Deprovisioning rules in any IAM system define the automated processes for managing the removal or deactivation of user accounts and access privileges when certain conditions are met.
These rules play a critical role in ensuring that access rights are promptly revoked when users no longer require them, enhancing security and compliance.
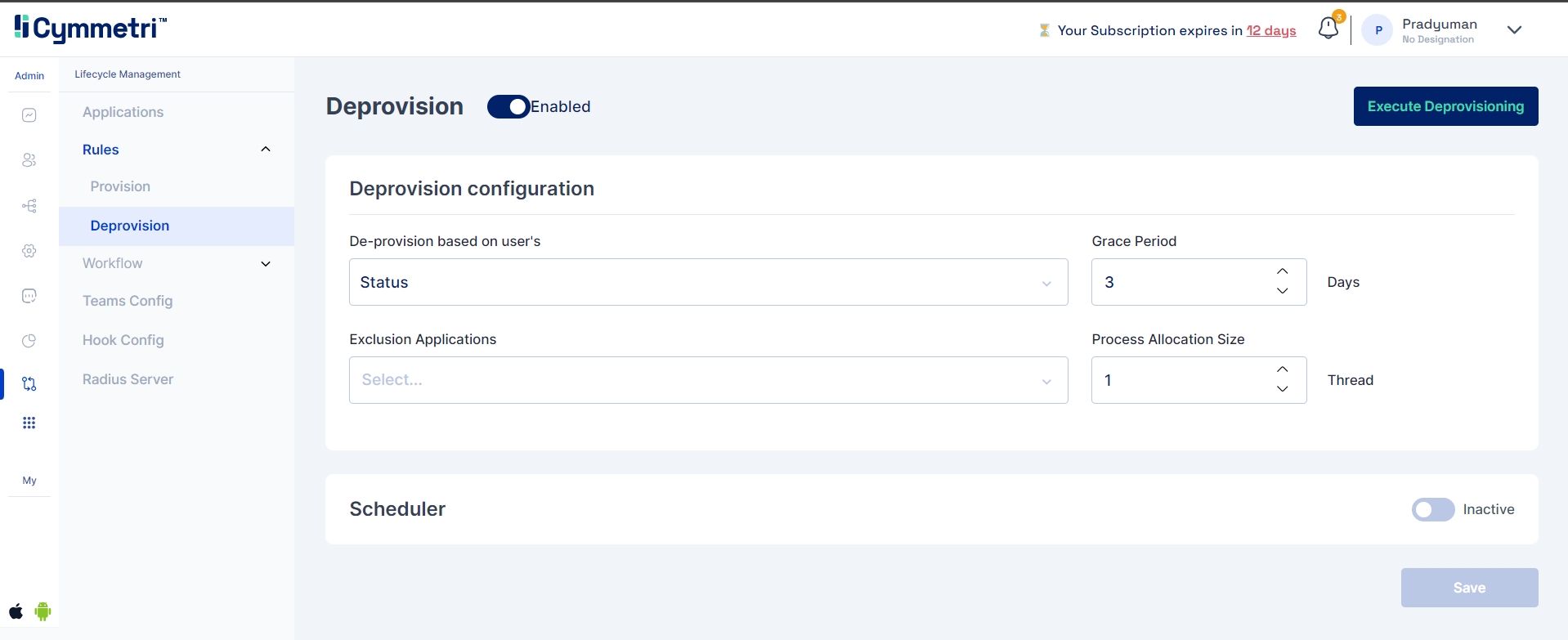
In Cymmetri, to establish deprovisioning rules, navigate to the "Deprovisioning" section within the rules under the User Lifecycle Management module.
Deprovisioning configuration includes the following:
Deprovisioning the user based on the Status or End Date of the user retrieved from the source system. Additionally, administrators can also choose to define provisioning based on any Hook Rule that provides users with the ability to insert custom logic for deprovisioning event.
Exclusion Application: This feature enables administrators to specify which applications should be exempt from the deprovisioning event in Cymmetri. Consequently, whenever deprovisioning is initiated, these selected applications will not be removed from a user's access.
Grace Period: The grace period allows you to set the number of days before the application is removed from the user's access.
Process Allocation Size: It refers to the number of simultaneous threads or parallel processes that Cymmetri allocates for executing the deprovisioning tasks. It determines how many user accounts or access revocations can be processed concurrently.
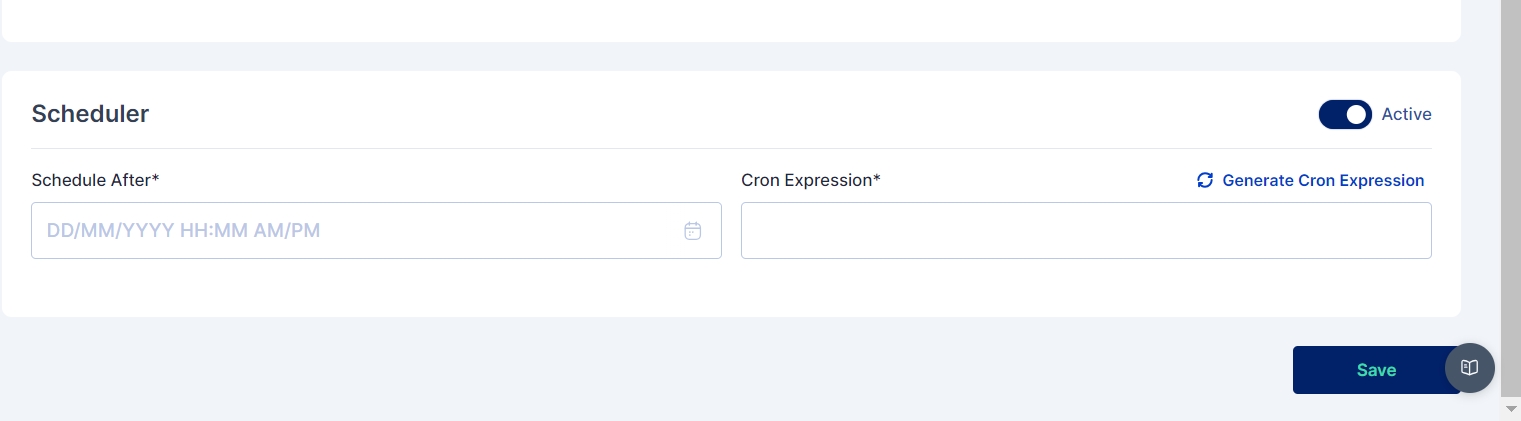
In Cymmetri, administrators can create a custom scheduler for a Deprovisioning rule to promptly eliminate unauthorized user access as per a specified timetable. This involves defining the scheduler using a cron expression, activating it, and saving the configured settings.
In any Identity and Access Management (IAM) system, provisioning rules are predefined instructions or policies that dictate how user accounts and access privileges are automatically created, modified, or deactivated across various IT systems and applications.
These rules streamline the process of managing user identities and access rights throughout their lifecycle within an organization.
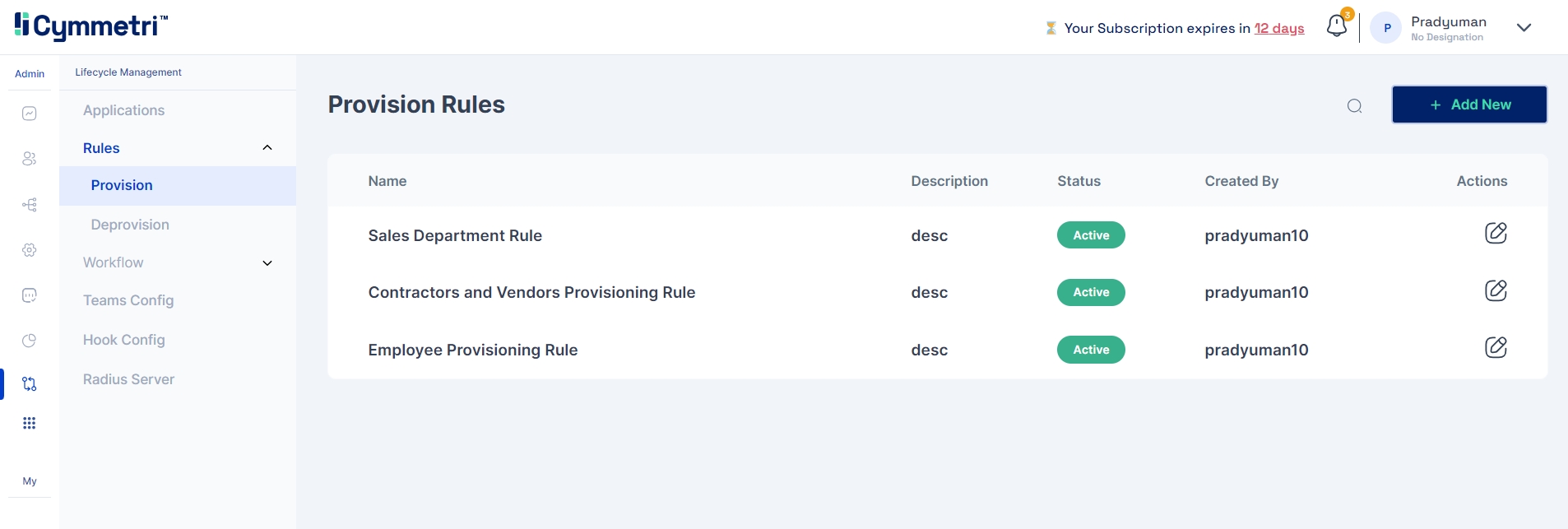
In Cymmetri, administrators have the ability to establish these rules within the "Rules" tab under the Lifecycle Management module. To do so, the administrator navigates to the "Provision" section, where the following page will be displayed.
On this page, administrators can view a comprehensive list of all the currently established rules within Cymmetri, along with an "Edit" button that allows them to make modifications to these rules.
On the top right corner of the page the admin can find the Add New button to add a new provisioning rule in Cymmetri.
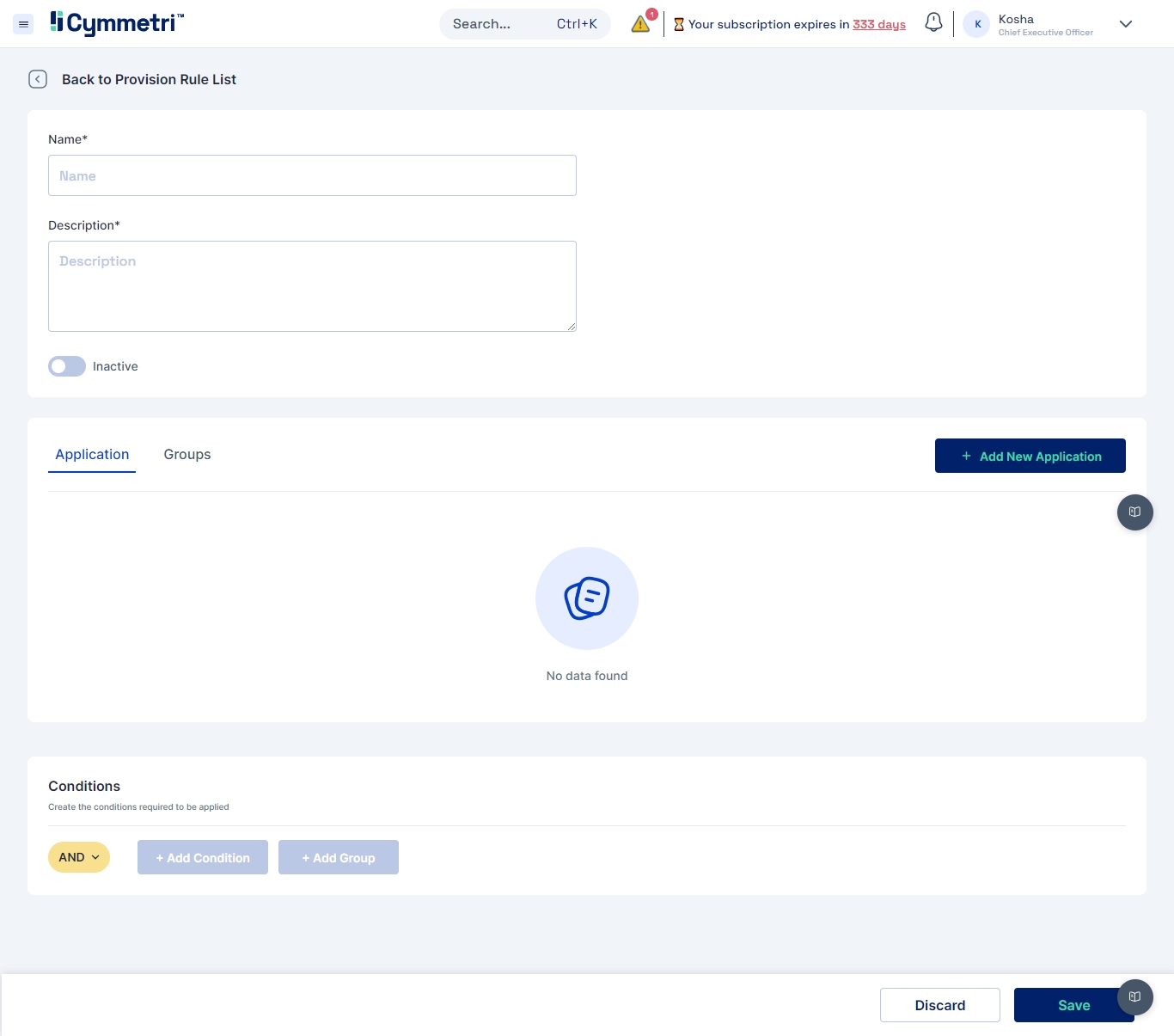
To add a new rule you must do the following:
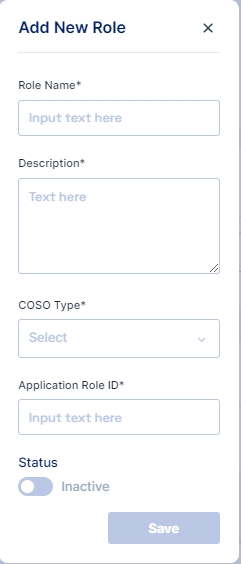
Add the name of the rule
Add Description of the rule
Activate the rule
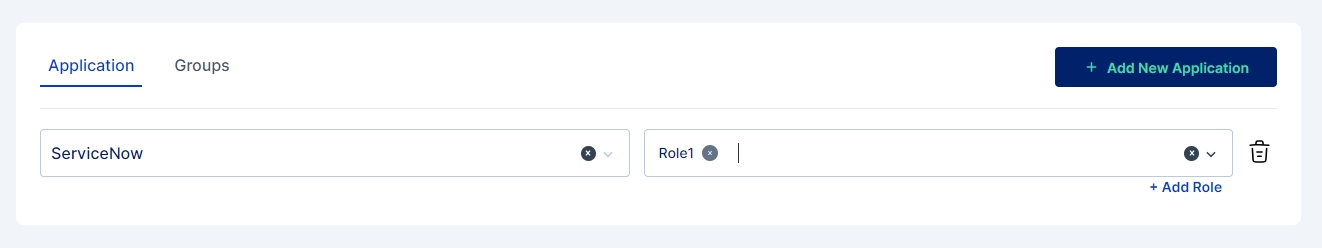
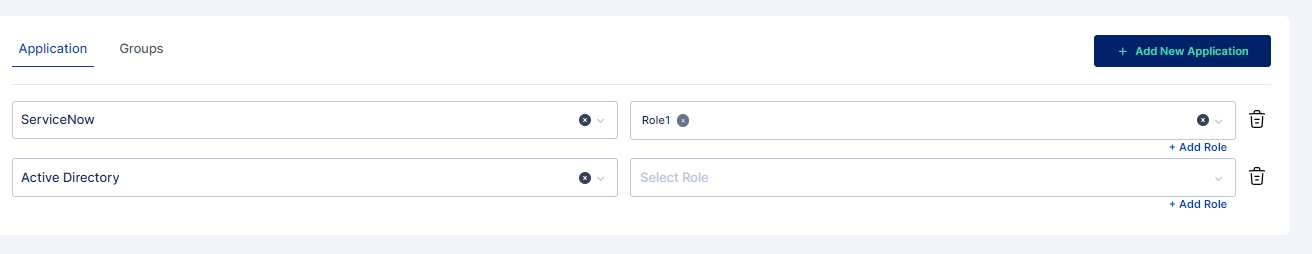
Next select one or more applications with their corresponding roles (if defined).
If necessary, roles can be created for the application directly within the provisioning rule before adding them.
Note: Multiple application and roles can be added in a single provisioning rule
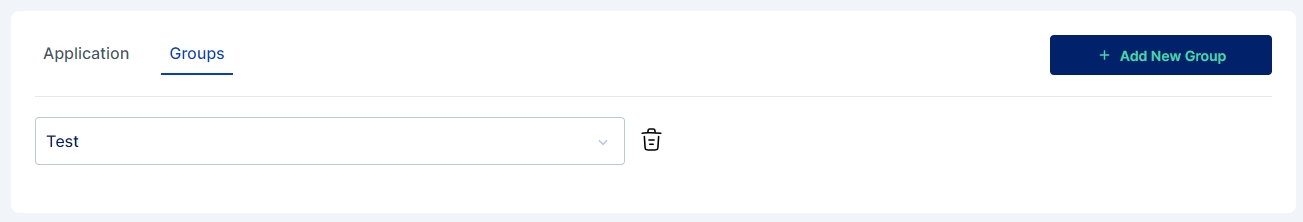
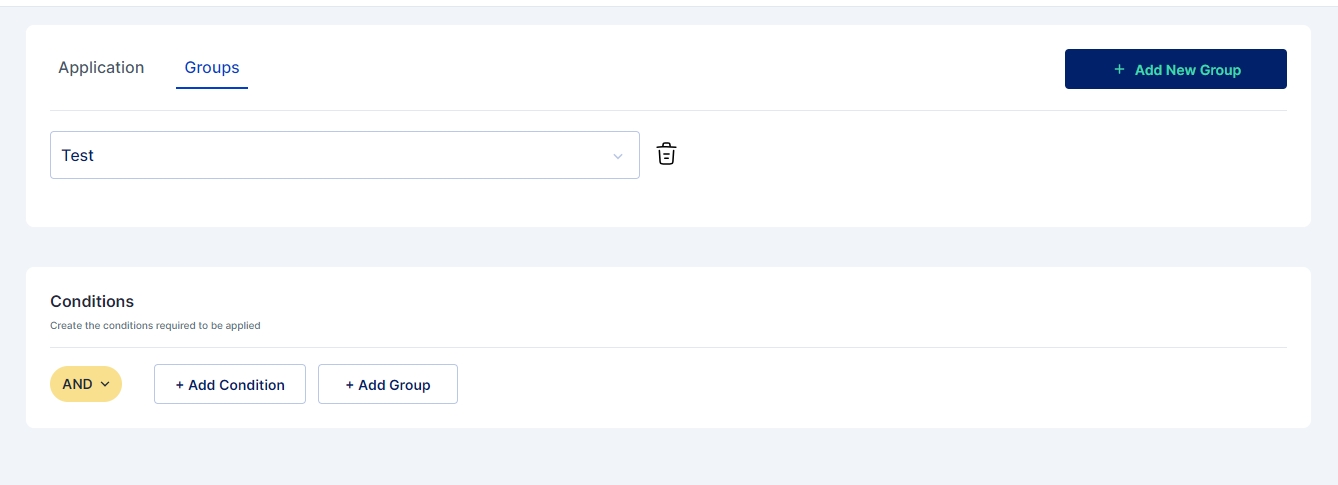
Just the way multiple applications can be assigned to users during provisioning, administrator can also assign one or more groups during the provisioning process.
For assigning groups the administrator needs to go to the Groups Tab and click on +Add New Group button.
Next a drop down appears where the user may select the group that the user needs to be a part of. Administrator may also assign multiple groups if required.
The next step is to add the condition upon which the rule will be activated within the system.
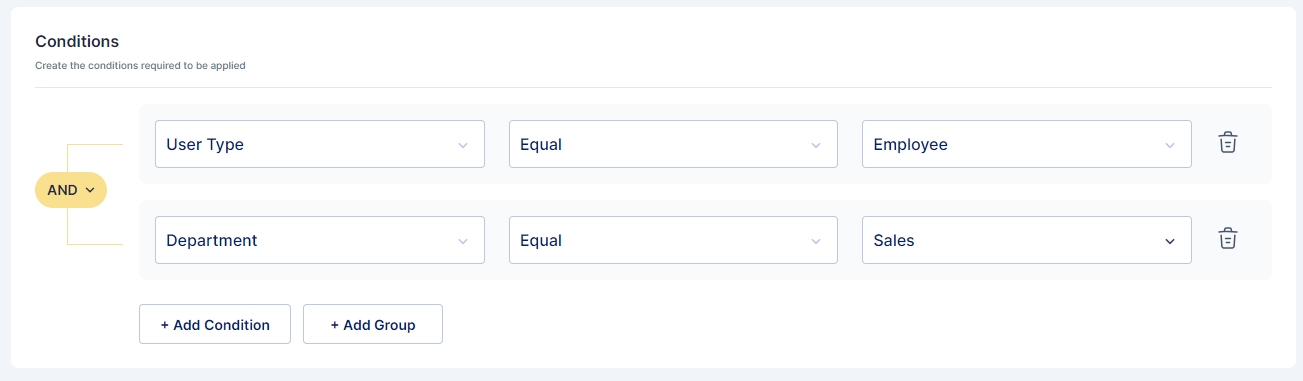
To add a condition navigate to the conditions section and click on + Add Condition button.
You can set up multiple conditions for the rule. For example, in the rule below, the conditions are that the user must be an "Employee," and their department should be "Sales."
A group of conditions can be added to be true/ false together.
The AND/ OR Switch allows to toggle if all the conditions are associated with an AND condition or an OR Condition
If required these conditions can be added, deleted or modified.
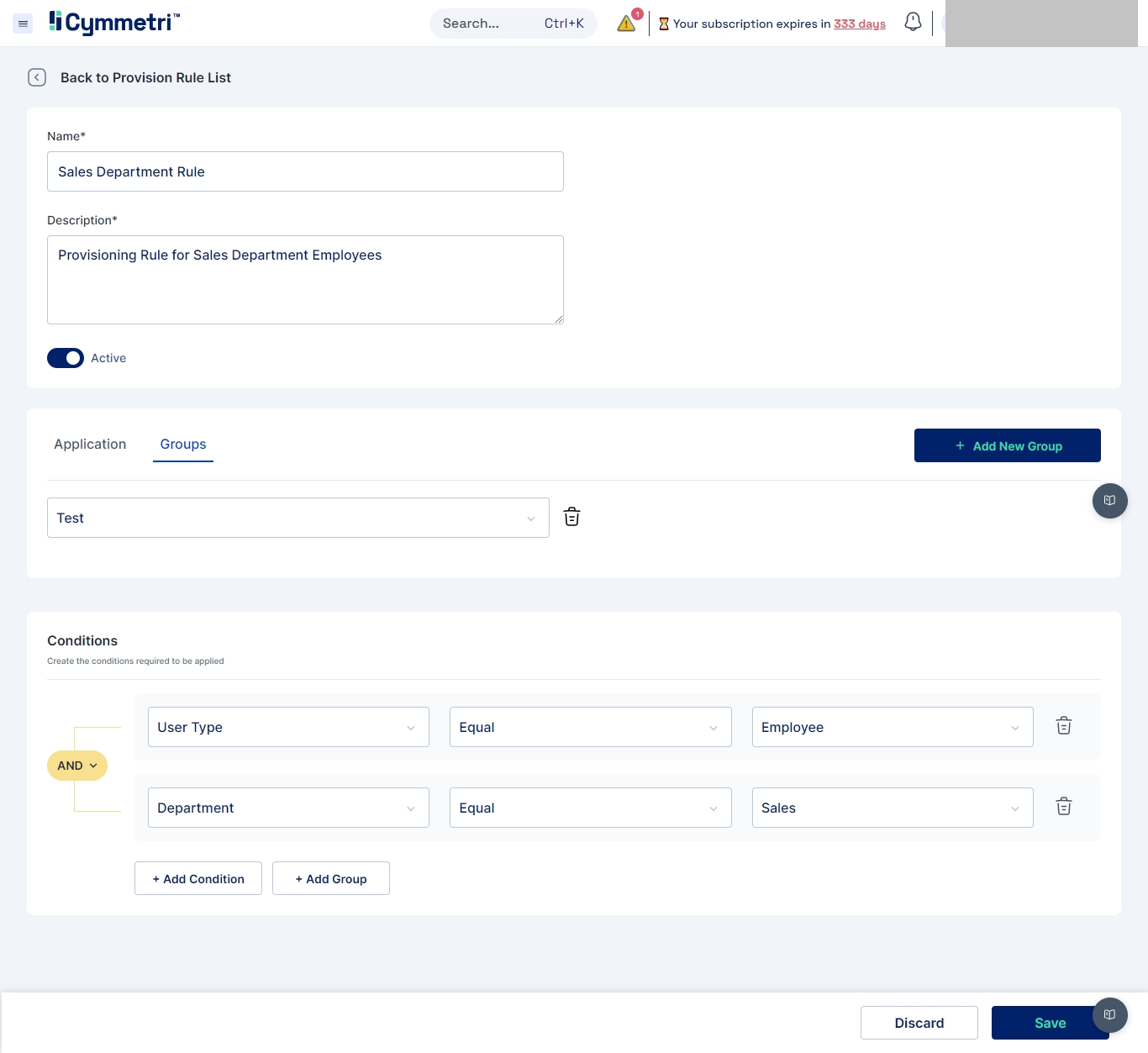
Once all the configurations are done the page needs to be saved. The Provision Rule creation page after all the configurations appears as below:
These rules automate and streamline the process of managing user accounts and access privileges across various systems and applications within an organization.