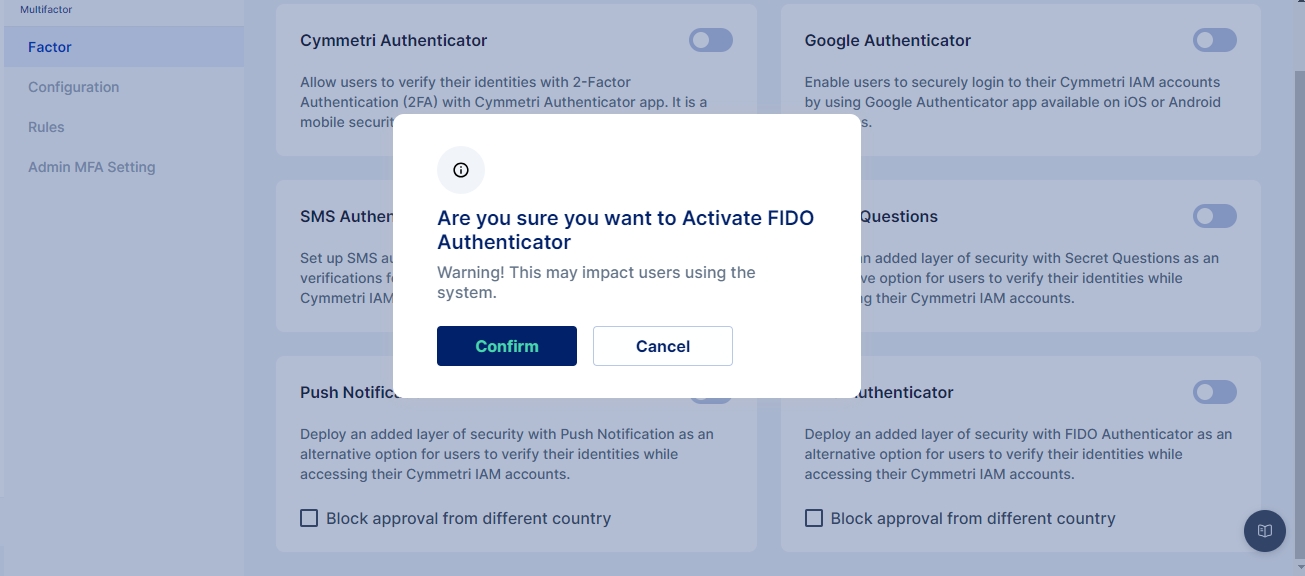
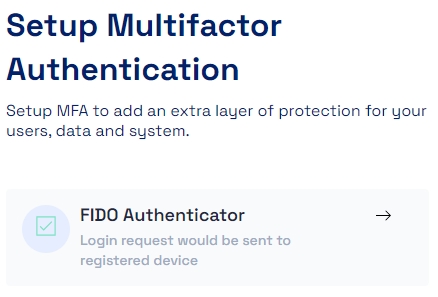
For configuring FIDO Authenticator in Cymmetri, select the FIDO Authenticator toggle button and click confirm to setup FIDO Authenticator as an MFA option
Next move to configure the rules for Multi-factor authentication policy for login
You may either click on the pencil icon to start editing the rule, or create a new rule as shown below:
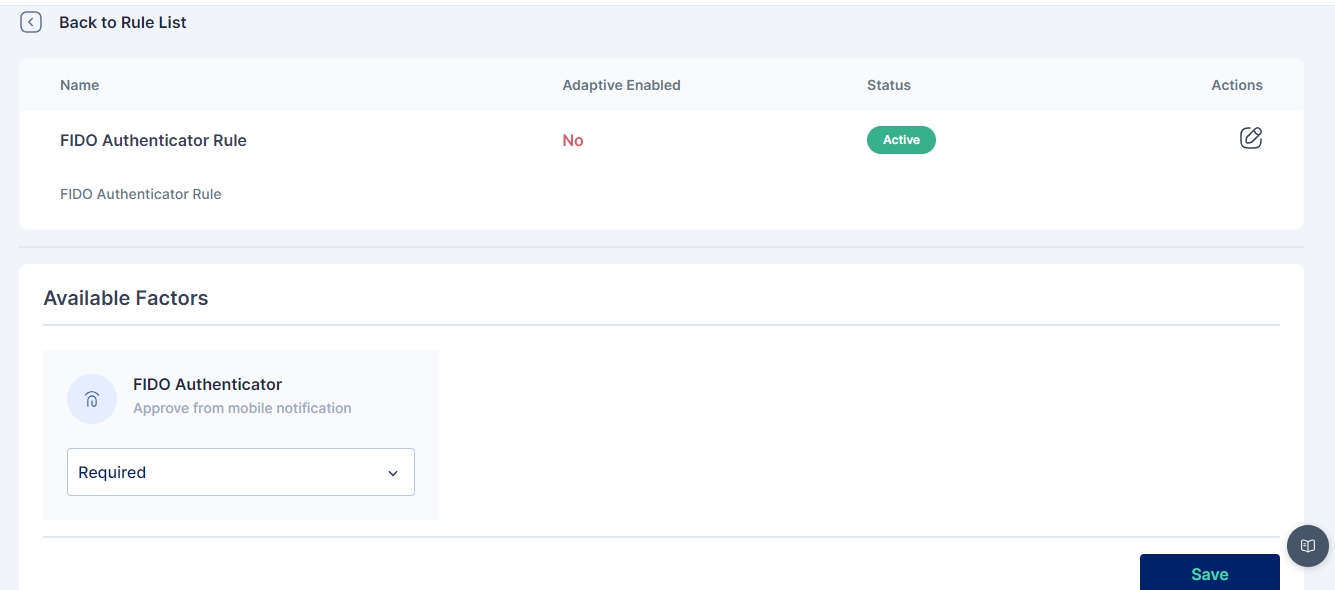
Once you have either created a new rule or edited an existing one, change the dropdown of the FIDO Authenticator factor to indicate that it is mandatory (required).
The options available for each factor are:
Required: This setting means that the corresponding factor is required to be enabled for each user, and every user must set up this factor in their next login.
Optional: This setting means that the corresponding factor is not required to be enabled for each user, and they may configure this option from their "My Workspace". Once the user configures it, they may use it for the purpose of second level of authentication during authentication. Disabled: This settings means that the corresponding factor is not required or enabled for each user, and the user may not configure or use it for authentication into the Cymmetri platform.
An administrator can further customize to whom the rule would be applicable by selecting user(s) or group of users in the "Assigned to" Tab, If the rule is to be applied to all the users then the "All Users" option need to be selected
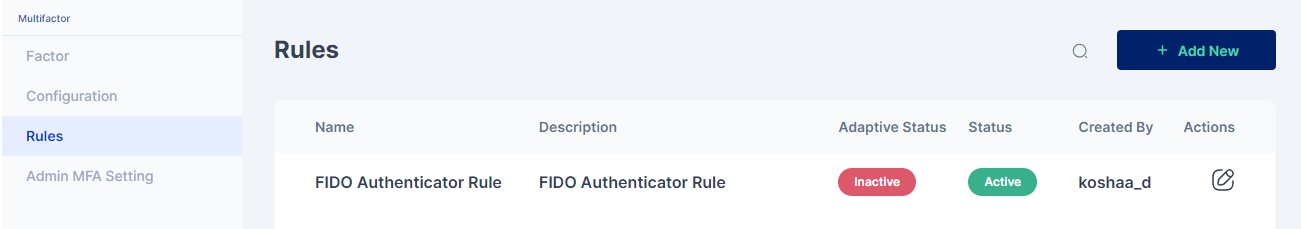
Once the changes are saved this is how the rule appears:
All subsequent logins of any user on the Cymmetri Identity platform will now require the use of the FIDO Authenticator mechanism.
The user needs to setup the Cymmetri Authenticator for receiving the push notification on the device, for which the user needs to download the Cymmetri Verifier app. The links below can be used to download the Cymmetri Verifier App on Android or IOS:
IOS- https://apps.apple.com/in/app/cymmetri-verify/id6455987489
Android - https://play.google.com/store/apps/details?id=com.cymmetri.verify
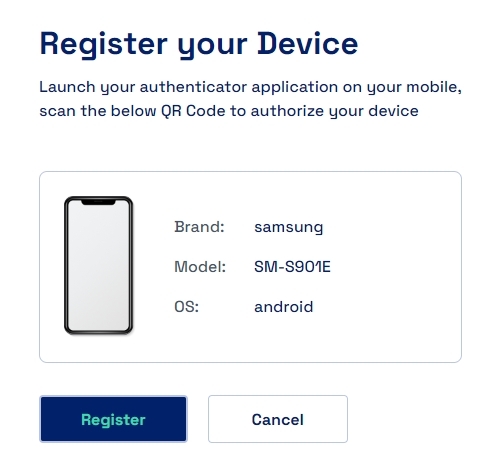
Once downloaded we need to scan the QR Code in the Cymmetri Verifier App to register the device
Once the device is registered successfully a notification is show on the dashboard
Now when the user selects FIDO Authenticator as an MFA mechanism and consent notification is sent to the mobile device (The consent notification appears as shown below) and the user needs to accept the consent in the stipulated time to be allowed to login also after the user accepts the consent the user needs to prove their identity by providing biometrics (such as fingerprint recognition, facial recognition).
Once successfully verified the user is redirected to the Dashboard
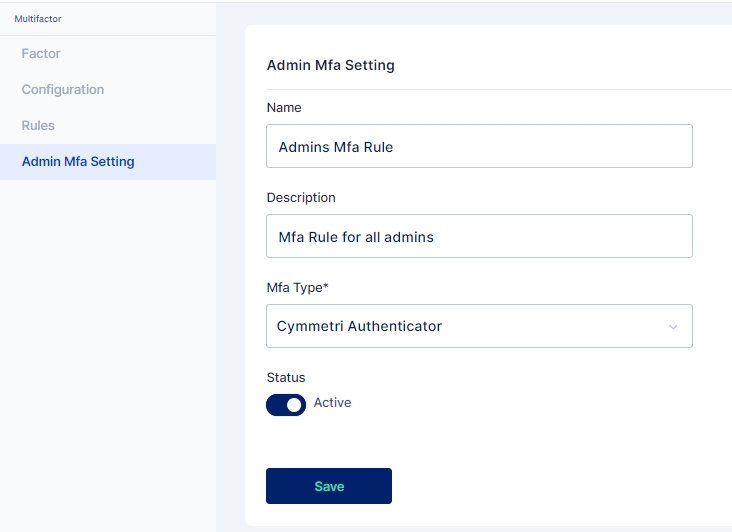
Admin MFA settings has been specifically designed to enhance security of administrative users by requiring a mandatory second-level authentication like Cymmetri Authenticator, Google Authenticator, Push Authenticator, SMS Authenticator, or Secret Questions. This extra layer of protection helps safeguard sensitive administrative logins, reducing the risk of unauthorized access and potential security breaches.
When configuring Admin MFA Setting administrators can choose the MFA Type from one of the following: Cymmetri Authenticator, Google Authenticator, Push Authenticator, SMS Authenticator, or Secret Questions and ensure that status is set to enabled.
Enabling Admin MFA ensures that administrators are always asked for a second level of authentication when they login into Cymmetri.
In our increasingly digitized world, safeguarding personal and sensitive information is of paramount importance. With cyber threats on the rise, traditional passwords alone are no longer sufficient to protect our digital identities and assets. This is where Multi-Factor Authentication (MFA) comes into play. MFA is a robust security measure that enhances online protection by requiring users to provide multiple forms of authentication before granting access to an account or system.
MFA typically involves three factors:
Something You Know: This is the traditional password or PIN that users have to enter. While passwords alone are susceptible to brute-force attacks or phishing, the combination with other factors adds an extra layer of security.
Something You Have: Users are also required to possess something physical, like a smartphone, smart card, or a security token. This device generates a one-time code, further authenticating the user.
Something You Are: This factor is based on biometric data, such as fingerprints, facial recognition, or retina scans. Biometrics add a high level of security as they are unique to each individual.
MFA offers several advantages:
Enhanced Security: By combining multiple authentication factors, MFA makes it significantly more challenging for cybercriminals to gain unauthorized access. Even if they have a password, they would still need physical access to a user's second-factor device or their biometric data.
Mitigation of Password Vulnerabilities: Since passwords are vulnerable to theft or hacking, MFA helps reduce the risks associated with compromised passwords.
Improved Compliance: In various industries, compliance standards require the implementation of MFA to protect sensitive data, reinforcing its importance in data protection and privacy.
User-Friendly: Modern MFA solutions are designed to be user-friendly, offering a seamless authentication experience through mobile apps or SMS verification.
Multi-Factor Authentication is a critical tool in our arsenal against the growing threats in the digital realm. By combining what we know, have, and are, MFA offers a robust defense, ensuring that only authorized individuals gain access to sensitive information and systems. It's a key element in the ongoing battle to safeguard our digital identities and data.
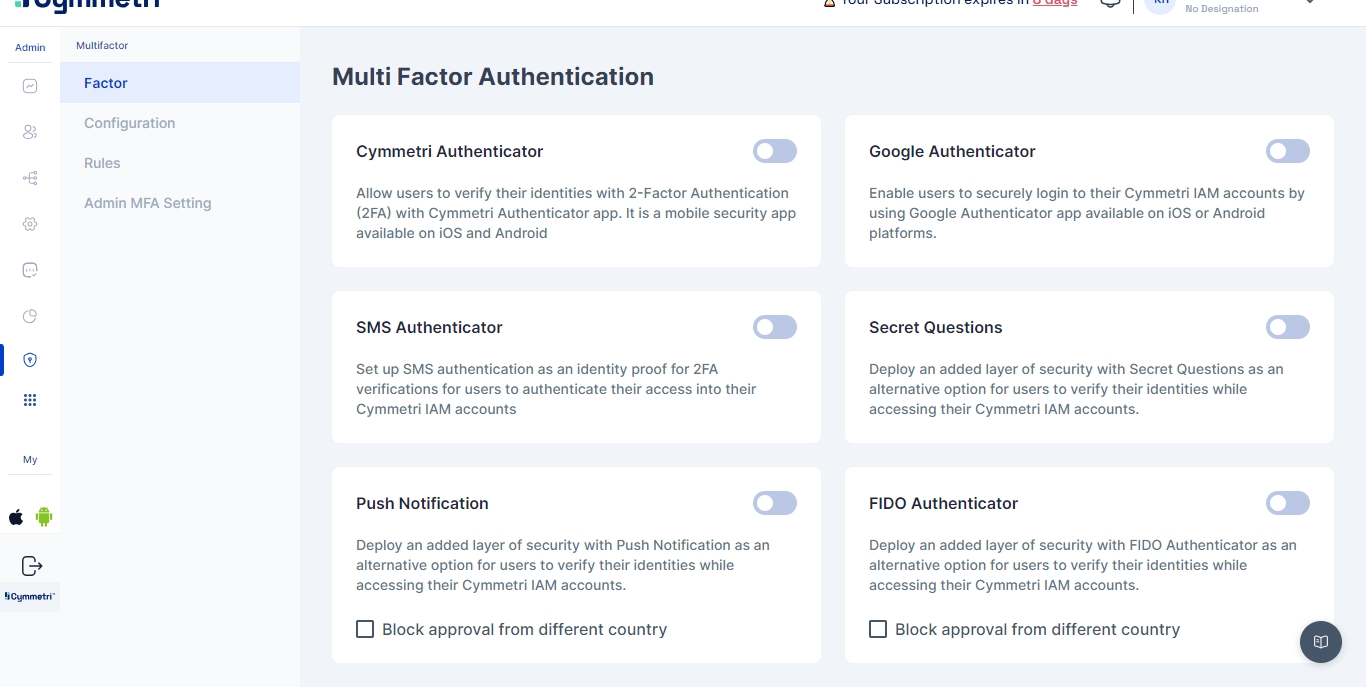
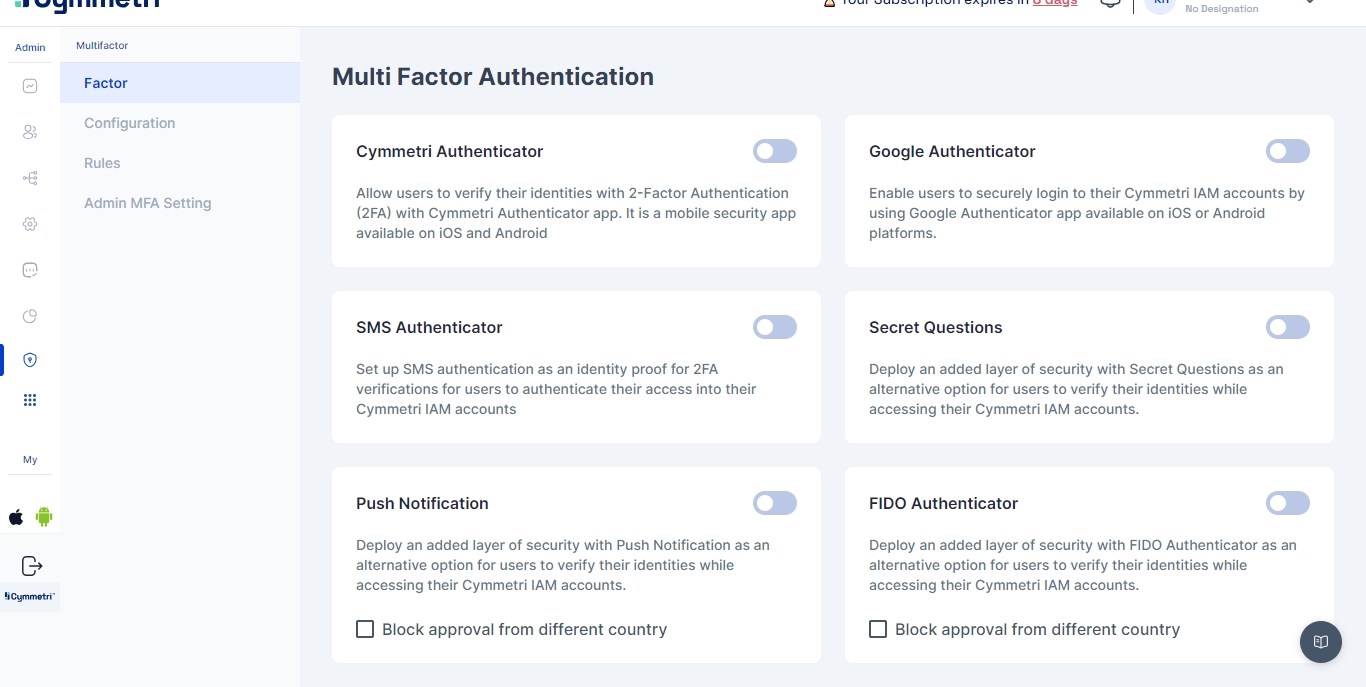
Multi-Factor Authentication is a mechanism used across the Cymmetri platform to deal with second level authentication.Typically employed using off-band mechanisms, Cymmetri allows flexibility by introducing both modern and traditional mechanisms, such as:
Cymmetri Authenticator
Push Authenticator
Google Authenticator
SMS Authenticator
Secret Questions
FIDO Authenticator
Access Multi-factor authentication by going to Products > Multifactor
Next, we select Factor sub-menu
In the upcoming sections we will explore each of these mechanisms.