Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
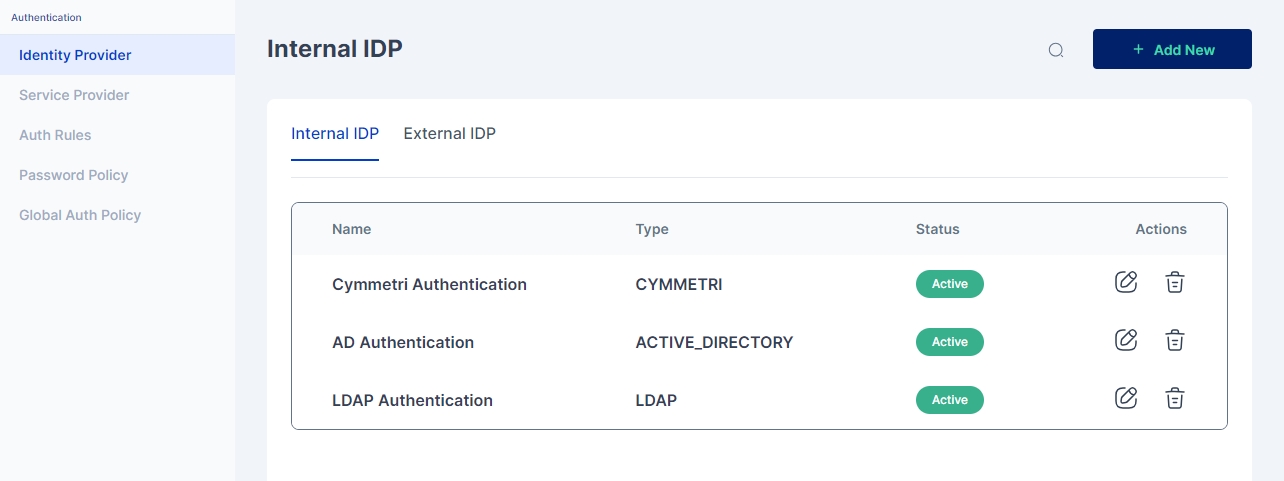
Cymmetri's Internal Identity Provider (IDP) is a powerful authentication solution that supports seamless integration with various Identity Providers (IDPs).
We will explore the configuration options for three types of IDPs:
Cymmetri,
Active Directory, and
LDAP.
The flexibility of the Cymmetri Internal IDP allows you to manage multiple IDPs of the same type, making it easy to adapt to diverse environments with different Active Directory/ LDAP instances. Cymmetri's Internal IDP aims to provide a centralized and adaptable authentication solution for your environment, supporting various IDP types.
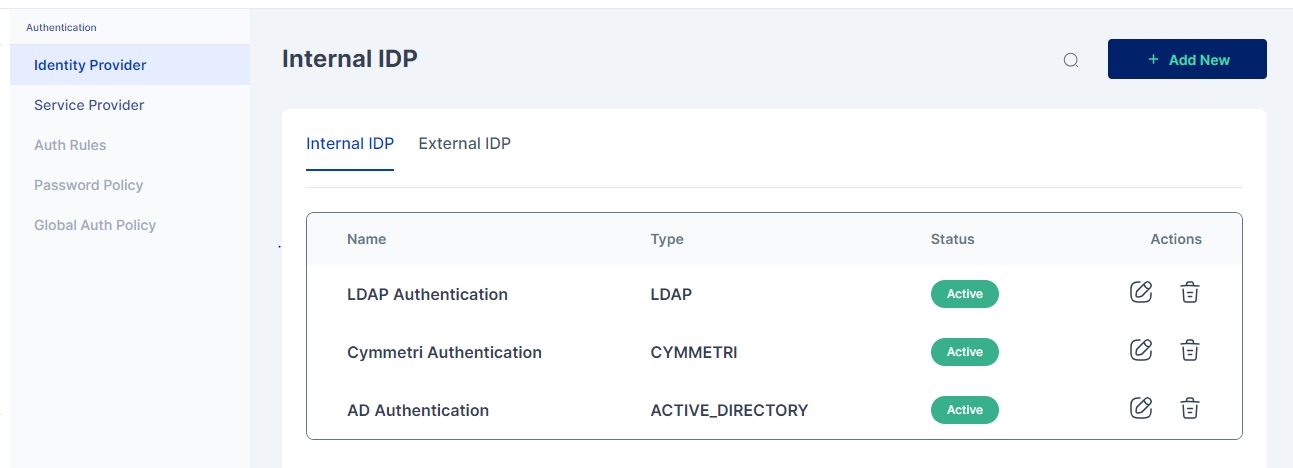
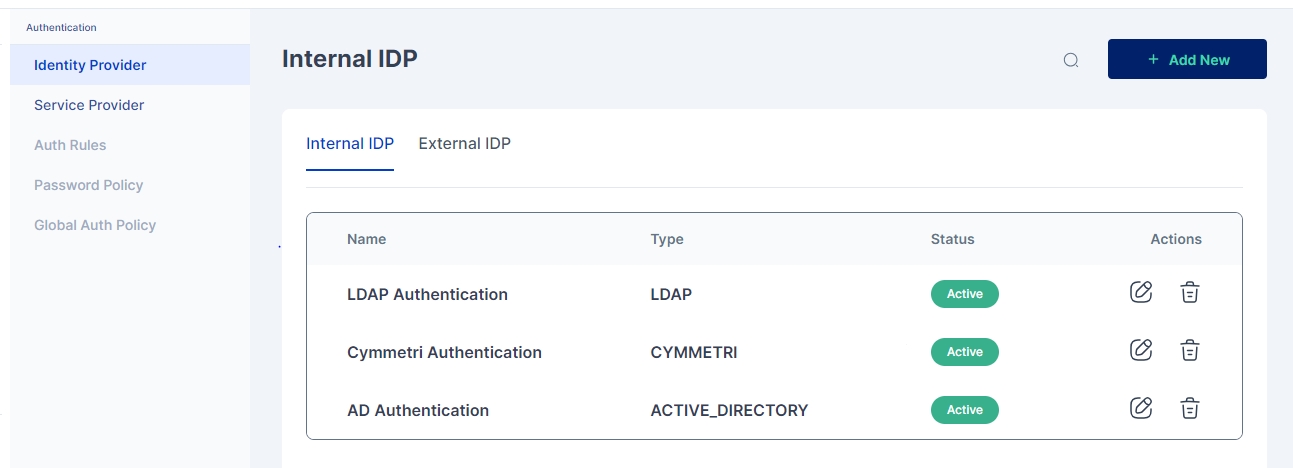
To access Internal Identity Providers navigate to Authentication-> Identity Provider->Internal IDP
To customize the applicability of different IDPs, administrators need to configure Authentication Rules. These rules enable the configuration of various conditions. When these conditions are met, the corresponding authentication mechanism or IDP is used for user authentication.
To access Internal Identity Providers navigate to Authentication-> Identity Provider->Internal IDP.
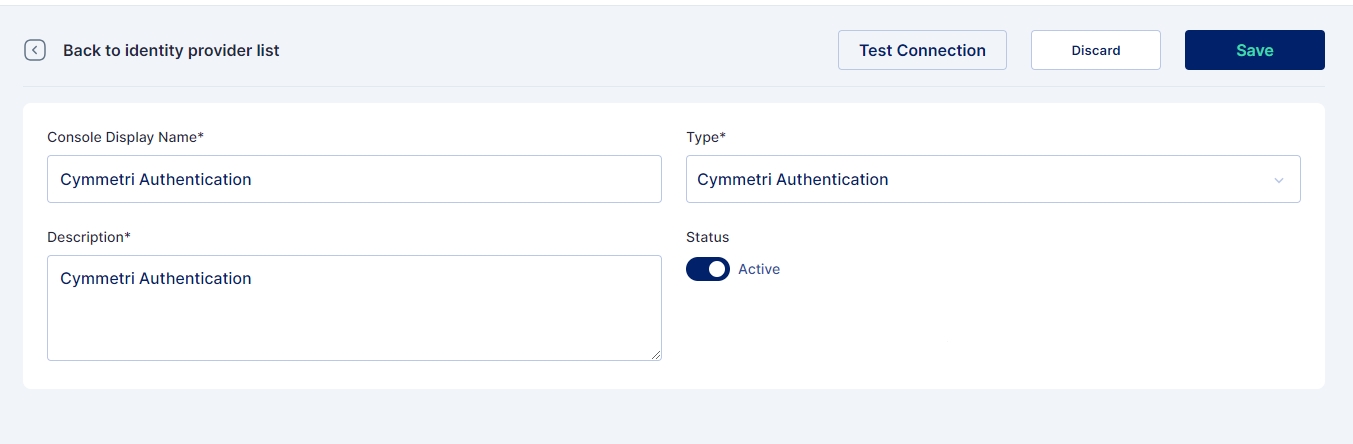
Since Cymmetri is a default Internal IDP no configuration is needed for it. An administrator may still have an option to disable Cymmetri Authentication which can be done by editing the Cymmetri Authentication Internal IDP mechanism.
An administrator may also change the Display Name and/ or Description as shown in the screen above.
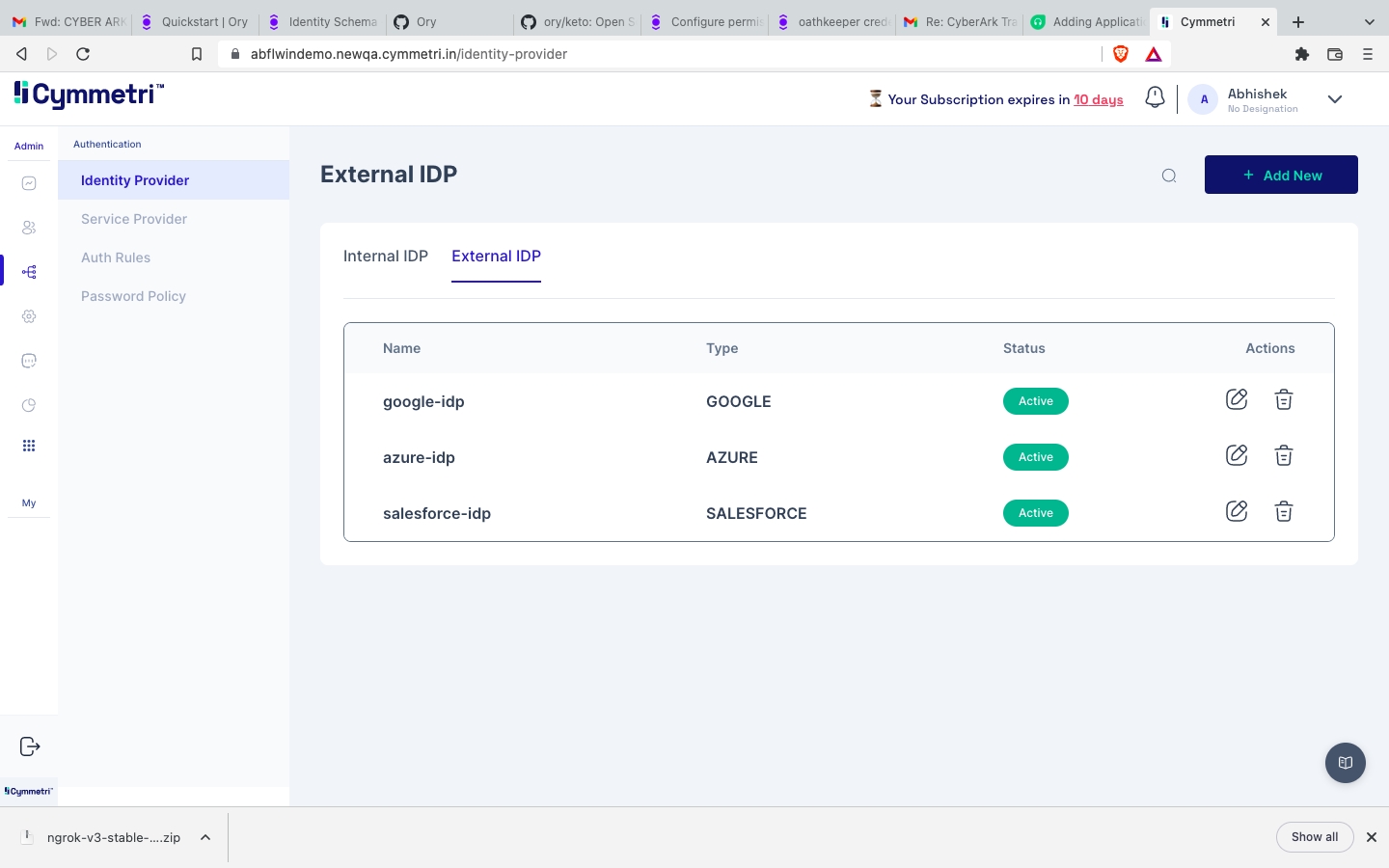
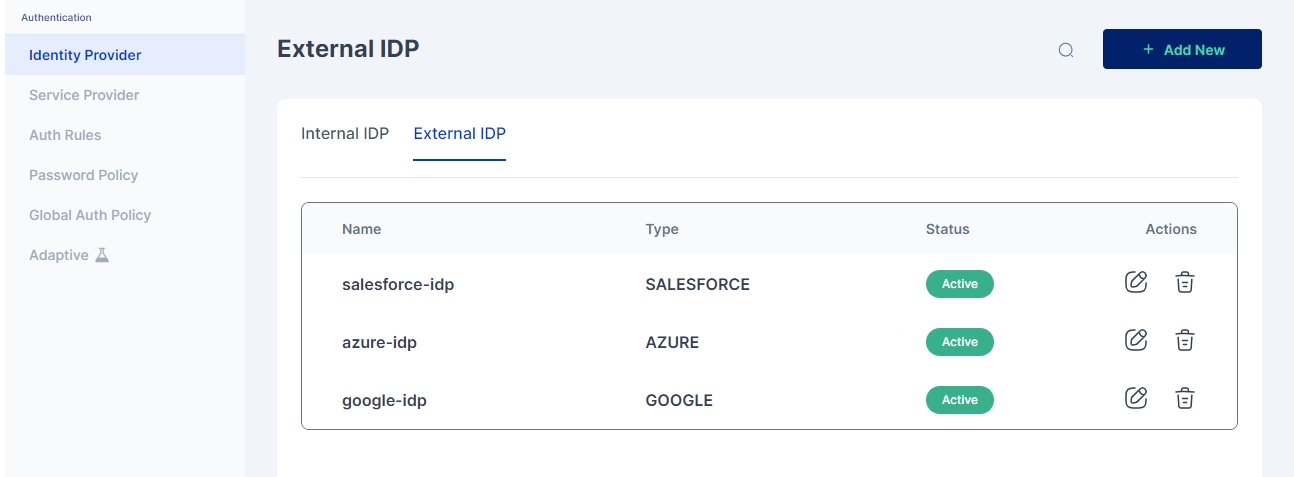
Cymmetri's External Identity Provider (IdP) feature allows you to authenticate user identities using different IdPs for various user types. This flexible configuration enables you to streamline access for both internal employees and external users, such as consultants, vendors, and their employees. In this documentation, we will guide you through the process of configuring an External IdP within Cymmetri's identity and access management system.
For internal employees, you can configure Cymmetri's Internal IdP mechanisms like Active Directory or LDAP. This allows seamless authentication for your organization's employees.
Whereas external users, such as consultants, vendors, and their employees, can be verified using popular External IdPs like Google, Azure, Salesforce, or any other supported IdP. This approach simplifies access for external parties while maintaining security and control.
To configure an External IdP in Cymmetri, the administrator needs to provide the following information:
Name: A descriptive name for the External IdP configuration.
IDP Type: The type or provider of the IdP (e.g., Google, Azure, Salesforce).
Entity ID: The unique identifier for the IdP entity.
SSO Service URL: The URL where Single Sign-On (SSO) requests should be sent.
Destination: The location where authentication responses should be directed.
Protocol Binding: The protocol used for communication with the IdP (e.g., HTTP Post, HTTP Redirect).
Name ID Policy and Value: This policy defines the format and content of the identifier that represents the authenticated user. For example:
Policy: email
Value: email
Certificate: The certificate used for secure communication between Cymmetri and the External IdP.
In the upcoming sections we will learn step-by-step implementation of the various External IDP mechanisms:
Google serves as a robust external Identity Provider (IDP) through its Identity Platform. Leveraging various authentication mechanisms, it facilitates secure user authentication for Cymmetri. This allows users to sign in with their Google credentials, ensuring a seamless and familiar login experience. Google's IDP mechanism is adopted for its reliability and user-friendly authentication processes, thus making it a preferred choice for integration into Cymmetri as an External IDP.
Azure AD serves as a robust external IDP, facilitating secure access into Cymmetri. Employing industry standards like OAuth 2.0 and SAML, it enables Single Sign-On (SSO) and multi-factor authentication. Azure AD seamlessly integrates with Cymmetri providing easy identity management and ensuring compliance with modern security standards.
Salesforce as an external Identity Provider (IDP) offers robust authentication and access control solutions. Utilizing industry-standard protocols like SAML and OAuth, Salesforce IDP ensures secure Single Sign-On (SSO) experiences.
Configuring External Identity Providers in Cymmetri gives you the flexibility to authenticate user identities using different IdPs tailored to specific user types. Whether it's for internal employees or external collaborators, Cymmetri's External IdP feature ensures secure and convenient access to your organization's resources.
Within Cymmetri, the authentication process is highly customizable through the definition of authentication rules. While the platform provides a default authentication rule, administrators have the ability to define custom authentication rules that align with the specific business needs and the variety of identity providers at their disposal.
For instance, let's consider a scenario where an organization has distinct user types, such as regular employees, contractors, and administrators. The administrators might require to authenticate employees with Active Directory as the identity provider and use Cymmetri's own authentication engine to verify the identity of vendors and contractors. With Cymmetri's flexibility, administrators can create authentication rules that cater to these varying requirements, ensuring a tailored and secure authentication experience based on user roles and organizational needs.
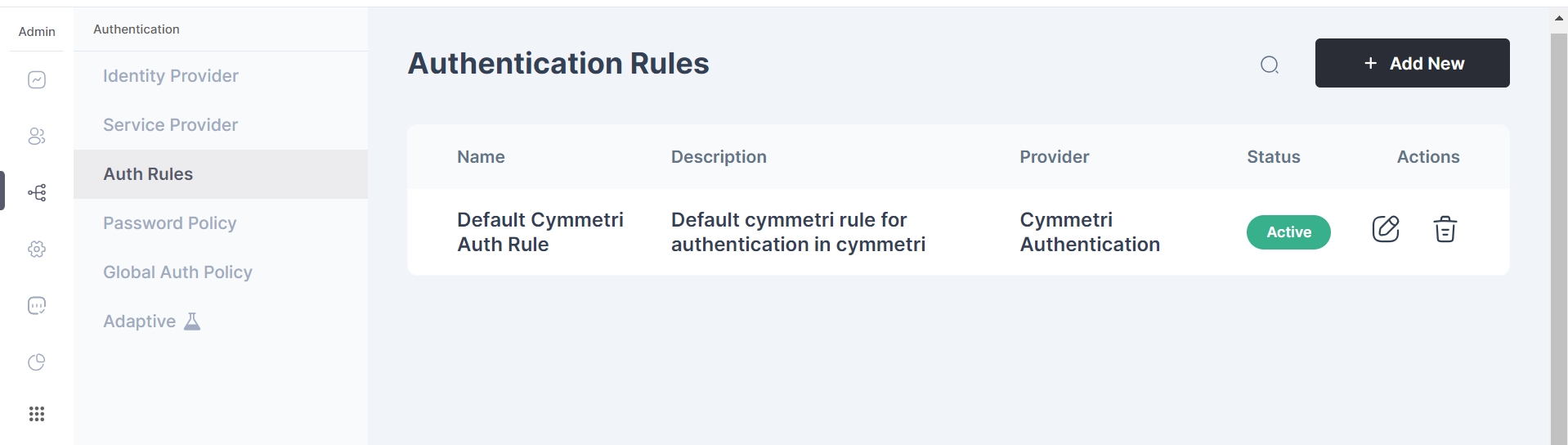
Admins can find authentication rules in Authentication tab in Cymmetri.
To create a new authentication rule, admin must simply click on the "Add New" button on the top right corner of the page.
The admin must fill in the following details
The name of the rule
Identity provider radio button ( Enable for External IDP or Disable for Internal IDP)
Identity provider
Description of the rule
Active Radio Button
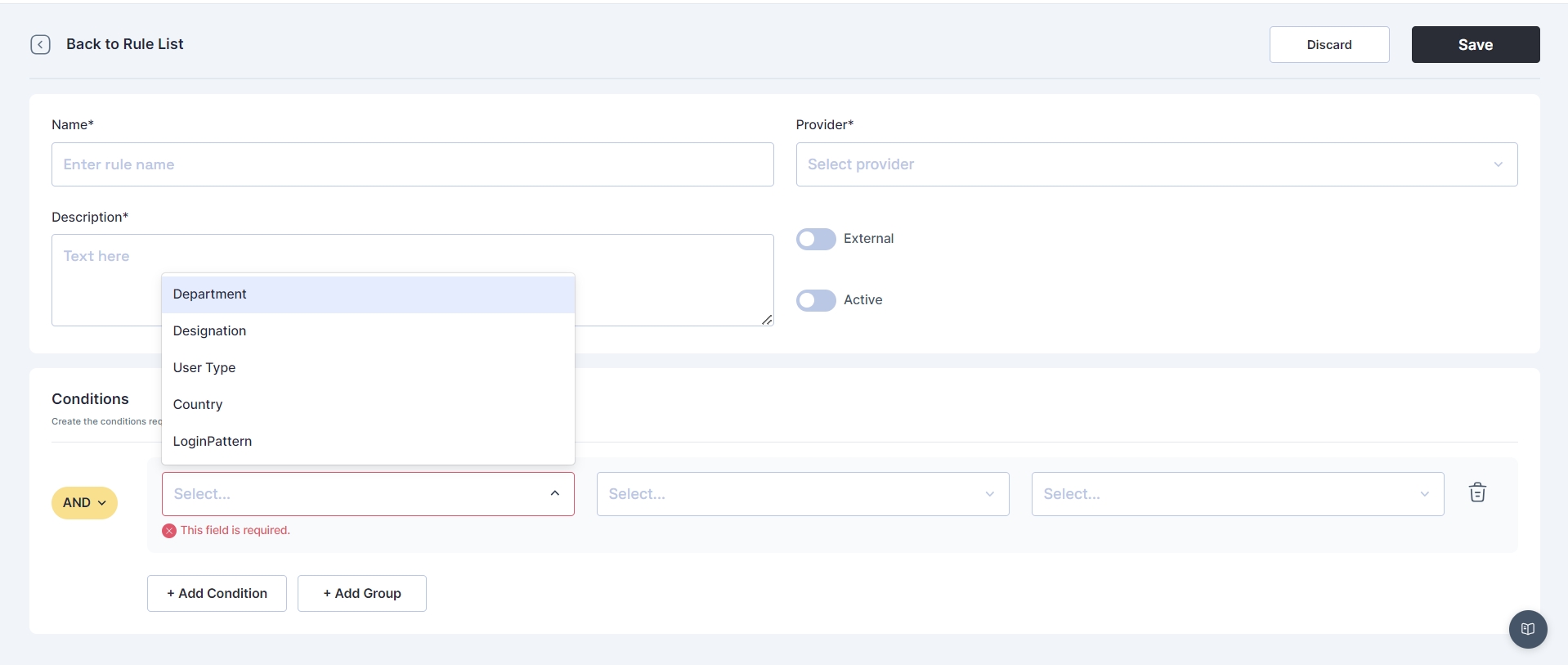
Conditions
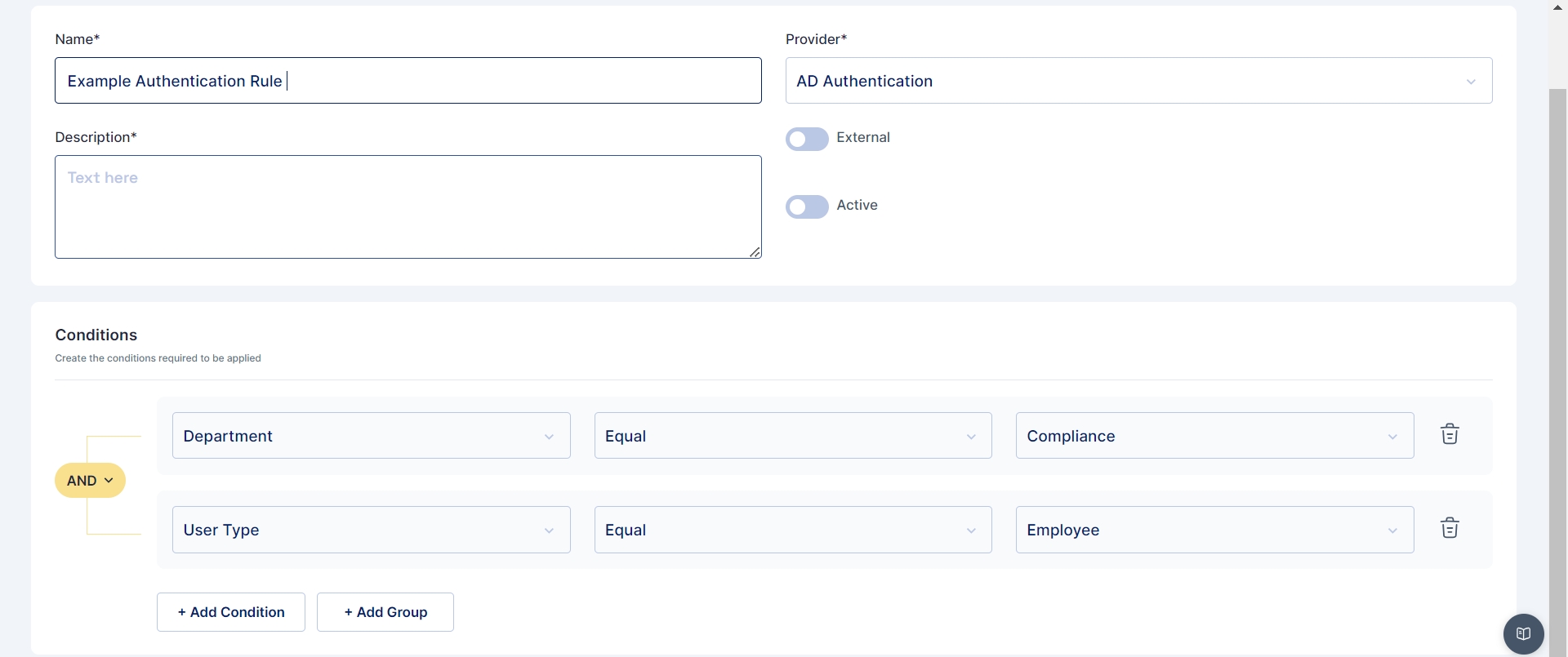
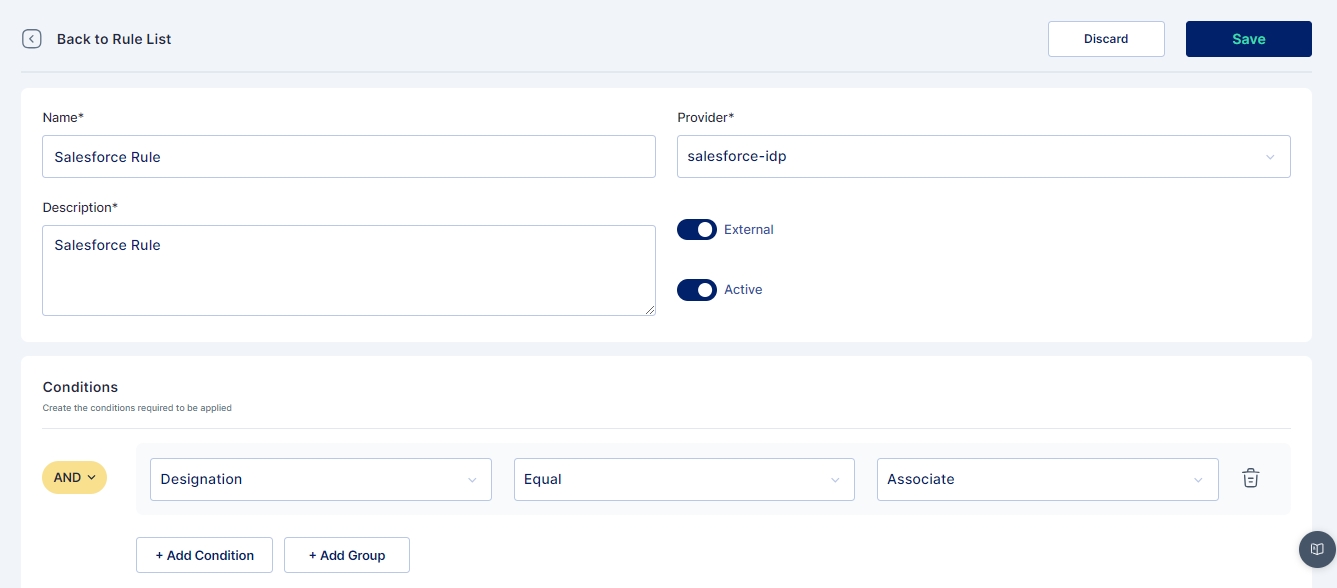
The administrator has the capability to establish rules based on conditions like: Department, designation, User Type, country, and Login Pattern.
Subsequently, the administrator defines regular expressions for conditions, specifying whether they should be equal to, not equal to, and assigns corresponding values.
Cymmetri facilitates the creation of multiple conditions for an authentication rule and provides the option to group these conditions using AND or OR logic.
In the image presented above, an exemplar authentication rule is showcased. This rule is structured to authenticate a user in Cymmetri through Active Directory if two conditions are met: the user's department must be equal to "Compliance," and the user type should be "Employee."
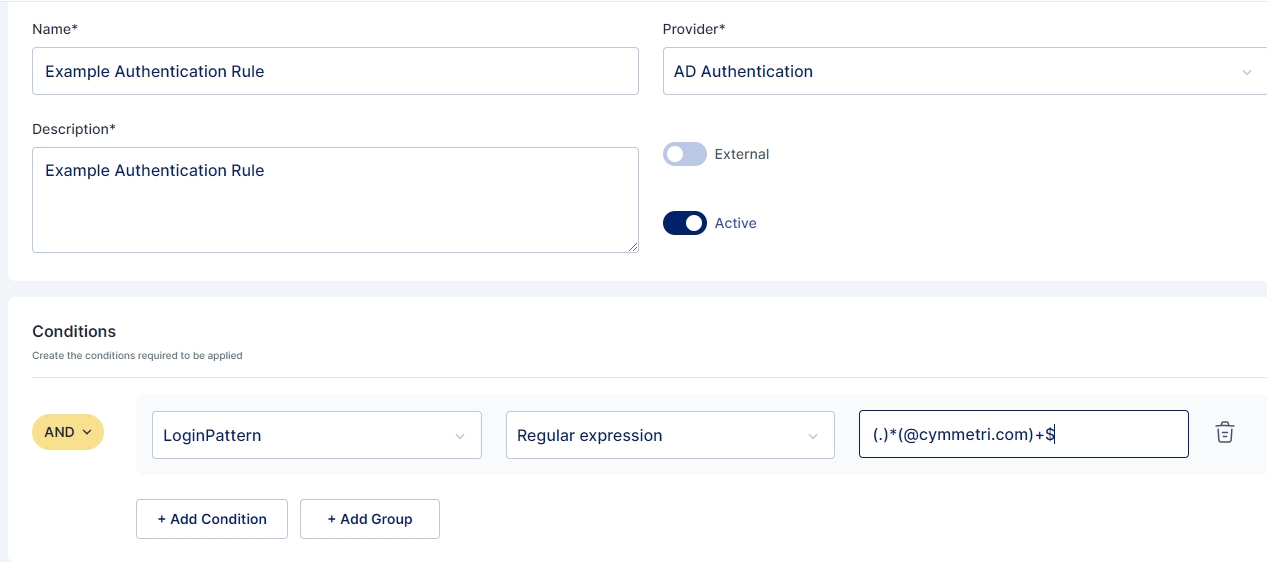
Similarly If you wish to set the Identity provider for users having email address ending with "@cymmetri.com" then you may select condition as LoginPattern > Regular Expression and its value as (.)*(@cymmetri.com)+$; and save the details.
This demonstrates how authentication rules can be precisely configured to suit specific criteria and streamline the authentication process based on defined conditions.
Active Directory (AD) is a robust Identity Provider (IDP) in enterprise environments. It authenticates and authorizes users, facilitating seamless access to resources. AD centralizes user management, streamlining security protocols and ensuring efficient user provisioning.
Active Directory can be utilized in Cymmetri as an Identity Provider (IDP), leveraging existing AD user accounts to access Cymmetri, as the platform supports the LDAP protocol.
For configuring AD as an Identity Provider, the primary service needed is the Adapter Service.
The Adapter Service or Auth Adapter Service is exposed as a rest service that runs on HTTPS and acts as an adapter to facilitate authentication using the LDAP protocol which is often employed for authentication purposes in various systems and every adapter service instance is called by the secret generated while installation/configuration of adapter service.
The rest endpoints are called by cymmetri-cloud AuthenticationService to connect to On-Prem AD/Ldap or cloud AD/Ldap. The AdaptorService is used to test connections, authenticate, change, and reset the password of a user.
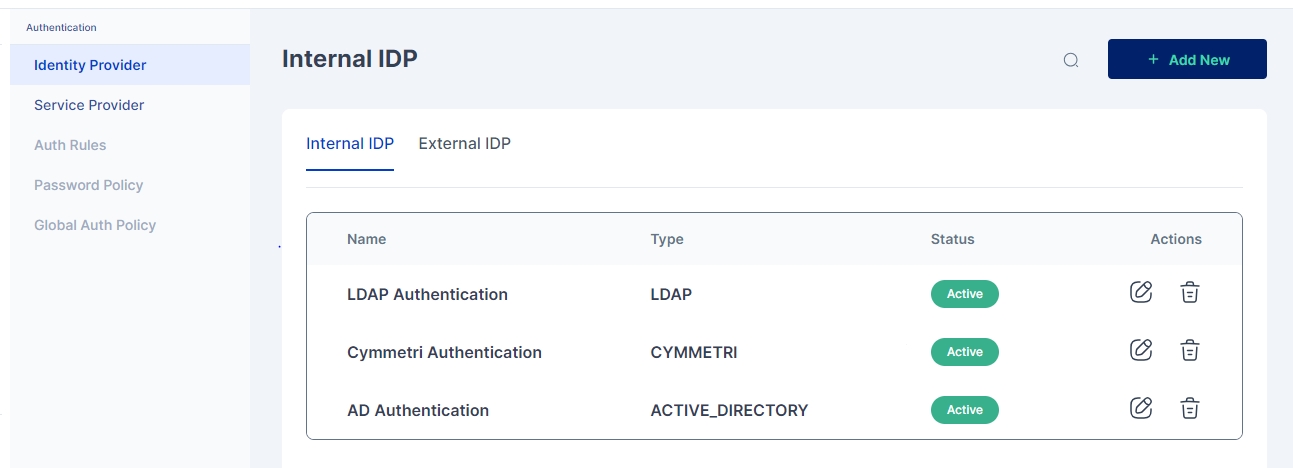
For configuring Active Directory as an internal IDP navigate to Authentication -> Identity Provider -> Internal IDP. Here you may either configure the already created AD Authentication instance or +Add New.
In either case, a screen opens where you need to provide the below-mentioned details.
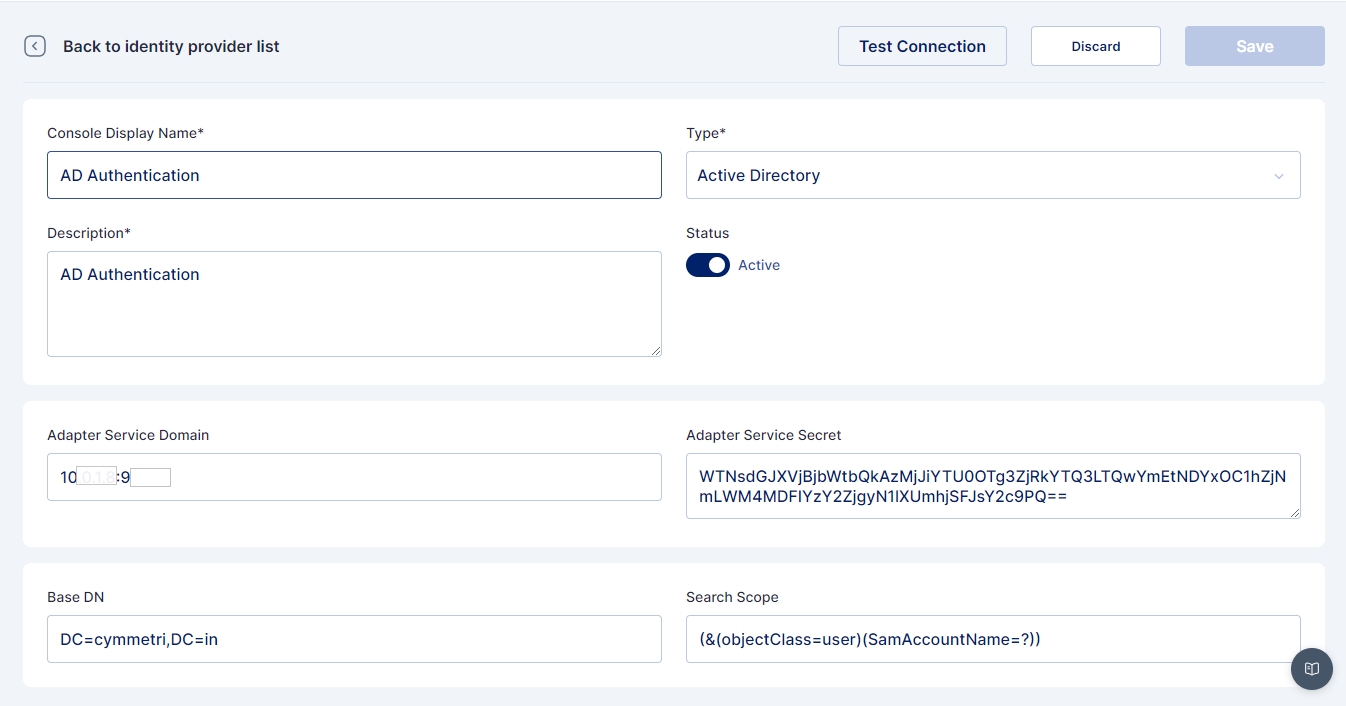
Name: AD Authentication
IDP Type: Active Directory
Description: A general description of the IDP type
Status: Active
Adapter Service Domain: Location (IP) of the server on which the Adapter Service is deployed
Adapter Service Secret: The secret generated while installing/configuring of adapter service
Base DN: Active Directory root domain name
Search Scope: A search scope for locating users in Active Directory
Once all the details are entered Save the changes and Test the Connection using the Test Connection button.
For enabling Active Directory to be used as an IDP for a specific set of users an Authentication Rule needs to be configured. Here you can see the steps on how to configure Authentication Rules.
Once the rule is configured, whenever a user matches the rule conditions, their credentials are verified against those stored in the Active Directory. Upon successful verification, the user is granted access to log in to Cymmetri.
A password policy is a set of rules and requirements established by an organization or system to govern how users create and manage their passwords.
The purpose of a password policy is to enhance security by promoting the use of strong, unique passwords and minimizing the risk of unauthorized access.
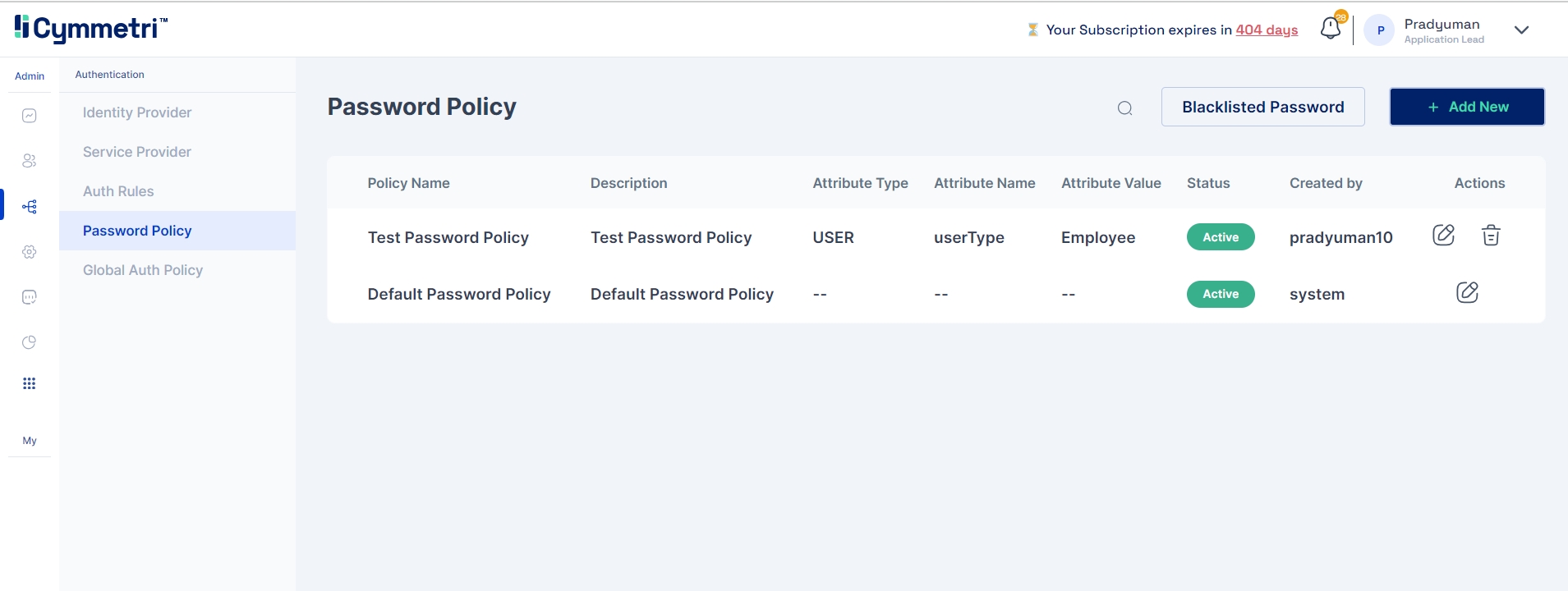
In Cymmetri, only the admin can create a password policy bby navigating to the authentication section and then in password policy.
Upon landing the user can view a default Cymmetri password policy which cant be deleted or deactivated.
To create a new password policy, the admin clicks on the add new button on the top right corner of the page.
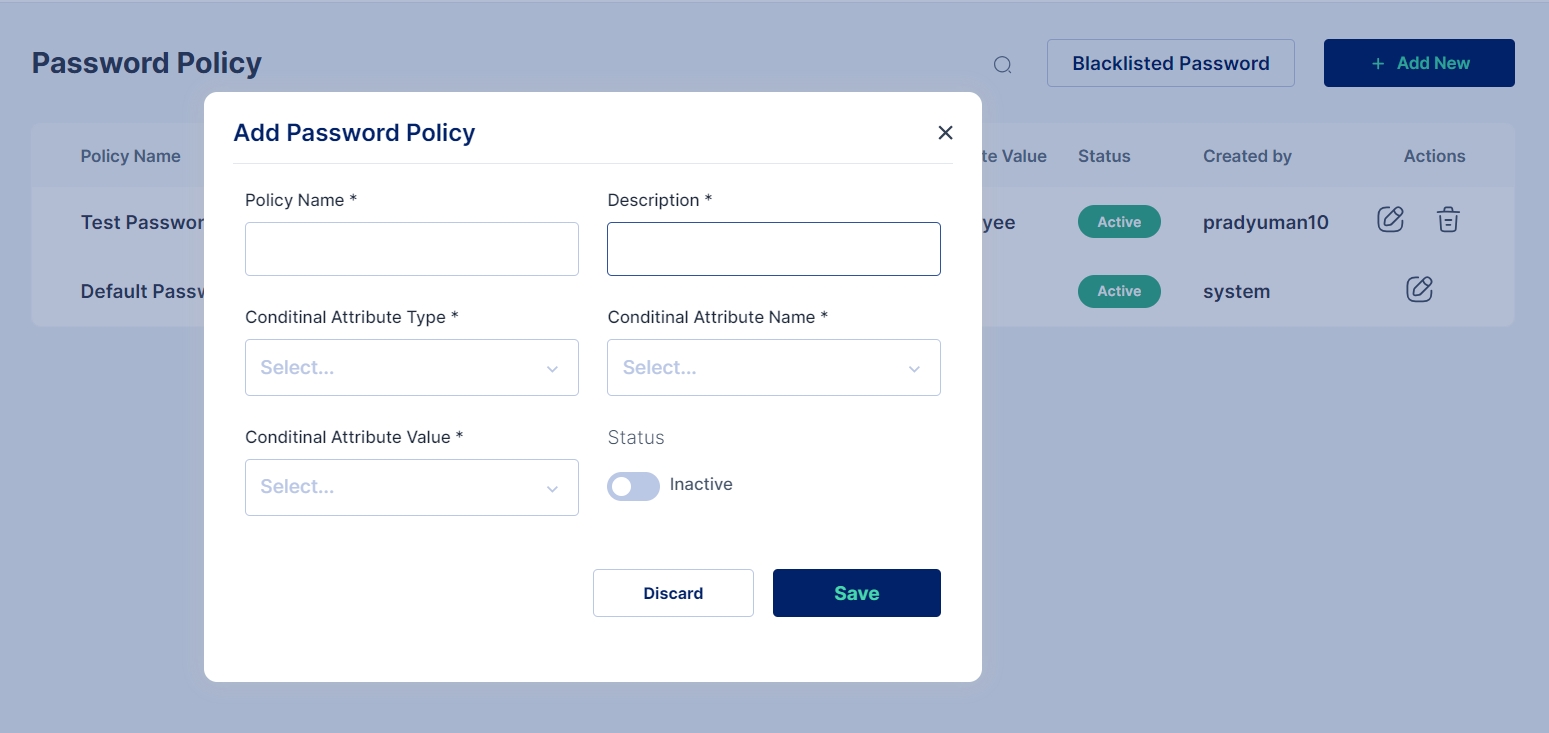
The user has to fill in the password policy form with the below details
Policy Name - Name of the policy
Description
Conditional attribute type - Default - User (Non modifiable)
Conditional attribute Name - Default - User Type (Non modifiable)
Conditional attribute value - ( Consultant, Employee, Vendor)
After saving the detail, a new password policy is created. The next step is to define the password policy. This is done by clicking on the edit button in front of the record.
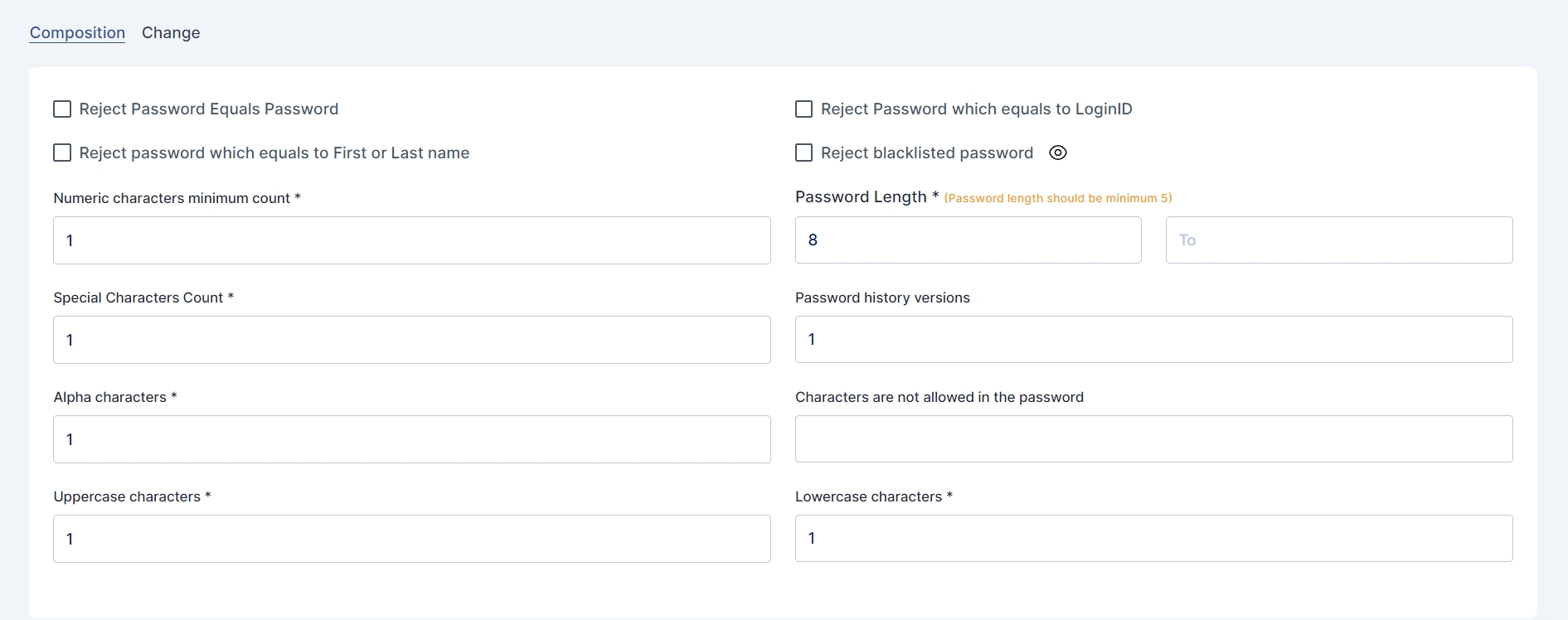
The admin can define the composition of the password. By rejecting
Password equals Password
Password which equals to LoginID
Password which equals to first or Last Name
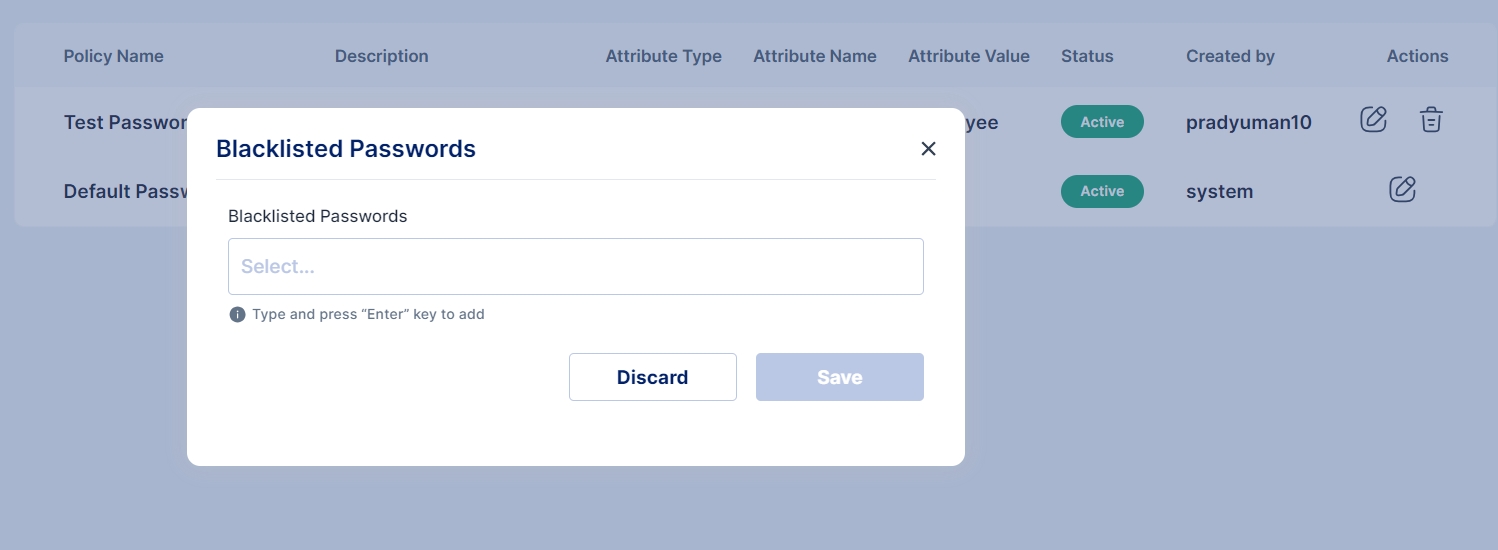
Blacklisted Password
The admin can also establish the following parameters
Numeric characters minimum count
Password Length
Special characters count
Password History versions
Alpha characters
Uppercase characters
Lowercase characters
Characters not allowed in the password
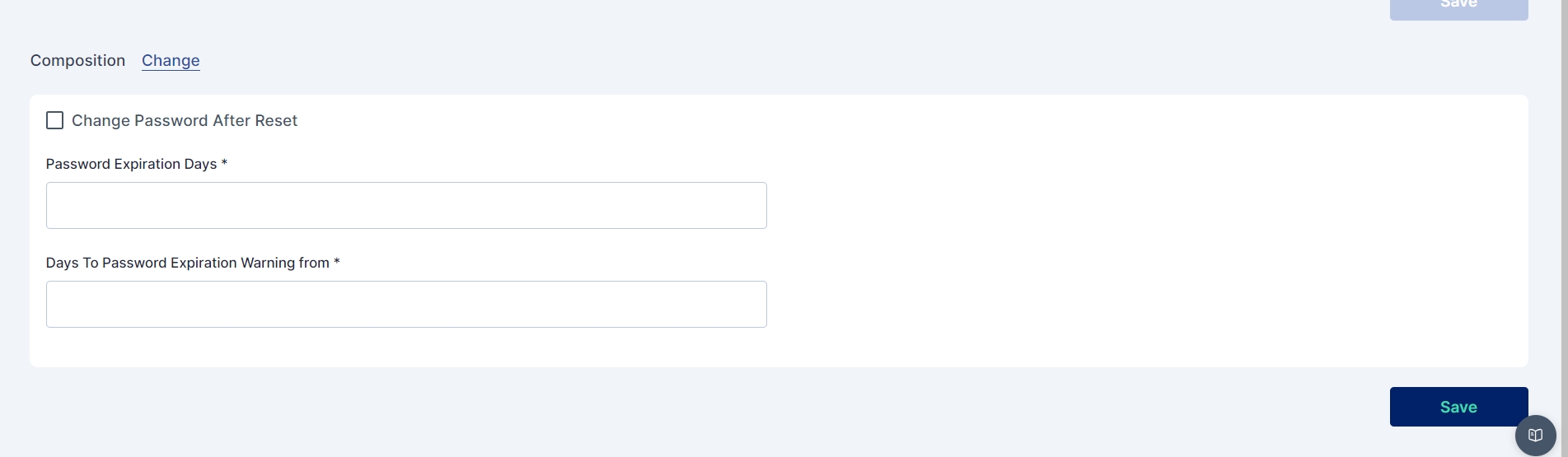
In the "change" subsection the admin can also define:
Password expiration days
Password expiration warning from (no of days)
Whether to change password on reset
The administrator also has the capability to set prohibited passwords, preventing users from using those specific passwords.
Lightweight Directory Access Protocol (LDAP) serves as an important Identity Provider (IDP) in enterprise environments. It authenticates and authorizes users, facilitating seamless access to resources. LDAP is commonly used as a directory service for managing user identities and authentication information within an organization.
LDAP can be utilized in Cymmetri as an Identity Provider (IDP), leveraging existing user accounts to access Cymmetri, as the platform supports the LDAP protocol.
For configuring LDAP as an Identity Provider one of the primary services needed is the Adapter Service.
The Adapter Service or Auth Adapter Service is exposed as a rest service that runs on HTTPS acts as an adapter to facilitate authentication using the LDAP protocol which is often employed for authentication purposes in various systems and every adapter service instance is called by the secret generated while installation/configuration of adapter service.
The rest endpoints are called by cymmetri-cloud AuthenticationService to connect to On-Prem AD/Ldap or cloud AD/Ldap. The AdaptorService is used to test connections, authenticate, change, and reset the password of a user.
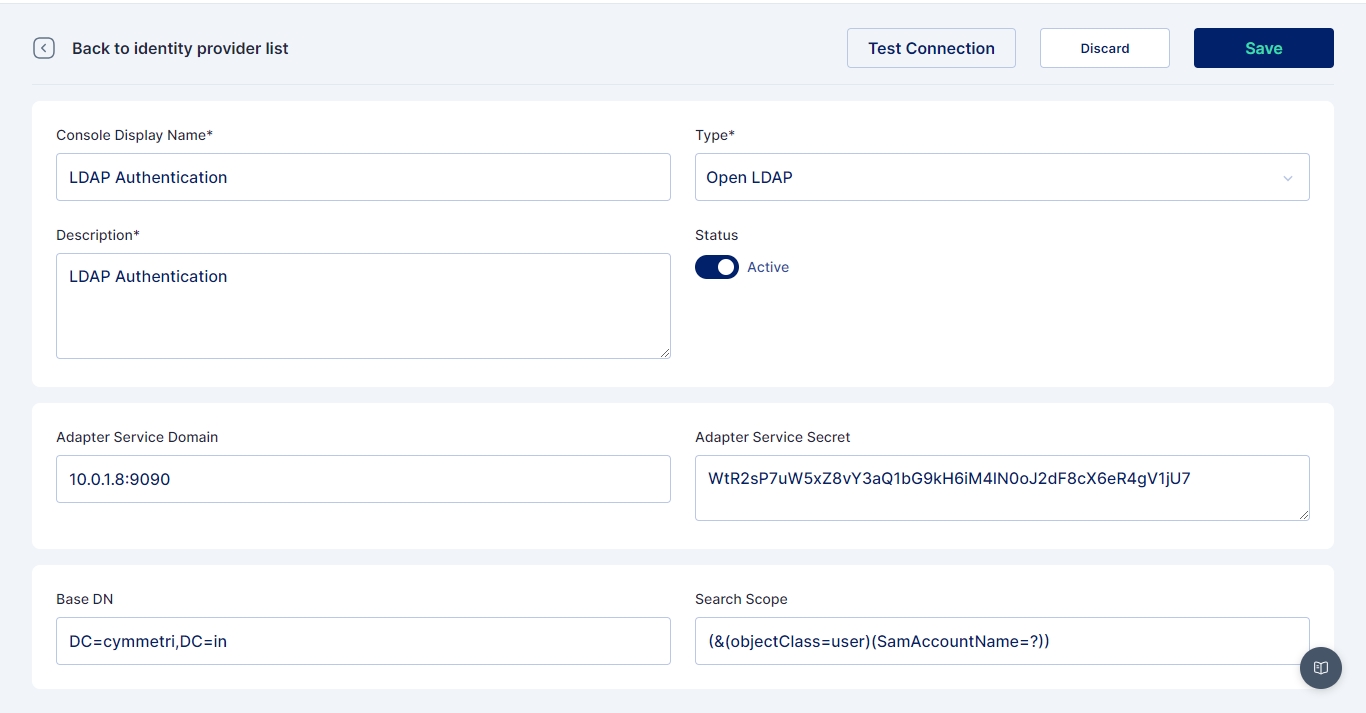
For configuring Active Directory as an internal IDP navigate to Authentication -> Identity Provider -> Internal IDP. Here you may either configure the already created LDAP Authentication instance or +Add New
In either case, a screen opens where you need to provide the below-mentioned details
Name: LDAP Authentication
IDP Type: Open LDAP
Description: A general description of the IDP type
Status: Active
Adapter Service Domain: Location (IP) of the server on which the Adapter Service is deployed
Adapter Service Secret: The secret generated while installing/configuring of adapter service
Base DN: LDAP root domain name
Search Scope: A search scope for locating users in LDAP
Once all the details are entered Save the changes and Test the Connection using the Test Connection button.
For enabling Open LDAP to be used as an IDP for a specific set of users an Authentication Rule needs to be configured. Here you can see the steps on how to configure Authentication Rules.
Once the rule is configured, whenever a user matches the rule conditions, their credentials are verified against those stored in LDAP. Upon successful verification, the user is granted access to log in to Cymmetri.
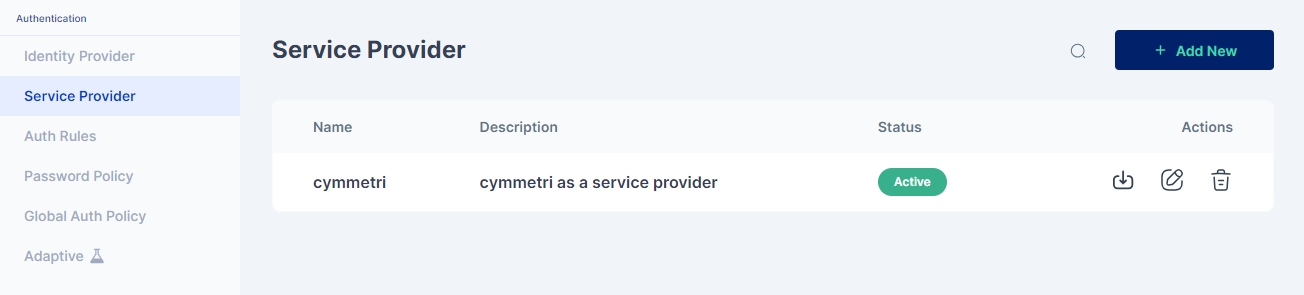
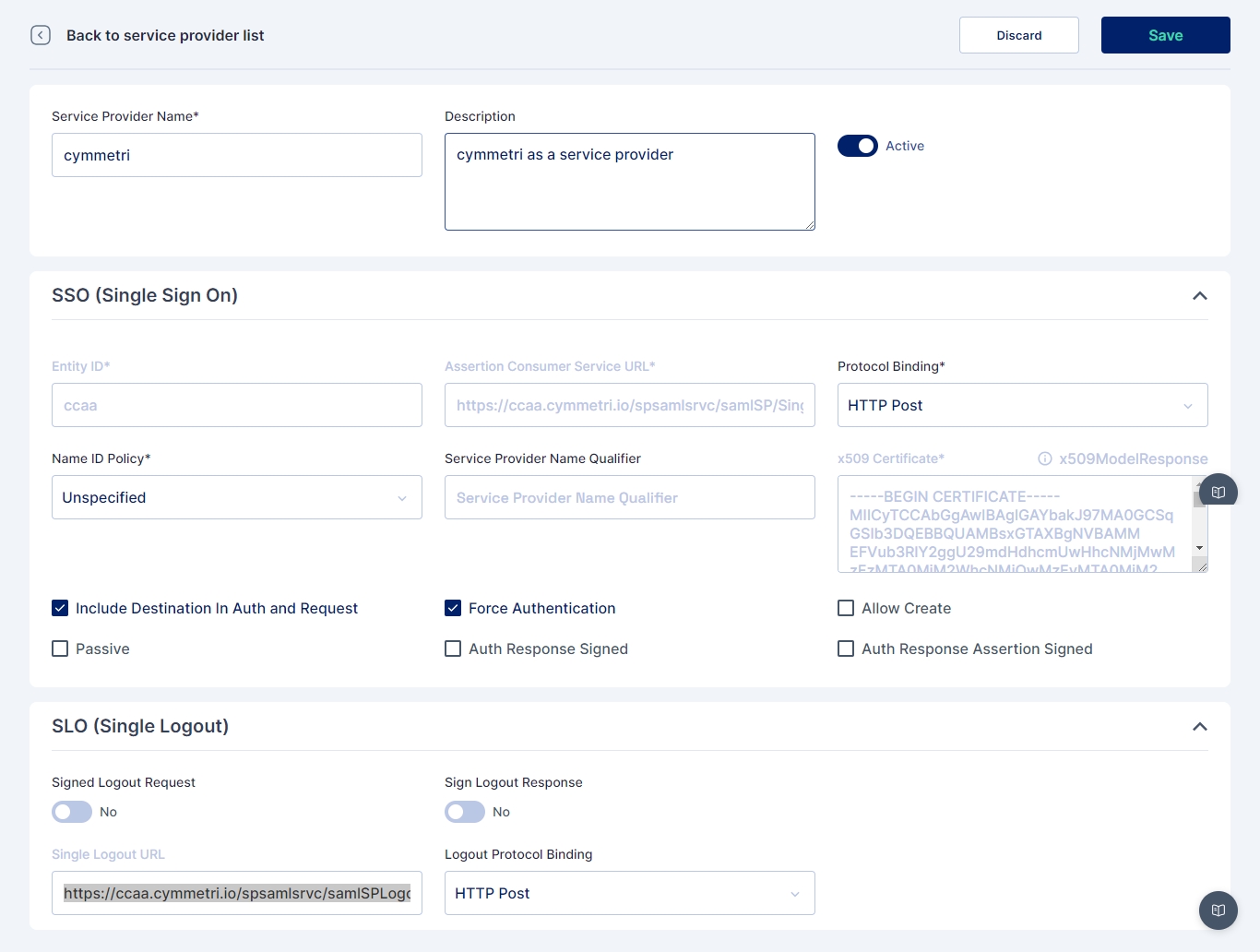
Administrator needs to go to Authentication->Service Provider
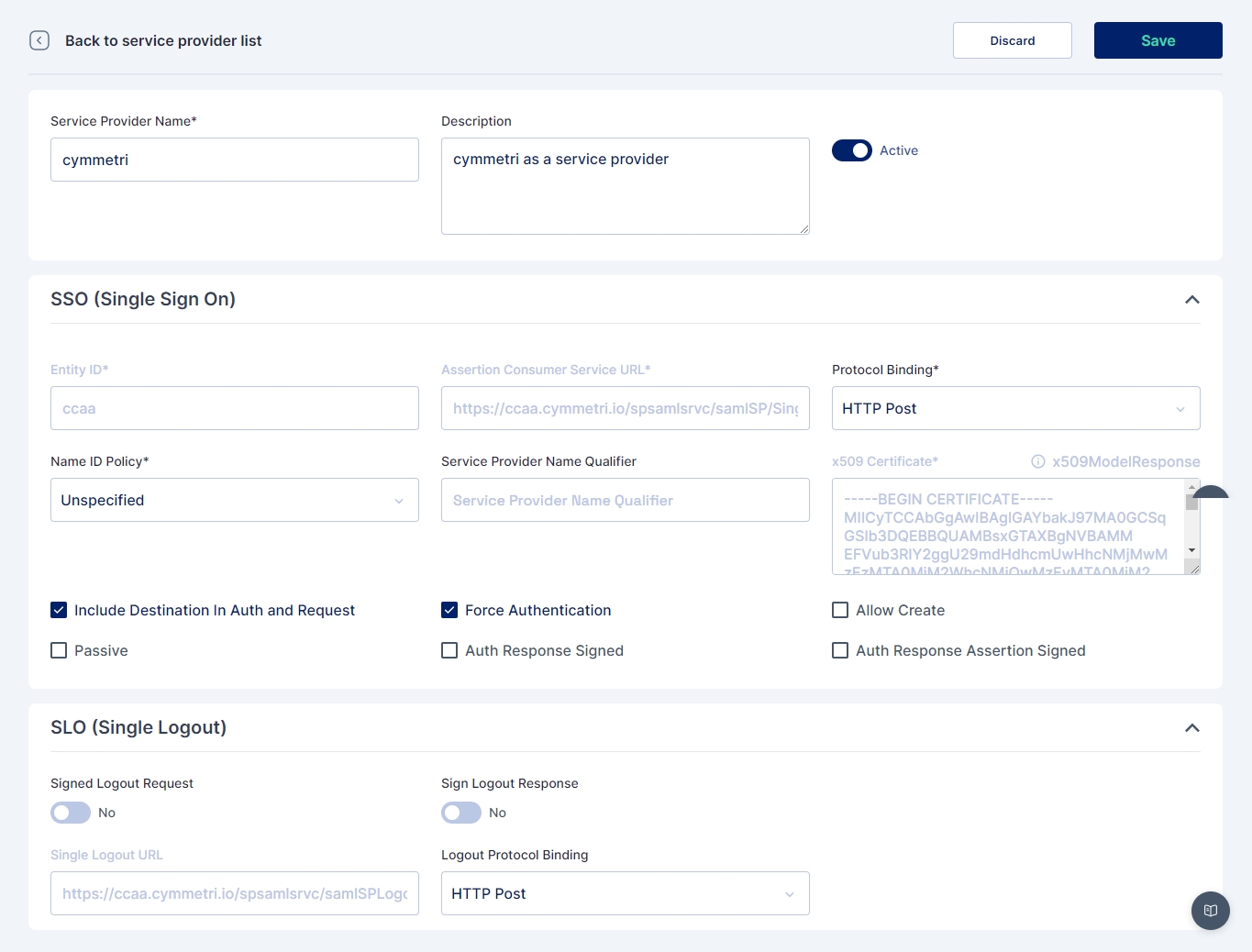
Then click on +Add New button, On the screen that appears most of the data is prefilled. Yet if the administrator needs the data can be changed as per need. Once done click on Save. The prepopulated data appears as below:
Once saved the Service Provider(Cymmetri) appears as below:
The service provider is created at this step, download the metadata(xml file) of the same.
The page shows how to configure a Service Provider.
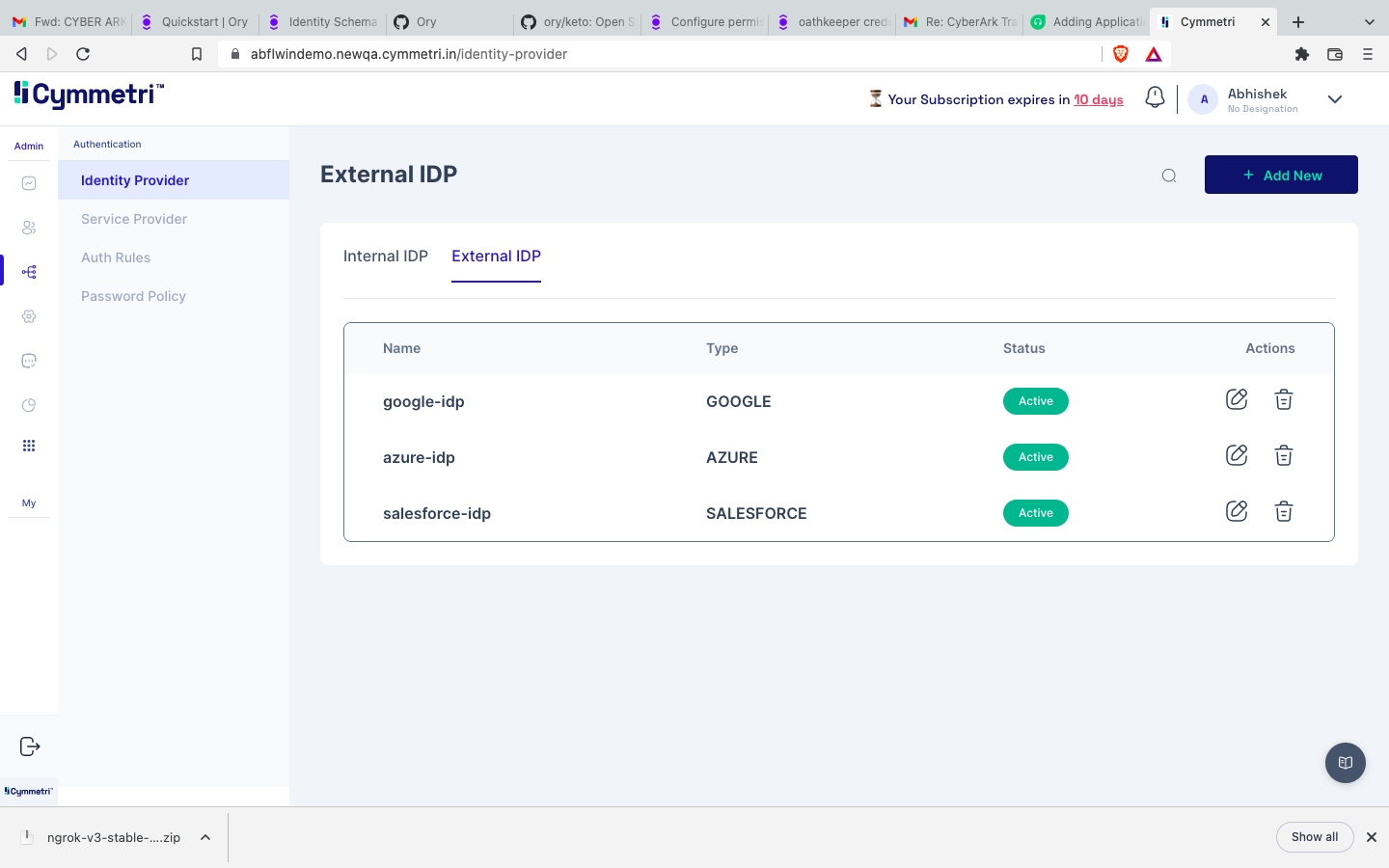
Navigate to External IDP in Identity Provider.
Select Azure-IDP.
Configure Azure AD for Creating Identity provider configuration
Now Login to the Azure portal and select Azure Active Directory.
Navigate to Enterprise applications and select New Application.
Create your own application and enter the name of the application.
Set up Single Sign On after creating the application using SAML.
Click on Edit basic SAML configuration.
Add Identifier (Entity ID) and Assertion Consumer Service URL from the XML file downloaded in step 3 (For Azure, Sign on and ACS URL are the same) and save the configuration.
Download the Certificate (Base64) from SAML Certificates.
Continue configuration of Identity Provider In Cymmetri Administration Console
Copy Azure AD Identifier from Set up, navigate to azure-idp in Cymmetri, and paste it in Entity ID. Similarly, copy the login URL and paste it into the Single Sign On Service URL in Cymmetri.
Open the Base64 certificate downloaded in step 12, copy it, and then paste it into the x509Certifcate field in Cymmetri.
Select the created service provider in the Service Provider Id field dropdown and save the changes.
Assigning users to applications in Azure Administration Console to allow users to use Azure as an External Identity provider
Navigate to Enterprise applications and select the application you created in step 8.
Go to Users and Groups, and select Add user/group and add the user.
If JIT provisioning needs to be enabled for Azure AD as external Identity provider, we may set it up using the steps below.
Navigate to JIT in external identity provider and enable JIT Configuration.
The following fields are mandatory in Cymmetri - firstName, lastName, login, userType, displayName, and email.
For Azure JIT configuration, the following mapping needs to be done -
First Name -
Application Field - http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname
Cymmetri Field - firstName
Last Name -
Application Field - http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname
Cymmetri Field - lastName
Login (Username) -
Application Field - http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name
Cymmetri Field - login
User Type -
Application Field - any string
Cymmetri Field - userType
Default Value - <will be one of Employee, Vendor, Consultant>
Display Name -
Application Field - http://schemas.microsoft.com/identity/claims/displayname
Cymmetri Field - displayName
Email Address -
Application Field - http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name
Cymmetri Field - email
Login to cymmetri using Azure Email Address
The user will be redirected to the Azure portal to enter the Azure credentials.
Once the credentials have been entered properly in the Azure portal, the user will be redirected back to Cymmetri and will be logged in successfully.
Replace the text "<host-name>" as the URL of the Cymmetri deployment (e.g., ) "aktestidp.ux.cymmetri.in" in the destination field - "https://<hostName>/spsamlsrvc/samlSP/SingleSignOnService" as "spsamlsrvc/samlSP/SingleSignOnService".
For enabling Azure IDP to be used as an IDP for a specific set of users an Authentication Rule needs to be configured. you can see the steps on how to configure Authentication Rules.
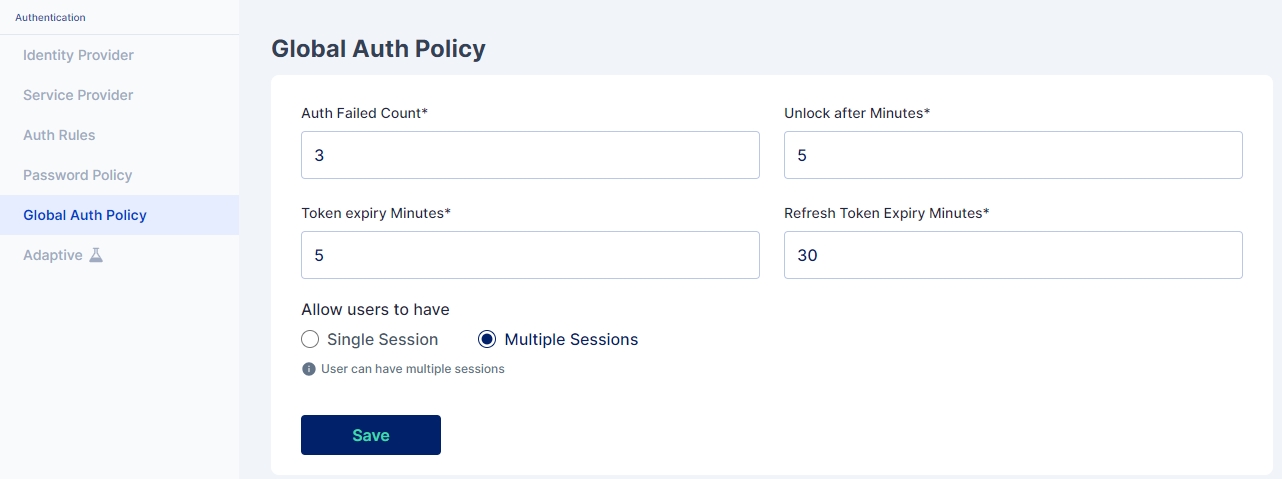
The Global Auth Policy allows to configure various user login parameters as shown below:
Auth Failed Count: The Auth Failed Count parameter signifies after how many failed login attempts will the user account be locked.
Unlock after Minutes: The Unlock after Minutes parameter signifies after how many minutes will a locked account be automatically unlocked.
Token Expiry Minutes: The Token Expiry Minutes parameter signifies after how many minutes will the session token expire.
Refresh Token Expiry Minutes: The Refresh Token Expiry Minutes parameter signifies after how many minutes will the refresh token expire.
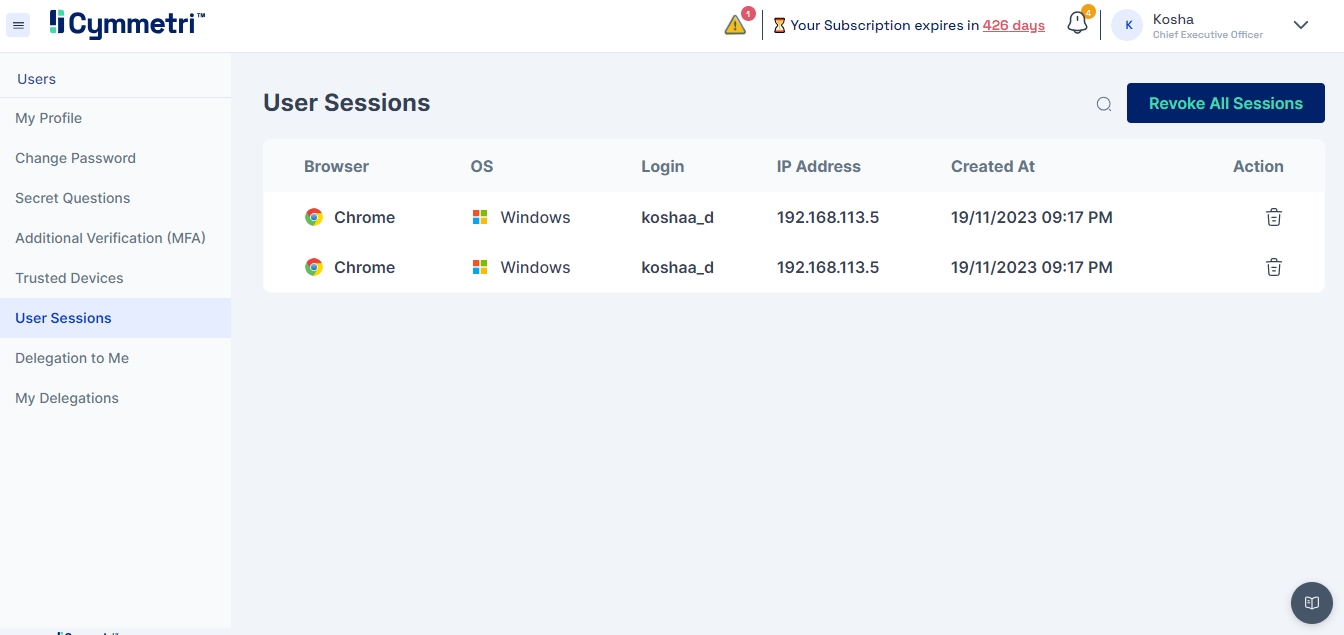
Cymmetri allows users to have multiple sessions simulatenously i.e. they can login simulatenously from various locations and keep all the sessions alive. It also provides control to the user to revoke any specific or all the sessions
Note: The link below shows steps as suggested by Salesforce to configure Salesforce as an Identity Provider: https://help.salesforce.com/s/articleView?id=sf.sso_sfdc_idp_saml_parent.htm&type=5
Here below the same steps are demonstrated to use Salesforce as an Identity Provider and Cymmetri as a Service Provider.
For configuring Salesforce to be used as an IDP the Salesforce Administrator needs to login to Salesforce as shown below:
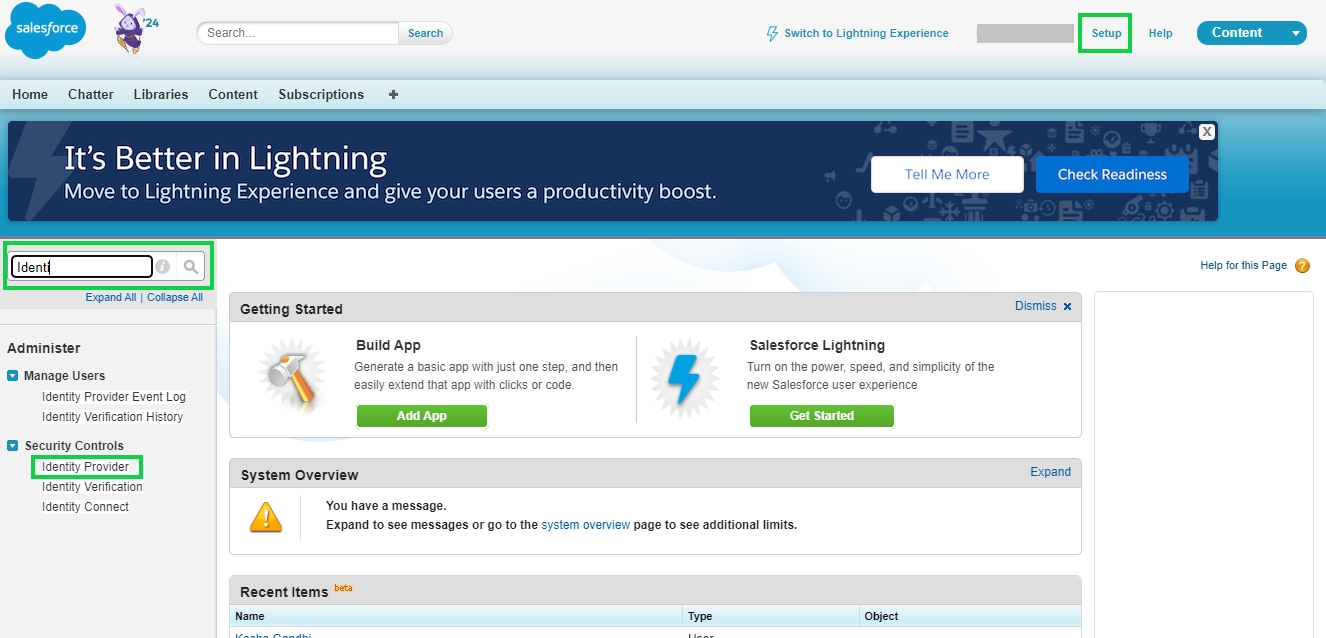
Once logged in the administrator needs to click on Setup on the top right and then in the search bar on the right side search for Identity Providers. Once found click on Security Controls -> Identity Provider menu
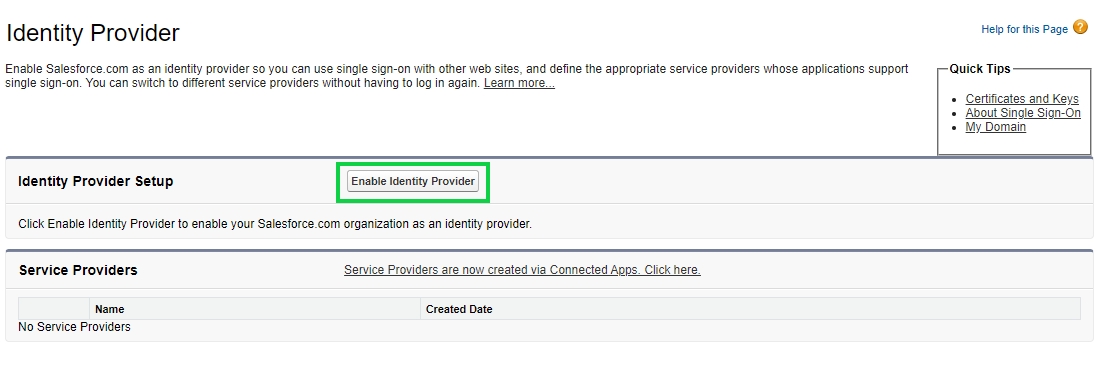
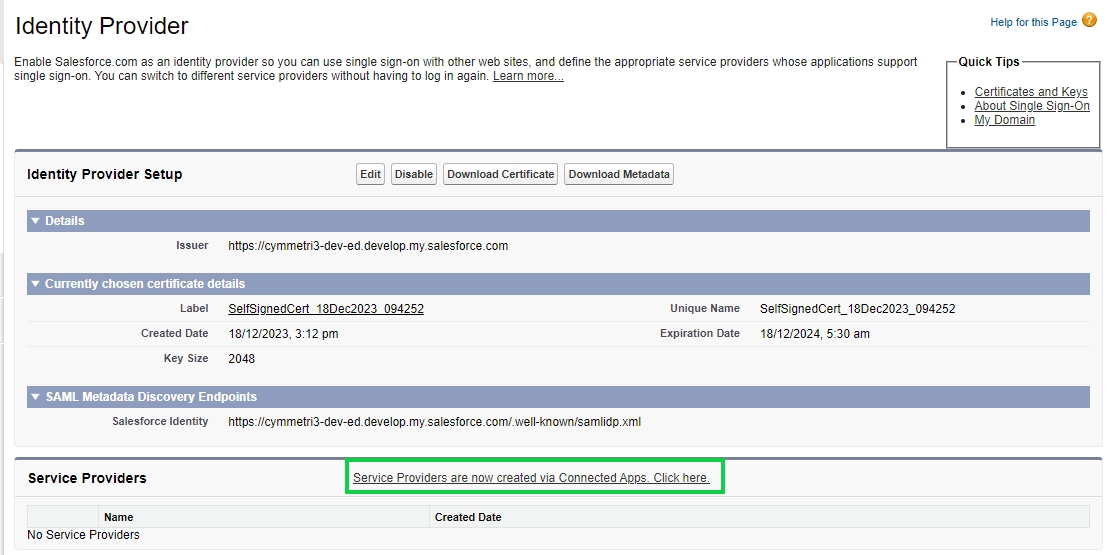
When the Identity Provider page opens click on the Enable Identity Provider button to enable Salesforce as an Identity Provider so that it can be used for authentication in Cymmetri.
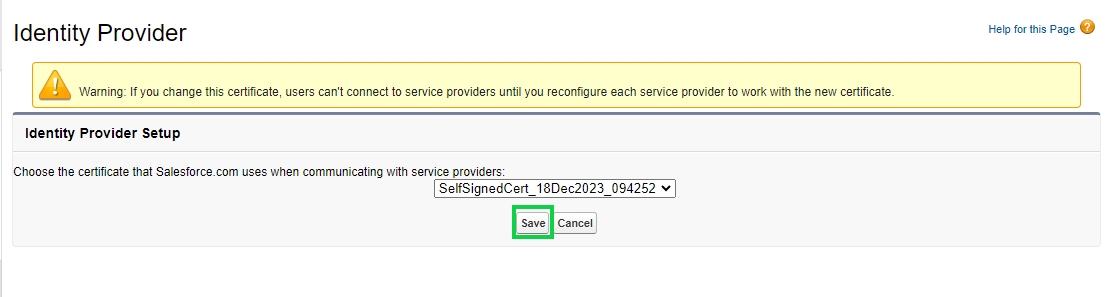
When the Enable Identity Provider button is clicked it opens a page that asks you to choose a certificate. Select the default certificate here and click Save.
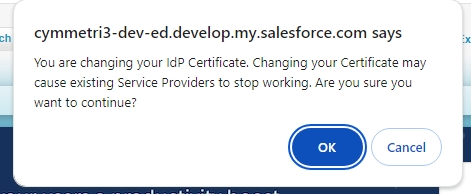
When saved it shows a warning message as below just click the OK button and continue.
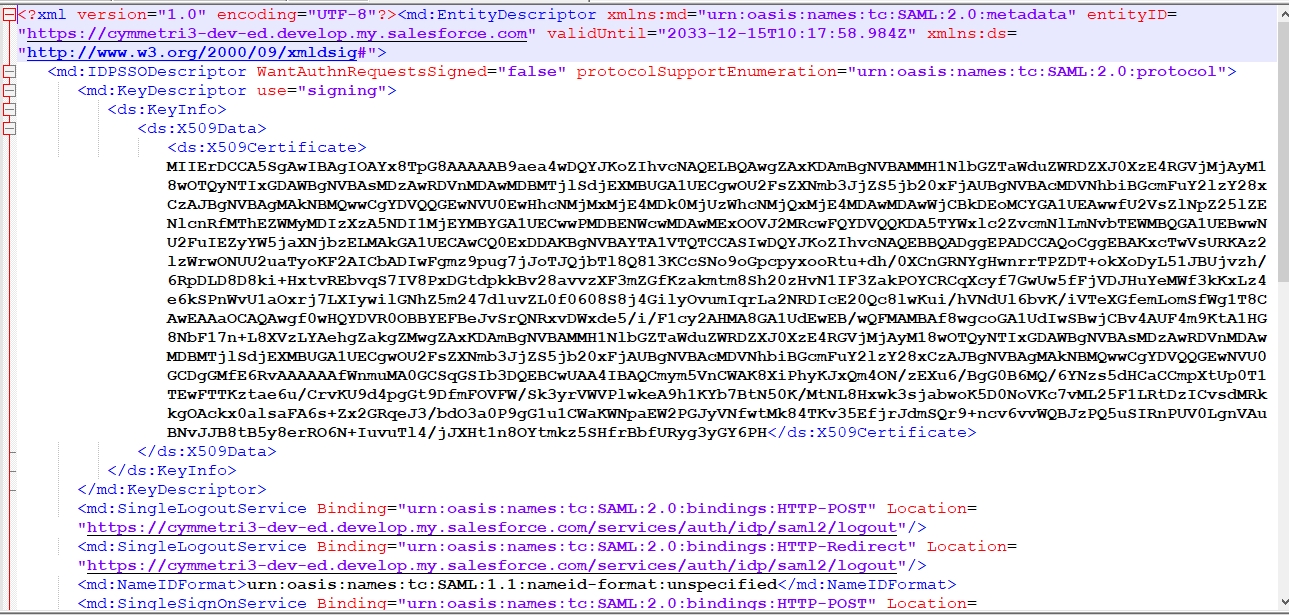
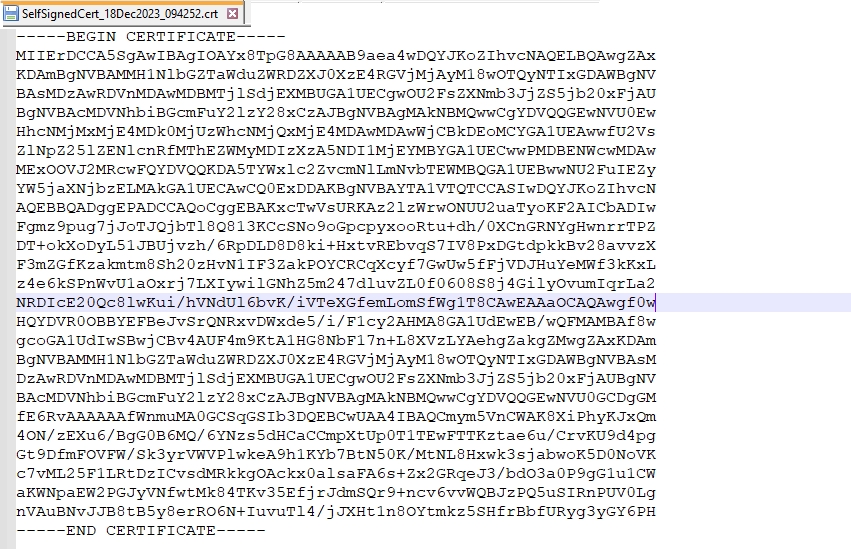
Once confirmed the screen as shown below appears you may download the certificate and the metadata file here using the Download Certificate and Download Metadata buttons. These files can be downloaded later during the end of the process which can be seen later in the documentation below.
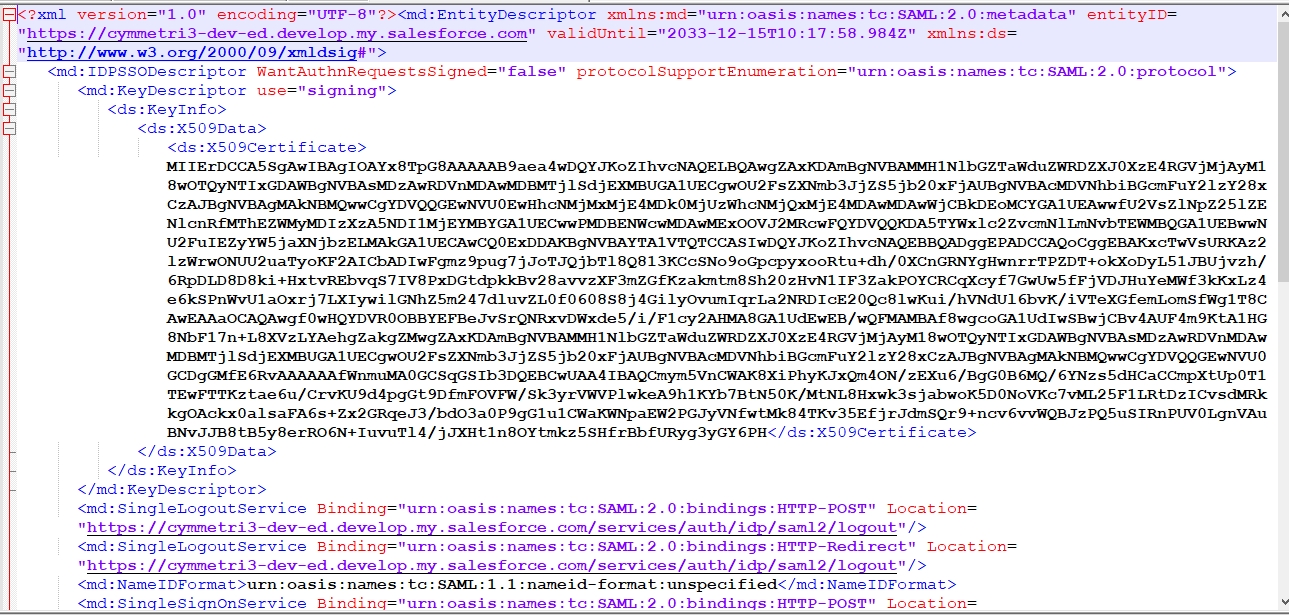
The metadata file appears as below, this data is used later to configure the External IDP in Cymmetri.
The certificate file appears as below this is also needed when configuring the External IDP in Cymmetri.
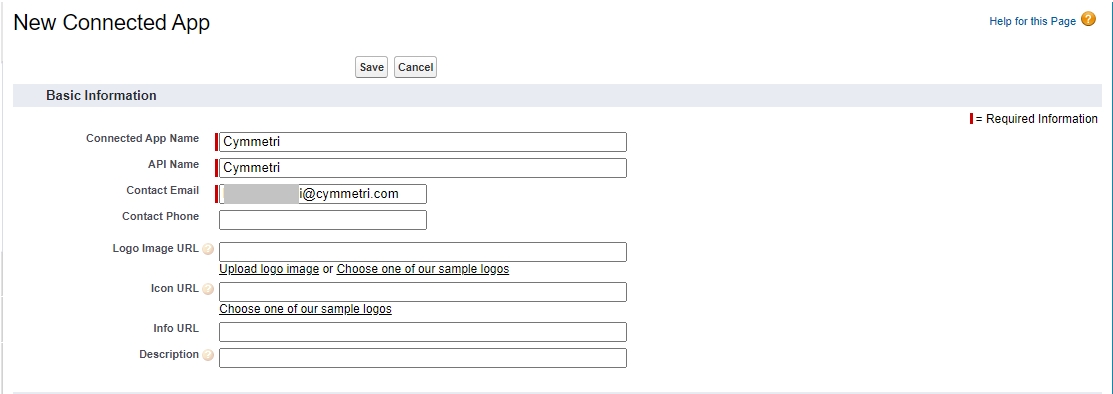
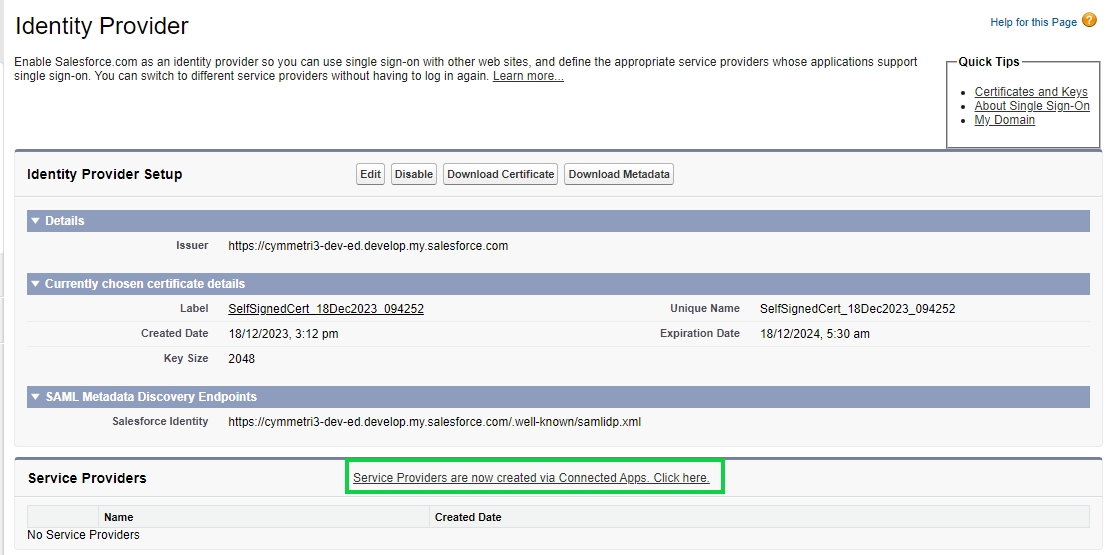
Once the files are downloaded next to add the Service Provider the salesforce administrator needs to click on Service Providers are now created via Connected Apps. Click here link. The mentioned link allows to create a Connected App for Cymmetri which acts as a service provider in Salesforce.
The link above leads to the page below where a new connected app can be added. The following details need to be mentioned to add a connected app:
Connected App Name: App Name (Cymmetri in this case)
API Name: Auto-populated based on the Connected App Name field, can be changed
Contact Email: a valid contact email
Note: Other fields shown in the image below are optional and hence can be skipped.
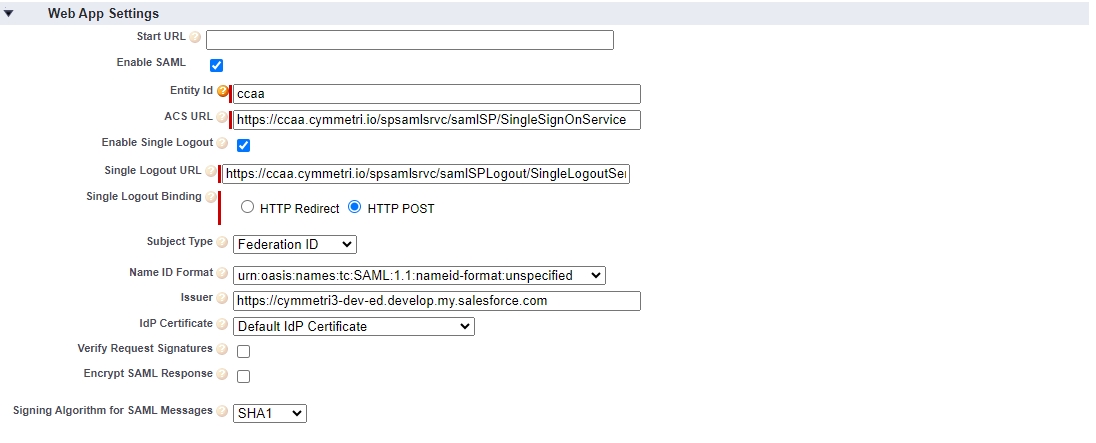
Next on the same page, there is a section called Web App Settings here click on Enable SAML to enable the SAML settings. Once enabled all the below-mentioned details need to be provided.
Entity Id: A unique identifier for a SAML entity, such as a Service Provider (SP) or Identity Provider (IDP), within a federated authentication environment.
ACS URL (Assertion Consumer Service URL): The endpoint where a service provider expects to receive SAML assertions from an identity provider, facilitating single sign-on (SSO) in a federated system.
Enable Single Logout: A configuration option indicating whether the system supports single logout functionality, allowing users to log out of all connected services in a federated environment with one action.
Single Logout URL: The endpoint to which a SAML entity sends logout requests as part of the single logout process when a user logs out of the federated system.
Single Logout Binding: The protocol or method used to transmit single logout requests and responses between SAML entities, often specified as either HTTP Redirect or HTTP POST.
Subject Type: Specifies the type of subject identifier used in SAML assertions, such as transient, persistent, or bearer, indicating how the identity of the user is communicated between the identity provider and the service provider.
Name ID Format: Defines the format of the NameID element in SAML assertions, determining how the user's identity is represented, such as email address, X.509 certificate, or unspecified.
Issuer: Identifies the entity that issues a SAML assertion, typically the identity provider, and is included in the SAML assertion to establish trust between the entities in a federated system.
IDP Certificate: The public key certificate associated with the identity provider, used by the service provider to verify the authenticity and integrity of SAML assertions and messages.
Signing Algorithm for SAML Messages: Specifies the cryptographic algorithm used to sign SAML messages, ensuring the integrity and authenticity of the information exchanged between identity providers and service providers in a federated
The above-mentioned details can be obtained by adding a service provider in Cymmetri as shown below. To know more about how to add a service provider in Cymmetri click here. Once created these details can be used in Salesforce as shown above.
Once all details are successfully added and saved the screen below appears which shows the configuration details.
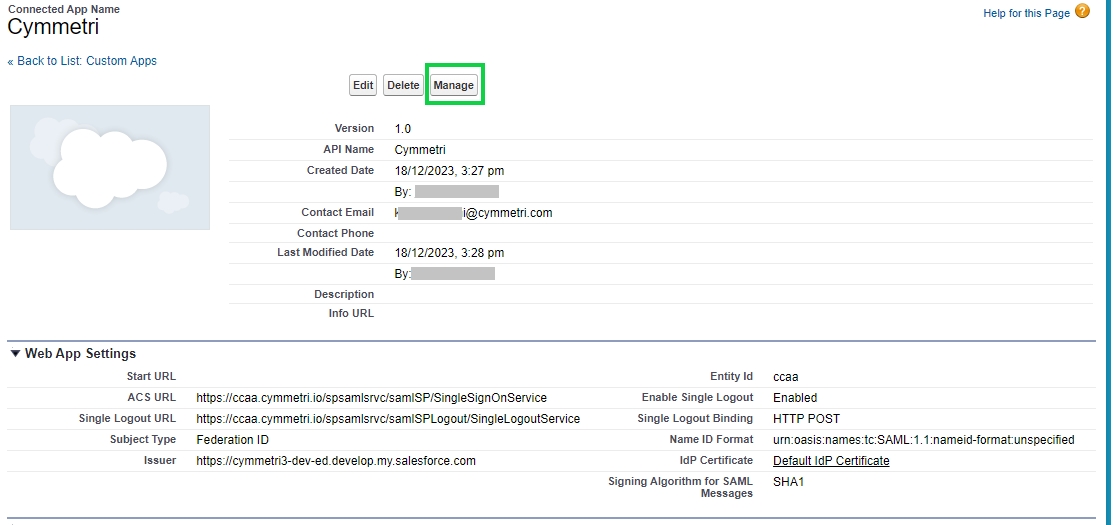
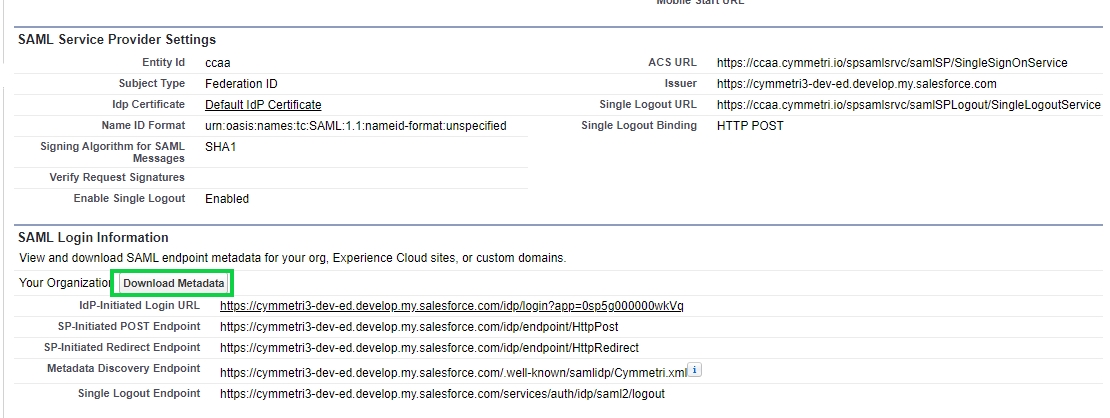
Administrators can click on the Manage button (as shown above) to view SAML Service Provider Settings and SAML Login Information. Administrators can also download metadata files here.
The downloaded metadata file appears as below. The details mentioned in the metadata file are used to configure an External IDP in Cymmetri.
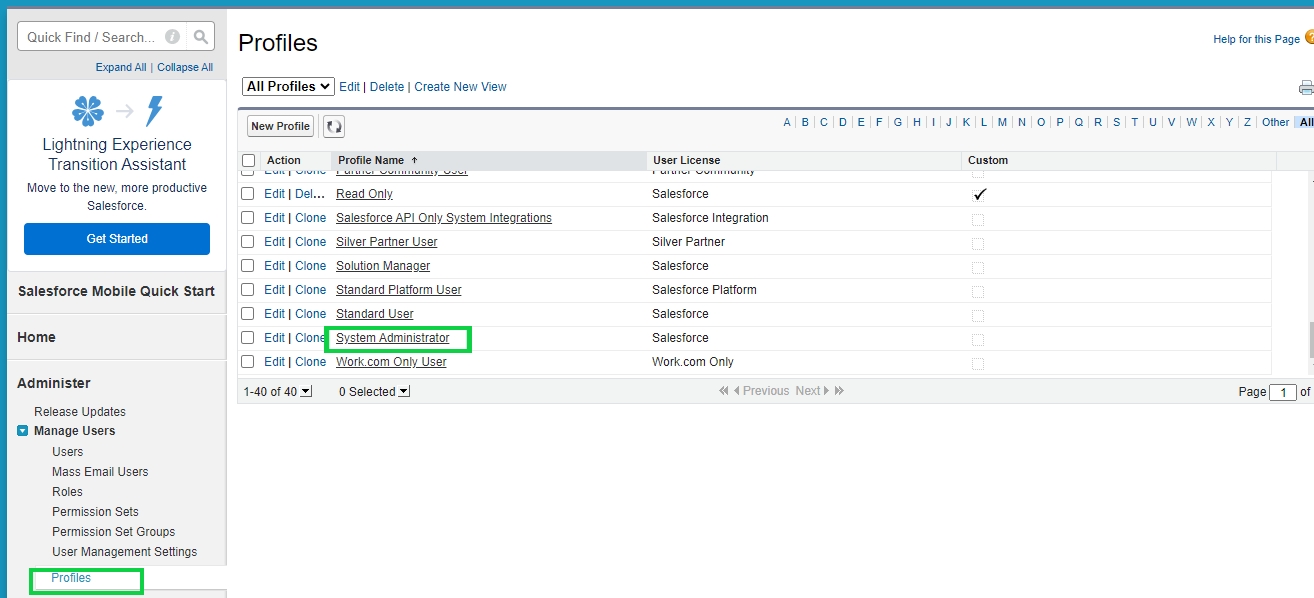
Based on the diverse profiles of users in Salesforce, the administrator needs to enable Connected App Access for these profiles. Here in this example access has been enabled for the System Administrator; similarly, it should be enabled for all profiles of various users who are intended to access Cymmetri.
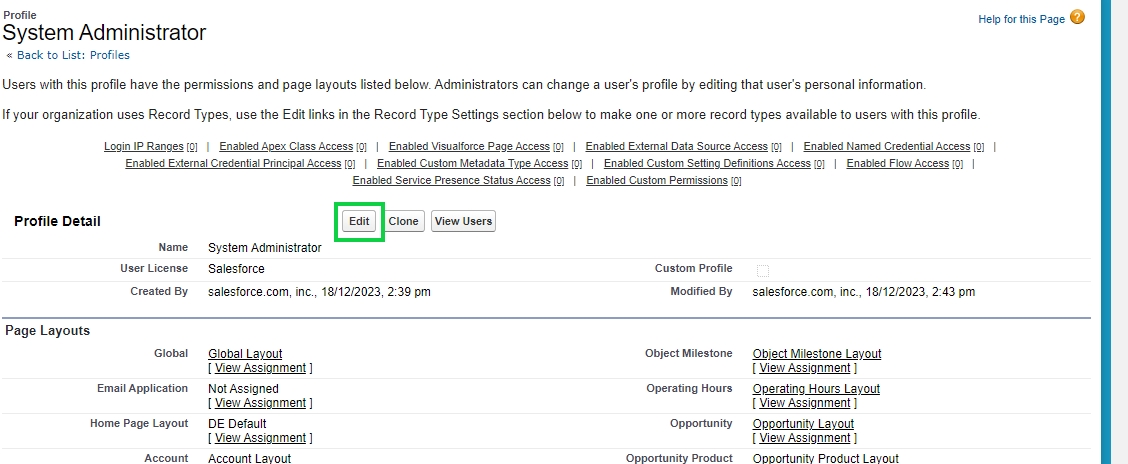
For enabling the connected app administrator needs to go to Setup->Manage Users-> Profiles, then select the profile for which the connected app needs to be enabled
Once the profile is selected click on the Edit button and look for the Connected App Access section.
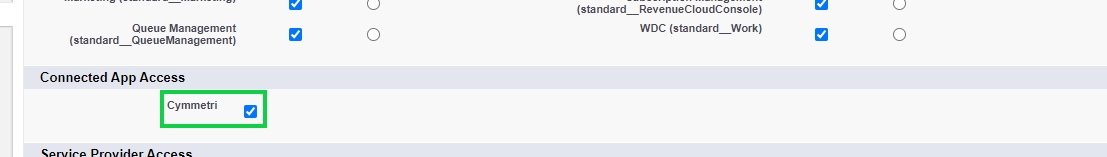
In the Connected App Access section look for the custom app you created(Cymmetri in this case) and click the checkbox to enable the access.
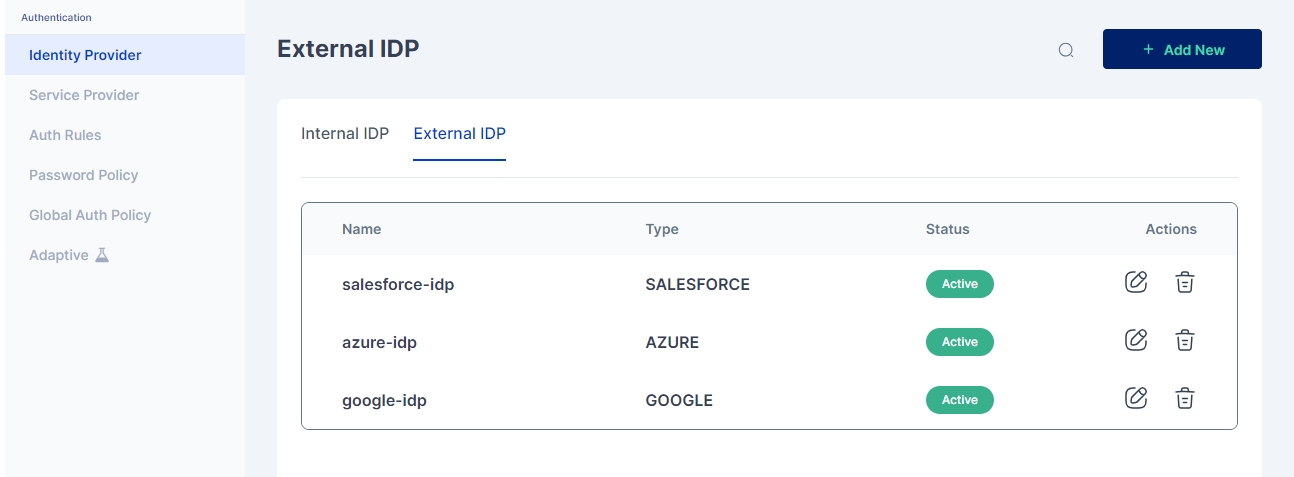
Once all the configurations on the Salesforce end are done, the administrator must proceed with the configuration on the Cymmetri side. To achieve this, the administrator needs to go to Authentication->Identity Provider->External IDP. Here you may either configure the already created salesforce-idp instance or +Add New
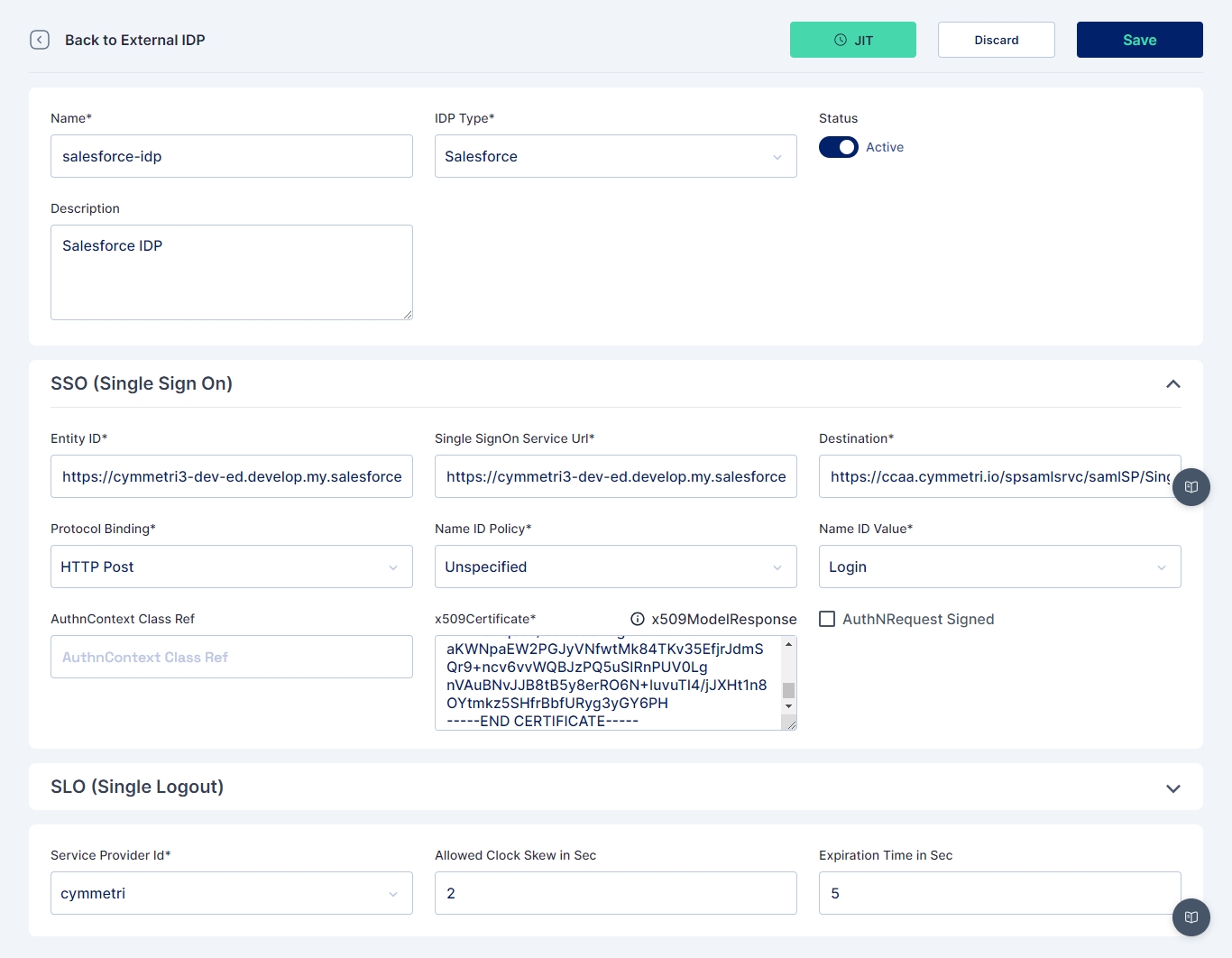
In either case, a screen opens where you need to provide the below-mentioned details
Name: salesforce-idp
IDP Type: Salesforce
Entity ID: Need to mention the EntityID from the metadata file downloaded from Salesforce
SSO Service URL: Need to mention the SingleSignonService URL from the metadata file downloaded from Salesforce
Destination: https://<hostname>/spsamlsrvc/samlSP/SingleSignOn
Protocol Binding: HTTP Post (can also be set to HTTP Redirect if it is set so in Salesforce)
Name ID Policy:
Policy: Unspecified(This may change based on what is configured in Salesforce)
Value: Login(This may change based on what is configured in Salesforce)
Certificate: Certificate downloaded from Salesforce
Logout Request URL: Need to mention the SingleLogoutService URL from the metadata file downloaded from Salesforce
Logout Protocol Binding: HTTP Post (can also be set to HTTP Redirect if it is set so in Salesforce)
Service Provider Id: cymmetri (Need to the select the configured Service Provider as shown above)
Once the external IDP is configured next we need to configure Authentication Rules as explained here and as shown below. Conditions mentioned here may vary based on actual scenario in which the IDP needs to be applicable.
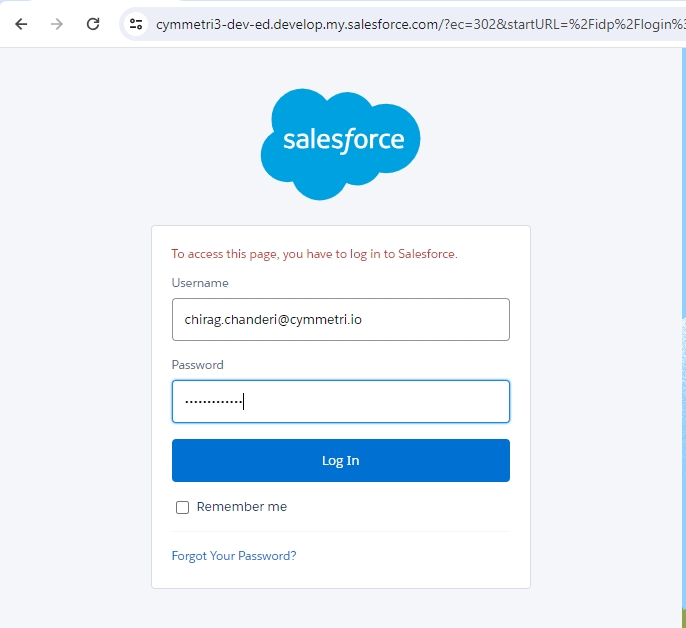
Now the user can login into Cymmetri using Salesforce. The user needs to provide his/her username and click on Next.
The user is then redirected to Salesforce login page where the user needs to enter their Salesforce credentials and click on Log in
Once the salesforce credentials are successfully validated the user is redirected to Cymmetri home page.
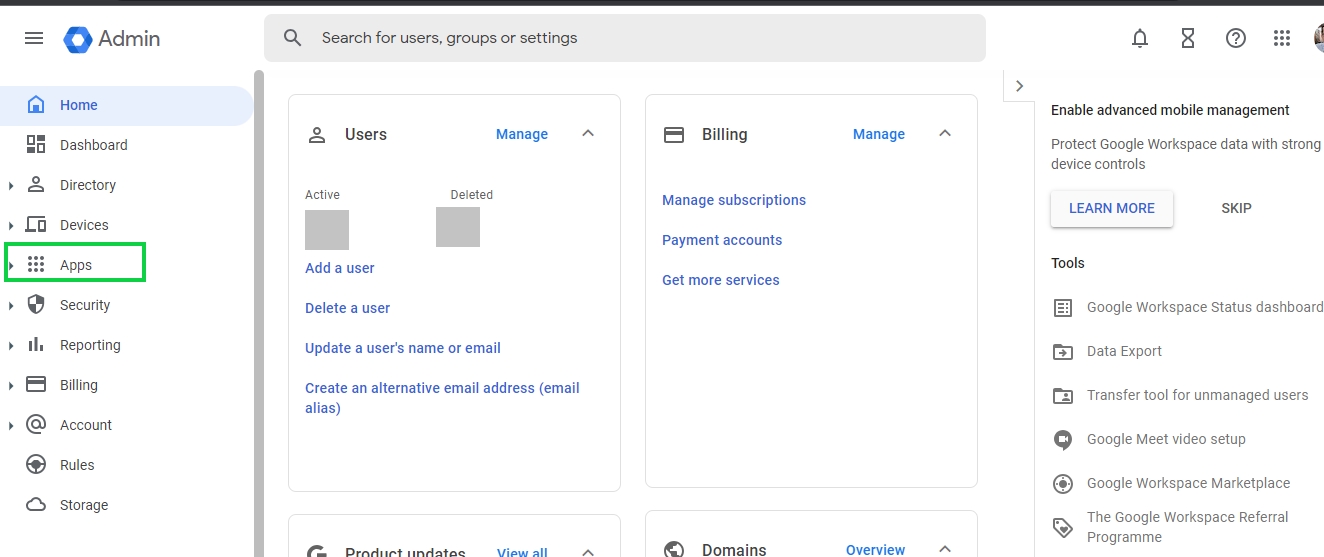
Log in to your Google admin account and go to the Admin Section as shown below:
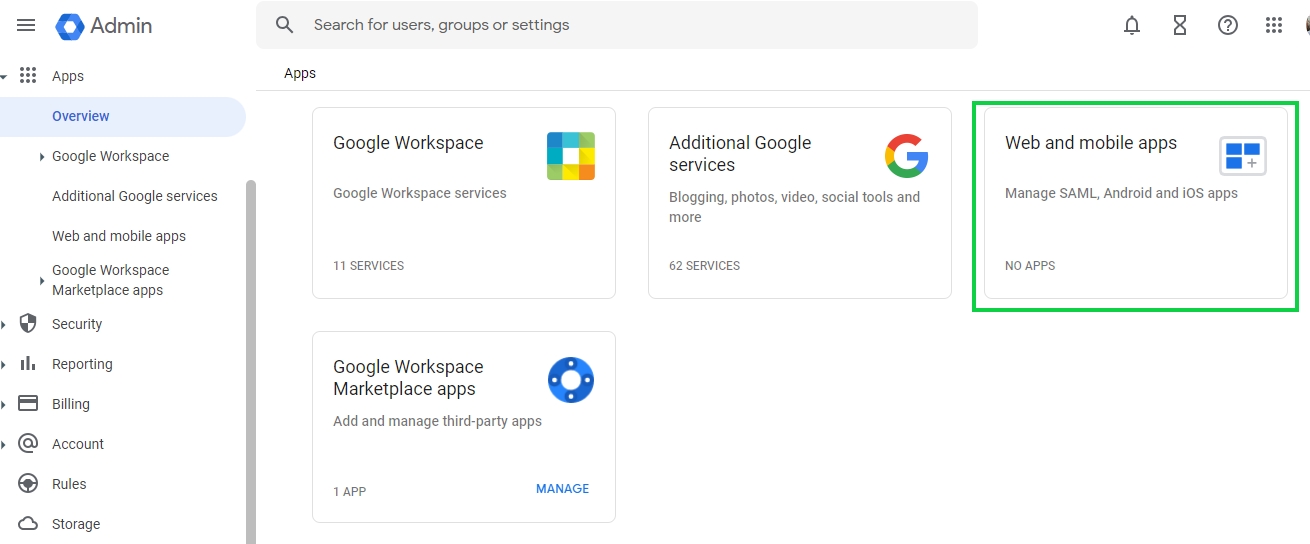
Once in the admin section click on Apps > Overview
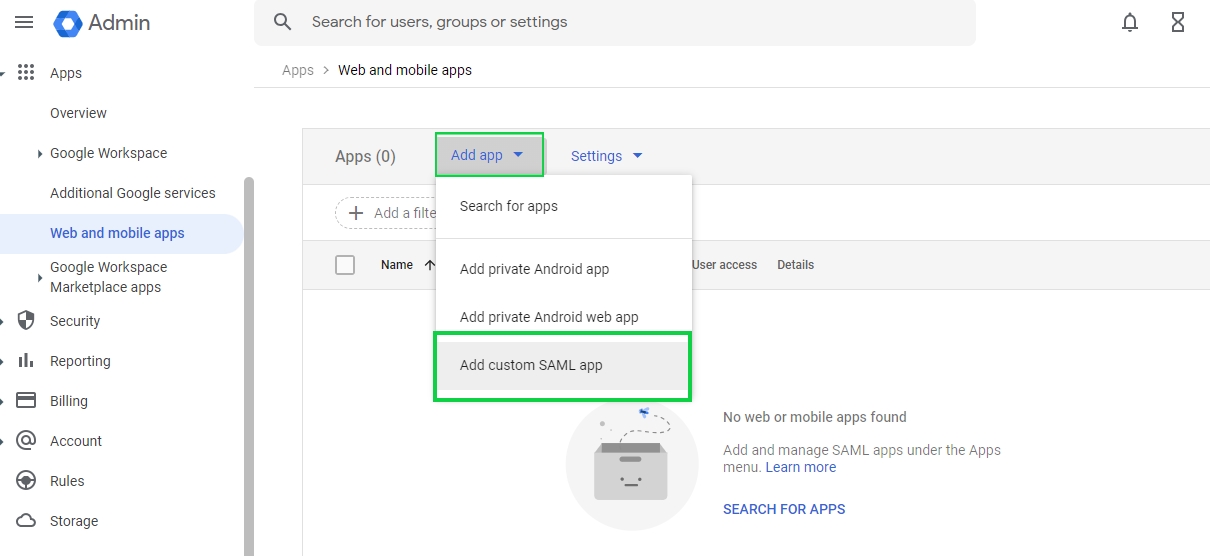
In the overview page click on the Web and mobile apps tile to add a new custom app
On the Web and mobile apps page click on the Add app dropdown and then select Add custom SAML app to add the Cymmetri tenant as a custom app
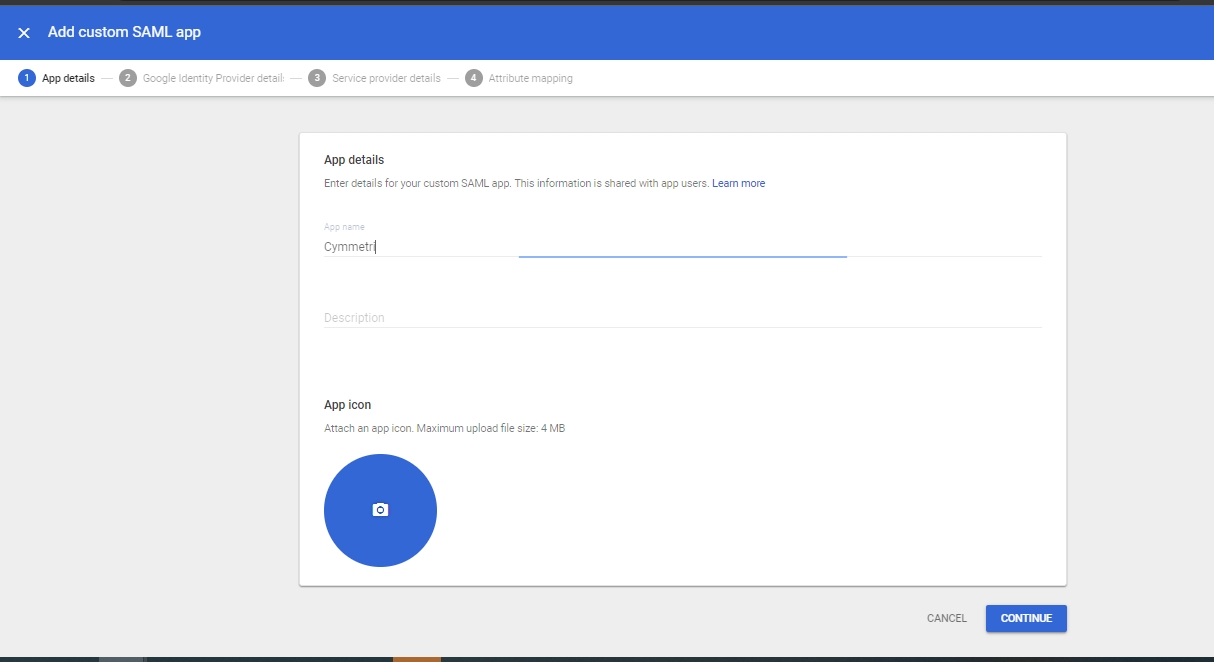
Provide a relevant App Name, Optionally a description for the application can be provided. An App Icon can also be attached if required. Once entered click on the Continue button
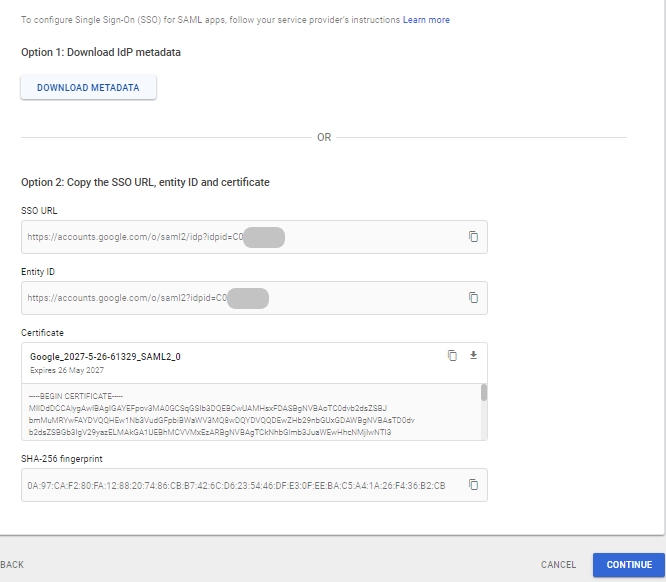
On the Google Identity Provider Detail page download the metadata file by clicking on the DOWNLOAD METADATA button. This metadata file needs to be used to get Entity ID, SSO URL, and Certificate. Administrators can download the certificate here or later as shown here. Once downloaded click on Continue.
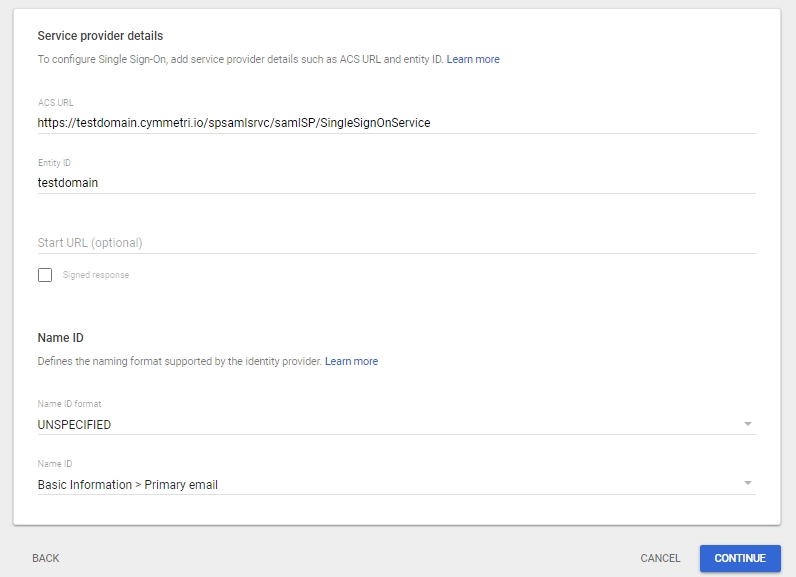
Once the IDP metadata and certificate are obtained the Service Provider(i.e. Cymmetri) details need to be provided. We need to provide the ACS URL and the Entity ID these details can be obtained from Cymmetri as shown here. No change needs to be done for the Name ID format and Name ID, it can be kept to UNSPECIFIED and Basic Information > Primary email. Once done click on Continue
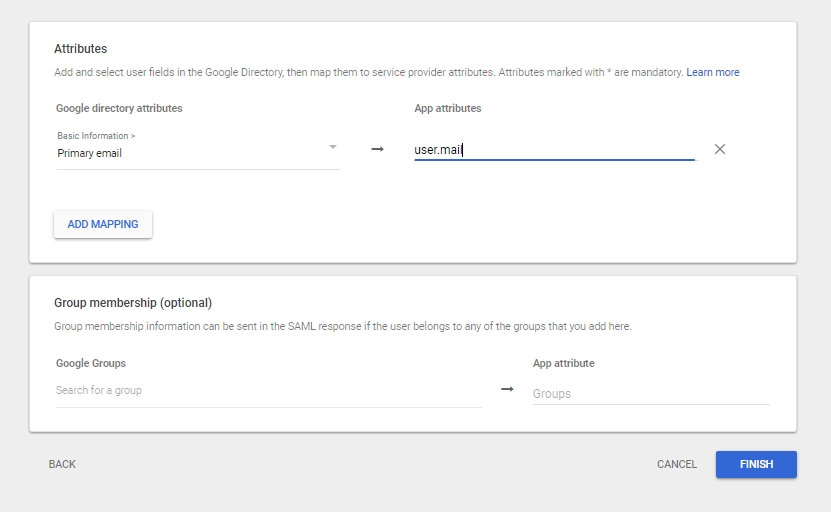
Attributes can be added on this screen which could then be sent as a SAML response to Cymmetri. These values can be used to create a user in Cymmetri if JIT provisioning is enabled on Cymmetri's side
Group membership information can also be sent by configuring groups here and if the user belongs to the configured group. Once attributes and groups are configured click on FINISH.
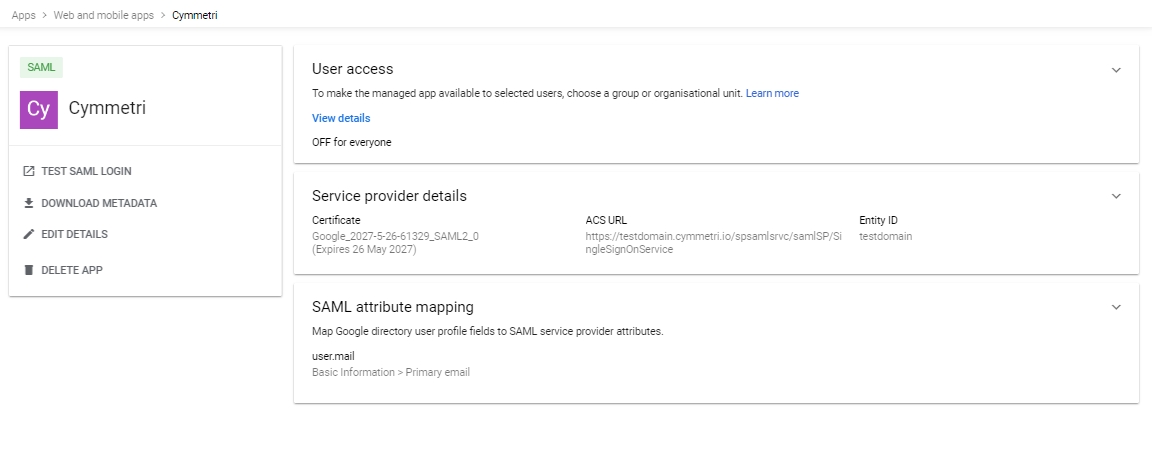
Once you click on the FINISH button the below screen appears that shows the configuration details. It also shows various shortcuts to Test SAML Login, Download Metadata, Edit Details, and Delete the App
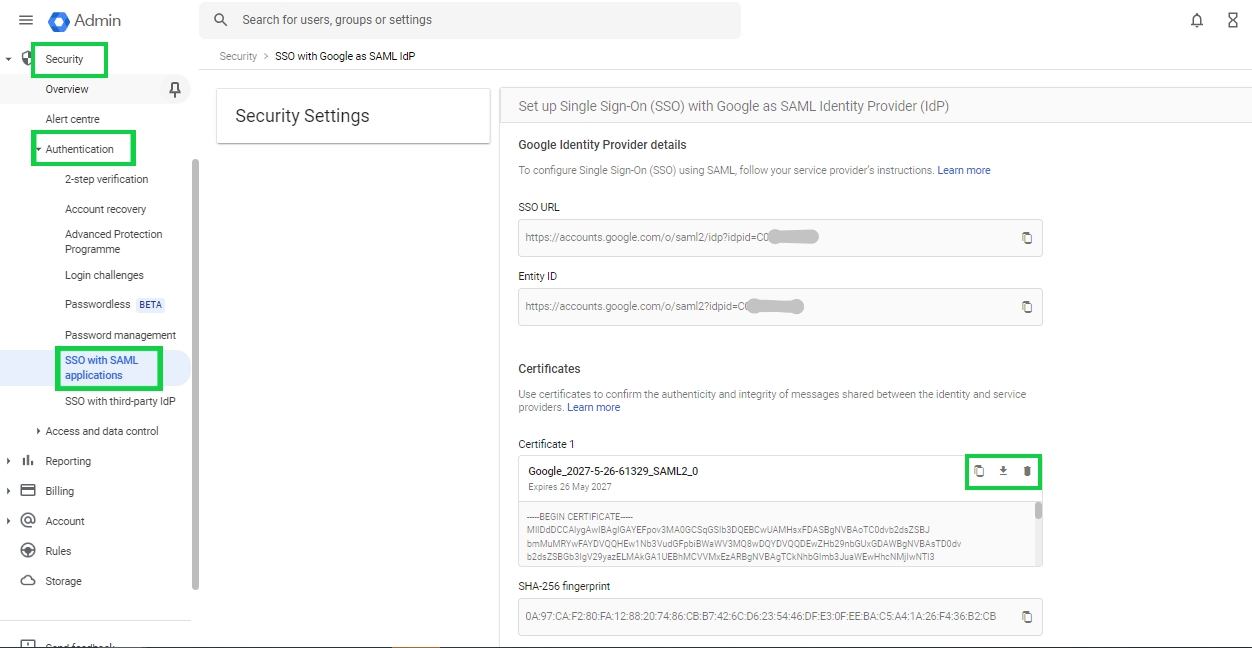
If the administrator does not download the certificate while configuring the custom application, it can be later downloaded. For the same the administrator needs to go to Security>Authentication>SSO with SAML applications. This will open the Security Settings page from where either the IDP details like SSO URL and Entity ID can be copied and the IDP Certificate can be downloaded. These details can be used to configure the IDP in Cymmetri.
Once Google IDP is configured, the administrator must proceed with the configuration on the Cymmetri side. To achieve this, the administrator needs to set up Cymmetri as a Service Provider and also incorporate Google as an external IDP.
The page here shows how to configure a Service Provider.
Once the Service Provider is configured, we need to configure Google as an external IDP.
Administrator needs to go to Authentication->Identity Provider->External IDP. Here you may either configure the already created google-idp instance or +Add New
In either cases a screen opens where you need to provide the below mentioned details
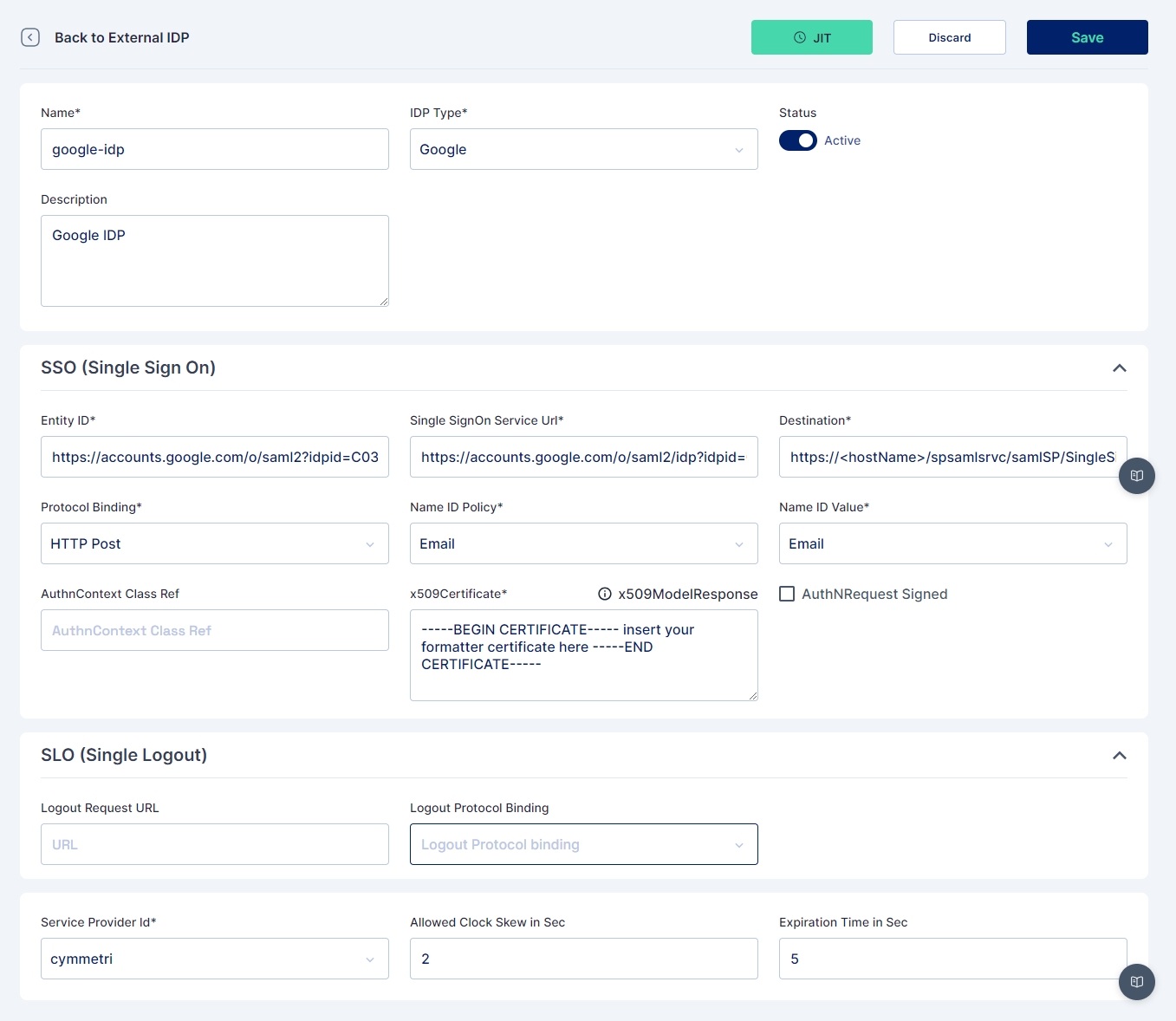
Name: Google IdP
IDP Type: Google
Entity ID: https://accounts.google.com/o/saml2?idpid=xxxxxxxxxxxx
SSO Service URL: https://accounts.google.com/o/saml2/idp?idpid=xxxxxxxxxxxx
Destination: https://<hostname>/spsamlsrvc/samlSP/SingleSignOn
Protocol Binding: HTTP Post (can also be set to HTTP Redirect if it is set so in Google IDP)
Name ID Policy:
Policy: Email (This may change based on what is configured in Google IDP)
Value: Email (This may change based on what is configured in Google IDP)
Certificate: Certificate downloaded from Google IDP
Logout Request URL: Need to mention the SingleLogoutService url from the metadata file if SLO (Single Logout) is configured in Google.
Logout Protocol Binding:HTTP Post (can also be set to HTTP Redirect if it is set so in Google IDP)
Service Provider Id: cymmetri (Need to the select the configured Service Provider as shown above)
Once all the details are entered Save the changes.
For enabling Google IDP to be used as an IDP for specific set of users an Authentication Rule needs to be configured. Here you can see the steps on how to configure Authentication Rules.
Once the rule is configured whenever a user matches with the rule conditions the user is redirected to Google screen and the user needs to provide his/her Google credentials to be able to login into Cymmetri.
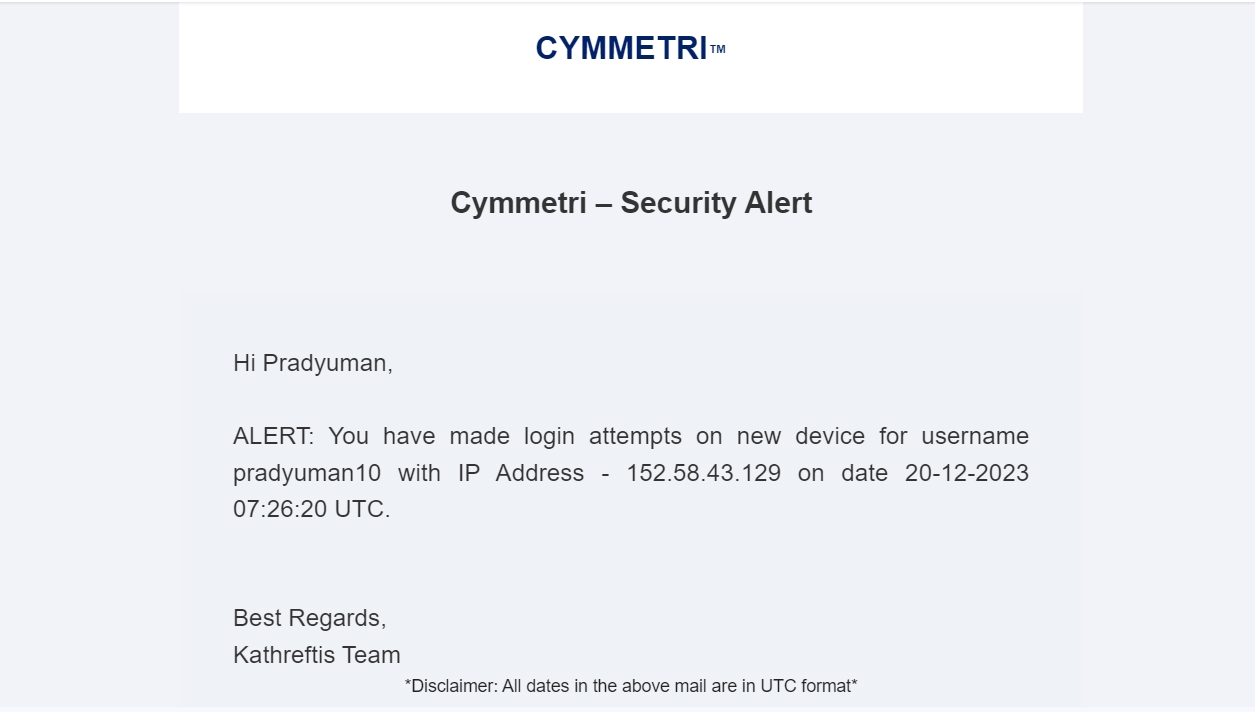
Adaptive authentication is an advanced security measure that assesses various factors and context elements in real-time to determine the level of risk associated with a user's access attempt.
Based on this risk assessment, the authentication system can dynamically adapt its level of scrutiny and request additional verification steps if needed. This approach enhances security while minimizing disruption for legitimate users.
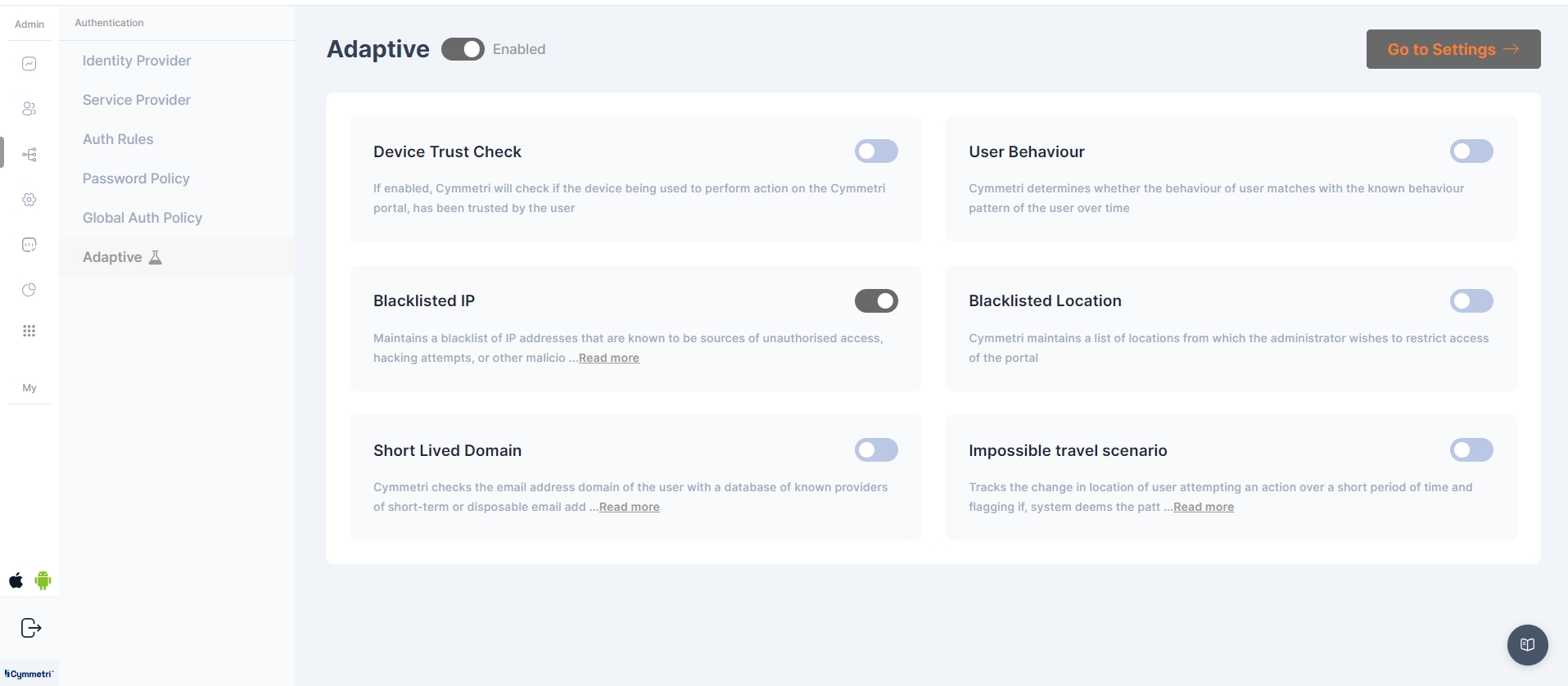
In Cymmetri there are various adaptive checks that the admin can enable for additional factor of authentication.
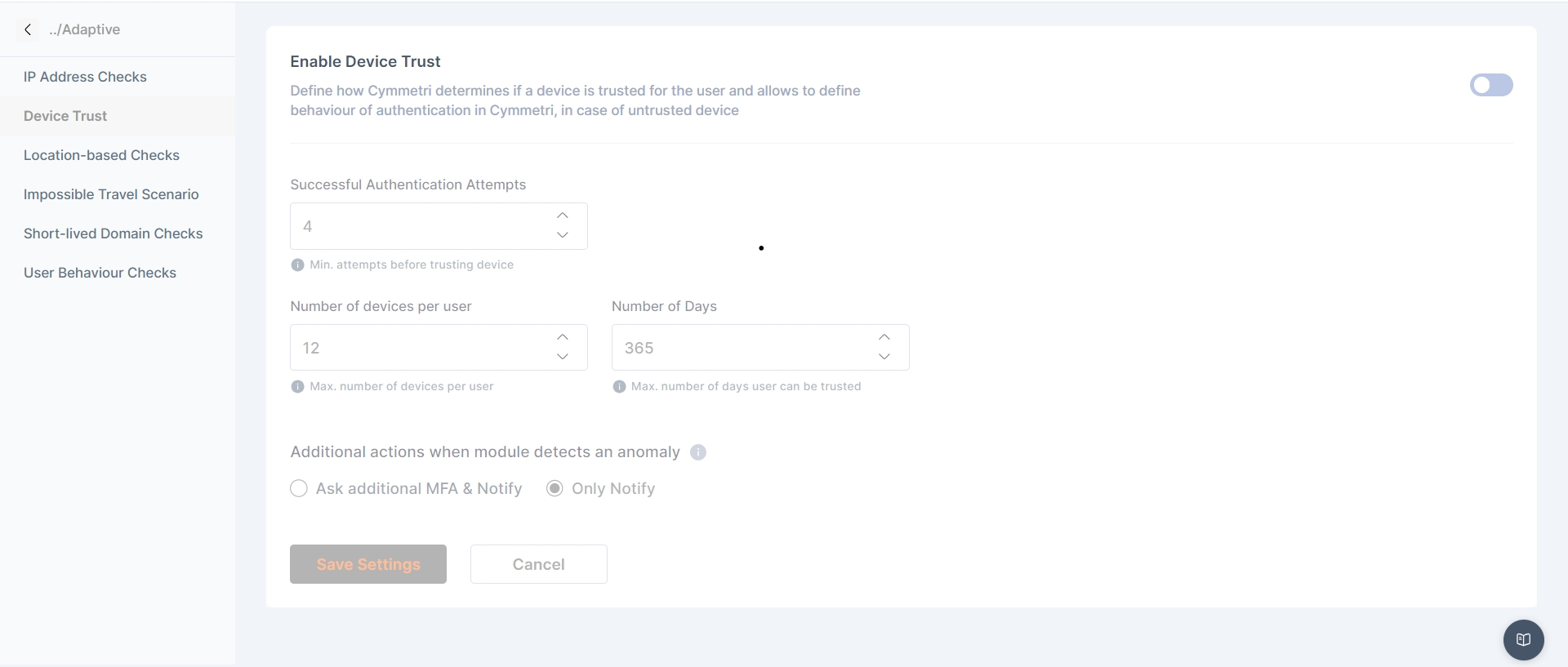
Device Trust Check - If enabled, Cymmetri will check if the device being used to perform action on the Cymmetri portal, has been trusted by the user
User Behavior - Cymmetri determines whether the behavior of user matches with the known behavior pattern of the user over time
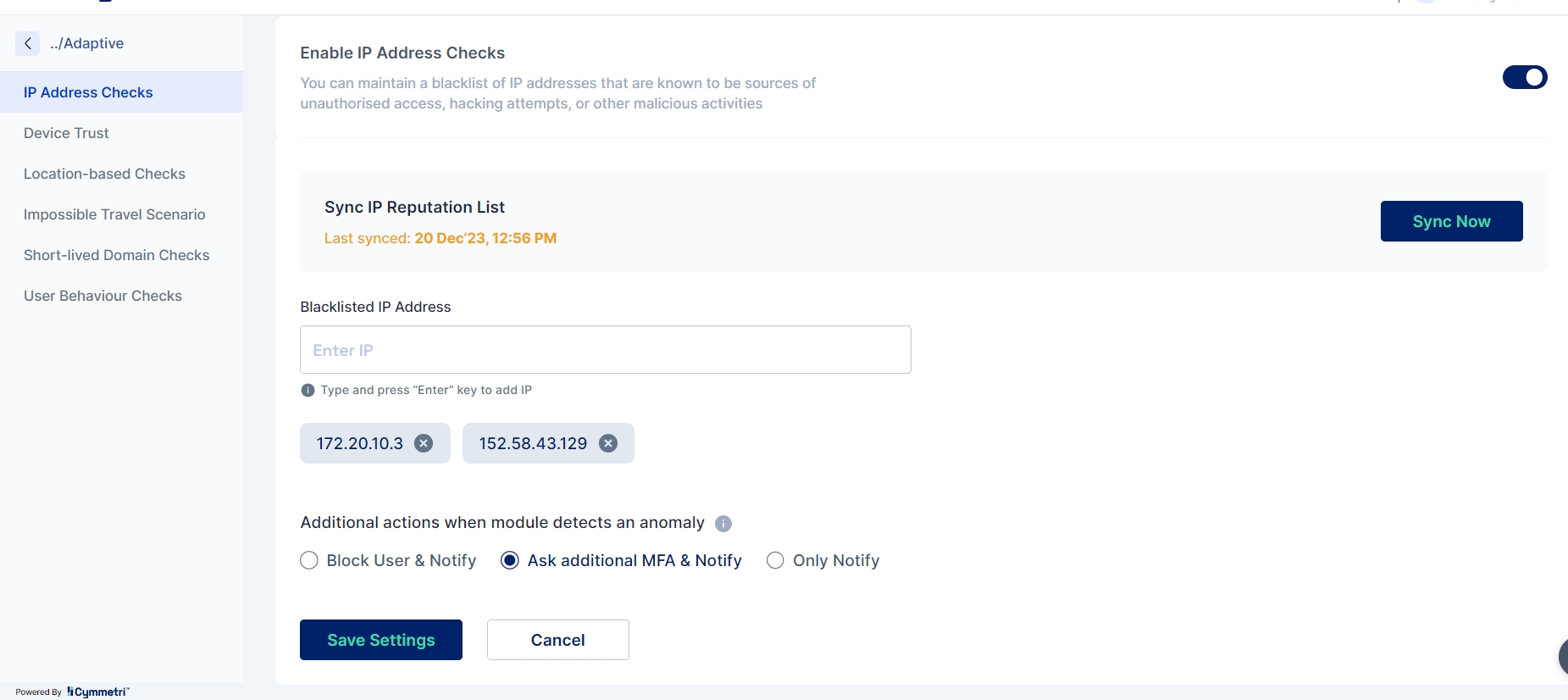
Blacklisted IP - Maintains a blacklist of IP addresses that are known to be sources of unauthorized access, hacking attempts, or other malicious activities
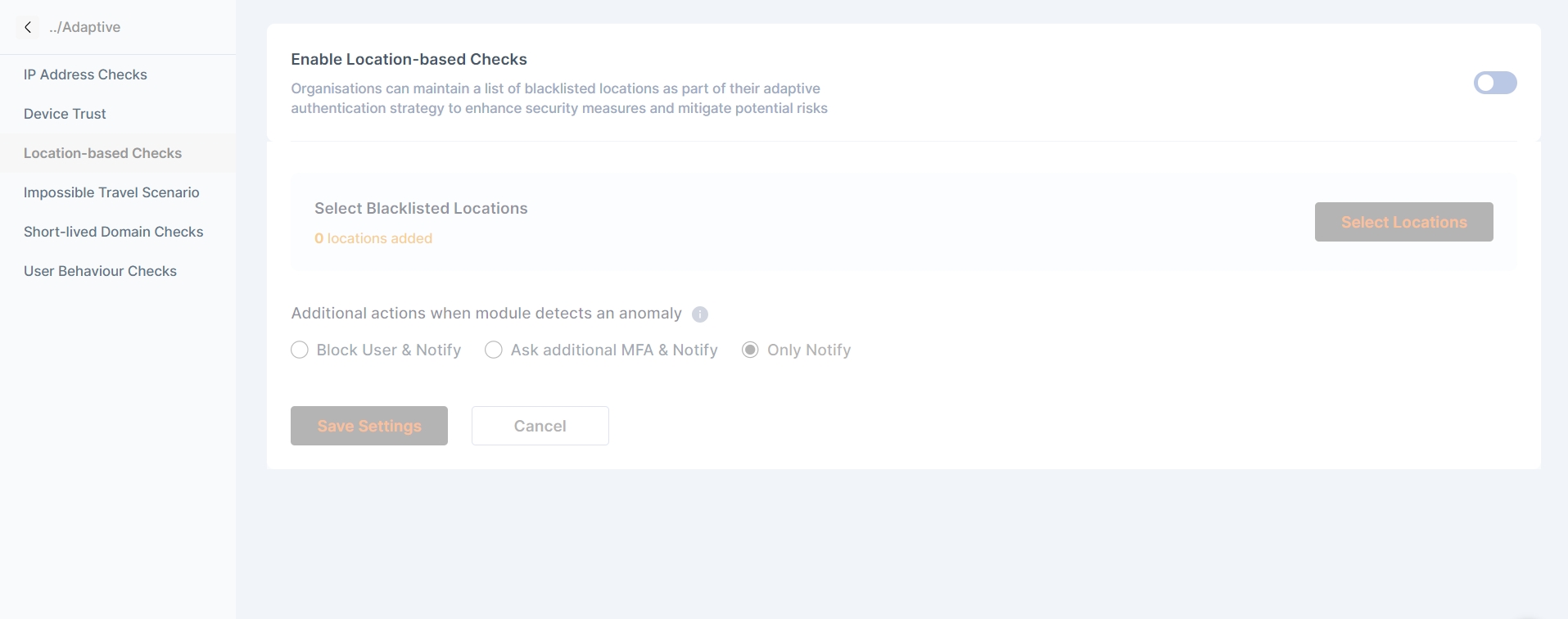
Blacklisted Location - Cymmetri maintains a list of locations from which the administrator wishes to restrict access of the portal
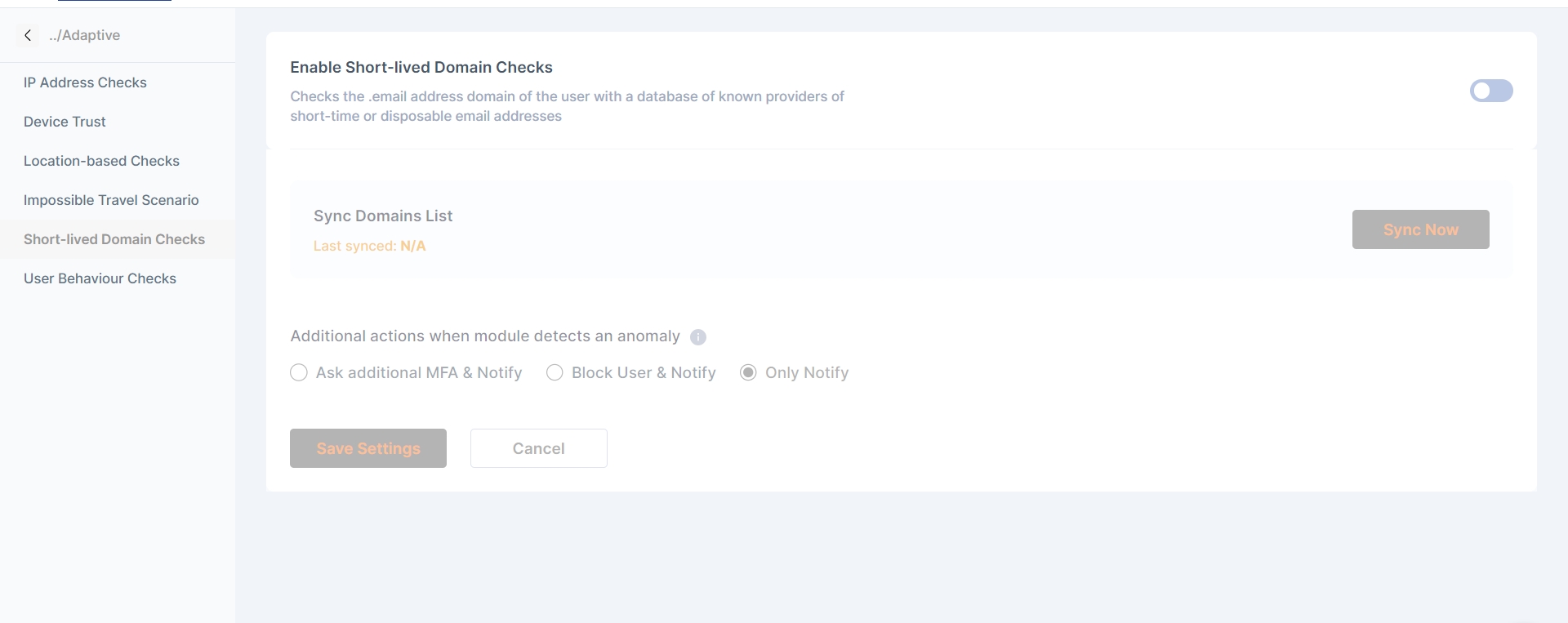
Short Lived Domain - Cymmetri checks the email address domain of the user with a database of known providers of short-term or disposable email addresses
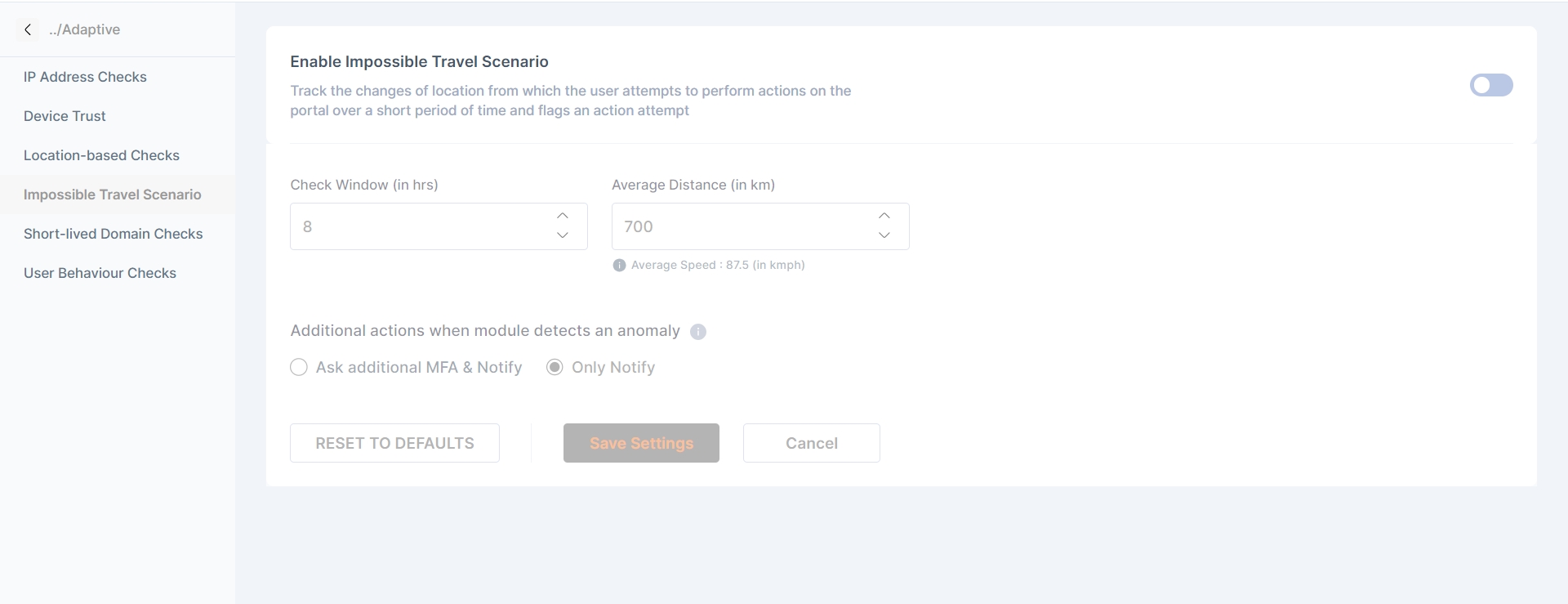
Impossible travel scenario - Tracks the change in location of user attempting an action over a short period of time and flagging if, system deems the pattern to be impossible.
The admin can enable these checks as per the business use case
To navigate to the adaptive settings page, click on the "Go to settings" button on the top right corner of the page.
Administrators can include an IP address in the blacklist by following these steps:
Enable the "IP address Check" radio button at the top of the page, input the IP address into the "Blacklisted IP address" field, and press enter. The specified IP will be added to the list. To synchronize the list with the database, click the "Sync Now" button.
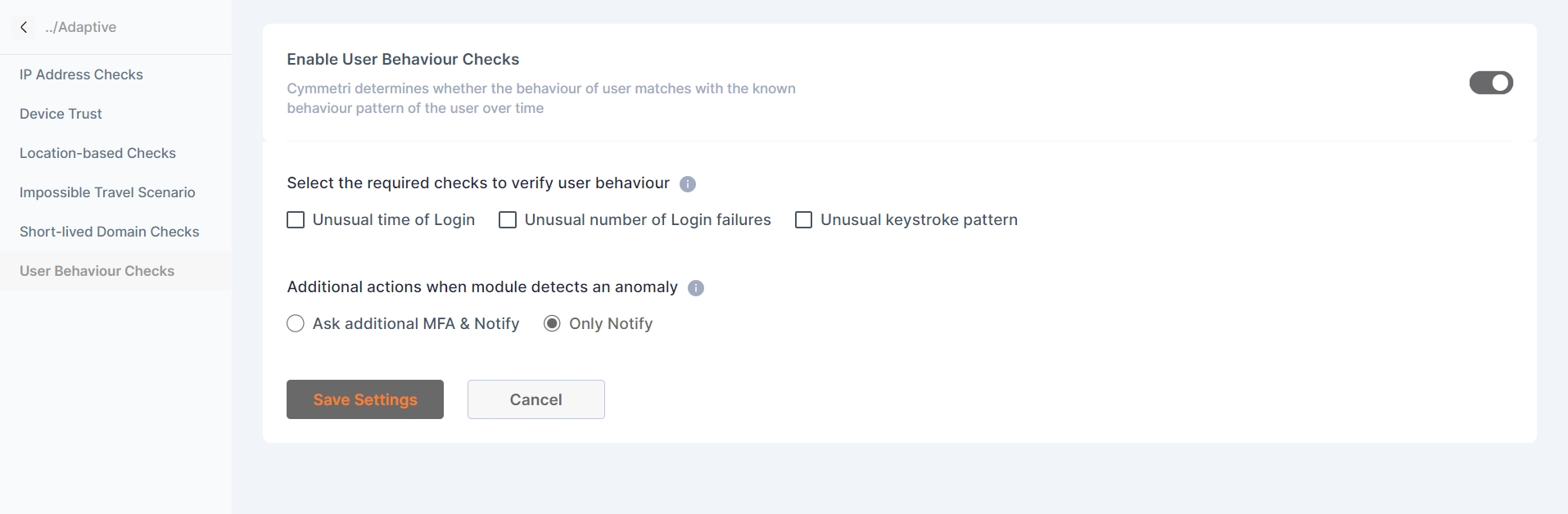
You can select additional actions when module detects an anomaly. They are the following:
Ask additional MFA and notify - If an MFA rule has been established and adaptive authentication is activated for it in the MFA section, when a user attempts to log in with a blacklisted IP address, the user will be prompted for additional factor(s) for authentication as defined by the rule. Additionally, the user will receive email notifications regarding the login activity.
Only Notify - This option solely sends a notification to the user about the login activity.
Block user and notify - This option not only blocks the user upon a login attempt with a blacklisted IP but also notifies the user on their registered email ID.
Define how Cymmetri determines if a device is trusted for the user and allows to define behavior of authentication in Cymmetri, in case of untrusted device
The admin can define
No of successful authentication attempts
Number of devices per user
Number of days
Additional action when module detects anomaly
Location based checks
Organizations can maintain a list of blacklisted locations as part of their adaptive authentication strategy to enhance security measures and mitigate potential risks
The admin can select the blacklisted location on this page. Also additional actions on these checks can be selected.
Impossible Travel Scenario
Track the changes of location from which the user attempts to perform actions on the portal over a short period of time and flags an action attempt
The admin can configure the:
Check Windows(in hrs)
Average Distance (in Km)
Short lived Domain Checks
Checks the .email address domain of the user with a database of known providers of short-time or disposable email addresses
The admin can Sync the database where the domains are stored and updated
User behavior checks
Cymmetri determines whether the behavior of user matches with the known behavior pattern of the user over time
The admin can select the required checks to verify the consumer behavior:
Unusual time of Login
Unusual number of Login failures
Unusual keystrokes pattern
The admin can enable, configure and save these adaptive checks individually as and when required.