Provisioning
In any Identity and Access Management (IAM) system, provisioning rules are predefined instructions or policies that dictate how user accounts and access privileges are automatically created, modified, or deactivated across various IT systems and applications.
These rules streamline the process of managing user identities and access rights throughout their lifecycle within an organization.
In Cymmetri, administrators have the ability to establish these rules within the "Rules" tab under the Lifecycle Management module. To do so, the administrator navigates to the "Provision" section, where the following page will be displayed.
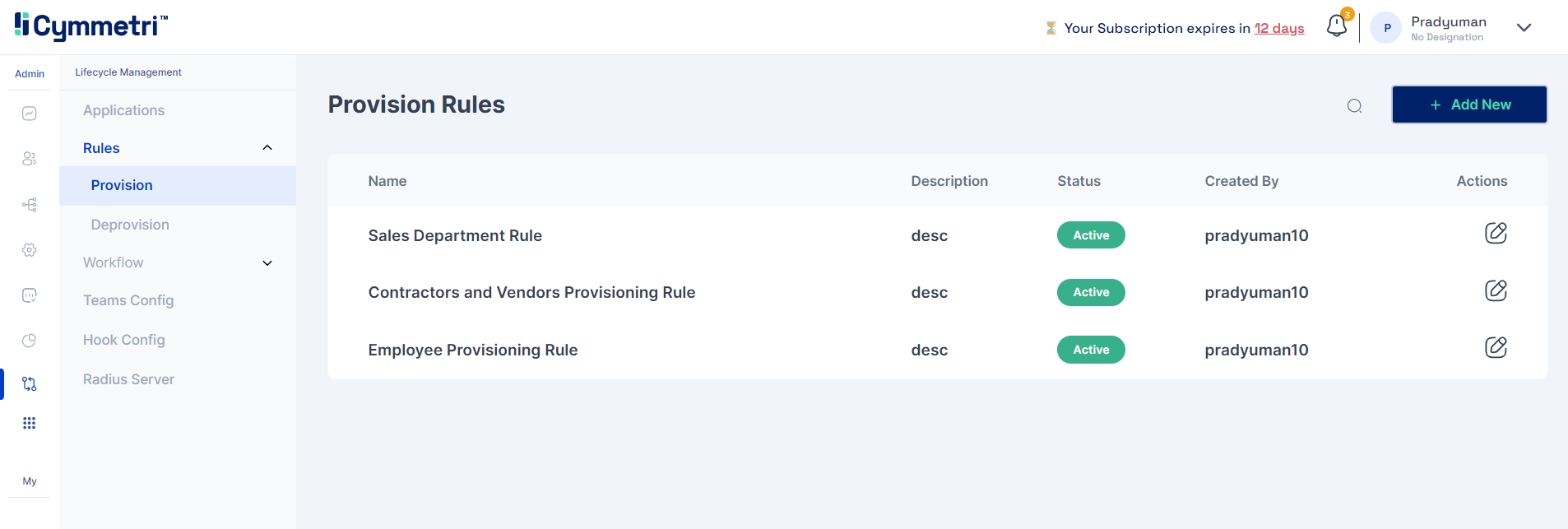
On this page, administrators can view a comprehensive list of all the currently established rules within Cymmetri, along with an "Edit" button that allows them to make modifications to these rules.
On the top right corner of the page the admin can find the Add new button to add a new provisioning rule in Cymmetri.
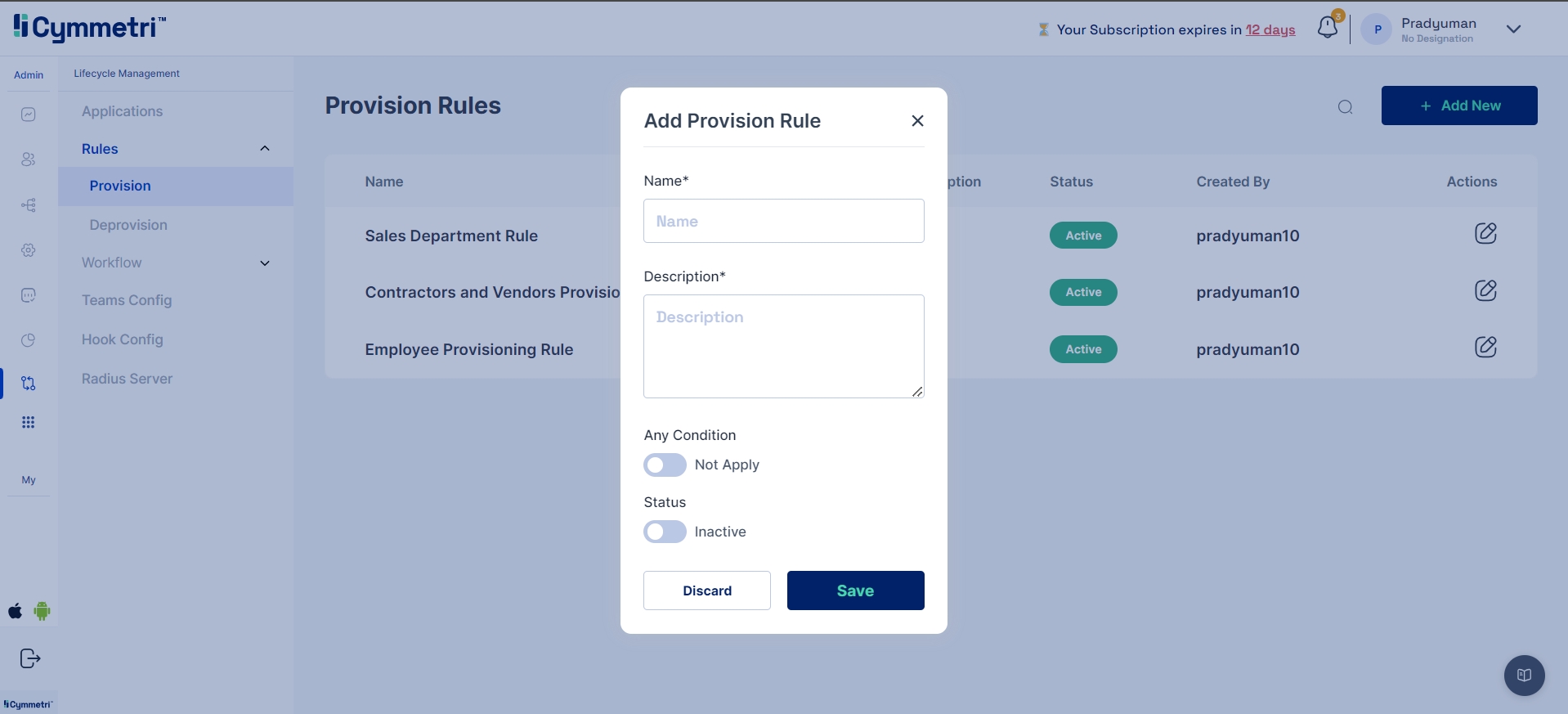
To add a new rule you must do the following:
Add the name of the rule
Add Description of the rule
Select whether any condition should be applied to the rule
Activate the rule and save
Once the rule is saved, it will be included in the main listing. To define or modify the rule, click on the "Edit" button corresponding to the record.
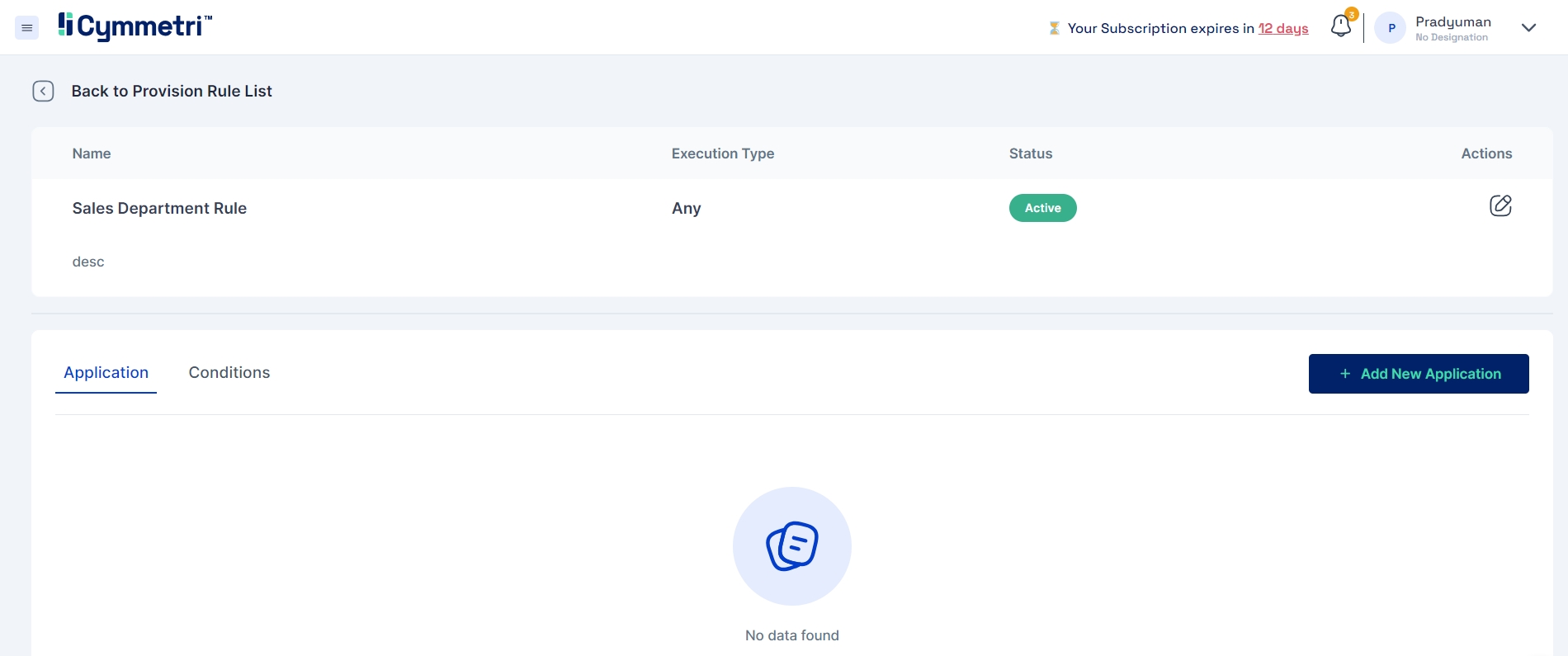
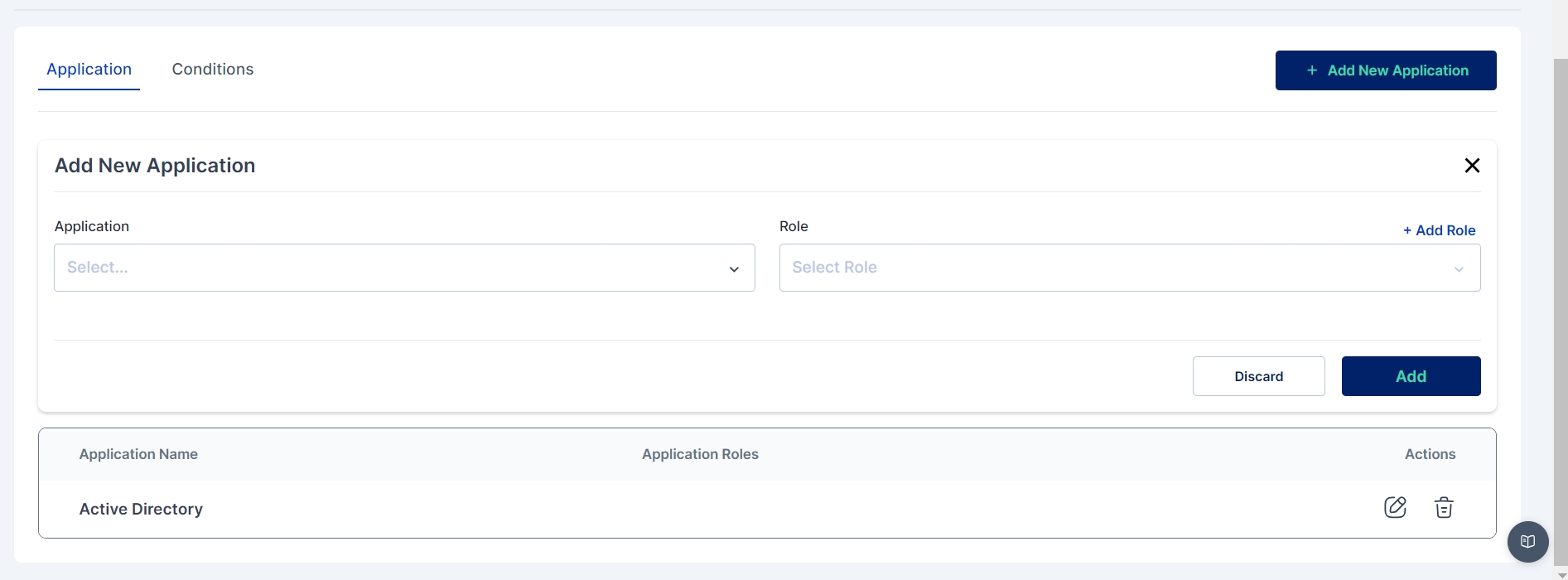
The initial step involves defining the rule by specifying the application and the corresponding roles that will activate the rule.
If necessary, roles can be created for the application directly within the provisioning rule before adding them.
Note: Multiple application and roles can be added in a single provisioning rule
The next step is to add the condition upon which the rule will be activated within the system.
To add a condition navigate to the conditions section and click on Add new condition button.
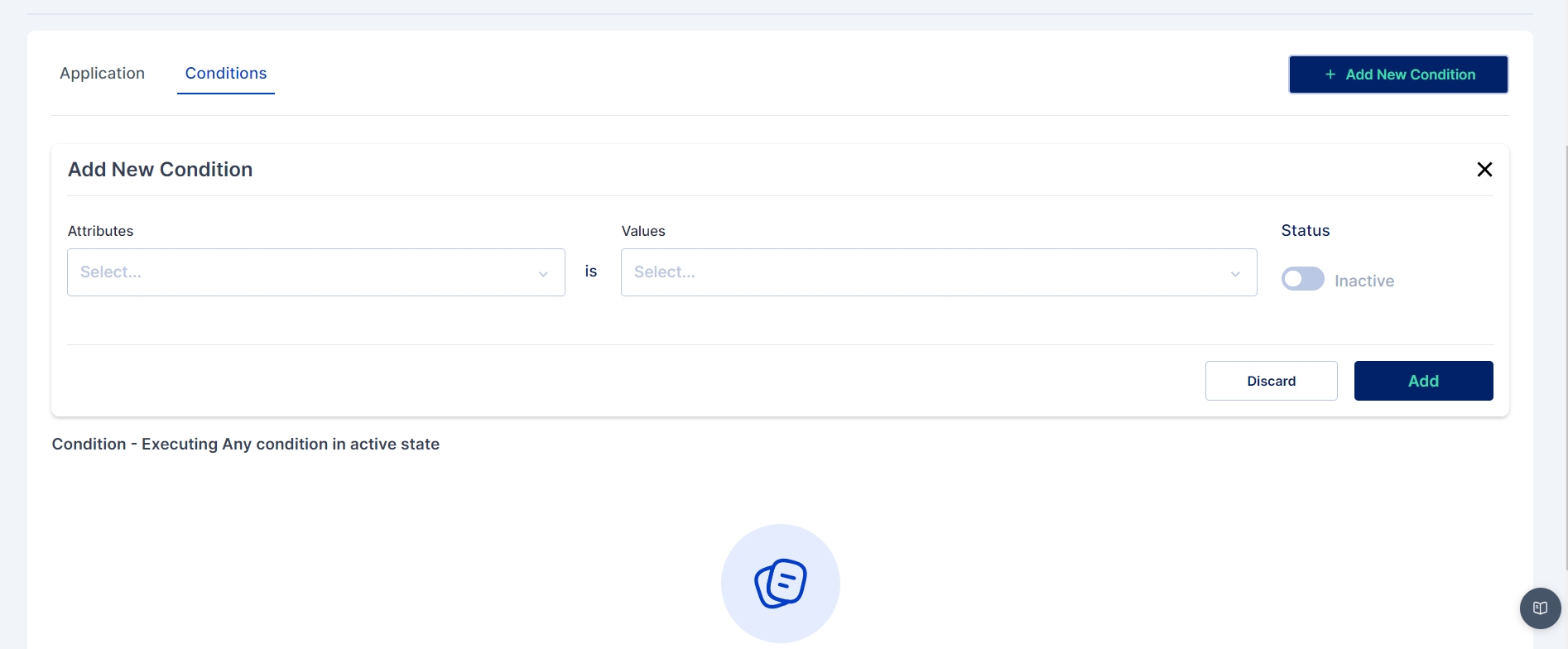
You can set up multiple conditions for the rule. For example, in the rule below, the conditions are that the user must be an "employee," and their department should be "Sales."
Note: Only the active conditions will be executed for the rule to trigger while provisioning.
If required these conditions can be added, deleted or modified.
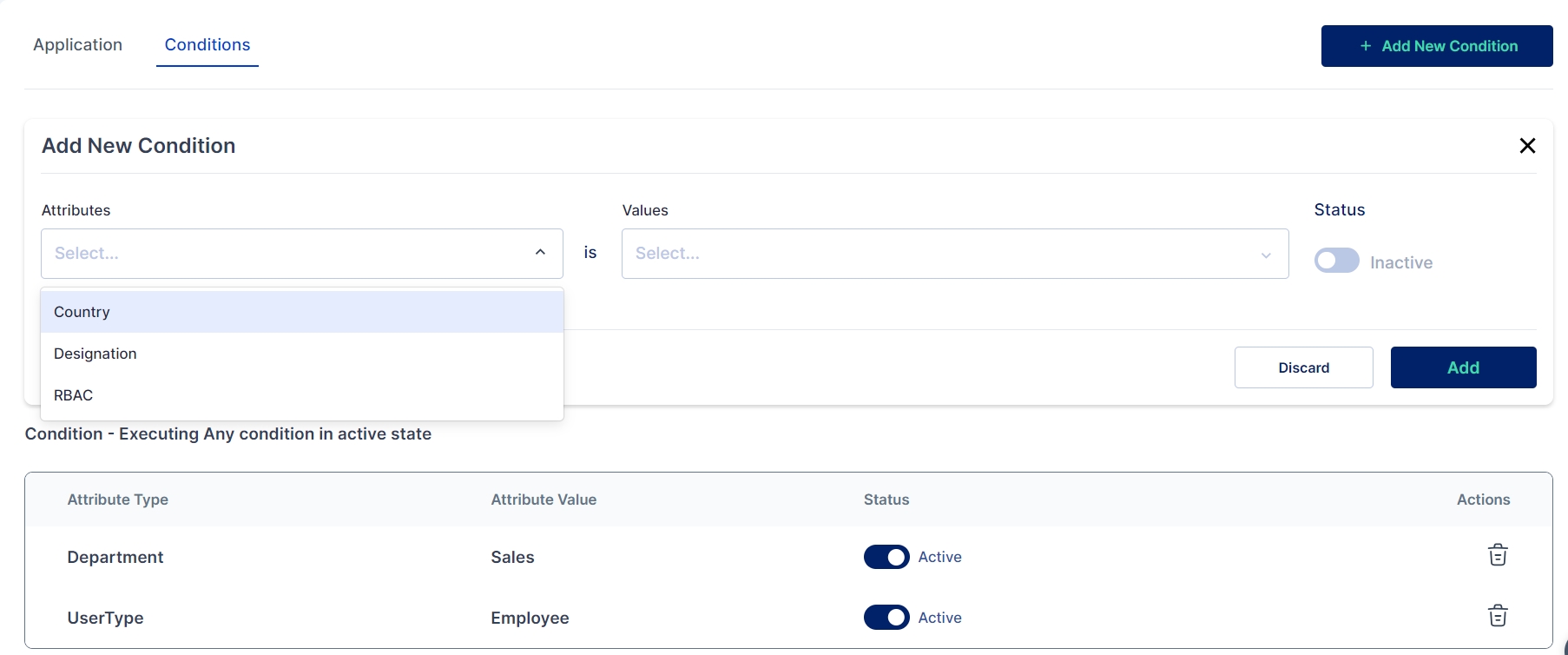
These rules automate and streamline the process of managing user accounts and access privileges across various systems and applications within an organization.
Was this helpful?
