Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Understand how to add and manage your cloud and on-premise applications through your Cymmetri Identity platform deployment. Your Cymmetri Identity deployment allows you to manage your cloud-based applications and on-premise applications from a single administration console.
Understand how to add the applications used by your organization, to be managed your Cymmetri Identity platform deployment. Use the FAQ to learn how to add applications to be managed in the deployment.
Single Sign On is the process of ensuring that once an end user is logged onto the Cymmetri Identity platform, they should be able to seamlessly move their session to any of your applications managed by your Cymmetri Identity platform deployment. Use the FAQ to learn how to configure Single Sign On for your application.
Modern IAM deployments wishing to have progressive authentication may require some critical application integrations within your deployment to perform additional authentication while performing Single Sign On for the end user. Use the FAQ to learn how to configure the Application Sign On Policy.
Provisioning refers to the process of creating, modifying, and in general pushing the user account information stored on the Cymmetri Identity platform to the applications managed by your Cymmetri Identity platform deployment. Use the FAQ to learn how to configure User Account Provisioning.
Reconciliation of User accounts is a primary activity in Identity Governance, which allows for synchronisation between the user account information on the managed application and the Cymmetri Identity platform deployments, including provisioning, modifying, deprovisioning, and modifying user account attributes based on various synchronisation states. Use the FAQ to learn how to configure the Identity Reconciliation Process.
Once an application has been added to the Cymmetri Identity platform deployment and the necessary configurations for Single Sign On, Provisioning and Reconciliation have been performed, an application may be assigned to an individual user or to a group of users. Use the FAQ to learn how to assign application to a user.
Connectors can be deployed in two ways:
Local connectors are deployed to a Cymmetri instance. This is the usual way how connectors are used. The connector is executed inside a Cymmetri instance, has the same lifecycle (start/stop), etc. Cymmetri can detect local connectors automatically and overall the connector management is easier.
Remote connectors are executed in a different process or on a different node than Cymmetri instance. Remote connectors are deployed to a connector server. There may be need to use a remote connector e.g. to access a file on a remote system (e.g. in case of CSV connector) or because of platform incompatibilities (e.g. .NET connectors)
Connector is not developed as local or remote. The placement of the connector is a deployment-time decision. There is just one connector package that can be deployed locally or remotely.
A connector server is required when a connector bundle is not directly executed within your application. By using one or more connector servers, the connector architecture thus permits your application to communicate with externally deployed bundles.
Connector servers are available for both Java and .NET.
A Java connector server is useful when you do not wish to execute a Java connector bundle in the same VM as your application. It may be beneficial to run a Java connector on a different host for performance improvements if the bundle works faster when deployed on the same host as the native managed resource. Additionally, one may wish to use a Java connector server under a Java remote connector server in order to eliminate the possibility of an application VM crash due to a fault in a JNI-based connector.
The use of .NET connector server is especially useful when an application is written in Java, but a connector bundle is written using C#. Since a Java application (e.g. J2EE application) cannot load C# classes, it is necessary to instead deploy the C# bundles under a .NET connector server. The Java application can communicate with the C# connector server over the network, and the C# connector server serves as a proxy to provide to any authenticated application access to the C# bundles deployed within the C# connector server.
Minimum Requirements:
Java 1.6 or later for 1.4.X.Y / Java 1.8 for 1.5.X.Y
Refer to your Java connectors to determine if there are any additional requirements
Unzip it in a directory of your choice (e.g. /usr/jconnserv) on the host where you wish to run the Java connector server
From the directory created above, run the Java connector server with no arguments to see the list of command-line options:
Linux / MacOS: ./bin/ConnectorServer.sh
Windows: \bin\ConnectorServer.bat
You should see the following output:
Run the connector server with the setkey option as described below to set your desired key into your properties file
Linux/ MacOS: ./bin/ConnectorServer.sh -setkey <key> -properties conf/ConnectorServer.properties
Windows: bin\ConnectorServer.bat /setkey <key> /properties conf\ConnectorServer.properties
For all other properties (e.g. port), edit the conf/connectorserver.properties manually. The available properties are described in the connectorserver.properties file.
Run the server by launching with the -run option:
Linux / MacOS: ./bin/ConnectorServer.sh -run -properties conf/ConnectorServer.properties
Windows: bin\ConnectorServer.bat /run -properties conf\ConnectorServer.properties
To deploy a Java connector:
Copy the Java connector bundle jar file into the bundles directory in your Java connector server directory
If necessary, add to the classpath any 3rd party jars required by any Java connector
Restart the Java connector server
The following steps are necessary to successfully communicate with a connector server using SSL:
Deploy an SSL certificate to the connector server's system.
Configure your connector server to provide SSL sockets.
Configure your application to communicate with the communicate with the connector server via SSL.
Refer to your application manual for specific notes on how to configure connections to connector servers. You will need to indicate to your application that an SSL connection is required when establishing a connection for each SSL-enabled connector server.
Additionally, if any of the SSL certificates used by your connector servers is issued by a non-standard certificate authority, your application must be configured to respect the additional authorities. Refer to your application manual for notes regarding certificate authorities.
Java applications may solve the non-standard certificate authority issue by expecting that the following Java system properties are passed when launching the application:
javax.net.ssl.trustStorePassword
For example, -Djavax.net.ssl.trustStorePassword=changeit
javax.net.ssl.trustStore
For example, -Djavax.net.ssl.trustStore=/usr/myApp_cacerts
Or, instead, the non-standard certificate authorities may be imported to the standard ${JAVA_HOME}/lib/security/cacerts.
Minimum Requirements:
Windows Server 2003 or 2008
.NET Framework 3.5 or higher
Refer to your .NET connector to determine if there are any additional requirements
Execute ServiceInstall.msi. Just follow the wizard. It will walk you through the whole process step by step. Upon completion, the Connector Server will be installed as a windows service.
Start the Microsoft Services Console. Check to see if the Connector Server is currently running. If so, stop it. From a command prompt, set the key for the connector Server. This is done by changing to the directory where the connector server was installed (by default: \Program Files\Identity Connectors\Connector Server) and executing the following command:
where <newkey> is the value for the new key. This key is required by any client that connects to this Connector Server.
Look through the configuration file and inspect all settings. The most common things to change would be the port, trace, and ssl settings.
The port, address, and SSL settings are in the tag called AppSettings, and look like this:
The port can be set by changing the value of connectorserver.port. The listening socket can be bound to a particular address, or can be left as 0.0.0.0. To setup to use SSL, you must set the value of connectorserver.usessl to true, and then set the value ofconnectorserver.certifacatestorename to your the certificate store name.
You will need to record for use later the following information regarding your connector server installation:
Host name or IP address
Connector server port
Connector server key
Whether SSL is enabled
Trace settings are in the configuration file. The settings look like this:
The Connector Server uses the the standard .NET trace mechanism. For more information about the tracing options, see Microsoft's .NET documentation for System.Diagnostics.
The default settings are a good starting point, but for less tracing, you can change the EventTypeFilter's initializeData to "Warning" or "Error". For very verbose logging you can set the value to "Verbose" or "All". The amount of logging performed has a direct effect on the performance of the Connector Servers, so be careful of the setting.
Any configuration changes will require the connector server to be stopped and restarted.
The best way to run the Connector Server is as a Windows service. When installing, the Connector Server is installed as a Windows service. This should be fine for most installations.
If for some reason, this is not adequate, the connector server may be installed or uninstalled as a Windows service by using the /install or /uninstall arguments on the command line. To run the Connector Server interactively, issue the command:
To install new connectors, change to the directory where the Connector Server was installed, and unzip the zip file containing the connector there. Restart the Connector Server.
To install additional Connector Servers on the same machine, download the Connector Server zip file from the downloads section. Create a directory to install to, and unzip the file there. Edit the configuration file as described above ensuring that you have a unique port. You may also want to make sure that the trace file is different as well. You can then run the additional Connector Server interactively or as a service.
In this section, we will provide you with detailed information about the types of applications and connectors supported by Cymmetri
Cymmetri seamlessly integrates with various cloud-based applications to help you efficiently manage user access and entitlements. The following are the pre-configured cloud-based applications that Cymmetri supports:
Azure: Manage user access and entitlements within your Microsoft Azure environment effortlessly.
Google Workplace: Simplify access management for Google Workspace applications, including Gmail, Google Drive, and more.
ServiceNow: Effectively control access to your ServiceNow instance to enhance security and compliance.
Salesforce: Streamline Salesforce user access management for better control and auditing.
SCIM v2.0 (Salesforce): Utilize the System for Cross-domain Identity Management (SCIM) 2.0 protocol specifically for Salesforce integration.
Github (Using SCIM 2.0 connector): Manage user access to GitHub repositories efficiently through our SCIM 2.0 connector.
Cymmetri extends its support beyond cloud-based applications to include various on-premises applications. Here are the on-premises applications supported by Cymmetri:
Active Directory: Efficiently manage user access to your Windows Active Directory resources.
OpenLDAP: Simplify access control for your LDAP directory services with Cymmetri's integration.
Lotus Notes: Streamline user access management for Lotus Notes applications.
Powershell: Integrate and manage access to PowerShell scripts and resources seamlessly.
CSV Directory: Effectively manage user access within CSV-based directory services.
Cymmetri offers versatile connector support to ensure seamless integration with a wide range of applications. Here are the supported connectors categorized by deployment type:
Cymmetri's Cloud Connectors are designed to simplify access management for various cloud-based applications. Supported cloud connectors include:
Azure: Easily manage access to Microsoft Azure resources with our cloud connector.
Google Workplace: Streamline access management for Google Workspace applications using our cloud connector.
ServiceNow: Control access to your ServiceNow instance efficiently with our cloud connector.
Salesforce: Seamlessly manage user access to Salesforce through our cloud connector.
SCIM 1.1: Leverage the SCIM 1.1 protocol for connector support, ensuring compatibility with various cloud services.
SCIM 2.0 (Basic, Bearer, Fixed Bearer): Our platform supports multiple SCIM 2.0 authentication methods to accommodate diverse integration needs.
For on-premises applications and custom integration scenarios, Cymmetri offers locally deployed connectors, providing flexibility and control. Supported locally deployed connectors include:
Active Directory: Manage access to Windows Active Directory resources seamlessly using our connector.
Custom Script for Databases: Custom Script based connectors using groovy scripts for database applications, tailored to your specific requirements.
LDAP: Integrate and manage access to LDAP-based directory services through our connector.
Lotus Notes: Simplify user access management for Lotus Notes applications with our connector.
Powershell: Seamlessly integrate and manage access to PowerShell resources using our connector.
REST API: Extend your integration capabilities with Cymmetri's support for RESTful API connectors leveraging the flexibility of Groovy and UI based scripts.
Cymmetri's comprehensive support for both pre-configured applications and versatile connectors ensures that you have the tools needed to efficiently manage user access and entitlements across a diverse range of applications and environments. For detailed setup instructions and configuration guidelines, please refer to the specific documentation for each application and connector.
Dynamic Forms enable administrators to request additional fields from either administrators or end-users when assigning applications. These additional user fields are then collected and used for provisioning the user into the managed application.
Creating a dynamic form involves the administrator configuring the managed application by clicking on the left-hand side menu item “Forms”.
Load the default form by clicking on the “Load Sample Data” button
Edit the default form, a preview of the form is shown on the right hand side.
Let us create a simple form that can capture
“Preferred Username” [text field] and
“Request Additional Modules” [Radio] with two options “Administrator” and “Read Only”.
Click on the Save button.
Click on the “Confirm” button in the popup to enable the form for the application.
Once the managed application has been added to your Cymmetri Identity platform tenant, you will be able to assign applications to your end-users.
There are three ways in which applications can be assigned to users:
Admin may assign an application directly to a user.
Admin may map an application to a group; and the user is added to the group or is already part of the group.
End User may request an application and is granted access to the application.
Let us understand the flow for each of the above mentioned scenarios:
Users with admin roles such as Organization Admin, Domain Admin, or Application Admin on the Cymmetri platform can assign managed applications to end-users .
First, we need to add the application to the Cymmetri platform
Next, we move to configure the application to assign it to an end user.
Click on the application tile to configure it.
The flow for assignment goes as follows -
Description:
Admin clicks on the application tile, and starts the configuration.
Click on the Assignments tab on the left hand side menu.
Click on the “Assign New” button on the Users menu.
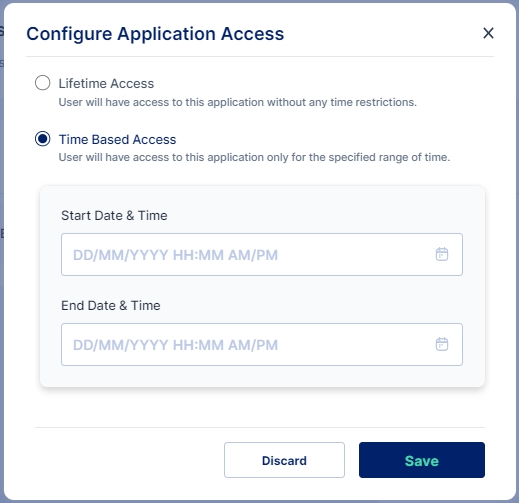
Here we need to decide whether we want to provide a Lifetime Access or a Time Based Access
Lifetime Access: Users have access to the application without any time restrictions.
Time Based Access: Users have access to the application only for the specified range of time. We need to provide a Start Date & Time and an End Date & Time for Time Based Access.
Now click on Save to register a request for the application assignment. If no Workflow is configured for the said application the application is immediately assigned to the user.
If a workflow for application provisioning is configured then the workflow is been initiated.
The workflow approver will then receive a request to approve the user assignment in their inbox.
Now the approver may approve or reject the user assignment
The approver may change the start and end date, if required; refer to the dynamic form attributes passed during the application assignment.
To continue the flow click on Accept button.
Now the next level of approver will be able to see the previous levels of approval, and similar to the previous level of approval, the approver may change the start and end date, if required; refer to the dynamic form attributes passed during the application assignment.
Click “Accept” to proceed.
After the last level approver has also approved the assignment, the backend processes will run the application provisioning flow.
Once the user has been provisioned in the application, they will be able to see it in their list of applications.
Users with admin roles, such as Organization Admin, Domain Admin, or Application Admin, in a Cymmetri Identity platform deployment, will have the ability to assign entire groups of users to managed applications.
First, we need to add the application to the Cymmetri platform
Next, we move to configure the application to assign it to a group.
Click on the application tile to configure it.
The flow for assigning a group to an application goes as follows:
Click on the application tile, and start the configuration.
Click on the Assignments tab on the left hand side menu.
3. Click on the “Assign New” button in the Groups section.
4. Search for the group you wish to assign the application to and click on the assign button.
5. Checking for the users who belong to the group, we can see that the application has been assigned.
6. Viewing the application tiles, we can see if the user was directly assigned the application or received access by the virtue of being part of a group.
Users on the Cymmetri platform can request access to a managed applications as a Self-Service feature.
The flow for an end-user to request for an application is as follows:
Visit the “My Workspace” menu.
Click on the “My Access” left-hand side menu.
3. Now Click on the “+ Request” button on the top-right button.
Here we need to decide whether we want to provide a Lifetime Access or a Time Based Access
Lifetime Access: Users have access to the application without any time restrictions.
Time Based Access: Users have access to the application only for the specified range of time. We need to provide a Start Date & Time and an End Date & Time for Time Based Access.
Now click on Save to register a request for the application assignment. If no Workflow is configured for the said application the application is immediately assigned to the user.
If a workflow for application provisioning is configured then the workflow is been initiated.
The workflow approver will then receive a request to approve the user assignment in their inbox.
Now the approver may approve or reject the user assignment
The approver may change the start and end date, if required; refer to the dynamic form attributes passed during the application assignment.
To continue the flow click on Accept button.
Now the next level of approver will be able to see the previous levels of approval, and similar to the previous level of approval, the approver may change the start and end date, if required; refer to the dynamic form attributes passed during the application assignment.
Click “Accept” to proceed.
After the last level approver has also approved the assignment, the backend processes will run the application provisioning flow.
Once the user has been provisioned in the application, they will be able to see it in their list of applications.
Applications menu in the administration page displays the various options pertaining to the Application Management Process.
Applications menu can be accessed in two ways:
Identity Hub
Login as either an Organization Administrator, Domain Administrator, or Application Administrator.
Click on the Identity Hub icon on the left side bar.
Click on the Applications text on the slide out bar.
Single Sign On Module
Login as either an Organization Administrator, Domain Administrator, or Application Administrator.
Click on the Products menu icon on the left side bar.
Click on the Single SignOn Module icon in the popup list.
4. Click on the Applications text on the slide out bar.
Applications supported by the Cymmetri platform fall majorly into three categories -
Pre-configured Applications These are the applications that have already been configured by the Cymmetri platform for provisioning on cloud or on-premises.
Custom Applications for Provisioning These are the applications that you wish to manage through Cymmetri and support the generic connectors that the Cymmetri platform provides.
Custom Applications for Single SignOn only When you need to add an application for the sole purpose of enabling Single Sign-On (SSO), Cymmetri offers the capability to add a custom application that can be configured for SSO using the supported mechanisms.
Once you have chosen the application to be added from the above categories, you are ready to add a new application.
1. Click on the “Add New” button on the top-right corner in the Applications page.
2. In the Add New Application screen, you may search for your desired application (e.g., Active Directory), or your desired connector (e.g., REST) or choose the “Custom” application type from the available application catalogue.
3. Now click on the tile shown in the list below to open the right slide out menu for renaming application as shown below.
4. Add your custom label (if you wish) in the text box and click on the “Add Application” button.
Application has been successfully added to your listing now. You may click on the configure now button to start configuring the application.
Google Apps is a software-as-a-service platform (SAAS) that provides email, calendar, documents and other services. This connector uses the Google Apps provisioning APIs to create, add, delete and modify user accounts and email aliases.
Note: 1. Only the Premium (paid) or Educational versions of Google Apps provide access to the provisioning APIs. 2. Connector will not work on the free Google Apps Domain
First obtain the client_secret.json file from your Google Apps instance -
Log in to your Google Apps Admin Console (at https://www.google.com/a/domain-name) and verify that Security > Enable API access is checked (For more information on these APIs, navigate to the Google Developers interface, and search for these APIs).
In the OAuth 2.0 application of choice (at https://console.developers.google.com), create credential of type Oauth Client ID / Other, then download the related client_secrets.json file.
Enter https://console.developers.google.com/
Create New Project
Click on Enabled API & Services
Search for Admin SDK API
Click on Admin SDK API and then click on the Enable button
Once enabled, Click on CREDENTIALS tab
Now click on Create Credentials
And select OAuth client ID option
Select Desktop app as Application type, provide a name for the OAuth 2.0 client and then click on the CREATE button
A response screen is visible that shows that the "OAuth client created" It also displays Your Client ID and Your Client Secret. You may download the JSON here using the DOWNLOAD JSON option.
Click on OAuth consent screen and then Click on edit app
Enter the required details and Click on save and update
Select Internal as User Type if you want to restrict access only to the users of your organization.
Click on SAVE AND CONTINUE button on the Scopes screen
Search for Admin SDK API and select
Select for group
Click on credential
Download OAuth client
Change to the directory where you have downloaded the bundle and run the following command on the client_secrets.json file that you obtained earlier in this procedure:
This command opens the default browser, and loads a screen on which you authorize consent to access the Google Apps account.
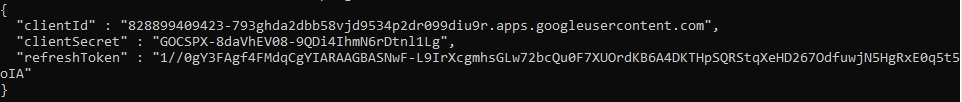
When you have authorized consent, the browser returns a code. Copy and paste the code into the terminal from which you ran the original command
A response similar to the following is returned.
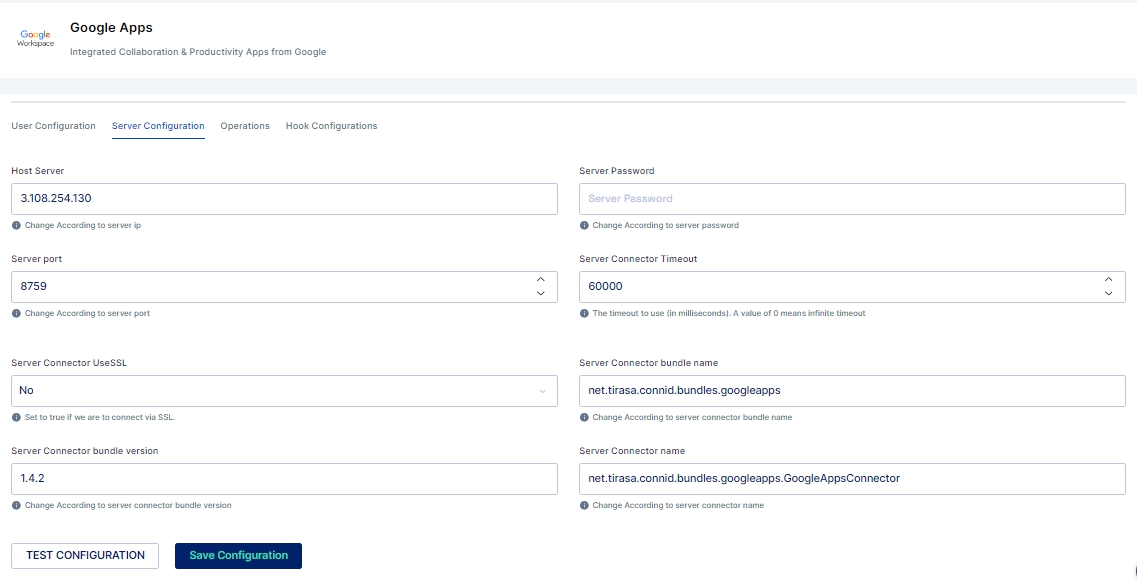
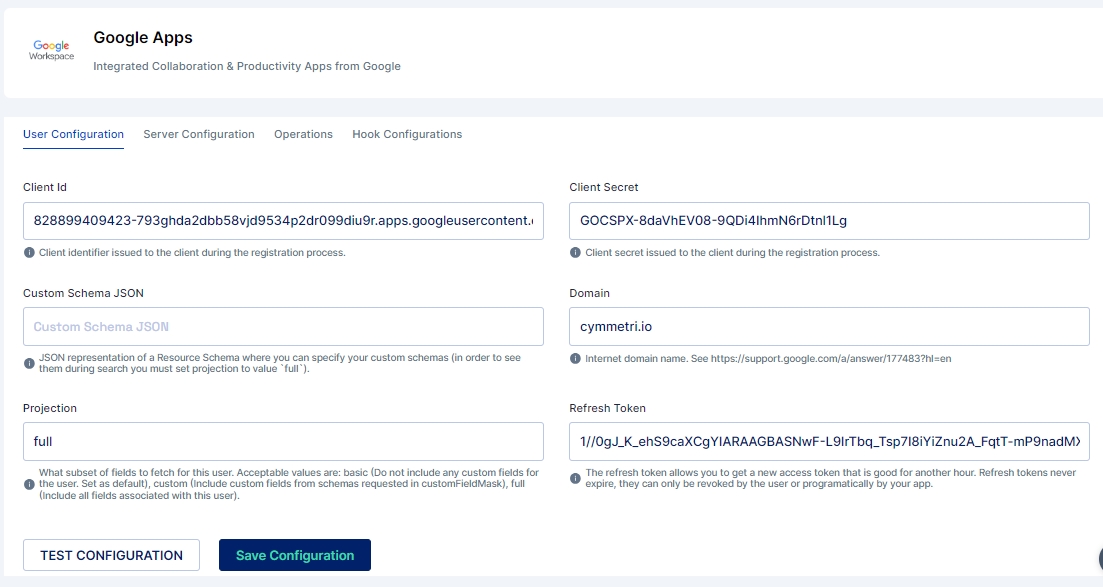
Once the above information is obtained we need to configure the Google App in Cymmetri with Server Configuration and User Configuration as shown below:
Cymmetri Platform allows for pre-configured provisioning settings for Azure Portal.
For Azure integration we need an azure enterprise account with its own domain configured in the Azure AD.
Refer following document to configure azure application
Azure Document https://connid.atlassian.net/wiki/spaces/BASE/pages/308674561/Azure [ConnID]
Create a new OAuth2 Application and provide the following configuration in Azure OAuth2 application.
Application will be created and now we will be able to configure.
Let us now click on Authentication tab on the left-hand side menu. We can choose account either in a single Organization Directory or multiple directory.
Click on Add a platform and we can add a new Redirect URI as “http://localhost”.
Further we can allow the Public Client flows.
Create a new Secret by first, clicking on Certificate and Secrets on the left-hand side menu, and then click on the “+ New Client secret” link, Enter Description and select the Expires option.
Provide the right permissions for the Connector to work by clicking on API Permissions tab on the left-hand side menu, then click on Add, then click on Microsoft Graph and then click on Application Permission and Delegated.
Search and select the following permissions/scopes in OpenID
APIConnectors.Read.All
Directory.ReadWrite.All
OpenID
PrivilegedAccess.Read.AzureAD
User.ReadWrite.All
We need to take consent from admin for getting access to Microsoft Graph API, Click on add permission, Click on “Grant Admin content for Unotech Software”, and finally Click on Yes.
Click on Expose an API and Click on Set to expose the API to be used by the Azure API client on the connector.
Configure Azure user and server config as follows:
Configure the User Configurations
Copy the application authority from the User Configure.
Configure the Client ID.
Configure the Client Secret.
Configure the Domain from Azure Active Directory.
Configure the Redirect URI exposed from the Azure AD.
Graph API base endpoint (User Config Resource URI)
Add the Azure Tenant ID
Choose the base username.
Click on Save, and test the connection.
For active directory configuration we need AD server with 636 port (ldaps protocol should be enabled).
Ensure that all your object classes are included here in the Entry object classes.
Configure the root suffix, which is the base DC and configure the Principal password.
Base Contexts for group entry searches is the base DN for searching for groups in the AD. Change the server hostname and use the domain name instead of IP address.
Enter the principal as the manager’s principal name, the principal is the user account that will be used for making LDAP queries to the Active Directory. SSL must always be true.
Test AD configuration before assigning an application to any user.
After testing AD configuration, Active Directory account will created for the user being provisioned into the Active Directory.
The Cymmetri Identity platform Active Directory provisioning supports the following functions -
Create user
Update user
Delete user
Server hostname needs to be configured for public access
For LDAP connector integration we need an LDAP server with the following detail sample.
Host/IP
LDAP Base Context
service user (Manager Username)
password (Manager User password)
After configure LDAP server we need to configure the Ldap application into the Cymmetri.
Check policy map to add proper attributes as needed by LDAP schema.
Integration REST Application
The REST connector is designed to manage provisioning by relying on RESTful service.
For REST applications we need target applications which support REST API’s.
Following configuration is tested for felicity application.
We need REST API’s to integrate with cymmetri.
Following are the cymmetri configuration which need to configure in user configuration in cymmetri.
It is Basic REST configuration which need to configure in application.
We need to provide Groovy code to run create user, update user, delete user and also recon pull and push (for recon pull we need to add sync script and for recon push we need to add search script)
For sample script please validate following link
Note: Please Configure script step by step
Configure test script at initial step and then test configuration for provided script (If configure successfully then only go for step b).
Configure create script and test configuration (If successfully configured then only go for step c).
Configure update script and test configuration (If successfully configured then only go for step d).
Configure delete script and test configuration (If successfully configured then only go for step e).
Configure sync(pull) script and test configuration (If successfully configured then only go for step f).
Configure search(push) script and test configuration (If successfully configured then only go to the next step).
Any application which supports SCIM v2.0 with bearer token is workable for application.
Following are configuration which is used for SCIM with bearer.
Base address - It is the endpoint of the target system which supports SCIM v2 API’s.
Username - Username to authenticate SCIM API endpoint.
Password - Password to authenticate SCIM API endpoint.
Security Token - It is a token which is used to authenticate.
Grant Type - It is grant type which is used to grant access for API’s.
Client Id - client id for authentication
Client Secret - client secret for authentication
Authentication type - It is Fixed Bearer compulsory.
Update method - Patch or Put method.
Accept - Http header which accepts (application/json etc).
Content Type - Http header which accepts (application/json etc).
Access Token Base Address - base address for access token
Access Token Node Id - node id for access token
Access Token Content Type - content type for access token.
Integration SCIM v2.0 with Basic
Any application which supports SCIM v2.0 with basic authentication is workable for application.
Following are configuration which is used for SCIM with basic authenticator.
Base address - It is the endpoint of the target system which supports SCIM v2 API’s.
Username - Username to authenticate SCIM API endpoint.
Password - Password to authenticate SCIM API endpoint.
Authentication type - It is Fixed Bearer compulsory.
Update method - Patch or Put method.
Accept - Http header which accepts (application/json etc).
Content Type - Http header which accepts (application/json etc).
Search for a user in the search text box, and once the user is found, click on the “Assign” button.
4. Click on the Application Icon to start the request process
Reference:
Any application which supports SCIM v2.0 with fixed bearer is workable for application.
Following are configuration which is used for SCIM with fixed bearer
Base address - It is the endpoint of the target system which supports SCIM v2 API’s.
Username - Username to authenticate SCIM API endpoint.
Password - Password to authenticate SCIM API endpoint.
Authentication type - It is Fixed Bearer compulsory.
Fixed Bearer Value - The value for fixed bearer.
Update method - Patch or Put method.
Accept - Http header which accepts (application/json etc).
Content Type - Http header which accepts (application/json etc).
Github Enterprise provides provisioning using SCIM 2.0
Pre-requisites
Create an account in Github (Enterprise).
Enable SAML for the Github tenant to be used with Cymmetri.
Step 1. Configure SSO in Cymmetri
Note the application URL received from the Git SAML configuration
Continue the configuration by logging into Cymmetri using at least Application Administrator role
Note: Public certificate gets from SSO metadata(cymmetri) and format it using following
https://www.samltool.com/format_x509cert.php
Note: Make sure when you test SAML then in cymmetri login with github admin users loginid which is added in cymmetri.
Configure Profile Mapping
Create User in Cymmetri and make sure login id of Cymmetri is same as gitHub Admin user login id.
Test SSO with the Cymmetri user.
Configure SCIM v2.0 (Github) application from master (cymmetri).
Basic provisioning policy attribute and policy map already aaded in default schema.
Github Application is run using Fixed Bearer token.
To get Fixed bearer token following steps used.
Step 1: Go to user settings in github
Step 2: Go to developer settings
Step 3: Go to personal access token and generate new token
Step4: Click on Configure SSO
Step 5: Click on Authorize
Use following cymmetri provision configuration and change according to github account.
Fixed Bearer Value copy from personal access token
Click on save
Click on Test Configuration with success message.
Check Policy map
Disable default for the respective attribute
Once the applications have been configured to allow that the end-users have been provisioned into the managed application. We may now start configuring the reconciliation process for an application. The reconciliation process involves identifying the user attributes as stored in the Identity hub (Cymmetri platform) and their attributes as a user or a group account in the managed application; and the ensuring that the synchronization of the user and group accounts takes place either one-way or both ways between the managed application and the Identity hub, to ensure that there no discrepancies in the accounts stored by both the systems.
The reconciliation process may follow two strategies -
Full Reconciliation Full reconciliation is typically carried out when the managed application is first introduced into an organization’s Cymmetri platform. This involves ensuring all user accounts (and group accounts, wherever applicable) from the Cymmetri platform, are synchronized with the account information on the managed application. This type of reconciliation often takes a longer time, and is often only used as a one-time activity.
Filtered Reconciliation The Cymmetri platform and the managed application might lose synchronization due to a number of reasons, including backend changes to the user or group account information on the managed application or failure of communication between the identity platform and the managed application. In such cases, filtered reconciliation is employed on a regular, scheduled basis. This includes filters for a particular set of users, or to choose only the users that have been modified on either platforms, this is known as filtered reconciliation.
Cymmetri platform allows for both types of reconciliation phases, by allowing administrator to define an optional user filter during the reconciliation process.
The reconciliation process involves two major processes:
Pull In this mechanism, the Cymmetri platform allows for user and group account information to be pulled from the managed application.
Push In this mechanism, the Cymmetri platform pushes the user and group account information to be pushed to the managed application.
Regardless of the process employed, the configuration for the most part remains the same. Let us explore the reconciliation configurations on the Cymmetri Platform:
You may access the reconciliation menu by clicking on the application tile, and then clicking on the “Reconciliation” left-hand side menu.
Proceed to configure by clicking on the “+ Add New” button.
Name: Refers to the name of the Reconciliation process
Modes: FILTERED_RECONCILIATION (Currently the only mode supported by Cymmetri)
Sync Fields: The field from the user/group’s account information as available on the Cymmetri platform that must be used as a basis to identify the corresponding account on the managed application database.
Source Attributes: The field from the user/group’s account information as available on the managed application database that must be used as a basis to match with the “Sync fields”.
Status: Whether to run the reconciliation for Active/Inactive users.
Type: Some applications allow GROUP reconciliation, but most will have USER reconciliation only.
Filled Reconciliation basic configuration looks as above.
Let us assume we are synchronizing the Cymmetri Platform with a cloud provider using email or mail attribute as the Sync field. As such users on both platforms having the same email address will be matched/un-matched.
User does not exist in Target system & exists in Cymmetri: This indicates a situation during a pull phase or a push phase, where the user account exists on the Cymmetri platform, but not in the managed application. This typically occurs when the users have been pulled into the Cymmetri platform, but the managed application is yet to be synchronized with these users.
User exists in Cymmetri & Target system: This indicates a situation during a pull phase or a push phase, where the user account exists on the Cymmetri platform and in the managed application, but they may or may not have the same attributes or the same values of the attributes.
User exists in Target system & does not exist in Cymmetri: This indicates a situation during a pull phase or a push phase, where the user account exists in the managed application database but not on the Cymmetri Identity platform. This typically occurs when the users have been pulled into the managed application through its backend and the users have not been centrally managed through the Cymmetri platform.
User does not exist in Target system & exists in Cymmetri:
PROVISION: User is created in the target system with the attributes as present in their Cymmetri user profile.
IGNORE: User is not modified in either system.
UPDATE: Not relevant for this scenario.
DEPROVISION: User is removed from the Cymmetri platform to be consistent with the managed application user database.
UNASSIGN: Not relevant for this scenario.
ASSIGN: User is assigned access to this system in Cymmetri, this option may be used in the case of options like JIT being available to generate user profile in the managed application.
UNLINK: Not relevant for this scenario.
LINK: Not relevant for this scenario.
User exists in Cymmetri & Target system:
PROVISION: User is created in the target system with the attributes as present in their Cymmetri user profile.
IGNORE: User is not modified in either system.
UPDATE: User information from the Cymmetri Identity platform is updated using the account information from the managed application and vice versa.
DEPROVISION: Not relevant for this scenario.
UNASSIGN: Not relevant for this scenario.
ASSIGN: User is assigned the managed application on the Cymmetri platform in case they are already not assigned.
UNLINK: Not relevant for this scenario.
LINK: Not relevant for this scenario.
User exists in Target system & does not exist in Cymmetri:
PROVISION: User is created in the Cymmetri Identity platform deployment using the account information from the managed application.
IGNORE: User is not modified in either system.
UPDATE: Not relevant for this scenario.
DEPROVISION: User is removed from the managed application user database.
UNASSIGN: Not relevant for this scenario.
ASSIGN: Not relevant for this scenario.
UNLINK: Not relevant for this scenario.
LINK: Not relevant for this scenario.
Scheduling the reconciliation process:
Next Execution Date: This indicates the base date to start the execution date and time of the reconciliation process.
Cron Expression: This indicates the frequency with which the further reconciliation events will be run. There are 6 fields here - * * * * * * (e.g., 5 15 0 1 8 *) ; they refer to seconds, minutes, hours, days, months, and year after the first execution date.