Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Cymmetri is a Converged Identity & Access Management Platform and a well-trusted platform acting as an advisor and an end-to-end partner for Security-aware teams looking to deploy Identity and Access Management Solutions across their organization.
We offer an industry-standard product backed by a strong team that always aims to innovate our solutions to cater to a wide variety of enterprise needs.
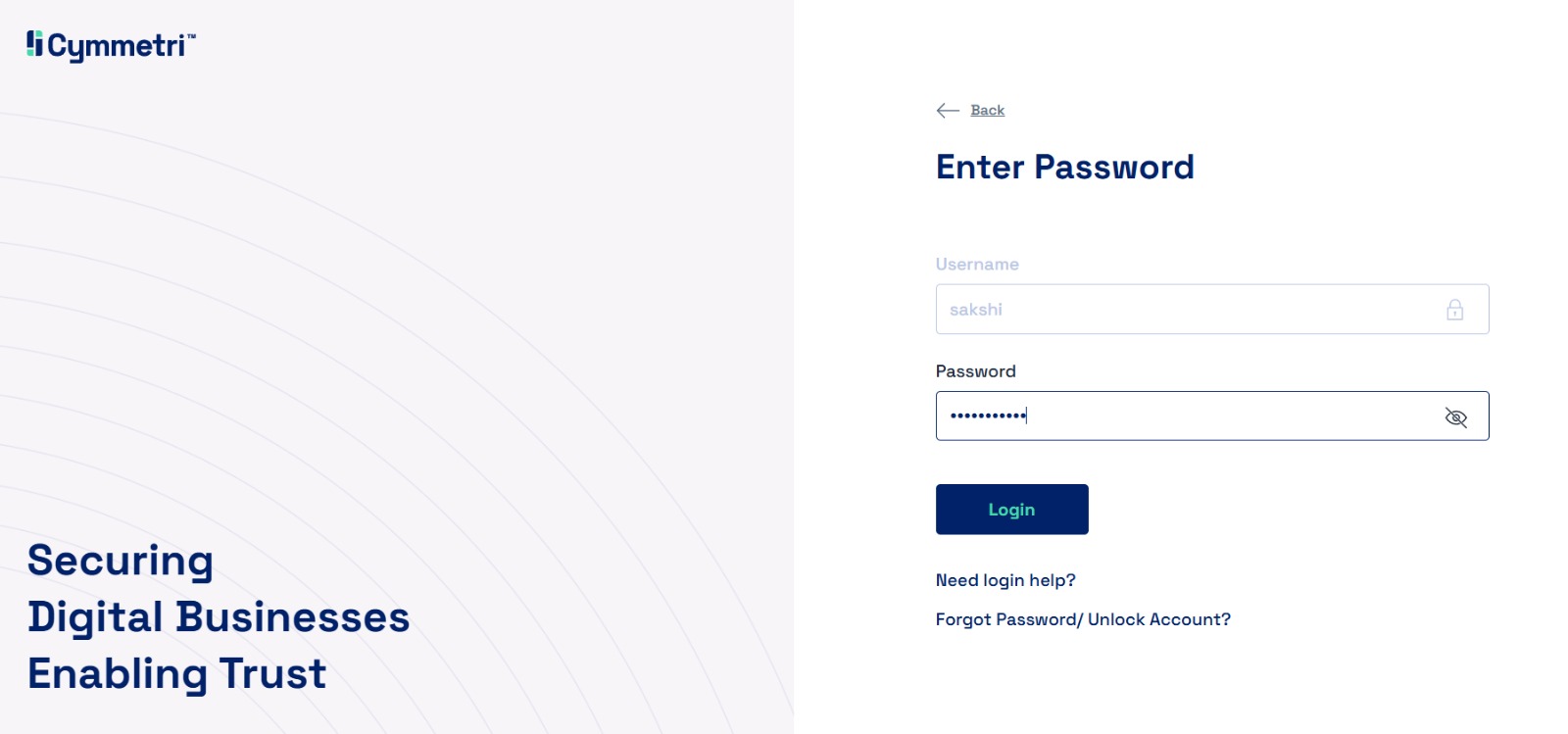
To access Cymmetri, users must use a web browser, such as Google Chrome or Safari, and enter the appropriate address in the address bar as shown below:
URL: https://<companyname>.cymmetri.com/login
Example: https://helpdocs.cymmetri.com/login
Once the address is entered, it opens a page as shown below, where the users may enter their username and password to access Cymmetri.

Version: cloud_3.1.0 product release
Date: 02 May 2024
Add Welcome Guide when no nodes added
Amaya Operations cards messages updated
Tooltip DX enhancements
Add confirmation dialogue when request method is missing
File Upload Validations based on filename length and file size
File validation applied on User Bulk Imports, Group Assignments, Application Assignments, Role Imports, Upload metadata SSO.
Branding Image upload applied image size validation and image name length valdation.
Validation also applied on self service User avatar upload, application icon upload.
Cymmetri Verify App issuer format is changed now so there wont be duplicate record creation from now onwards, earlier we did not take into account of the environment but now we are considering that as well
Deprovision Via scheduler when threshold value is set:- Past date user is also getting deprovisioned when rule is applied on status
Application-Role-One role mandatory, validation should be present at least one active
Node name without spaces overlap
Amaya- Not able to drag down node which is at the top most corner
Manager notification: receiving user name required manager name
Workflow initiated for form but form is getting updated without workflow approval.
In application setting if show to user flag off then also application show in recent application.
Unable to identify application properties data type where value is empty
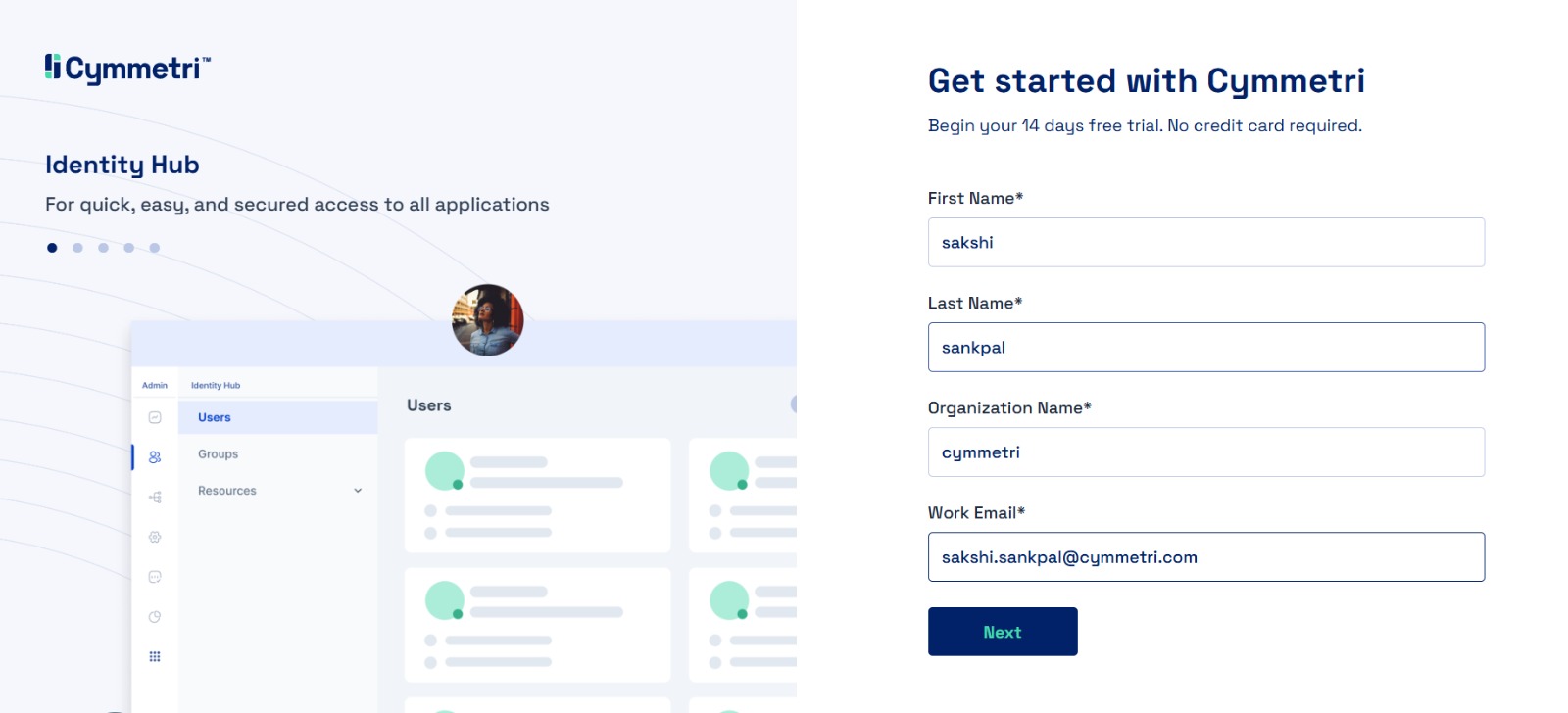
Start by clicking on the link register.cymmetri.io to start the registration of your tenant on the Cymmetri Cloud 2.0, and enter your personal details with your work email. Click on Next.
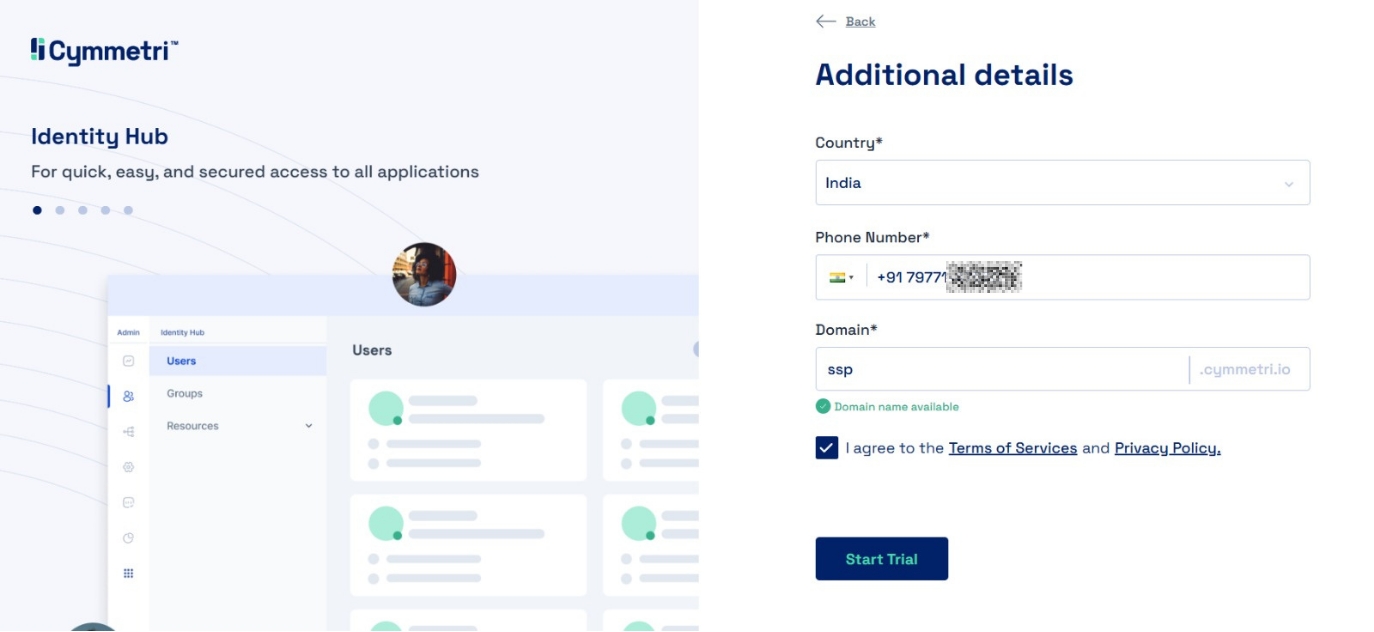
Enter your country and phone number (mandatory to receive OTP), and enter a domain name for your tenant. In case the domain available message is not shown, choose a different domain name. Click on the Start Trial button.
You will receive an OTP on your mobile number from the previous step. Enter the OTP here and wait for a few seconds for your tenant to be created.
You will be redirected to your domain to create the first Organization Admin user. Ensure that your password matches the password policy.
You will receive a message showing that your tenant has been created.
Click on the Login button to proceed with the onboarding process
Enter your username and press Next
Enter your password and proceed with the setup of your tenant by clicking on the Login button.
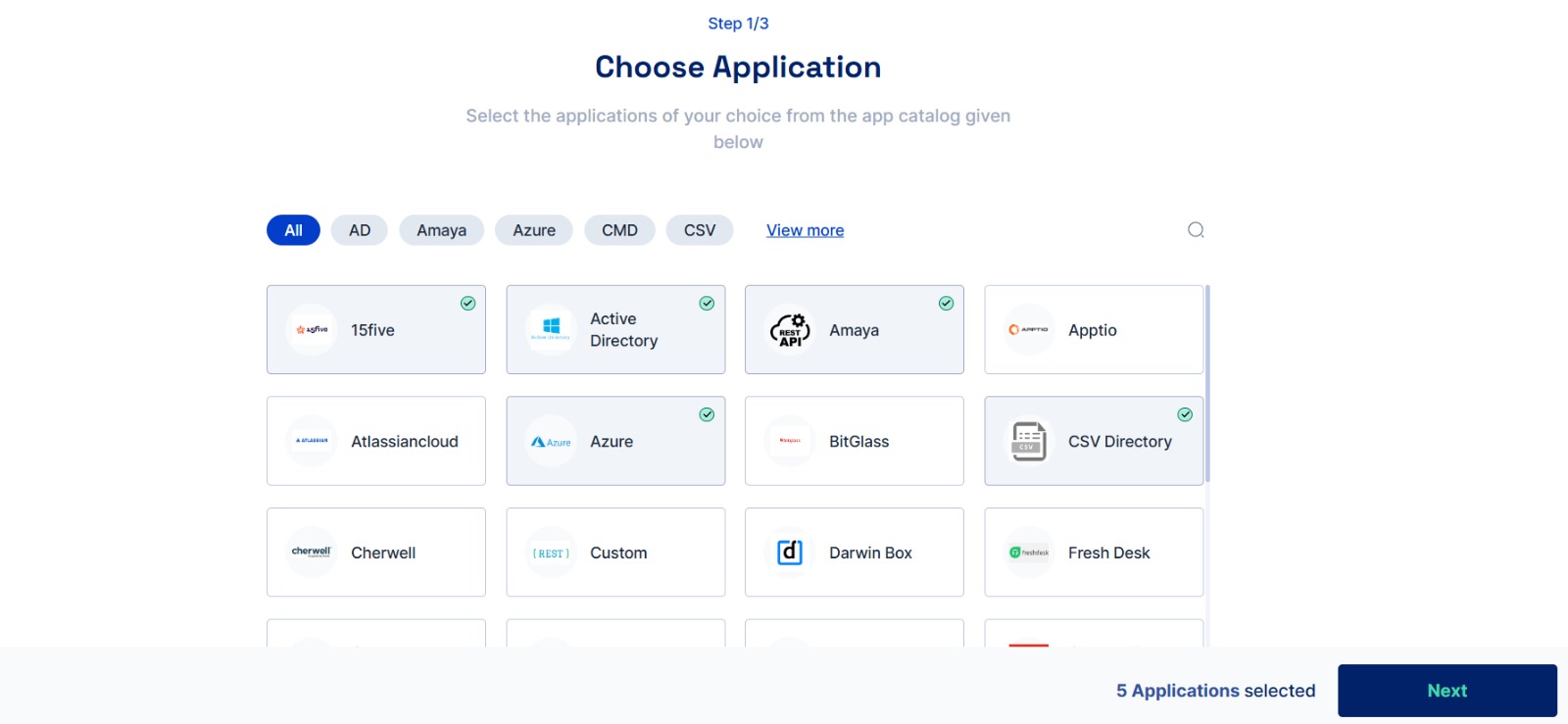
Choose applications from the application catalogue, and click on the application icon for all the applications you wish to add. Then click on the Next button.
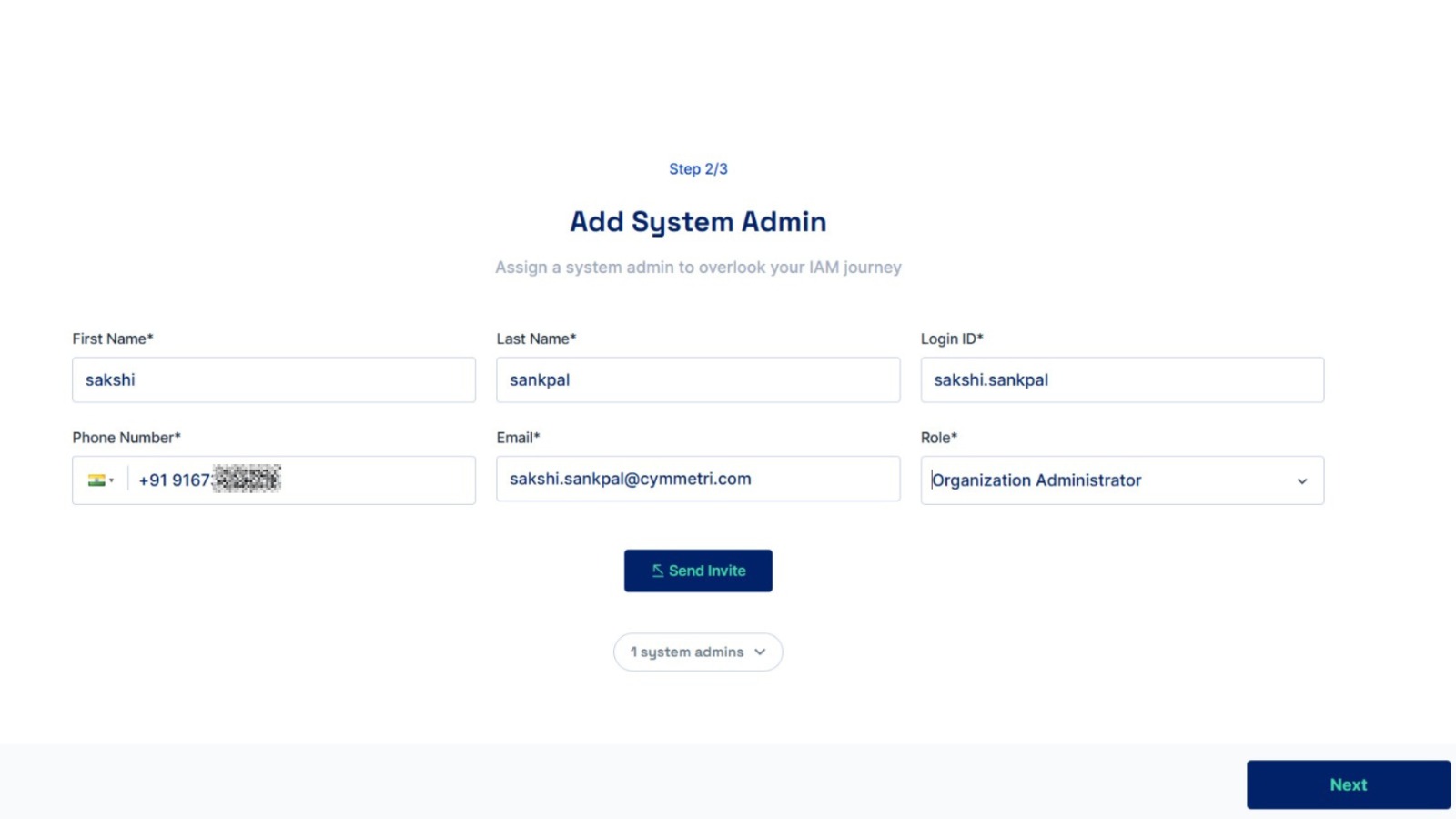
Enter details to create a second administrator account. Click on the Send Invite button to create an administrator. Click on the Next button to proceed.
(Optional) Add users if you wish to. Then click on Finish.
You will be redirected to the Dashboard to proceed with the system.
Next Steps:
The Cymmetri dashboard acts as a central command center for identity management, providing a visual summary of key metrics and quick access to administrative functions. Upon logging in, administrators see a comprehensive overview of user activity, system health, and important shortcuts.
The main dashboard section provides critical insights into daily user activity and authentication health:
Users Activity: The total count of successful user logins on the current day.
The admin can delete the user from the users tab in the identity hub section.
After the user is deleted, they are moved to the Suspended Users tab.
In the section for suspended users, the administrator has two options: they can choose to
Resume User - Which relocates the user back to the all users section OR
This section stores and manages user accounts that have been archived or deactivated. These accounts are usually no longer active but are retained for historical or compliance purposes.
You can see the other condition when the users are moved to the archived users
This page provides Cymmetri administrators with the capability to monitor and manage all user sessions across the entire platform.
This functionality allows administrators to gain insights into ongoing user activities, view active sessions, and, if necessary, terminate or manage these sessions for security, compliance, or administrative purposes.
The admin can terminate all the user sessions at once or select them individually. The page also has a search option for the admin to search the desired user session.
Administrator needs to go to Authentication->Service Provider
Then click on +Add New button, On the screen that appears most of the data is prefilled. Yet if the administrator needs the data can be changed as per need. Once done click on Save. The prepopulated data appears as below:
The Global Auth Policy allows to configure various user login parameters as shown below:
Auth Failed Count: The Auth Failed Count parameter signifies after how many failed login attempts will the user account be locked.
Unlock after Minutes: The Unlock after Minutes parameter signifies after how many minutes will a locked account be automatically unlocked.
Token Expiry Minutes: The Token Expiry Minutes parameter signifies after how many minutes will the session token expire.
Refresh Token Expiry Minutes: The Refresh Token Expiry Minutes parameter signifies after how many minutes will the refresh token expire.
Campaign - Campaign action reminder email time calculation wrong
Campaign- Campaign is getting aborted and summary is showing blank when campaign for local group is executed.
Custom attribute - When custom attribute filter is applied in users, showing no users found
Workflow- Preference config box is not visible while deprovisioning application
Self service app: While setting up secret question authentication in mobile app, user need to click twice on question field.
User activity Ascending Descending not working
Amaya Connector Recon- Showing duplicate role remarks, but in duplicate field showing 0 records
Identity Hub- Groups- After editing groups when on application / activity page user is redirected to users page by default
My workspace> Create new tags- showing older suggestion as soon as clicked on new tag field
AD Application - View attribute is empty
Tenant registration | Pressing tab key glitches UI
Missing error code mapping
Grade Workflow- When workflow preference config is set to visible, and workflow is applied for user creation, then popup box is showing user list but in pending showing unknown instead of user list
Amaya- When the back button is clicked, a save/discard popup box will appear. However, clicking anywhere on the page directly navigates the user away from the operation page.
Amaya- Save/Discard popup box should not be shown when user is trying to go back without saving any changes
Mobile app- Secret question- Field is showing required even when data is present in field
Cymmetri Verify app- Password recovery should be provided for Exported TOTP user files in case user forgets the password
login via Authenticator-identity provider is inactive then also user able to login.
syslog-configuration- UDP test, for invalid IP also giving success.
Unable to have TOTP account for same username on different environments
Reconciliation Enhancement a. Reconciliation Job Notifications b. Reconciliation Job Dashboard c. Handling of Partial Job Failures d. Reconciliation Filters
Email Configuration Update a) Mail Username and Password fields no longer require validation, allowing them to be empty. This is because some email servers do not require authentication. b) Other fields, such as Mail Port, Mail Host, and Mail Sender, still require validation to ensure proper email functionality
Form logic-When TAT is executed then in the detail show the message "Form Logic Workflow Rejected by system"
Assign Application- The application page not getting refreshed automatically after deleting/assigning applications.
Amaya Policy Mapping- The search button should be present.
Amaya || Validation prevents the usage of variables in the URL
FormLogic || Step 2 of form || Form config JSON should be mandatory
Amaya- The present header key disappeared when saving the value
Quick setup policy mapping- When any fields are not filled and an error is shown, the user should be taken to the error field
Amaya>Policy Mapping- Showing repeated validation message on UI when clicking on the reset button
Amaya- When the JSON body type is changed from raw to any other format, the previous type is cleared, but the response is not being updated accordingly
Amaya- After 3-4 attempts of clicking the validate/save button, the validation message is no longer being displayed.
Form logic-form detail-Need to provide rule link.
Staging Users - Version History - Change the text "Update Version" to "Updated Version"
Form logic-When TAT is executed then in the detail show the message "Form Logic Workflow Rejected by system"
Onboarding- The page is being skipped when the "Create User" popup box is clicked outside of it.
Audit log- UI layout is getting distorted for long role name
Application role- The Role page layout is getting distorted when a role with a long name is created
Application Role- When a role with a long name, including spaces, is created, the UI (specifically the Cancel and Save buttons) is affected while unassigning the role from a user account.
Application Role- UI is getting impacted.
Selfservice mobile app-inbox-User detail not showing.
CSV Bulk Import- When a bulk file is imported via CSV, attribute fields take time to load
Amaya Policy Mapping- The search button should be present.
Workflow || Additional Form Info || Readonly text-based form submissions
Policy map- Empty values are getting saved in the policy mapping
Amaya- When the JSON body type is changed from raw to any other format, the previous type is cleared, but the response is not being updated accordingly
UI new user walkthrough- Sentence correction needed
UI new user walkthrough- Description should be changed
Quick setup policy mapping- When any fields are not filled and an error is shown, the user should be taken to the error field
Amaya- After 3-4 attempts of clicking the validate/save button, the validation message is no longer being displayed.
Form logic-Form table-sorting not working
Form logic-Pre and post hook should be nonmandatory
Form logic-User submissions-Provide date filter
Form logic-on all screen search only works for the exact case, expected should work for matching cases.
Partner portal-add user-country list not loading.
CSV Bulk Import- When a bulk file is imported via CSV, attribute fields are taking time to load.
Form details UI is different in Pending and Completed Workflow than showing in the selfservice inbox section.
Form logic-Selfservice app-My Requests-form detail not showing
Skip Password Expiry- Session expires when the refresh button is clicked having skip password expiry enabled
FormLogic || Unable to save rule after changing condition
Manager notification: receiving user name required manager name
In the application setting if to user flag is off then the also application shows in the recent application.
Unable to identify application properties data type where value is empty
Amaya || Create user operation fails due to an invalid password
Reports- Records are displayed after 11min approximately
Deprovision Rule executed via Scheduler - Workflow is not getting initiated for the set of users based on status/end date
Workflow List - Getting error " Contact system administrator" on technova tenant
FormLogic || Step 2 of form || Form config JSON should be mandatory
Recon - Abort sync state - System is getting auto abort and failure log showing nothing and
Recon Dashboard History> Search field- A Placeholder should be added specifying search is applicable for only the application name, also No data found should be shown and pagination should get clear when the page is empty
Recon Failure sync status - Showing "Reconciliation In Progress" in fail status
Application Recon History- Slider should be added at the bottom
Recon Dashboard history- Users/groups are getting created in Cymmetri even when the process is aborted from the dashboard
API Client Refers to API Extension.
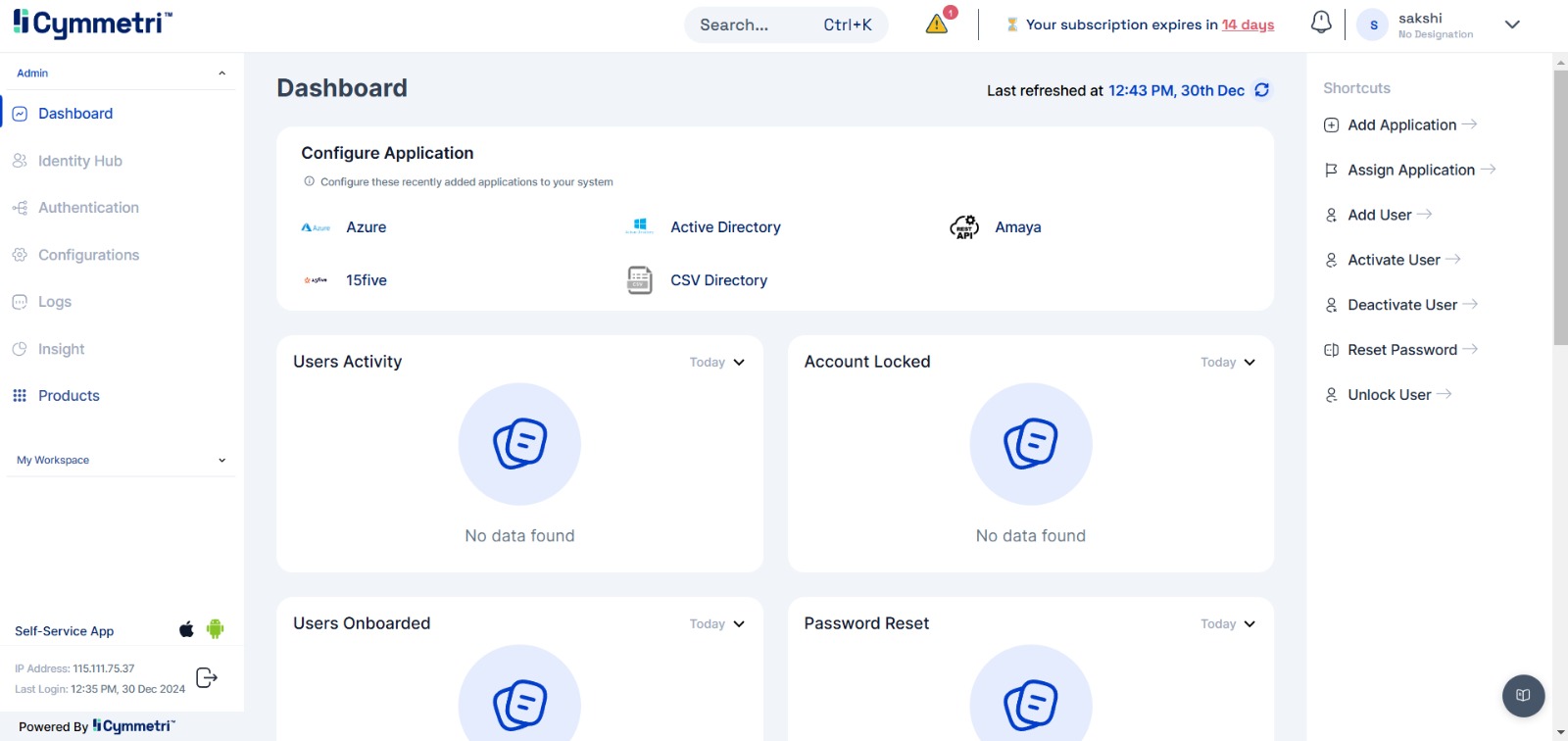
Accounts Locked: The number of user accounts that have been locked on the current day, often due to failed login attempts.
Users Onboarded: A count of all new users who have been provisioned in the system on the current day.
Password Reset: The total number of password reset activities that have occurred on the current day.
Authentication Stats: A breakdown of successful and failed login attempts over a specified period, helping to monitor security events.
App Identity: Displays the status of application reconciliation, specifically related to user identities.
Shortcut to Configure Recently Added Application: A direct link to configure newly onboarded applications by defining roles, provisioning, reconciliation, and Single Sign-On (SSO) settings.
The dashboard also displays high-level system KPIs, providing a snapshot of the identity environment's scale and configuration.
Application: The total number of applications integrated into Cymmetri.
Active Users: The total number of users with active accounts in the system.
Total Users: The overall count of all users who have been onboarded into Cymmetri.
Roles: The total number of application-specific roles that have been created.
Workflows: The total number of approval workflows configured in the system.
Password Policy: The total number of distinct password policies created for user authentication.
Rules: The total number of business rules created for provisioning, Multi-Factor Authentication (MFA), and approval workflows.
Users Unlogged: The number of users who have been provisioned but have never logged in to Cymmetri.
Located on the right side of the dashboard, the Shortcuts section offers quick access to common administrative tasks, streamlining routine operations.
Add User: Directs you to the user creation page to add new users to the system.
Activate User: Displays a list of inactive users, allowing you to quickly reactivate an account.
Deactivate User: Displays a list of active users, allowing you to deactivate an account and revoke access.
Reset Password: Navigates to the password reset function for a selected user.
Unlock User: Provides a direct way to unlock a user account that has been locked due to failed login attempts or other restrictions.
Add Application: A direct link to the application integration wizard.
Assign Application: Simplifies the process of assigning an existing application to an individual user or a group.
The service provider is created at this step, download the metadata(xml file) of the same.
Cymmetri allows users to have multiple sessions simulatenously i.e. they can login simulatenously from various locations and keep all the sessions alive. It also provides control to the user to revoke any specific or all the sessions

Version: cloud_4.0 product release
Date: 10 October 2025
Upgraded Node.js version to v20.16.0 for frontend build generation.
Migrated the backend framework to Spring Boot v3.4.4 and upgraded multiple dependent libraries.
Supports multiple role assignments if the application supports it.
Conditional Node: Expression builder support using forwarded data variables.
Transformational Node: Modify or add new attributes (primarily used in sync operations).
API Node:
Create/Update/Delete/Role Assign/Unassign operations.
New templates added in AMAYA for:
Zoho Expenses
Zoho Books
Zoho CRM
Zoho Desk
12-hour frequency added for MFA enforcement on applications.
Based on a configuration property, SSO and PAM can now be enabled/disabled independently for flexible access control.
Enhanced UI with conflict details on Teams & Inbox pages.
Bug fix for handling multiple conflicting rules under the same SoD policy.
Preventive approach for checking the potential violation of the user to stop violations from occurring.
Users can now view reconciliation summaries directly from the table view.
Skip updates if the application is not assigned.
Skip user update if already linked; remarks added to history.
For both-exist update case: if application is not assigned then user update will not happen; remark “Application not present so skipping” added and marked as error.
For both-exist link case: validation added — if the application is already assigned, the user will be skipped and a remark added in the reconciliation history.
This release extends reconciliation capabilities to include both users and their associated roles.
Role Synchronization: Along with users, one or more roles (if present) can now be synced into Cymmetri. Supported sources include REST API applications, database applications, and Amaya.
Role Reconciliation Dashboard: A new dashboard provides visibility into roles, with options to keep or remove stale roles (roles not present in the source but existing in Cymmetri).
Final delete provisioning call triggered by default unless explicitly disabled.
Property-based toggle: cymmetri.suspend.to.archive.provision.triggered = false disables it.
Application and status logs are now captured under USER_CHANGE_STATUS for traceability.
Bulk actions introduced via the dashboard:
Lock/Unlock User
Activate/Deactivate User
Delete User
Assign Local Group
New hook: Application Post Update After Commit — provides enhanced support for executing actions after an application update is finally committed in Cymmetri.
Support for JMS with Redis Streams is provided now.
Enhanced logic for unique Task ID generation.
Task ID format can now be configured (length, characters).
New notification templates added for application assign / un-assign / update, post-workflow emails:
Target User Notification (the user for whom application event is triggered)
Annotations enable dynamic approver configuration in access reviews and workflows. They can be assigned as reviewers or approvers for both Application and Group Reviews. Supported combinations include:
User only
User + Application
User + Application + Role
User + Group
Approvers can be individual users or groups.
Introduced the Group Review capability in access reviews. Admins can now initiate reviews based on:
All Groups
Specific multiple Groups
Specific multiple Applications
Support for Exclusion Access Types has been introduced in Application Access Review Campaigns, allowing more granular control over which accesses are excluded from reviews. The following types are now supported:
On Create by Provision Rule
On Update by Provision Rule
Exception Applications
Global Applications
The Data Pipeline enables merging and processing of data from multiple sources for views, such as:
MongoDB to ClickHouse
ClickHouse to ClickHouse
The processed data is stored in ClickHouse, and can be leveraged in hooks, APIs, and for reporting.
Cymmetri's Policy Simulator enables rule-based enforcement of access and compliance policies by evaluating "Should" and "Should NOT" scenarios. It identifies access gaps or violations (e.g., missing MFA or conflicting roles) and allows launching targeted review campaigns based on these insights.
Cymmetri now supports CAPTCHA validation using hCaptcha and Traditional CAPTCHA, enhancing protection against automated and bot-based attacks.
The Ticker feature allows administrators to broadcast time-bound text-based updates, announcements, or alerts directly within Cymmetri. Messages can be broadcasted to specific users before and after login based on rules.
Cymmetri now supports configurable Self Registration, allowing users to securely register themselves based on defined parameters and policies.
Admins can configure registration fields and hook code for creating and updating sub users (Team Members).
New self-registered users can set their login passwords using the Activation link support.
Admins or Managers can send a reset password link to registered users so they can set their login passwords.
Cymmetri’s Role Management enhancements improve handling of roles at an individual level, including:
Role-wise Status Management (e.g., Success, Fail) for better visibility and traceability of role lifecycle events.
Single Role Retry Mechanism.
Time-based Role Management with Status Tracking.
Old vs. New Role List Management.
The 360 Degree Reconciliation feature allows pulling user and role information from target applications connected to Cymmetri, enabling comparison of users and their entitlements across applications, the source of truth, and the Cymmetri identity store. Use cases include:
Identities present in Source application but not in Identity Store.
Identities present in Source but not in Target application.
Similar reports for entitlements across applications.
Admin can provide configuration, registration fields, password reset activation link, and hook code for creating and updating sub users (Team Members).
Admin can configure the Manager Application setting in the Assign Application setting to restrict the Manager to assign and the user to request only applications that are assigned to the manager.
The Banner feature allows administrators to broadcast time-bound image-based updates, announcements, or alerts directly within Cymmetri. Banners can display scrolling images or carousels and can link to an external page via a valid URL. They can be broadcasted to specific users before and after login based on rules.
Enhancements provide more control and flexibility over Cymmetri data:
Custom Reports (Dashlets): End users can create reports with various dimensions and measures.
Export & Share: Download reports as CSV/PDF or send via email.
Custom Dashboards: Combine multiple reports into personalized dashboards for a complete view of KPIs and metrics.
The Cymmetri Help Page serves as a vital resource, offering users a comprehensive documentation hub that breaks down all the features and provides step-by-step configurations for various functionalities.
To access this valuable documentation, you can visit https://help.cymmetri.io directly. Alternatively, you can simply click on the help icon located at the bottom left of your Cymmetri tenant screens.
Comprehensive Feature Explanation: The Cymmetri Help Page covers all the features of the platform straightforwardly. Whether you are a beginner or an experienced user, you can find detailed explanations of each feature, ensuring you have a clear understanding of its purpose and functionality.
Step-by-Step Configurations: One of the highlights of the Help Page is its provision of step-by-step configurations for various features. This means you can follow a simple, structured guide to set up and customize different aspects of Cymmetri according to your specific needs.
User-Friendly Language: The documentation is crafted in a manner that balances technical precision with user-friendly language. You won't find unnecessary jargon, making it accessible for users with varying levels of technical expertise.
Cymmetri has integrated advanced CAPTCHA validation capabilities to bolster security against automated threats and bot-based attacks. The platform now supports two distinct methods, providing administrators with a flexible approach to securing user interactions.
hCaptcha: This method is a privacy-focused and widely adopted alternative to traditional CAPTCHA. It requires users to perform a simple task (e.g., identifying objects in an image) to prove they are human, effectively blocking bots while maintaining user privacy.
Traditional CAPTCHA: This classic method uses distorted text or numbers that users must correctly enter. While this method is effective, it can sometimes be more challenging for users to solve.
These integrations enable Cymmetri to enhance its security posture by providing a robust defense layer, ensuring that user registration and login processes are protected from malicious automated activity.
To enable and configure CAPTCHA, administrators must navigate to the Configuration section and select Captcha Configuration.
From this menu, the administrator has two options:
hCaptcha Type: Selecting this option enables hCaptcha validation, which utilizes simple, interactive tasks for user verification.
Traditional CAPTCHA: Choosing this option will implement the classic method of using distorted text.
The administrator can then save the configuration.
Below is an example of what the Traditional CAPTCHA looks like to an end-user.
Global Search is a powerful, word-based search feature that empowers users to instantly navigate across various pages in Cymmetri by simply typing in relevant keywords. This functionality streamlines the process of locating specific information, making it significantly easier to access any content within Cymmetri with just a few keystrokes. By incorporating Global Search in Cymmetri, the time spent browsing through menus or sifting through irrelevant data is minimized, directly enhancing productivity and user experience.
The Global Search feature is available in the top bar, which makes it available on all pages as shown below:
For using the Global Search, the user needs to click on the search box. When clicked, it opens a search dialog box.
Note: The search dialog box can also be opened using Ctrl+K (in Windows) or Command+K (in Mac)
Upon entering a term, you'll receive precise matches or helpful suggestions. Simply browse the list and select the desired page to view it, clicking anywhere outside the search modal instantly closes it, allowing you to seamlessly return to your previous page.
The page also provides certain shortcuts which can be used for ease:
Esc: Close the search Dialog box
↓↑: for Navigate up and down the search list
Enter: For opening the selected page
The Search box appears below in non-administrative logins:
Administrator tasks pertaining to bulk users may be eased by creating groups of users.
Access the group configuration page by clicking Identity Hub > Groups on the left-hand side.
Click on the “+Add New” button to start creating a new group
Group Name: Indicates the name of the group.
Group Type: For environments not using Active Directory, either Local or Remote Group may be chosen. In case Active Directory is being used for synchronization in the tenant, the appropriate type according to the group policy object must be chosen.
Parent Group: If a parent group is chosen, all the policies and rules applicable to the parent group will be assigned to this new group, in addition to the policies and rules specifically applied to this new group.
Group Description: Optionally, a description may be provided to the group.
Once all the details have been entered, click on the Save button, and a new group is created.
Delegation as a process in the Cymmetri platform refers to the ability of any end-user to delegate their responsibilities to any other end-user on the platform. As such, delegation provides the ability to the delegatee to perform various actions, including Single Sign On, Application Requests, managing workflows by providing approvals, and performing Cymmetri administrative actions (if the delegator has the required permissions on the platform), among other actions. However, the login flow for the delegatee stays the same.
Access the Delegation administration panel, by clicking on the Configuration left-hand side menu item and then clicking on the Delegations menu item.
For any user to be able to delegate their work to other users, the user should be added to the delegation users list; To Add Users to the delegation list so that they can delegate their activities, click on the Assign New button and select one or more users to add to this list.
User and Assignee Consent
The User and Assignee Consent sections allow organizations to align task delegation practices with their unique policies. This customizable feature empowers administrators to define specific consent texts, ensuring that both the user delegating a task and the delegatee receiving it acknowledge and agree to these terms.
The user consent will be displayed whenever the delegator (user) goes to their settings in their Workspace and assigns a delegation to an end-user (delegatee). This consent will be recorded in the Cymmetri backend for audit logging purposes.
Similarly, the assignee consent will be recorded when the end-user (delegatee/assignee) logs into the account for their manager (delegator/user).
Here's how it works:
Administrator Configuration: Administrators can craft consent texts tailored to their organization's requirements. These texts typically outline the responsibilities, expectations, and any legal or compliance aspects associated with task delegation.
User Perspective: When a user decides to delegate a task to someone else, they will be presented with the customized consent text. The user must carefully review and accept the terms before proceeding with the delegation process. This step ensures that the user is aware of the implications of task delegation and is willing to proceed.
Assignee Perspective: On the other side, the delegatee who is about to receive the delegated task will also be presented with relevant consent text. They must thoroughly read and accept these terms before taking on the responsibility. This step helps establish clarity and accountability for the delegatee.
Upon receiving a delegation request, the user is notified via email and within the platform.
To view the delegated task the delegatee can go to Settings->Delegation to Me to see details about the delegated tasks and the user who has assigned the task
The user needs to click on the Accept button to accept the delegation. On clicking the Accept button an Assignee(delegatee) Consent is shown which the users need to read and confirm. The Consent also shows details of the delegator and the duration of the delegation.
Once the user accepts the delegation the user sees a login button, to login into cymmetri as the delegator
On clicking the login button the delegatee is redirected to the delegator's My Workspace Dashboard.
The delegatee can access and perform actions on all the applications assigned to them and if any application is excluded during delegation they are not visible to the delegatee.
Self-registration empowers users with greater control over their accounts, reducing the administrative burden on IT and security teams. These enhancements focus on a secure and streamlined self-registration process and improved password management.
Configurable Self-Registration: Cymmetri now supports self-registration, allowing new users to create their accounts securely. This process is governed by pre-defined parameters and policies, ensuring that all new accounts meet your organization's security and compliance standards from the outset.
Activation and Password Management:
Activation Link: Once a new user self-registers, the system automatically sends them an activation link. This link allows them to set their own secure password, finalizing their account setup.
Password Reset Link: For existing users, administrators, or managers can now easily send a password reset link. This empowers users to securely reset their login credentials independently, eliminating the need for manual password changes by support staff.
These updates automate key user management tasks, providing a more efficient and secure experience for both users and administrators.
To enable and manage these features, administrators must perform the following configuration steps:
Access Configuration Settings: Navigate to Configuration → Self Registration Config within the Cymmetri interface.
Choose Password Generation Method: The administrator has two primary options for password management:
Generate Activation Link: This option, as described above, sends a link to the user, allowing them to create their own password.
Generate Password: This alternative automatically generates a temporary password that the user must use to log in for the first time before being prompted to change it.
Add Custom Fields: For increased flexibility, the administrator can add new User Registration Fields by clicking + Add Registration Field, allowing for the collection of additional information relevant to the organization.
Cymmetri's Internal Identity Provider (IDP) is a powerful authentication solution that supports seamless integration with various Identity Providers (IDPs).
We will explore the configuration options for three types of IDPs:
Cymmetri,
Active Directory, and
LDAP.
The flexibility of the Cymmetri Internal IDP allows you to manage multiple IDPs of the same type, making it easy to adapt to diverse environments with different Active Directory/ LDAP instances. Cymmetri's Internal IDP aims to provide a centralized and adaptable authentication solution for your environment, supporting various IDP types.
To access Internal Identity Providers navigate to Authentication-> Identity Provider->Internal IDP
To customize the applicability of different IDPs, administrators need to configure . These rules enable the configuration of various conditions. When these conditions are met, the corresponding authentication mechanism or IDP is used for user authentication.
To access Internal Identity Providers navigate to Authentication-> Identity Provider->Internal IDP.
Since Cymmetri is a default Internal IDP no configuration is needed for it. An administrator may still have an option to disable Cymmetri Authentication which can be done by editing the Cymmetri Authentication Internal IDP mechanism.
An administrator may also change the Display Name and/ or Description as shown in the screen above.
In Cymmetri, the Attribute Setting is a tool for user attribute management.
It provides administrators with granular control over attribute visibility during user creation or updation processes. This feature empowers administrators to enable or disable both predefined and custom attributes effortlessly.
When an attribute is disabled, that associated field doesn't appear anywhere in the user creation or updation pages, streamlining the user management experience.
Cymmetri can work with systems that handle user account provisioning manually, such as help desk or service request platforms. These systems typically rely on human intervention to create, modify, or deactivate user accounts, and Cymmetri can communicate or integrate with them to streamline these processes.
For example: If a company hires a new employee, the help desk team manually creates an account for the employee. Cymmetri connects with this help desk system to track or manage the account creation process.
Custom Attributes may be added for all user entities in your Cymmetri Platform. This allows organizations to add custom user attributes that are used across the applications in the organization.
For example, your organization has a custom attribute that captures and uses the local language of your employees and vendors to provide local services. This attribute may be stored in your Active Directory and may need to be synchronized to your organization’s other applications during the course of an employee or vendor’s employment.
Cymmetri platform allows the administrator to define custom attributes on a tenant-wide level.
Custom attributes can be used at various places, like when creating a user, as a filter when searching for users, and are visible in the other sections of user info
The Ticker feature is a powerful communication tool in the Cymmetri platform that allows administrators to broadcast real-time, time-sensitive, text-based messages to users. It's a key component for improving internal communication and enhancing security awareness.
This feature provides a robust channel for broadcasting important updates and alerts, including:
Urgent Announcements: Instantly communicate system-wide announcements, such as new policies or security reminders.
Maintenance Notifications: Inform users about scheduled system maintenance or downtime to minimize disruption.
The User Management interface in Cymmetri provides an intuitive and efficient way to manage users within Cymmetri. The interface is designed to support both list and card views, allowing administrators to easily navigate through user profiles according to their preferences. To access the User Management page, navigate through: Identity Hub -> User
The UserManagement Page provides various features that ease user management.
This feature allows administrators to perform multiple user management tasks simultaneously, streamlining the process of managing a large number of user accounts. The following actions can be performed in bulk, namely:
Lock User
Unlock User
Activate User
Users may be imported into the Cymmetri platform using the bulk Import Users feature.
Please Note: User import process follows the synchronization policies as defined .
For Importing Users in the Cymmetri platform administrator needs to click on Identity Hub > User menu and then click on the Bulk Import > Import Users button.
Active Directory (AD) is a robust Identity Provider (IDP) in enterprise environments. It authenticates and authorizes users, facilitating seamless access to resources. AD centralizes user management, streamlining security protocols and ensuring efficient user provisioning.
Active Directory can be utilized in Cymmetri as an Identity Provider (IDP), leveraging existing AD user accounts to access Cymmetri, as the platform supports the LDAP protocol.
For configuring AD as an Identity Provider, the primary service needed is the Adapter Service.
The Adapter Service or Auth Adapter Service is exposed as a rest service that runs on HTTPS and acts as an adapter to facilitate authentication using the LDAP protocol which is often employed for authentication purposes in various systems and every adapter service instance is called by the
Lightweight Directory Access Protocol (LDAP) serves as an important Identity Provider (IDP) in enterprise environments. It authenticates and authorizes users, facilitating seamless access to resources. LDAP is commonly used as a directory service for managing user identities and authentication information within an organization.
LDAP can be utilized in Cymmetri as an Identity Provider (IDP), leveraging existing user accounts to access Cymmetri, as the platform supports the LDAP protocol.
For configuring LDAP as an Identity Provider one of the primary services needed is the Adapter Service.
The Adapter Service or Auth Adapter Service is exposed as a rest service that runs on HTTPS acts as an adapter to facilitate authentication using the LDAP protocol which is often employed for authentication purposes in various systems and every adapter service instance is called by the
Cymmetri's External Identity Provider (IdP) feature allows you to authenticate user identities using different IdPs for various user types. This flexible configuration enables you to streamline access for both internal employees and external users, such as consultants, vendors, and their employees. In this documentation, we will guide you through the process of configuring an External IdP within Cymmetri's identity and access management system.
For internal employees, you can configure Cymmetri's Internal IdP mechanisms like Active Directory or LDAP. This allows seamless authentication for your organization's employees.
Whereas external users, such as consultants, vendors, and their employees, can be verified using popular External IdPs like Google, Azure, Salesforce, or any other supported IdP. This approach simplifies access for external parties while maintaining security and control.
Within Cymmetri, the authentication process is highly customizable through the definition of authentication rules. While the platform provides a default authentication rule, administrators have the ability to define custom authentication rules that align with the specific business needs and the variety of identity providers at their disposal.
For instance, let's consider a scenario where an organization has distinct user types, such as regular employees, contractors, and administrators. The administrators might require to authenticate employees with Active Directory as the identity provider and use Cymmetri's own authentication engine to verify the identity of vendors and contractors. With Cymmetri's flexibility, administrators can create authentication rules that cater to these varying requirements, ensuring a tailored and secure authentication experience based on user roles and organizational needs.
Admins can find authentication rules in Authentication tab in Cymmetri.
To create a new authentication rule, admin must simply click on the "Add New" button on the top right corner of the page.
The admin must fill in the following details
The "Import History" tab in Cymmetri provides a comprehensive record of all data imports, ensuring transparency and accountability in managing user and system information. This feature is designed to offer administrators insights into the history of data imports, facilitating effective tracking and auditing.
To check the import history in Cymmetri, go to the "Import History" tab within the Logs section. This area keeps track of all bulk import events, including imports for user and application assignments.
In this section, administrators can find a detailed history of import events, including:
File Name: The name of the file that was imported.
Understand how to add and manage your cloud and on-premise applications through your Cymmetri Identity platform deployment. Your Cymmetri Identity deployment allows you to manage your cloud-based applications and on-premise applications from a single administration console.
Understand how to add the applications used by your organization to be managed in your Cymmetri Identity platform deployment. Use the FAQ to learn how to add applications to be managed in the deployment.
For any user to be able to delegate their work to other users, the user should be added to the delegation users list; Check how to Add Users to the delegation list so that they can delegate their activities.
Following are the steps to delegate work to a delegatee:
The logged-in user needs to go to their Settings Page by clicking on the user's username on the top right
Once on the Settings Page user needs to click on the My Delegations menu
Cymmetri provides a robust suite of provisioning operations that enable seamless identity and access management across various applications. Below is a detailed overview of the provisioning operations supported by Cymmetri.
1. Test Operation
Purpose: The Test Operation is used to validate the connectivity and configuration settings between Cymmetri and the target application or directory service. This operation ensures that all necessary parameters, such as API endpoints, credentials, and schema mappings, are correctly configured.
Usage Scenario: Before initiating any provisioning tasks, administrators can use the Test Operation to verify that the integration between Cymmetri and the target system is functioning as expected.
Any application which supports SCIM v2.0 with fixed bearer is workable for application.
Following are configuration which is used for SCIM with fixed bearer
Base address - It is the endpoint of the target system which supports SCIM v2 API’s.
Integration SCIM v2.0 with Basic
Any application which supports SCIM v2.0 with basic authentication is workable for application.
Following are configuration which is used for SCIM with basic authenticator.
Integration REST Application
The REST connector is designed to manage provisioning by relying on RESTful service.
For REST applications we need target applications which support REST API’s.
Following configuration is tested for felicity application.
Resolved a bug which previously required calling an additional API to get UID.
Iterator Node: Transform and update object lists for synchronization.
Subflow: Sub-process specifically applicable within an Iterator context.
Run Flow: Allows debugging with mock data to validate flow logic.
Run Request: Preview flow execution with input variables, bypassing actual provisioning.
Multipod reconciliation support added.
Assign a deleted or inactive user as a manager to users (updation provided to allow creation and updation of users with inactive RM).
Assign Delete Manager to user
Requester Notification (the user who initiated application event for the target user)
Inbox - Bulk Action: Approvers can perform bulk actions on multiple access requests directly from their inbox (select several requests and approve or reject in one operation).
Pending Workflows – Unclaimed Workflows:
On the Pending Workflows page, workflows not yet claimed will display "UNCLAIMED" in the Current Assign column.
A note will be shown: “Pending claim with group, grade, userlist, or no approver found. See details for actual assignment.”
ROLE: Backward compatibility with all roles list; contains a list of successfully assigned roles and new roles that are to be assigned.
ALREADYASSIGN: Set of all the roles that are assigned to the user.
NEWROLE: Single role (new role which is being assigned).
Single Sign On is the process of ensuring that once an end user is logged onto the Cymmetri Identity platform, they should be able to seamlessly move their session to any of your applications managed by your Cymmetri Identity platform deployment. Use the FAQ to learn how to configure Single Sign On for your application.
Modern IAM deployments wishing to have progressive authentication may require some critical application integrations within your deployment to perform additional authentication while performing Single Sign On for the end user. Use the FAQ to learn how to configure the Application Sign On Policy.
Provisioning refers to the process of creating, modifying, and, in general, pushing the user account information stored on the Cymmetri Identity platform to the applications managed by your Cymmetri Identity platform deployment. Use the FAQ to learn how to configure User Account Provisioning.
Reconciliation of User accounts is a primary activity in Identity Governance, which allows for synchronisation between the user account information on the managed application and the Cymmetri Identity platform deployments, including provisioning, modifying, deprovisioning, and modifying user account attributes based on various synchronisation states. Use the FAQ to learn how to configure the Identity Reconciliation Process.
Once an application has been added to the Cymmetri Identity platform deployment and the necessary configurations for Single Sign On, Provisioning, and Reconciliation have been performed, an application may be assigned to an individual user or to a group of users. Use the FAQ to learn how to assign an application to a user.
Purpose: The Sync Operation synchronizes user and group data between Cymmetri and the connected applications. This operation ensures that the identity information in Cymmetri is in sync with the data in external systems.
Usage Scenario: The Sync Operation is typically scheduled to run at regular intervals or triggered manually to ensure that changes in the external system (e.g., new users, updated roles) are reflected in Cymmetri.
3. Search Operation
Purpose: The Search Operation allows administrators to query the target application or directory for specific users or groups. This operation is essential for identifying and managing specific identities in the external system.
Usage Scenario: Administrators can use the Search Operation to find users based on attributes such as username, email, or group membership, facilitating targeted management tasks like updates or deletions.
4. Create Operation
Purpose: The Create Operation is used to provision new user accounts or groups in the target application or directory based on the identity data maintained in Cymmetri.
Usage Scenario: When a new employee joins an organization, the Create Operation can be triggered to automatically provision their account in various applications, ensuring immediate access to necessary resources.
5. Update Operation
Purpose: The Update Operation allows administrators to modify existing user or group attributes in the target system. This operation is crucial for maintaining accurate and up-to-date identity information across systems.
Usage Scenario: If an employee's role changes, the Update Operation can be used to modify their access privileges or update their profile information in connected applications.
6. Delete Operation
Purpose: The Delete Operation is used to de-provision user accounts or groups from the target application or directory. This operation is essential for removing access when users leave the organization or no longer require certain resources.
Usage Scenario: Upon the termination of an employee, the Delete Operation can be triggered to remove their accounts from all connected applications, ensuring security and compliance.
7. Role Assign Operation
Purpose: The Role Assign Operation assigns specific roles to users in the target system, granting them access to particular resources or permissions.
Usage Scenario: When an employee is promoted to a managerial position, the Role Assign Operation can be used to grant them additional access rights aligned with their new responsibilities.
8. Role Unassign Operation
Purpose: The Role Unassign Operation removes previously assigned roles from users, revoking their access to certain resources or permissions.
Usage Scenario: If an employee is reassigned to a different department, the Role Unassign Operation can be utilized to revoke roles that are no longer relevant to their new position.



Configure Hooks and Registration Fields:
Pre-Hook and Post-Hook: The administrator must set up both pre-hook and post-hook configurations. These are custom scripts or actions that can be run before or after a new user account is created, allowing for custom validation or integration with other systems.
User Registration Fields: The administrator must define the fields that will be displayed to users during the self-registration process (e.g., First Name, Last Name, Email, Department).



To start configuring custom attributes, click on the Configurations menu on the left-hand side and then click on the Custom Attributes menu.
Click on the Add New button to start adding a custom attribute
Fields to be updated:
Name/ Key: refers to the label assigned to the custom attribute.
Description: allows you to provide additional details or notes about the custom attribute for reference and clarity.
Status: Allows activation of the custom attribute. Only if it is set to active is the attribute available to use in the User Object.
Note: A custom attribute, once created, can only be set to inactive; it cannot be deleted.
Tickers are highly configurable, offering two primary display options to give administrators full control over their communication strategy.
Before Login
This option is designed for broadcasting critical messages that every user must see before they can access the system. These tickers appear directly on the login page and are essential for communicating information like system-wide outages or mandatory security alerts.
To configure a "Before Login" ticker, administrators define the following parameters:
Name: A unique, descriptive name to easily identify the ticker.
Start Date & End Date: Specifies the time frame during which the ticker will be visible.
Show Tickers: Set to Before Login to ensure the message is displayed on the login page.
Status: The state of the ticker, either Active (visible) or Inactive (hidden).
Message: The specific text content to be displayed.
After Login
This option is used for displaying messages on the user's dashboard after they have successfully logged in. It's suitable for general announcements, policy updates, or news that isn't a hard requirement for system access.
The configuration parameters are the same as the "Before Login" option, with one crucial difference: Show Tickers is set to After Login.
A key advantage of the "After Login" option is its support for conditional logic. Administrators can add rules to display messages only to specific users or groups based on attributes like department or role. This ensures communication is highly targeted and relevant.
Search Functionality: Quickly find users with the integrated search feature, saving time and improving manageability.
Advanced Filtering: The granular filtering capability ensures that administrators can pinpoint users based on specific criteria, making user management tasks more streamlined. The list of users can be narrowed down using various filters, including:
Account Status
User Status
Users' Login Status
Location
Department
Designation
Usertype
Custom Attributes
For each user, the following information is prominently displayed:
Display Name: The full name of the user as it appears in the organization.
Email: The user's primary email address.
Mobile Number: Contact number of the user.
User Status Indicator: An intuitive green or red dot next to the display picture indicates whether a user is active or inactive, respectively.
A context menu associated with each user profile offers a suite of actions, enabling administrators to manage user accounts directly from the interface. Available actions include:
Reset Password: Securely reset a user's password.
Mark Inactive: Change a user's status to inactive.
Assign Group: Add the user to specific groups for access control and organizational purposes.
Assign Application: Allocate applications to the user as per their role and requirements.
Edit Info: Update user information such as email, mobile number, and other personal details.
Delete User: Remove the user from the system entirely.
Delete User
Lock User: This action disables a user's access to all services and applications without deleting their account. A locked user cannot log in until their account is unlocked.
Unlock User: This action restores a user's access to their account, allowing them to log in and access services.
Activate User: This action makes a user account active, allowing the user to access services. This is typically used for newly created accounts or accounts that were previously deactivated.
Deactivate User: This action temporarily suspends a user's account, preventing them from logging in or accessing any services. The account and its data are retained and can be reactivated later.
Delete User: This action permanently removes a user account and all associated data from the system. This action is irreversible.
This feature allows administrators to assign multiple users to a local group in a single operation. The process is a two-step workflow to ensure accuracy and prevent accidental changes.
Step 1: Review User Selection
The administrator selects a group of users to be assigned to a specific local group.
A review screen is presented, displaying a list of the selected users.
The administrator can add or remove users from this list before proceeding.
Step 2: Finalize Assignment
The administrator confirms the final list of users to be assigned to the group.
The system then performs the assignment action for all users on the finalized list.
A confirmation or action summary is typically displayed, showing the status of the bulk assignment.
Bulk Action Dashboard
A dedicated dashboard provides a summary of all recent bulk actions. This dashboard allows administrators to review:
The type of action performed (e.g., "Lock User," "Assign Local Group").
The total number of users affected by the action.
The status of the action (e.g., "Completed," "In Progress," "Failed").
A detailed log of each user's outcome, including any errors that may have occurred.
This dashboard provides a transparent overview of all bulk operations, ensuring accountability and easy troubleshooting.
Click on the “+Add New” button.
Enter the required information and scroll down to add further information.
Click on the Save button to move to the next configuration page, and copy the automatically generated password.
Optionally, a group can be assigned to the user.
And also, applications can be assigned to the user.
Once all the above steps are completed successfully, the user is created with the assigned groups and assigned applications.
The Edit User form will be displayed, where you can modify the user's information as needed.
After making the necessary changes, click Save to update the user's details.
Saving the changes may also trigger updates in target applications, depending on the configuration. This ensures that any modifications made are synchronized across all relevant systems.
Click on the Upload File button and select the file you wish to import
Once the file is selected ensure that the default parameters selected match your requirements else you may change these parameters as per your requirement and click on the Next button.
Match the Column names from the CSV file with the Cymmetri User Attributes using this File Info dialog box.
Scroll down and click on the Import button. Note: A "Skip user workflow" check box is available to skip execution of any user workflow configured for the creation of users, if not selected it may trigger user creation workflow, and the process of importing users may slow down due to the numerous approvals that the approver might have to do.
Once Imported results of successfully Imported Users, Duplicate Users, or any error that occurred during import can be seen in Logs > Import History page
The rest endpoints are called by cymmetri-cloud AuthenticationService to connect to On-Prem AD/Ldap or cloud AD/Ldap. The AdaptorService is used to test connections, authenticate, change, and reset the password of a user.
For configuring Active Directory as an internal IDP navigate to Authentication -> Identity Provider -> Internal IDP. Here you may either configure the already created AD Authentication instance or +Add New.
In either case, a screen opens where you need to provide the below-mentioned details.
Name: AD Authentication
IDP Type: Active Directory
Description: A general description of the IDP type
Status: Active
Adapter Service Domain: Location (IP) of the server on which the Adapter Service is deployed
Adapter Service Secret: The secret generated while installing/configuring of adapter service
Base DN: Active Directory root domain name
Search Scope: A search scope for locating users in Active Directory
Once all the details are entered Save the changes and Test the Connection using the Test Connection button.
For enabling Active Directory to be used as an IDP for a specific set of users an Authentication Rule needs to be configured. Here you can see the steps on how to configure Authentication Rules.
Once the rule is configured, whenever a user matches the rule conditions, their credentials are verified against those stored in the Active Directory. Upon successful verification, the user is granted access to log in to Cymmetri.
The rest endpoints are called by cymmetri-cloud AuthenticationService to connect to On-Prem AD/Ldap or cloud AD/Ldap. The AdaptorService is used to test connections, authenticate, change, and reset the password of a user.
For configuring Active Directory as an internal IDP navigate to Authentication -> Identity Provider -> Internal IDP. Here you may either configure the already created LDAP Authentication instance or +Add New
In either case, a screen opens where you need to provide the below-mentioned details
Name: LDAP Authentication
IDP Type: Open LDAP
Description: A general description of the IDP type
Status: Active
Adapter Service Domain: Location (IP) of the server on which the Adapter Service is deployed
Adapter Service Secret: The secret generated while installing/configuring of adapter service
Base DN: LDAP root domain name
Search Scope: A search scope for locating users in LDAP
Once all the details are entered Save the changes and Test the Connection using the Test Connection button.
For enabling Open LDAP to be used as an IDP for a specific set of users an Authentication Rule needs to be configured. Here you can see the steps on how to configure Authentication Rules.
Once the rule is configured, whenever a user matches the rule conditions, their credentials are verified against those stored in LDAP. Upon successful verification, the user is granted access to log in to Cymmetri.
To configure an External IdP in Cymmetri, the administrator needs to provide the following information:
Name: A descriptive name for the External IdP configuration.
IDP Type: The type or provider of the IdP (e.g., Google, Azure, Salesforce).
Entity ID: The unique identifier for the IdP entity.
SSO Service URL: The URL where Single Sign-On (SSO) requests should be sent.
Destination: The location where authentication responses should be directed.
Protocol Binding: The protocol used for communication with the IdP (e.g., HTTP Post, HTTP Redirect).
Name ID Policy and Value: This policy defines the format and content of the identifier that represents the authenticated user. For example:
Policy: email
Value: email
Certificate: The certificate used for secure communication between Cymmetri and the External IdP.
In the upcoming sections we will learn step-by-step implementation of the various External IDP mechanisms:
Google serves as a robust external Identity Provider (IDP) through its Identity Platform. Leveraging various authentication mechanisms, it facilitates secure user authentication for Cymmetri. This allows users to sign in with their Google credentials, ensuring a seamless and familiar login experience. Google's IDP mechanism is adopted for its reliability and user-friendly authentication processes, thus making it a preferred choice for integration into Cymmetri as an External IDP.
Azure AD serves as a robust external IDP, facilitating secure access into Cymmetri. Employing industry standards like OAuth 2.0 and SAML, it enables Single Sign-On (SSO) and multi-factor authentication. Azure AD seamlessly integrates with Cymmetri providing easy identity management and ensuring compliance with modern security standards.
Salesforce as an external Identity Provider (IDP) offers robust authentication and access control solutions. Utilizing industry-standard protocols like SAML and OAuth, Salesforce IDP ensures secure Single Sign-On (SSO) experiences.
Configuring External Identity Providers in Cymmetri gives you the flexibility to authenticate user identities using different IdPs tailored to specific user types. Whether it's for internal employees or external collaborators, Cymmetri's External IdP feature ensures secure and convenient access to your organization's resources.
The name of the rule
Identity provider radio button ( Enable for External IDP or Disable for Internal IDP)
Identity provider
Description of the rule
Active Radio Button
Conditions
The administrator has the capability to establish rules based on conditions like: Department, designation, User Type, country, and Login Pattern.
Subsequently, the administrator defines regular expressions for conditions, specifying whether they should be equal to, not equal to, and assigns corresponding values.
Cymmetri facilitates the creation of multiple conditions for an authentication rule and provides the option to group these conditions using AND or OR logic.
In the image presented above, an exemplar authentication rule is showcased. This rule is structured to authenticate a user in Cymmetri through Active Directory if two conditions are met: the user's department must be equal to "Compliance," and the user type should be "Employee."
Similarly If you wish to set the Identity provider for users having email address ending with "@cymmetri.com" then you may select condition as LoginPattern > Regular Expression and its value as (.)*(@cymmetri.com)+$; and save the details.
This demonstrates how authentication rules can be precisely configured to suit specific criteria and streamline the authentication process based on defined conditions.
Import Type: Specifies the type of import, such as user or application assignment import.
Created By: Shows who initiated or performed the import.
Created At: Indicates the timestamp of when the import occurred.
For a closer look at the import history, administrators can click on the eye icon next to a specific record. This detailed view provides insights into the imported record statuses, including:
Created Successfully in Cymmetri: Indicates records that were successfully created within the Cymmetri system during the import.
Duplicated in the System While Importing: Highlights instances where records already existed in the system, preventing duplication during the import process.
Error Occurrence During Import with Remarks: Flags any errors that occurred during the import, accompanied by remarks detailing the nature of the issue.
Note: My Delegations menu will appear only if the logged-in user is added to the delegation users list. Here is how to Add Users to the delegation list.
Toggle Status: Enable the Toggle Status to Active
Start Date: The date from which the user is delegated the work
End Date: The date up to which the access is delegated
Delegated To: The user (delegatee) to whom the work is delegated. This dropdown populates the list of all users to whom the task can be assigned
Excluded Applications: List of applications whose access is not provided to the delegatee
Once all the details are filled the user is expected to accept the consent to be able to configure the delegation. The consent looks something similar to as shown below:
Once confirmed the user needs to click on the I agree check box and save the delegation.
Once saved the delegatee can see and accept the delegation in their My Delegation Page under Settings.
Username - Username to authenticate SCIM API endpoint.
Password - Password to authenticate SCIM API endpoint.
Authentication type - It is Fixed Bearer compulsory.
Fixed Bearer Value - The value for fixed bearer.
Update method - Patch or Put method.
Accept - Http header which accepts (application/json etc).
Content Type - Http header which accepts (application/json etc).
Base address - It is the endpoint of the target system which supports SCIM v2 API’s.
Username - Username to authenticate SCIM API endpoint.
Password - Password to authenticate SCIM API endpoint.
Authentication type - It is Fixed Bearer compulsory.
Update method - Patch or Put method.
Accept - Http header which accepts (application/json etc).
Content Type - Http header which accepts (application/json etc).
We need REST API’s to integrate with cymmetri.
Following are the cymmetri configuration which need to configure in user configuration in cymmetri.
It is Basic REST configuration which need to configure in application.
We need to provide Groovy code to run create user, update user, delete user and also recon pull and push (for recon pull we need to add sync script and for recon push we need to add search script)
For sample script please validate following link
Note: Please Configure script step by step
Configure test script at initial step and then test configuration for provided script (If configure successfully then only go for step b).
Configure create script and test configuration (If successfully configured then only go for step c).
Configure update script and test configuration (If successfully configured then only go for step d).
Configure delete script and test configuration (If successfully configured then only go for step e).
Configure sync(pull) script and test configuration (If successfully configured then only go for step f).
Configure search(push) script and test configuration (If successfully configured then only go to the next step).


















Version: cloud_3.1.2 product release
Date: 13 June 2024
The workflow self-approval module was updated to support custom attributes (type: user type and Converter Type: String ) as condition parameters.
Teams config module updated to support custom attribute (type: user type and Converter Type: String ) as condition parameter.
On behalf module updated to support the custom attribute (type: user type and Converter Type: String ) as a condition parameter.
Auth Rule module updated to support custom attribute (type: user type and Converter Type: String ) as condition parameter.
Quick Setup - Setup applications using pre-defined operations
Import-Export App Configuration - Transfer configurations of applications smoothly between tenants, simplifying the setup for users by ensuring all configurations, including user configurations, server configurations, and policy maps, are accurately migrated.
Removal of Deprovision Rule Exclusion Applications Field: a) Manual Execute Deprovisioning b) Deprovisioning via Scheduler c) Update Threshold Delete Config d) Deprovision Rule Updation e) Backward Compatibility f) Suspend or Resume User g) Impact on UI
Access review reject process updated, on rejection workflow support added.
SAML Single Logout
The new screen will show loading on UI till tenant creation is completed once OTP is verified
Interchanged position of login ID and email on add/edit user for better UX.
Add support for the page number field for pagination in Amaya
360 Recon
Lotus Notes Connector
Application Policy Map (Active Directory) samAccountName is compulsory for Create only flag in User as well as Group (AD application new bundle - When SAMaccount name is set to false in Group policy map, members are not assigned in group when recon Pull is executed for both exist=Update).
Added Warning information and warning popups (Only UI changes no impact on backend functionality): a. Creation of user manually. b. Updating of user manually. c. Bulk upload CSV (creation of user) d. Manager assignment e. Policy map creation and updation f. Reconciliation Pull operation g. Reconciliation push operation h. Selfservice ➝ Teams: i. Creation of user ii. Updation of user
Removal of Email validation from the backend
The user info page crashed while the user edit fails
Import/Export of App Configuration
Amaya- Detailed description of failed/executed logs should be shown
AD application new bundle- The group link attribute in the db is empty, and users are not getting updated in the group
Manager notification: receiving user name required manager name
Unable to identify application properties data type where value is empty
Amaya || Create user operation fails due to an invalid password
In forgot password/password breach condition-asking disabled MFA factor also
The Banner Management feature allows you to display customizable messages or images to users. These banners can be configured to appear either on the login page (before a user authenticates) or within the user portal (after a user logs in). You can define a name, a start and end date, visibility options, and an active status toggle for each banner. This is useful for sharing announcements, reminders, or policy updates with specific audiences.
Prerequisites:
To configure a banner, ensure you have the following:
Image Files: You can upload up to five images. They must be in JPEG, PNG, or JPG format and have a maximum file size of 500 KB each.
Filenames: Each image filename can be up to 30 characters long.
Targeting Conditions: For banners shown After Login, you can set conditions using user attributes such as User Type (e.g., "Employee") or Department (e.g., "HR"). You can use AND/OR logic to create complex rules.
Step 1: Create a New Banner
Navigate to the Configurations section.
Click on Add Banner.
Step 2: Define Banner Details
Enter a descriptive Name for the banner.
Set the Start Date and End Date to control when the banner is active.
Step 3: Select Banner Visibility
Choose whether the banner should appear Before Login or After Login.
After Login Banner:
Upload: Click to upload an image file. You can use drag-and-drop or a manual upload.
URL: Enter a URL to redirect users to a specific page when they click the banner.
Conditions: Apply a set of conditions based on user attributes to ensure the banner is only displayed to a targeted group of users. Once configured, the banner will appear as a pop-up after a user logs in. Clicking the banner will redirect them to the specified URL. Users can close the banner by clicking the cross mark and confirming.
Before Login Banner:
Select the Before Login option and save the changes.
The banner will be displayed on the login page before any authentication occurs.
Clicking the banner will redirect to the specified URL. Users can dismiss the banner by clicking the cross mark.
Tenant branding in Cymmetri allows you to personalize and enhance the visual identity of your environment. With tenant branding, you can customize the appearance of your platform, including logos, color schemes, and even tailored messages, aligning it with your organization's branding guidelines.
This not only creates a cohesive and professional user experience but also reinforces your brand's presence throughout the Cymmetri environment. It's a powerful tool for organizations looking to maintain a consistent and recognizable image while utilizing Cymmetri's identity and management capabilities.
The Cymmetri platform allows a certain level of customization to your tenant from the administration panel. This includes the ability to modify the default Cymmetri branding scheme to your own Organization’s branding scheme.
Your Organization Name and Tagline
Your Organization Logo
Your Organization Branding Colors (Primary, Secondary, Accent Colors)
To access the branding menu, first click on the Configuration menu on the left-hand side and then proceed by clicking on the Branding menu item.
Start the configuration by entering your Organization Name and Tag Line
Proceed by adding a Welcome text and Welcome Tagline, and select whether the Cymmetri help icon should be visible to the user or not
The configuration will be applied in a few seconds to reflect your branding.
In Cymmetri, the administrator now has the option to select the "Reset to default theme" button, allowing them to revert to the original theme.
Notifications are triggered from the Cymmetri platform for various actions occurring on the platform either through direct action by the end-user or by the virtue of some backend action (such as running of a scheduler for a campaign). Cymmetri platform ships with default notification templates listed below-
Mandatory Notifications
Sign-up / Registration
OTP Notification
Access Code Manager Notification
Access Code User Notification
Optional Notifications
Workflow Notification
Reviewer Notification
Application Access Approval Request
Application Assignment
Please note: The above notifications are available out of the box. The system also allows custom notifications to be triggered for specific events using the Cymmetri Webhooks. The custom action trigger can call an existing Cymmetri notification template or a custom template can be included in the webhook code.
The default templates may be modified by the administrator using the following process:
Access the notification templates menu by clicking on the configuration menu on the left-hand side menu bar and then clicking on the Notification templates pop-up menu.
Click on the eye icon to preview the corresponding template
Values in <> anchor tags and ${} reflect macros.
Click on the pencil icon shown above the image to edit the template.
We may treat this template as an email and edit the subject of the email.
By default, the email notification will be sent to the corresponding affected end-user, but selecting the toggle option for “Send notification to Reporting Manager” will also copy the mail to the Reporting Manager of the affected end-user, allowing for offline follow-up for the notification.
In user lifecycle management, the transition of a user's status from Suspended to Archived initiates a critical de-provisioning sequence. This process is designed to ensure that all user entitlements are permanently revoked from target applications, a final action controlled by a configurable flag.
User Creation and Initial Status: The process begins with a user being created in the system, with their initial status set to Active.
Suspension Initiation: An administrator initiates the suspension of a user by selecting the "Delete User" option. This action changes the user's status to Suspended, thereby revoking their login privileges while retaining their account information.
Movement to Suspended List: The user's profile is then moved to the Suspended Users list, allowing administrators to differentiate between active and temporarily disabled accounts.
Log Verification: The administrator can verify this status change by reviewing the system logs. The logs will record the status transition from "ACTIVE" to "DELETE." This log entry also provides a clear record of the user's application status, indicating if any associated applications were also de-provisioned at this stage.
Forced Deletion: Should the administrator require immediate, permanent de-provisioning, the "FORCE DELETE" option can be used. This action bypasses the standard suspended state and triggers the final de-provisioning call immediately, ensuring that all entitlements are permanently removed.
Final Validation: To confirm the user's complete de-provisioning, the administrator can once again validate the status in the system logs. The logs will confirm the final deletion and provide a complete audit trail of the user's lifecycle, from creation to final de-provisioning.
Cymmetri’s 360-Degree Reconciliation feature provides a robust solution for ensuring data integrity and consistency across your organization’s identity landscape. This functionality involves pulling user and role information from various applications connected to the Cymmetri platform. This collected data is then compared against your organization's primary Source of Truth (e.g., HRMS) and the Cymmetri identity store.
Key Capabilities and Benefits
This feature provides a holistic, 360-degree view of user entitlements, allowing administrators to easily identify and rectify discrepancies. It facilitates several critical reporting and security scenarios, including:
Identity Discrepancy Reporting: The system can generate reports highlighting users who exist in the source application but are not present in the Cymmetri identity store or a target application. This helps identify onboarding failures or synchronization issues.
Entitlement Mismatch Analysis: It provides a comprehensive comparison of user entitlements (roles, permissions, etc.) across multiple applications. This allows for the easy identification of unauthorized access or provisioning errors, such as a user having a role in one application but not in another where it is required, or vice versa.
Enhanced Audit and Compliance: By providing a single, consolidated view of all user entitlements, the feature significantly streamlines audit processes. It ensures that user access aligns with established policies and helps maintain a secure posture by highlighting potential security risks.
Any application which supports SCIM v2.0 with bearer token is workable for application.
Following are configuration which is used for SCIM with bearer.
Base address - It is the endpoint of the target system which supports SCIM v2 API’s.
Username - Username to authenticate SCIM API endpoint.
Password - Password to authenticate SCIM API endpoint.
Security Token - It is a token which is used to authenticate.
Applications menu in the administration page displays the various options pertaining to the Application Management Process.
Applications menu can be accessed as mentioned below:
Identity Hub
Login as either an Organization Administrator, Domain Administrator, or Application Administrator.
Click on the Identity Hub icon on the left side bar.
Click on the Applications text on the slide out bar.
Applications supported by the Cymmetri platform fall majorly into three categories -
Pre-configured Applications These are the applications that have already been configured by the Cymmetri platform for provisioning on cloud or on-premises.
Custom Applications for Provisioning These are the applications that you wish to manage through Cymmetri and support the generic connectors that the Cymmetri platform provides.
Custom Applications for Single SignOn only When you need to add an application for the sole purpose of enabling Single Sign-On (SSO), Cymmetri offers the capability to add a custom application that can be configured for SSO using the supported mechanisms.
Once you have chosen the application to be added from the above categories, you are ready to add a new application.
1. Click on the “Add New” button on the top-right corner in the Applications page.
2. In the Add New Application screen, you may search for your desired application (e.g., Active Directory or some authorative source like Darwin Box or Oracle HCM), or your desired connector (e.g., REST) or choose the “Custom” application type from the available application catalogue.
And also support for other standard categories of applications as shown below:
3. Now click on the tile shown in the list below to open the right slide out menu for renaming application as shown below.
4. Add your custom label (if you wish) in the text box and click on the “Add Application” button.
Application has been successfully added to your listing now. You may click on the configure now button to start configuring the application.
Annotation provides a centralized mechanism to define and select dynamic approvers for workflows, application access reviews, and group access reviews, enabling dynamic approval routing, which makes it easy to configure and manage.
The Annotation feature, found under the Configurations tab, allows you to designate specific users as approvers for critical identity management operations. By configuring an Annotation and selecting it within a Workflow (say, user creation) or an Access Review Campaign (for application/groups), all associated approval requests are routed directly to the Annotation-defined approver(s). Annotations enable the administrator to easily change the actual user without changing the annotation, which makes it a one-point change that gets applied at all various places where the annotation is used as an approver. With the flexibility of applying to both the application and group, it makes it easy to reuse the annotation and increases its usability.
Note:
Annotation names must be lowercase and cannot contain any special characters.
Users once created in the Cymmetri platform can be assigned to a group. Assigning users to a group helps ease the administrative efforts to apply the same policies and assign applications to multiple users.
When assigning users to groups, various approaches can be used:
Adding User to Group (from the Group Page)
A password policy is a set of rules and requirements established by an organization or system to govern how users create and manage their passwords.
The purpose of a password policy is to enhance security by promoting the use of strong, unique passwords and minimizing the risk of unauthorized access.
In Cymmetri, only the admin can create a password policy bby navigating to the authentication section and then in password policy.
Upon landing the user can view a default Cymmetri password policy which cant be deleted or deactivated.
The Cymmetri platform provides a centralized view for monitoring and auditing all reconciliation activities under the Audit Logs menu. This functionality offers administrators both a high-level summary and detailed drill-down views of each reconciliation job.
The Reconciliation History table, accessible via Audit Logs → Reconciliation History, has been enhanced to display the key reconciliation summary metrics directly in the table view.
This enhancement allows administrators to quickly assess the health and outcome of each reconciliation run without navigating to a separate detail page. The at-a-glance summary typically includes:
Pending Records: Count of records awaiting processing.
Synced Records: Count of records successfully synchronized (created, updated, or deleted).
In Cymmetri the "Scheduler History" feature plays a crucial role in maintaining visibility and control over scheduled tasks and operations. This functionality is designed to offer administrators insights into the history of scheduled events, providing transparency, accountability, and efficient management of routine processes.
In the "Scheduler History" tab, accessible within the Logs section of Cymmetri, administrators can delve into the details of scheduled tasks, gaining insights into various aspects of the scheduler's operation. The information presented includes:
Event of the Scheduler: Specifies the type of scheduler event that took place.
Event of the Scheduler: Specifies the type of scheduler event that took place.
AD policy map- Spaces should be trimmed automatically if included while creating a policy attribute
Tenant creation not working
New tenant Registration- Showing subscription end for tenant which is not even registered completely
Secret question configuration- Admin user should be able to delete secret questions when not in use
Secret Question- When a question is already in use and the user trying to delete a question then it should not display a successful delete message.
Secret question- Displaying removal validation message when editing a question
User> Activity- Add a cross (x) button to clear the selection
Onbehalf Config - If the Description is kept blank, no error message is getting displayed on the screen while saving.
Team Config - If the Description is kept blank, no error message is getting displayed on the screen while saving.
On Behalf config- When the view button is clicked, the user is still able to check or uncheck the boxes.
Custom attribute- Even when a custom attribute is disabled from the configuration, it remains visible in the policy map selected dropdown menu
Users - View User- Custom attribute fields text UI is breaking
Custom Attribute- Require text change in success message to " Custom Attribute activated successfully"
Edit User - After deactivating the already assigned custom attribute, in edit user, the system is showing info XYZz" attribute is inactive for the active custom attribute also.
Identity Hub- When clicking on edit info from the user menu action, the user account edit page should open instead of the user display page.
CTRL+K: When any feature/module is already opened and the user presses the ctrl +k button from the keyboard then the search filter modal is opened at the back
Delegation - Delegator and Delegatee consent should not get updated if the user has already set some other consent.
Users> Group- Rename the label from 'Delete' to 'Unassign'.
Audit- Logs for deprovisioned users are getting repeated.
Custom Field- Policy Map- Date is not showing in the correct format
Mobile app- When clicking on the user name for the first time after killing the app, the keyboard is hidden
Custom Attribute-Provision- When a custom attribute with special characters is created and applied in a provision rule (for user creation), the provision rule fails to trigger after the user is created.
Global search (Ctrl+K) - even if characters are not matching still shows suggestions
User setting- An error message should be shown when any action is performed and when landing/refreshing the settings page
Cymmetri Selfservice App - Need to change the message showing in the popup screen while TOTP is getting authenticated.
Mozilla Browser specific- User getting stuck when password-less Webauthn is On
Application - SSO - While clicking on Preview assertion, getting the error "processing please wait"
Product menu getting hidden on workflow page: a. Menu action- Displaying an error message when a user already has one role assigned and tries to assign a menu action.
The user info page crashed while the user edit fails
Import/Export- Showing error message when importing the file into a new tenant (AD specific)
Custom Attribute-Provision- When a custom attribute with special characters is created and applied in a provision rule (for user creation), the provision rule fails to trigger after the user is created.
Quick setup- Data is not getting reset after closing the policy mapping popup box, but getting reset when clicking on the "I'll do later button"
Add Page Number support for Amaya.
Application - SSO While saving the same config in two applications, while clicking on Edit SP config, a popup showing do you want to continue editing the SP configuration? but only the continue button is given
Application - SSO - While saving the configuration in a new application, the save button loader is loading continuously
360 recon-Hide runnow button from detail view
360 recon dashboard filter-add dropdown for break type
360 recon dashboard-label change account overdue to account overdue in the target (also add some info on i icon what is this)
360 recon-Already running recon need to handle, disable the play button, or show a message
360 dashboard-make label consistent
360 recon dashboard-action details showing blank
360 Degree recon-For execution showing error
360 Degree Recon- History some time loading some time not
Recon 360 recon- A validation message for missing data is not required as it already shows no data found on the page when recon is not executed at all
360 recon dashboard-action details showing blank
360 dashboard-Search not working on break type
360dashboard-loginid filter not working
360 recon detail data showing mismatch
360 recon execute audit log not present
360 recon dashboard-on 2nd run details getting repeated
Amaya Azure- Showing route issue error message
Import Application- UI for the name is not proper
Import/Export- Recon is not working for AD's new application bundle
Teams config - while removing the condition in Group condition, shows the error " Please try again"
On Behalf config - while removing the condition in Group condition, shows the error " Please try again"
Teams Config - If the condition is kept blank and save is clicked, getting the error " Please try again"
On behalf config- If the condition is kept blank and save is clicked, getting the error " Please try again"
Import/Export Application- Convertor field types in the policy map are not getting imported
Import/Export - When any application configuration is imported into a new tenant, the user should be redirected to the application provisioning page after the upload
Import application- Showing an error message when importing an Amaya-based application if the exported application was without the policy map checked
Amaya- Policy Map Password attribute datatype identified as password instead of string
Amaya- Rename all operations(Test, Search, Sync, etc....) in sentence case
Workflow- Even after updating Grade as the 2nd level approver in the workflow, the 1st level approver is still being set at level 2
Workflow- After updating the user list as the 2nd level approver in the workflow, the 1st level approver is still being set at level 2
Workflow- When the level 3 approver is updated in the workflow, a 'Workflow Not in Range' error message is displayed.
Workflow- Even after updating the reporting manager as the 2nd level approver in the workflow, the 1st level approver is still being set at level 2
Workflow- When workflow over workflow is applied 2nd level approver is not getting updated
360 recon should consider full sync
360 recon fails then that 360 recon should be abort
Amaya Felicity Role assignment- Taking time to provide an error message
Deprovision- Exclusion Application- Application going in pending deletion state when that particular application is added in exclusion application while manually deleting a user from the Identity hub
360 Recon sync with bulk data showing heap size issue
AD new application- User list is not getting displayed showing urersrvc unknown error.
My workspace> Inbox- When workflow assignment is reassigned by admin, then the previous approver should not be able to accept or reject the request if the page is already open in the previous approver account.
Inbox - Workflow Request for setup for application - Need to enhance the details as per user interface.
Error in the server log-authsrvc , No impact on the functional flow
After the campaign workflow triggered on revoked, even though the campaign had ended and the workflow was approved, applications were still getting unassigned.
Campaign - Reviewer can approve self review request
The campaign not getting end, for tenant 2711
Workflow TAT- Workflow is getting aborted when grade is set at second level approver and set TAT time is over
Workflow TAT- Workflow is getting aborted when 2 level approver is set and set TAT time is over
Workflow TAT- Workflow is getting aborted when workflow approver is assigned to the user list
Workflow TAT- Showing error when the user is not present and TAT is over
Workflow TAT- Showing unauthorized error when TAT is over and operation is getting aborted
Recon pull- with both existing links, audit detail not showing
Workflow rule configuration-on edit workflow, previously selected role getting save
AD new bundle- Managed View- View should be proper while separating multiple OU in proxy addresses
AD new bundle- Manager and account expiry is not visible in the Managed view
AD new bundle- managed view- Value is not displayed in a proper format in Name in managed view
AD new bundle- Managed View- Showing different Start time/created time
In the User creation workflow, L1 - User List approved, L2 - reporting manager after TAT is expired, the request is not getting auto reject.
Pending Workflow List - If the approver is User list and Grade then it should display in Current Assign in the pending list
User Workflow - If the reporting manager is set as 2 level approver, the reporting manager is showing as Unknown
Policy Map- When the attribute is searched via the search button and that attribute is deleted then other attributes are not loaded
Profile Picture- After clicking once on the upload button, that button should be disabled
PAM-Server access not getting terminated even after time ends (Related to HA environment only)
User - Assign Application - Workflow initiated - Workflow Approvals page displays User list in Grade type
Pending Workflow -If the L1 approver is User List, then while clicking on the info icon, the popup does not show the user list. Also, it is " Grade List Details"
PAM-Server access not getting terminated even after time ends (Related to HA environment only)
Workflow Rule - Workflow is initiated when the group is set as an approver, the group is not visible on the popup screen
AD new bundle>Group- When the "Sam account name" update checkbox is unchecked and the user attempts to update the description, the description does not get updated in the AD
deployment_analytics_1 Service CPU utilization is 100%
Import/ Export- When a file is exported from a different env (Dev) and imported to QA env, then credentials are also imported along
Security Bug Fixes:- E2E request/response payload encryption for all APIs of authservice (as of now, planning to rollout for all the services in the next phase)
Amaya-Autofill policy map, When the value is not present to the user at the time of application then Amaya passes "$." to the target
Campaign - Reviewer can approve self review request
After the campaign workflow was triggered on revoked, even though the campaign had ended and the workflow was approved, applications were still getting unassigned.
Remote Group- AD Application- When users are removed from a remote group in Cymmetri, those members should also be removed from the group in the Active Directory
Amaya- Client ID should be visible in encrypted form
Provision Rule - While creating and configuring the custom attribute as "New ", the system is not initiating the rule.
AD new bundle- When an AD application is assigned to a remote group, the application is highlighted in the background while assigning but disappears as soon as the application popup box is closed
Reports- When the report is scheduled, Scheduler history shows content not found and the execution status is aborted.
AD Application- When the Ad test provision fails, and the user tries to delete the application from a user account, then the application should gointon a fail deletion state
Audit- Taking time to load audit logs
AD Application- Showing error when inserting start date in AD
In the application setting to user flags off then the also application shows in the recent application.
User lock- When a user account is active, and the same account is logged in through another browser, and by any means, the account gets locked, the first session should get terminated.
Branding- When show Unlock link from branding is kept as No, and the admin user account gets locked, then the user is not able to unlock the account from the login page
Application- When a user is adding /removing a role then it is not getting reflected without refreshing
group push-not taking user in AD at the time of update
Passwordless- WebAuthn; Showing not allowed error
Delegation-On behalf: when login by the delegate and the on-behalf condition is not satisfied still shows the on-behalf toggle button and gets removed when refreshed
AD Application- Group name should not accept space while creating or updating group name
Audit- Audi log should show log when the user is not getting any records in Recon history but showing task executed





































Proceed by adding your URL to the Website text box and clicking “Fetch Brand”.
If your organization’s branding is available, the logo and the corresponding color scheme will be displayed in the menu below.
If your branding is unavailable, you may configure it yourself by uploading your logo and editing your primary color, secondary color, and accent color.
Click on the Save and Sync Server button to make the branding configuration apply to the entire website.
User Activation
Application Scheduled Deprovisioning
Delegation User Notification
Application Access Approval Request Denied by Approver
Application Access Approval Request Granted
User Notification
Login Failed
Password Expiry Notification
Review Assignment Notification
Self Approval Notification
Login Adaptive Failed Notification
MFA Failed Notification
User Threshold
User attribute update / Profile update
Pending Access Certification Notification
Ad-Hoc Certification Notification
User Risk score changes
Requestee Notification
Requestor Notification
The administrator may edit the HTML using the provided HTML editor to add/change any template button/text/background. The macros required for the particular template are already provided in the sample default notification template.
Click on the Save button to save the notification template.
Grant Type - It is grant type which is used to grant access for API’s.
Client Id - client id for authentication
Client Secret - client secret for authentication
Authentication type - It is Fixed Bearer compulsory.
Update method - Patch or Put method.
Accept - Http header which accepts (application/json etc).
Content Type - Http header which accepts (application/json etc).
Access Token Base Address - base address for access token
Access Token Node Id - node id for access token
Access Token Content Type - content type for access token.
This section outlines how to set up an Annotation and integrate it into a user creation workflow, directing approval requests to your chosen approver.
I. Annotation Setup
Navigate to Configurations: From your product's main navigation, go to Configurations.
This enhancement introduces the Group Review capability within the access review system. This feature provides administrators with a more flexible and targeted approach to initiating access reviews.
Administrators can now initiate comprehensive reviews based on the following criteria:
All Groups: This option enables a comprehensive review of all user access permissions across every group within the system.
Specific Multiple Groups: This provides a focused approach, enabling administrators to select and review permissions for a pre-defined set of groups.
Specific Multiple Applications: This functionality allows for a granular review of user access rights associated with a select number of specific applications.
This new capability streamlines the access review process by enabling more precise and efficient auditing of user permissions, thereby reducing the time and effort required to ensure compliance and security.
Navigate to Identity Governance (IGA): Access the main IGA module from the Cymmetri
Access Group Access Review: From the IGA menu, select the "Group Access Review" option to initiate the configuration process for a group-based campaign.
Go to Campaign: Navigate to the Campaign section within the Group Access Review interface.
Create or Edit Campaign:
Click "Add New" to create a new access review campaign.
Alternatively, select and Edit an existing campaign to modify its settings.
Add Campaign Details: Provide all necessary campaign details, such as the campaign name, description, and schedule.
Select Target Group: In the second step of the campaign setup, choose Groups as the campaign target. Add the specific group that was previously associated with the designated Annotation.
Select Annotation: In the third step, select the Annotation option. From the dropdown menu, choose the specific Annotation created for the group approval process (e.g., groupapprover). This action links the campaign to the predefined approver logic.
Save, Publish, and Run: Complete the campaign setup by clicking Save, then Publish, and finally Run the campaign to initiate the access review.
Approval Request Routing: All access review requests for the targeted group will be automatically routed to the approver defined by the selected Annotation.
Approver Action: The designated approver should perform the following steps:
Log in to Cymmetri using the credentials of the Annotation-assigned approver.
Navigate to the Access Review tab.
Within the Access Review section, go to the Active list to view all pending requests.
d. Filter the view to display Group requests, if applicable.
e. Review all pending access review requests for the specified groups. The approver can then Approve or Reject each request based on their assessment of the user's need for continued access.
Assigning a Group to a User (from the User's Page)
Bulk Assigning Users to a Group (Using Group Assignment on Group Page)
First, the administrator needs to click on the group name and enter the configuration for the group.
Now, go to the Users Page and click on the +Add button to get a list of users to add to the group
3. Now, click on the assign button next to the user you wish to add to the group. Once assigned, the user can be seen on the Users page of the Group as shown below:
For this approach, the Administrator needs to go to Identity Hub > User page and then select the user from the list to whom the group needs to be assigned
Go to the user's page, select the Groups menu, and click on the "+Assign New" button
This opens a pop-up window where a list of all groups is visible
Click on the assign button, and the group is assigned to the user, or you may say the user becomes a part of the group
For this approach, the Administrator needs to go to Identity Hub > Group page and then click on the Group Assignment button
A screen pops up that lets you select the CSV file you want to upload to import the users that need to be assigned to the group. This CSV file needs to have one column that contains the login ID of users. Upload the CSV file, you may also use the sample data file available and modify it to match your user's login ID.
Once the file is selected and uploaded, next you need to select the group to which you want to assign the users.
After selecting the group, the column in the CSV file needs to be mapped with the Cymmetri login column.
Once mapped, click on the import button, and the users will be mapped to the assigned group, provided the login ID is correct
Results of successfully Imported Users, Duplicate Users, or any errors that occurred during import can be seen in the Logs > Import History page
To create a new password policy, the admin clicks on the add new button on the top right corner of the page.
The user has to fill in the password policy form with the below details
Policy Name - Name of the policy
Description
Conditional attribute type - Default - User (Non modifiable)
Conditional attribute Name - Default - User Type (Non modifiable)
Conditional attribute value - ( Consultant, Employee, Vendor)
After saving the detail, a new password policy is created. The next step is to define the password policy. This is done by clicking on the edit button in front of the record.
The admin can define the composition of the password. By rejecting
Password equals Password
Password which equals to LoginID
Password which equals to first or Last Name
Blacklisted Password
The admin can also establish the following parameters
Numeric characters minimum count
Password Length
Special characters count
Password History versions
Alpha characters
Uppercase characters
Lowercase characters
Characters not allowed in the password
In the "change" subsection the admin can also define:
Password expiration days
Password expiration warning from (no of days)
Whether to change password on reset
The administrator also has the capability to set prohibited passwords, preventing users from using those specific passwords.
Error Records: Count of records that failed during the synchronization process.
Total Records: The total number of records processed or considered in the run.
For a deeper analysis of a specific reconciliation run, administrators can select the View History option. This detailed view provides granular data organized across several key categories:
Modes
Sync field, Source attribute, Job completion time
Specifies the primary attribute used for matching records, the source attribute used for data, and the final timestamp of the job's completion.
Conditions
User does not exist in the Target System & exists in Cymmetri
Identifies users flagged for provisioning to the target system.
User exists in Cymmetri & Target System
Identifies users flagged for profile update or validation across both systems.
User exists in Target System & does not exist in Cymmetri
Identifies orphaned accounts in the target system, flagged for de-provisioning or review.
Summary
Pending Records, Synced Records, Error Records, Total Records
The final statistical outcome of the reconciliation job.
The Role Reconciliation Dashboard is a specialized sub-page within the Recon History section dedicated to auditing and managing user role entitlements.
This dashboard provides administrators with the following granular details for each user involved in a role reconciliation activity:
Login
The unique login identifier of the user.
Already Assigned
The set of roles that the user held before the current reconciliation process was executed.
Fetched
The roles for this user that were successfully retrieved from the target application during the reconciliation run.
Newly Assigned
Roles that have been provisioned to the user as a direct result of the reconciliation logic.
To Be Removed
Roles identified by the reconciliation logic as needing to be revoked from the user's profile.
Status
The current state of a role assignment, indicating if the role has been removed, is currently under administrator review, or has been confirmed for continued assignment.
Actions
Interactive options allowing the administrator to drill down for further details on the specific role or to initiate a manual action (e.g., overriding the removal status).
To establish a new reconciliation job, please refer to the dedicated documentation on Reconciliation Configuration.
Operation Performed on the Scheduled Period: Outlines the specific action executed during the scheduled period.
Planned At: Indicates when the scheduler was initially planned or scheduled.
Sub Event: Offers details about any sub-events associated with the scheduler operation.
Executed At: Specifies the timestamp when the scheduler was executed.
Execution Status: Highlights the status of the scheduler execution, indicating whether it was successful or encountered issues.
Remarks (If Any): Includes any additional remarks or notes related to the scheduler operation, offering insights into the execution process.
The scheduler history provides various filters to identify status of failed jobs as shown below:
These failed jobs are sent out as alerts to specified users as per the notifications template
Reconciliation History provides a centralized dashboard for all system reconciliation jobs in one page. The relevant admin user can view the summary of all the tasks in progress, completed or aborted.
The tasks that have failed can be manually processed to run again by clicking on the retry button next to the failed history.
The Reconciliation job will also alert the specified Cymmetri user of the tasks over email. The configuration is two-fold-
Global notification
Specific application notification
Cymmetri includes the ability to retry failed records based on the failed event. Administrators can configure the maximum number of retry attempts and set up notifications according to these settings.
Cymmetri will send the alerts for all job status events to the specified user or email.
A Batch Task in Cymmetri is a configurable, automated job designed to perform bulk operations by executing a specific backend API endpoint. These tasks can be scheduled to run at predefined intervals or be triggered manually. They are commonly used for operations like data synchronization, user lifecycle management (e.g., deactivating inactive accounts), and report generation.
Before you can configure a batch task, you must ensure the following are in place:
API Endpoint: The backend API endpoint that the task will call must be fully developed and operational.
Permissions & Authentication: The API endpoint must have the necessary permissions to perform its intended function, and Cymmetri must be configured with the proper credentials to authenticate with it.
Clear Business Logic: The logic behind the task must be well-defined to ensure it performs the correct operation on the right data set.
Manual Testing: The API endpoint should be manually tested to confirm it works as expected before being integrated into a batch task.
Step 1: Navigate to Batch Tasks
In the Cymmetri platform, go to the Configurations menu.
Select Batch Tasks.
Step 2: Add a New Task
Click the Add Task button to create a new batch task configuration.
Step 3: Define Task Details
Name: Provide a unique, descriptive name for the task.
Description: Enter a brief explanation of the task's purpose.
Endpoint: Specify the particular API operation the task will execute.
Complete Batch Task URL: Provide the full URL of the API endpoint.
Step 4: Configure Scheduling
Use the toggle switch to enable or disable scheduling.
If enabled, configure the task's frequency. You can select from options such as daily, weekly, or monthly runs, or create a custom schedule using a CRON expression.
To generate a custom schedule, use the Generate Cron Expression tool, then click Generate and Apply.
If disabled, the task will only run when manually triggered.
Click Save to finalize the task configuration.
After a task runs, its status and execution details will be recorded in the Audit Log.
Step 5: Execute a Batch Task
To manually run a task, find it in the list of batch tasks.
Click the edit icon next to the task's name.
Select the Run option.
To verify the execution, navigate to the Audit Log, where you can view the status and results of the executed batch task.
Log in to your Google admin account and go to the Admin Section as shown below:
Once in the admin section click on Apps > Overview
In the overview page click on the Web and mobile apps tile to add a new custom app
On the Web and mobile apps page click on the Add app dropdown and then select Add custom SAML app to add the Cymmetri tenant as a custom app
Provide a relevant App Name, Optionally a description for the application can be provided. An App Icon can also be attached if required. Once entered click on the Continue button
On the Google Identity Provider Detail page download the metadata file by clicking on the DOWNLOAD METADATA button. This metadata file needs to be used to get Entity ID, SSO URL, and Certificate. Administrators can download the certificate here or later as shown . Once downloaded click on Continue.
Once the IDP metadata and certificate are obtained the Service Provider(i.e. Cymmetri) details need to be provided. We need to provide the ACS URL and the Entity ID these details can be obtained from Cymmetri as shown here. No change needs to be done for the Name ID format and Name ID, it can be kept to UNSPECIFIED and Basic Information > Primary email. Once done click on Continue
Attributes can be added on this screen which could then be sent as a SAML response to Cymmetri. These values can be used to create a user in Cymmetri if JIT provisioning is enabled on Cymmetri's side
Group membership information can also be sent by configuring groups here and if the user belongs to the configured group. Once attributes and groups are configured click on FINISH.
Once you click on the FINISH button the below screen appears that shows the configuration details. It also shows various shortcuts to Test SAML Login, Download Metadata, Edit Details, and Delete the App
If the administrator does not download the certificate while configuring the custom application, it can be later downloaded. For the same the administrator needs to go to Security>Authentication>SSO with SAML applications. This will open the Security Settings page from where either the IDP details like SSO URL and Entity ID can be copied and the IDP Certificate can be downloaded. These details can be used to configure the IDP in Cymmetri.
Once Google IDP is configured, the administrator must proceed with the configuration on the Cymmetri side. To achieve this, the administrator needs to set up Cymmetri as a Service Provider and also incorporate Google as an external IDP.
The page shows how to configure a Service Provider.
Once the Service Provider is configured, we need to configure Google as an external IDP.
Administrator needs to go to Authentication->Identity Provider->External IDP. Here you may either configure the already created google-idp instance or +Add New
In either cases a screen opens where you need to provide the below mentioned details
Name: Google IdP
IDP Type: Google
Entity ID: https://accounts.google.com/o/saml2?idpid=xxxxxxxxxxxx
SSO Service URL
Once all the details are entered Save the changes.
For enabling Google IDP to be used as an IDP for specific set of users an Authentication Rule needs to be configured. you can see the steps on how to configure Authentication Rules.
Once the rule is configured whenever a user matches with the rule conditions the user is redirected to Google screen and the user needs to provide his/her Google credentials to be able to login into Cymmetri.
Adaptive authentication is an advanced security measure that assesses various factors and context elements in real-time to determine the level of risk associated with a user's access attempt.
Based on this risk assessment, the authentication system can dynamically adapt its level of scrutiny and request additional verification steps if needed. This approach enhances security while minimizing disruption for legitimate users.
In Cymmetri there are various adaptive checks that the admin can enable for additional factor of authentication.
Device Trust Check - If enabled, Cymmetri will check if the device being used to perform action on the Cymmetri portal, has been trusted by the user
User Behavior - Cymmetri determines whether the behavior of user matches with the known behavior pattern of the user over time
Blacklisted IP - Maintains a blacklist of IP addresses that are known to be sources of unauthorized access, hacking attempts, or other malicious activities
Blacklisted Location - Cymmetri maintains a list of locations from which the administrator wishes to restrict access of the portal
Short Lived Domain - Cymmetri checks the email address domain of the user with a database of known providers of short-term or disposable email addresses
Impossible travel scenario - Tracks the change in location of user attempting an action over a short period of time and flagging if, system deems the pattern to be impossible.
The admin can enable these checks as per the business use case
To navigate to the adaptive settings page, click on the "Go to settings" button on the top right corner of the page.
Administrators can include an IP address in the blacklist by following these steps:
Enable the "IP address Check" radio button at the top of the page, input the IP address into the "Blacklisted IP address" field, and press enter. The specified IP will be added to the list. To synchronize the list with the database, click the "Sync Now" button.
You can select additional actions when module detects an anomaly. They are the following:
Ask additional MFA and notify - If an MFA rule has been established and adaptive authentication is activated for it in the MFA section, when a user attempts to log in with a blacklisted IP address, the user will be prompted for additional factor(s) for authentication as defined by the rule. Additionally, the user will receive email notifications regarding the login activity.
Only Notify - This option solely sends a notification to the user about the login activity.
Block user and notify - This option not only blocks the user upon a login attempt with a blacklisted IP but also notifies the user on their registered email ID.
Define how Cymmetri determines if a device is trusted for the user and allows to define behavior of authentication in Cymmetri, in case of untrusted device
The admin can define
No of successful authentication attempts
Number of devices per user
Number of days
Additional action when module detects anomaly
Location based checks
Organizations can maintain a list of blacklisted locations as part of their adaptive authentication strategy to enhance security measures and mitigate potential risks
The admin can select the blacklisted location on this page. Also additional actions on these checks can be selected.
Impossible Travel Scenario
Track the changes of location from which the user attempts to perform actions on the portal over a short period of time and flags an action attempt
The admin can configure the:
Check Windows(in hrs)
Average Distance (in Km)
Short lived Domain Checks
Checks the .email address domain of the user with a database of known providers of short-time or disposable email addresses
The admin can Sync the database where the domains are stored and updated
User behavior checks
Cymmetri determines whether the behavior of user matches with the known behavior pattern of the user over time
The admin can select the required checks to verify the consumer behavior:
Unusual time of Login
Unusual number of Login failures
Unusual keystrokes pattern
The admin can enable, configure and save these adaptive checks individually as and when required.
In Cymmetri, the Audit Logs serve as a vital tool to maintain transparency, accountability, and security in your identity and access setup. This feature meticulously records a detailed account of various activities, ensuring a comprehensive overview of critical events and system changes.
Cymmetri uses a high performance columnar database management system designed for online analytical processing (OLAP). Its architecture and features make it well-suited for maintaining audit logs with strong protection and tamper resistance.
Below are key capabilities that contribute to these aspects:
Audit logs are critical in any security framework as they provide a reliable trail of all activities within a system. Ensuring that these logs are tamper-proof is vital to maintaining the integrity, accountability, and transparency of the data. Cymmetri, a robust identity management platform, implements several best practices and technological safeguards to ensure that audit logs remain tamper-proof. Here’s how Cymmetri achieves this:
Cymmetri uses immutable storage for audit logs, meaning once data is written, it cannot be altered or deleted. This ensures that even privileged users or attackers cannot manipulate the logs. The immutable nature of the storage ensures that records are permanent and always available for audits.
Each audit log entry in Cymmetri is hashed using cryptographic algorithms, such as SHA-256, before being written to the storage. Hashing creates a unique digital fingerprint of the log entry, making any changes immediately detectable. If the contents of an entry were altered in any way, the hash would no longer match, thus providing tamper-evident logs.
To add an extra layer of tamper-proofing, Cymmetri leverages chain technology for audit logs. Each log entry is chained to the previous one using cryptographic hashes. This makes it impossible to alter any individual log without breaking the entire chain. chain ensures both immutability and accountability since every change or addition to the log becomes part of a transparent, verifiable sequence.
Cymmetri strictly enforces role-based access controls to restrict who can view and interact with the audit logs. Only authorized personnel have the rights to access the logs, and the system records all accesses, creating an additional layer of oversight. This minimizes the risk of tampering from internal threats or misconfigurations.
Cymmetri ensures that audit logs are stored in multiple secure locations using distributed databases or cloud storage. This redundancy guarantees that even if one storage instance is compromised, the logs in other locations remain intact. Regular backups further protect the integrity of logs by ensuring that a historical record is always available.
Each audit log entry is time-stamped with a high degree of precision to ensure traceability and integrity. The timestamps are included in the cryptographic hashes, making it impossible to modify both the content and the timing of the log entries. This creates a reliable chain of events that can be used to track down and investigate suspicious activities.
Cymmetri’s tamper-proof audit logs combine state-of-the-art technologies like cryptographic hashing, immutable storage, and chain to ensure that the integrity of the audit trail remains intact. With features like RBAC, redundancy, time-stamping, and real- monitoring, Cymmetri offers a highly secure logging framework that prevents any unauthorized modifications, ensuring full accountability across its systems.
For administrators looking to review system-related logs in Cymmetri, the process is simple. Just head to the "Audit Logs" tab within the Logs section. Here, you'll find a wealth of information, covering everything from user logins to requests for accessing applications.
Cymmetri Audit Log maintains all events processed via Cymmetri. The events are tracked based on per object event log as per the Cymmetri logging framework. Events that become part of the the log are-
Human driven events processed by the system. Example- a Cymmetri Admin changing an application configuration.
Scheduled events processed by the system. Example- Deprovisioning job to disable Cymmetri users.
Events triggering associated processes as set up in the system. Example- Authentication service will verify the authentication rule to check for Passwordless or MFA based login journey.
Cymmetri goes the extra mile by capturing each and every system event, offering administrators a thorough understanding of what's happening within the platform.
For a closer look at a specific log entry, administrators can click on the eye icon next to it. This action provides a detailed response, offering insights into the exact activities that took place.
The admin can also filter the logs based on:
The actor who performed the event
The performed event
Start and end date of the events
Target and target type
Cymmetri provides a reference view for the changes occurred during an audit event.
In essence, Cymmetri's Audit Logs empower administrators with the tools they need to keep a close eye on system activities, ensuring a secure and well-documented identity and access management environment.
Github Enterprise provides provisioning using SCIM 2.0
Pre-requisites
Create an account in Github (Enterprise).
Enable SAML for the Github tenant to be used with Cymmetri.
Step 1. Configure SSO in Cymmetri
Note the application URL received from the Git SAML configuration
Continue the configuration by logging into Cymmetri using at least Application Administrator role
Note: Public certificate gets from SSO metadata(cymmetri) and format it using following
Note: Make sure when you test SAML then in cymmetri login with github admin users loginid which is added in cymmetri.
Configure Profile Mapping
Create User in Cymmetri and make sure login id of Cymmetri is same as gitHub Admin user login id.
Test SSO with the Cymmetri user.
Configure SCIM v2.0 (Github) application from master (cymmetri).
Basic provisioning policy attribute and policy map already aaded in default schema.
Github Application is run using Fixed Bearer token.
To get Fixed bearer token following steps used.
Step 1: Go to user settings in github
Step 2: Go to developer settings
Step 3: Go to personal access token and generate new token
Step4: Click on Configure SSO
Step 5: Click on Authorize
Use following cymmetri provision configuration and change according to github account.
Fixed Bearer Value copy from personal access token
Click on save
Click on Test Configuration with success message.
Cymmetri platform has six different admin roles with various levels of access to the various menus and resources on the administration portal of Cymmetri.
In addition to these six admin roles, Cymmetri also supports three different privileged user roles that grant varying levels of access (read, write, report) to privileged users within Cymmetri.
The various admin roles on the Cymmetri Identity Platform may be described as follows:
The 360 Degree Recon is one of a type feature of Cymmetri that enables administrators to have a holistic view of user data.
The 360-degree reconciliation process in Cymmetri is designed to ensure that identity data across different systems is consistent and up-to-date. The reconciliation process involves comparing records from Cymmetri with the records in target systems (like Active Directory) and identifying discrepancies that need to be addressed.
The 360-degree reconciliation process in Cymmetri is crucial for maintaining data integrity across all connected systems. By regularly running reconciliation, organizations can ensure that their identity data is accurate.
The 360 degree recon can be configured for all the provisioning applications supported by Cymmetri. Here we will be seeing an example of 360 Degree Recon with Active Directory.
Dynamic Forms enable administrators to request additional fields from either administrators or end-users when assigning applications. These additional user fields are then collected and used for provisioning the user into the managed application.
For creating a dynamic form the administrator needs to configure the managed application. For e.g. Identity Hub->Applications->Service Now(Application may change )->Forms
Load the default form by clicking on the “Load Sample Data” button
Cymmetri seamlessly integrates with various cloud-based applications to help you efficiently manage user access and entitlements. The following are the pre-configured cloud-based applications that Cymmetri supports:
Azure: Manage user access and entitlements within your Microsoft Azure environment effortlessly.
Google Workplace: Simplify access management for Google Workspace applications, including Gmail, Google Drive, and more.
ServiceNow: Effectively control access to your ServiceNow instance to enhance security and compliance.
Salesforce: Streamline Salesforce user access management for better control and auditing.
SCIM v2.0 (Salesforce): Utilize the System for Cross-domain Identity Management (SCIM) 2.0 protocol specifically for Salesforce integration.
Github (Using SCIM 2.0 connector): Manage user access to GitHub repositories efficiently through our SCIM 2.0 connector.
Cymmetri extends its support beyond cloud-based applications to include various on-premises applications. Here are the on-premises applications supported by Cymmetri:
Active Directory: Efficiently manage user access to your Windows Active Directory resources.
OpenLDAP: Simplify access control for your LDAP directory services with Cymmetri's integration.
Lotus Notes: Streamline user access management for Lotus Notes applications.
Powershell: Integrate and manage access to PowerShell scripts and resources seamlessly.
CSV Directory: Effectively manage user access within CSV-based directory services.
Cymmetri offers versatile connector support to ensure seamless integration with a wide range of applications. Here are the supported connectors categorized by deployment type:
Cymmetri's Cloud Connectors are designed to simplify access management for various cloud-based applications. Supported cloud connectors include:
Azure: Easily manage access to Microsoft Azure resources with our cloud connector.
Google Workplace: Streamline access management for Google Workspace applications using our cloud connector.
ServiceNow: Control access to your ServiceNow instance efficiently with our cloud connector.
Salesforce: Seamlessly manage user access to Salesforce through our cloud connector.
SCIM 1.1: Leverage the SCIM 1.1 protocol for connector support, ensuring compatibility with various cloud services.
SCIM 2.0 (Basic, Bearer, Fixed Bearer): Our platform supports multiple SCIM 2.0 authentication methods to accommodate diverse integration needs.
For on-premises applications and custom integration scenarios, Cymmetri offers locally deployed connectors, providing flexibility and control. Supported locally deployed connectors include:
Active Directory: Manage access to Windows Active Directory resources seamlessly using our connector.
Custom Script for Databases: Custom Script based connectors using groovy scripts for database applications, tailored to your specific requirements.
LDAP: Integrate and manage access to LDAP-based directory services through our connector.
Lotus Notes: Simplify user access management for Lotus Notes applications with our connector.
Powershell: Seamlessly integrate and manage access to PowerShell resources using our connector.
REST API: Extend your integration capabilities with Cymmetri's support for RESTful API connectors leveraging the flexibility of Groovy and UI based scripts.
Cymmetri's comprehensive support for both pre-configured applications and versatile connectors ensures that you have the tools needed to efficiently manage user access and entitlements across a diverse range of applications and environments. For detailed setup instructions and configuration guidelines, please refer to the specific documentation for each application and connector.


















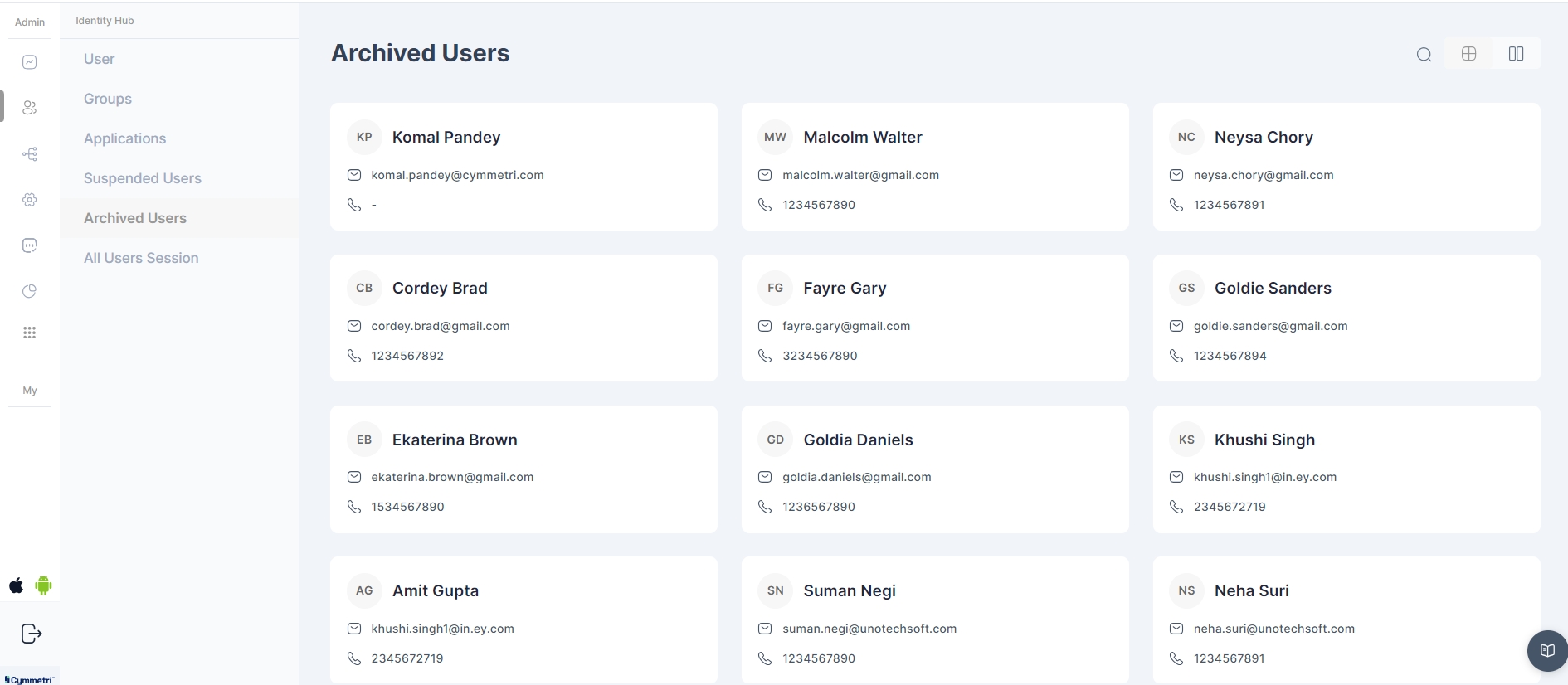








Destination: https://<hostname>/spsamlsrvc/samlSP/SingleSignOn
Protocol Binding: HTTP Post (can also be set to HTTP Redirect if it is set so in Google IDP)
Name ID Policy:
Policy: Email (This may change based on what is configured in Google IDP)
Value: Email (This may change based on what is configured in Google IDP)
Certificate: Certificate downloaded from Google IDP
Logout Request URL: Need to mention the SingleLogoutService url from the metadata file if SLO (Single Logout) is configured in Google.
Logout Protocol Binding:HTTP Post (can also be set to HTTP Redirect if it is set so in Google IDP)
Service Provider Id: cymmetri (Need to the select the configured Service Provider as shown above)
Status of the event - all, success, and failed
Check Policy map
Disable default for the respective attribute
General configuration for the threshold updated.
UI changes for:
Creation, updation, and deletion of users.
Retry staging users from the staging dashboard.
Archive for user threshold
Updated Email Title and Template.
Notifications for user threshold:
Notification field made mandatory.
Org Admin set as default notifier (not supported for old tenants).
Notification Field in User Threshold Config for delete users
Staging dashboard:
Updates to the staging dashboard view and error messages.
Display names shown during threshold delete operations.
Manual “Move to Archive” button added for staging users.
Failure handling for moving staging users to archive, including audit log display.
User Directory Search
Quick search updated to support:
Employee ID, email, mobile, first name, last name, middle name, display name, login.
Dropped support for: grade, userType, department, designation, custom attributes.
Email Validation
Removal of Email validation from backend
2. Workflow
Custom Attributes in Workflow Rule Events
Supported events:
User Creation
Application Provisioning, Deprovisioning, and Update
Pending Workflow Enhancements
Reassign user functionality added to the inner page.
Requester and requestedFor columns added.
UI/ UX Changes
The inbox title within the workflow setup event now displays the workflow name.
The Pending Workflow List now includes 'Requester' and 'Requested For' columns for display.
User details section in Inbox Requests will now include assigned application details
User Delete Workflow
Workflow and rule configuration support added.
Workflow assignee escalation:
If the workflow-task assignee is the same as target-user/requester then assign task to assignee's reporting-manager. Application level configuration support provided, default is disabled.
Default Workflow Rule
A workflow rule that is configured without any conditions, It triggers when no other rule matches. Supported events include:
User Creation, Application Provisioning, Application Deprovisioning, Workflow Setup, Application Role, Decommission Device, Application Update, Access Review Reject, User Delete, Form Logic Workflow, Exception Application, Movers
3. UI/UX Enhancements
Warning added || Application Config Import Modal || Auto 'Create Only' for User Principal policy mappings
Amaya || Add support for JSON body validation through validate button
Inconsistent button placement across certain modules has been rectified by aligning them to a standardized position below.
Onboarding Walkthrough for new users.
Audit log comparison for oldObject and newObject when they are in detailed format
QR code zoom feature added to FIDO, TOTP, and push authenticator scanners.
Improved runtime error handling with a sitewide error page.
Enhanced build performance by 46%.
4. Identity Governance
RecommendationEngine
Enables seamless integration and management of application and role recommendations.
Supports generation of personalized application and role suggestions.
Supports the automatic synchronisation of data from various sources, ensuring that recommendations are always based on the user behaviour.
All recommendation engine configurations, data synchronisation are stored and can be easily retrieved and updated as needed.
Campaign and workflow integration for approvals and recommendations.
Scheduler history provided with container status.
Campaign: Recommendation details shown on assignment approver action in campaign for campaign assign.
Inbox: Recommendation on application assignment workflow request in inbox for approver.
Role Based Forms
Per role form request was introduced which enabled to invoke a new form for every new role requested by the end user
Improved Campaign Visibility & Control
Includes notifications for Managers, internal users, and external emails, along with downloadable campaign reports.
The ability to extend running campaigns provided and Initial planned end dates visible in tooltip after the campaign gets extended
Save as Draft feature is provided in approvers view, where approver can select and approve multiple requests as draft and then save all of them as one.
Recommendation Scheduler History: Provides information on whether the recommendation engine is configured, along with the scheduler history, including its status (running or completed) and the number of records processed.
Recommendation Engine Scheduler: It tells you about the running container for the particular tenant on the version page
Highlighted the SOD Rule (name) being violated during the recommendation to the user
5. Mover Process
Gradual rollout across phases:
Phase 1: UI configuration without backend integration.
Phase 2:
UI performance optimisation, made new UI designs and implementation to boost the performance by reducing API call compare to earlier UI proposed
Default scheduler (No execution)
Added calculation for applicationToSkip, applicationToRemove and applicationToAdd (backend only).
Refactor existing Cymmetri user update API (backend) .
Manual Update
Reconciliation -Both exist update
Teams -User update
Refactor existing deprovision and provision rule execution
If mover configuration is active then only calculations will perform for application to remove.
Phase 3: Dashboard for deprovisioned apps
Phase 4: Deprovision Scheduler, Workflow, Dashboard Enhancements, and Notifications.
6. Application Management
Reconciliation
360 Degree Reconciliation:
Compare tab for comparing source and target applications.
Generate and download csv reports.
Reconciliation Dashboard Enhancements:
Reconciliation Filters,
Partial job failure handling, and
Reconciliation job notification configs.
Removed global-level and added application-level recon notification configuration.
Reconciliation Activity Log - Show previous and next 10 minutes activity log for each reconciled entity (user/group)
360 degree recon support for Simple LDAP Application
Exceptional Applications
Configuration Side
Schema, Masters, and Template with application mapping
Quick Setup
Bulk Application Un-assignment
Bulk Application Un-assignment allows administrators to remove access to applications and roles from multiple users simultaneously using a CSV file.
On Demand Access
On Demand Access Request offers the capability to define on-demand roles, allowing administrators to enable access dynamically.
Global Apps
Global Apps allows the user to configure applications that are applicable to all the users which are not available via On Demand or Exceptional Applications Configuration
Role description is provided under the role name whenever an application is requested.
Role Management
Parent and child role support added in CSV imports and manual role creation.
Application ➝ Assignments ➝ User assign ➝ Failure/Pending assignment user list Integration
Data logger service version information added.
Optimized the data-logging framework for better performance.
Full sync support added(this step is an optional step and required only if any of the below conditions match),
Tenant audit database is not present, or
Tenant audit database is corrupt so fresh setup is required.
Optimized the tenant registration database creation process.
Tenant Registration Process Resumption: If the tenant registration process is interrupted, it can be seamlessly resumed and completed using the existing account configuration. The registration process can be resumed from the following stages:
Pending OTP Verification
Incomplete Credential Setup
External IDP SSO: Added support to log in to Cymmetri as an external identity provider for IDP-initiated SSO.
SAML IDP SSO: Added support to send IDP-initiated (Cymmetri) SSO response to Cymmetri as a service provider.
TOTP Config:
Look-ahead window: Added support for 0 as an option inside the dropdown.
SDK Integration:
Implementing SDK integration for mobile push notifications to resolve issues with the existing legacy API of:
Fido Based Notifications and
Normal Push Based Notifications
The Form Logic functionality enables you to store custom data using flexible, administrator-defined forms.
It empowers you to create forms tailored to your specific data collection requirements, providing a versatile solution for various data management needs.
Form Logic webhook sample request schema and sample script updated for user details.
Skip Password Expiry has been added to the PasswordChangeRule.
This option allows administrators to exempt specific users or groups from the regular password expiration process.
When enabled for a user, they will not receive any warnings or notifications regarding password expiry, and they will not be required to change their passwords due to expiration.
Active Directory || SimpleAD Connector upgrade
UserAccountControl attribute support added
memberOf attribute support in manage system viewer
ProxyAttribute attribute support added
Amaya
Added the following templates for quick setup:
Atlassian
Zoho CRM
LDAP Connector
A new connector named 'SimpleLDAP' has been added for connecting to LDAP Applications.
The LDAP adapter has been updated with a new feature that eliminates the need to enter a username and password for each execution.
ScriptOn(Database) Connector
Manual Link operation support added
Email Configuration Update
Mail Username and Password fields no longer require validation, allowing them to be empty. This is because some email servers do not require authentication.
Other fields, such as Mail Port, Mail Host, and Mail Sender, still require validation to ensure proper email functionality
Reports Email Scheduling
Configuration support added for fetching a report of current business day.
Advanced Analytics
Authentication Data model created
Support for downloading reports in CSV or PDF.
Generate Report
New Generate Report button when viewing reports in Insights > Reports > View icon
External Logs
This feature provides a centralised way to capture and view logs from external applications interacting with Cymmetri via webhooks or batch tasks.
This enables administrators to debug external interactions directly within Cymmetri, simplifying the monitoring and troubleshooting process
Redis Cache support provided for the My Workspace section to improve performance.
APIEXT:
Exposed a new API for implementation team to get user details based on email, login and/or displayName
manager notification: receiving user name required manager name
In application setting if show to user flag off then also application show in recent application
Amaya || Unable to identify application properties data type where value is empty
Amaya || Create user operation falls due to invalid password
Reports-Records are getting displayed after 11min approximately
recommendation run for tenant 2711 taken 2 days, 3 hours, 8 minutes, and 12 seconds for 345,000 users
During reconciliation, when the user login ID is left blank and the loginGenerator is activated, the process fails due to the empty login
This is the so-called 'super admin' administrator role in the Cymmetri platform. Administrators with this role have the authorization to modify any settings or make changes to the tenant.
This is a slightly less privileged administrator. Most tenant-wide system settings, such as the configuration of SMS and email providers (when configured by the tenant), are restricted for domain administrators. All other configurations can be viewed and edited by administrators with the Domain Administrator role.
An administrator with the role of Application Administrator has access to Identity Hub configurations, including Application, User, and Group configurations. The Application Administrator can map users and groups to applications and can edit all configurations related to Application Management.
An administrator with the role of Report Administrator has access to the Reports menu, which includes the ability to view, modify, and add new reports.
The Helpdesk administrator has access to a very limited set of administrative functionalities, such as resetting the password of the end-user, removing configured Multifactor authentication options, and other such common use cases.
All administrative users have editing access to the various administrative sections of the Cymmetri platform. However, administrators with the "Read Only Administrator" role do not have editing access to any of the settings or configurations; they only have "Read Only" access to the administrative section.
PAM Write Access in Cymmetri grants users the privilege to connect to servers via RDP or SSH and perform write or modification actions on those servers. Users with PAM Write Access have the ability to make changes, update configurations, and perform tasks that involve altering data or settings on the connected servers. This access level is typically assigned to administrators and IT personnel responsible for making configuration changes or updates on various servers within the Cymmetri environment.
PAM Read Access provides users with the ability to connect to servers using RDP or SSH and view the content and configurations on those servers. However, users with PAM Read Access do not have the authority to make modifications or changes to the server settings or data. This level of access is suitable for individuals who need to monitor server activities, check logs, or retrieve information from servers without the need to alter any server configurations.
PAM Report Access is designed for users who require access to PAM-related reports without the need to connect to servers via RDP or SSH directly. Users with PAM Report Access can generate and access reports that provide insights into server activities, access logs, or other relevant data within Cymmetri. Such users can also configure schedulers to send timely reports to various other users. This level of access is beneficial for auditors, compliance teams, or individuals focused on analyzing server-related information for reporting and auditing purposes.
Follow the steps mentioned below to promote a user as an admin in the Cymmetri platform.
Click on the Configuration menu on the right-hand side
Now, click on the Admins sub-menu within the Configuration menu
Click on the "+Add New" button to add a new administrator
To assign an administrator role to a user, search for the user and then click the 'Assign' button.
Select the chosen administration role and click on Save
The administrator has been assigned the role of “Report Administrator”.
All admins is a section where various Cymmetri admins are displayed to the admin user
As the first step for configuring 360 Recon the administrator needs to configure a pull recon as explained here.
Once the pull recon is configured the user next needs to go on the 360 Degree Recon page as shown below:
The 360-Degree Reconciliation page displays all the pull reconciliations configured for either users or groups. The administrator can select a configured reconciliation and run a 360-degree reconciliation for that specific pull.
Once the 360-degree reconciliation is started the administrator can then go to the History tab and view the results of the reconciliation on the reconciliation dashboard
Reconciliation Dashboard
The reconciliation dashboard provides an overview of the latest reconciliation run, including key metrics and visualizations to help administrators quickly identify and address issues.
Key Metrics:
Last Start Date: Indicates the start time of the most recent reconciliation run.
Last End Date: Indicates the end time of the most recent reconciliation run.
Total Processed Records: The total number of records processed during the reconciliation.
Records Pulled from Target App: The number of records pulled from the target application (e.g., Active Directory).
Present in Cymmetri only: Number of records that exist in Cymmetri but not in the target system.
Present in Target only: Number of records that exist in the target system but not in Cymmetri.
Accounts Overdue in the target: Number of accounts that are overdue in the target system but not reflected in Cymmetri.
Break Type Analysis
The break type analysis section uses a pie chart to categorize the types of breaks (discrepancies) identified during the reconciliation. In the example shown in the image, all breaks are categorized as "Present in Cymmetri only," indicating that certain records exist in Cymmetri but are missing from the target system.
Filter Options
Administrators can filter the results based on several criteria:
Login ID: Search for discrepancies related to specific user logins.
Break Type: Filter the results based on the type of break (e.g., "IDM exists, Target not exists").
Break Count Min/Max: Filter based on the minimum and maximum break counts.
Reconciliation Results Table
The results table provides detailed information on the discrepancies found during the reconciliation process.
Columns:
User Login: The login ID of the user in the Cymmetri IDM system.
Source Application Login: The corresponding login ID in the source application (e.g., Active Directory).
Application Login: The login ID in the application (if applicable).
Break Type: Describes the nature of the discrepancy (e.g., "IDM exists, Target not exists").
Break Count: Indicates how many times this particular break type was found for the user.
Actions: Provides option for viewing the user details for further understanding of the user data
Common Break Types
IDM Exists, Target Not Exists: This indicates that the user or identity exists in the Cymmetri IDM system but does not exist in the target system (e.g., Active Directory).
Target Exists, IDM Not Exists: This indicates that the user or identity exists in the target system but does not exist in the Cymmetri IDM system.
Actions to Resolve Discrepancies
Once discrepancies are identified, administrators can take the following actions:
Manual Review: Examine the discrepancy details and determine if the record should be updated, deleted, or if the discrepancy can be ignored.
Automated Actions: Depending on the configuration, some discrepancies can be automatically resolved by provisioning or de-provisioning the necessary accounts.
Let us create a simple form that can capture
“Preferred Username” [text field] and
“Request Additional Modules” [Radio] with two options “Administrator” and “Read Only”.
The code below shows how to create a simple form described above:
The UI Schema is like a set of json properties that are used to configure how the form should look and behave. It lets you tweak things like the length of a text box or whether a choice should be shown as radio buttons or checkboxes. In the example code, we're using the UI Schema to make the "preferredName" field have a placeholder and also set a maximum length. For "additionalModules," we're using widget property to make it show up as a radio button.
The Preview Form Data displays how the data entered in the UI will be gathered and shows the structure in which the data will be sent to the API.
The preview of the form looks as below after making the changes:
Once configured the administrator can Click on the Save button.
Once saved a confirm box appears to enable the form; the administrator needs to click on the Confirm button in the popup to enable the form for the application.
There are four options in that can be configured after enabling forms in Cymmetri
Form View: If enabled, the user has the option to see the application request form within the My Access section.
Form Edit: If enabled, the user has the option to edit the application request form within the My Access section, this will make changes in the respective fields in the target application.
Role Assignment: If activated, the user will be displayed the request form for applications that are already assigned to them when attempting to request additional roles.
Role Unassignment: If activated, the user will be displayed the form for applications when he/she is raising requests for role removal.
The page here shows how to configure a Service Provider.
Navigate to External IDP in Identity Provider.
Select Azure-IDP.
Configure Azure AD for Creating Identity provider configuration
Now Login to the Azure portal and select Azure Active Directory.
Navigate to Enterprise applications and select New Application.
Create your own application and enter the name of the application.
Set up Single Sign On after creating the application using SAML.
Click on Edit basic SAML configuration.
Add Identifier (Entity ID) and Assertion Consumer Service URL from the XML file downloaded in step 3 (For Azure, Sign on and ACS URL are the same) and save the configuration.
Download the Certificate (Base64) from SAML Certificates.
Continue configuration of Identity Provider In Cymmetri Administration Console
Copy Azure AD Identifier from Set up, navigate to azure-idp in Cymmetri, and paste it in Entity ID. Similarly, copy the login URL and paste it into the Single Sign On Service URL in Cymmetri.
Replace the text "<host-name>" as the URL of the Cymmetri deployment (e.g., ) "aktestidp.ux.cymmetri.in" in the destination field - "https://<hostName>/spsamlsrvc/samlSP/SingleSignOnService" as "spsamlsrvc/samlSP/SingleSignOnService".
Open the Base64 certificate downloaded in step 12, copy it, and then paste it into the x509Certifcate field in Cymmetri.
Select the created service provider in the Service Provider Id field dropdown and save the changes.
For enabling Azure IDP to be used as an IDP for a specific set of users an Authentication Rule needs to be configured. you can see the steps on how to configure Authentication Rules.
Assigning users to applications in Azure Administration Console to allow users to use Azure as an External Identity provider
Navigate to Enterprise applications and select the application you created in step 8.
Go to Users and Groups, and select Add user/group and add the user.
If JIT provisioning needs to be enabled for Azure AD as external Identity provider, we may set it up using the steps below.
Navigate to JIT in external identity provider and enable JIT Configuration.
The following fields are mandatory in Cymmetri - firstName, lastName, login, userType, displayName, and email.
For Azure JIT configuration, the following mapping needs to be done -
First Name -
Application Field - http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname
Cymmetri Field - firstName
Last Name -
Login to cymmetri using Azure Email Address
The user will be redirected to the Azure portal to enter the Azure credentials.
Once the credentials have been entered properly in the Azure portal, the user will be redirected back to Cymmetri and will be logged in successfully.
The Application Detail Page provides comprehensive management features for applications within the system. It includes various sub-pages for configuring assignments, sign-on protocols, policies, provisioning settings, roles, and more. Below we outline the functionalities and configurations available on each sub-page.
This page allows administrators to assign users and groups to an application. Users or group members can access the application if it is configured for Single Sign-On (SSO) or get provisioned in the application if it is a provisioning application.
Features:
Assign users and groups to the application.
View and manage existing assignments.
Configures the application for sign-on using various protocols.
Supported Protocols:
SAML: Configure SAML-based single sign-on.
OpenID: Set up OpenID Connect for authentication.
Reverse Proxy: Configure reverse proxy settings for sign-on.
Configure Multi-Factor Authentication (MFA) for the application’s SSO settings.
Features:
Configure MFA prompts and policies.
Manage MFA settings to ensure secure access.
Configure application provisioning with various settings organized into tabs.
Tabs:
User Configuration: Define application attributes and settings for provisioning.
Server Configuration: Set up connector server parameters.
Operations: View provisioning operations supported
Create and manage application roles and import roles from CSV files.
Features:
Create new roles.
Import roles via CSV for bulk role creation.
Manage and edit existing roles.
Configure mapping between the provisioning source application and Cymmetri user fields.
Features:
Define and manage field mappings for data synchronization.
View data mappings for User Pull Reconciliation.
Ensure accurate data exchange between systems.
Configure general settings for the application. This section allows you to modify application label and description. You may also configure other settings as shown below:
This section lets you set application's risk which enables for identifying overall risks for users. The Risk level can be set to High, Medium, Low and Unknown
Administrator may configure visibility settings as shown below
Show to User: This setting when enabled lets the user see an application assigned to them.
User can request: This setting when enabled lets the user to request an application which is not assigned to the user.
Administrator may configure various role settings as shown below:
Multiple role assignments: which allows a user to have multiple roles in the said application and
Mandatory roles: This setting mandates that when the application is assigned atleast one role is assigned to the user
Add notes for end users and administrators.
This page lets you configure all the attributes from the provisioning source whose data needs to be synced on either sides.
Configure reconciliation settings for data synchronization.
Features:
Set up pull reconciliations to retrieve data from the source application.
Configure push reconciliations to update data in the source application.
Manage reconciliation schedules and tasks.
Configure dynamic forms used in workflows for additional data collection.
Features:
Create and manage dynamic forms.
Configure forms to collect data during workflow processes.
View and edit form data as required by administrators and users
Manage tags and meta information for applications.
Features:
Create and assign tags for categorization and search.
Add and manage meta information for various purposes.
Use tags and meta data to enhance application organization, search and categorization
Description: Provides a comprehensive reconciliation view for data synchronization across the system.
Features:
View detailed reconciliation data and statuses.
Analyze and resolve reconciliation issues.
This document provides a formal, step-by-step guide to configuring an AD integration with the Cymmetri platform. This integration allows Cymmetri to act as a central identity store, managing users and their attributes within the AD environment.
Before beginning the configuration, ensure you have the following:
Domain Administrator Credentials: A username and password for a AD account with full administrative privileges.
Domain & Controller Details: The Domain Name and the IP address or hostname of the AD domain controller.
SSL/TLS Certificates: For secure communication via port 636, the Certificate Authority (CA) certificate must be exported from the AD server and imported into the Cymmetri connector server. This ensures the communication channel is trusted and encrypted. Refer the link below for more details:
Network Access: Ensure that necessary ports (especially 636 for secure LDAPS communication) are open and accessible between the Cymmetri connector server and the AD domain controller.
Step 1: Configure your Active Directory Certificate and export it to Connector Server
Exporting your Active Directory certificate to the Connector Server is a necessary and crucial step. This ensures that the Active Directory and Cymmetri Identity Server can communicate over LDAPS (LDAP over SSL). For this to happen, LDAPS requires a properly formatted certificate installed in your Active Directory Domain Controllers. Please refer to this link and follow the same steps:
Once the certificate has been imported per the above instructions, you must restart the application to apply the changes made.
Step 2: Create the AD Application in Cymmetri
Navigate to the Identity Hub and select Application.
Click Create Application.
Search for "Active Directory" and select the appropriate application type.
Name the application "Simple AD" to easily identify it within Cymmetri.
Step 3: Create a Policy Map
The policy map defines the attribute mapping between Cymmetri and AD. This is crucial for synchronizing user data correctly.
Go to the Policy Attribute section.
Review the pre-filled, standard attribute mappings (e.g., sAMAccountName to login, givenName to firstName, mail to email).
Add any new or custom attributes by clicking Add new, entering the attribute name and description, and saving.
Step 4: Configure User & Server Settings
This two-part step establishes the connection parameters and user search criteria.
User Configuration:
Principal & Principal Password: Enter the credentials of the domain administrator account. This account is used by Cymmetri to connect to AD.
Server Hostname: The IP address or hostname of the AD domain controller.
User Entry Searches & Base Contexts: Define the LDAP search queries and organizational units (OUs) that Cymmetri will use to find users and groups within AD.
Click Save Configuration and then Test Configuration to verify a successful connection.
Server Configuration:
Server Hostname: The hostname of the Cymmetri connector server.
Server Password: The password for the connector server.
Server Port: The port number for communication (e.g., 636 for secure LDAPS).
Connector Bundle Name & Version: The name and version of the Cymmetri connector bundle, which facilitates communication with AD.
Click Save Configuration, then Test Configuration.
Step 5: Perform a Reconciliation (Push)
A Push Reconciliation is the process of synchronizing user data from Cymmetri to the AD target system.
Navigate to Reconciliation.
Select the Push option.
Click Add New to create a new push reconciliation job.
Configure the job settings and execute it.
Monitor the job status by navigating to Recon History.
Step 6: Verify Reconciliation in AD
To confirm that the push reconciliation was successful, verify the user data directly within the AD target system.
Use Remote Desktop Protocol (RDP) to connect to the AD server.
Enter the computer credentials (IP address and password) to connect.
Once logged in, open the Active Directory management console.
Right-click on the domain and use the Find function to search for the user who was pushed from Cymmetri. If the user appears with the correct attributes, the reconciliation was successful.
Google Workspace is a software-as-a-service platform (SAAS) that provides email, calendar, documents and other services. This connector uses the Google Workspace provisioning APIs to create, add, delete and modify user accounts and email aliases.
Note: 1. Only the Premium (paid) or Educational versions of Google Workspace provide access to the provisioning APIs. 2. Connector will not work on the free Google Workspace Domain
For Configuring Google Workspace for provisioning we need to first obtain the client_secret.json file from the Google Workspace instance.
Go To and create a new Project if not already created. A new project needs to be created because it allows you to manage the credentials required to access Google APIs and services securely. A new project can be created by clicking on the New Project on top right or by clicking on the the Resource Dropdown
And the on the NEW PROJECT link on top right
Next enter the Project name and select Organisation and Location as shown below and click on CREATE button
The Admin SDK API is needed to programmatically manage and interact with various aspects of a Google Workspace domain, such as users, groups, organizational units, and settings. Here are some key reasons why the Admin SDK API is essential:
User Management: The Admin SDK API allows you to create, retrieve, update, and delete user accounts in your Google Workspace domain. You can manage user details such as name, email address, password, and organizational unit.
Group Management: You can create, retrieve, update, and delete groups within your Google Workspace domain using the Admin SDK API. This includes managing group members and settings.
Organizational Unit Management: The API enables you to manage organizational units (OUs) within your Google Workspace domain. You can create, retrieve, update, and delete OUs, as well as move users and groups between OUs.
To enable ADMIN SDK API click on Enabled API & Services and Search for Admin SDK API:
Click on Admin SDK API and then click on the Enable button
Once enabled, Click on CREDENTIALS tab
Now click on Credentials section and click on CREATE CREDENTIALS button and in that select OAuth client ID option
Select Desktop app as Application type, provide a name for the OAuth 2.0 client and then click on the CREATE button
A response screen is visible that shows that the "OAuth client created" It also displays Your Client ID and Your Client Secret. You may download the JSON here using the DOWNLOAD JSON option.
Click on OAuth consent screen and then Click on EDIT APP. Enter the required details and Click on SAVE AND CONTINUE button
Select Internal as User Type if you want to restrict access only to the users of your organization.
Search for Admin SDK API on the Scopes screen and select scope for user: .../auth/admin.directory.user
Select the scope for group: .../auth/admin.directory.group
Next Click on Credentials section and downlaod OAuth client json file on your local machine by clicking on the Download OAuth client button.
Next download thebundle for Google Workspace from the Connector Server website. Once downloaded open a new command prompt and change to the directory where you have downloaded the bundle and run the following command on the client_secrets.json file that you obtained earlier step:
This command opens the default browser, and loads a screen on which you authorize consent to access the Google Apps account. When you have authorized consent, the browser returns a code. Copy and paste the code into the terminal from which you ran the original command
A response similar to the following is returned.
Once the above information is obtained we need to configure the Google Workspace in Cymmetri with Server Configuration and User Configuration as shown below:
Once the configuration is done click on TEST CONFIGURATION button to check if the configuration is working.
Once the test is successful next go to the Assigments section and assign the application to a user as shown below:
Once assigned ensure that the user is created in Google Workspace.
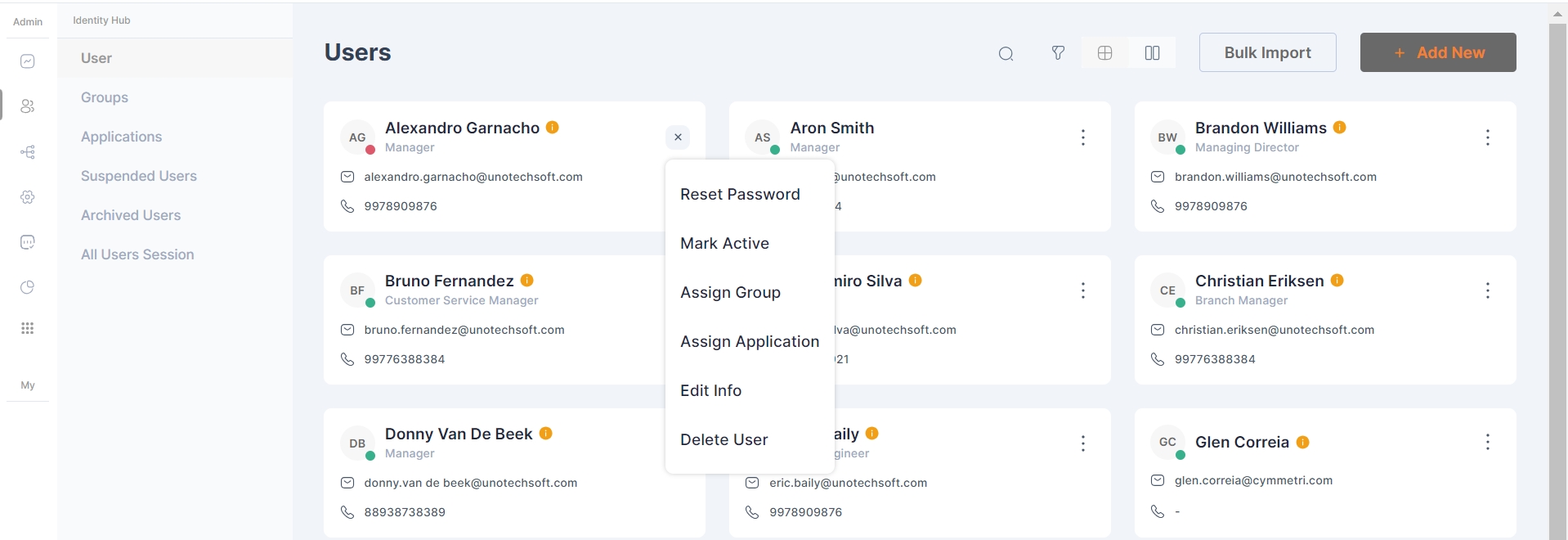
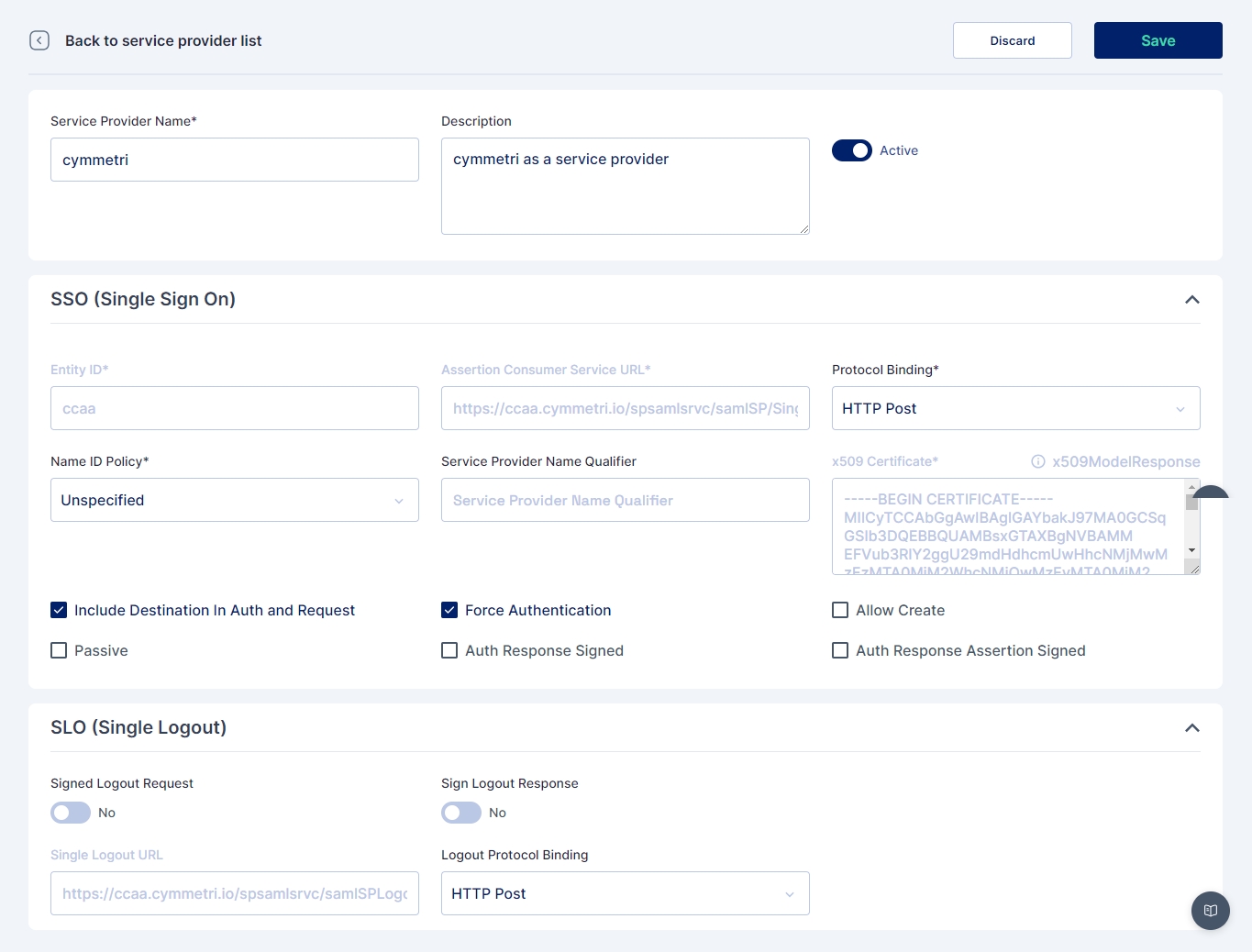
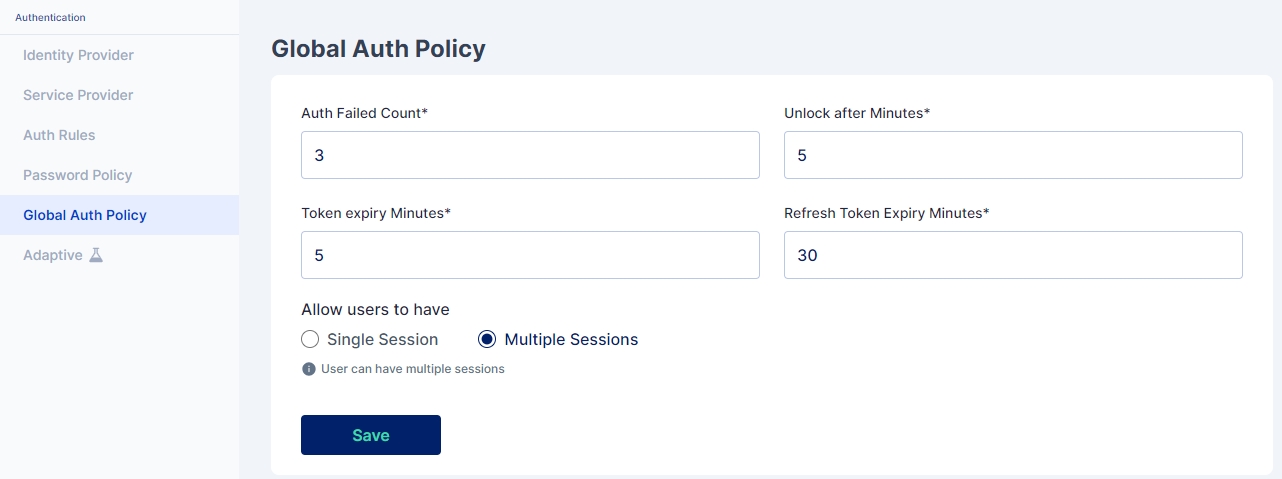


Masters are key-value pairs that can be defined for the entire tenant. The key(name) in this context refers to the label to be shown on the Cymmetri User Interface, and the value is the backend identifier used to reference this field in various processes, rules, and policies defined in the Cymmetri platform.
Cymmetri platform allows for configuring several masters in the system, the major classification among which are Global masters (which allow for creating master key-value pairs that may be used for various situations, such as creating a new department, designation, and other custom attributes for users in the system) and Zone masters (which are network configurations that may be used to whitelist or blacklist user access onto the platform as well as act as a source for adaptive Multi-factor authentication).
The Cymmetri Architecture without the password filter utility allows for one-way synchronization of passwords from Cymmetri to managed applications like Active Directory. Active Directory passwords may therefore be updated, once the user password is updated in Cymmetri.
However, to keep both the Cymmetri database and Active Directory user passwords in synchronization, there is a need for Cymmetri database to receive password change notification from the Active Directory, when the password is directly updated in Active Directory.
Active Directory provides for the use of Password Filter which can intercept the request for password change and can make an API call to Cymmetri to update the password in Cymmetri database as well.
LDAP, or Lightweight Directory Access Protocol, is a protocol for accessing and managing directory services over a network. It provides a centralized, hierarchical way to store and authenticate identity-related information like user accounts, groups, and organizational data. This document outlines the formal steps to configure a Simple LDAP application in Cymmetri used for LDAP Provisioning.
Before beginning the configuration, ensure you have the following:
LDAP server login credentials: Specifically, the Bind DN and password.
{
"type": "object",
"required": [
"preferredName"
],
"properties": {
"preferredName": {
"type": "string",
"title": "Preferred Username",
"default": ""
},
"additionalModules": {
"type": "string",
"title": "Additional Modules",
"enum": [
"admin",
"readonly"
],
"enumNames": [
"Administrator",
"Read-Only"
],
"default": ""
}
}
}{
"preferredName": {
"placeholder": "Enter preferred name",
"maxLength":5
},
"additionalModules": {
"ui:widget": "radio"
}
}Workflow Inbox will now include start date and end date filters.
Manager assign Import
Manager Link Import
Manager gets a link while the user imports using csv.
Also manager assignment from UI
Added a new recon failure notification template.
Self-service Side
List Exception Applications
Request Exception Application functionality
Workflow integration and dashboard for exception requests.
Exception workflow configuration and invocation of the workflow for exception application access requests.
Zoho Books
Zoho Expenses
General Config based role data type
Provided support for integer values for ROLE assignment through Amaya.

























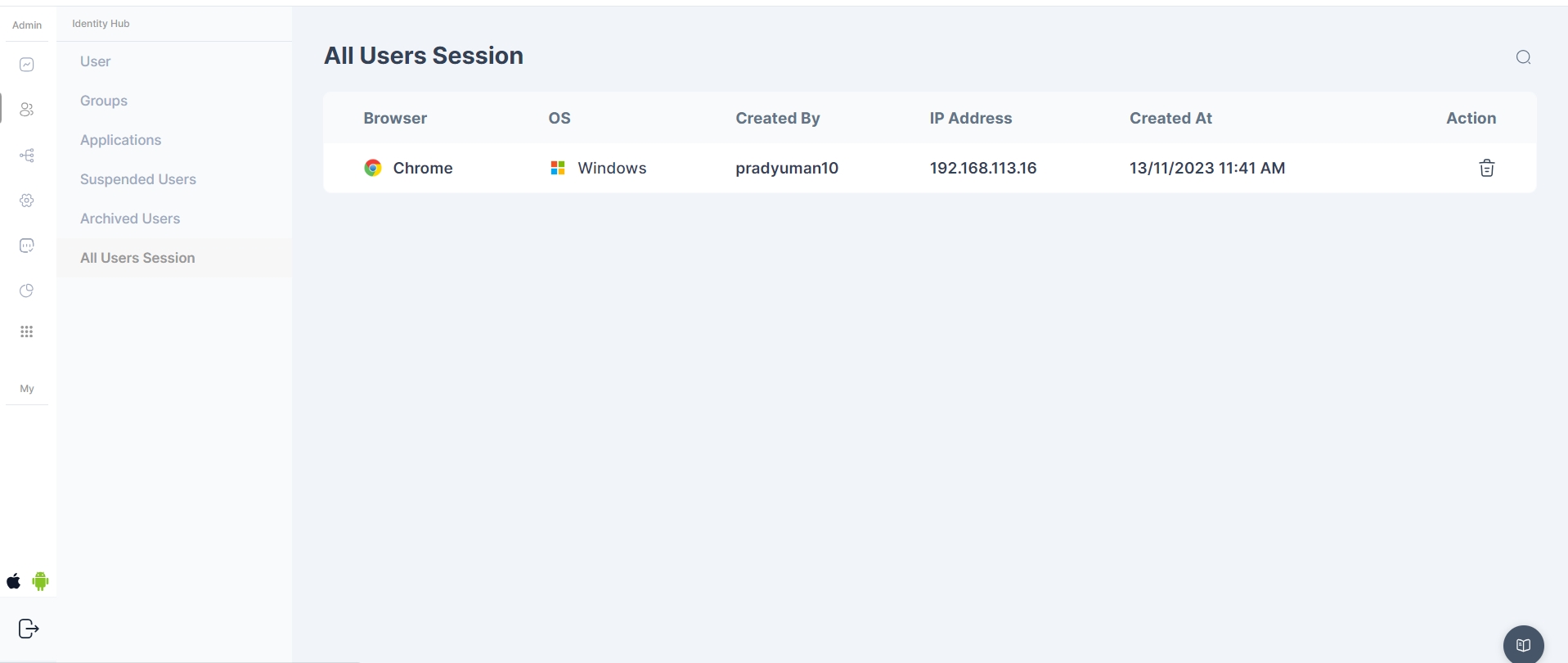
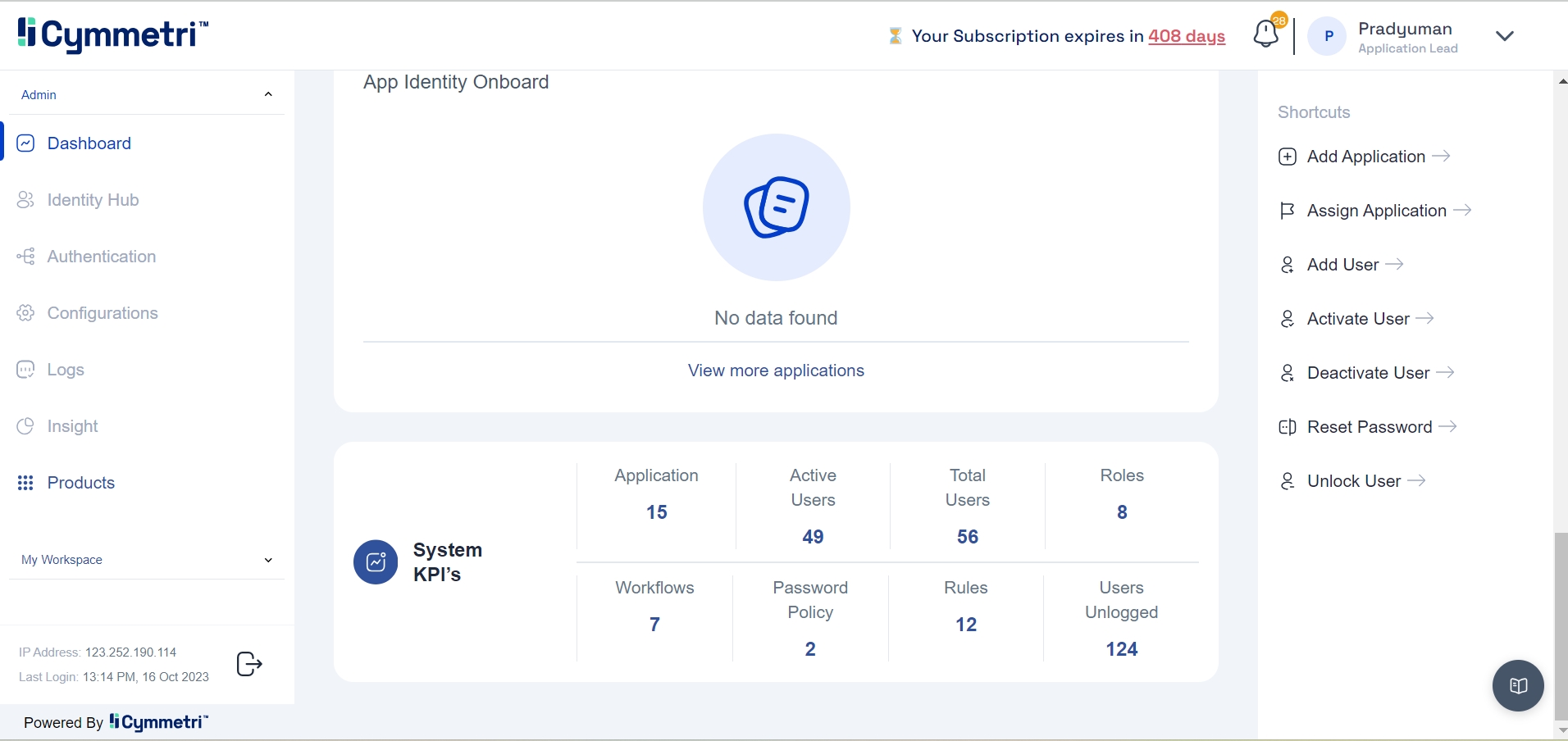
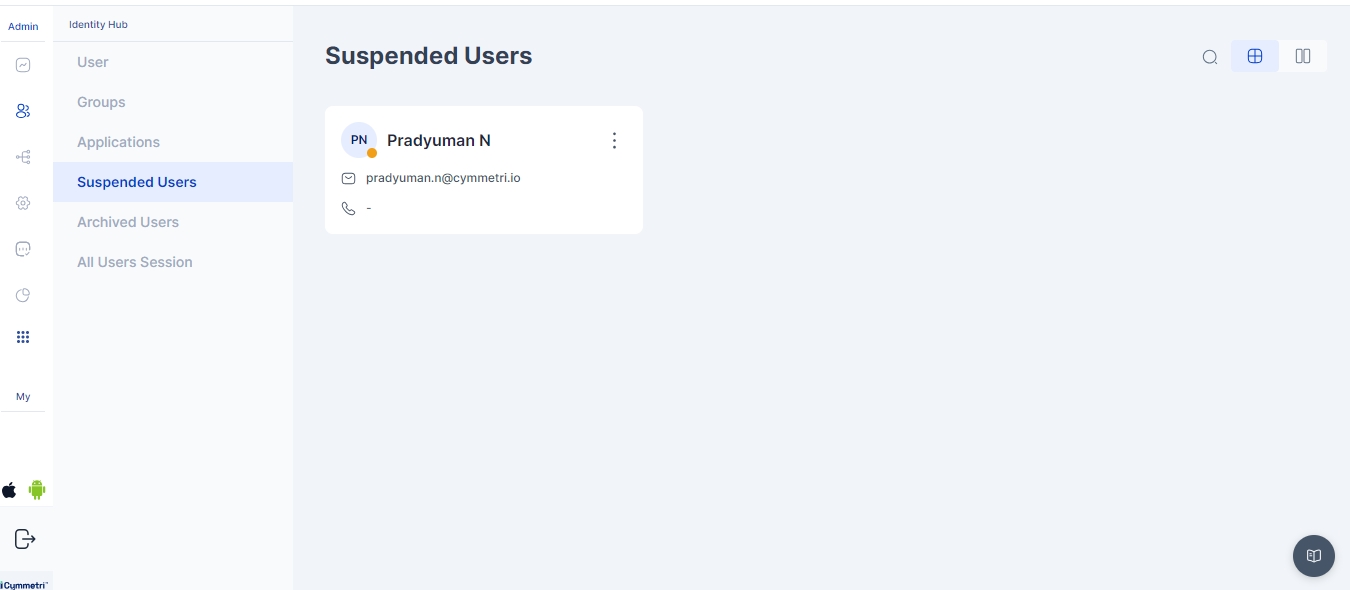
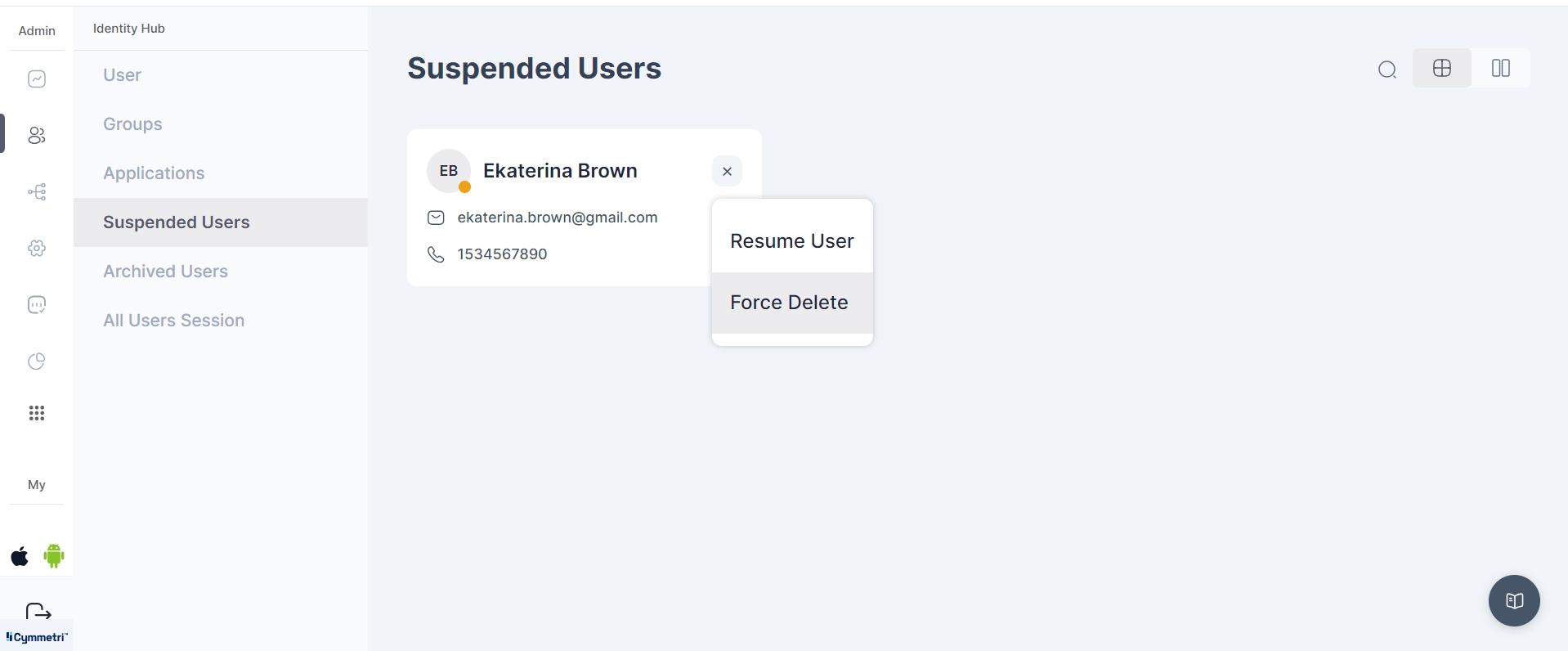
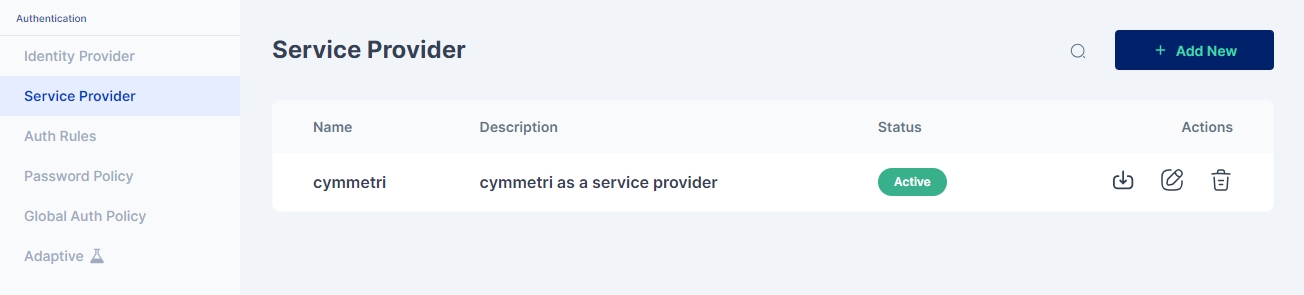
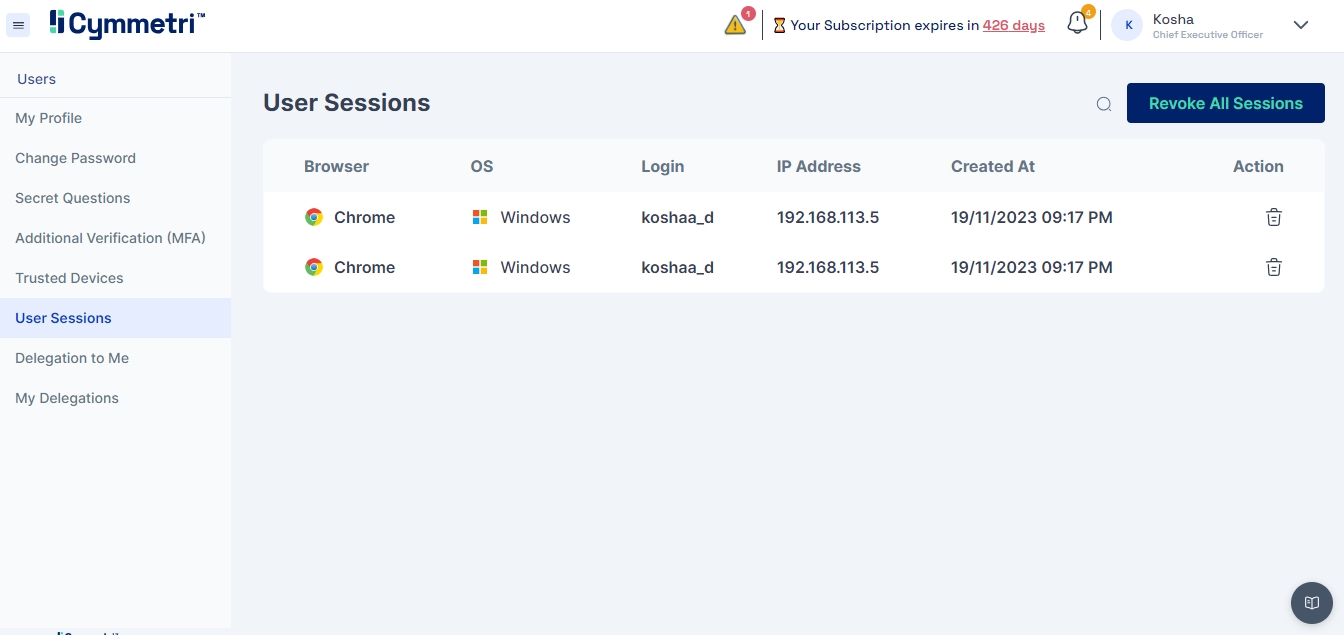
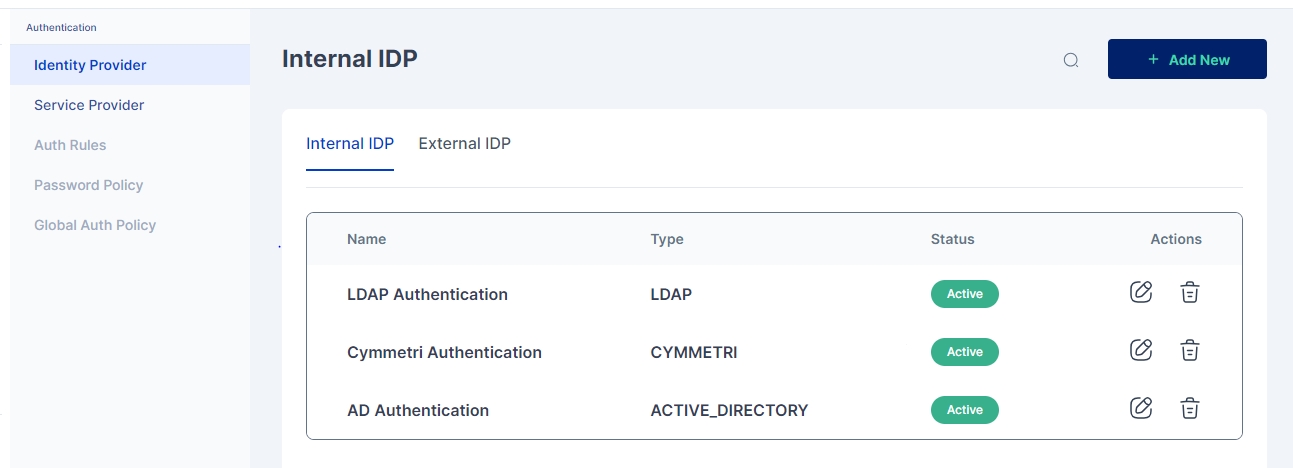
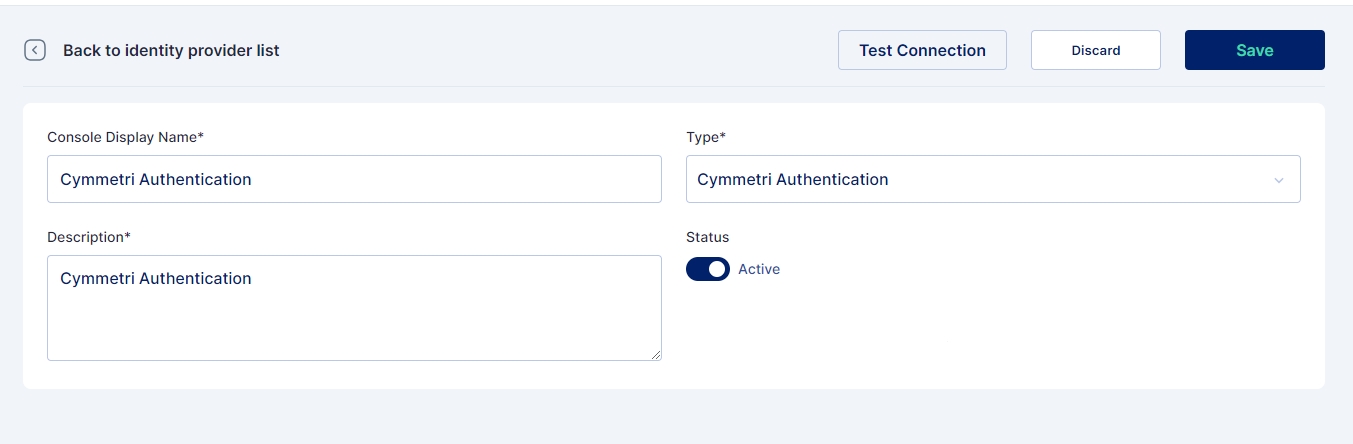
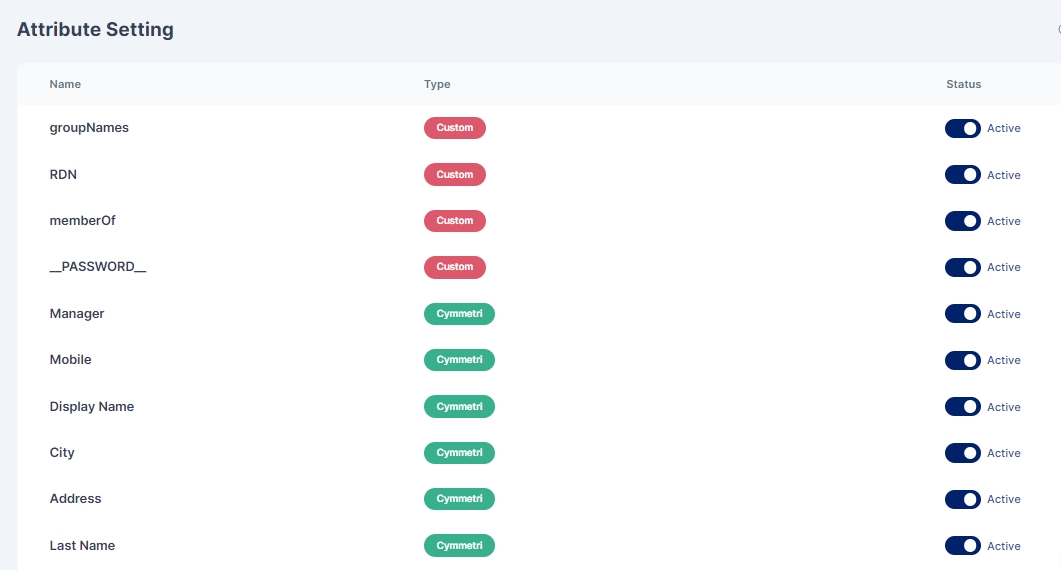
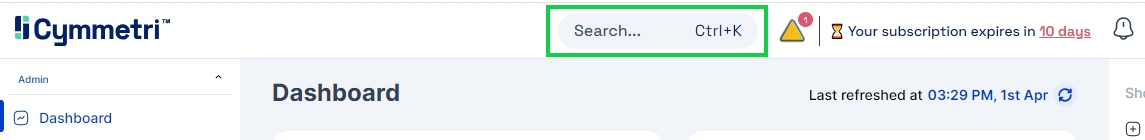
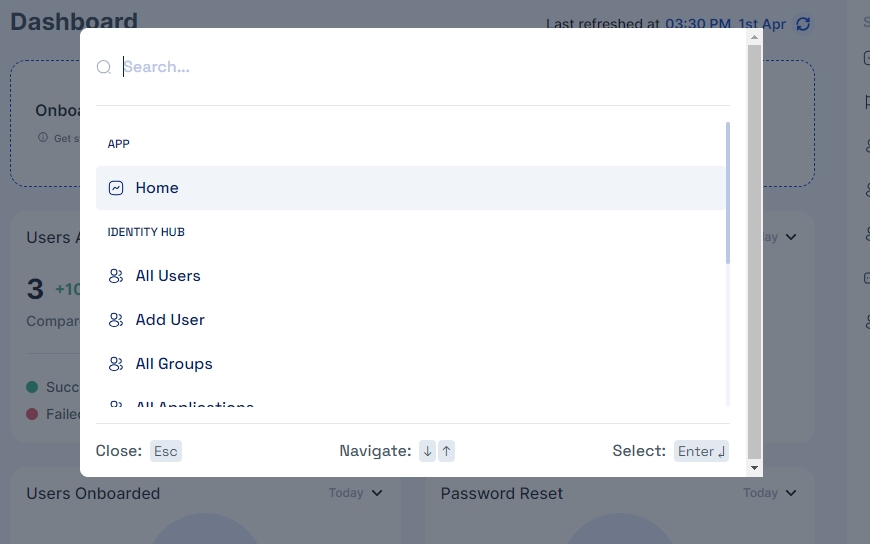
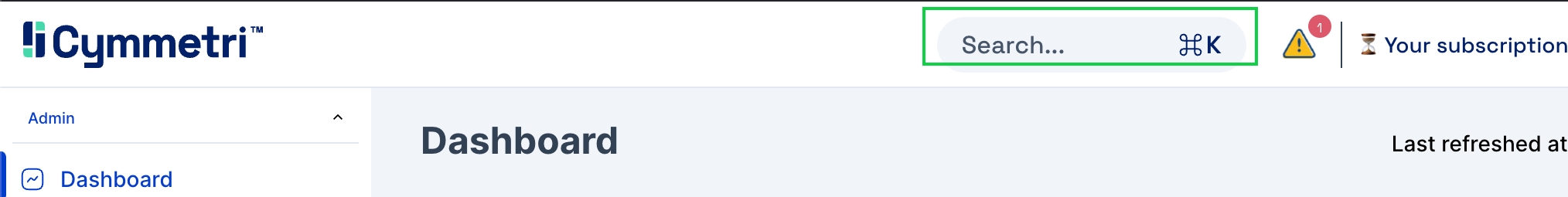
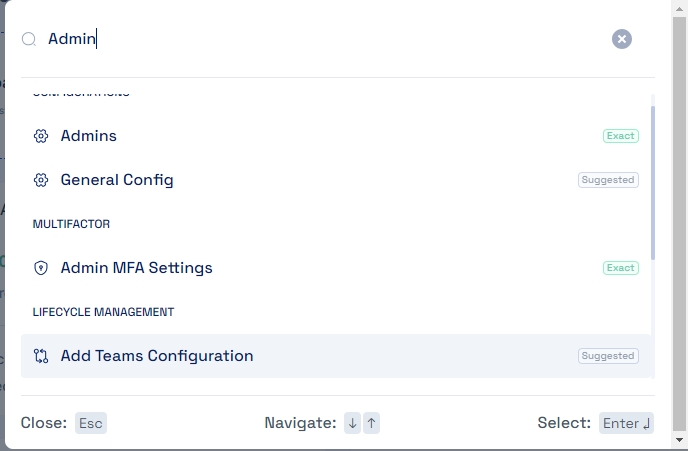
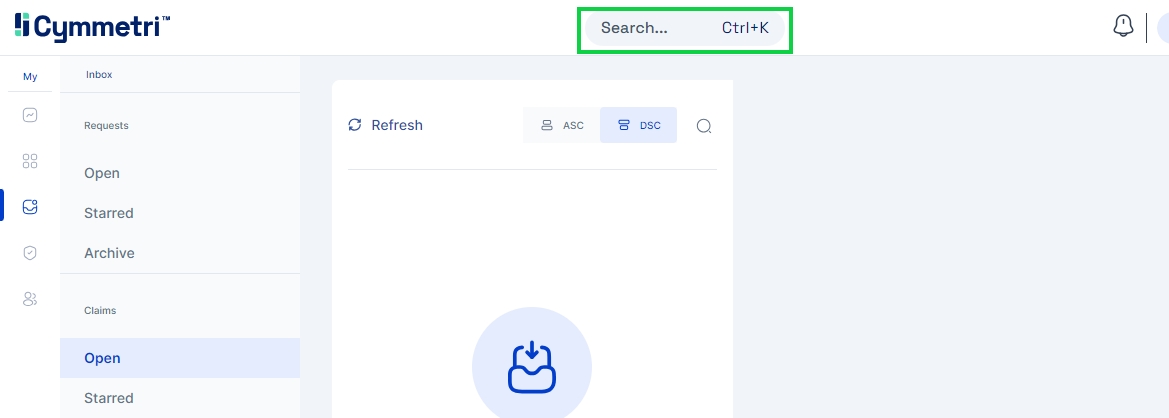
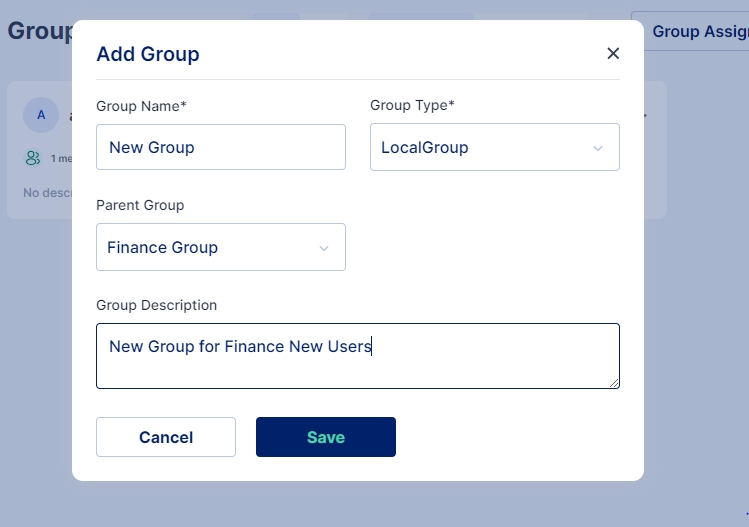
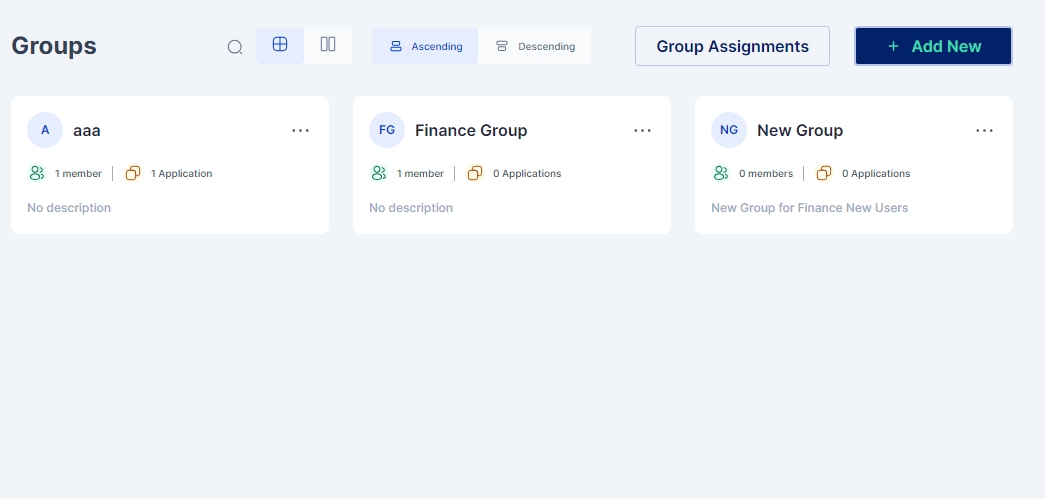
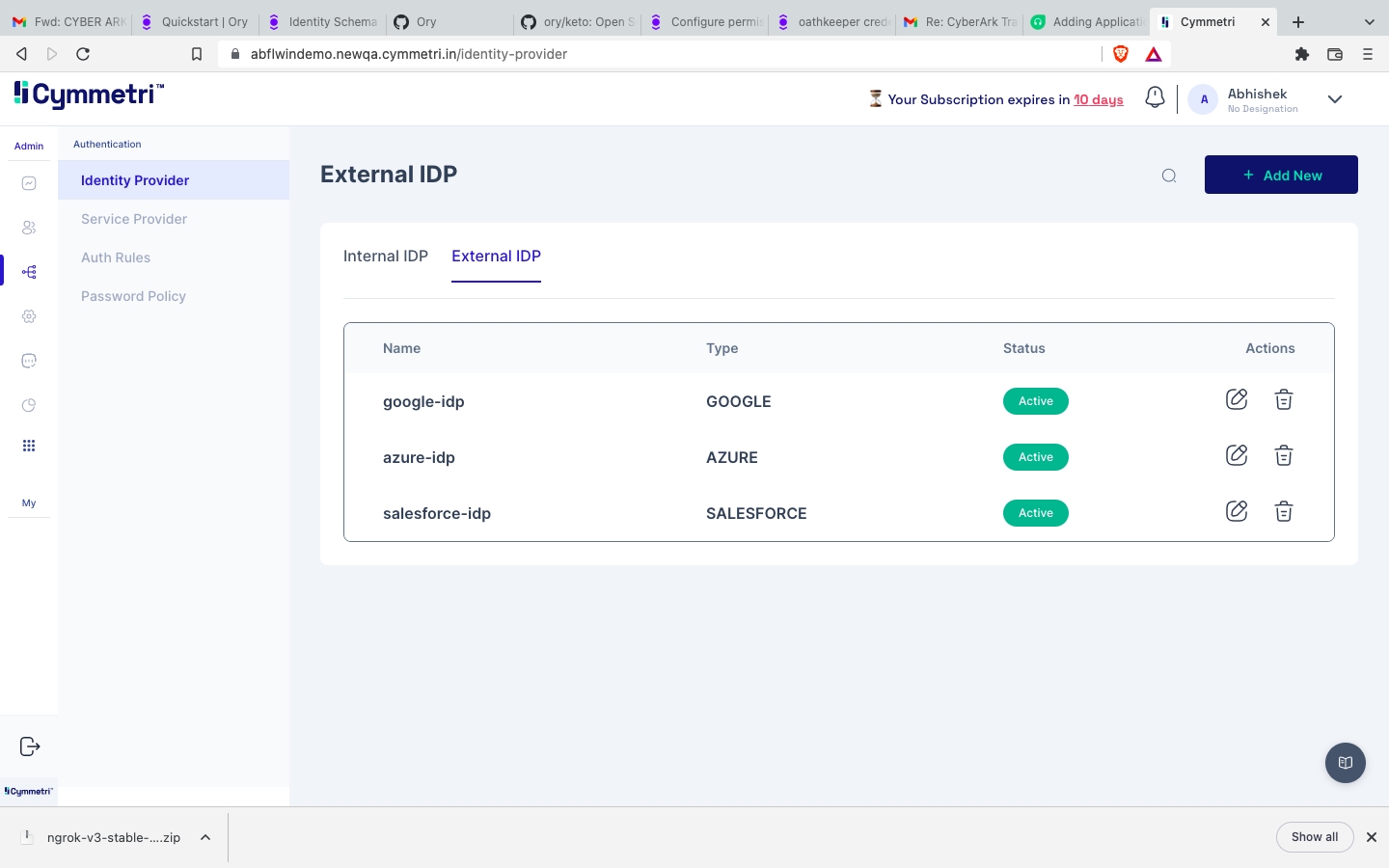
Application Field - http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname
Cymmetri Field - lastName
Login (Username) -
Application Field - http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name
Cymmetri Field - login
User Type -
Application Field - any string
Cymmetri Field - userType
Default Value - <will be one of Employee, Vendor, Consultant>
Display Name -
Application Field - http://schemas.microsoft.com/identity/claims/displayname
Cymmetri Field - displayName
Email Address -
Application Field - http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name
Cymmetri Field - email
API SSO: Set up API-based single sign-on.
Features:
Protocol selection and configuration.
Test and validate sign-on settings.
Manage sign-on settings for different environments.
Hook Configurations: Configure hooks for triggering provisioning actions.
Features:
Manage and configure provisioning details.
View and edit provisioning settings.
Monitor provisioning operations.
Ensure roles are correctly provisioned in target applications.
Settings Management: You can manage various domain-wide settings, such as email routing, calendar sharing settings, and device management settings, using the Admin SDK API.
Security and Compliance: The API provides features for managing security and compliance settings within your Google Workspace domain, such as 2-step verification, password policies, and audit logs.
Country
Country key-value pairs are stored in the system, and are available as drop-downs wherever needed in the system - User attributes, Policies and other mappings.
UserType
UserType is used as one of the conditions while defining authentication policies and as an input in the rule engine.
Department
Department is used as one of the conditions while defining authentication policies and as an input in the rule engine, and also as a user attribute.
Designation
Designation is used as one of the conditions while defining authentication policies and as an input in the rule engine, and also as a user attribute.
RBAC
RBAC (System Roles) is used as one of the conditions while defining authentication policies and as an input in the rule engine, and also as a user attribute.
Follow the steps below to Add a New Master:
Click on the "+Add New" button to add a new master of any category mentioned above.
Enter the Name and Value for the new Master, then select the type of master you wish to create and enable the active toggle button to make the master active. Once all values are entered, click on the Save button
A new Global Master is successfully created in the selected category
The RBAC Master allows the maintenance of role entitlements for the organization.
Zone masters indicate the network zones that may be used for blacklisting or whitelisting access to the Cymmetri Identity platform deployment. It may also be used for detecting users from certain zones and assigning relevant multi-factor authentication policies.
Zone Name: Used to refer to a zone in other configurations on the Cymmetri platform.
Inactive/Active: Toggle button to check whether the zone is active (configurable as a condition for other rules on the Cymmetri platform).
Gateway IP: Refers to the Gateway IP address for the network zone.
Proxy IPs: Proxy Server IP addresses that may be used to direct to this network or the IP addresses outside of the zone that would indicate a connection from this zone.
CIDR: Refers to the CIDR notation of the subnet of the network that this zone refers to. CIDR Notation.
For adding a new Zone Master or for editing an existing one, fill in all the mandatory details on the screen as shown above, click on the enable toggle button, and finally click the “Save” button.
A sample is shown below :
Note: This screenshot shows sample/test data only and must not be used in production
The Grade Master is a Global Master used to define numeric grades that categorize employees and establish hierarchical precedence. Grades are critical for building approval matrices in workflow rules that depend on organizational levels. Here we define Grade Values (numbers) and associated Labels (descriptions).
Numeric grades allow clear precedence ordering.
Lower numbers usually represent higher precedence (e.g., Grade 1 = Director).
Easy comparison (e.g., Grade 2 > Grade 3) makes it suitable for workflows.
Avoids ambiguity that text-only labels would create.
Grade Value
Numeric value representing the grade. Determines precedence logic. Must be unique.
Yes
Label
A descriptive label for the grade (e.g., “Manager”, “Executive”).
Yes
Status
Active / Inactive toggle. Only active grades can be used in workflows.
Yes
Go to Admin → Configurations → Masters → Grade.
The Grade Master page displays a list of existing grades with:
Precedence (from Grade Value)
Grade Value
Label
Status
Actions (Edit option)
Click + Add New.
Enter Grade Value (numeric).
Enter Label.
Set Status (Active/Inactive).
Click Save.
Click the Edit icon.
Update Grade Label, or Status.
Save changes.
Keep Grade Values numeric and unique.
Align numbers with your organizational hierarchy (e.g., 1 = most senior).
Use meaningful labels for clarity.
Set obsolete grades to Inactive rather than deleting them.

Cymmetri Password Filter dll will be deployed in the Active directory environment and system variables (environment variables) are configured to allow the password filter to connect to the Cymmetri deployment.
Active Directory server needs to be restarted once the configuration is performed.
Once the user changes the password on a domain-connected computer using Ctrl+Alt+Delete utility OR if the Active Directory administrator resets the user's password using Active Directory tools, the password filter will be triggered.
The password filter DLL will receive the username and the plaintext password from the Active Directory, once the password change has been applied on the Active Directory.
The password filter DLL will encrypt the password using RSA encryption with a public key and will send the encrypted password and the username to the Cymmetri deployment using a REST API call over HTTPS.
The Cymmetri deployment receives the username and encrypted password, it decrypts the password using private key.
Once the password is decrypted, the Cymmetri deployment updates the password in Cymmetri database for the given user.
If the user is assigned multiple applications for provisioning, the action of updating user's password in Cymmetri database will trigger password update for the user in other provisioned applications. However, Active directory application will not receive this password update, to avoid loops.
CYMMETRI_APP_ID
<application-id-of-active-directory-in-Cymmetri>
CYMMETRI_CLIENT_TOKEN
Authorization: Bearer <token-from-api-client>
CYMMETRI_ENDPOINT_URL
https://<cymmetri-domain>/apiext/api/password/filter/updateUserPassword
CYMMETRI_PUBLIC_KEY_FILE
<path of public key file in Active Directory Server>
Download the dll file and the public key file from here - CPFv308.dll - https://drive.google.com/file/d/15uPQYnJr7HUWnxHLPSpYtsWGKkm5HnLC/view?usp=share_link public.pem - https://drive.google.com/file/d/1OdBLal4RTA5bMqABJEq3zQeLxNzSOE0R/view?usp=share_link
Place the CPFv308.dll file in the C:\Windows\System32 folder.
Run regedit and go to the following path: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa
You must now see a page similar to this:
Select the element Notification Packages and double click it
Add the line “CPFv308” and Click on OK to save the registry entry.
Exit the registry editor.
Save the public.pem file to any directory and note the name of the directory. Ex - C:\Users\Administrator\Desktop\public.pem
For testing the deployment, Login into the Cymmetri portal as an administrator and note the application ID of the Active Directory application configured for provisioning. Ex - 69125912519fb123
Also, create a new API client.
Click on renew secret and note the bearer token generated.
Ex - eyJhbGciOiJIUzI1NiJ9.eyJzdWIiOiJOZXcgQVBJIENsaWVudCIsInRlbmFudCI6IjI3NyJ9.L_q7I4MFcZSFXetdSvzD7hxvfcSrUUaJEkwhUTfHgus
Go to Control Panel > System > Advanced System Settings and click on environment variables.
Add the following System variables.
Key = CYMMETRI_APP_ID; Value = <application-id-of-active-directory>; Example = 6015991fdfeab12c
Key = CYMMETRI_CLIENT_TOKEN; Value = Authorization Bearer <token-from-api-client>; Example = Authorization: Bearer eyJhbGciOiJIUzI1NiJ9.eyJzdWIiOiJOZXcgQVBJIENsaWVudCIsInRlbmFudCI6IjI3NyJ9.L_q7I4MFcZSFXetdSvzD7hxvfcSrUUaJEkwhUTfHgus
Key = CYMMETRI_ENDPOINT_URL; Value = <domain>/apiext/api/password/filter/updateUserPassword; Example =
Key = CYMMETRI_PUBLIC_KEY_FILE; Value = <path of public.pem file>; Example = C:\Users\Administrator\Desktop\public.pem
Save the environment variables.
Create a folder as C:\passfilter_logs to store the logs.
Take a restart of the Active Directory Server.
Navigate to the Configuration Menu.
Look for the Password Filter option in the Configuration Menu.
Once on the page click on "+Add New" button
This will open the configuration page, You should find a toggle button to enable the Password Filter. Turn it on to enable the filter.
Once the Password Filter is enabled, you'll need to choose the filter type.There are two options: "Include" and "Exclude."
"Include" means that only the applications selected in the included applications dropdown will receive synced passwords and have their passwords changed correspondingly.
"Exclude" means that all applications except the ones selected in the excluded applications dropdown will receive synced passwords and have their passwords changed correspondingly.
Next you select the Filtered Application this is usually the managed application where the password changed has happened which in this case is Active Directory
Next, determine which type of authenticator you want to use for password synchronization.
You typically have three options: Cymmetri Authenticator, AD (Active Directory) Authenticator, or LDAP (Lightweight Directory Access Protocol) Authenticator.
Choose the appropriate authenticator based on your requirements and configuration.
After completing the above steps, make sure to save your configuration settings.Click on the "Save" button to save your changes.
LDAP server access: To configure and test connections.
SSL/TLS certificates: Required for secure connections using LDAPS (LDAP over SSL). The LDAPS port (typically 636) must be enabled, and the CA certificate must be exported from the LDAP server and imported into the connector server.
Key information needed for the configuration includes:
Server Hostname and Port: The address of the LDAP server and the port for communication (e.g., 636 for LDAPS).
Base DN (Distinguished Name): The starting point for all searches within the directory hierarchy (e.g., dc=example,dc=com).
OU (Organizational Unit) name: The name of the specific organizational unit you are targeting.
Navigate to Identity Hub → Application.
Click Create Application and search for "Simple LDAP."
The policy map defines which attributes are fetched from your LDAP directory.
Go to the Policy Attribute section. The table is pre-filled with common LDAP attributes, but you can add new ones.
cn (Common Name): The full name of the user.
uid (User ID): A unique user identifier.
sn (Surname): The user’s last name.
Standard Attribute Mapping:
The following mappings are typically used for provisioning:
telephoneNumber → mobile
cn → login
givenName → firstName
mail → email
sn → lastName
cn → firstName
Adding New Attributes:
Click 'Add new'.
Enter the attribute name and description, then click Save.
Toggle the Active switch to enable the new attribute.
In the same window, go to the Policy Map option.
Map each LDAP attribute to its corresponding Cymmetri user attribute. By default, the mapping is set to false and needs to be manually configured.
This section defines how Cymmetri searches for and interacts with user entries in LDAP.
Navigate to User Configuration.
Enter the Root Suffixes.
Provide the Principal Password.
Enter the Base Contexts for group entry searches.
Enter the Server HostName.
Enter the Principal (the Bind DN)
Enter the User Entry Searches.
Click Save Configuration and then Test Configuration to verify a successful connection.
This section defines the connection parameters for the connector server.
Enter the Server Hostname.
Enter the Server Password.
Enter the Server Port.
Enter the Server Connector Bundle Name.
Enter the Server Connector Bundle Version.
Enter the Server Connector name.
Click Save Configuration and then Test Configuration.
Step 6: Execute Push Reconciliation on LDAP
Click on Reconciliation, select push, and click on add new
Configure Push Recon Configuration
Click On Run Recon and View in History
Click on the View Icon to see the Progress and the result of reconciliation
View in Reconciliation History
Step 7: View Reconciliation Push User in the LDAP Target System
Go to http://10.0.6.17/phpldapadmin and enter the required credentials.
Select the required server
Click on search and verify in the search filter by entering its value
iOS
NA
Mac OS
NA
Windows
Chrome
66
Edge
16
Firefox
57
Opera
57
Safari
53
Chrome Android
12.1
Firefox Android
66
Opera Android
57
Safari iOS
47
Samsung Browser
12.2
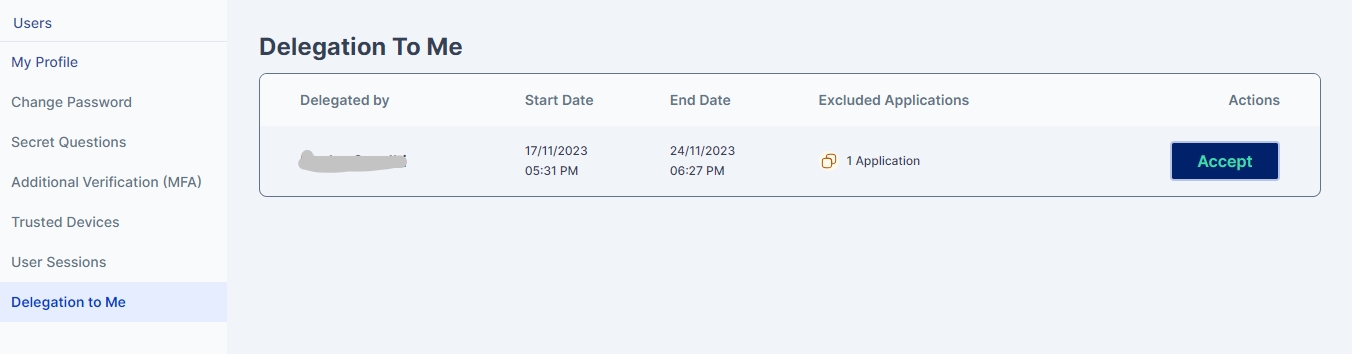
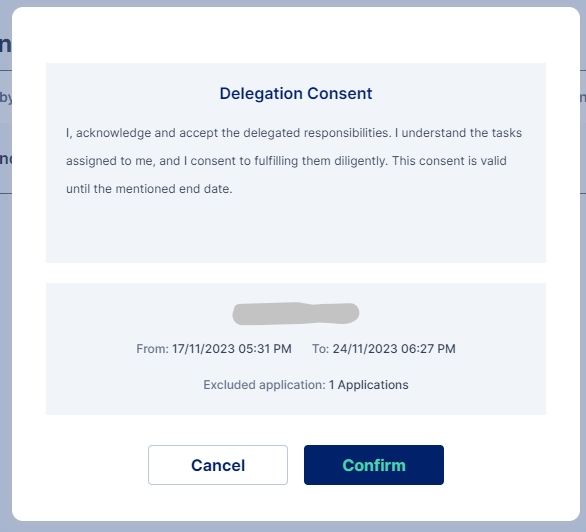
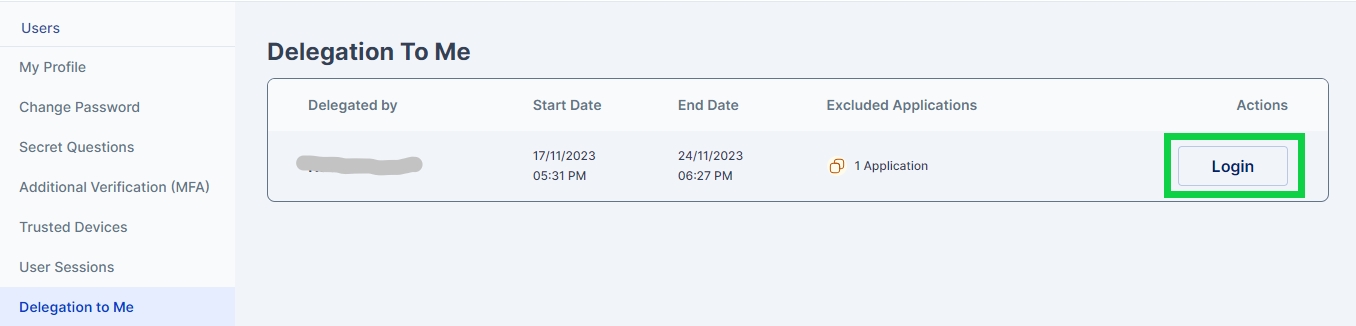
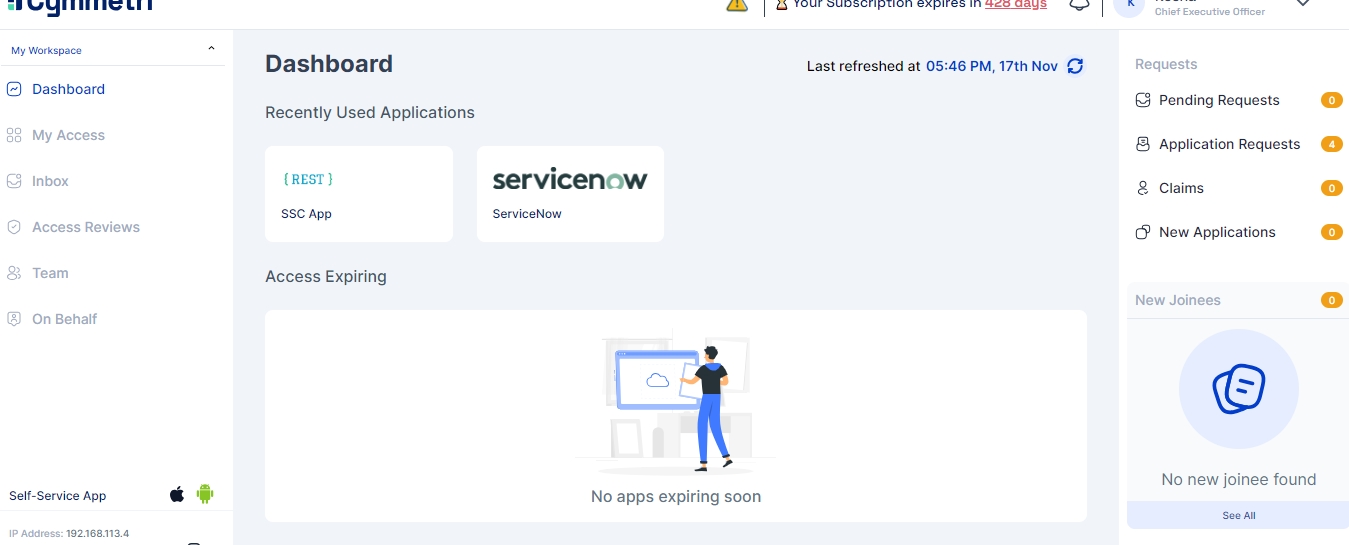
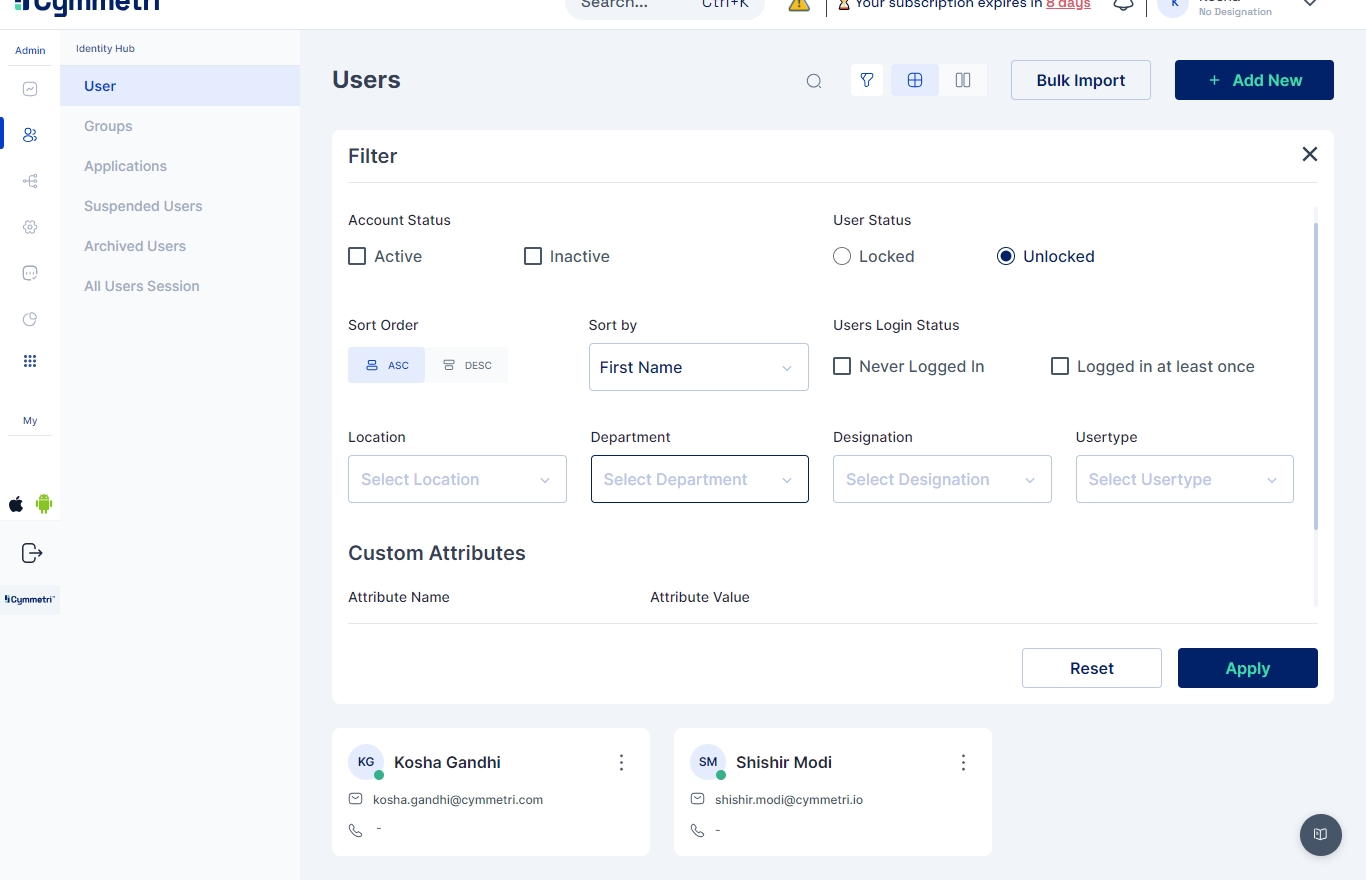
Connectors can be deployed in two ways:
Local connectors are deployed to a Cymmetri instance. This is the usual way how connectors are used. The connector is executed inside a Cymmetri instance, has the same lifecycle (start/stop), etc. Cymmetri can detect local connectors automatically and overall the connector management is easier.
Remote connectors are executed in a different process or on a different node than Cymmetri instance. Remote connectors are deployed to a connector server. There may be need to use a remote connector e.g. to access a file on a remote system (e.g. in case of CSV connector) or because of platform incompatibilities (e.g. .NET connectors)
Connector is not developed as local or remote. The placement of the connector is a deployment-time decision. There is just one connector package that can be deployed locally or remotely.
A connector server is required when a connector bundle is not directly executed within your application. By using one or more connector servers, the connector architecture thus permits your application to communicate with externally deployed bundles.
Connector servers are available for both Java and .NET.
A Java connector server is useful when you do not wish to execute a Java connector bundle in the same VM as your application. It may be beneficial to run a Java connector on a different host for performance improvements if the bundle works faster when deployed on the same host as the native managed resource. Additionally, one may wish to use a Java connector server under a Java remote connector server in order to eliminate the possibility of an application VM crash due to a fault in a JNI-based connector.
The use of .NET connector server is especially useful when an application is written in Java, but a connector bundle is written using C#. Since a Java application (e.g. J2EE application) cannot load C# classes, it is necessary to instead deploy the C# bundles under a .NET connector server. The Java application can communicate with the C# connector server over the network, and the C# connector server serves as a proxy to provide to any authenticated application access to the C# bundles deployed within the C# connector server.
Minimum Requirements:
Java 1.6 or later for 1.4.X.Y / Java 1.8 for 1.5.X.Y
Refer to your Java connectors to determine if there are any additional requirements
Download the Connector Server package
From the directory created above, run the Java connector server with no arguments to see the list of command-line options:
Linux / MacOS: ./bin/ConnectorServer.sh
Windows: \bin\ConnectorServer.bat
You should see the following output:
Run the connector server with the setkey option as described below to set your desired key into your properties file
Linux/ MacOS: ./bin/ConnectorServer.sh -setkey <key> -properties conf/ConnectorServer.properties
Windows: bin\ConnectorServer.bat /setkey <key> /properties conf\ConnectorServer.properties
Run the server by launching with the -run option:
Linux / MacOS: ./bin/ConnectorServer.sh -run -properties conf/ConnectorServer.properties
Windows: bin\ConnectorServer.bat /run -properties conf\ConnectorServer.properties
To deploy a Java connector:
Copy the Java connector bundle jar file into the bundles directory in your Java connector server directory
If necessary, add to the classpath any 3rd party jars required by any Java connector
Restart the Java connector server
The following steps are necessary to successfully communicate with a connector server using SSL:
Deploy an SSL certificate to the connector server's system.
Configure your connector server to provide SSL sockets.
Configure your application to communicate with the communicate with the connector server via SSL.
Refer to your application manual for specific notes on how to configure connections to connector servers. You will need to indicate to your application that an SSL connection is required when establishing a connection for each SSL-enabled connector server.
Additionally, if any of the SSL certificates used by your connector servers is issued by a non-standard certificate authority, your application must be configured to respect the additional authorities. Refer to your application manual for notes regarding certificate authorities.
Java applications may solve the non-standard certificate authority issue by expecting that the following Java system properties are passed when launching the application:
javax.net.ssl.trustStorePassword
For example, -Djavax.net.ssl.trustStorePassword=changeit
javax.net.ssl.trustStore
For example, -Djavax.net.ssl.trustStore=/usr/myApp_cacerts
Or, instead, the non-standard certificate authorities may be imported to the standard ${JAVA_HOME}/lib/security/cacerts.
Minimum Requirements:
Windows Server 2003 or 2008
.NET Framework 3.5 or higher
Refer to your .NET connector to determine if there are any additional requirements
Execute ServiceInstall.msi. Just follow the wizard. It will walk you through the whole process step by step. Upon completion, the Connector Server will be installed as a windows service.
Start the Microsoft Services Console. Check to see if the Connector Server is currently running. If so, stop it. From a command prompt, set the key for the connector Server. This is done by changing to the directory where the connector server was installed (by default: \Program Files\Identity Connectors\Connector Server) and executing the following command:
where <newkey> is the value for the new key. This key is required by any client that connects to this Connector Server.
Look through the configuration file and inspect all settings. The most common things to change would be the port, trace, and ssl settings.
The port, address, and SSL settings are in the tag called AppSettings, and look like this:
The port can be set by changing the value of connectorserver.port. The listening socket can be bound to a particular address, or can be left as 0.0.0.0. To setup to use SSL, you must set the value of connectorserver.usessl to true, and then set the value ofconnectorserver.certifacatestorename to your the certificate store name.
You will need to record for use later the following information regarding your connector server installation:
Host name or IP address
Connector server port
Connector server key
Whether SSL is enabled
Trace settings are in the configuration file. The settings look like this:
The Connector Server uses the the standard .NET trace mechanism. For more information about the tracing options, see Microsoft's .NET documentation for System.Diagnostics.
The default settings are a good starting point, but for less tracing, you can change the EventTypeFilter's initializeData to "Warning" or "Error". For very verbose logging you can set the value to "Verbose" or "All". The amount of logging performed has a direct effect on the performance of the Connector Servers, so be careful of the setting.
Any configuration changes will require the connector server to be stopped and restarted.
The best way to run the Connector Server is as a Windows service. When installing, the Connector Server is installed as a Windows service. This should be fine for most installations.
If for some reason, this is not adequate, the connector server may be installed or uninstalled as a Windows service by using the /install or /uninstall arguments on the command line. To run the Connector Server interactively, issue the command:
To install new connectors, change to the directory where the Connector Server was installed, and unzip the zip file containing the connector there. Restart the Connector Server.
To install additional Connector Servers on the same machine, download the Connector Server zip file from the downloads section. Create a directory to install to, and unzip the file there. Edit the configuration file as described above ensuring that you have a unique port. You may also want to make sure that the trace file is different as well. You can then run the additional Connector Server interactively or as a service.
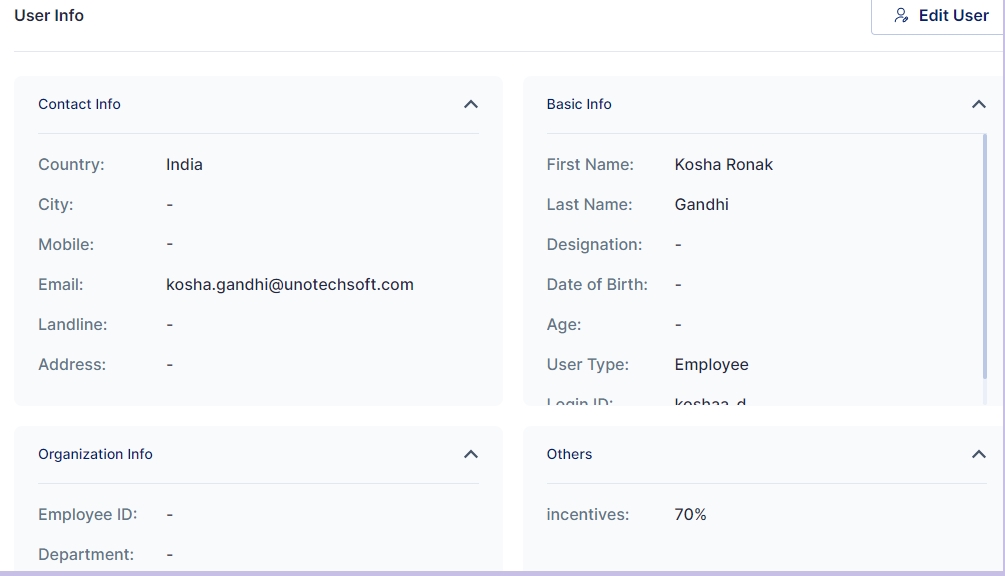
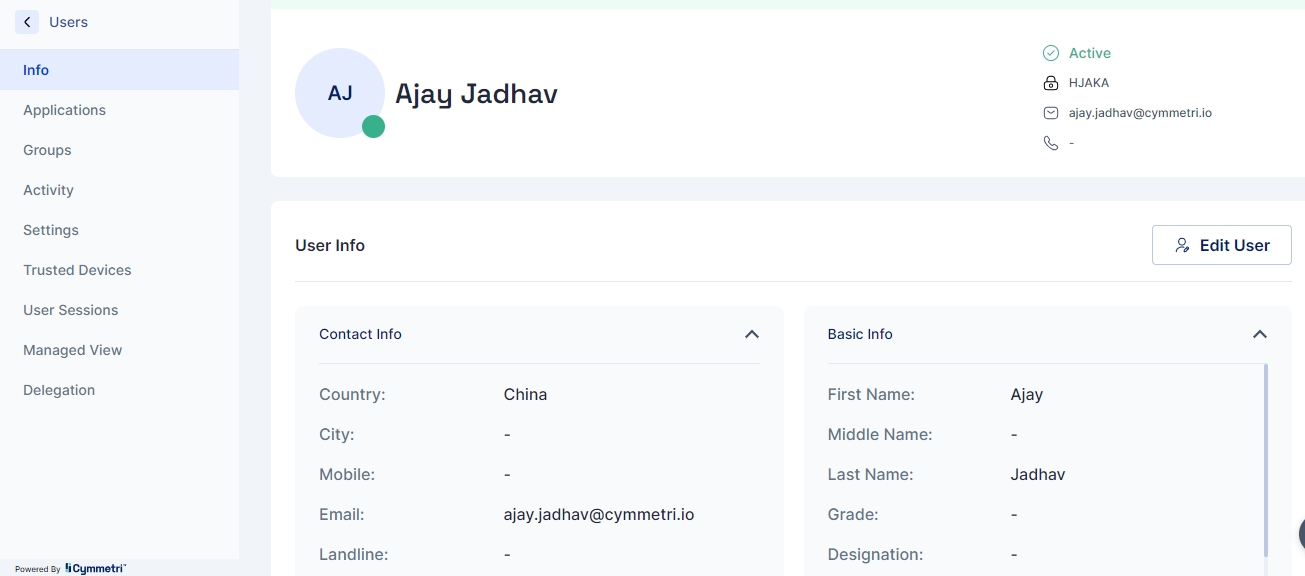
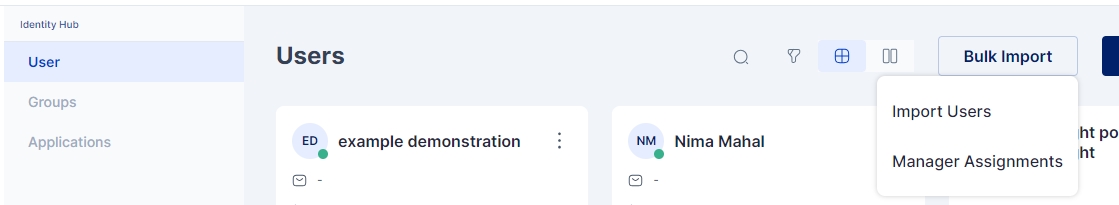




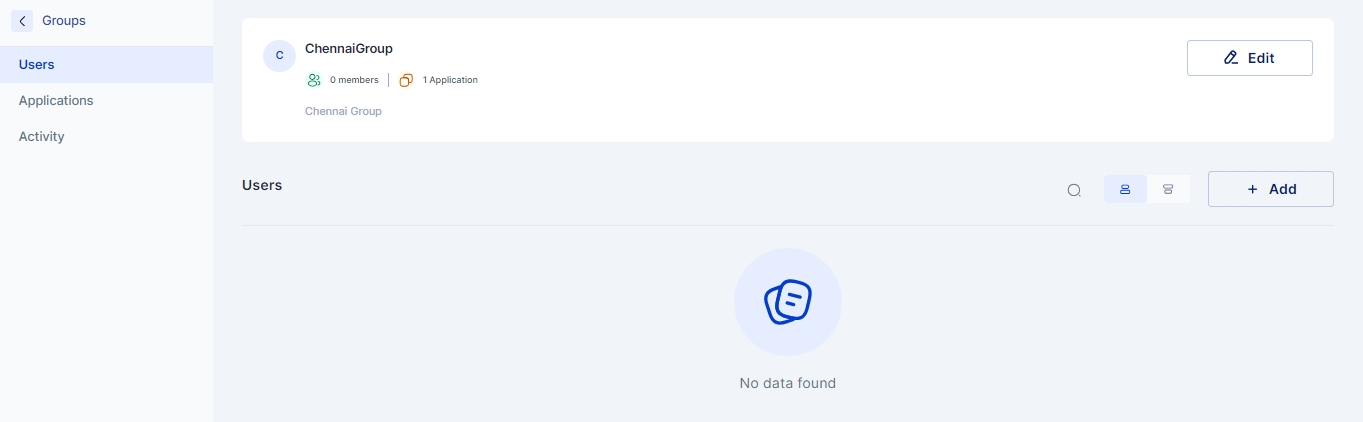
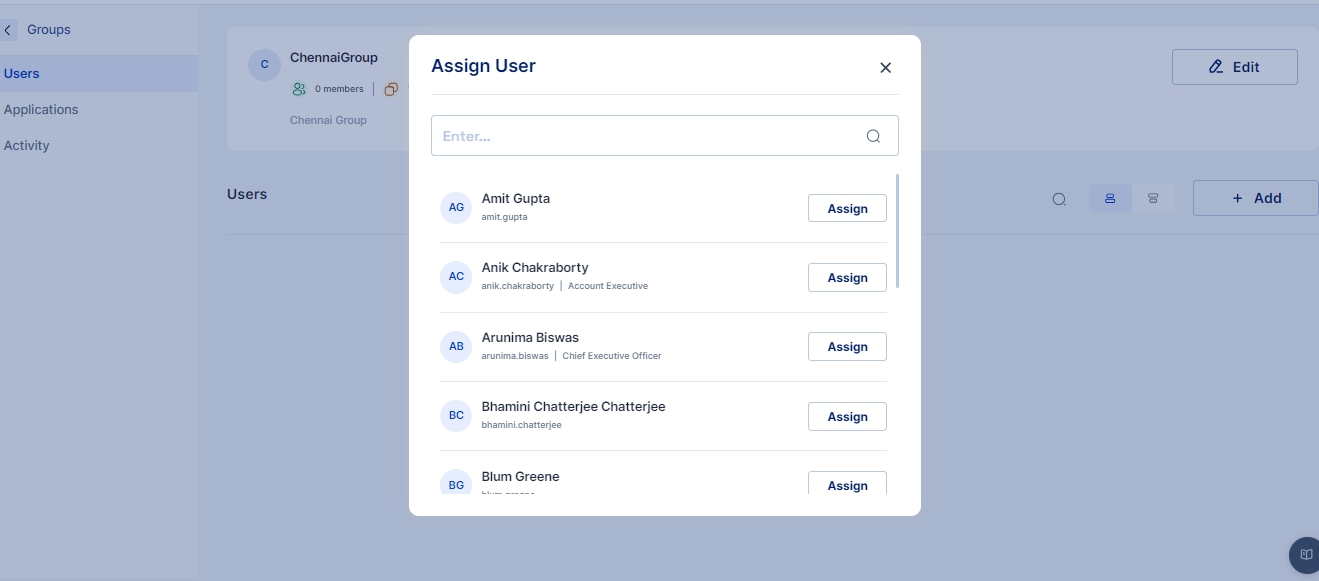
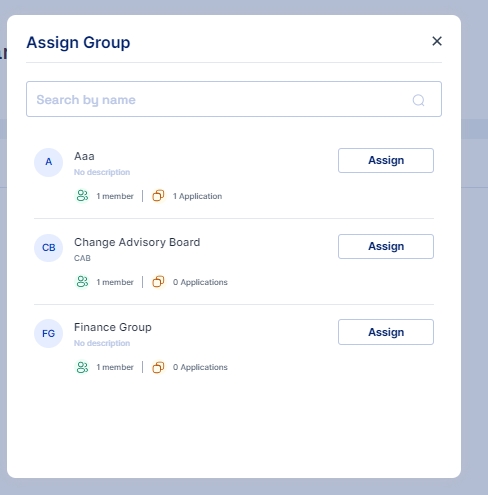
'
Note: The link below shows steps as suggested by Salesforce to configure Salesforce as an Identity Provider:
Here below the same steps are demonstrated to use Salesforce as an Identity Provider and Cymmetri as a Service Provider.
For configuring Salesforce to be used as an IDP the Salesforce Administrator needs to login to Salesforce as shown below:
$ jar xvf net.tirasa.connid.bundles.googleapps-1.4.2.jar
$ java -jar net.tirasa.connid.bundles.googleapps-1.4.2.jar /path/to/client_secrets.json
Please open the following address in your browser: ?
access_type=offline ...Attempting to open that address in the default browser now...
Please enter code: XXXXXXXX






























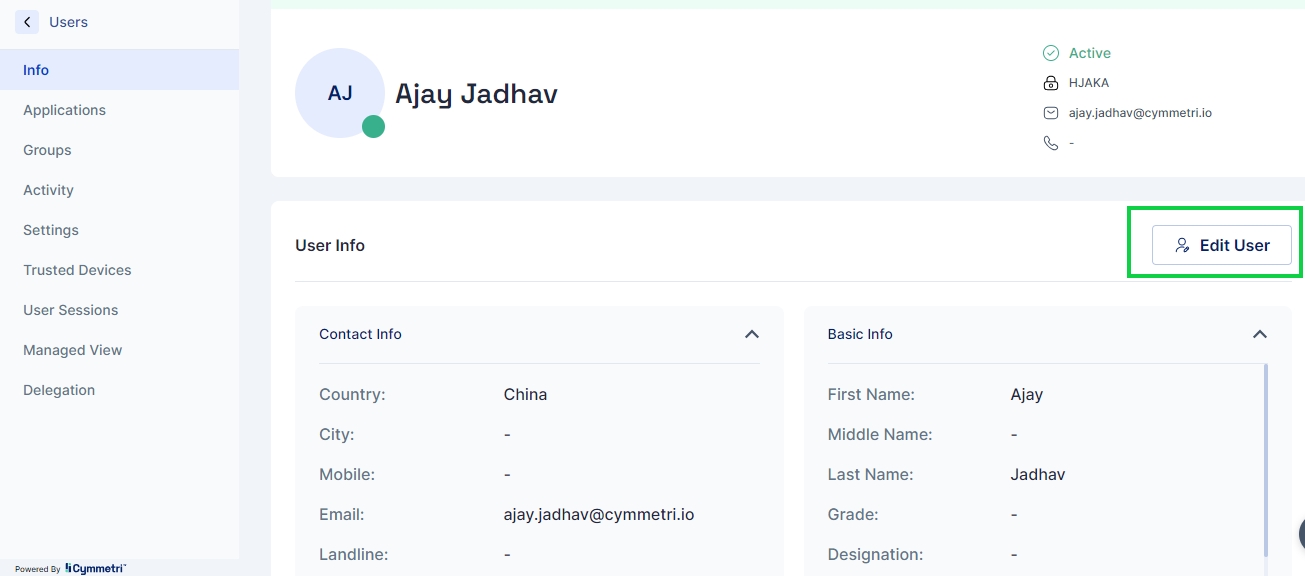

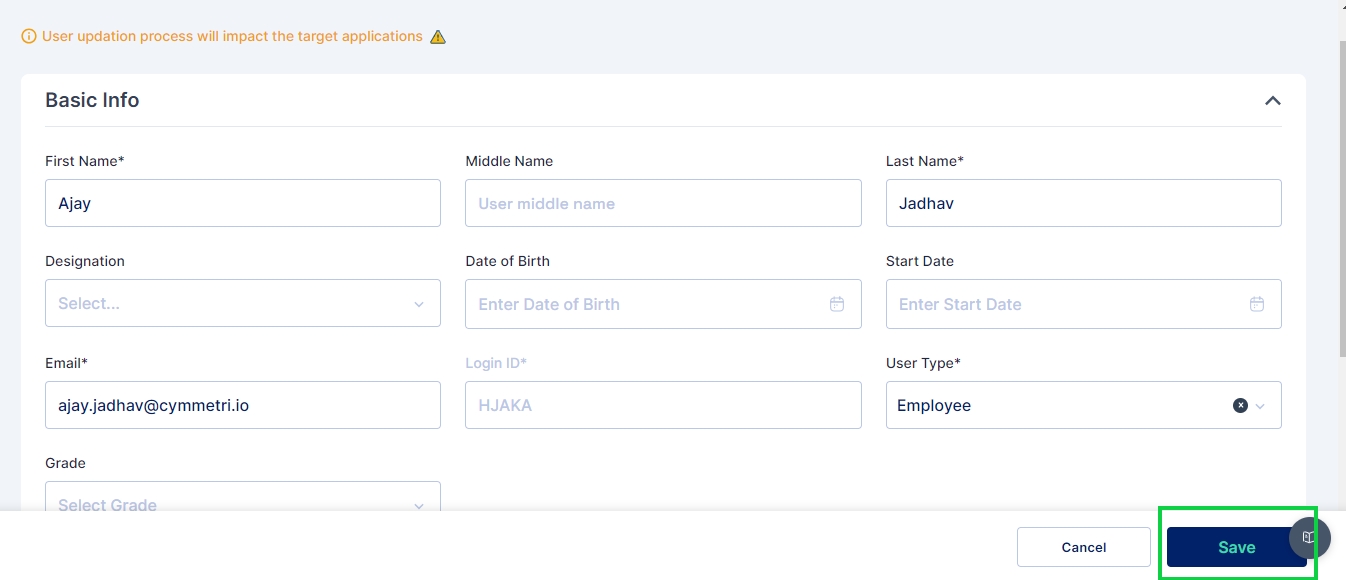
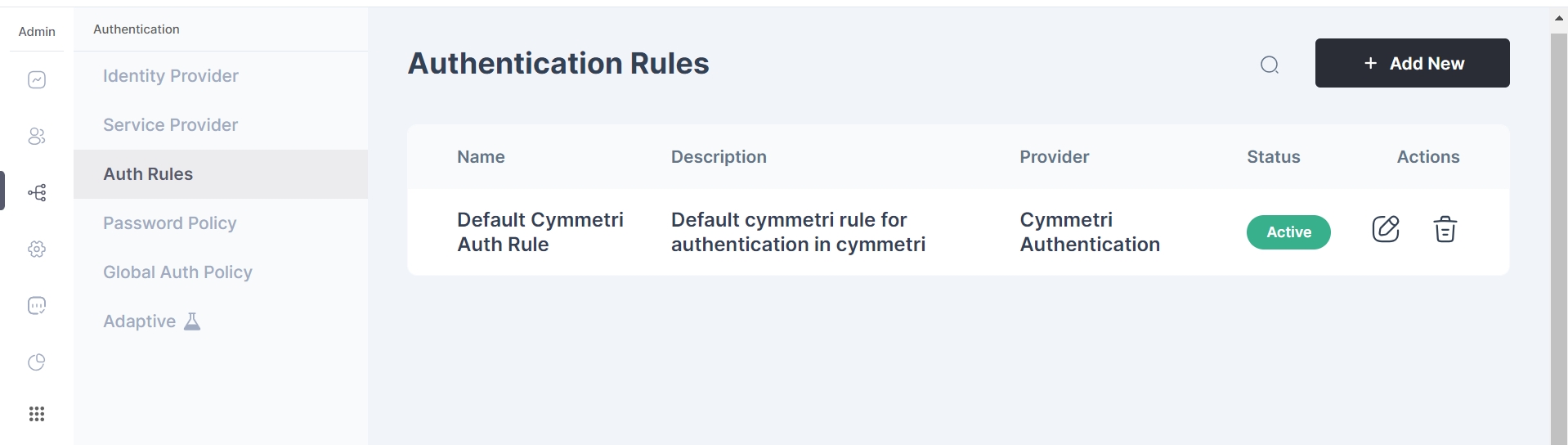
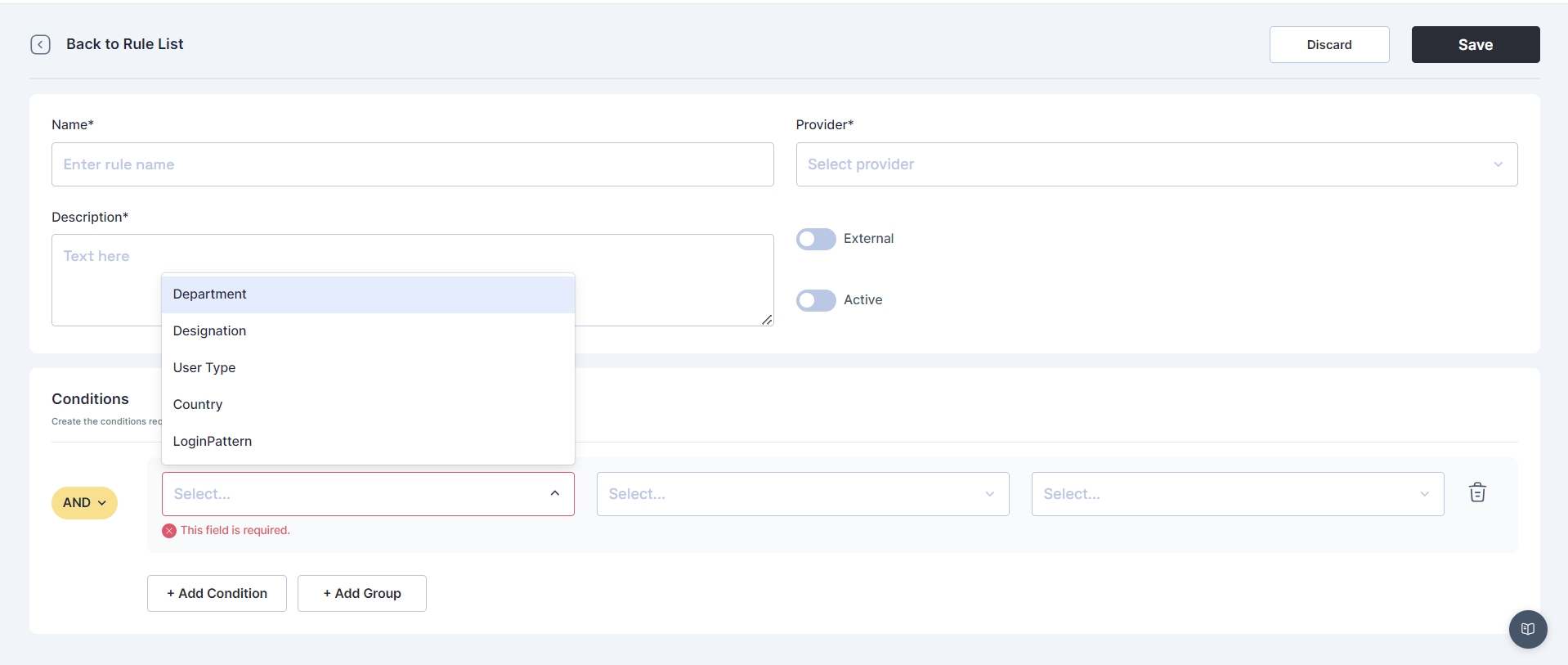
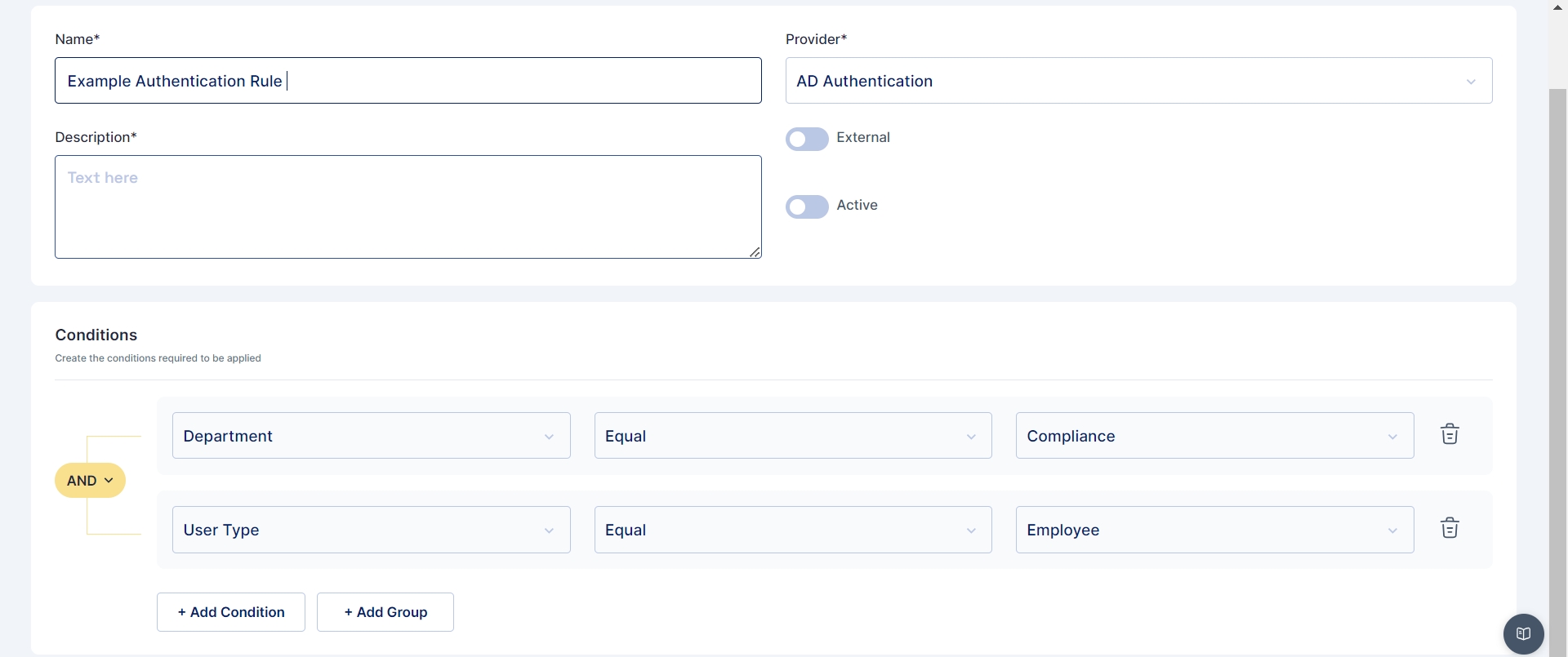
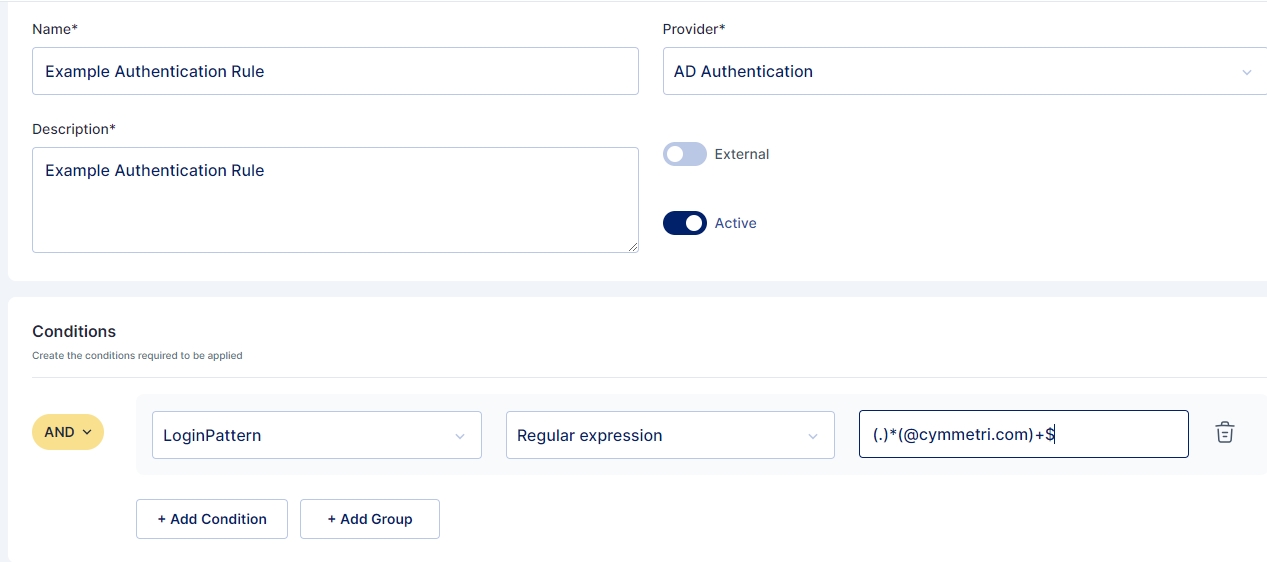
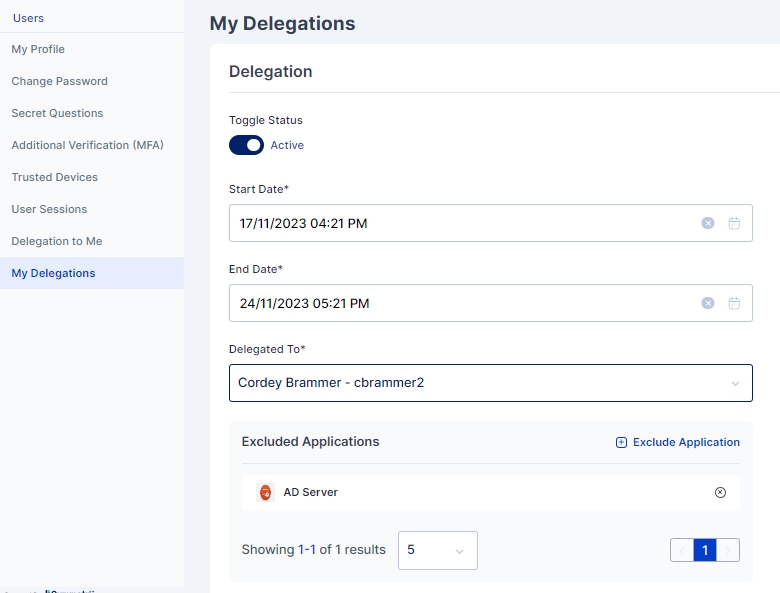
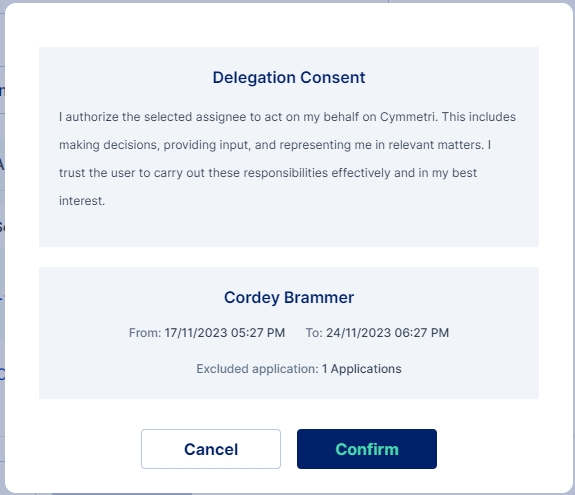
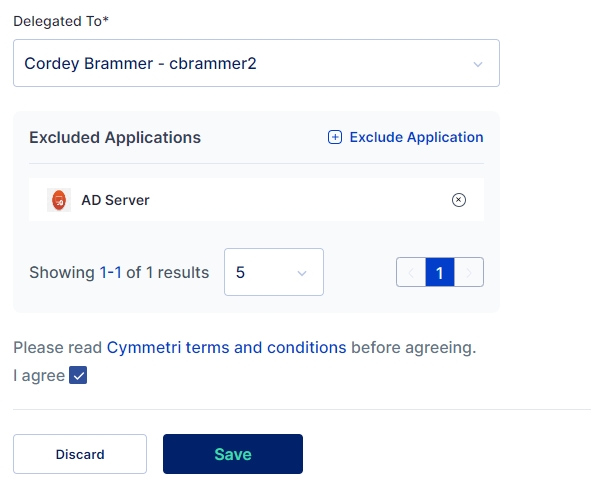
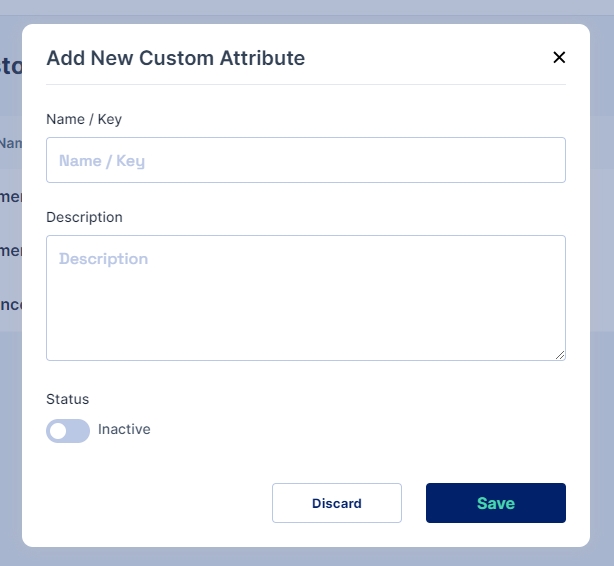

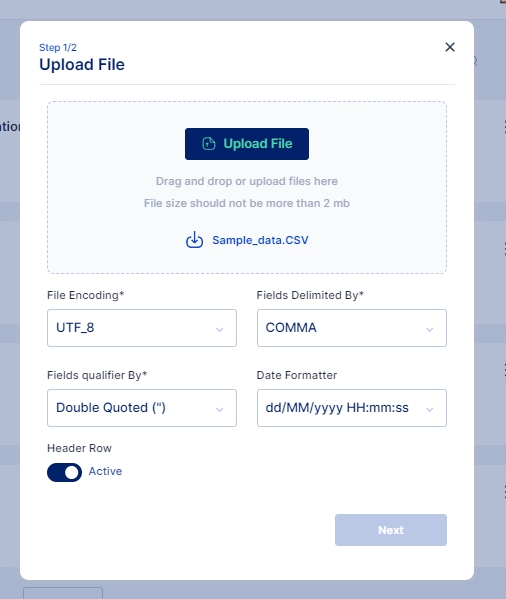

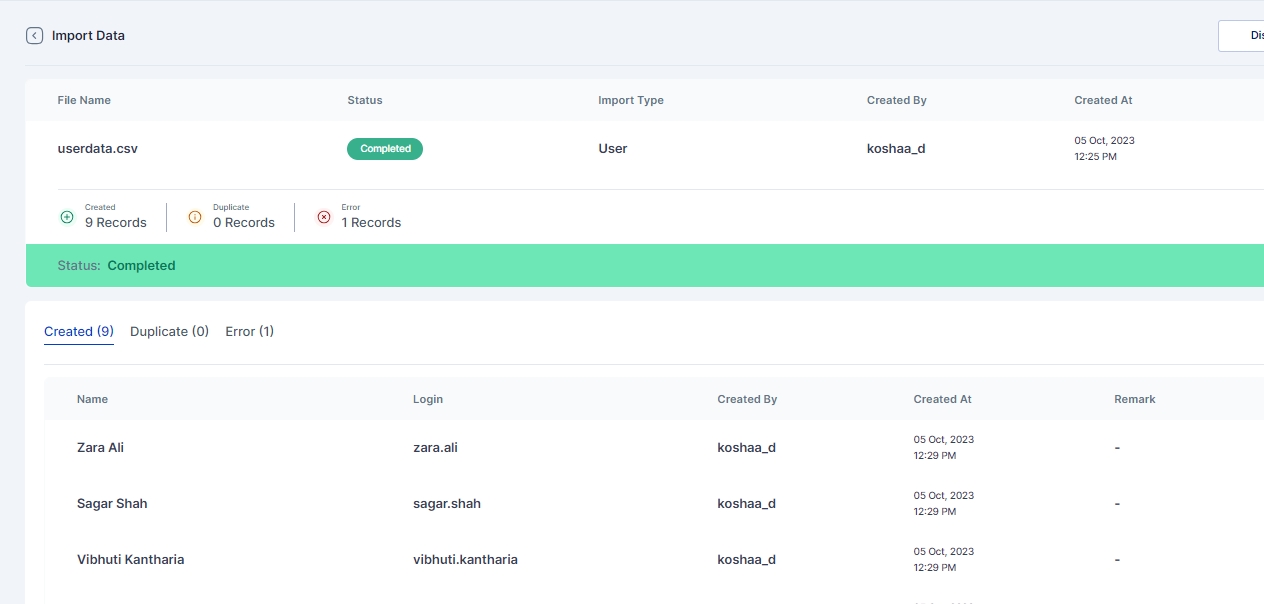
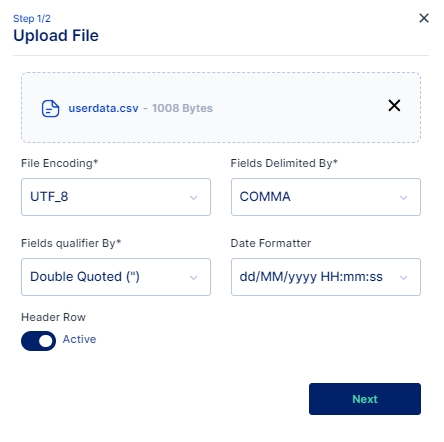

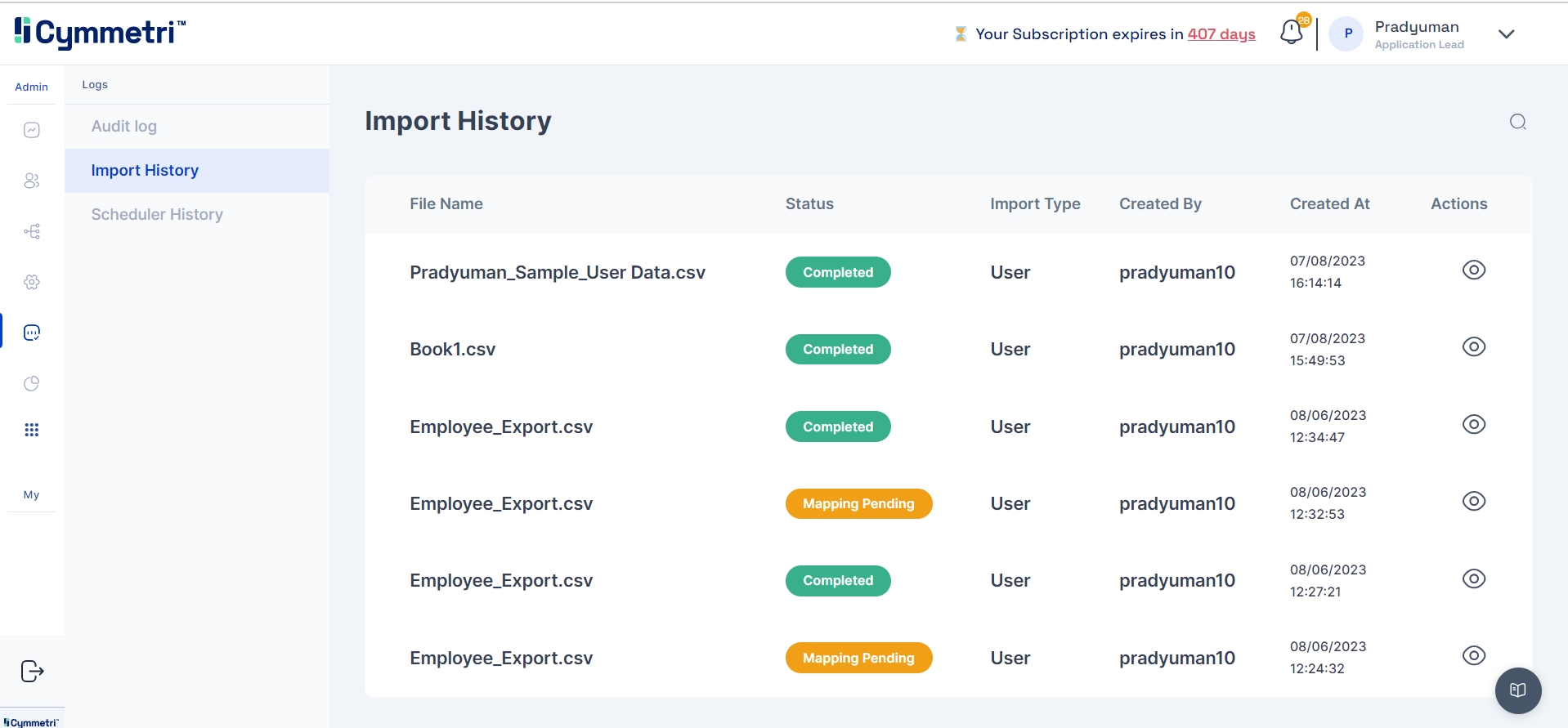
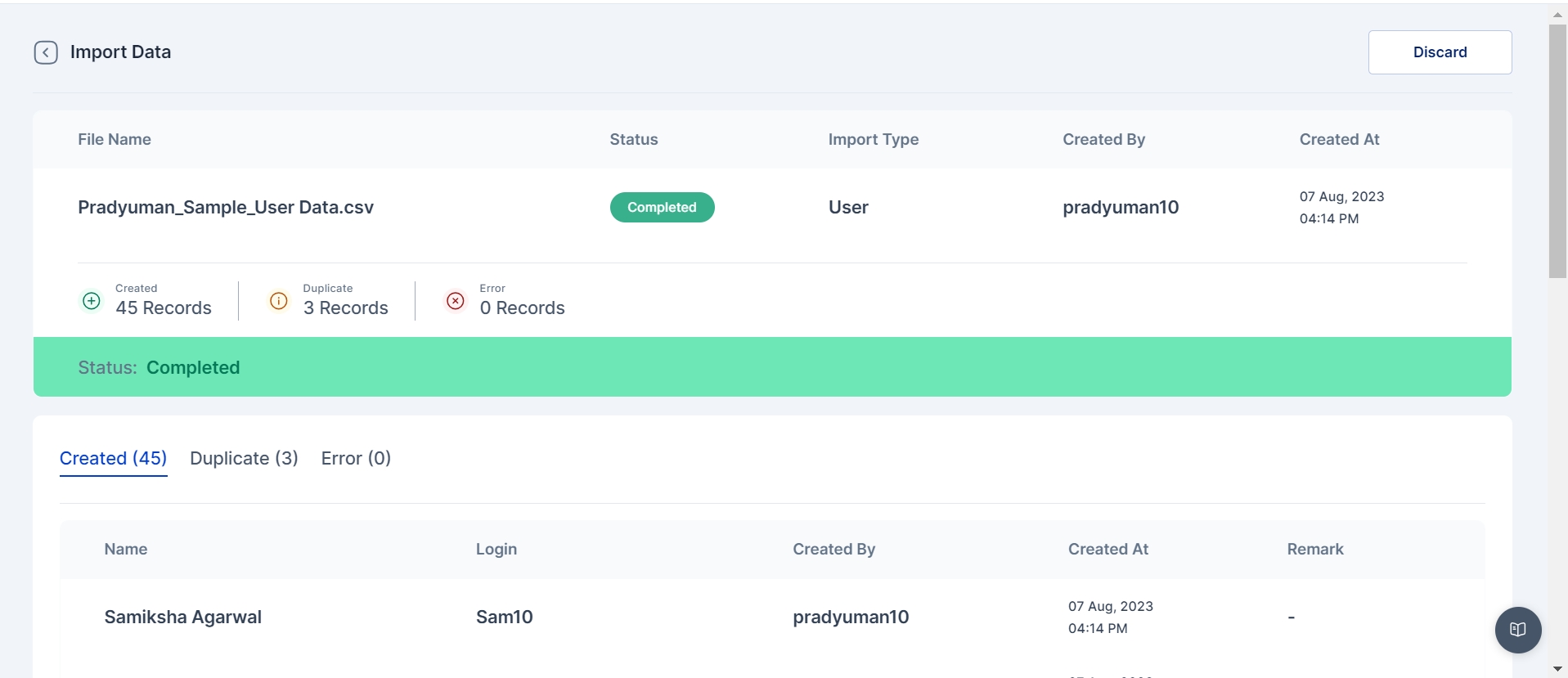
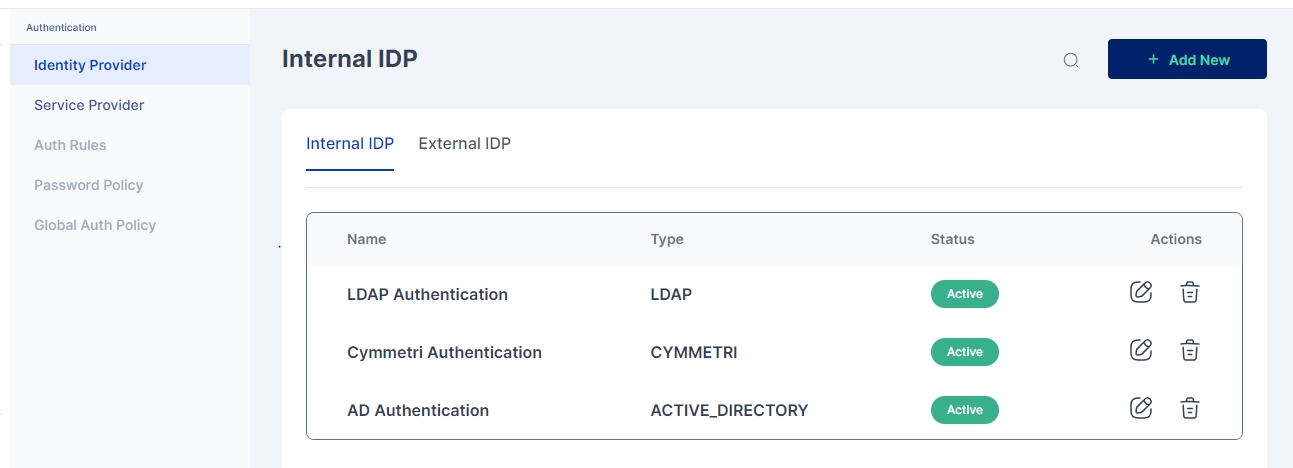
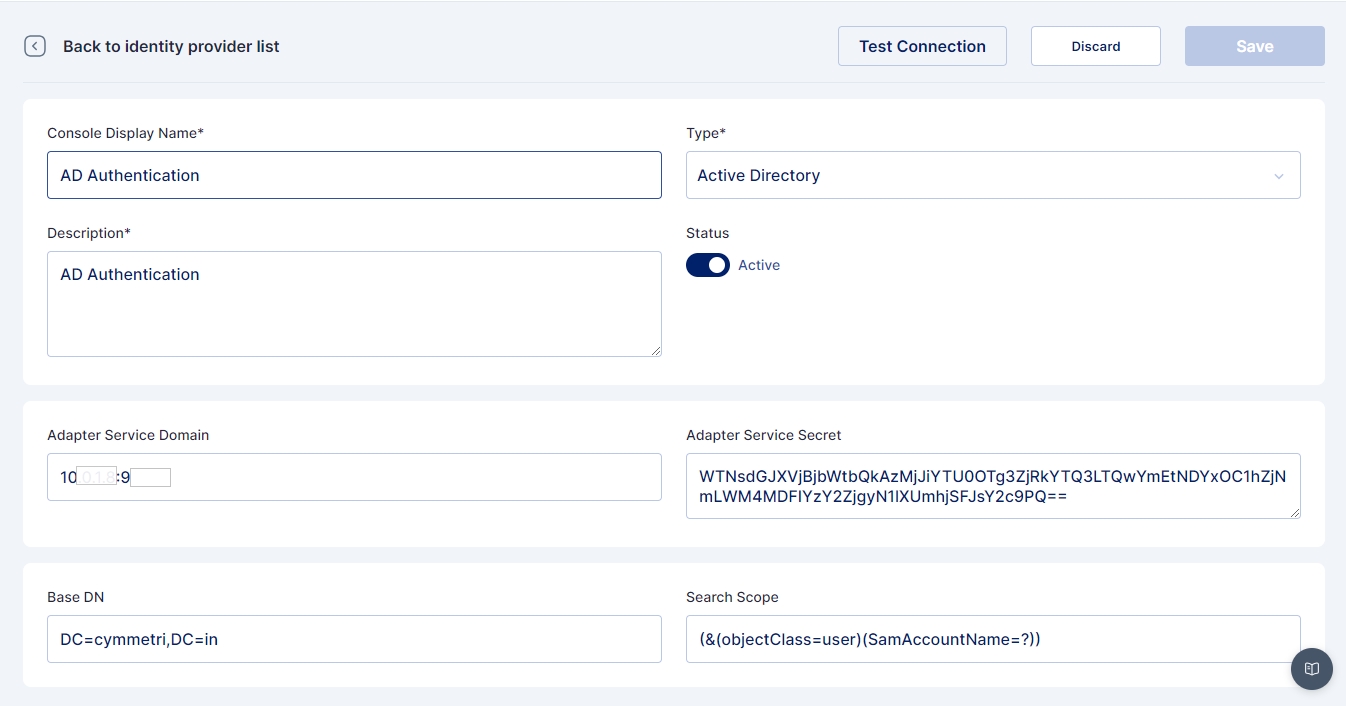

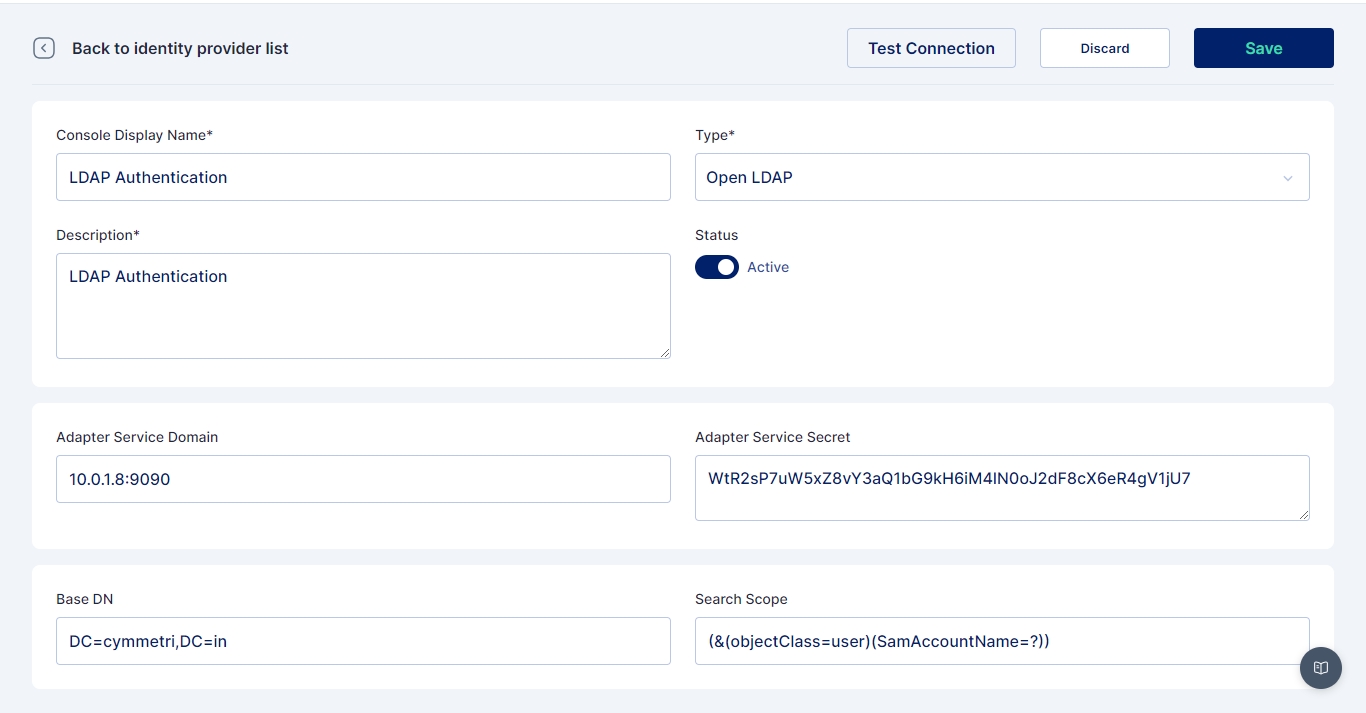


Unzip it in a directory of your choice (e.g. /usr/jconnserv) on the host where you wish to run the Java connector server
For all other properties (e.g. port), edit the conf/connectorserver.properties manually. The available properties are described in the connectorserver.properties file.
Usage:
Main -run -properties
Main -setkey -key -properties
Main -setDefaults -properties ConnectorServer /setkey <newkey><add key="connectorserver.port" value="8759" />
<add key="connectorserver.usessl" value="false" />
<add key="connectorserver.certificatestorename" value="ConnectorServerSSLCertificate" />
<add key="connectorserver.ifaddress" value="0.0.0.0" /><system.diagnostics>
<trace autoflush="true" indentsize="4">
<listeners>
<remove name="Default" />
<add name="myListener" type="System.Diagnostics.TextWriterTraceListener"
initializeData="c:\connectorserver2.log" traceOutputOptions="DateTime">
<filter type="System.Diagnostics.EventTypeFilter" initializeData="Information" />
</add>
</listeners>
</trace>
</system.diagnostics>ConnectorServer /runWhen the Identity Provider page opens click on the Enable Identity Provider button to enable Salesforce as an Identity Provider so that it can be used for authentication in Cymmetri.
When the Enable Identity Provider button is clicked it opens a page that asks you to choose a certificate. Select the default certificate here and click Save.
When saved it shows a warning message as below just click the OK button and continue.
Once confirmed the screen as shown below appears you may download the certificate and the metadata file here using the Download Certificate and Download Metadata buttons. These files can be downloaded later during the end of the process which can be seen later in the documentation below.
The metadata file appears as below, this data is used later to configure the External IDP in Cymmetri.
The certificate file appears as below this is also needed when configuring the External IDP in Cymmetri.
Once the files are downloaded next to add the Service Provider the salesforce administrator needs to click on Service Providers are now created via Connected Apps. Click here link. The mentioned link allows to create a Connected App for Cymmetri which acts as a service provider in Salesforce.
The link above leads to the page below where a new connected app can be added. The following details need to be mentioned to add a connected app:
Connected App Name: App Name (Cymmetri in this case)
API Name: Auto-populated based on the Connected App Name field, can be changed
Contact Email: a valid contact email
Note: Other fields shown in the image below are optional and hence can be skipped.
Next on the same page, there is a section called Web App Settings here click on Enable SAML to enable the SAML settings. Once enabled all the below-mentioned details need to be provided.
Entity Id: A unique identifier for a SAML entity, such as a Service Provider (SP) or Identity Provider (IDP), within a federated authentication environment.
ACS URL (Assertion Consumer Service URL): The endpoint where a service provider expects to receive SAML assertions from an identity provider, facilitating single sign-on (SSO) in a federated system.
Enable Single Logout: A configuration option indicating whether the system supports single logout functionality, allowing users to log out of all connected services in a federated environment with one action.
Single Logout URL: The endpoint to which a SAML entity sends logout requests as part of the single logout process when a user logs out of the federated system.
Single Logout Binding: The protocol or method used to transmit single logout requests and responses between SAML entities, often specified as either HTTP Redirect or HTTP POST.
Subject Type: Specifies the type of subject identifier used in SAML assertions, such as transient, persistent, or bearer, indicating how the identity of the user is communicated between the identity provider and the service provider.
Name ID Format: Defines the format of the NameID element in SAML assertions, determining how the user's identity is represented, such as email address, X.509 certificate, or unspecified.
Issuer: Identifies the entity that issues a SAML assertion, typically the identity provider, and is included in the SAML assertion to establish trust between the entities in a federated system.
IDP Certificate: The public key certificate associated with the identity provider, used by the service provider to verify the authenticity and integrity of SAML assertions and messages.
Signing Algorithm for SAML Messages: Specifies the cryptographic algorithm used to sign SAML messages, ensuring the integrity and authenticity of the information exchanged between identity providers and service providers in a federated
The above-mentioned details can be obtained by adding a service provider in Cymmetri as shown below. To know more about how to add a service provider in Cymmetri click here. Once created these details can be used in Salesforce as shown above.
Once all details are successfully added and saved the screen below appears which shows the configuration details.
Administrators can click on the Manage button (as shown above) to view SAML Service Provider Settings and SAML Login Information. Administrators can also download metadata files here.
The downloaded metadata file appears as below. The details mentioned in the metadata file are used to configure an External IDP in Cymmetri.
Based on the diverse profiles of users in Salesforce, the administrator needs to enable Connected App Access for these profiles. Here in this example access has been enabled for the System Administrator; similarly, it should be enabled for all profiles of various users who are intended to access Cymmetri.
For enabling the connected app administrator needs to go to Setup->Manage Users-> Profiles, then select the profile for which the connected app needs to be enabled
Once the profile is selected click on the Edit button and look for the Connected App Access section.
In the Connected App Access section look for the custom app you created(Cymmetri in this case) and click the checkbox to enable the access.
Once all the configurations on the Salesforce end are done, the administrator must proceed with the configuration on the Cymmetri side. To achieve this, the administrator needs to go to Authentication->Identity Provider->External IDP. Here you may either configure the already created salesforce-idp instance or +Add New
In either case, a screen opens where you need to provide the below-mentioned details
Name: salesforce-idp
IDP Type: Salesforce
Entity ID: Need to mention the EntityID from the metadata file downloaded from Salesforce
SSO Service URL: Need to mention the SingleSignonService URL from the metadata file downloaded from Salesforce
Destination: https://<hostname>/spsamlsrvc/samlSP/SingleSignOn
Protocol Binding: HTTP Post (can also be set to HTTP Redirect if it is set so in Salesforce)
Name ID Policy:
Policy: Unspecified(This may change based on what is configured in Salesforce)
Value: Login(This may change based on what is configured in Salesforce)
Certificate: Certificate downloaded from Salesforce
Logout Request URL: Need to mention the SingleLogoutService URL from the metadata file downloaded from Salesforce
Logout Protocol Binding: HTTP Post (can also be set to HTTP Redirect if it is set so in Salesforce)
Service Provider Id: cymmetri (Need to the select the configured Service Provider as shown above)
Once the external IDP is configured next we need to configure Authentication Rules as explained here and as shown below. Conditions mentioned here may vary based on actual scenario in which the IDP needs to be applicable.
Now the user can login into Cymmetri using Salesforce. The user needs to provide his/her username and click on Next.
The user is then redirected to Salesforce login page where the user needs to enter their Salesforce credentials and click on Log in
Once the salesforce credentials are successfully validated the user is redirected to Cymmetri home page.





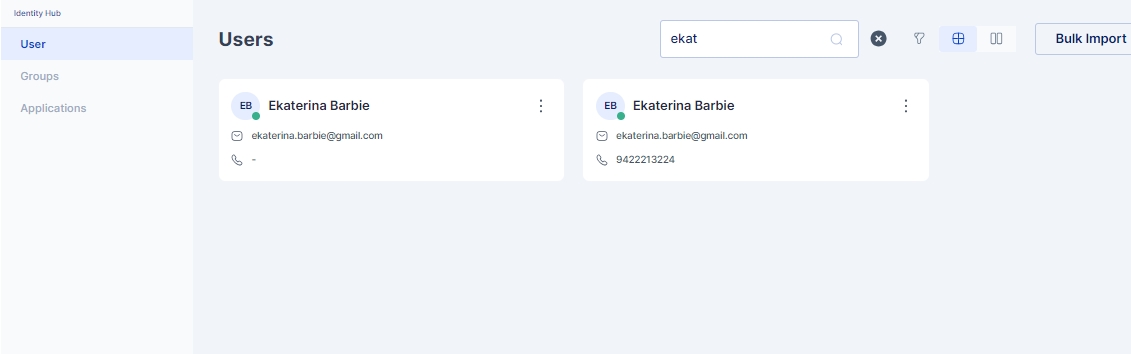



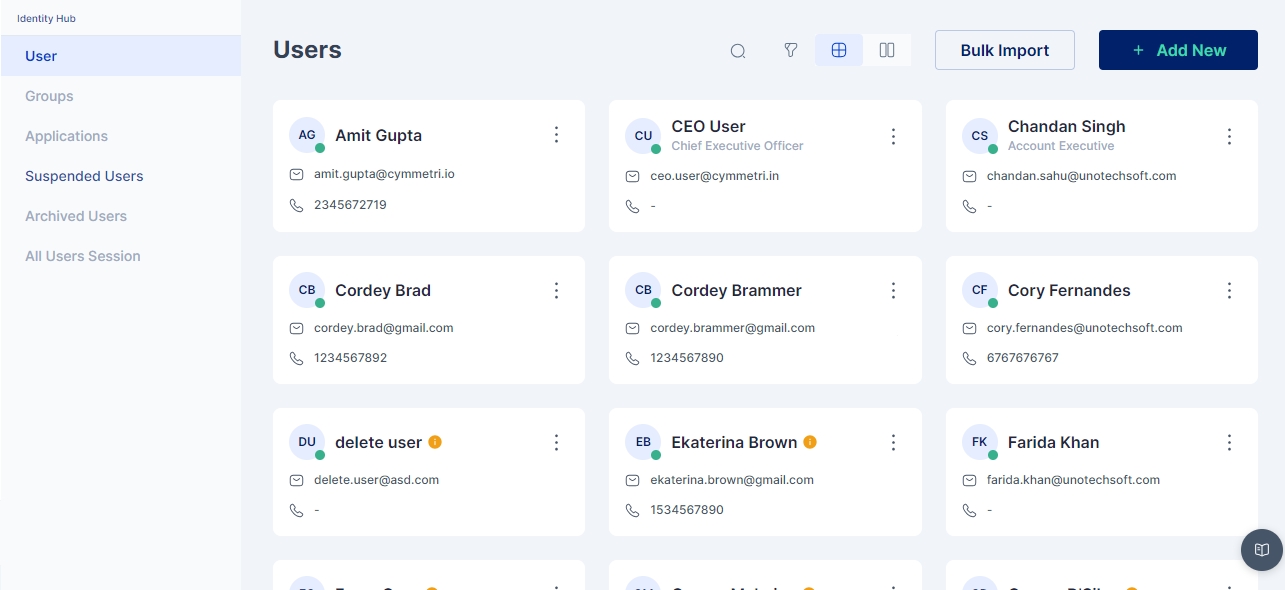
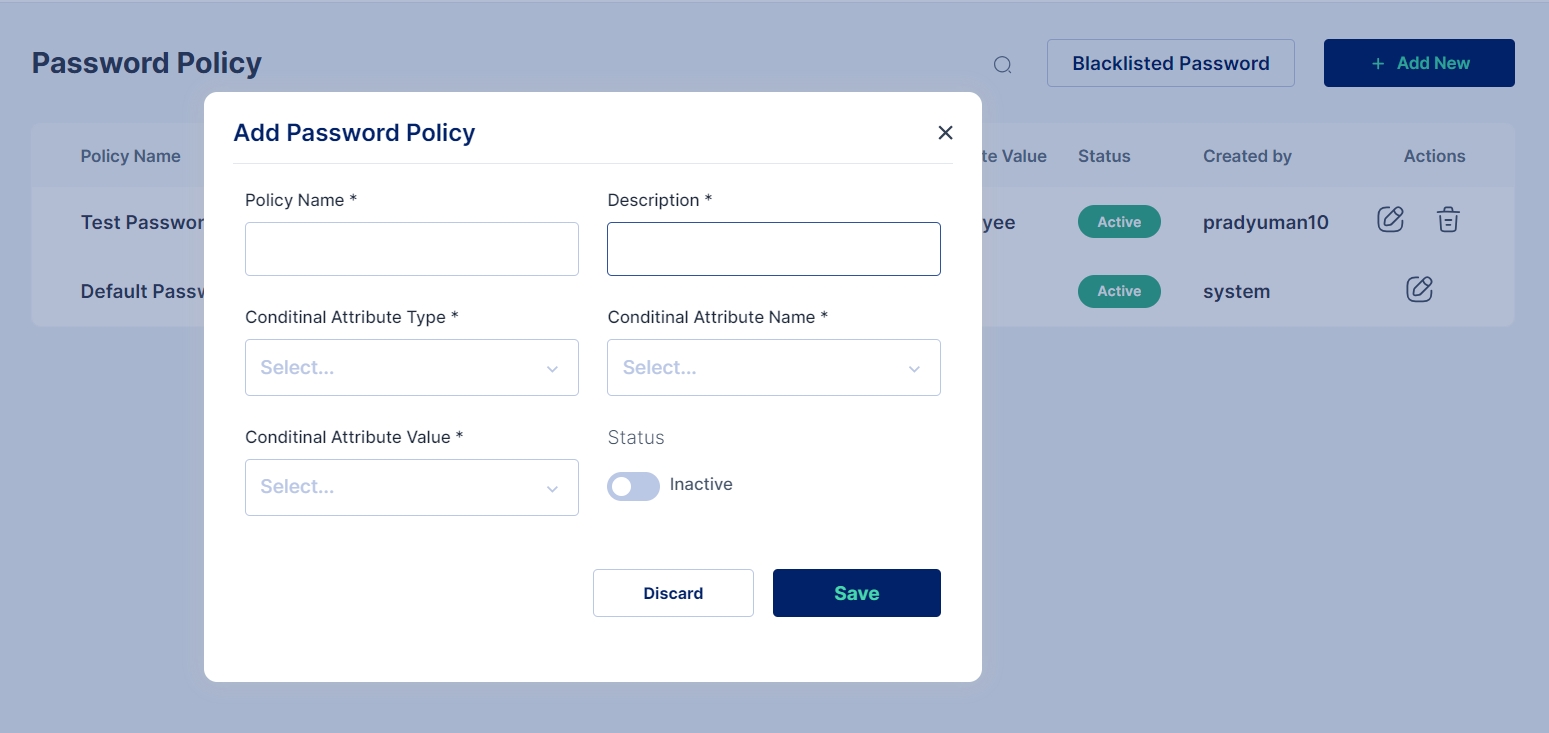
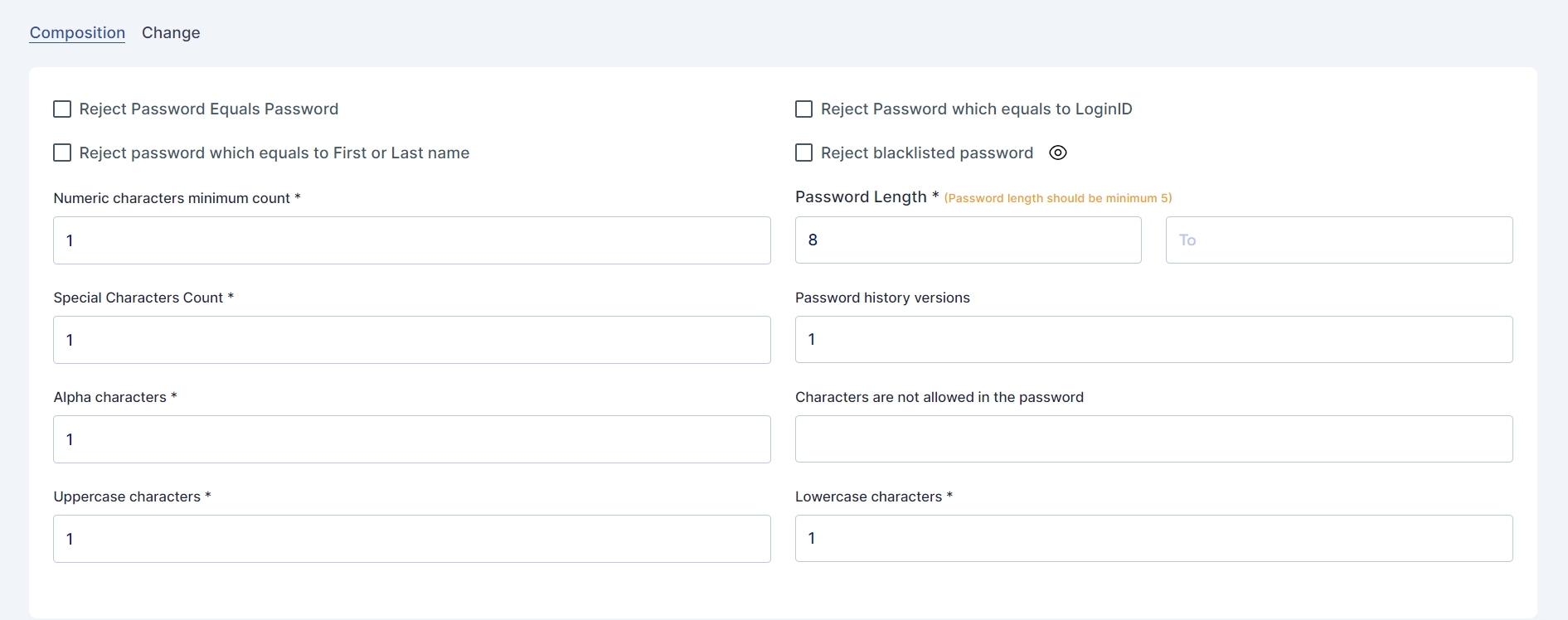
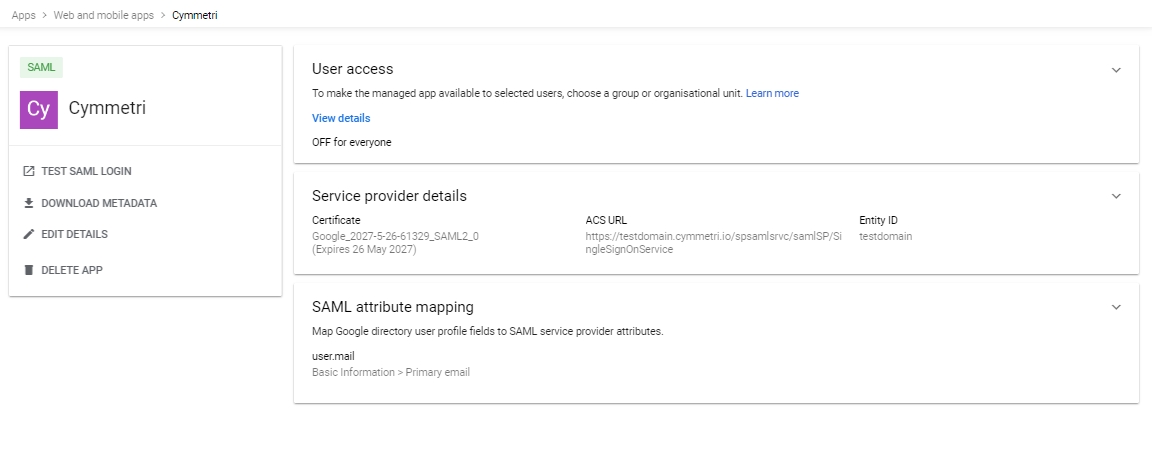
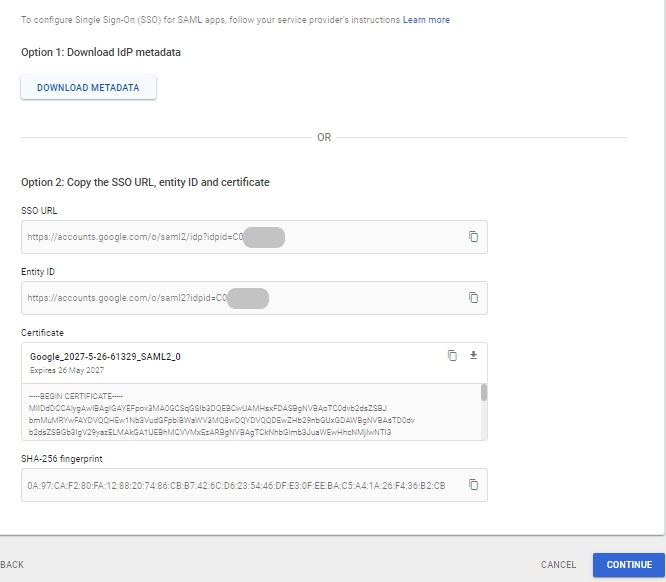

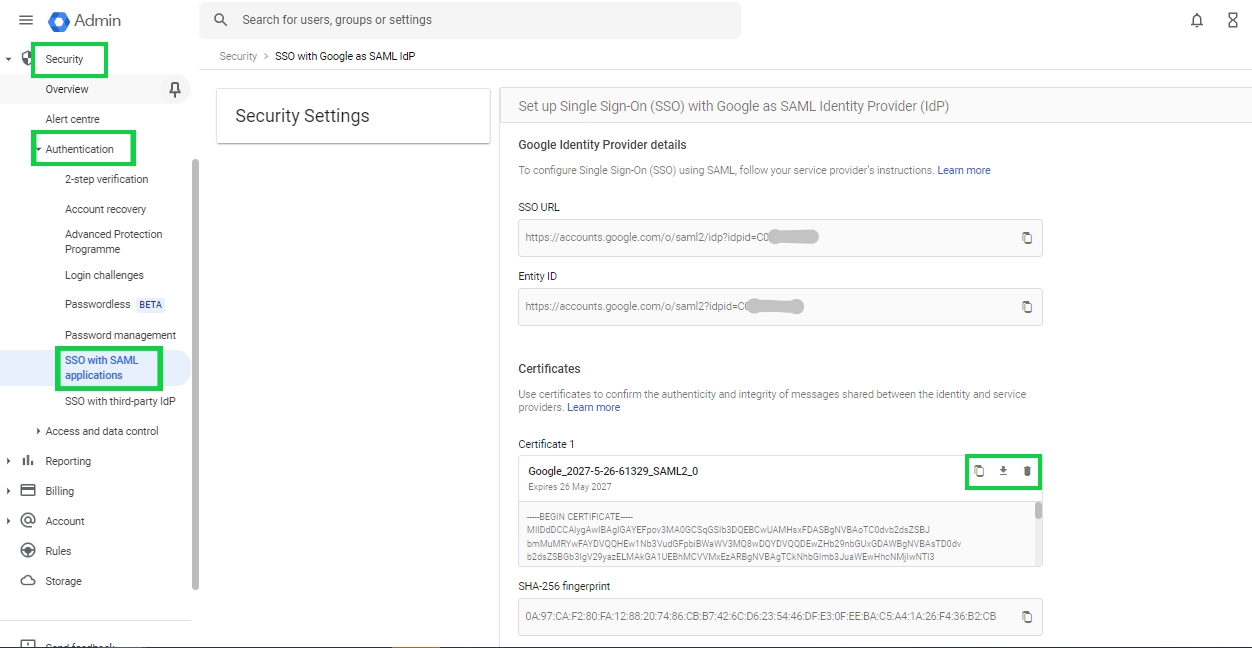
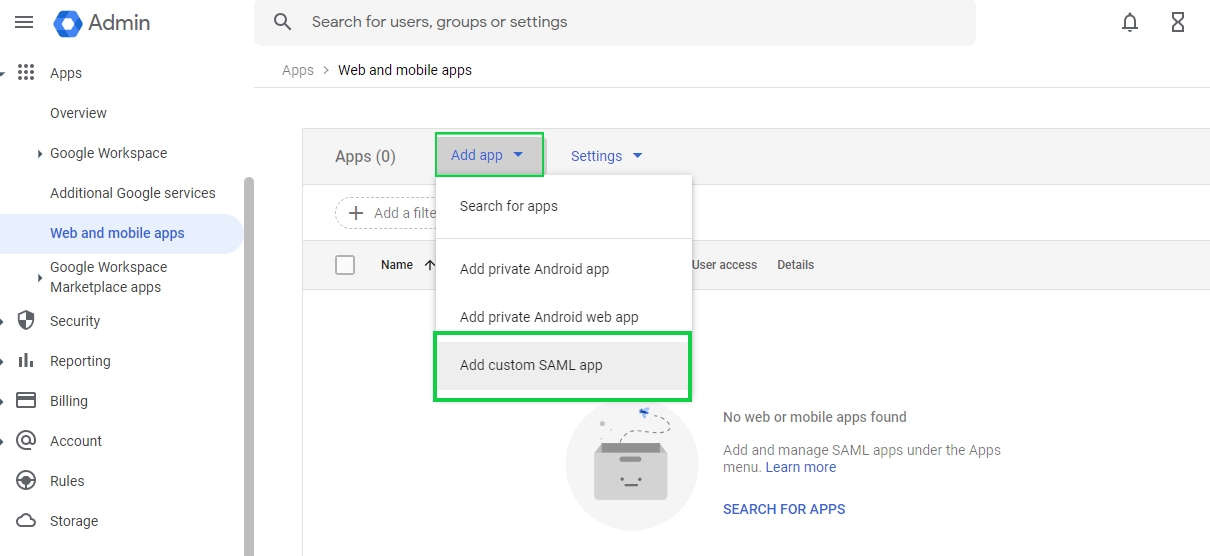


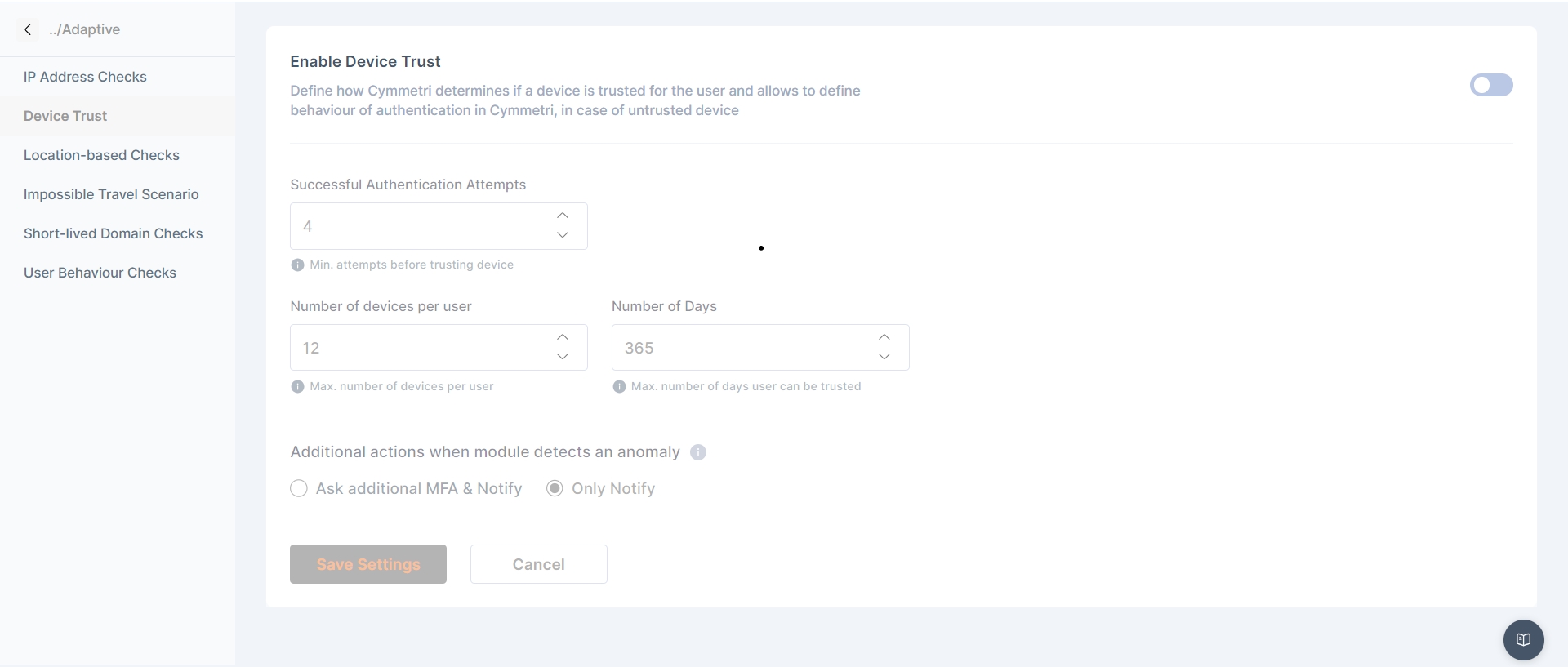
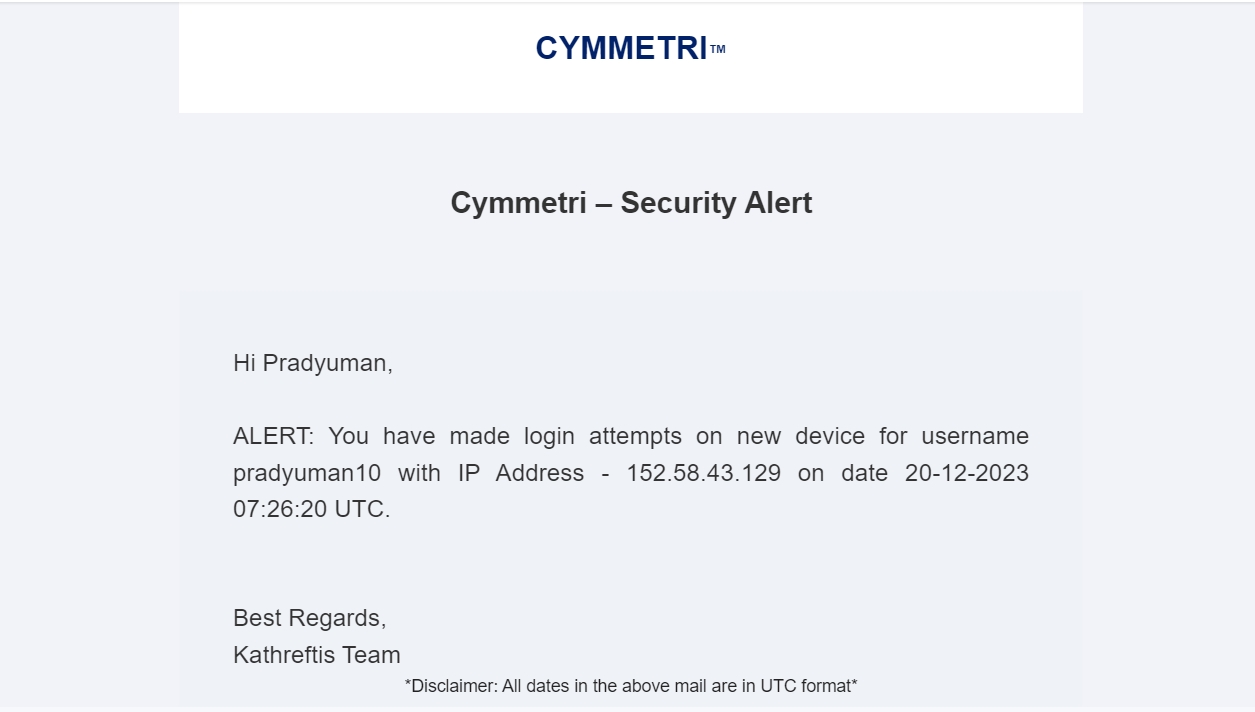

This page is designed to provide a comprehensive view of an individual user's information, facilitating easy access and management for administrators.
The top section of the User Details Page showcases the following crucial user information:
The user's profile picture is prominently displayed, offering a visual identification of the user. This feature aids in personalizing the user experience and making navigation more intuitive.
Right next to the profile picture, users can find the current status of the user, which indicates whether the user is Active, Inactive, or Pending. This status helps in quickly understanding the user's engagement level.
This is a unique identifier for the user within the system. It serves as a key piece of information for various administrative processes, including user tracking, support, and security checks.
The user's Email ID is displayed, providing an essential communication link. It is used for sending notifications, password resets, and other critical communications.
The user's mobile number is listed if provided. This number can be utilized for two-factor authentication, urgent alerts, or direct contact purposes.
This structured format ensures that an administrator or any authorized viewer can quickly access and understand a user's essential information without navigating through multiple pages.
The user's risk details are visible on the page to notify that the user is a high-risk user. On further clicking on that page, it shows the User's Risk metrics.
This page provides a comprehensive overview of the user information managed within our system. The data is categorized into several sections to facilitate easy access and understanding of each user's profile. These sections are detailed below.
First Name: The user's given name.
Middle Name: The user's middle name, if applicable.
Last Name: The user's family name.
Grade: The user's grade (a set of values needs to be defined for this field in the Masters).
Country: The country where the user is located.
City: The city within the country.
Mobile: The user's mobile phone number.
Email: The user's email address is used for electronic correspondence.
Employee ID: A unique identifier assigned to the user within the organization.
Department: The department to which the user is assigned.
Start Date: The date when the user commenced their current position.
End Date: If applicable, the date when the user's current position will or has ended.
Additionally, this page may display values for custom attributes specific to our organization. These attributes allow for the capture of information not covered by the standard categories but deemed necessary for our operations.
This comprehensive user information page ensures that all pertinent data regarding an individual within our organization is readily accessible, facilitating smooth operations, management decisions, and communication.
This page is designed to streamline the management and assignment process of applications for users. It offers a section where you can easily view all your assigned applications along with their current status. Additionally, it allows for the straightforward assignment of new applications to your profile.
Viewing Assigned Applications: Upon accessing the page, you will be presented with a list of applications currently assigned to you. Each application tile gives a snapshot of the application's status, enabling you to quickly assess which applications require your attention.
Assigning Roles: Application Roles can be assigned to the user using the Assign Role option. This option also allows the assignment of multiple roles to a user.
Unassign Assigned Applications: Assigned applications can be removed using the delete option in the (⋮) menu.
Searching for Applications: To facilitate ease of access, a search function is incorporated into the interface. This feature allows you to quickly find specific applications by typing the name or part of it into the search bar, saving you time and effort from manually scrolling through the list of applications.
Note: In instances where an application has not been successfully assigned, the interface provides direct actions to resolve the issue without needing to navigate away from the page. Each application tile includes an (⋮) menu with two options:
Retry: If an application's assignment process encounters an issue, you can select this option to attempt assigning the application again.
Delete: If the assignment issue remains unresolved or if you no longer wish to keep the application, you can choose to remove the application from your list entirely.
This page provides an overview of the groups to which a user is assigned, reflecting the current status of each.
Upon accessing the page, users are presented with a list of all the groups to which they are currently assigned. Each entry includes the group's name, description, number of users in the group and number of applications assigned to the group.
To enhance the user's role or access within the system, the Add New Button is prominently positioned. This option allows users to be added to more groups, expanding their access and functionalities within the application. The process is designed to be straightforward, guiding the user through a simple process to ensure accurate group assignments.
This menu option, found within the ellipse (⋮) menu, takes you to the groups pag,e where you may edit any information related to the group
Equally important is the capacity to manage the departure from groups, which is facilitated by the Delete Group option. Also found within the ellipse (⋮) menu, this feature does not delete the group itself but rather unassigns the user from the selected group. This action ensures the user's access and permissions within the application are precisely tailored, maintaining security and relevance.
This page shows the user-specific audit log for all the various actions and activities performed by the user. This may include all activities related to the user, as shown below
Status:
You can change the status of users and accounts in our system to manage access and control.
Locked: Stops user access temporarily. This is used for security reasons or if there are too many failed login attempts.
Unlocked: Gives access back to the user, allowing them to log in and use the system.
Active: The account is in use, and everything works normally.
Inactive: Temporarily not in use, but can be activated again.
Delete: The account is deleted and moved to suspended accounts
The administrator has three distinct options for configuring the password reset process, allowing them to choose a method that best fits the organization's security policies and workflow.
Generate Password: This option allows the user's manager to generate a random, one-time password.
Generate Password and Send to User's Email: With this option, the manager triggers the password reset, and the system automatically generates a new password and sends it directly to the user's registered email address.
Send Reset Password Link to User's Email: This is the most secure option. The manager initiates the process, but instead of a password, the system sends a secure, time-sensitive "Reset Password" link to the user's email. The user must click the link to create a new password.
Generate Password
Generate Password and Send to Users' Email
Send Reset Password link to Users Email
This section can be used to assign tenant-wide roles defined in the master to the user.
Secret Questions
This section shows a list of secret questions selected by the user
Additional MFA
Administrators can view the MFA mechanisms configured by the user, as well as remove the configured MFA if required for a specific user
If Adaptive MFA is configured for users and a configuration for Device Trust is done, Cymmetri maintains a list of Trusted devices that satisfy the conditions of the Device Trust configuration. This list of devices trusted based on the configuration done by the admin is listed on this page with the following information about each device: Browser, OS, Created At, Trusted, Action(remove device)
This page provides Cymmetri administrators with the capability to monitor and manage all user sessions. It provides the following information: Browser, OS, Created By, IP Address, Created At, and Action (delete session). A user may have multiple session entries if the Multiple Session configuration is enabled.
The Managed View page shows the user data based on various provisioning applications assigned to a user. This page shows the Attribute Name, Managed System Value, and IDM Value
Attribute Name: Attribute name as defined in the policy attribute page of the provisioning application
Managed System Value: Value as saved in the provisioning application
IDM Value: Value as saved in Cymmetri
In Cymmetri, one of the features available to users is the ability to delegate self-service access. This capability enables users to assign their access rights and responsibilities to other users temporarily. Ideal for scenarios such as vacations, business trips, or whenever a user needs someone else to manage their duties without forfeiting their credentials or compromising security.
This page shows the delegation provided by the user; this may be currently in progress or the delegation that was last completed.
The page shows the status of the Delegation (INPROGRESS, COMPLETED), Designated To, Start Date, End Date, and the list of Excluded Applications(if any)
Once the managed application has been added to your Cymmetri Identity platform tenant, you will be able to assign applications to your end-users.
There are three ways in which applications can be assigned to users:
Admin may assign an application directly to a user.
Admin may map an application to a group; and the user is added to the group or is already part of the group.
End User may request an application and is granted access to the application.
Bulk Assignment of application to a set of users
Let us understand the flow for each of the above mentioned scenarios:
Users with admin roles such as Organization Admin, Domain Admin, or Application Admin on the Cymmetri platform can assign managed applications to end-users .
First, we need to add the application to the Cymmetri platform
Next, we move to configure the application to assign it to an end user.
Click on the application tile to configure it.
The flow for assignment goes as follows -
Description:
Admin clicks on the application tile, and starts the configuration.
Click on the Assignments tab on the left hand side menu.
Click on the “Assign New” button on the Users menu.
Users with admin roles, such as Organization Admin, Domain Admin, or Application Admin, in a Cymmetri Identity platform deployment, will have the ability to assign entire groups of users to managed applications.
First, we need to add the application to the Cymmetri platform
Next, we move to configure the application to assign it to a group.
Click on the application tile to configure it.
The flow for assigning a group to an application goes as follows:
Click on the application tile, and start the configuration.
Click on the Assignments tab on the left hand side menu.
3. Click on the “Assign New” button in the Groups section.
4. Search for the group you wish to assign the application to and click on the assign button.
5. Checking for the users who belong to the group, we can see that the application has been assigned.
6. Viewing the application tiles, we can see if the user was directly assigned the application or received access by the virtue of being part of a group.
Users on the Cymmetri platform can request access to a managed applications as a Self-Service feature.
The flow for an end-user to request for an application is as follows:
Visit the “My Workspace” menu.
Click on the “My Access” left-hand side menu.
3. Now Click on the “+ Request” button on the top-right button.
4. Click on the Application Icon to start the request process
Here we need to decide whether we want to provide a Lifetime Access or a Time Based Access
Lifetime Access: Users have access to the application without any time restrictions.
Time Based Access: Users have access to the application only for the specified range of time. We need to provide a Start Date & Time and an End Date & Time for Time Based Access.
An administrator can bulk assign an application to a set of users. This an be achieved by uploading a .csv file which contains user information like., loginId, appUserId and roleId. For bulk assigning applications to users in Cymmetri platform administrator needs to
Click on Identity Hub > Applications menu and then click on the Applications Assignments button.
A screen pops up that lets you select the csv file you want to upload that contains the list of users to whom the application needs to be assigned, Upload the csv file, you may also use the sample data file available and modify it to match your user details.
Click on the Upload File button and select the file you wish to import
Once the file is selected ensure that the default parameters select match your requirement else you may change these parameters as per your requirement.
Once you have ensured the parameters are correct next select the application that needs to be assigned and click on Next button.
Match the Column names from the CSV file with the corresponding attributes using this File Info dialog box and click on the Import button.
Note: The "Link Application" check box is available to provision the user in the target application
Once Imported results of successfully Imported Users, Duplicate Users or any error that occurred during import can be see in Logs > Import History page
If any workflow is configured on the application provisioning then the corresponding workflow is triggered after the successful completeion of assignment as shown below:


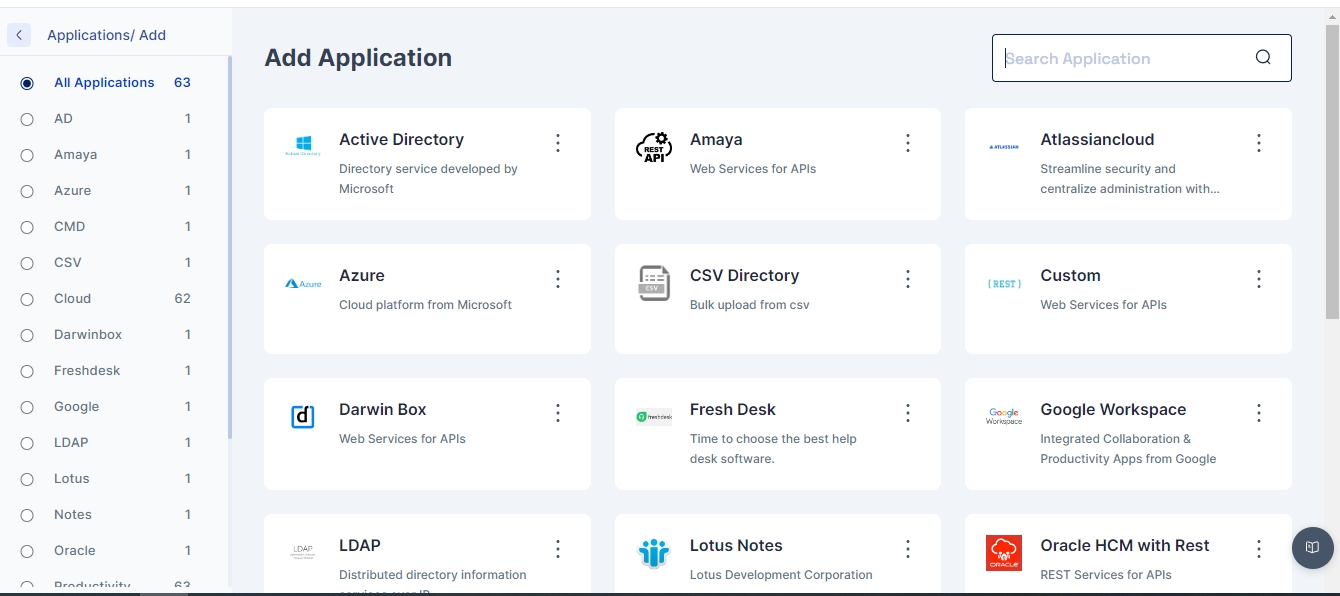

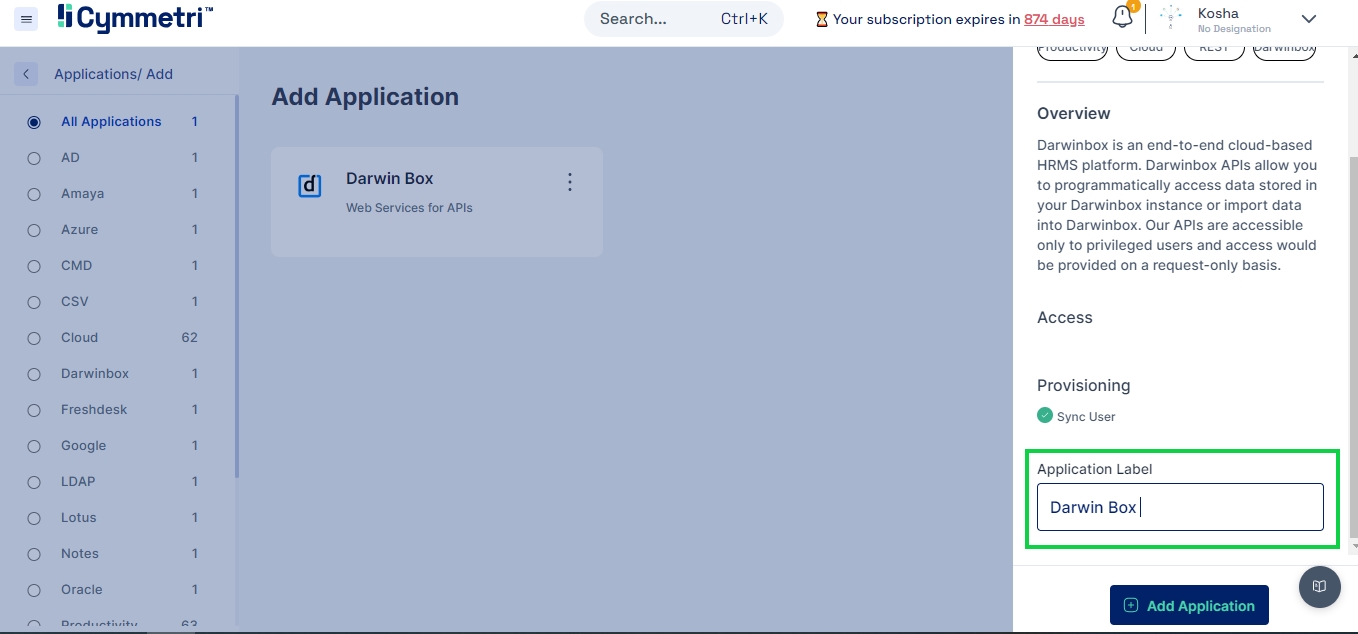
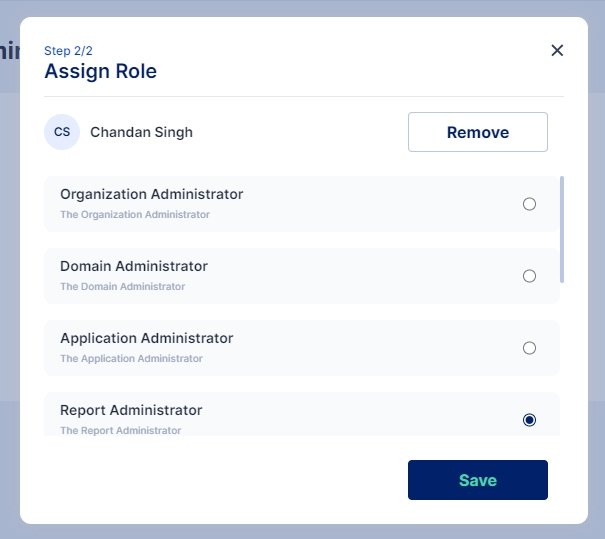
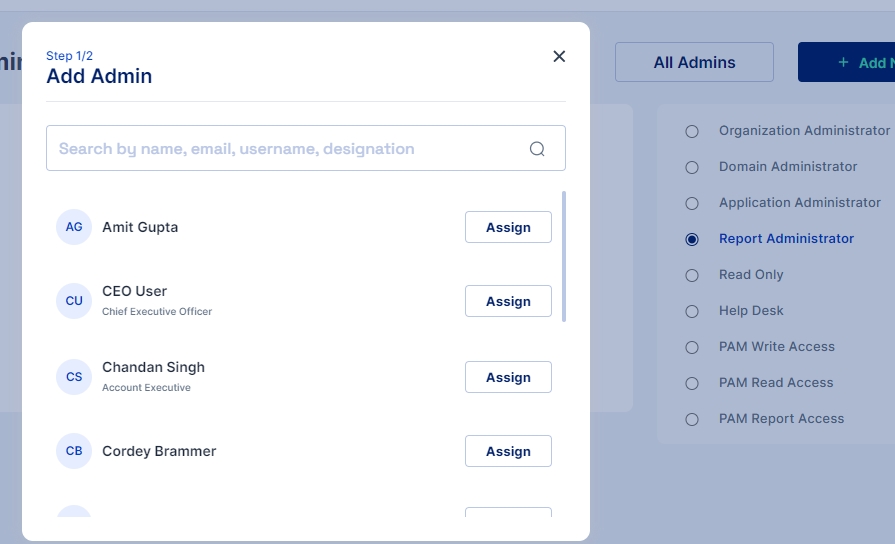
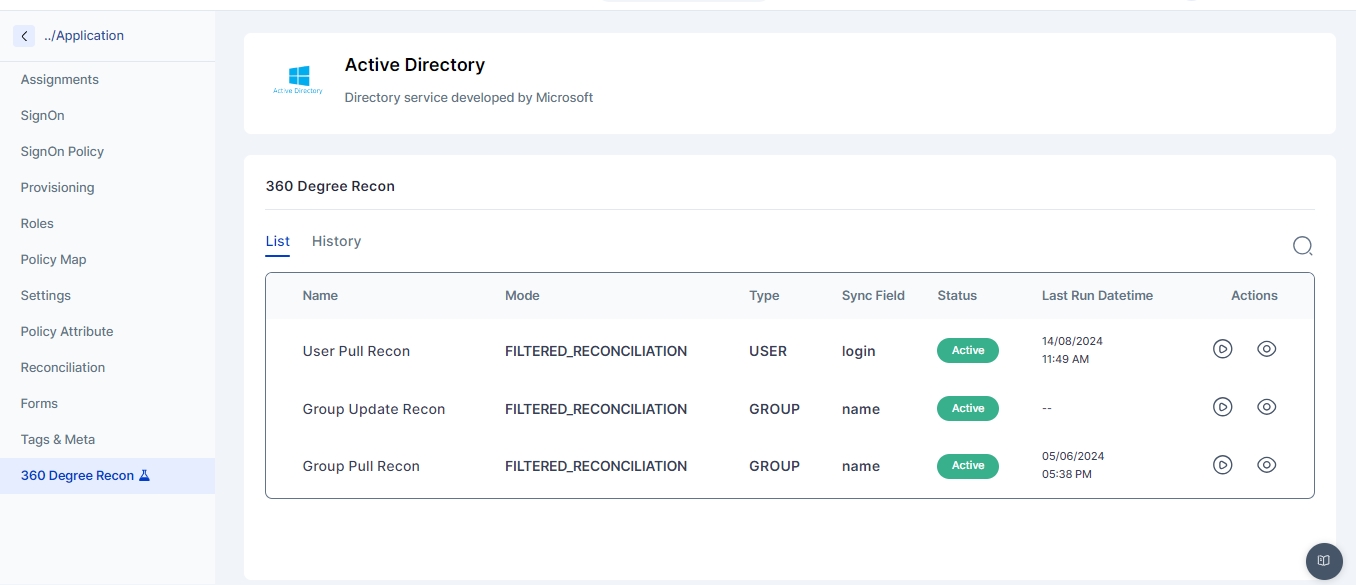

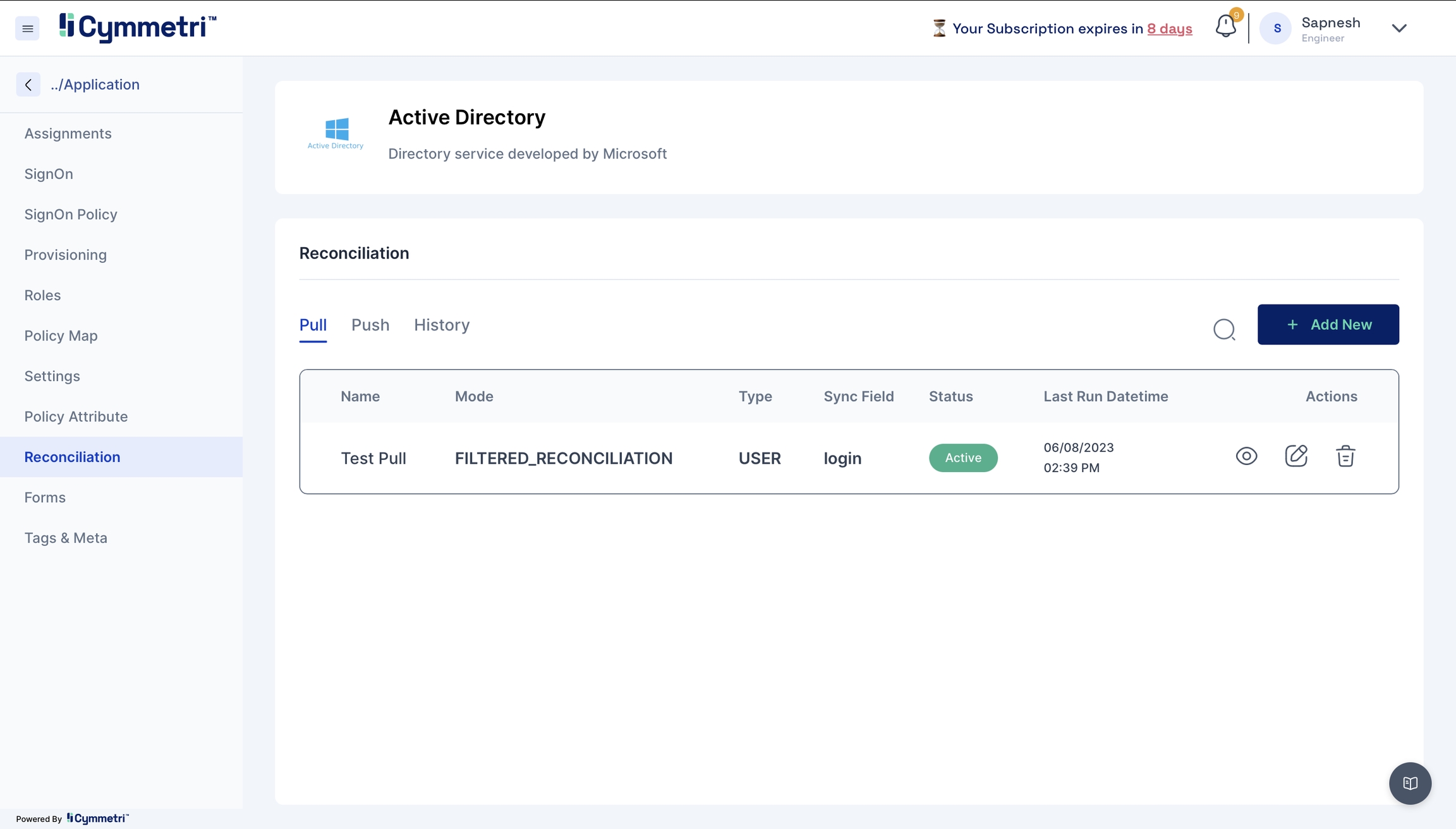
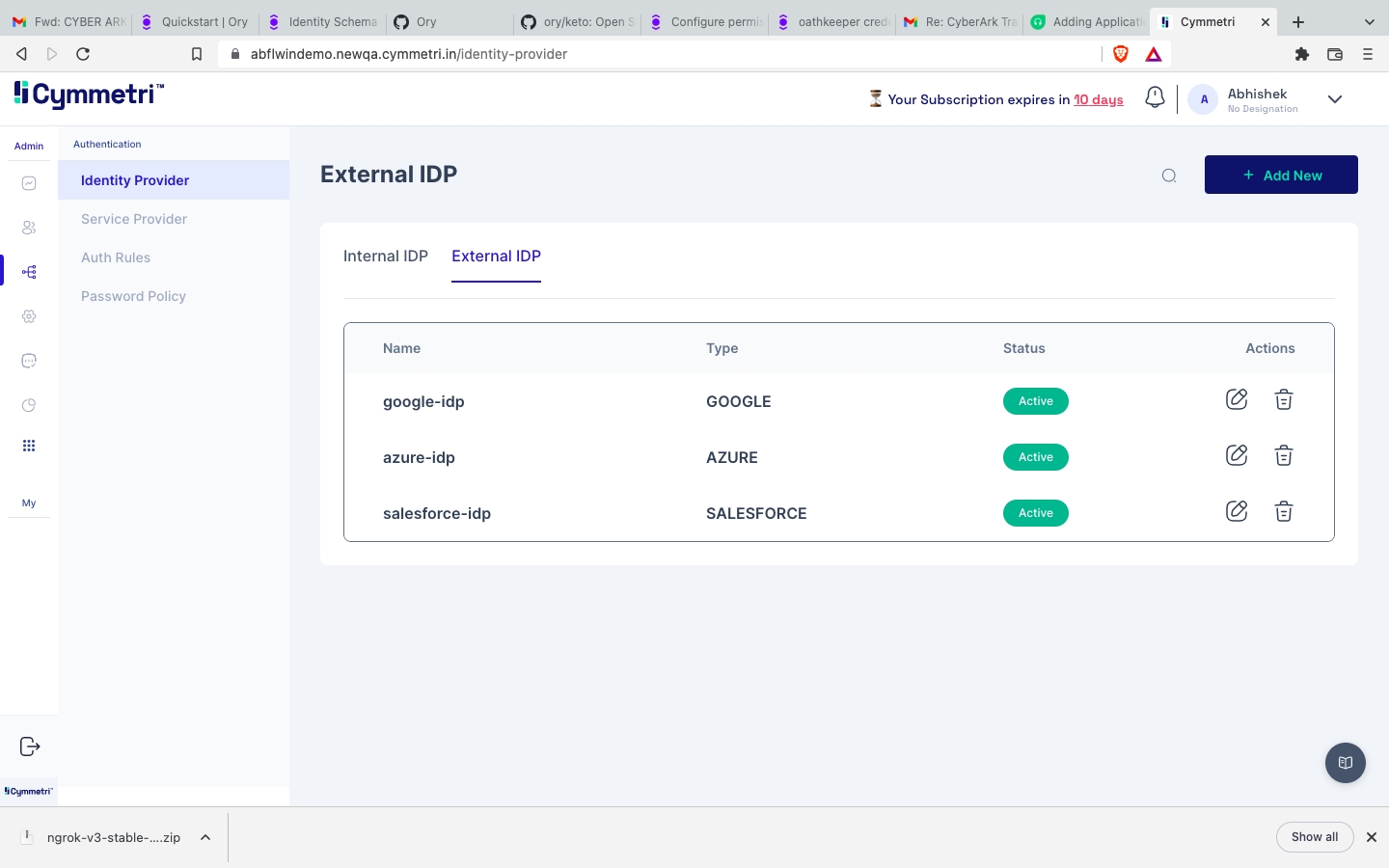
In this section within Cymmetri, a range of general or broad configuration settings and options are managed. These settings encompass various foundational configurations that affect the overall behavior of Cymmetri.
There are different system configurations in Cymmetri mentioned below:
In the Time-Based configuration, system administrators can determine whether the system will send repeated notifications to users based on the number of days remaining, as specified in the 'Send Notifications before' field. This occurs when an application is assigned to the user as a time-based application and is about to expire.
Azure provisioning in Cymmetri involves setting up configurations to automate the creation and management of user accounts in Microsoft Entra ID. This allows for seamless user onboarding and offboarding processes.
To implement Azure provisioning in Cymmetri, follow these general steps:
The administrator needs to login to Azure Portal: https://portal.azure.com
Once logged in click on More services-> button
In the next screen click on Identity -> App registrations inside the Identity management section
Next click on New registration to register a new App. Registering your application establishes a trust relationship between your app and the Microsoft identity platform. The trust is unidirectional: your app trusts the Microsoft identity platform, and not the other way around. Once created, the application object cannot be moved between different tenants.
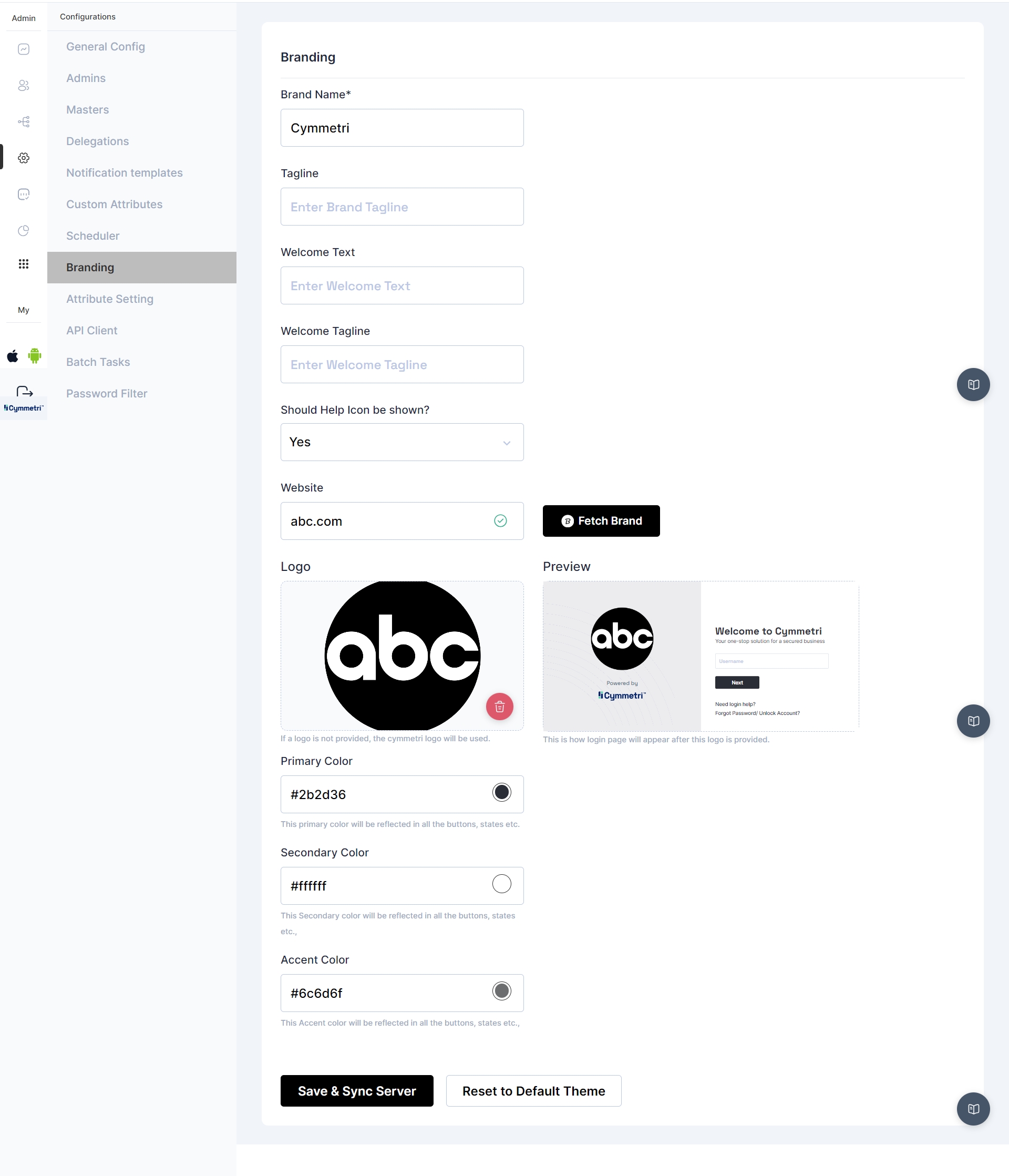
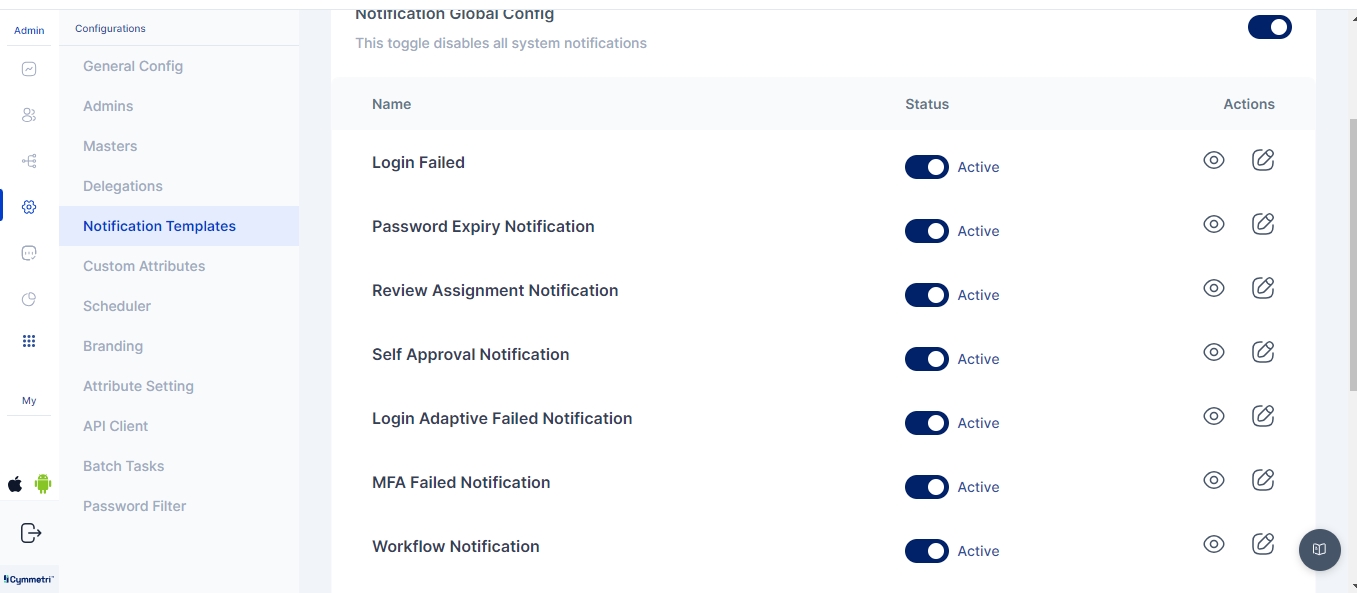

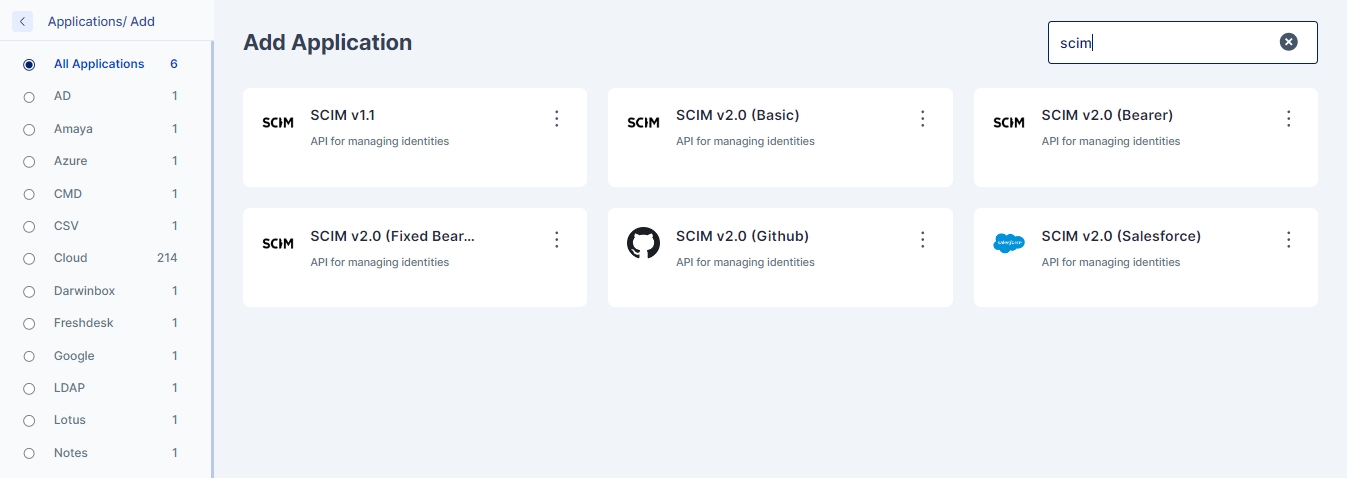

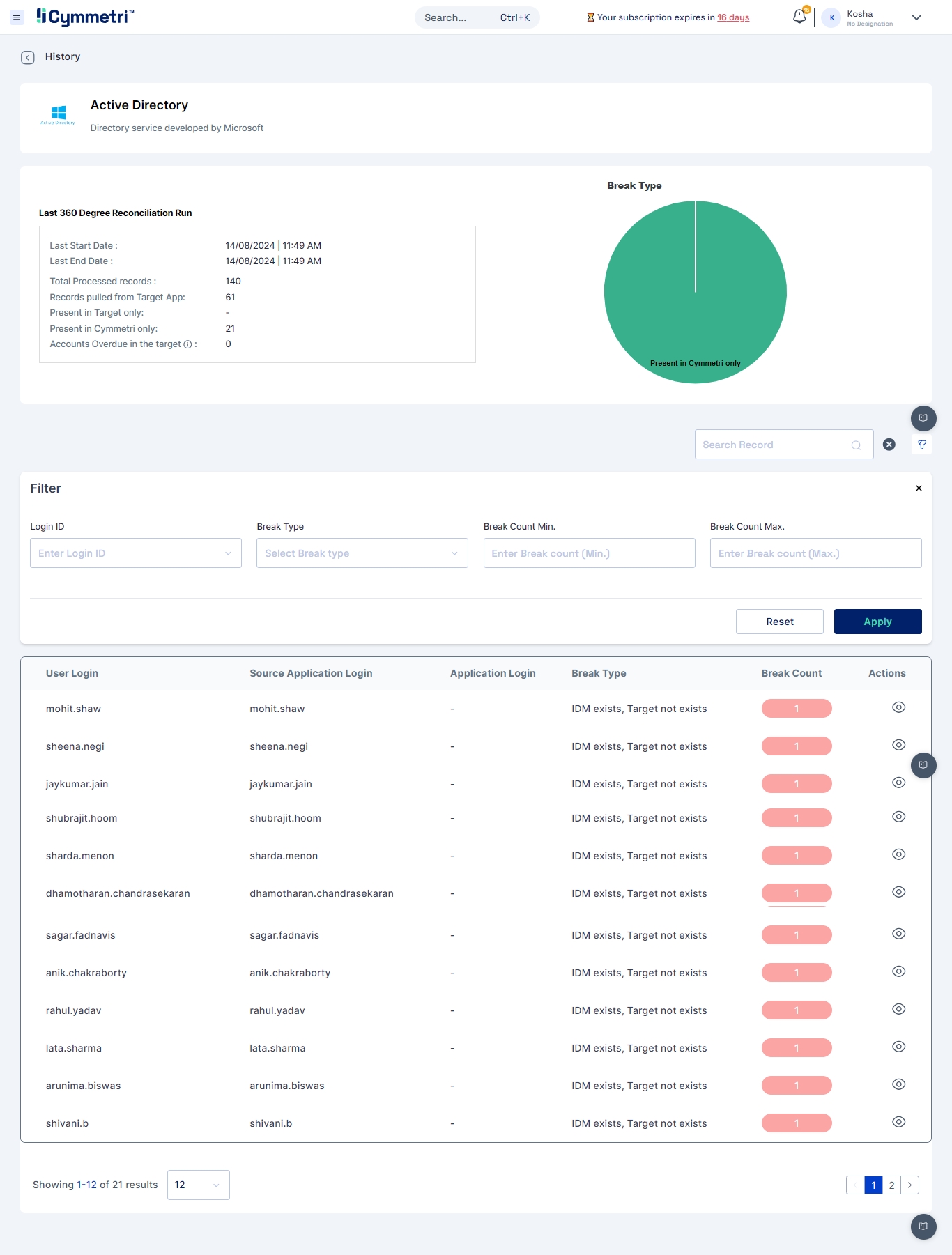



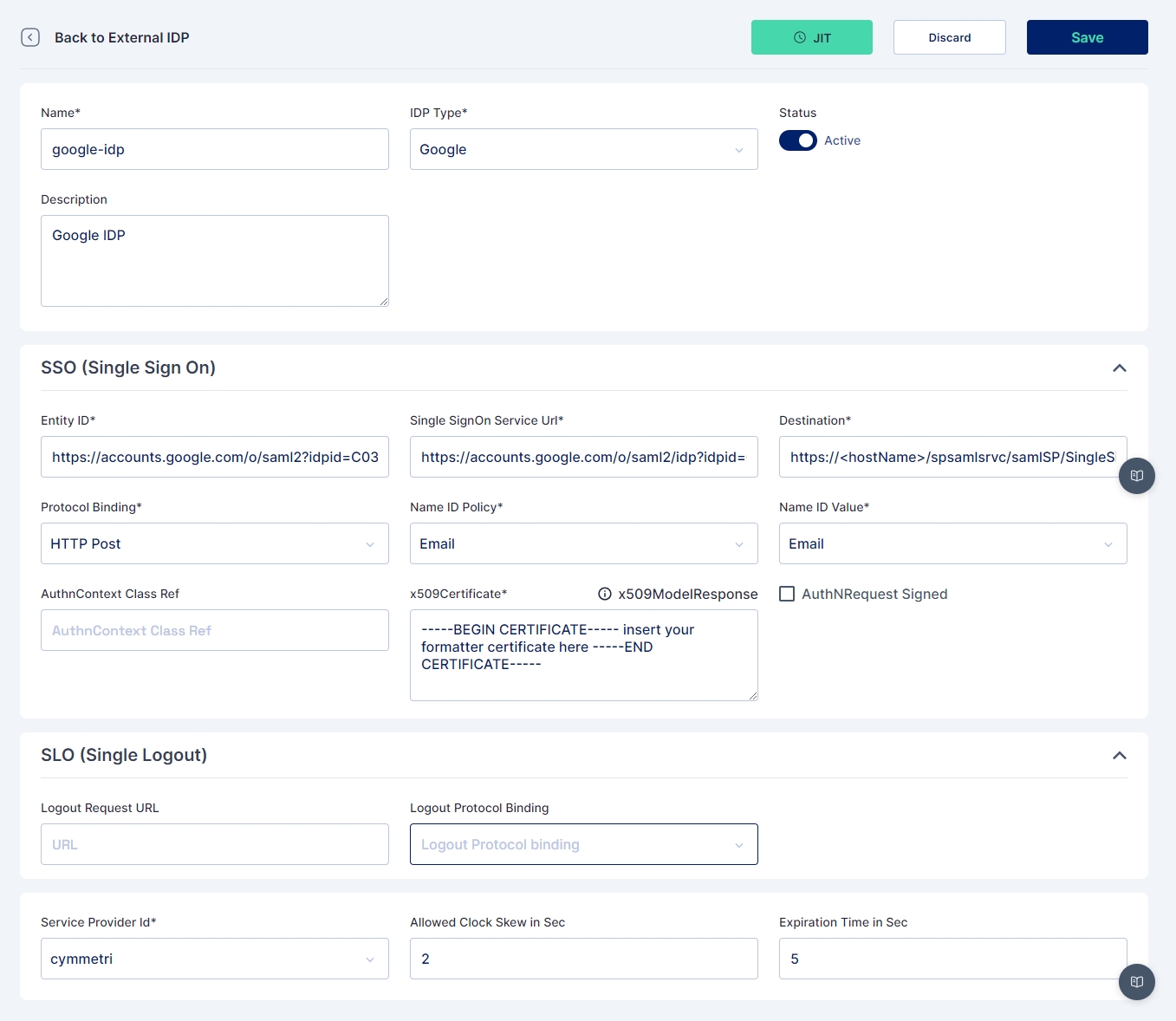

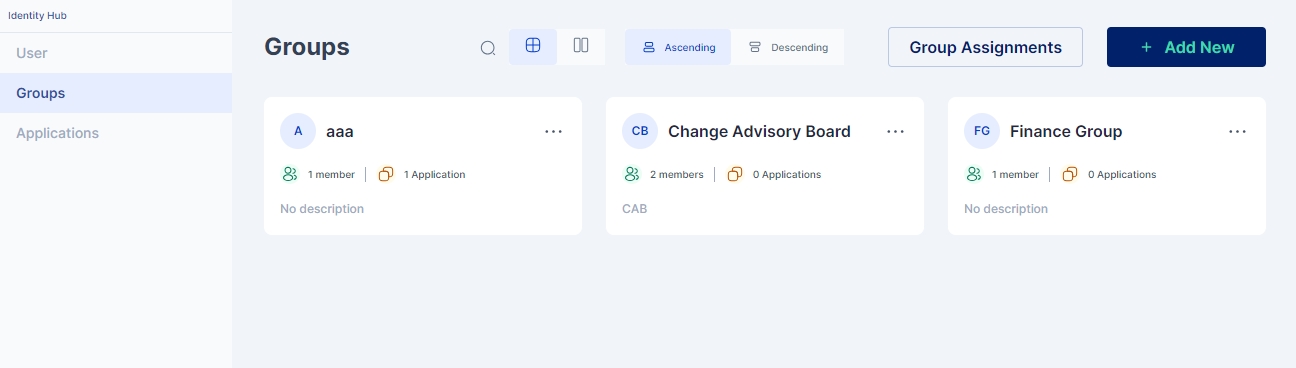
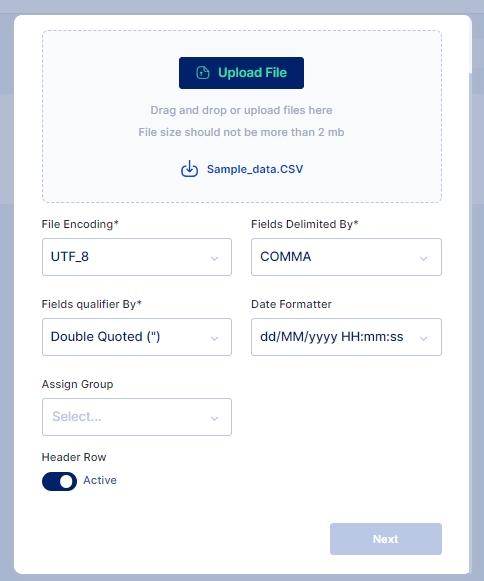
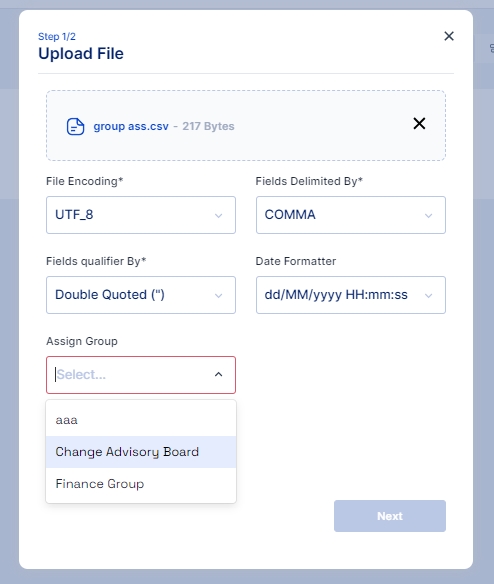
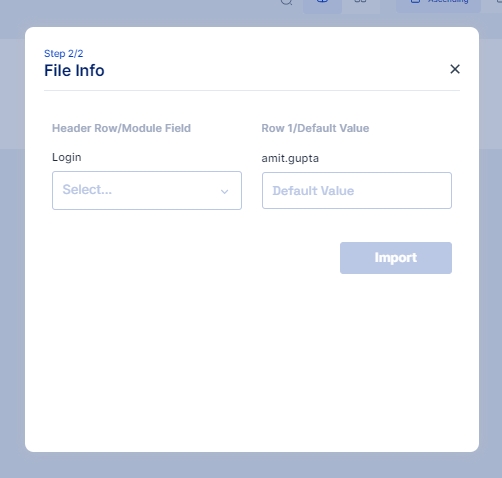
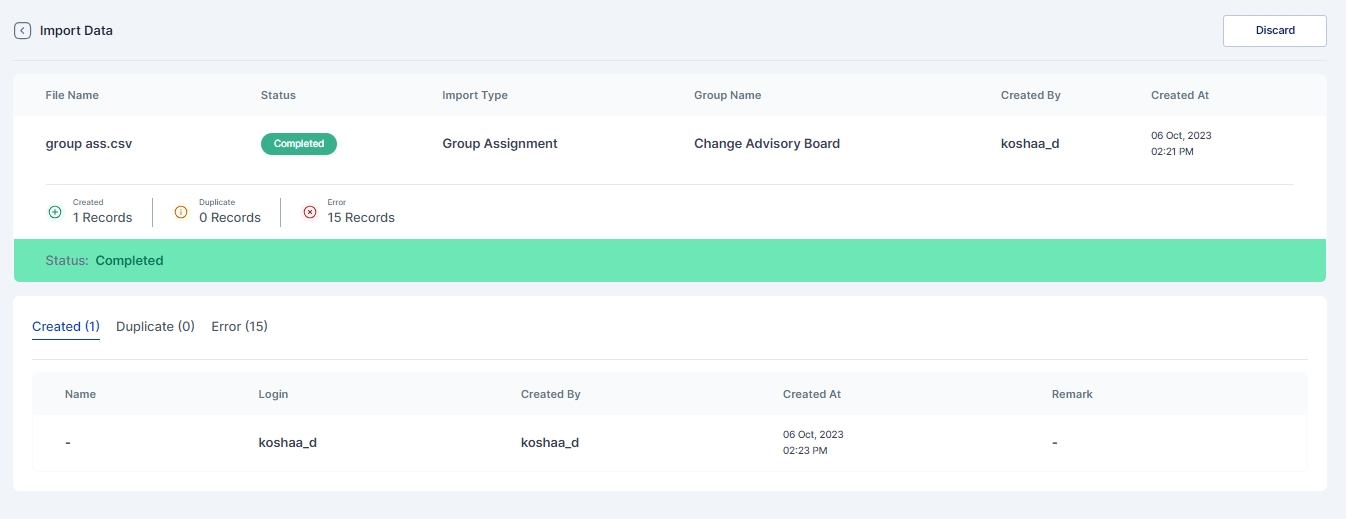
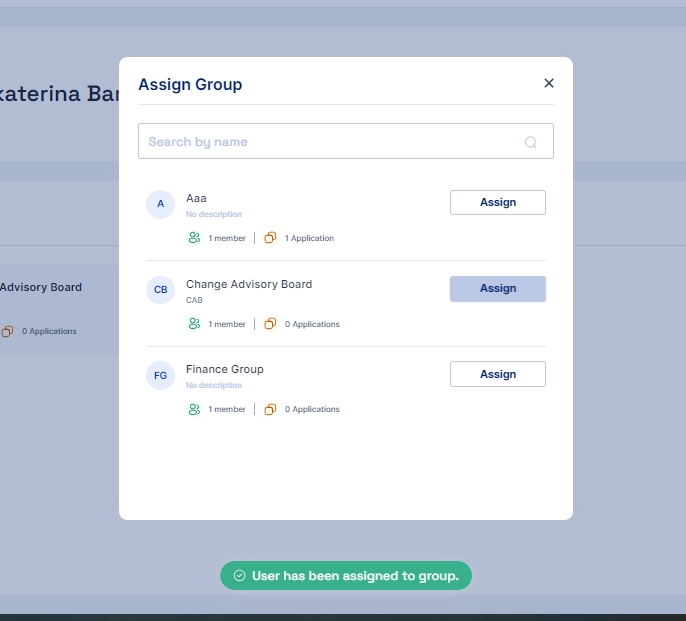
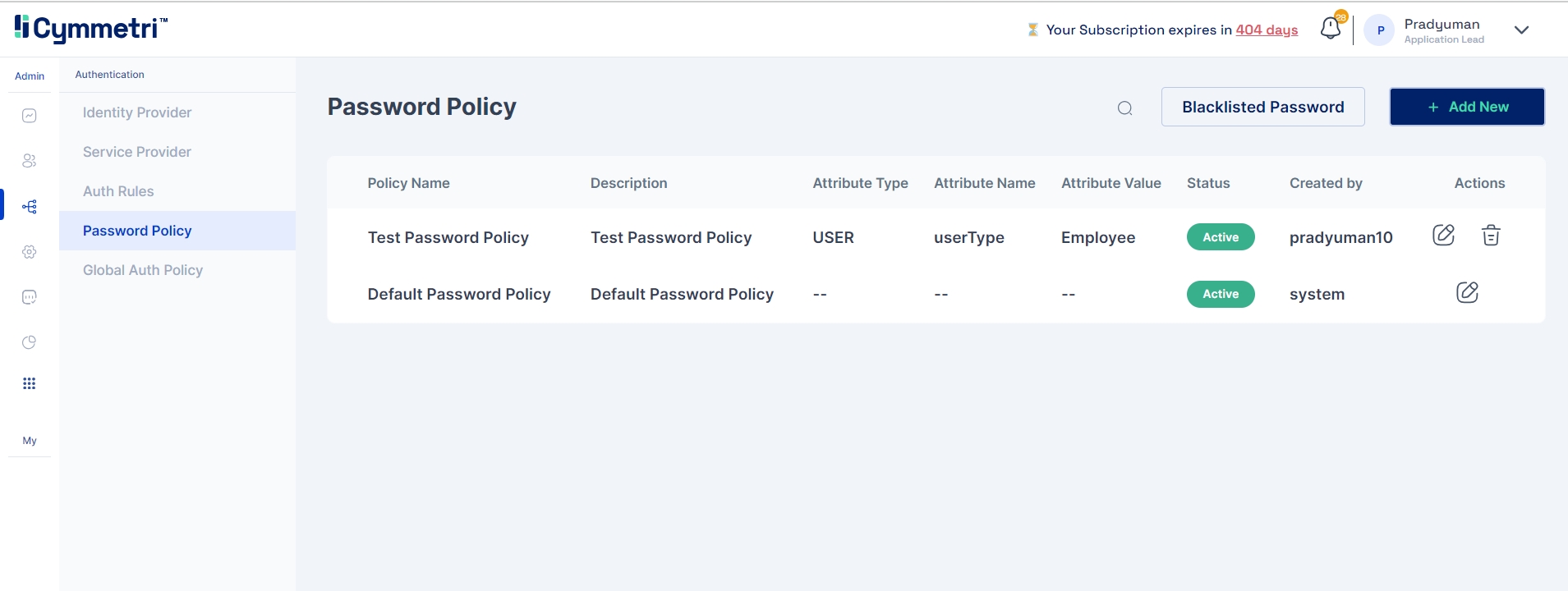
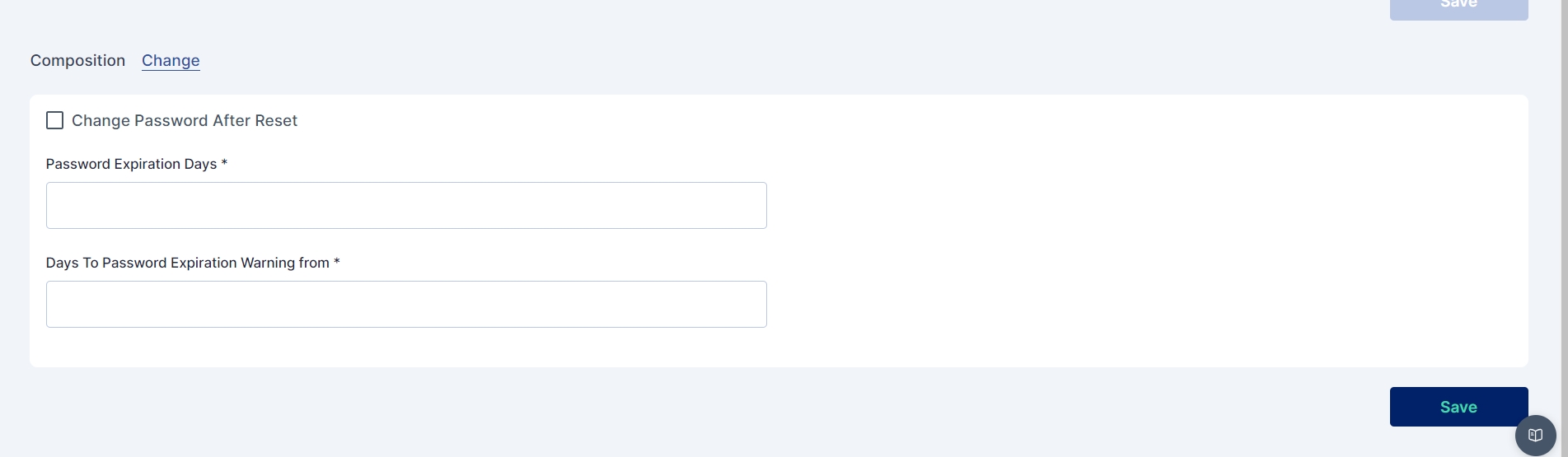
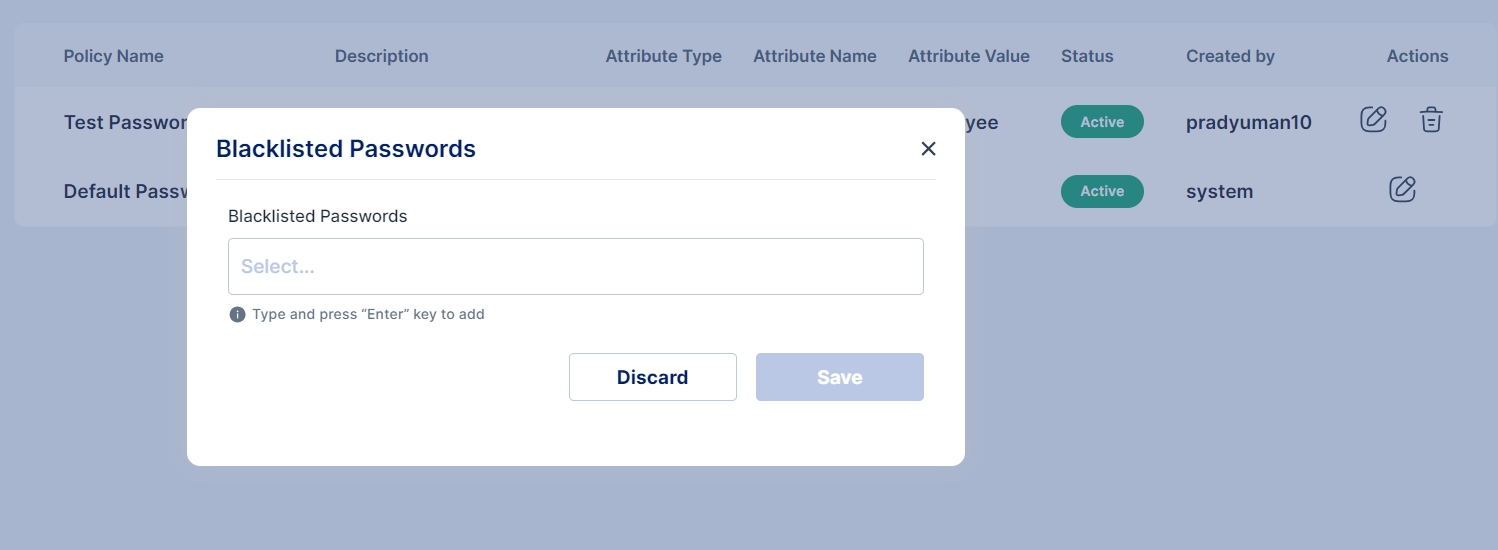
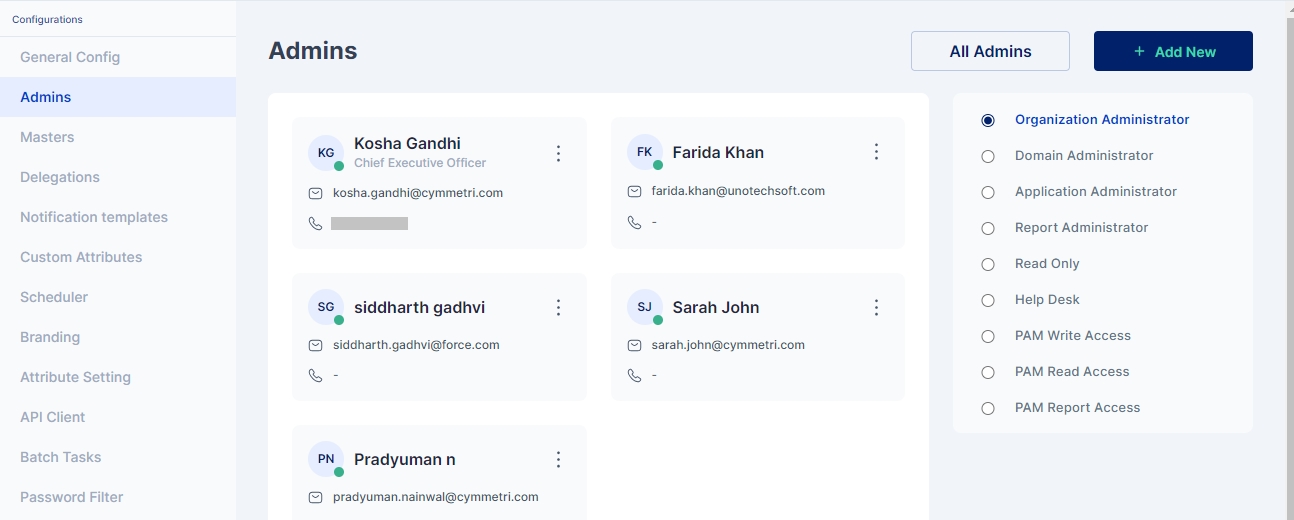

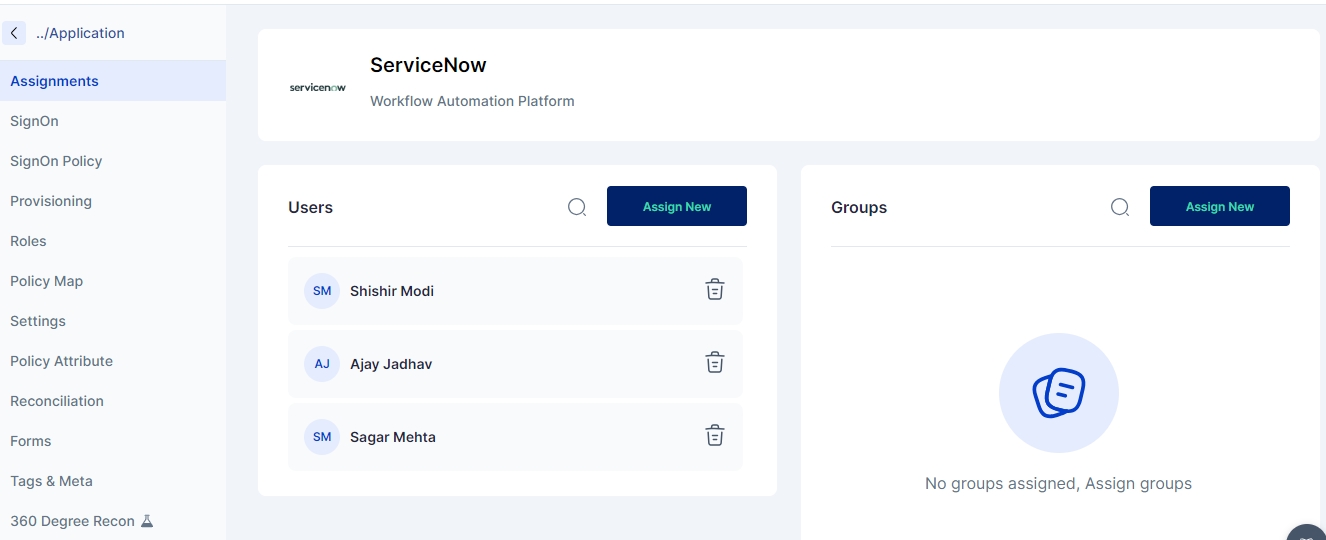
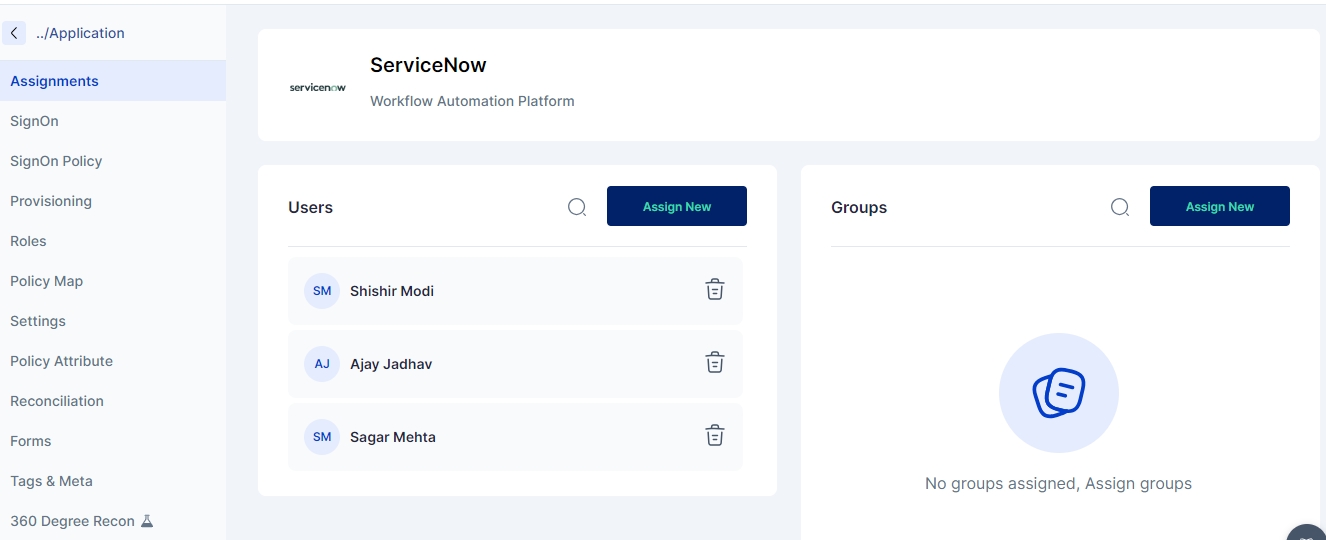
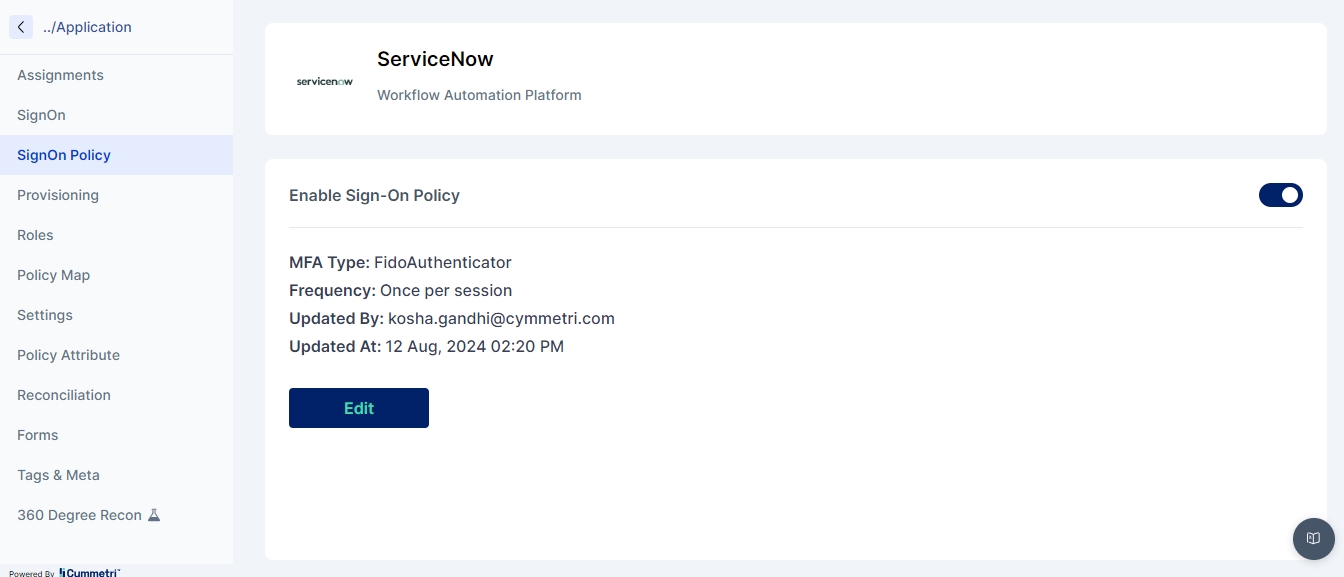
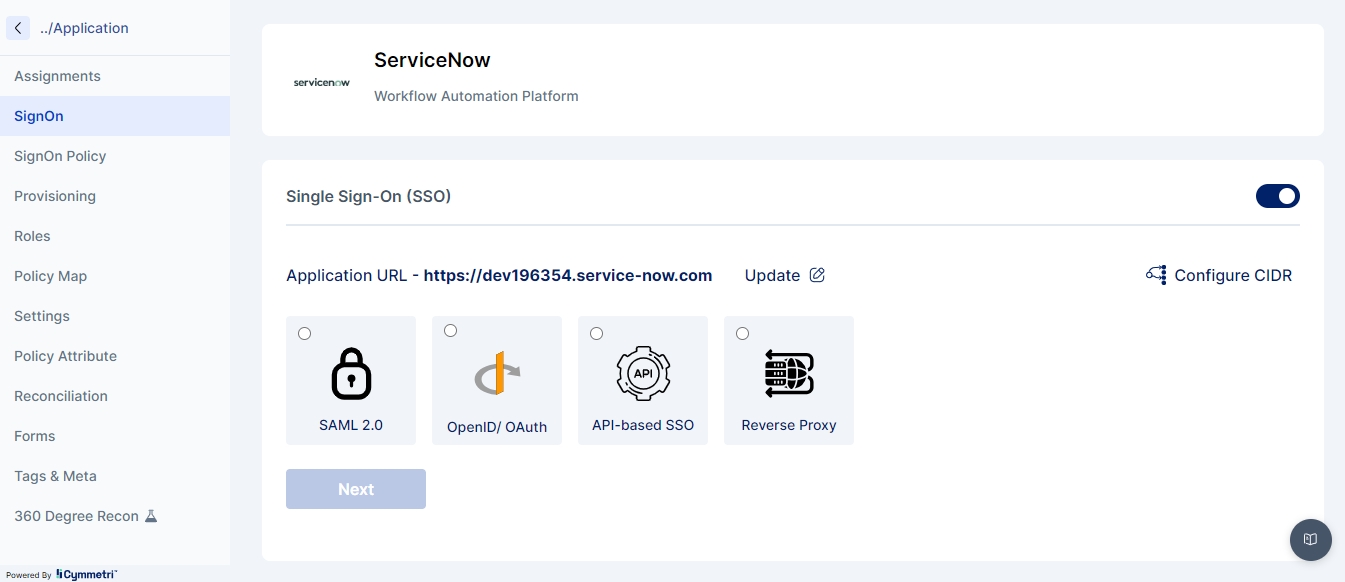
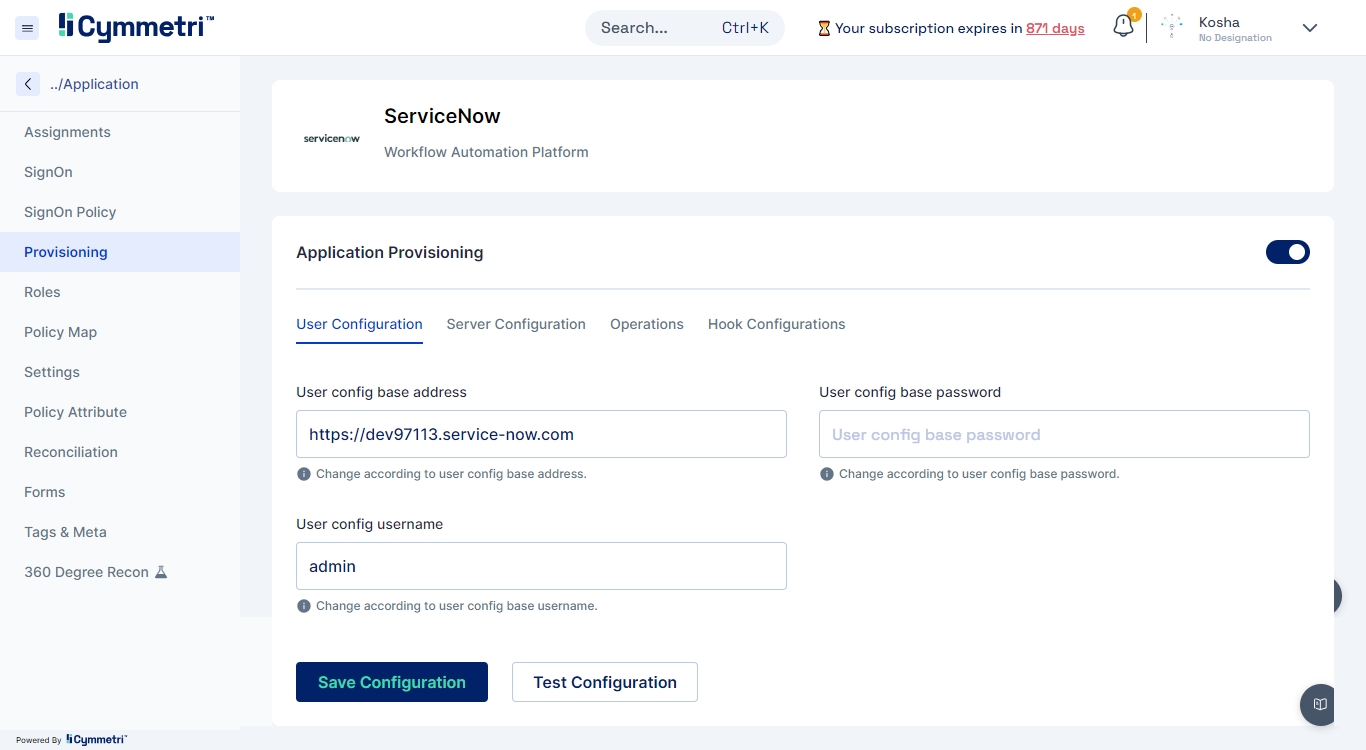
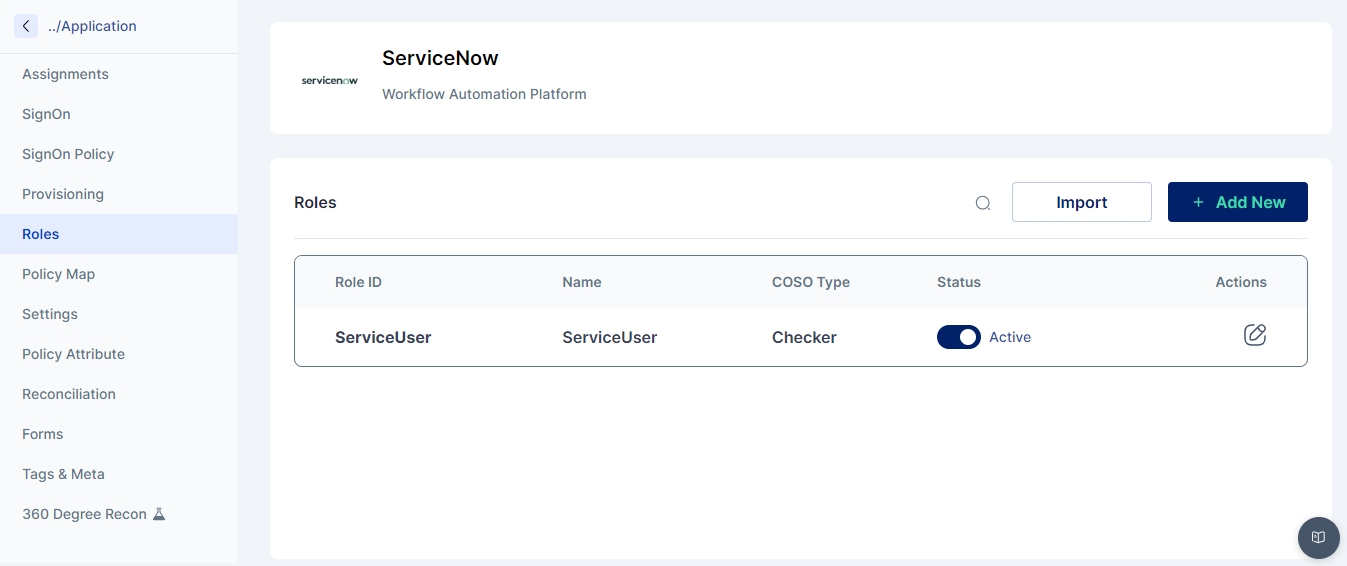
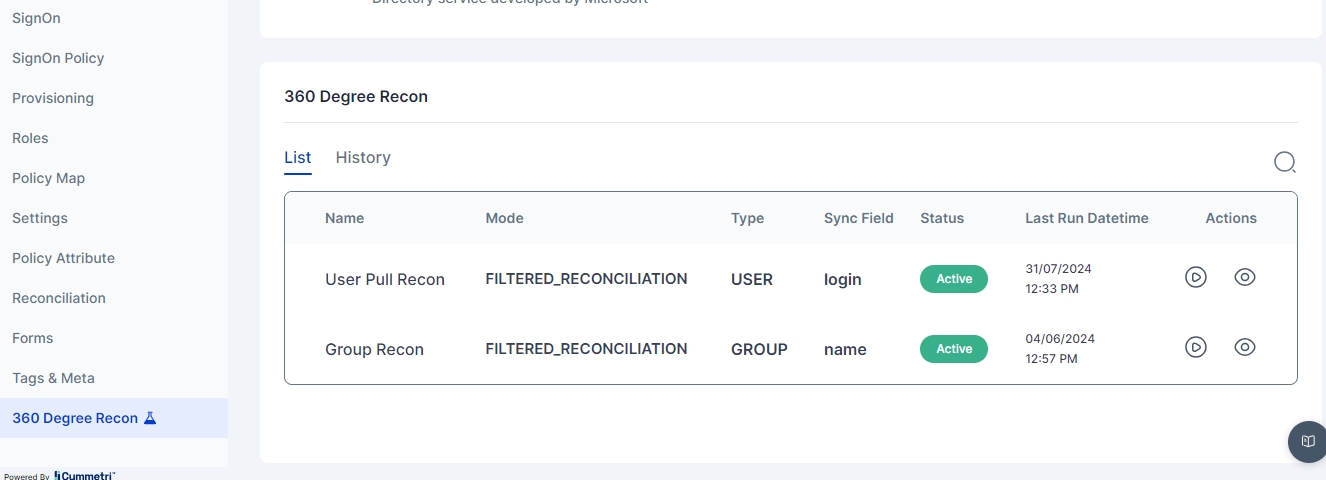
Designation: The specific title or position the user holds.
Date of Birth: The user's birth date.
Age: The user's current age is calculated from the date of birth.
User Type: Classification of the user based on the user types defined in the system.
Login ID: The unique identifier used by the user to access the system.
Landline: The user's landline phone number, if applicable.
Address: The user's full postal address.
Manager: The user's direct supervisor or manager.
Assigning New Applications: Should you need to add more applications to your list, the process is simple. Just click on the Add New Button located on the interface. This action opens up a selection window where you can choose additional applications that you wish to assign to the user.








Search for a user in the search text box, and once the user is found, click on the “Assign” button.
Here we need to decide whether we want to provide a Lifetime Access or a Time Based Access
Lifetime Access: Users have access to the application without any time restrictions.
Time Based Access: Users have access to the application only for the specified range of time. We need to provide a Start Date & Time and an End Date & Time for Time Based Access.
Now click on Save to register a request for the application assignment. If no Workflow is configured for the said application the application is immediately assigned to the user.
If a workflow for application provisioning is configured then the workflow is been initiated.
The workflow approver will then receive a request to approve the user assignment in their inbox.
Now the approver may approve or reject the user assignment
The approver may change the start and end date, if required; refer to the dynamic form attributes passed during the application assignment.
To continue the flow click on Accept button.
Now the next level of approver will be able to see the previous levels of approval, and similar to the previous level of approval, the approver may change the start and end date, if required; refer to the dynamic form attributes passed during the application assignment.
Click “Accept” to proceed.
After the last level approver has also approved the assignment, the backend processes will run the application provisioning flow.
Once the user has been provisioned in the application, they will be able to see it in their list of applications.
If a workflow for application provisioning is configured then the workflow is been initiated.
The workflow approver will then receive a request to approve the user assignment in their inbox.
Now the approver may approve or reject the user assignment
The approver may change the start and end date, if required; refer to the dynamic form attributes passed during the application assignment.
To continue the flow click on Accept button.
Now the next level of approver will be able to see the previous levels of approval, and similar to the previous level of approval, the approver may change the start and end date, if required; refer to the dynamic form attributes passed during the application assignment.
Click “Accept” to proceed.
After the last level approver has also approved the assignment, the backend processes will run the application provisioning flow.
Once the user has been provisioned in the application, they will be able to see it in their list of applications.
These settings and configurations within Cymmetri are specifically related to the management and customization of email-related functionalities. This configuration area allows administrators to set up, manage, and customize the email communications as per the organization's needs.
Archive Config
Within the Archive Config section, administrators have the ability to determine the duration a user remains suspended before transitioning to the archived users' section. This can be specified using the "Archive After" setting.
The system incorporates a scheduler feature, enabling administrators to automate the transition of users from the suspended state to the archived state. The scheduler runs within defined time frames, streamlining the management of user statuses.
As an example, if the "User Archive After" configuration is set to 0 days, a user will promptly move to the archived users section upon suspension, and if it is set to a higher number it will wait for the configured number of days before moving the user to archive. This allows for flexibility in tailoring user management to specific organizational needs.
Within the Workflow Preference Config, administrators have the ability to specify the visibility and editability of workflows associated with user access requests for a particular application. This setting allows for tailored control over how approvers interact with the configured workflow.
When this option is selected, approvers for the requested application are visible to the user initiating the access request. Transparency is maintained throughout the workflow process.
Opting for this configuration ensures that approvers for the requested application remain hidden from the user. The workflow operates discreetly in the background without user visibility.
If this preference is chosen, users initiating access requests have the ability to select approvers based on their availability, providing a more dynamic and user-centric workflow experience.
This functionality applies if a workflow has been configured for the specified application, offering flexibility in managing user access requests in alignment with organizational requirements.
The approvers mapped in the workflow can only be edited only if they are part of the "user list" in workflow configurations.
In conclusion, if the workflow preference config is set to Editable, the requester will only be able to select the approver from the workflow if the approvers are part of a user list.
The administrators have a centralized control panel to define how a user's manager can perform password resets. This feature streamlines the process while ensuring security and flexibility.
The administrator has three distinct options for configuring the password reset process, allowing them to choose a method that best fits the organization's security policies and workflow.
Generate Password: This option allows the user's manager to generate a random, one-time password. The manager must then securely communicate this password to the end-user, who is required to use it for their next login and change it to a new, permanent password immediately. This method ensures that the manager does not have access to the user's long-term password.
Generate Password and Send to User's Email: With this option, the manager triggers the password reset, and the system automatically generates a new password and sends it directly to the user's registered email address. This eliminates the need for the manager to manually transmit the password, reducing the risk of human error and improving efficiency.
Send Reset Password Link to User's Email: This is the most secure option. The manager initiates the process, but instead of a password, the system sends a secure, time-sensitive "Reset Password" link to the user's email. The user must click the link to create a new password, ensuring that only they have access to their account and that the process is compliant with modern security best practices.
To add a layer of security and prevent unauthorized password resets, administrators can enable the "OTP required" setting. When this is activated, a one-time password (OTP) is sent to the user's registered mobile number before the password reset can be finalized. This ensures that the user is the legitimate owner of the account before any password changes are applied, guaranteeing that only the right person's password is being reset.
For understanding how the admin resets the password, refer to User Details.
The User Decommission Config is a vital feature in Cymmetri, allowing administrators to automate user decommissioning based on login activity.
In this configuration, actions are triggered if the user hasn't logged in to Cymmetri in N number of days
Config Days: Set the threshold for user inactivity in terms of days. Users who have not logged in for the specified duration will be subject to the defined actions.
Actions: Choose from three distinct actions to be taken when the specified inactivity threshold is reached:
None: No action will be taken based on user inactivity.
Inactive: Users exceeding the configured inactivity period will be marked as inactive.
Delete: Users who have not logged in for the specified duration will be suspended from the system.
Syslog configuration in Cymmetri allows for the seamless integration of logging and event information with external Syslog servers. By defining specific parameters, administrators can ensure that critical system events, user access information, and other relevant data are transmitted in real-time to a Syslog server.
Syslog Config fields:
Syslog Name - Assign a unique name to this Syslog configuration
App Name - Specify the application name associated with this Syslog configuration.
Server Host Name - Enter the hostname or IP address of the Syslog server that will receive log messages
Server port - Define the port number on the Syslog server where log messages will be sent.
Protocol - Choose the preferred protocol for Syslog communication - TCP or UDP.
In configuring these parameters, administrators tailor Cymmetri's interaction with external Syslog servers, optimizing the logging process to meet organizational needs.
Webhooks in Cymmetri's admin module provide a powerful mechanism for real-time communication and integration with external applications or services. Administrators can configure various webhook settings to enhance the system's functionality and streamline interactions with external components.
Protocol - Communication protocol - (Static field)
Method - HTTP method for webhook requests - (Static Set to post)
Server - Enter the server or endpoint URL where the webhook payloads will be delivered.
Server Context path - provide the context path for the specific service within the server.
Secret - This secret key, known to both Cymmetri and the external service, helps authenticate the webhook requests.
Token Expiry Minutes - Define the duration (in minutes) for which authentication tokens associated with webhook requests are valid.
This setting determines if a user can initiate requests for new applications through the Cymmetri self-service page.
When the status is active, the user will see the "Add New" button on the "My Access" page within the "My Workspace" section. By clicking this button, the user can submit an access request for additional applications.
The User Threshold Config in Cymmetri primarily includes three key functions — Create Count, Update Count, Delete Count, and Send threshold notifications to. These define the maximum number of user creation, modification, and deletion operations permitted within the system in a single day, ensuring controlled provisioning and preventing unintended bulk changes.
Create Count: Sets the maximum number of new user accounts that can be generated.
Update Count: Defines the upper limit for modifications or changes to existing user profiles.
Delete Count: Establishes the cap on how many user accounts can be removed.
Threshold Notifications: You can configure who should be notified when the threshold is exceeded. Notification will be sent via email.
The recommendation configuration defines how the engine generates, manages, and displays application or role suggestions for users during campaigns and workflows. It ensures recommendations are personalized using user attributes, access history, and peer behavior, while maintaining compliance through segregation of duties checks. The configuration also allows dynamic recalculation of scores when user data changes, provides flexibility to enable or disable recommendations with corresponding updates in the UI and history, supports multiple tenants, and retains recommendation history for reporting even if recommendations are later disabled. 1. Recommendation Engine in Campaign:
Recommendation Engine in Approver Inbox:
The External SoD Checks Config enables configuration of segregation-of-duties checks, webhook connections, and workflows to detect, notify, and manage access violations during application assignments. The Webhooks Config in Cymmetri’s External SoD Service is used to establish connections with external systems or services. It allows the platform to send real-time event notifications (such as SoD violations or workflow triggers) to defined webhook endpoints. When All Applications is selected, External SoD checks will run for every application, except those explicitly listed in the Excluded section, which will be ignored during violation detection.
Application Assignment with role during External SOD Checks: When a user is assigned an application along with a specific role, the system evaluates the assignment against configured External SoD rules.
Multiple SOD Violations Detected: It indicates that a user’s application or role assignment has triggered more than one segregation-of-duties conflict, all of which are captured and sent for review through the workflow process.
Inbox Violations: Segregation-of-duties conflicts detected during application or role assignments, which are delivered to the user’s or approver’s inbox for review and necessary action.
Workflow Approver View: It is the interface where approvers can review, approve, or reject access requests that have triggered segregation-of-duties violations, ensuring proper compliance before access is granted.
This integrated advanced CAPTCHA validation capabilities bolsters the security against automated threats and bot-based attacks. The platform now supports two distinct methods, providing administrators with a flexible approach to securing user interactions.
hCaptcha: This method is a privacy-focused and widely adopted alternative to traditional CAPTCHA. It requires users to perform a simple task (e.g., identifying objects in an image) to prove they are human, effectively blocking bots while maintaining user privacy.
Traditional CAPTCHA: This classic method uses distorted text or numbers that users must correctly enter. While this method is effective, it can sometimes be more challenging for users to solve.
These integrations enable Cymmetri to enhance its security posture by providing a robust defense layer, ensuring that user registration and login processes are protected from malicious automated activity.
From this menu, the administrator has two options:
hCaptcha Type: Selecting this option enables hCaptcha validation, which utilizes simple, interactive tasks for user verification.
Traditional CAPTCHA: Choosing this option will implement the classic method of using distorted text.
The administrator can then save the configuration. Below is an example of what the traditional CAPTCHA looks like to an end-user.

Next enter the Application Name and select the Supported account types to organizational directory only : Accounts in this organizational directory only (Cymmetri Organization only - Single tenant) and then click on Register
Once registered next click on Authentication menu and +Add a platform.
On the next screen select Mobile and desktop applications
Enter a Custom redirect URIs: http://localhost and click on Configure
Further enable the Public Client flows and click on Save button
Next go to Certificates and secrets menu and create a new client secret:
Next enter a Description for the and select the duration after which the secret would Expire -Recommended is 180 days (6 months) but can be changed as per the need. Once both the details are entered click on Add button
Next copy and save the Client Secret ID and Client Secret Value in a safe and accessible place. Client secret values cannot be viewed, except for immediately after creation. Be sure to save the secret when created before leaving the page.
Once the client secret details are stored next click on API permissions menu and then + Add a permission
On this page select Microsoft Graph
On the next page we require permissions for both Delegated and Application permissions. Select each type of permission and in that Search and select the following permissions/scopes:
APIConnectors.Read.All
Directory.ReadWrite.All
OpenID (Not available for Application Permissions)
PrivilegedAccess.Read.AzureAD
User.ReadWrite.All
Directory.Read.All
Once all the permissions are added a warning is shown: "You are editing permission(s) to your application, users will have to consent even if they’ve already done so previously." The administrator needs to click on the "Grant admin consent for Cymmetri Organization" link
On the click of the link a popup appears to grant admin consent, click on Yes
Next click on Expose an API and then click on Add to add an Application ID URI: The Application ID URI, also called identifier URI, is a globally unique URI used to identify the web API. This URI is the prefix for scopes in the Oauth protocol. You can either use the default value in the form of api://, or specify a more readable URI.
On the next page keep the default values intact and click on Save button
Finally you can see the Overview page that contains all the information you need to configure Azure in Cymmetri.
Also the User config Application Authority can be obtained from the endpoint section in the Overview page:
This completes the Azure side of the configuration, next the administrator needs to need to move to Cymmetri and configure the Azure application. Mentioned below are the steps required to configure Azure in Cymmetri:
Add a new Azure application Identity Hub->Applications and then click on the +Add New button
Once added the administrator needs to go to Policy Attribute section and ensure all the below mentioned attributes are present (Add if not already present):
mailNickname
displayName
__PASSWORD__
__NAME__
userPrincipalName
givenName
surname
usageLocation
Next the administrator needs to go to the Policy Map section and ensure a mapping shown as below is created:
displayName
displayName
-
True
True
__NAME__
login
-
True
True
Once the policy map is created next the administrator needs to go to Provisioning section and then to Server Configuration and need to configure the connector server as shown below:
Once the Server Configuration is done next the administrator needs to implement User Configuration with the below mentioned fields:
User config Application Authority: This is the authority under which the application operates. For example, if you're using Azure AD, the application authority might be https://login.microsoftonline.com/<tenant_id>/oauth2/authorize
User config application client id: This is the unique identifier for your application. It is provided by Azure when you register your application. For example, e9a5a8b6-8af7-4719-9821-0deef255f68e.
Client Secret: This is a secret key used by the application to prove its identity when requesting access tokens. It should be kept confidential. For example, 7f7df45a-251e-49d3-a396-748bf8e05a3c.
User config domain: This is the domain associated with your Azure AD. For example, contoso.onmicrosoft.com.
User config base password: This is the base password used for your application. For example, MyBasePassword123.
Redirect URI: This is the URI to which Azure AD will redirect the user after authentication. For example, api://05b765c3-d64f-7704-b0d8-5c4c6bc674df
User config resource URI: This is the URI of the resource (API, web app, etc.) that the application wants to access. For example, https://graph.microsoft.com.
Azure Tenant ID: This is the identifier for your Azure AD tenant. For example, 72f988bf-86f1-41af-91ab-2d7cd011db47.
User config base username: This is the base username used for your application. For example, [email protected].
Once the configuration is done and saved, Next click on TEST CONFIGURATION to test if Cymmetri is able to connect to Azure Server.
For assigning any sort of licenses to a user of various products two main policy map entries need to done as shown below:
azureLicense: Need to provide license key for the product you wish to assign to the user
usageLocation: This field needs a two-letter country code (ISO standard 3166). Required for users that are assigned licenses due to legal requirements to check for availability of services in countries. Examples include: US, JP, and IN.
The value for azureLicense can be obtained as explained below:
Go to https://admin.microsoft.com/ and login using the admin credentials. Once logged in go to Billing->Licenses->Microsoft Teams Exploratory
Once you click that it opens the page from which we can copy the product id from URL as shown below:
Once all the above configuration is done, on the same page in Cymmetri go to Assignments section and assign users to the application and ensure that these users are created in Azure's Microsoft Entra ID along with the Microsoft Teams license.
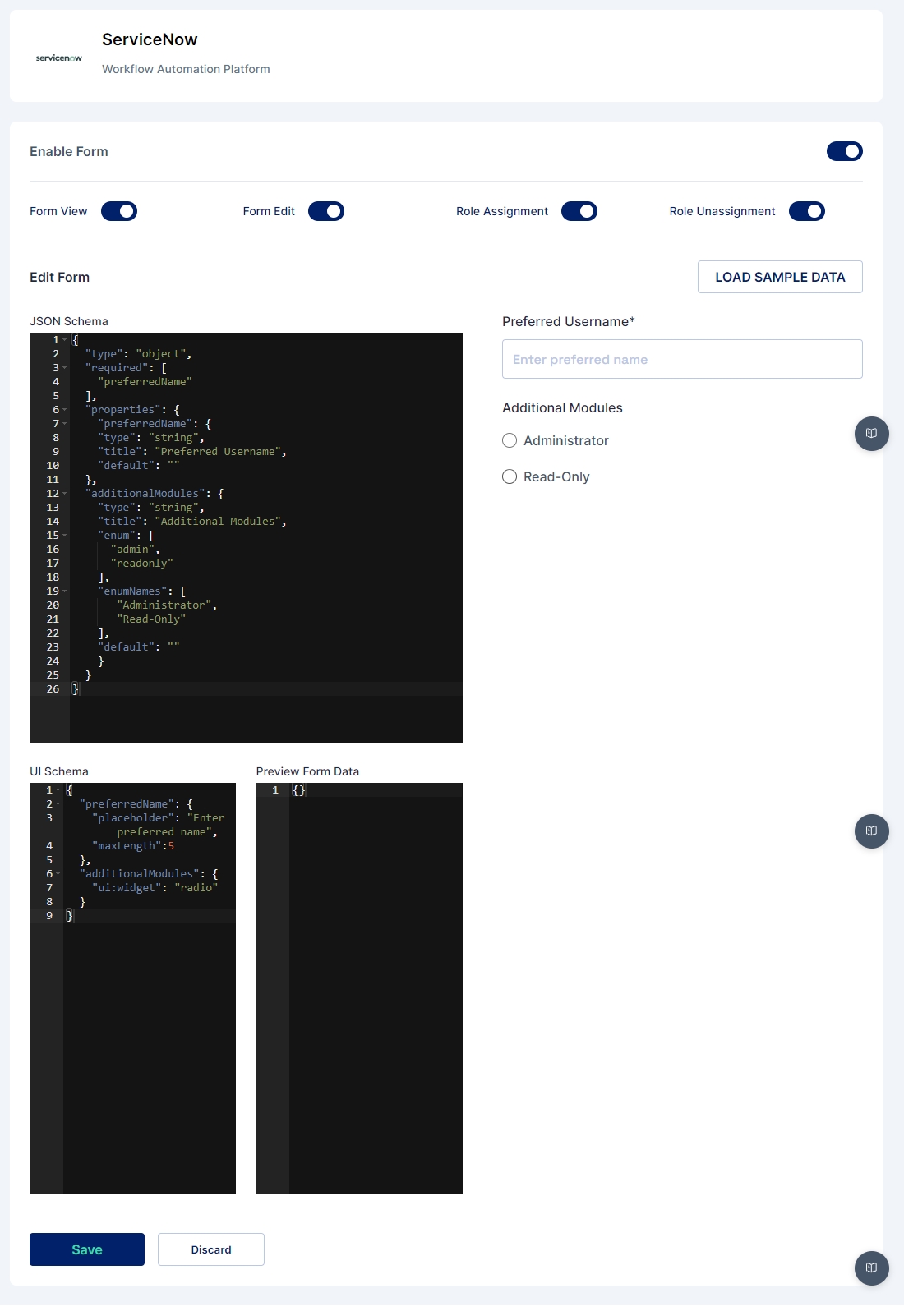
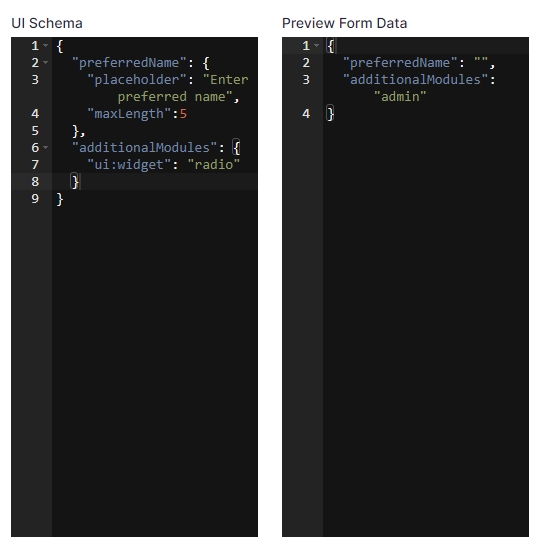
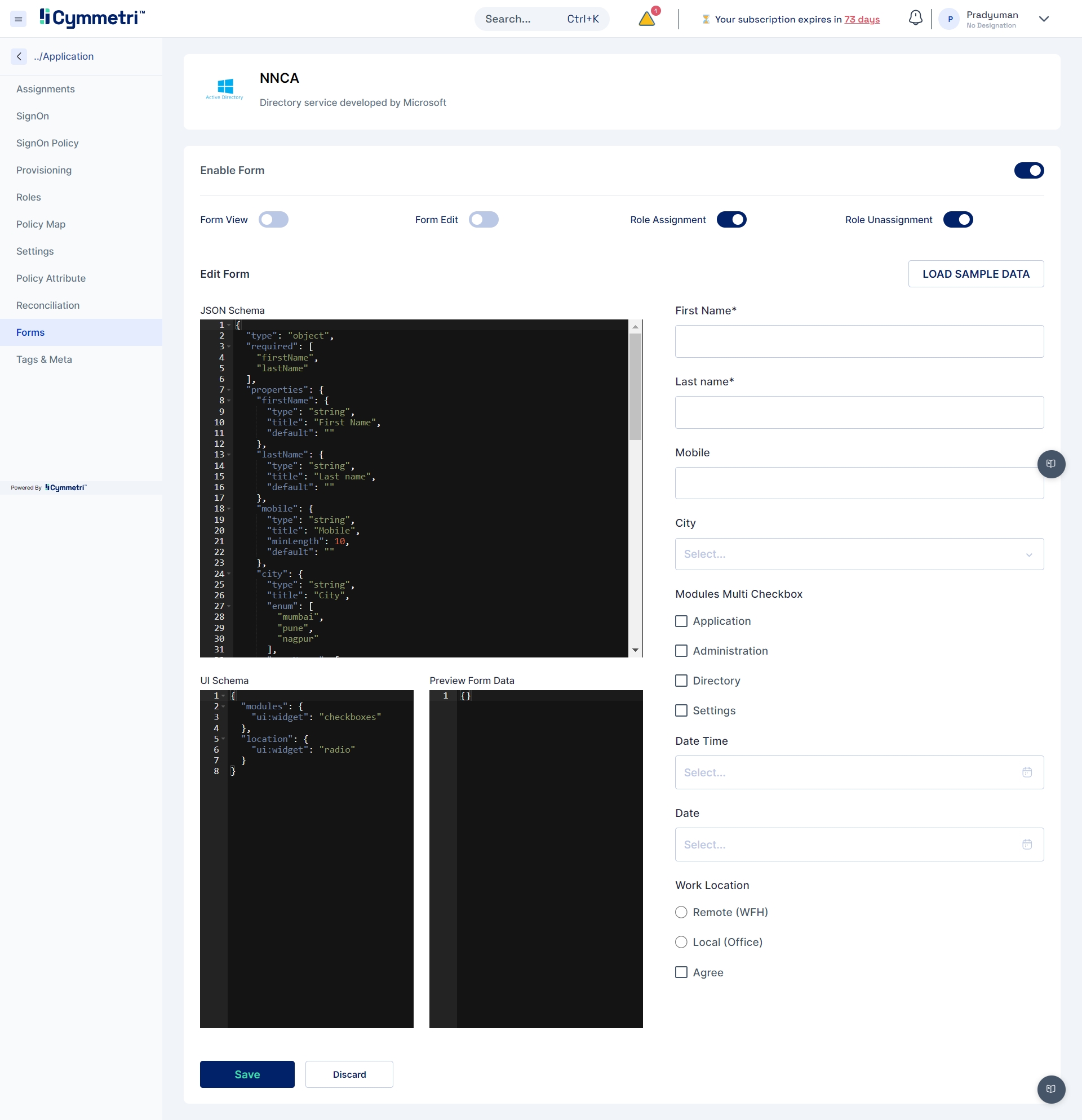
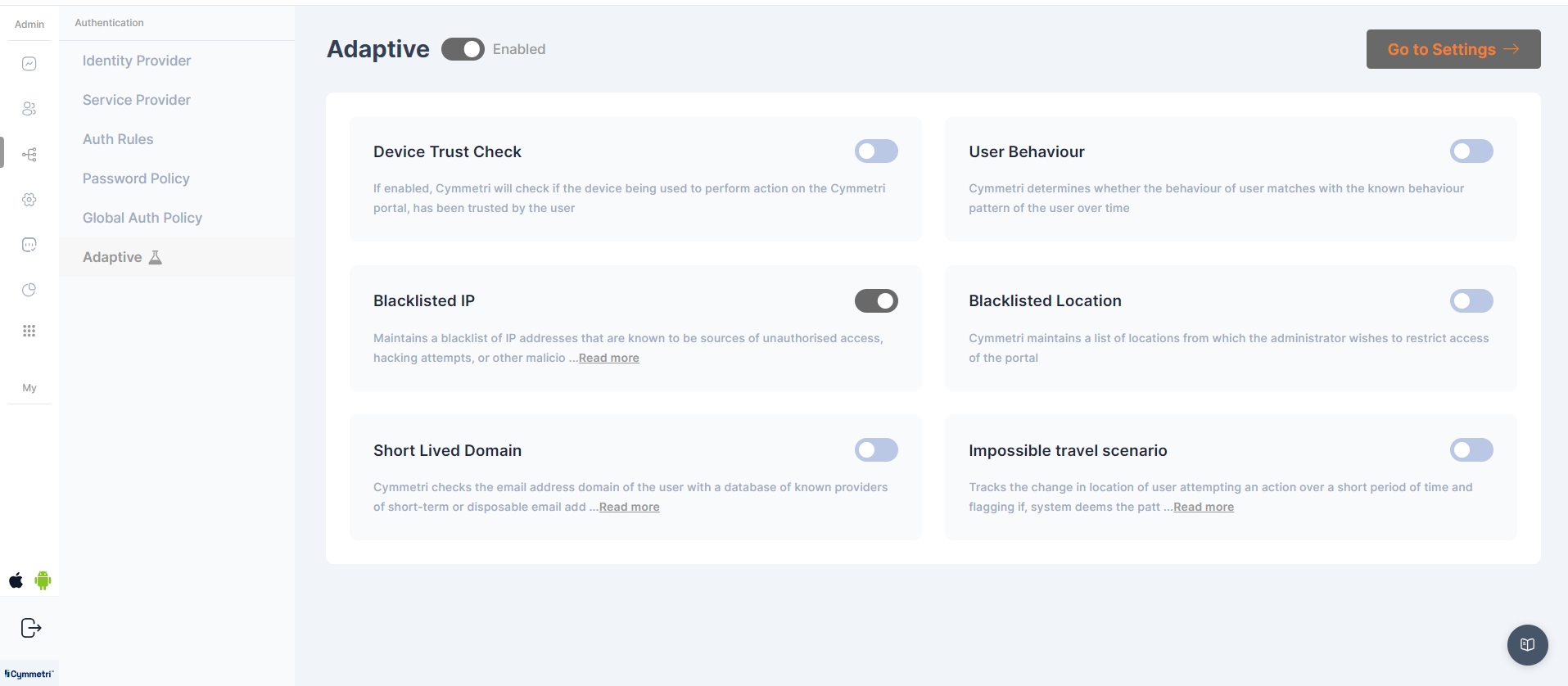







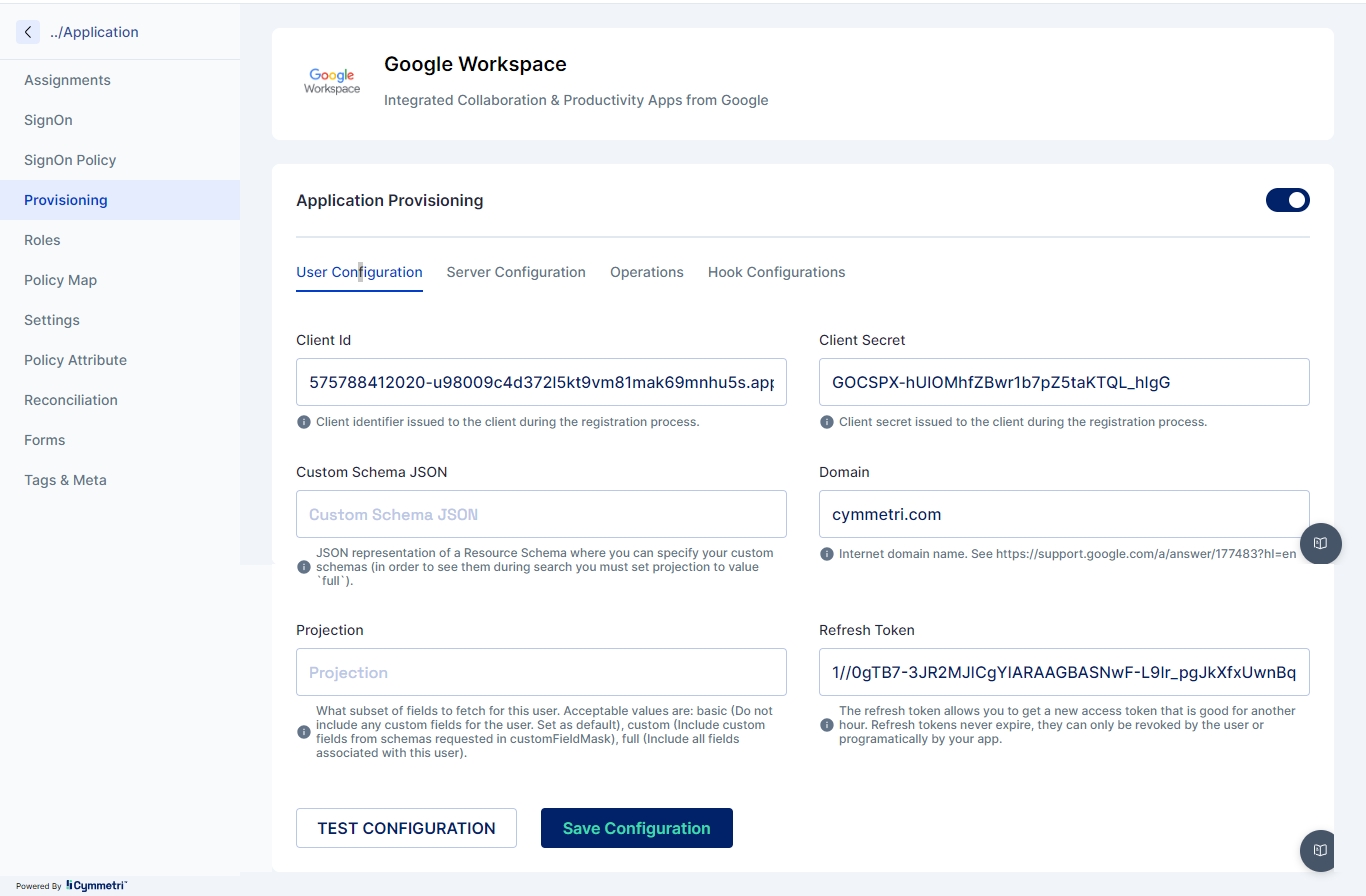


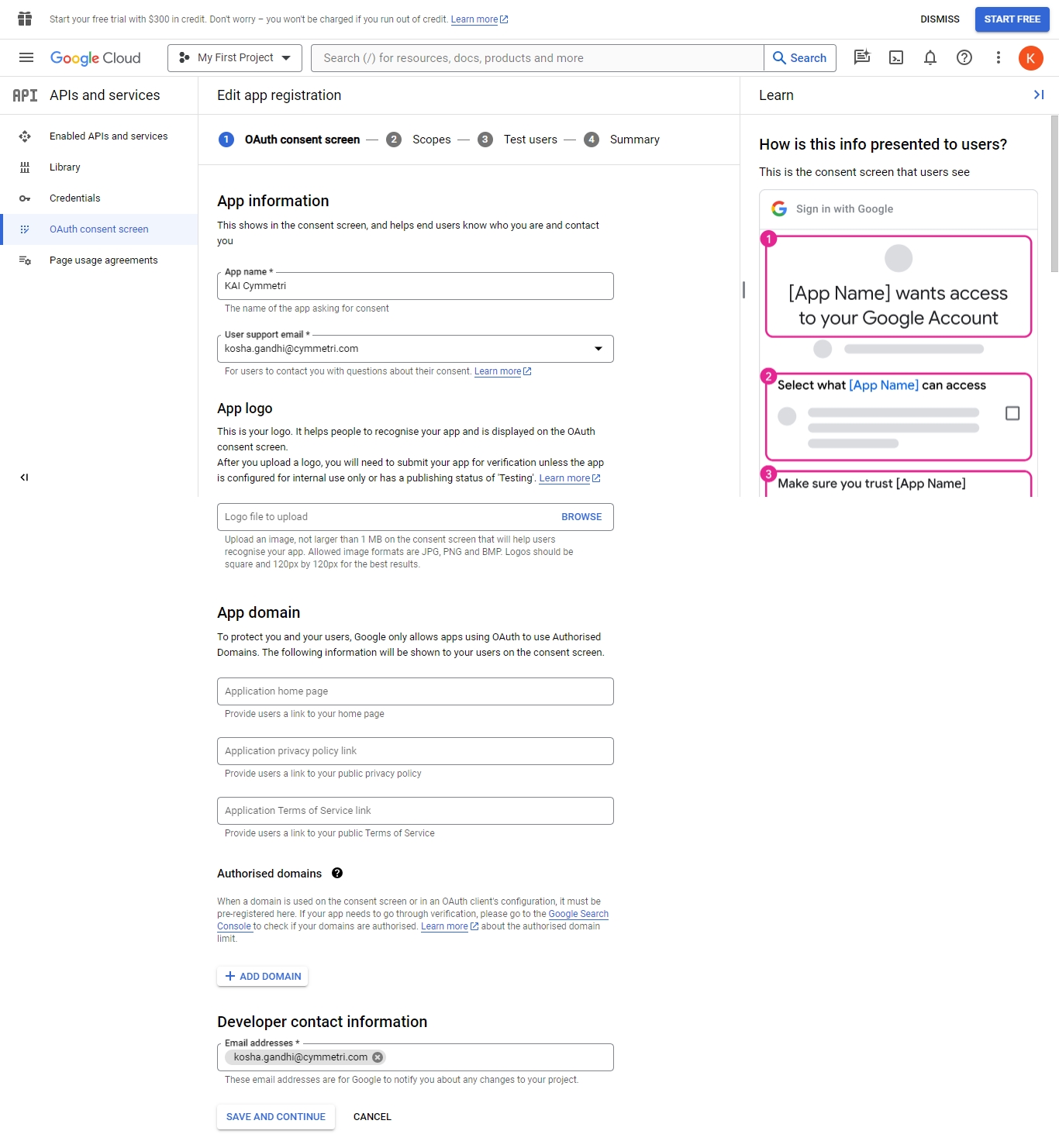
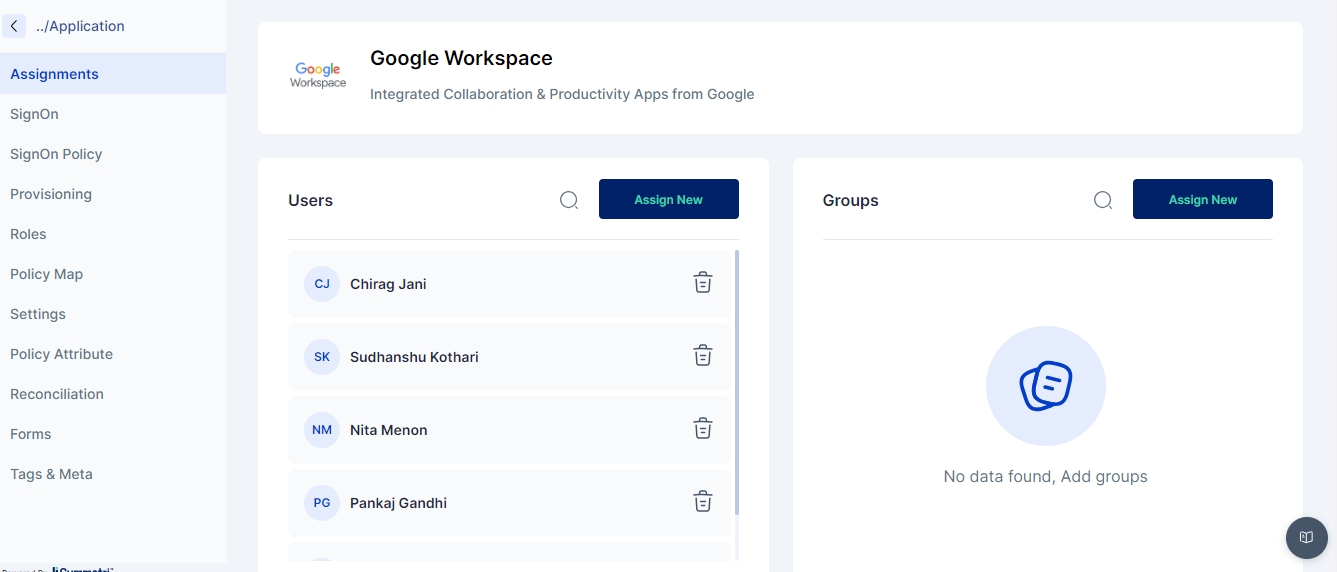

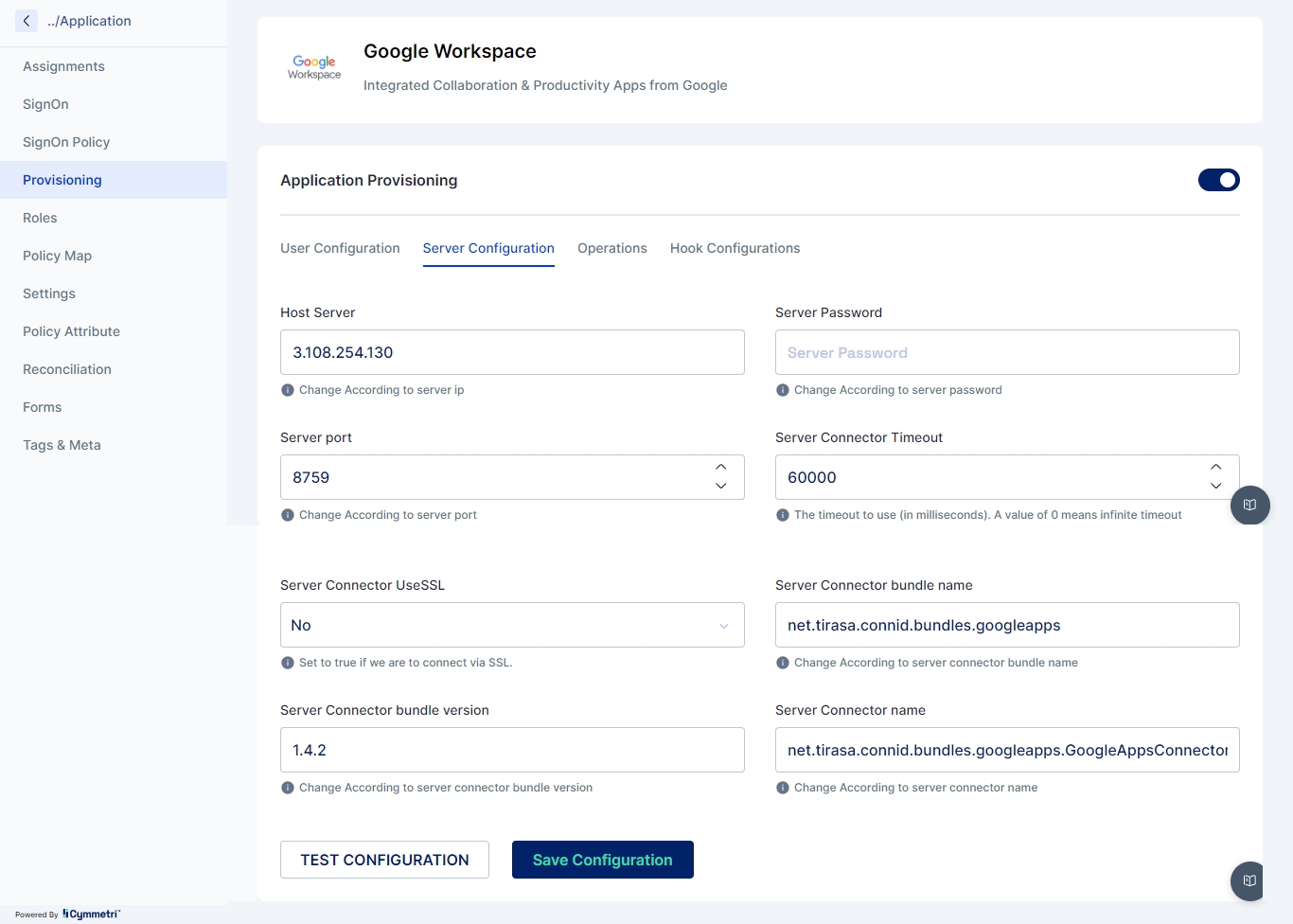
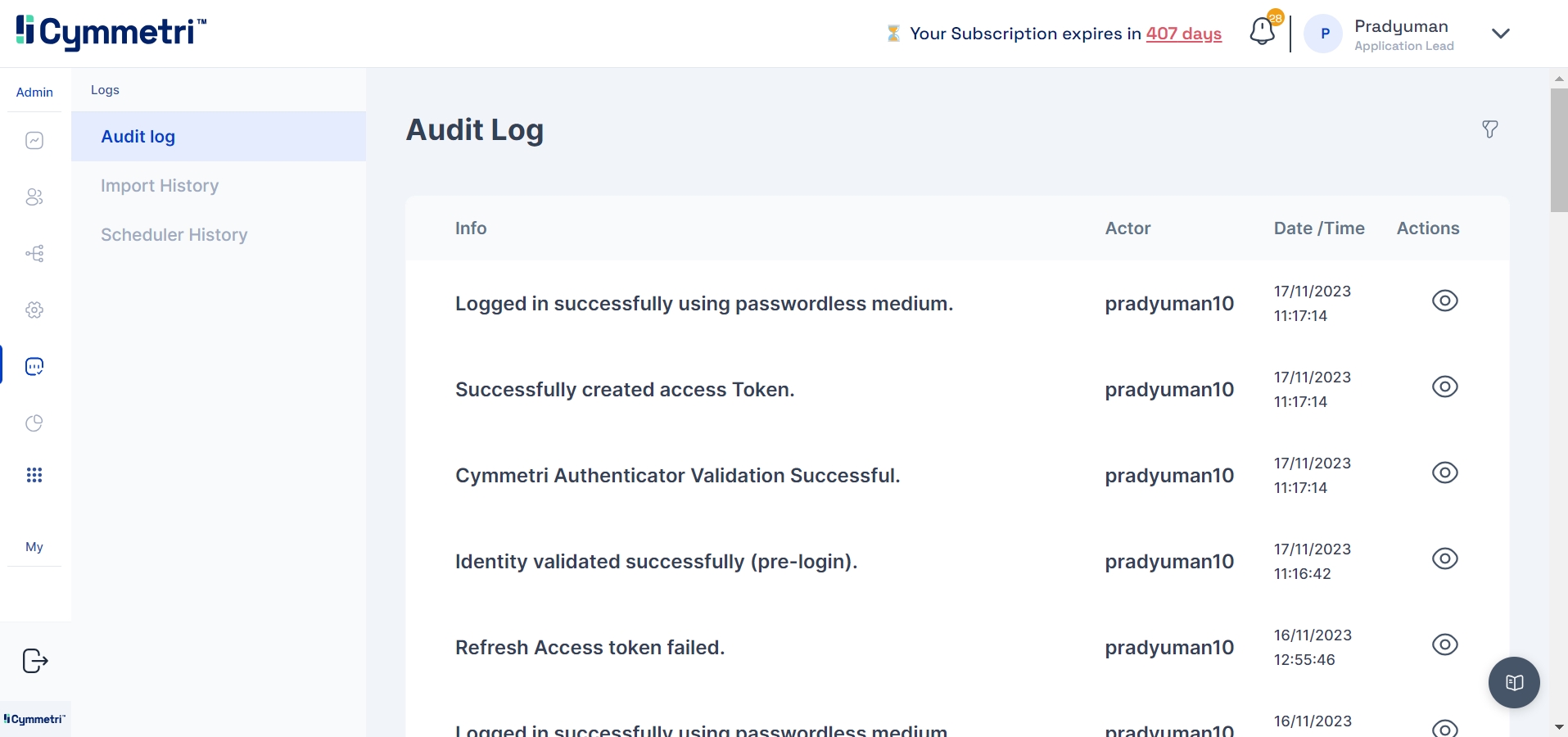

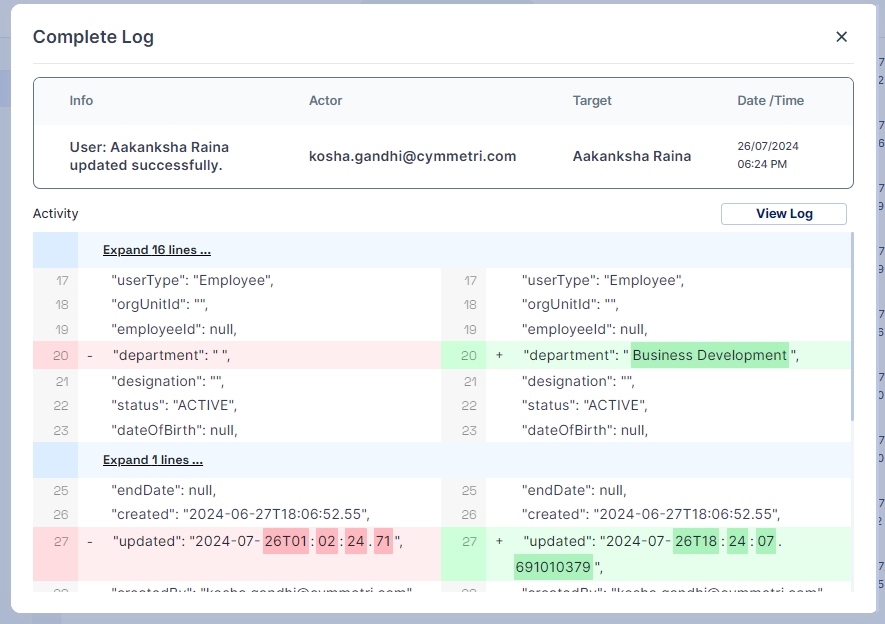

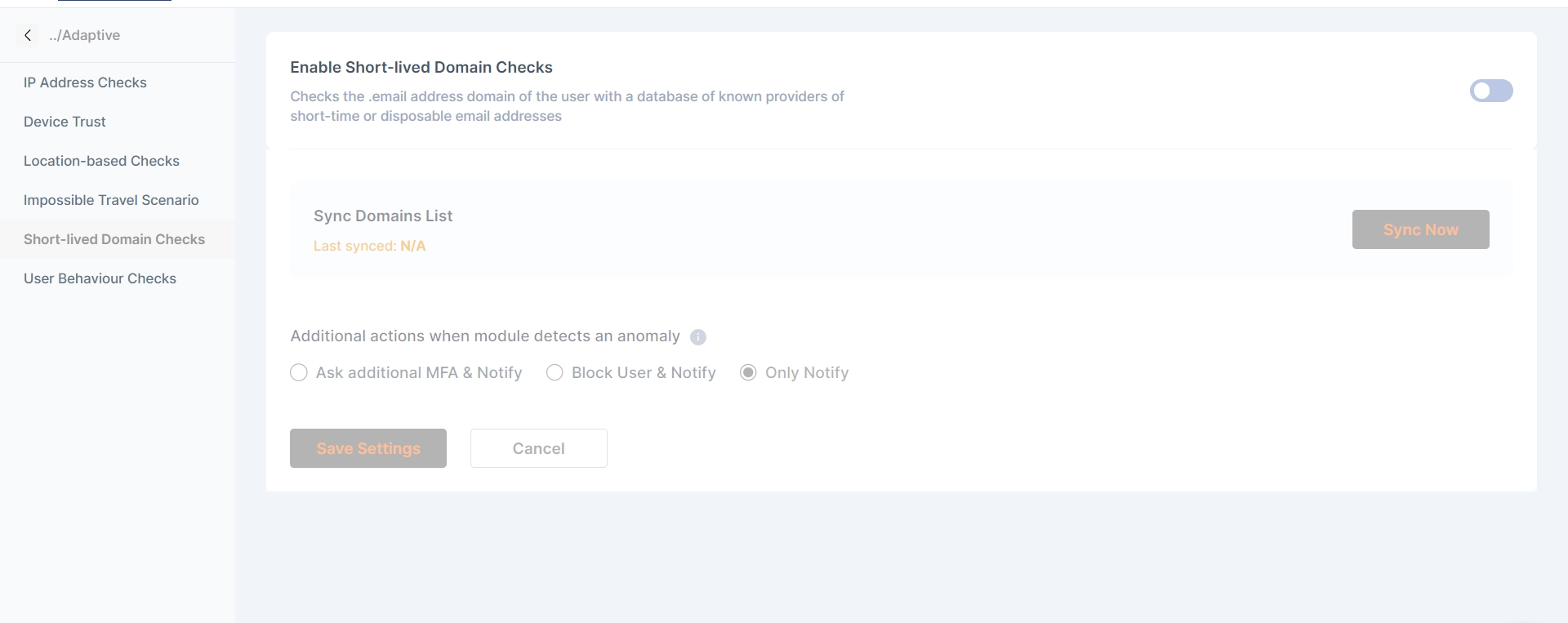
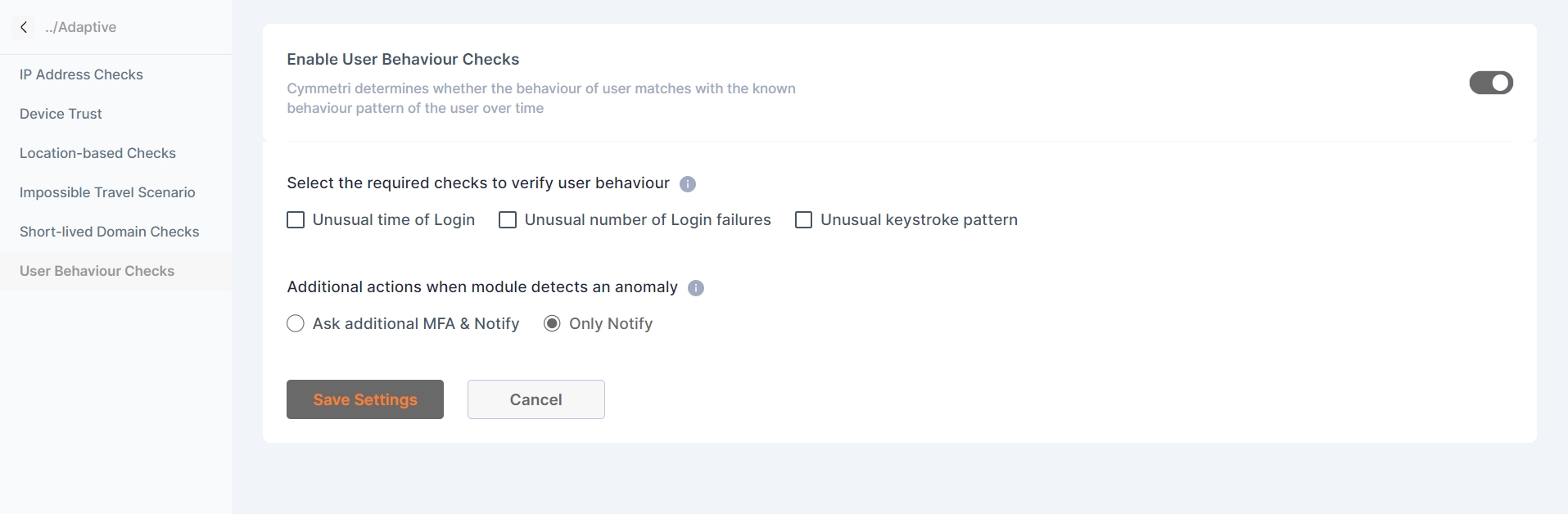
__PASSWORD__
password
-
True
True
mailNickname
mailNickName
-
True
True
userPrincipalName
login
True
True
True
givenName
firstName
-
True
True
surname
lastName
-
True
True
-
True
True
usageLocation
country
True
True
azureLicense
azureLicense
<actual license key>
True
True
























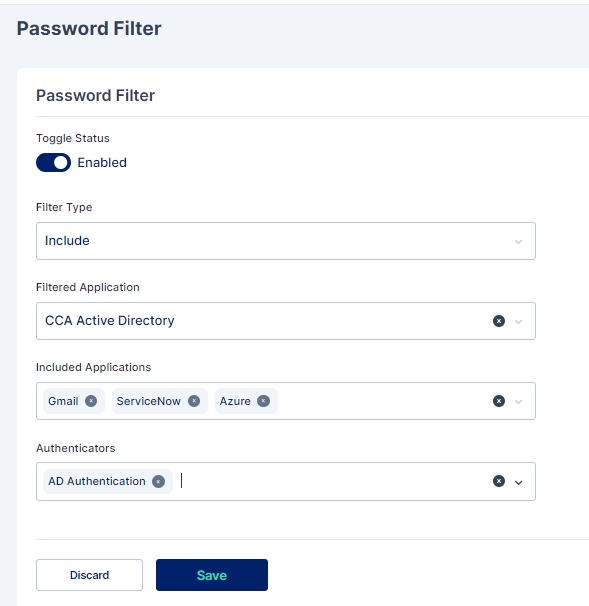
















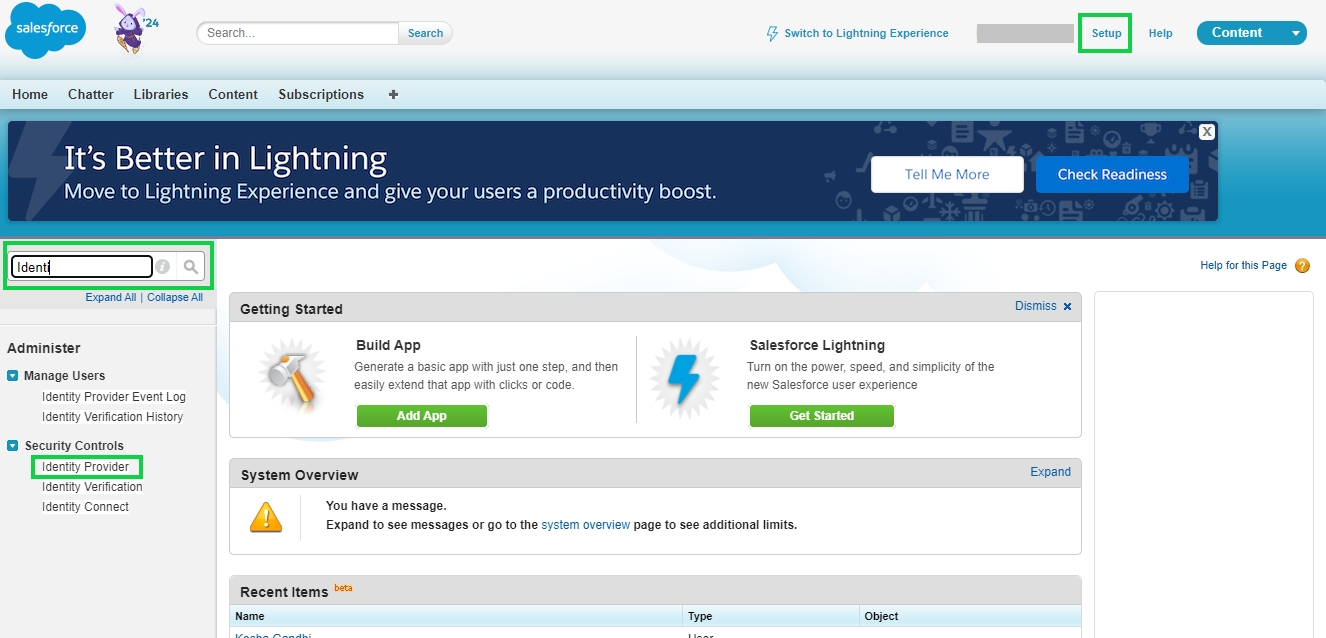
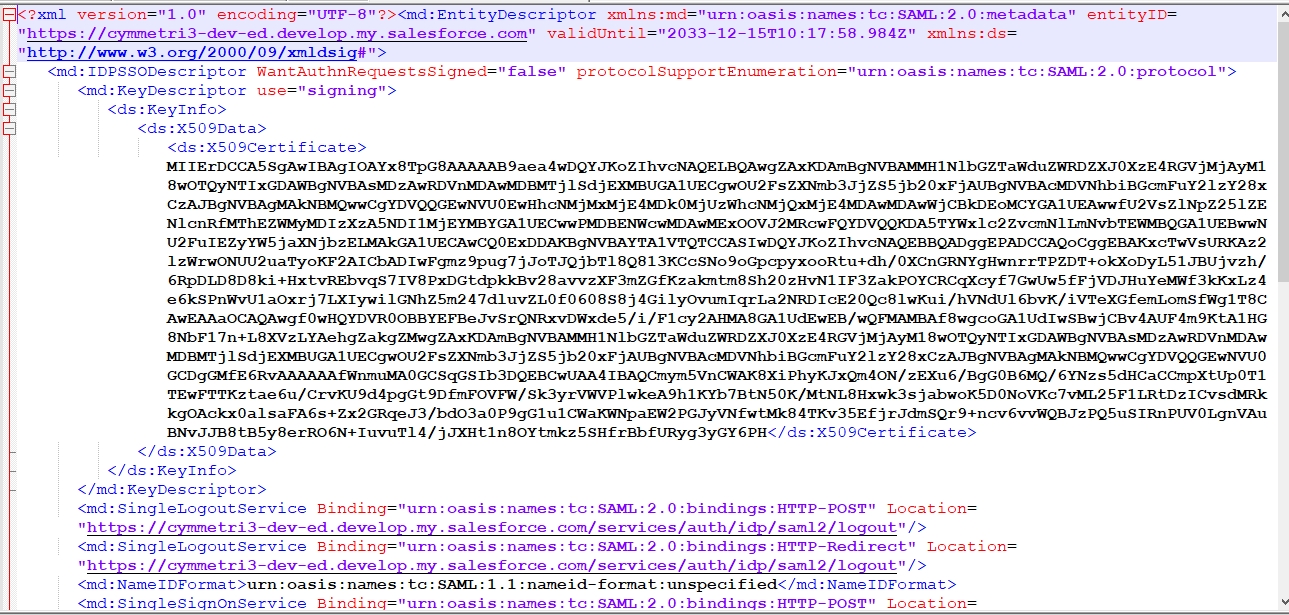
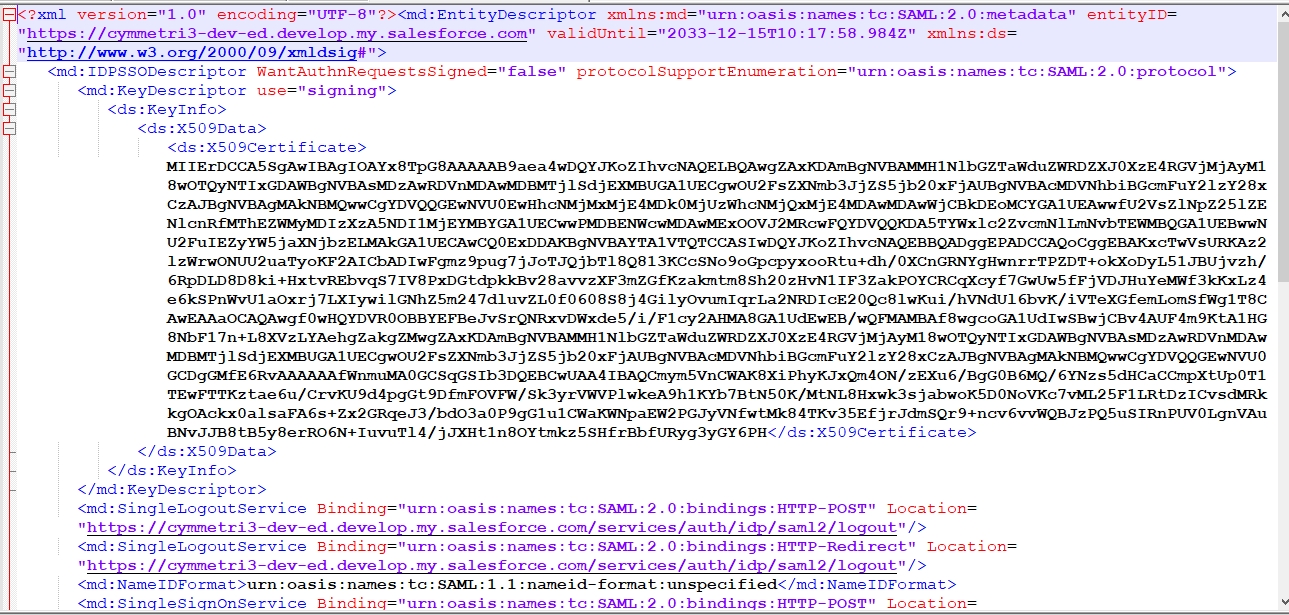

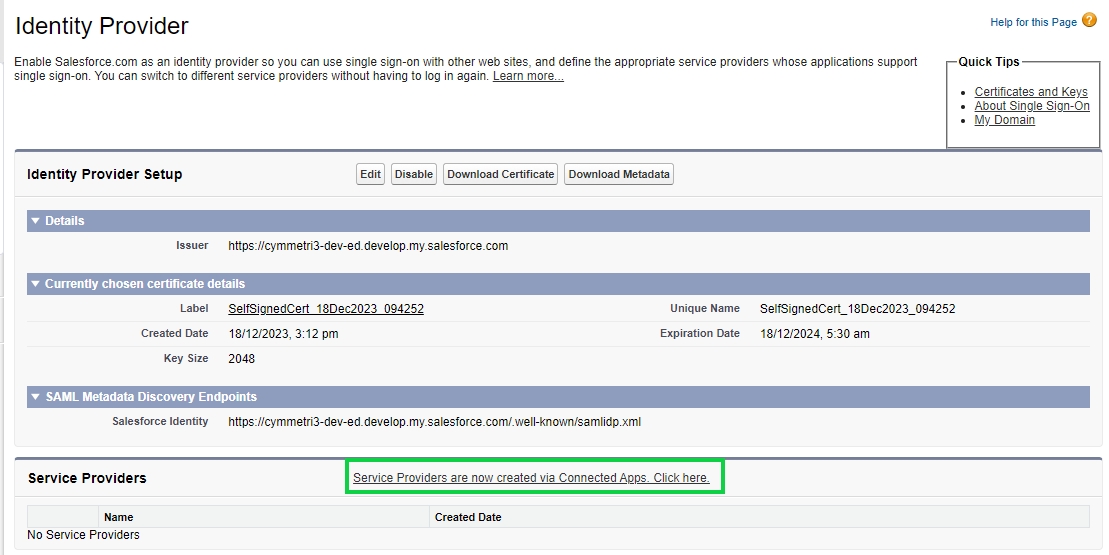
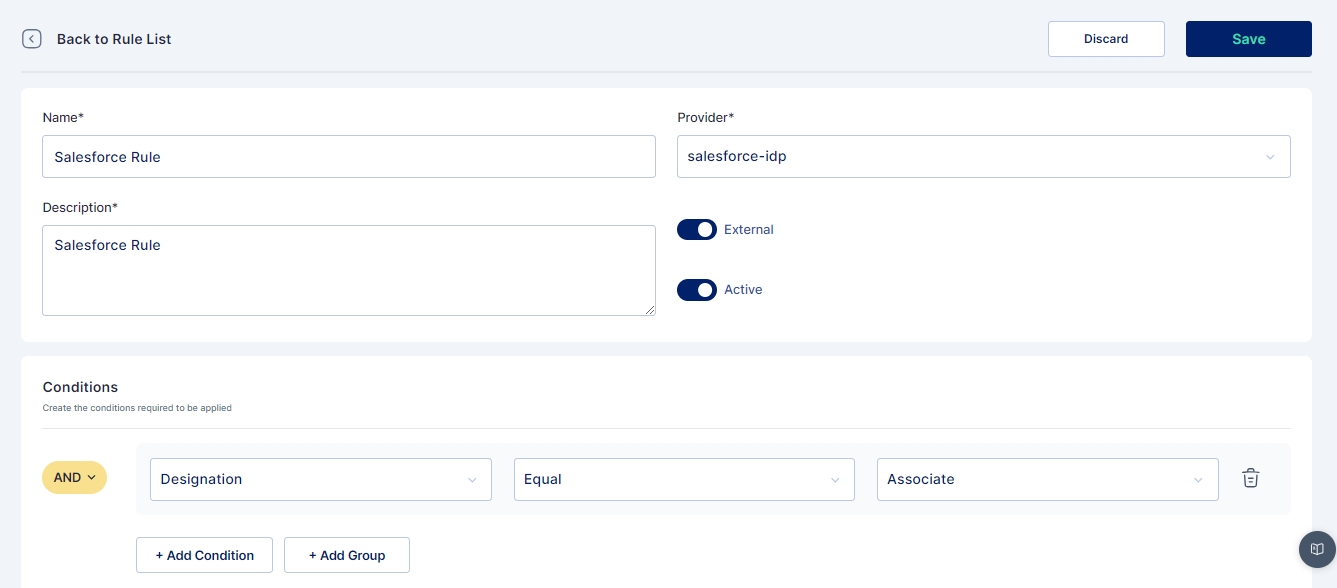

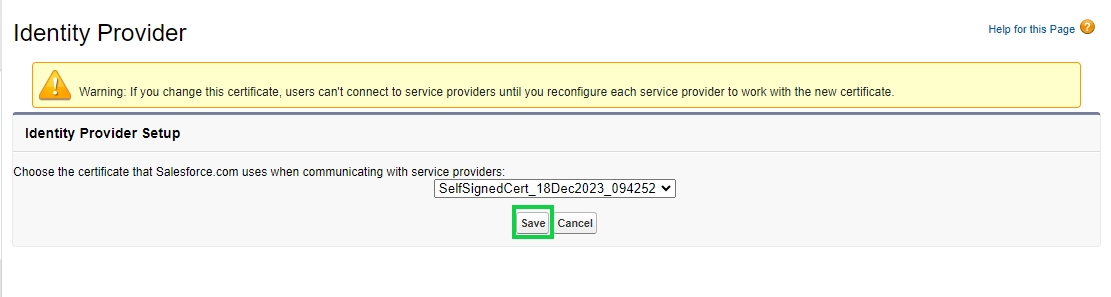

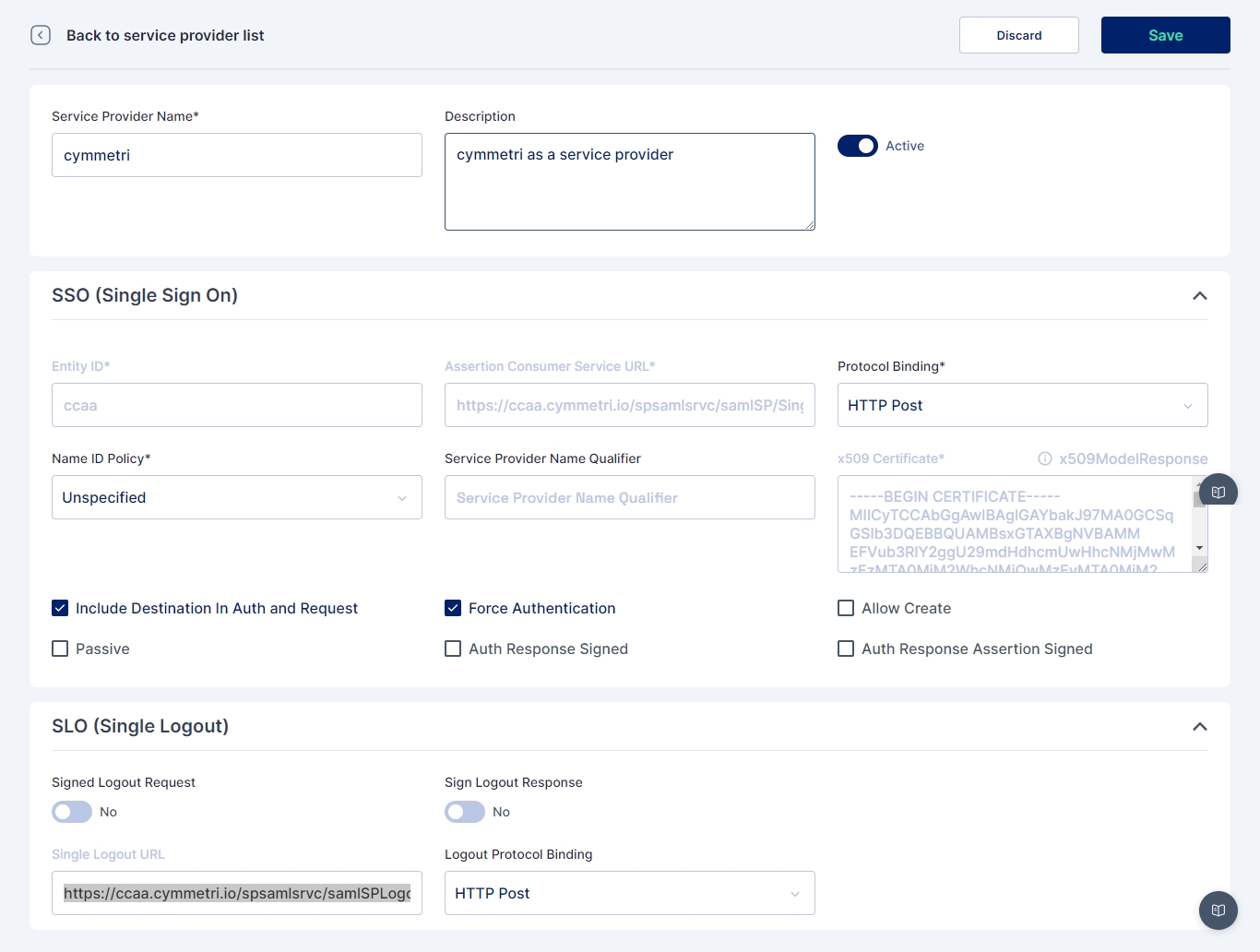


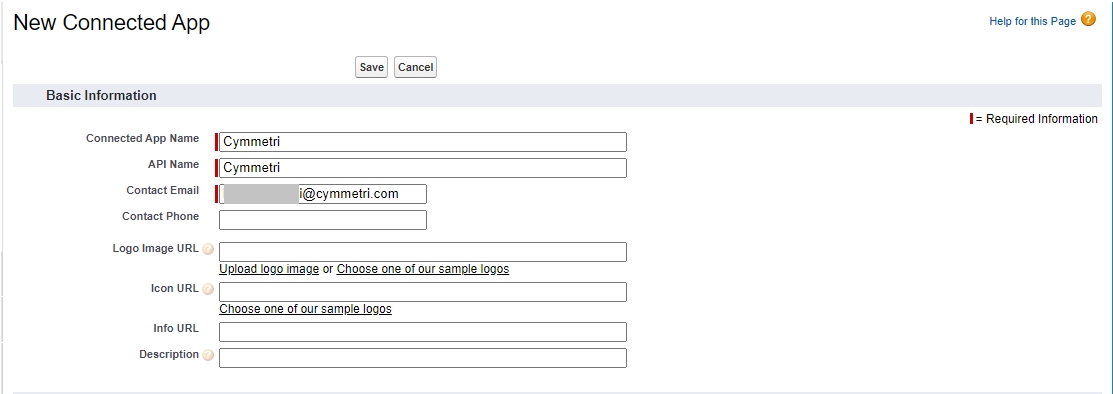
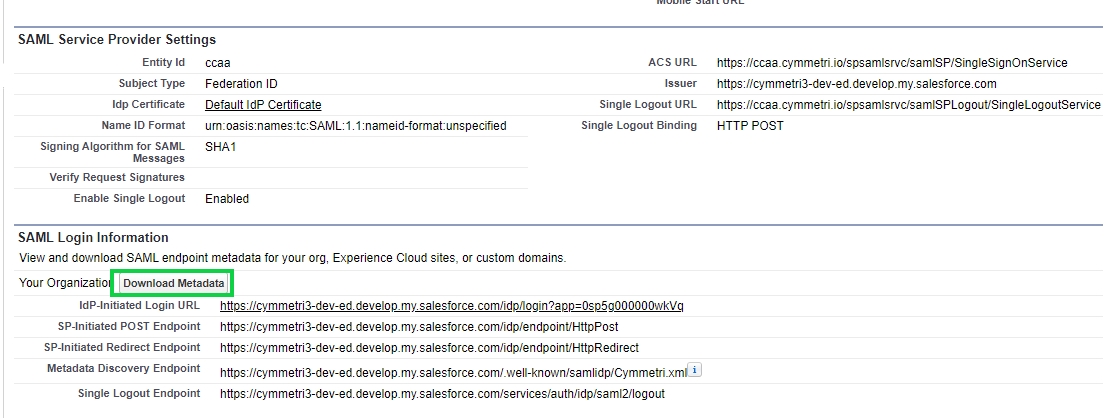
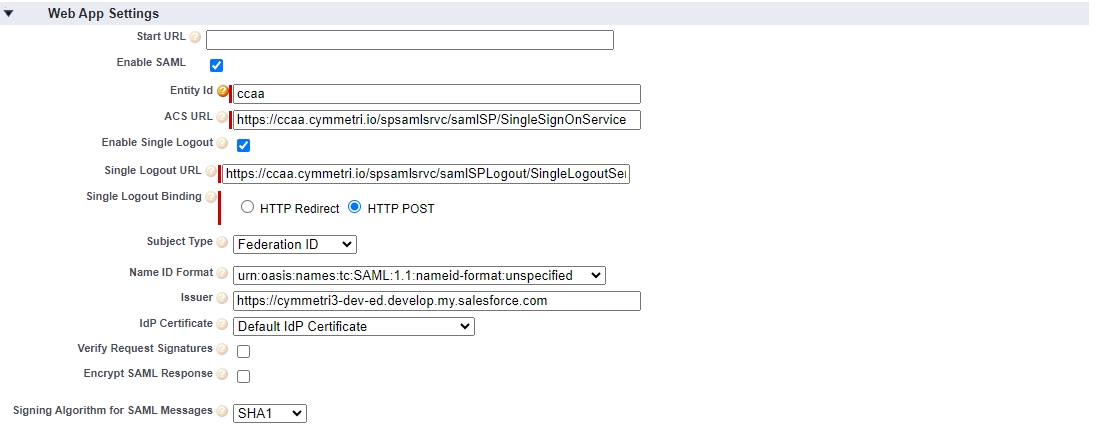








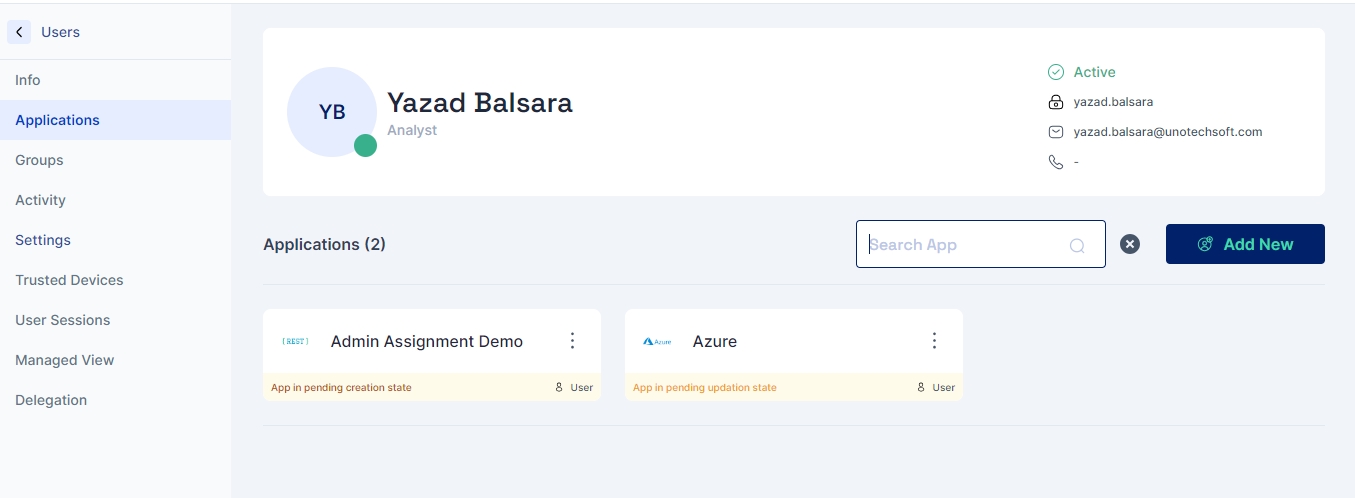
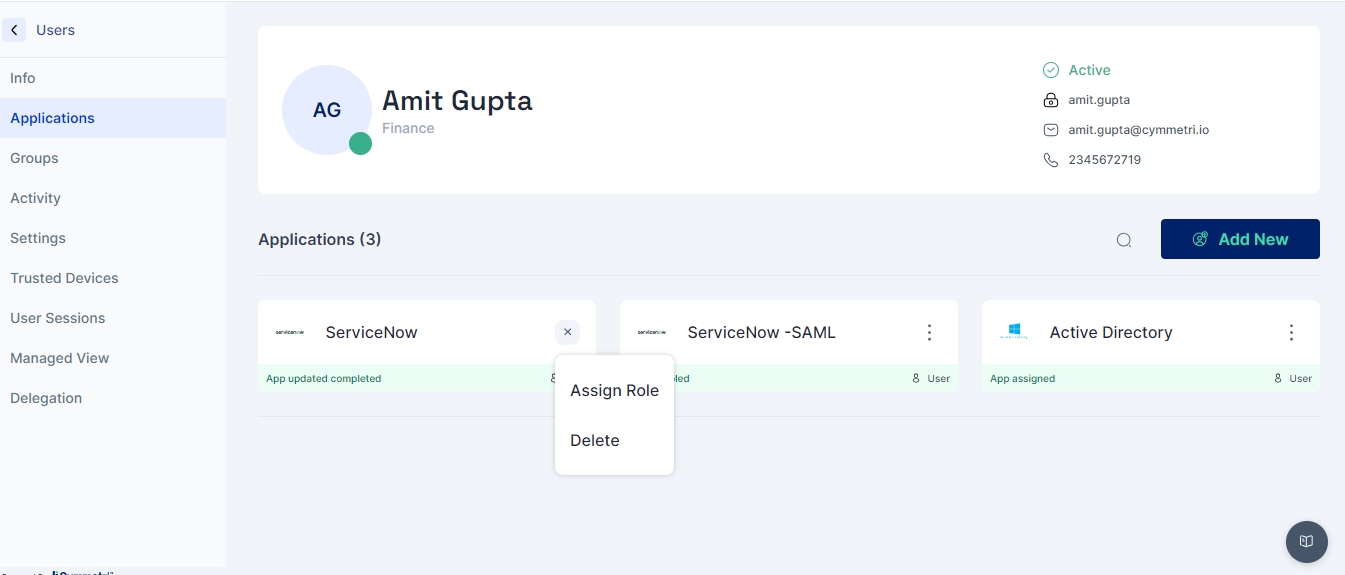
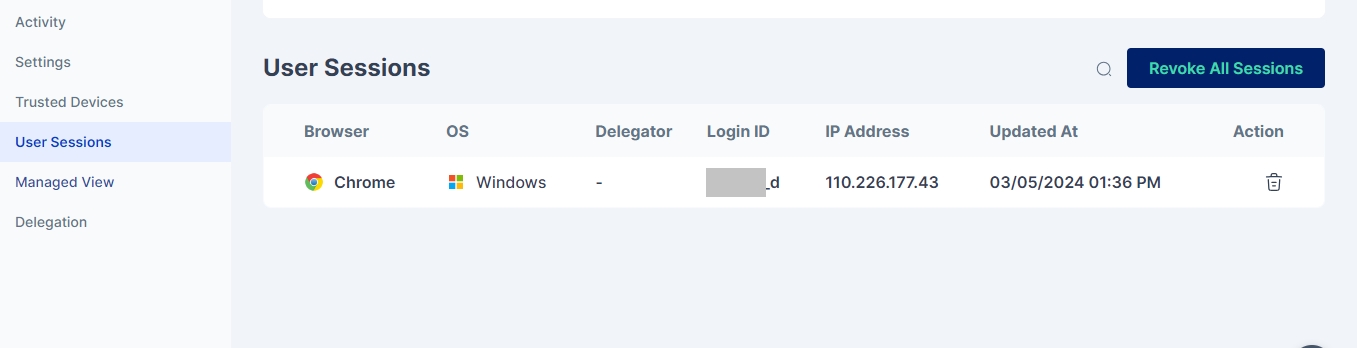
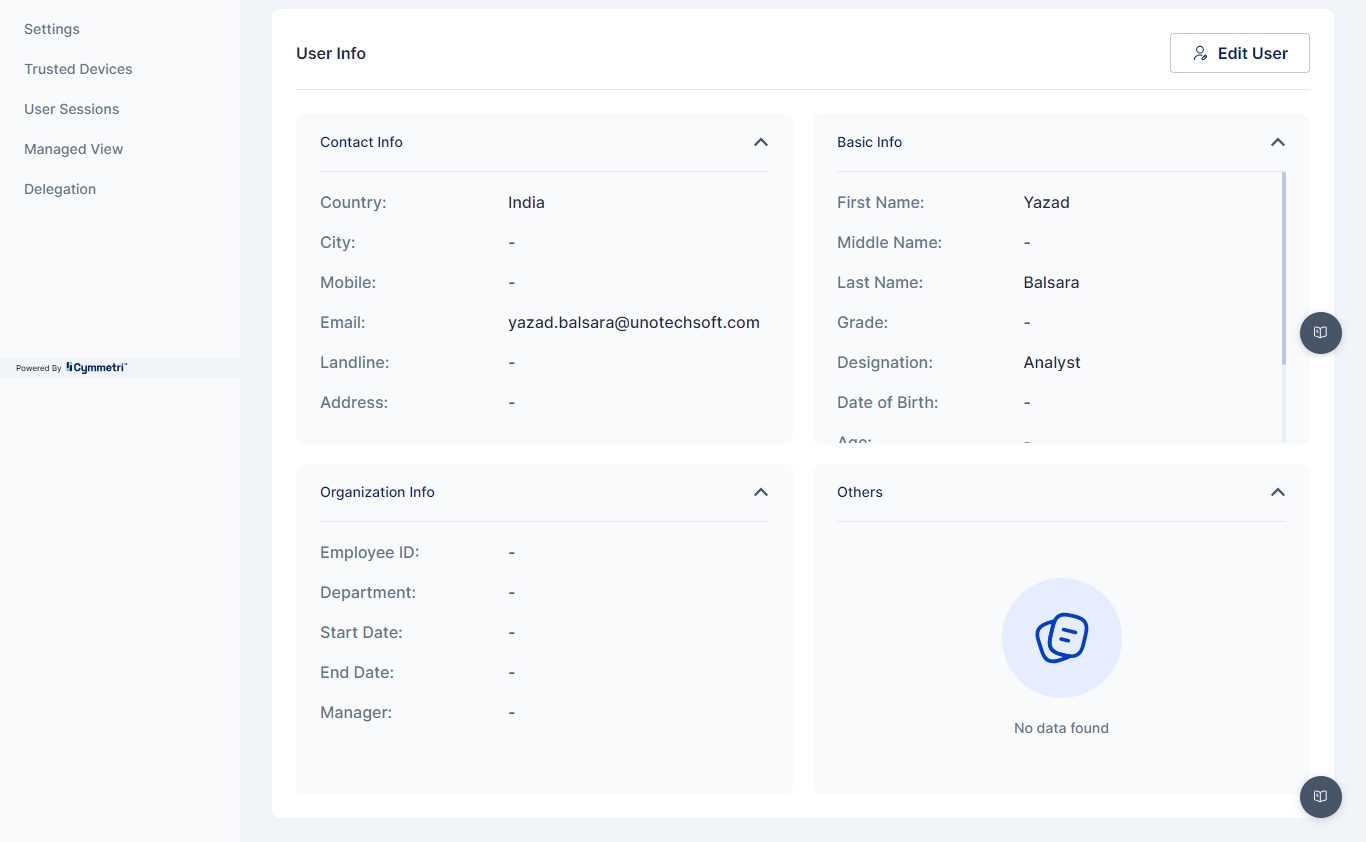
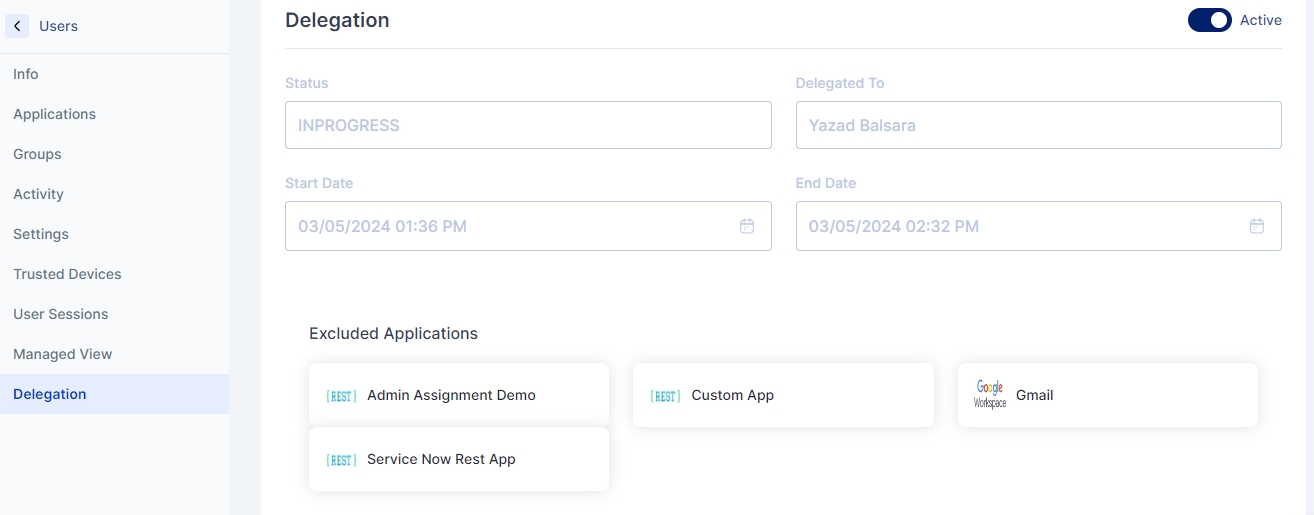

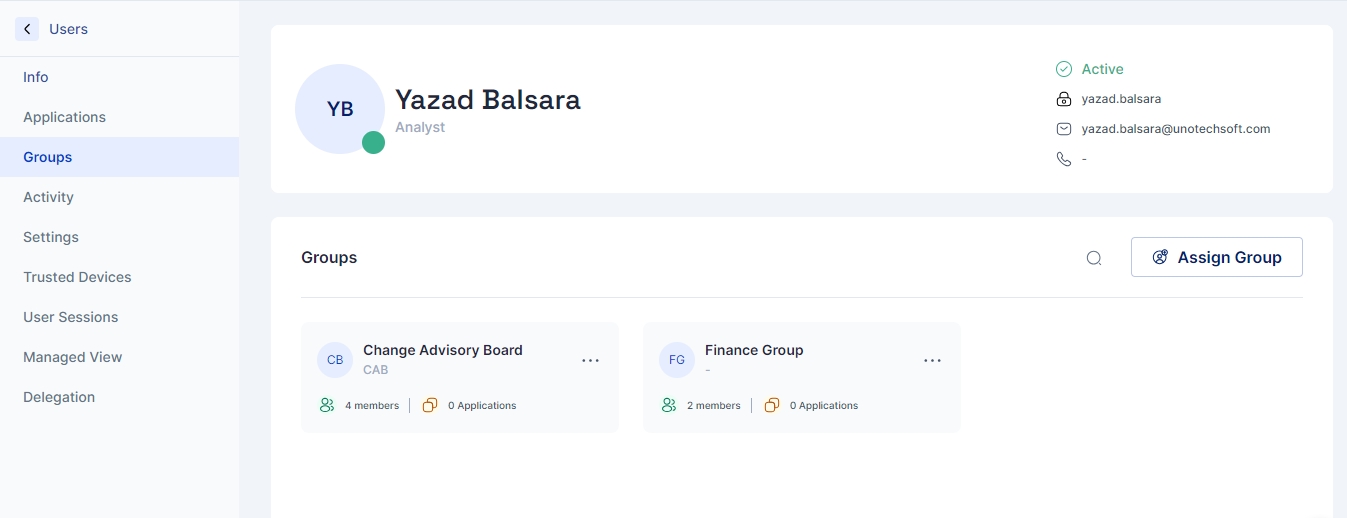
(3.1.0 - 3.1.6)
3.1.0 Beta (02 May 2024)
Add a Welcome Guide when no nodes are added
Amaya Operations cards messages updated
Tooltip DX enhancements
Add confirmation dialogue when the request method is missing
Deprovision Via scheduler when threshold value is set:- Past date user is also getting deprovisioned when rule is applied on status
Application-Role-One role mandatory, validation should be present at least one active
Node name without spaces overlap
Amaya- Not able to drag down node which is at the top most corner
Manager notification: receiving user name required manager name
Workflow initiated for form but form is getting updated without workflow approval.
In application setting if show to user flag off then also application show in recent application.
Unable to identify application properties data type where value is em



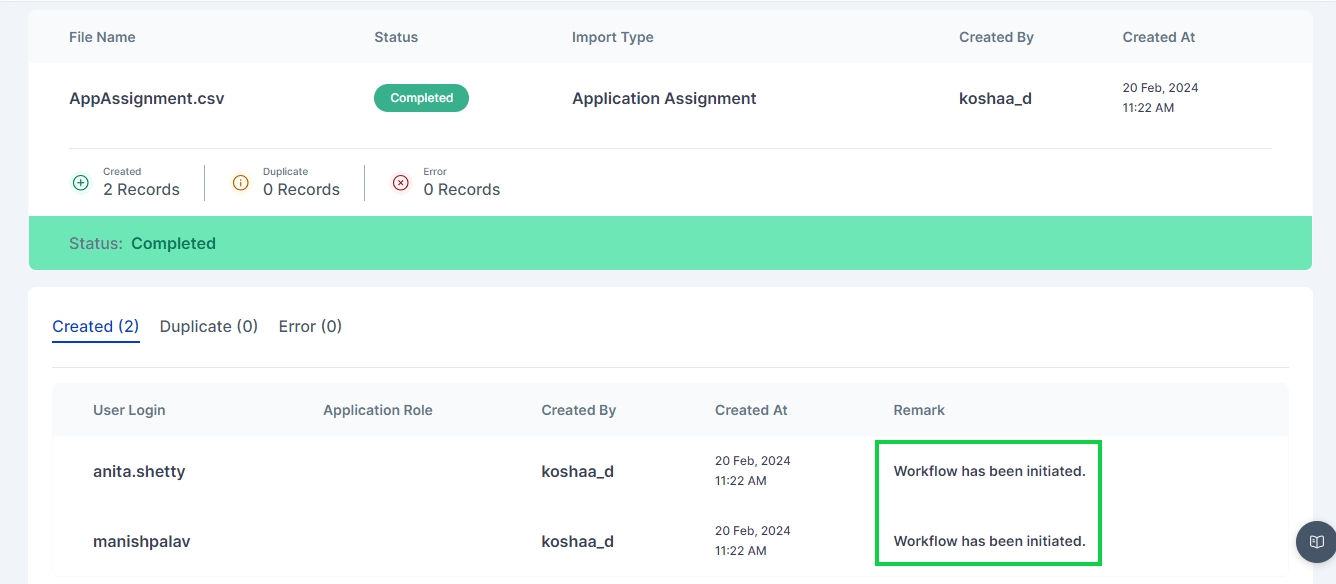
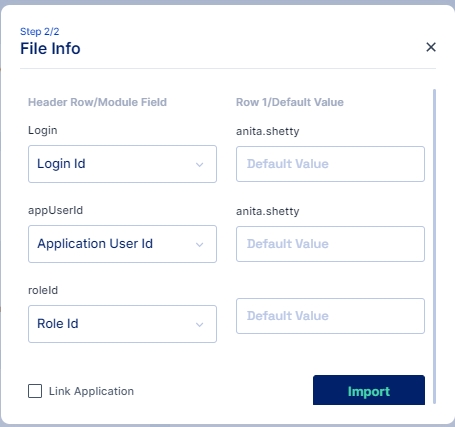
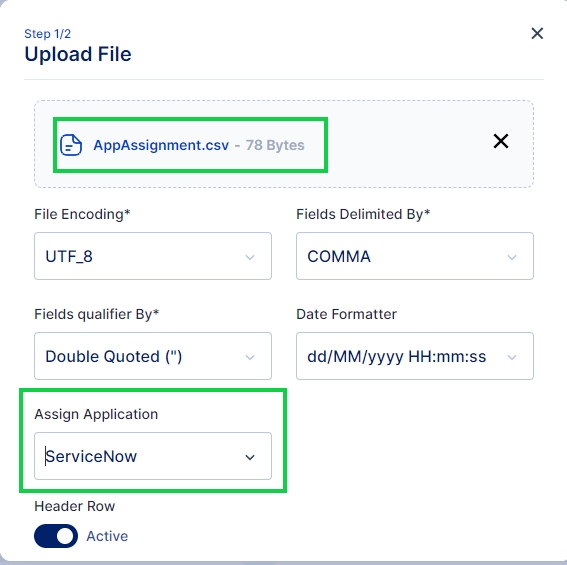
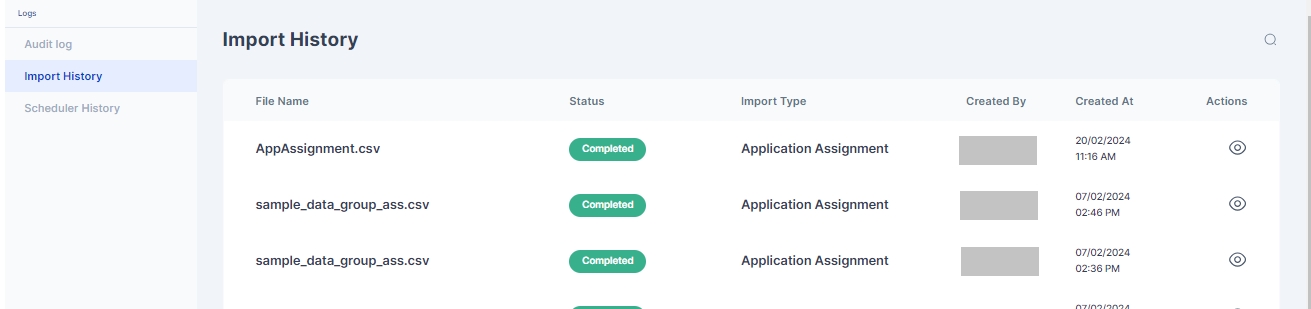
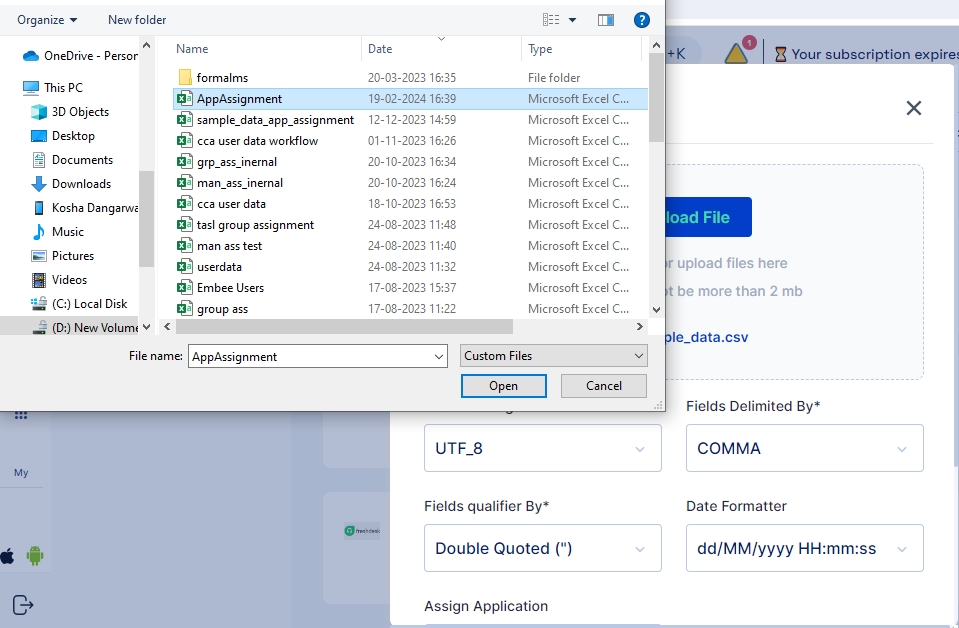

File Upload Validations based on filename length and file size: File validation applied on User Bulk Imports, Group Assignments, Application Assignments, Role Imports, and Upload metadata SSO. Branding Image upload applied image size validation and image name length validation. Validation is also applied on self-service User avatar upload and application icon upload.
Cymmetri Verify App issuer format is changed now so there wont be duplicate record creation from now onwards, earlier we did not take into account of the environment but now we are considering that as well
Campaign - Campaign action reminder email time calculation wrong
Campaign- Campaign is getting aborted and summary is showing blank when campaign for local group is executed.
Custom attribute - When custom attribute filter is applied in users, showing no users found
Workflow- Preference config box is not visible while deprovisioning application
Self service app: While setting up secret question authentication in mobile app, user need to click twice on question field.
User activity Ascending Descending not working
Amaya Connector Recon- Showing duplicate role remarks, but in duplicate field showing 0 records
Identity Hub- Groups- After editing groups when on application / activity page user is redirected to users page by default
My workspace> Create new tags- showing older suggestion as soon as clicked on new tag field
AD Application - View attribute is empty
Tenant registration | Pressing tab key glitches UI
Missing error code mapping
Grade Workflow- When workflow preference config is set to visible, and workflow is applied for user creation, then popup box is showing user list but in pending showing unknown instead of user list
Amaya- When the back button is clicked, a save/discard popup box will appear. However, clicking anywhere on the page directly navigates the user away from the operation page.
Amaya - Save/Discard popup box should not be shown when user is trying to go back without saving any changes.
Mobile app- Secret question- Field is showing required even when data is present in field
Cymmetri Verify app- Password recovery should be provided for Exported TOTP user files in case user forgets the password
login via Authenticator-identity provider is inactive then also user able to login.
syslog-configuration- UDP test, for invalid IP also giving success. Unable to have TOTP account for same username on different environments .
3.1.2 Beta (26 July 2024)
Workflow self-approval module updated to support custom attribute (type :user type and Converter Type: String ) as condition parameter.
Teams config module updated to support custom attribute (type :user type and Converter Type: String ) as condition parameter.
On behalf module updated to support custom attribute (type :user type and Converter Type: String ) as condition parameter.
Auth Rule module updated to support custom attribute (type :user type and Converter Type: String ) as condition parameter.
Quick Setup - Setup applications using pre-defined operations
Import-Export App Configuration - Transfer configurations of application smoothly between tenants, simplifying the setup for users by ensuring all configuration, including user configurations, server configurations, and policy maps, are accurately migrated.
Removal of Deprovision Rule Exclusion Applications Field: a) Manual Execute Deprovisioning b) Deprovisioning via Scheduler c) Update Threshold Delete Config d) Deprovision Rule Updation e) Backward Compatibility f) Suspend or Resume User g) Impact on UI
Access review reject process updated, on rejection workflow support added.
SAML Single Logout
New screen that will show loading on UI till tenant creation is completed once OTP is verified
Interchanged position of login id and email on add/edit user for better UX.
Add support for page number field for pagination in Amaya
360 Recon
Lotus Notes Connector
Application Policy Map (Active Directory) samAccountName is compulsary for Create only flag in User as well as Group (AD application new bundle - When SAMaccount name is set to false in Group policy map, members are not assigned in group when recon Pull is executed for both exist=Update).
Added Warning information and warning popups (Only UI changes no impact on backend functionality): a. Creation of user manually. b. Updation of user manually. c. Bulk upload csv (creation of user) d. Manager assignment e. Policy map creation and updation f. Reconciliation Pull operation g. Reconciliation push operation h. Selfservice ➝ Teams: i. Creation of user ii. Updation of user
Removal of Email validation from backend
User info page gets crashed while user edit fails
Import/Export of App Configuration
Amaya- Detailed description of failed/executed logs should be shown
AD application new bundle- Group link attribute in db is empty, users are not getting updated in group
AD policy map- Spaces should be trimmed automatically if included while creating a policy attribute
Tenant creation not working
New tenant Registration- Showing subscription end for tenant which is not even registered completely
Secret question configuration- Admin user should be able to delete secret question when not in use
Secret Question-When a question is already in use and user trying to delete question then it should not display successful delete message
Secret question- Displaying removal validation message when editing a question
User> Activity- Add cross (x) button to clear the selection
Onbehalf Config - If Description is kept blank , no error message is getting displayed on screen while saving.
Team Config - If Description is kept blank , no error message is getting displayed on screen while saving.
On Behalf config- When the view button is clicked, the user is still able to check or uncheck the boxes
Custom attribute- Even when a custom attribute is disabled from the configuration, it remains visible in the policy map selected dropdown menu
Users - View User- Custom attribute fields text UI is breaking
Custom Attribute- Require text change in success message to " Custom Attribute activated successfully"
Edit User - After deactivating the already assigned custom attribute, in edit user , system is showing info "xyz" attribute is inactive for active custom attribute also.
Identity Hub- When clicked on edit info from user menu action, user account edit page should get open instead of user display page
CTRL+K: When any feature/module is already opened and user press ctrl +k button from keyboard then search filter modal is getting opened at back
Delegation - Delegator and Delegatee consent should not get updated if user has already set some other consent
Users> Group- Rename the label from 'Delete' to 'Unassign'.
Audit- Logs for deprovisioned user is getting repeated.
Custom Field- Policy Map- Date is not showing in correct format
Mobile app- When clicked on user name for first time after killing app , keyboard is getting hidden
Custom Attribute-Provision- When a custom attribute with special characters is created and applied in a provision rule (for user creation), the provision rule fails to trigger after the user is created.
Global search (Ctrl+K) - even if characters are not matching still showing suggestions
User setting- Error message should be shown when any action is performed and when landing/refreshing setting page
Cymmetri Selfservice App - Need to change the message showing in popup screen while TOTP is getting authenticated.
Mozilla Browser specific- User getting stuck when password less Webauthn is On
Application - SSO - While clicking on Preview assertion , getting error "processing please wait"
Product menu getting hide on workflow page: a. Menu action- Displaying an error message when a user already has one role assigned and tries to assign a menu action.
User info page gets crashed while user edit fails
Import/Export- Showing error message when importing file into new tenant (AD specific)
Custom Attribute-Provision- When a custom attribute with special characters is created and applied in a provision rule (for user creation), the provision rule fails to trigger after the user is created.
Quick setup- Data is not getting reset after closing policy mapping popup box, but getting reset when clicked on "I ll do later button"
Add Page Number support for Amaya
Application - SSO While saving the same config in two applications, while clicking on Edit SP config , popup showing do you want to continue editing the SP configuration? but only continue button is given
Application - SSO - While saving the configuration in new application, save button loader is loading continuously
360 recon-Hide runnow button from detail view
360 recon dashboard filter-add dropdown for break type
360 recon dashboard-label change account overdue to account overdue in the target (also add some info on i icon what is this)
360 recon-Already running recon need to handle,disable play button or show message
360 dashboard-make label consistent
360 recon dashboard-action details showing blank
360 Degree recon-For execution showing error
360 Degree Recon- History some time loading some time not
Recon 360 recon- Validation message for missing data is not required as it already shows no data found on page when recon is not executed at all
360 recon dashboard-action details showing blank
360 dashboard-Search not working on break type
360dashboard-loginid filter not working
360 recon detail data showing mismatch
360 recon execute audit log not present
360 recon dashboard-on 2nd run details getting repeated
Amaya Azure- Showing route issue error message
Import Application- UI for name is not proper
Import/Export- Recon is not working for AD new application bundle
Teams config - while removing the condition in Group condition, showing error " Please try again"
On Behalf config - while removing the condition in Group condition, showing error " Please try again"
Teams Config - If condition is kept blank and save is clicked , getting error " Please try again"
On behalf config- If condition is kept blank and save is clicked , getting error " Please try again"
Import/Export Application- Convertor field types in policy map is not getting imported
Import/Export - When any application configuration is imported into a new tenant, the user should be redirected to the application provisioning page after the upload
Import application- Showing an error message when importing an Amaya-based application if the exported application was without the policy map checked
Amaya- Policy Map Password attribute datatype identified as password instead of string
Amaya- Rename all operations(Test, Search, Sync, etc....) in sentence case
Workflow- Even after updating Grade as the 2nd level approver in the workflow, the 1st level approver is still being set at level 2
Workflow- After updating the user list as the 2nd level approver in the workflow, the 1st level approver is still being set at level 2
Workflow- When the level 3 approver is updated in the workflow, a 'Workflow Not in Range' error message is displayed.
Workflow- Even after updating the reporting manager as the 2nd level approver in the workflow, the 1st level approver is still being set at level 2
Workflow- When workflow over workflow is applied 2nd level approver is not getting updated
360 recon should consider full sync
360 recon fails then that 360 recon should be abort
Amaya Felicity Role assignment- Taking time to provide error message
Deprovision- Exclusion Application- Application going in pending deletion state when that particular application is added in exclusion application while manually deleting user from Identity hub
360 Recon sync with bulk data showing heap size issue
AD new application- User list is not getting displayed showing urersrvc unknown error.
My workspace> Inbox- When workflow assignment is reassigned by admin, then previous approver should not be able to accept or reject request if page is already open in previous approver account.
Inbox - Workflow Request for setup for application - Need to enhance the details as per user interface.
Error in the server log-authsrvc ,No impact on functional flow
After the campaign workflow triggered on revoked, even though the campaign had ended and the workflow was approved, applications were still getting unassigned.
Campaign - Reviewer can approve self review request
Campaign not getting end, for tenant 2711
Workflow TAT- Workflow is getting aborted when grade is set at second level approver and set TAT time is over
Workflow TAT- Workflow is getting aborted when 2 level approver is set and set TAT time is over
Workflow TAT- Workflow is getting aborted when workflow approver is assigned to user list
Workflow TAT- Showing error when user is not present and TAT is over
Workflow TAT- Showing unauthorized error when TAT is over and operation is getting aborted
Recon pull- with both exist link, audit detail not showing
Workflow rule configuration-on edit workflow ,previously selected role getting save
AD new bundle- Managed View- View should be proper while separating multiple OU in proxy addresses
AD new bundle- Manager and account expiry is not visible in Managed view
AD new bundle- managed view- Value is not displayed in proper format in Name in managed view
AD new bundle- Managed View- Showing different Start time/created time
In User creation workflow L1 - User List approved , L2 - reporting manager , after TAT is expired , request is not getting auto reject.
Pending Workflow List - If approver is User list and Grade then it should display in Current Assign in pending list
User Workflow - If reporting manager is set as 2 level approver , reporting manager is showing as Unknown
Policy Map- When attribute is searched via search button and that attribute is deleted then other attributes are not getting loaded
Profile Picture- After clicking once on the upload button, that button should be disabled
PAM-Server access not getting terminated even after time end (Related to HA environment only)
User - Assign Application - Workflow initiated - Workflow Approvals page displays User list in Grade type
Pending Workflow -If L1 approver is User List , then while clicking on the info icon, popup not showing user list .Also it is " Grade List Details"
PAM-Server access not getting terminated even after time end (Related to HA environment only)
Workflow Rule - Workflow is initiated when group is set as approver , group is not visible on popup screen
AD new bundle>Group- When the "Sam account name" update checkbox is unchecked and user attempt to update the description, the description does not get updated in AD
deployment_analytics_1 Service CPU utilisation is 100%
Import/ Export- When file is exported from different env (Dev) and imported to QA env, then credentials are also imported along
Security Bug Fixes :- E2E request/response payload encryption for all APIs of authservice
manager notification : receiving user name required manager name
Unable to identify application properties data type where value is empty
Amaya || Create user operation fails due to invalid password
In forgot password/password breach condition-asking disabled MFA factor also
Amaya-Autofill policy map, When value is not present to the user at the time of application then amaya passing "$." to the target
Campaign - Reviewer can approve self review request
After the campaign workflow triggered on revoked, even though the campaign had ended and the workflow was approved, applications were still getting unassigned.
Remote Group- AD Application- When users are removed from a remote group in Cymmetri, those members should also be removed from the group in Active Directory
Amaya- Client id should be visible in encrypted form
Provision Rule - While creating and configuring the custom attribute as "New ", system is not initiating the rule.
AD new bundle- When an AD application is assigned to a remote group, the application is highlighted in the background while assigning but disappears as soon as the application popup box is closed
Reports- When report is scheduled, Scheduler history is showing content not found and execution status is getting aborted
AD Application- When Ad test provision is failed, and user trying to delete application from user account, then application should go in fail deletion state
Audit- Taking time to load audit logs
AD Application- Showing error when inserting start date in AD
In application setting if show to user flag off then also application show in recent application.
User lock- When a user account is active, and the same account is logged in through another browser and by any means account gets locked, the first session should get terminated.
Branding- When show Unlock link from branding is kept as No, and admin user account gets locked, then user is not able to unlock account from login page
Application- When user is adding /removing role then it is not getting reflected without refreshing
group push-not taking user in AD at the time of update
Passwordless- WebAuthn; Showing not allowed error
Delegation-On behalf: when login by delegate and on-behalf condition is not satisfied still showing on-behalf toggle button and getting removed when refreshed
AD Application- Group name should not accept space while creating or updating group name
Audit- Audi log should show log when user is not getting any records in Recon history but showing task executed
3.1.3 Beta (26 July 2024)
User Threshold: a. A UI change has been made in the general configuration for the threshold. b. Creation of user c. Updation of user d. Deletion of user e. Staging for user threshold f. Retry staging user from staging dashboard. g. Archive for user threshold h. Notification for user threshold
User directory search API updated for quick search (keyword): a. Support dropped for: grade, userType, department, designation, custom-attributes b. Supported on: employeeId, email, mobile, firstName, lastName, middleName, displayName, login
Data logger service version info added.
Tenant registration database creation process optimisation.
Pending Workflow Inner page applied functionality to reassign user from inner page
Added QR code zoom feature on FIDO, TOTP and push Authenticator scanner.
VPT: Modify routes of api - /usersrvc/api/user/directory/list/{appId} remove user role form routes.
Custom Attribute support in following Workflow Rule Events a. User Creation b. Application Provisioning c. Application Deprovisioning d. Application Update
Added the following templates in Amaya Quick Setup: • Atlassian • Zoho CRM • Zoho Desk • Zoho Books • Zoho Expenses
Provided support for integer values for ROLE assignment through Amaya.
Tenant Registration Process Resumption: In the event that the tenant registration process is interrupted, it can be seamlessly resumed and completed using the existing account configuration. The registration process can be resumed from the following stages: a. Pending OTP Verification b. Incomplete Credential Setup
Active Directory || SimpleAD Connector upgrade: a. UserAccountControl attribute support added b. memberOf attribute support in manage system viewer c. ProxyAttribute attribute support added
External IDP SSO: a. added support to login into cymmetri as external identity provider as idp initiated sso.
SAML IDP SSO: a. added support to send idp initiated (cymmetri) sso response to cymmetri as service provider.
TOTP Config
Removal of Email validation from backend
DataLogger | Refer configuration steps here: a. data-logging framework optimisation. b. Full sync support, this step is optional step and required only if, • Tenant audit database is not present, or • Tenant audit database is corrupt so fresh setup is required.
Error in the server log-authsrvc ,No impact on functional flow
Team config - Create - Discard button issue - After clicking not able to add the details in condition section
Rule engine- Remove "above" word from note
login with admin-Campaign detail show role also, currently role showing only for campaign manager
Amaya API returning null if error instead of error and errorCode
Hide metabase analytics
Workflow rule configuration-on edit workflow ,previously selected role getting save
User - Assign Application - Workflow initiated - Workflow Approvals page displays User list in Grade type
Pending Workflow -If L1 approver is User List , then while clicking on the info icon, popup not showing user list .Also it is " Grade List Details"
Identity Hub- Pending initial login symbol is visible far away from user name
On behalf configuration - While disable and enabling the toggle,popup message shows "This change will take effect on user's next login" but it is getting reflecting on the fly.
On-behalf>Delegation- On behalf menu is not visible when logged in via Delegatee account
SSO- Group mapping- Save button should be enabled when mandatory fields are filled
Workflow- Even after updating the reporting manager as the 2nd level approver in the workflow, the 1st level approver is still being set at level 2
Global search (Ctrl+K) - even if characters are not matching still showing suggestions
Product menu getting hide on workflow page
LDAP connector-LDAP SSL should be save in Boolean in the DB
User setting- Error message should be shown when any action is performed and when landing/refreshing setting page
User setting- External idp rule is active-An admin user should not be able to lock a user when the external IDP rule matches the user condition
Schedule history-ad by default todays filter for from and to
Teams config- When the view button is clicked, the user is still able to check or uncheck the boxes
Menu action- Displaying an error message when a user already has one role assigned and tries to assign a menu action.
Custom Attribute-Provision- When a custom attribute with special characters is created and applied in a provision rule (for user creation), the provision rule fails to trigger after the user is created.
Lifecycle Management - All menus - Discard button is not working as expected.
Application - SSO While saving the same config in two applications, while clicking on Edit SP config , popup showing do you want to continue editing the SP configuration? but only continue button is given
Application - SSO - While saving the configuration in new application, save button loader is loading continuously
Amaya- Rename all operations(Test, Search, Sync, etc....) in sentence case
Group Policy map- For group custom attribute Cymmetri field type should be automatically selected as working in users custom field
Teams config - while removing the condition in Group condition, showing error " Please try again"
On Behalf config - while removing the condition in Group condition, showing error " Please try again"
Teams Config - If condition is kept blank and save is clicked , getting error " Please try again"
On behalf config- If condition is kept blank and save is clicked , getting error " Please try again"
Import/Export- Showing error message when importing file into new tenant (AD specific)
Import application-show error message user or groupwise
Import application- Showing an error message when importing an Amaya-based application if the exported application was without the policy map checked
Import/Export - When any application configuration is imported into a new tenant, the user should be redirected to the application provisioning page after the upload
Amaya Azure- Showing route issue error message
Import/Export Application- Convertor field types in policy map is not getting imported
Import/Export- Recon is not working for AD new application bundle
Workflow- When workflow over workflow is applied 2nd level approver is not getting updated
Workflow- Even after updating Grade as the 2nd level approver in the workflow, the 1st level approver is still being set at level 2
Workflow- After updating the user list as the 2nd level approver in the workflow, the 1st level approver is still being set at level 2
Workflow- When the level 3 approver is updated in the workflow, a 'Workflow Not in Range' error message is displayed.
Workflow TAT- Workflow is getting aborted when workflow approver is assigned to user list
Team config - Create - Discard button issue - After clicking not able to add the details in condition section
Import/Export- By default, the time in the application name should be removed when exported
Rule engine- Remove "above" word from note
login with admin-Campaign detail show role also, currently role showing only for campaign manager
Hide metabase analytics
Error in the server log-authsrvc ,No impact on functional flow
AD new application- User list is not getting displayed showing urersrvc unknown error.
Campaign not getting end, for tenant 2711
Workflow rule configuration-on edit workflow ,previously selected role getting save
AD application new bundle - When SAMaccount name is set to false in Group policy map, members are not assigned in group when recon Pull is executed for both exist=Update
My workspace> Inbox- When workflow assignment is reassigned by admin, then previous approver should not be able to accept or reject request if page is already open in previous approver account.
After the campaign workflow triggered on revoked, even though the campaign had ended and the workflow was approved, applications were still getting unassigned.
Workflow TAT- Workflow is getting aborted when grade is set at second level approver and set TAT time is over
Workflow TAT- Workflow is getting aborted when 2 level approver is set and set TAT time is over
Workflow TAT- Showing error when user is not present and TAT is over
Workflow TAT- Showing unauthorized error when TAT is over and operation is getting aborted
User - Assign Application - Workflow initiated - Workflow Approvals page displays User list in Grade type
Reports- SSO based application- Reports are blank/ not showing data when SSO based application are accessed
Pending Workflow -If L1 approver is User List , then while clicking on the info icon, popup not showing user list .Also it is " Grade List Details"
AD new bundle>Group- When the "Sam account name" update checkbox is unchecked and user attempt to update the description, the description does not get updated in AD
Import/ Export- When file is exported from different env (Dev) and imported to QA env, then credentials are also imported along
Identity Hub- Pending initial login symbol is visible far away from user name
On behalf configuration - While disable and enabling the toggle,popup message shows "This change will take effect on user's next login" but it is getting reflecting on the fly.
In User creation workflow L1 - User List approved , L2 - reporting manager , after TAT is expired , request is not getting auto reject.
On-behalf>Delegation- On behalf menu is not visible when logged in via Delegatee account
Import Manager-Manager is deleted and user trying to assign then in the import history showing success but in audit showing failed
Application delete-Campaign-Deleted application available for review
AD new bundle- User policy map- When Sam account name is mapped with any attribute and update checkbox is kept false, and user is updated, audit log is showing failed
Workflow>Inbox- Address fields name in inbox /pending workflow and identity hub users are not same
SSO- Group mapping- Save button should be enabled when mandatory fields are filled
Campaign-email report showing error
deployment_analytics_1 Service CPU utilization is 100%
Application - Form - When submitted as blank, after assigning the application page is getting blank.
Reports- Records are getting displayed after 11min approximately
Csv Import users- An error message is not shown when the user is unable to save user details if a space is included in the email
After the campaign workflow triggered on revoked, even though the campaign had ended and the workflow was approved, applications were still getting unassigned.
User Workflow - If reporting manager is set as 2 level approver , reporting manager is showing as Unknown
Workflow>Inbox- Address fields name in inbox /pending workflow and identity hub users are not same
Export- Rename Config type to Select All
MFA- When default MFA rule is inactive, user is able to delete default rule as well
Amaya connector>Policy mapping- Bottom slider should be fixed
Amaya || Validation preventing usage of long valid header
Amaya Connector- By default only green colored (confirmed policy attributes) only should be checked
Amaya Quick Setup- When an auto test run fails and operations are manually updated, clicking 'Generate Policy Mapping' should exit the page.
Application delete-Campaign-Deleted application available for review
Import Manager-Manager is deleted and user trying to assign then in the import history showing success but in audit showing failed
Import/Export- By default, the time in the application name should be removed when exported
SSO - OpenID - Configure CIDR - Add - While clicking on Add icon without entering any details , blank data is getting added.
SSO - OpenID - Configure CIDR - While clicking on delete icon ,no message is getting displayed and entry is getting removed
Workflow List - View - Showing label as "Custom Workflow "
Import/ Export- Application name while importing file should be limited to 50character
Application - SSO - SLO toggle enable/disable audit log
SOD; policies-Policy owner name is not getting updated after updating user name from Identity hub and without owner name policy is getting saved
AD new bundle- When recon is executed for both exist update but application is not linked, still user is getting updated.
Application - Form - When submitted as blank, after assigning the application page is getting blank.
Masters - Grade- While clicking on Add button it is showing edit page of existing record
Tenant registration- Showing suspicious popup box when clicked on verify your email
New tenant registration- If tenant is already on registration page then after clicking verify email from mail box should show tenant is already registered
Tenant registration- Taking time to register tenant
Email verification - Email verify link is redirecting to otp verification screen.
My Workflow> Teams- Add short menu button
Tenant creation not working
After release v 3.1.2, for old updated tenant campaign module is disabled
Portal-For module update showing error, already exist
Push and FIDO scan zoom functionality not available at the time of Device MFA
Push and FIDO scan zoom functionality not available at the time of application MFA
User setting- External idp rule is active-An admin user should not be able to reset user password when the external IDP rule matches the user condition
manager notification : receiving user name required manager name
In application setting if show to user flag off then also application show in recent application.
Unable to identify application properties data type where value is empty
Amaya || Create user operation fails due to invalid password
User-Email with invalid email id like NA, this user not able to use MFA with OTP
3.1.4 Beta (13 August 2024)
UI/UX || Warning added || Application Config Import Modal || Auto 'Create Only' for User Principal policy mappings
A new feature has been developed for the "Recommendation Engine", enabling seamless integration and management of application and role recommendations. The recommendation engine supports the generation of personalised application and role suggestions for each user. The system supports the automatic synchronisation of data from various sources, ensuring that recommendations are always based on the user behaviour. All recommendation engine configurations, data synchronisation are stored and can be easily retrieved and updated as needed.
UI/UX || Amaya || Add support for JSON body validation through validate button
Audit log comparison for oldObject and newObject when they are in detailed format
UI/UX Inconsistent buttons placement in some module fixed to a default below position
UI/UX Onboarding walkthrough of New users
ICICI: a. The inbox title in the workflow setup event has been updated to display the workflow name. b. Workflow (Pending workflow list) requester and requestedFor column added for display
Identity Analytics (Reporting Engine)
End to End Request/Response Payload Encryption for all authservice's API. (/authsrvc/*)
User Threshold (Phase 2): i. Update Email Title and Template ii. Create a new 'Move to Archive' button to manually archive a user. iii. Make the notifications field mandatory in the User Threshold Configuration. iv. Added the Org Admin as the default notifier in the user threshold configuration.(Not supported for old tenant). v. Update UI Error Message Format vi. The User Threshold staging mode name has been changed. vii. Failure to Move Staging User to Archive Manually and Audit Log Display for fail. viii. The changes made to the staging dashboard view. Include a comparison between the previous and updated versions of the UI. ix. Show the display name in the Threshold Delete operation on the Staging Dashboard. x. Notification Field in User Threshold Config for delete users.
Amaya- When server connector timeout is changed and test configuration is clicked, it is showing "connector not found in cloud" error in Audit log
Import User - If loginid already exist , then remark shows "Usrsrvc.existing Login" . Change this text to "Existing Login Id"
Import/Export- Showing host server details when file is imported for script connector
My Access - Tags - Roles is not getting displayed in Application
Application - Clicking on the role tile ,SSO is happening and also while clicking on close icon, SSO is happening
Applications- When any attribute is updated (made empty in the target application) and recon for both exist operation is executed, the corresponding attribute in Cymmetri should also be cleared
Reports- SSO based application- Reports are blank/ not showing data when SSO based application are accessed (To correct the data need to perform data-logger sync for respective tenant. Refer configuration steps here)
Deprovision- User is getting deprovisioned even after user status is changed to Active from Inactive
User threshold mail notification- Title changes required
Audit log-Recon - When recon is executed with status as Inactive, audit log is showing "Recon initiated successfully" but not any log for execution failed/aborted
Audit Filter- Add cross button in Target Type and Action field.
Threshold Config- Validation message for all three operations should be similar
Threshold Create/Update- Spelling for exceeded is not correct
Notification Template - Toggle and status should display in status column as per other modules.
Create User- While creating user on newly created tenant, assign group page showing text "No group assigned , assign group"
User setting- External idp rule is active-An admin user should not be able to reset user password when the external IDP rule matches the user condition
Create user - While creating user on newly created tenant, assign application page showing text "No data found, add application"
Audit Filter- Add cross button in Target Type and Action field.
Portal-For module update showing error, already exist
My Access - Tags - Roles is not getting displayed in Application
Threshold Config- Validation message for all three operations should be similar
Threshold Create/Update- Spelling for exceeded is not correct
Notification Template - Toggle and status should display in status column as per other modules.
Create User- While creating user on newly created tenant, assign group page showing text "No group assigned , assign group"
Create user - While creating user on newly created tenant, assign application page showing text "No data found, add application"
Group Unassignment: The message appearing on group unassignment is incorrect
Push and FIDO scan zoom functionality not available at the time of Device MFA
Push and FIDO scan zoom functionality not available at the time of application MFA
Campaign Reassign -inactive users are also listed for reassignment on click
Login page- AD auth- Provide proper UI message when AD adapter details are incorrect
Amaya- When server connector timeout is changed and test configuration is clicked, it is showing "connector not found in cloud" error in Audit log
Import User - If loginid already exist , then remark shows "Usrsrvc.existing Login" . Change this text to "Existing Login Id"
User threshold- Pending Staging- When changing page select all box should be unchecked.
Threshold Pending staging- Whenever the page changes or the number of records per page is modified, the selection should be reset
Import/Export- Showing host server details when file is imported for script connector
Threshold pending staging- When the retry button is clicked multiple times, the validation message does not appear after the third click on UI
Application assignment- Change user search suggestion watermark
Onboarding registration- When resolution is at 80%, PAM report admin option is not visible in dropdown
Reports- SSO based application- Reports are blank/ not showing data when SSO based application are accessed
After release v 3.1.2, for old updated tenant campaign module is disabled
Onboarding registration- When an application is selected and then reverted to the previous page, selecting the application again causes the application count to double
External JIT- JIT configuration should be disabled until new external idp configuration details are filled
External IDP- JIT- API is showing "undefined" error on clicking JIT button and on enabling JIT configuration
External IDP- JIT- Reverse the title, it is confusing for user
MFA - Secret Question - Question selection is getting non-selectable after entering incorrect answers and then retrying for correct answer
My workspace>Inbox- Count is not showing when records are in claim
Reports( Employee's with upcoming contract end date) - By default date filter should be applied of 30 days
Provision Rule - Cursor of the condition is getting overlapped with footer of the page.
Onboarding - Login credentials timeout error
My Access - Superset Application logo and label should be changed
Applications- When any attribute is updated (made empty in the target application) and recon for both exist operation is executed, the corresponding attribute in Cymmetri should also be cleared
Deprovision- User is getting deprovisioned even after user status is changed to Active from Inactive
Audit log-Recon - When recon is executed with status as Inactive, audit log is showing "Recon initiated successfully" but not any log for execution failed/aborted
User threshold mail notification- Title changes required
Application- Managed view- When manager is removed from Cymmetri, user is still getting displayed in managed view
Create Threshold Config> Csv import- Showing empty records in pending staging list when threshold limit is exceed and user are imported via csv file
Reports- SSO based application- Reports are blank/ not showing data when SSO based application are accessed
My workspace>Inbox- Count is not showing when records are in claim
login with admin-Campaign detail show role also, currently role showing only for campaign manager
Cymmetri Selfservice App - Once we click on the web link from scanner , it should show confirmation popup on screen (Suggestion)
Selfservice Mobile App - When app is in Quit state and open the app via scanner(camera), it is not redirecting to login page of the website
Push Authenticator - Need to change the error message
User creation- While creating new users then going to next level that is on groups page and then on application page ,then user should be redirected back to the group's page when back button is clicked instead of existing user creation page
Showing error when saving workflow with name( User creation, Application provisioning, Application deprovisioning)
deployment_analytics_1 Service CPU utilisation is 100%
Campaign-email report showing error
Some time tenant registration not working,showing WriteConflict error in the service
Application provisioning and deprovisioning workflow initiated request is not getting displayed in activity logs.
Workflow Rules - Application Deprovisioning event - If condition is set as RegEx for custom attribute is not working
User update-Showing audit failed-Write conflict
Report - Updated record should display on top.
Auth rule showing unknown error
Workflow List - View any workflow detail - While clicking on info icon it is showing Grade List Detail
AD-Recon-If Policy attribute marked inactive then also it is getting pull from AD
Login via Application admin- When click on application showing processing please wait error message
Applications- Application are not getting assigned to user and also audit log is not visible for the same
PAM write admin not able to assign users, user list not populating
manager notification : receiving user name required manager name
In application setting if show to user flag off then also application show in recent application.
Unable to identify application properties data type where value is empty
Amaya || Create user operation fails due to invalid password
Reports- Records are getting displayed after 11min approximately
3.1.5 Beta (6 August 2024)
UI/UX - Workflow Inbox User detail will now have applications detail as well assigned to the user
UI/UX - Workflow Inbox will have start date and end date filter
User delete workflow support a. Workflow configuration support b. Rule configuration support
CISO Dashboard - REVERTED
Amaya || General Config based role data type
PAM write admin not able to assign users, user list not populating
Policy map- Empty value are getting saved in policy mapping
Workflow Rule update - View - Created by and updated by fields are empty
Superset - OpenId issue - While doing sso for superset application, it should is getting redirect superset url with error "The request to sign in was denied"
Threshold configuration- Replace could be to can be
Policy Map- When searching in the search box by any attribute, the search should get reset after changing tabs
Onboarding - Login credentials timeout error
Application- When searching user in application, user can be searched by first name, last name, login id but not by First name+lastname
PAM write admin not able to assign users, user list not populating
TOTP-Lookahead window change , on click save button show warning message,
User delete Workflow - Pending Workflow - Application details tab is not present
manager notification : receiving user name required manager name
In application setting if show to user flag off then also application show in recent application.
Unable to identify application properties data type where value is empty
Amaya || Create user operation fails due to invalid password
Reports- Records are getting displayed after 11min approximately
Deprovision Rule executed via Scheduler - Workflow is not getting initiated for the set of users on the basis of status/end date
Workflow List - Getting error " Contact system administrator" on technova tenant
3.1.6 (10 September 2024)
Form Logic - The FormLogic functionality, enables you to store custom data using flexible, administrator-defined forms. It empowers you to create forms tailored to your specific data collection requirements, providing a versatile solution for various data management needs. 360 Degree Reconciliation - Compare tab added to the current feature, where user can compare with the source application and target application and further generate reports and download csv.
SkipPasswordExpiry - We are enhancing our Password Policy by introducing a new field
SkipPasswordExpiry, within the PasswordChangeRule. This enhancement allows users to opt out of the password expiry process entirely. When the SkipPasswordExpiry field is enabled, users will not receive warnings or notifications about password expiry, nor will they be prompted to change their password due to its expiration.
Connector: SimpleLDAP application.
ICICI Client - Role Based form delivery in IGA.
SDK based integration to send mobile push notifications to mitigate legacy API issues: a. Fido Based Notifications b. Normal Push Based Notifications The LDAP adapter has been updated with a new feature that eliminates the need to enter a username and password for each execution.
Form logic-Configured Forms -On click setting icon screen getting flicker
Selfservice Submit form-Update error message and backend error code if pre and post hook script h
Form logic-on form submit close form
Form logic-Selfservice-My Form Submissions pagination, page getting blank
Archived Forms detail-Revision data showing wrong, showing non existing list
Form logic-After changing form schema, form detail showing blank
Form logic-User submissions-Provide search by taskeid, username, loginid
Form logic-on all screen search only working for the exact case, expected should be work for matchin
Form logic-Form table-sorting not working
Form logic-Pre and post hook should be non mandatory
Form map with rule-if form map more than defined limit then error message showing only one time
Staging users details - Version history log user details not loading
Form logic-Configured form and archive form detail, back button behaviour is not as expected, need
Form logic-Form Access Rules-Link form, save button should be disabled till form selection
form logic- if request is timeout or fail then feature showing disabled
Form logic-User submissions-Provide date filter
Workflow || Additional Form Info || Readonly text-based form submissions
Timebased Application: Timebased application assignment message spelling incorrect
Deprovision- When applications are assigned via group and deprovision is executed all the application
Teams - Suspended Users - List View - Edit - It is redirecting to Users but showing a blank screen
Application Search: When clicking on "View More Applications" and searching for an application, the
Pending Staging- When no records are present on the page, the "Select All" button should be disabled
User Onboarding - Dropdowns are not loading when creating a user after adding an Admin during t
Global search - Pending action is not coming in global search
manager notification : receiving user name required manager name
In application setting if show to user flag off then also application show in recent application.
Unable to identify application properties data type where value is empty
Amaya || Create user operation fails due to invalid password
Reports- Records are getting displayed after 11min approximately
Deprovision Rule executed via Scheduler - Workflow is not getting initiated for the set of users on th
Workflow List - Getting error " Contact system administrator" on technova tenant
FormLogic || Step 2 of form || Form config JSON should be mandatory


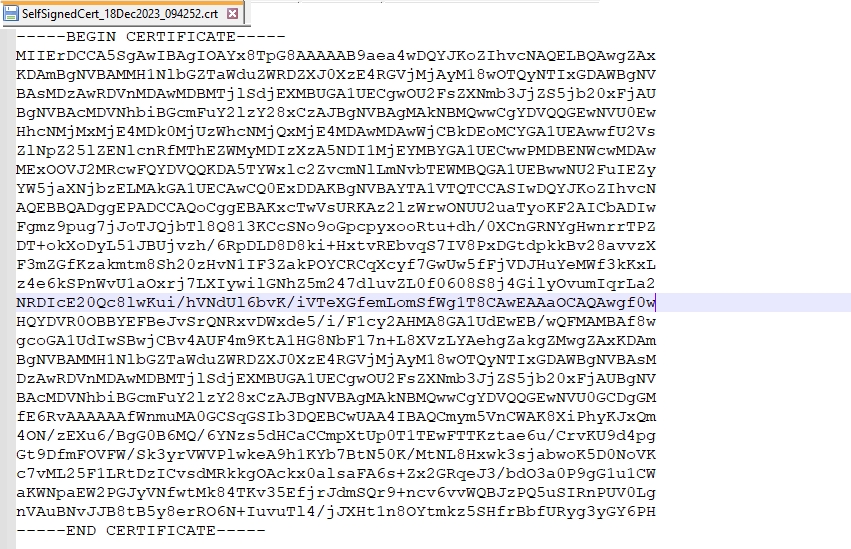



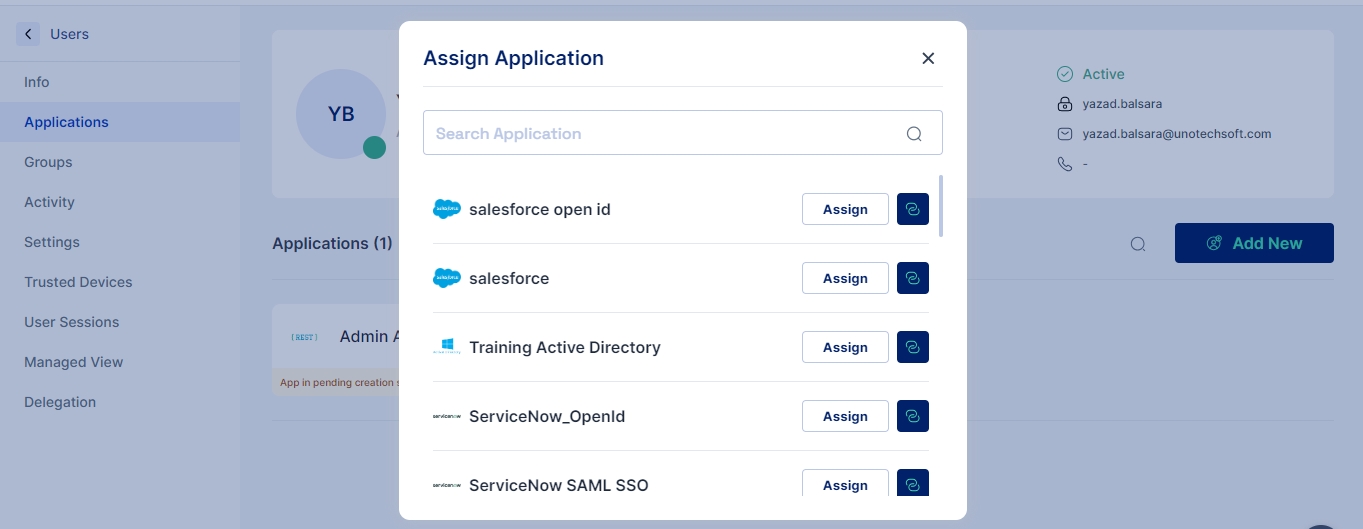
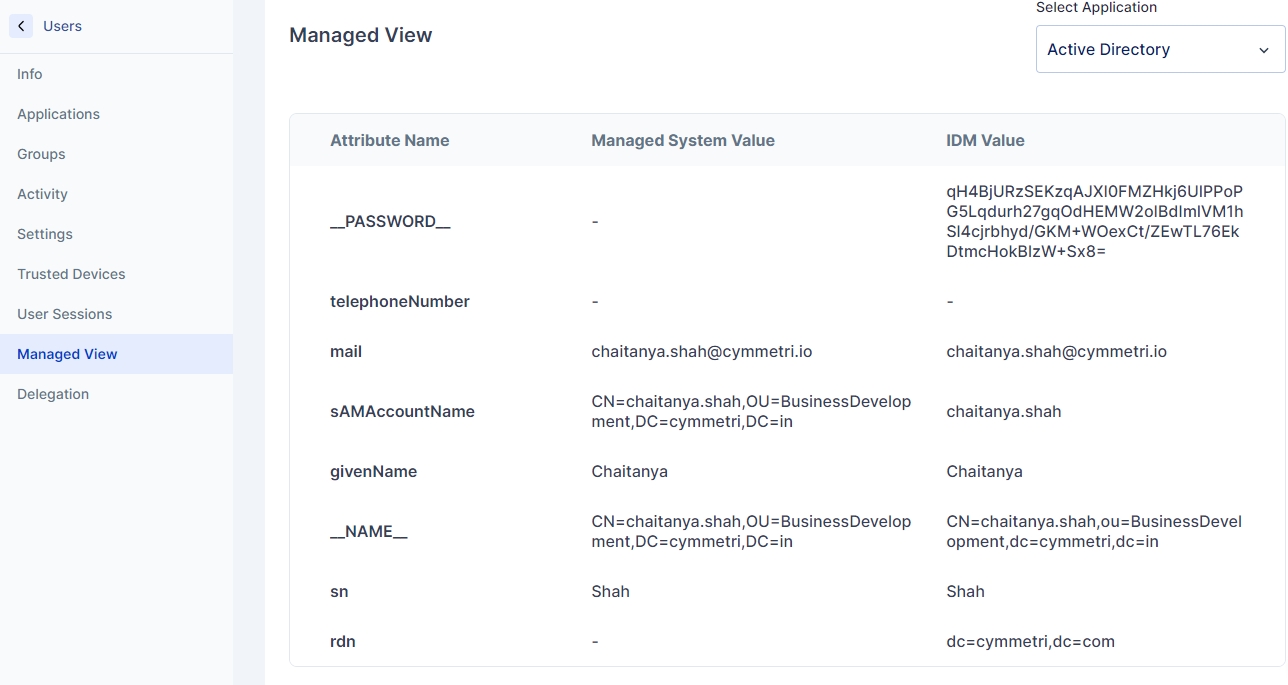

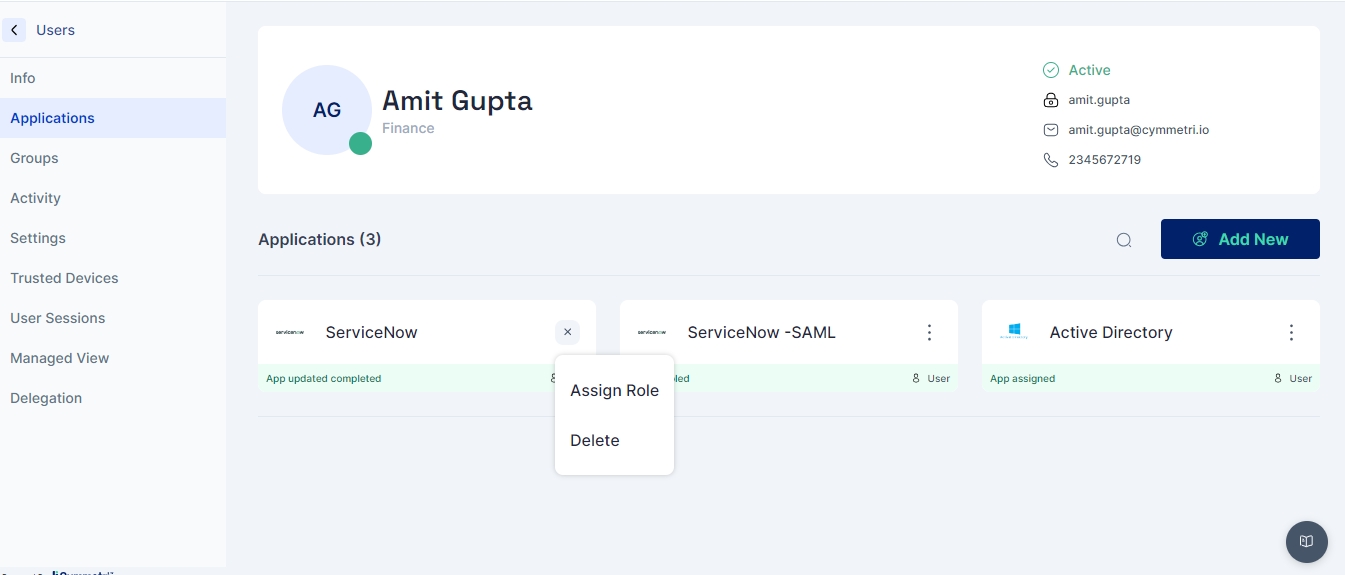


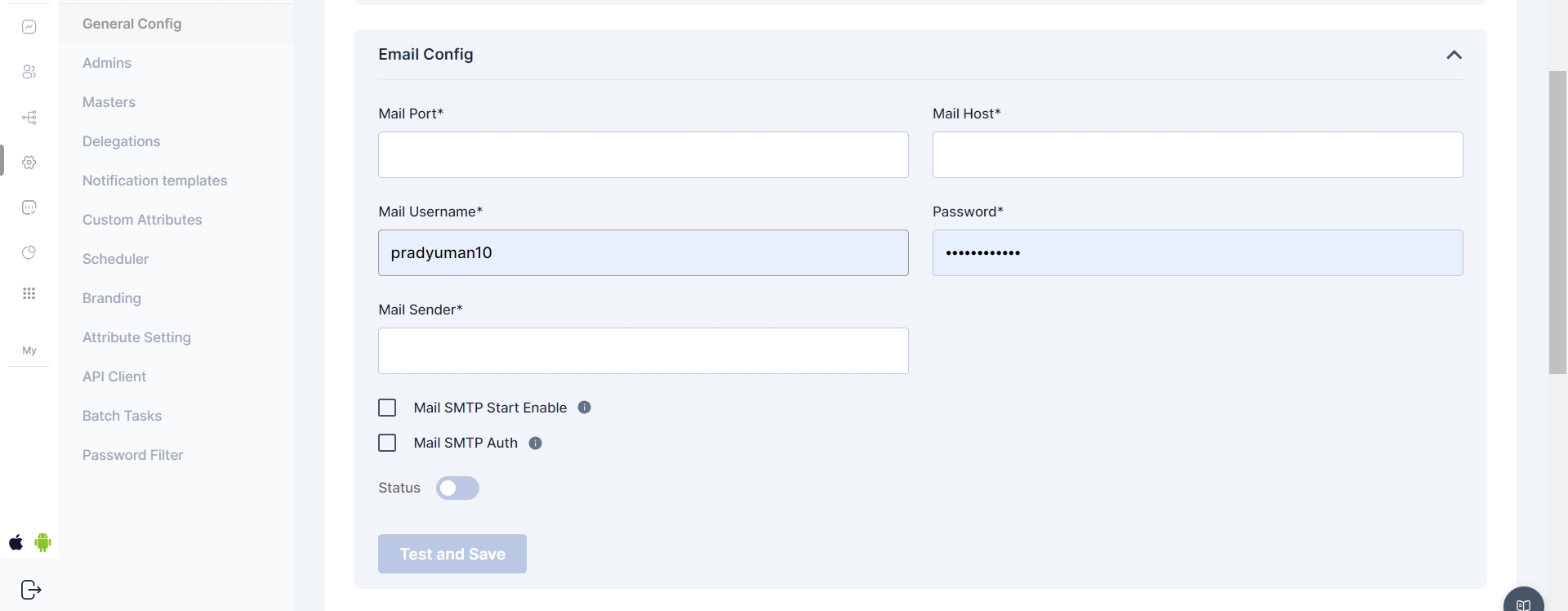
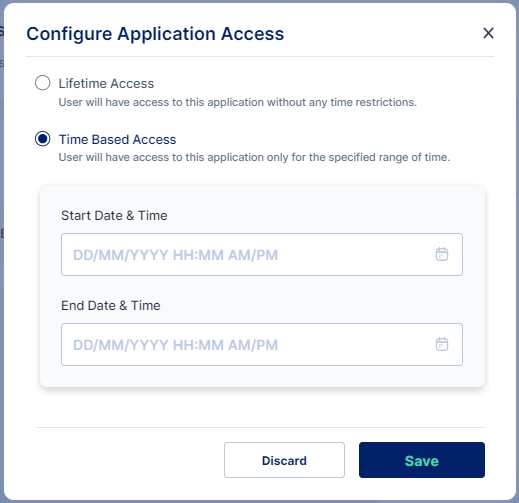

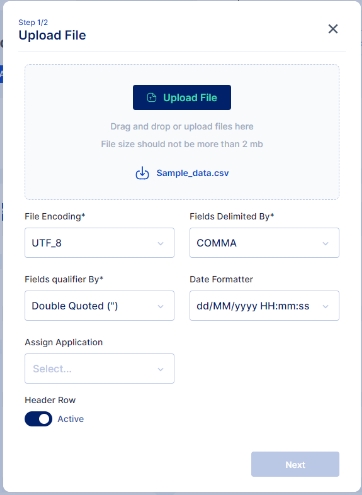

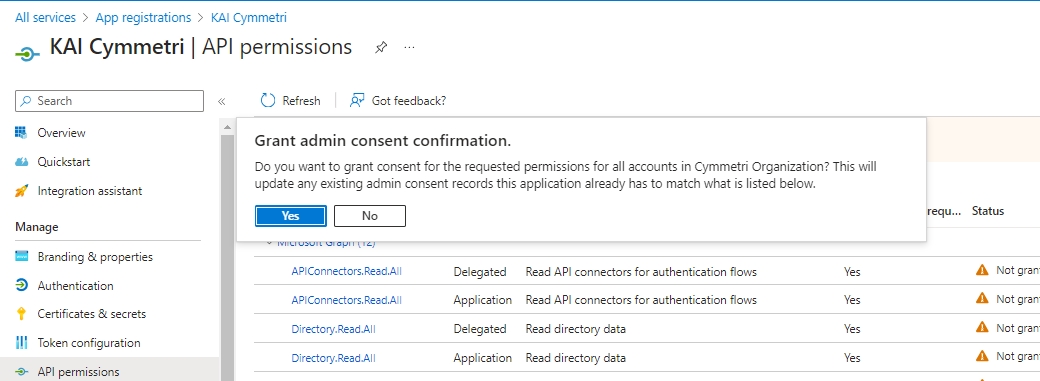
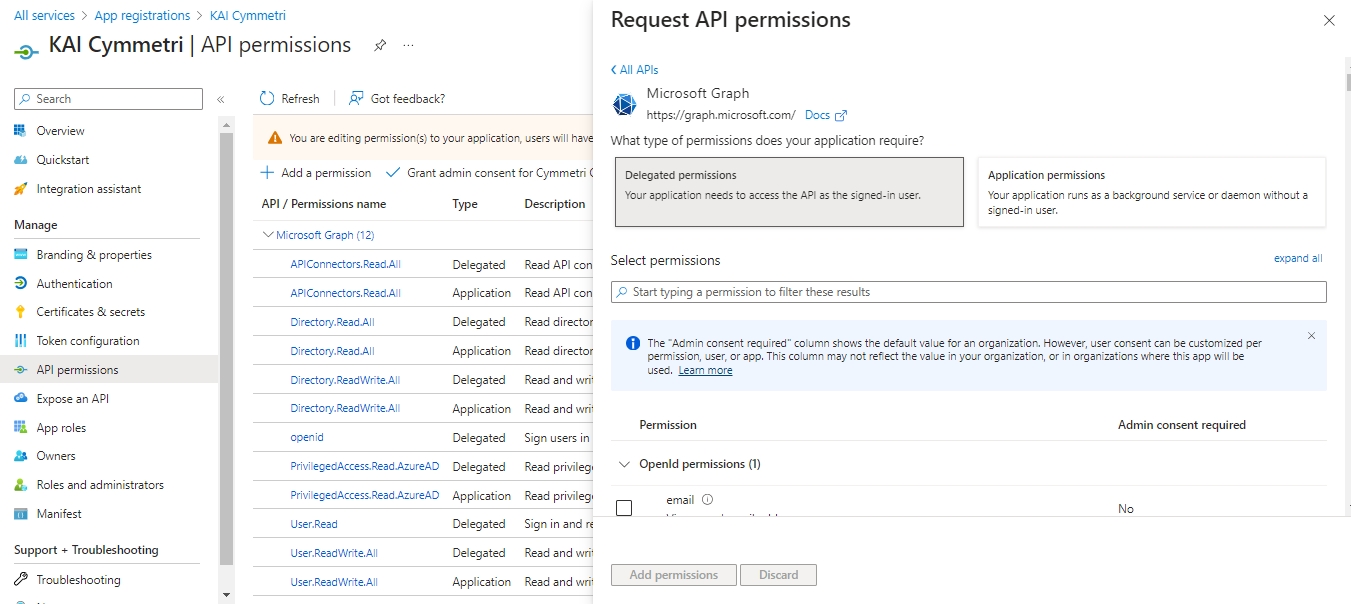
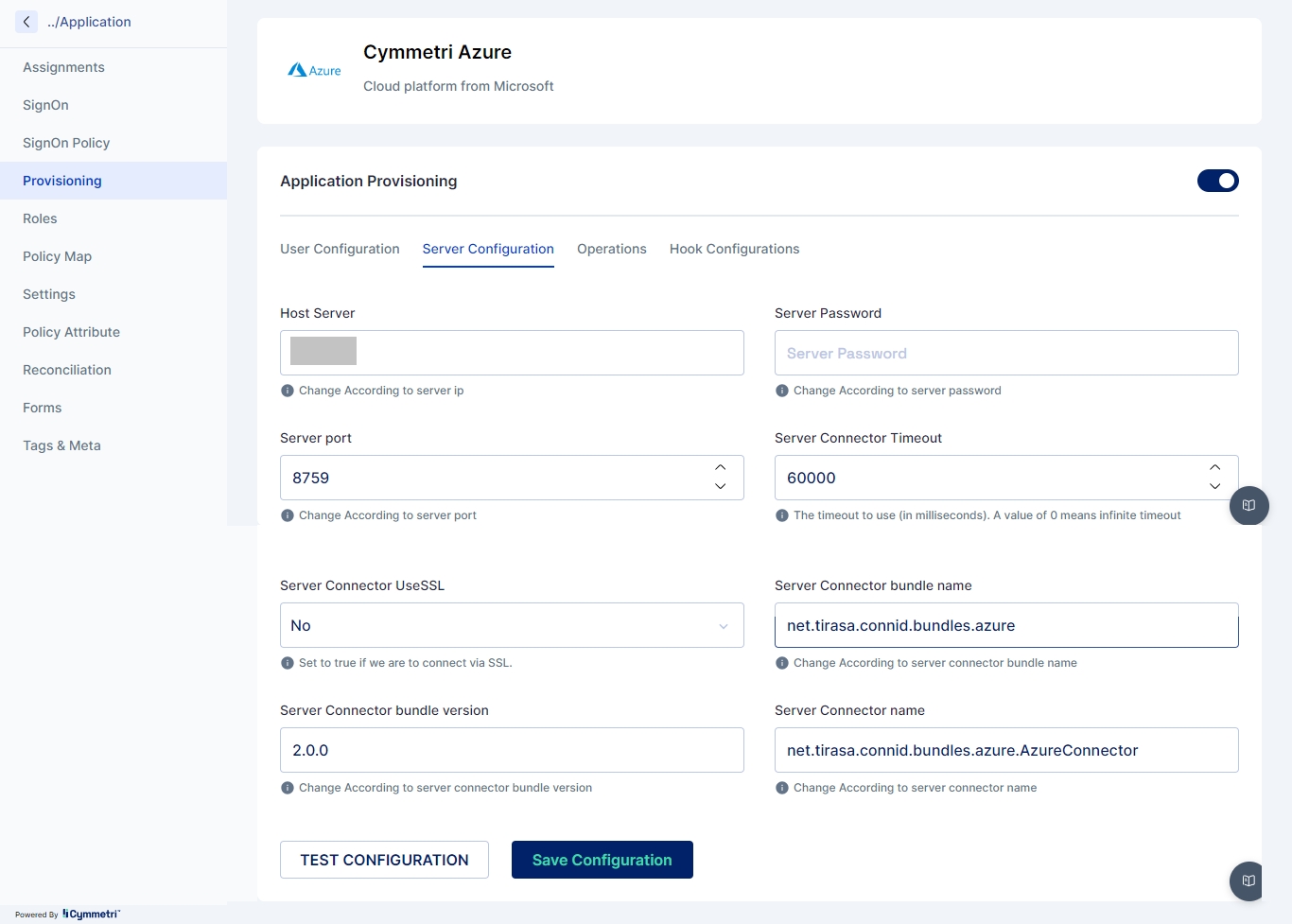
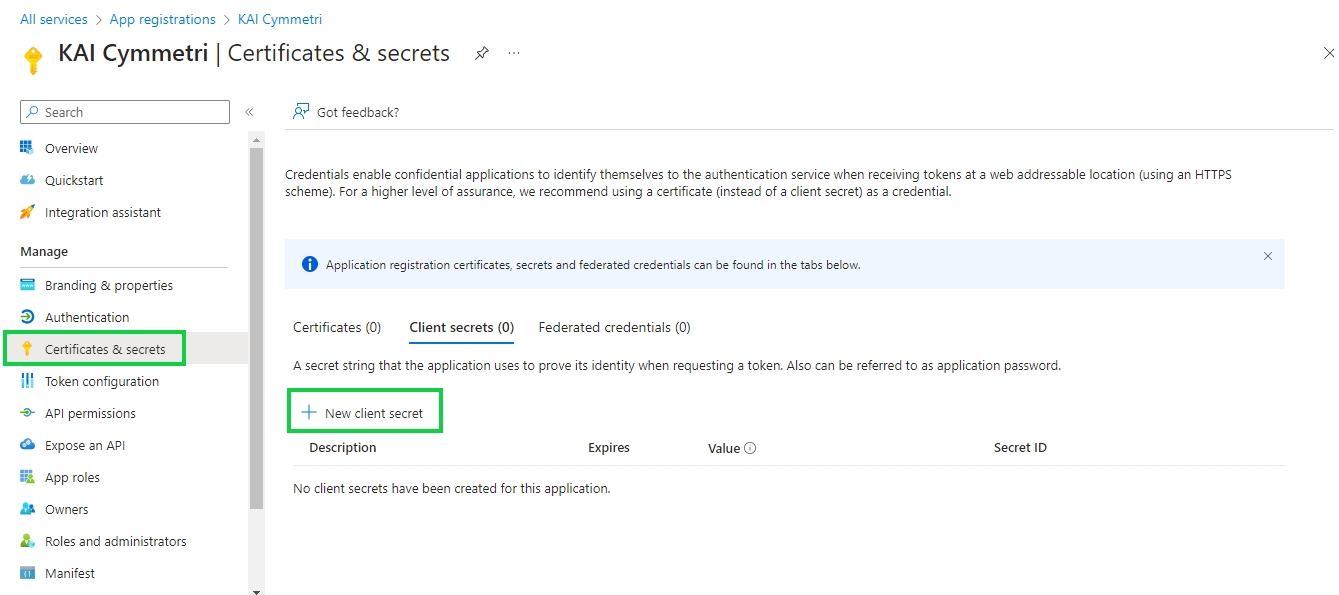
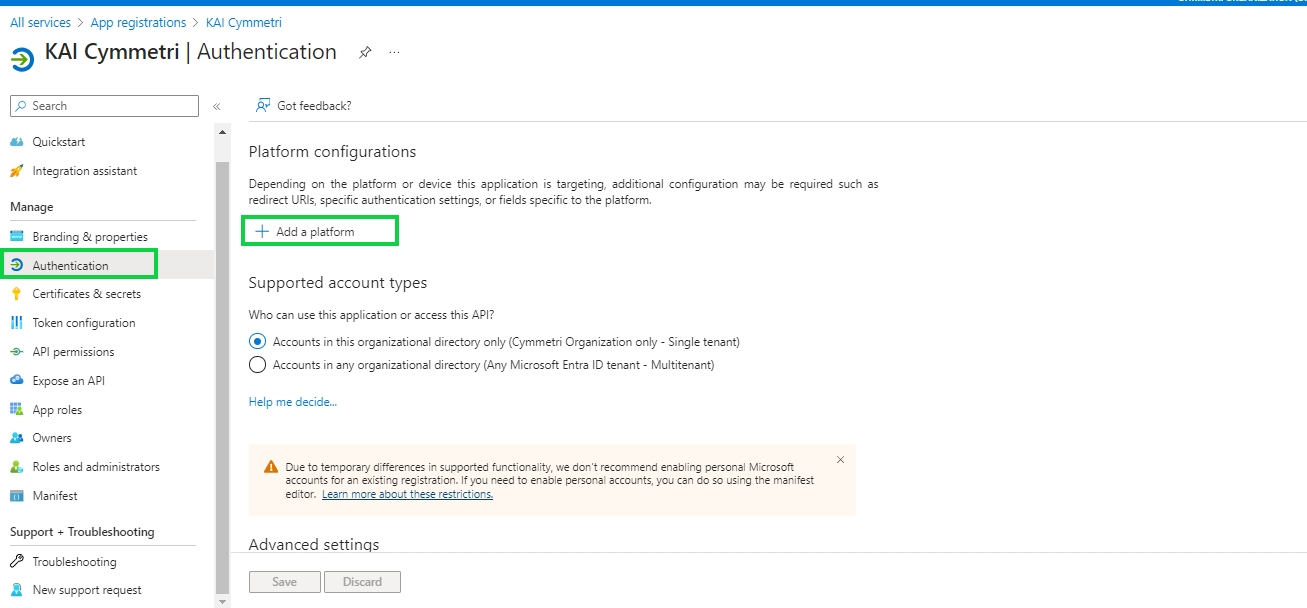

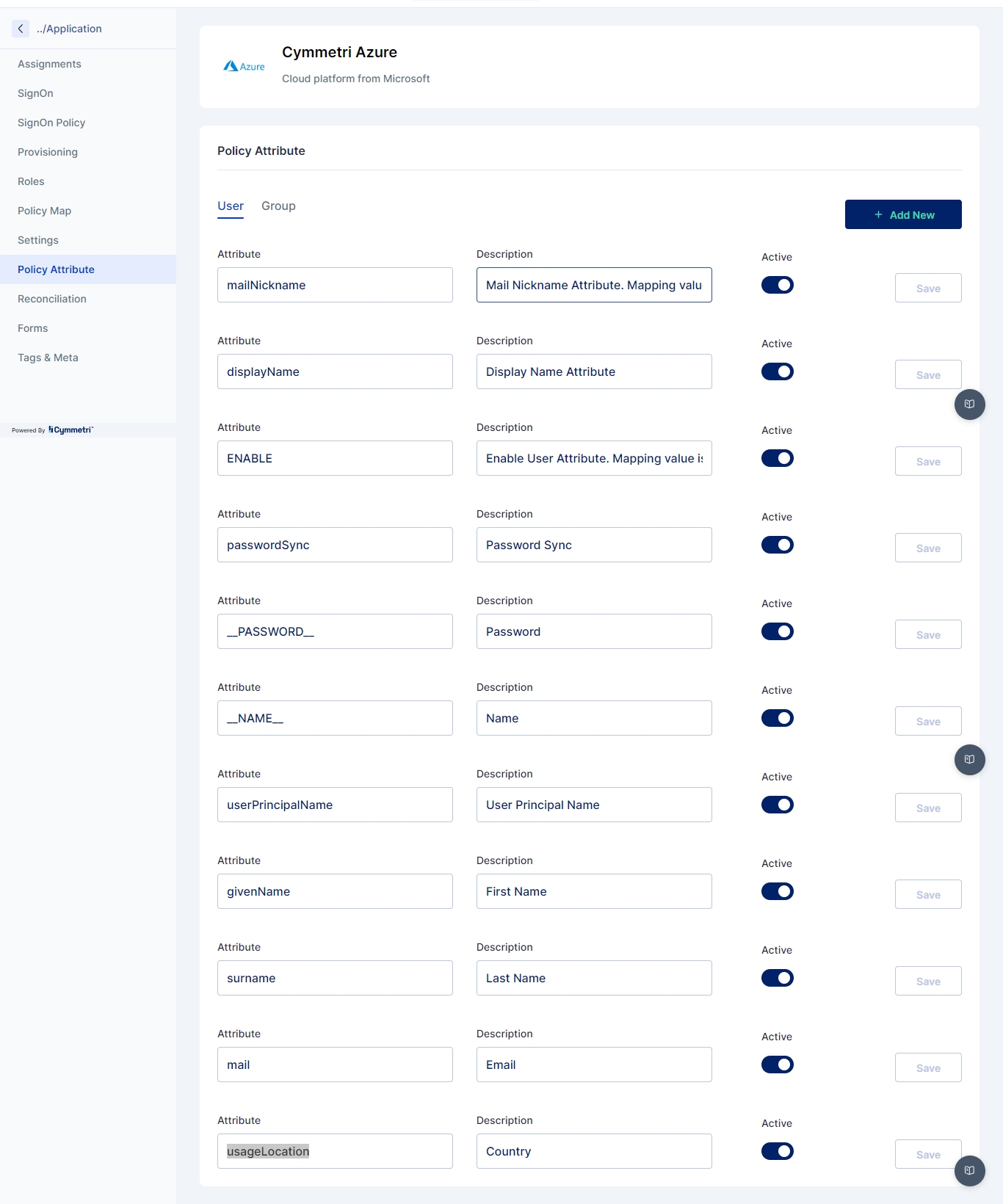
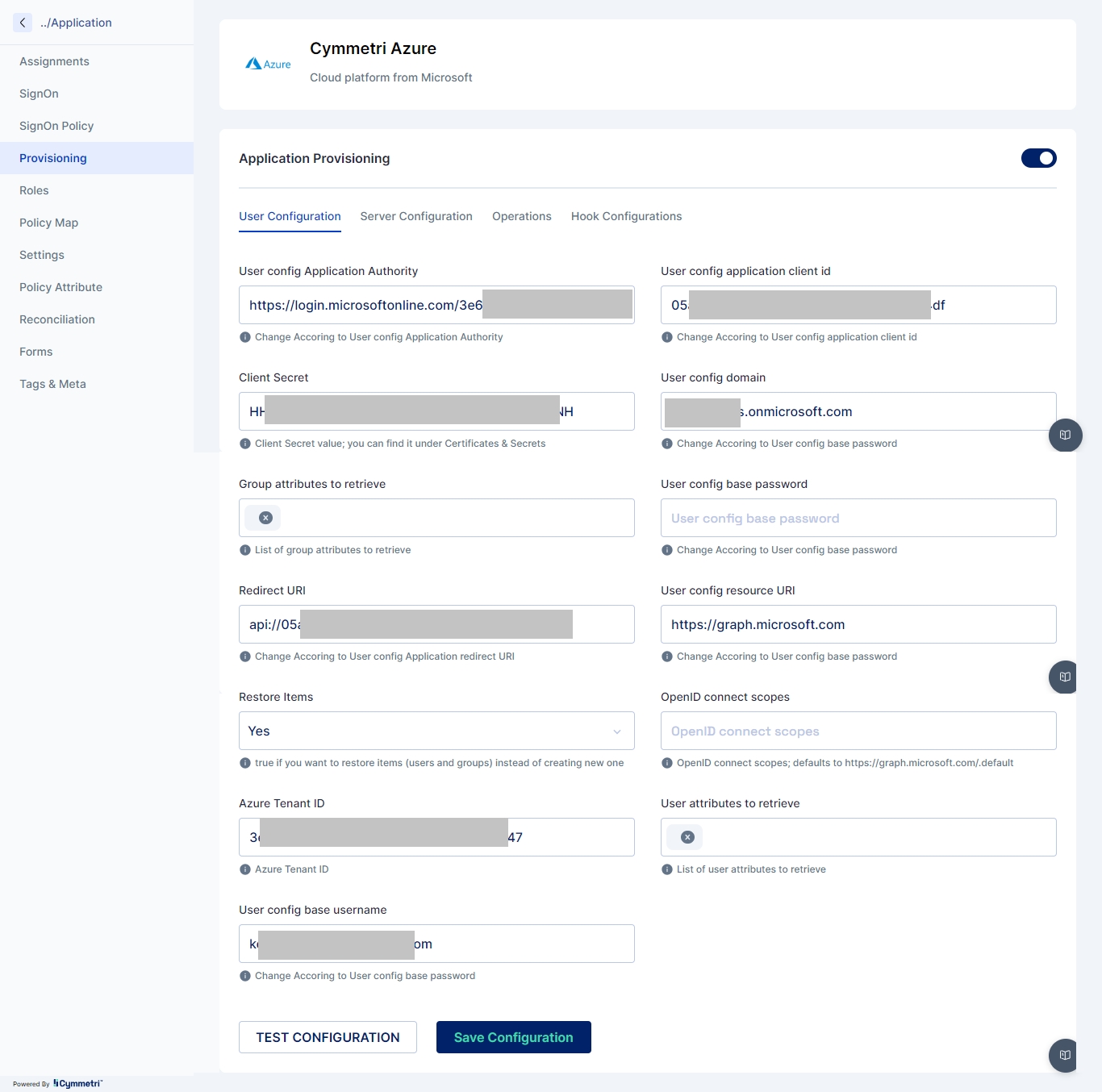
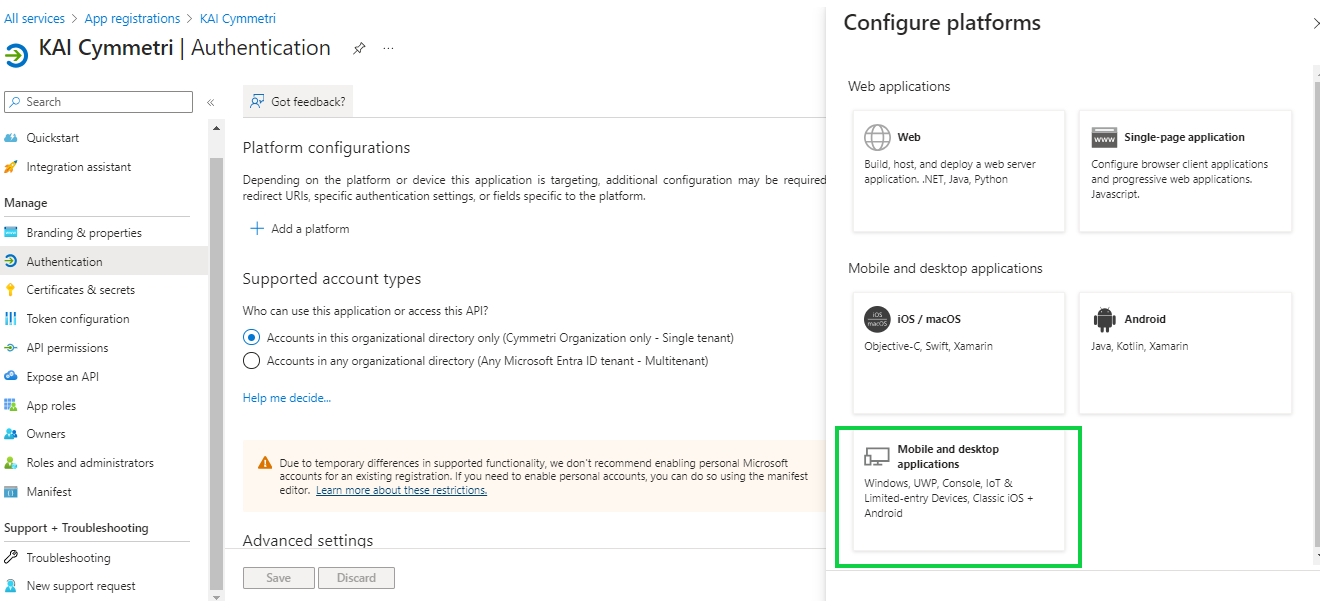
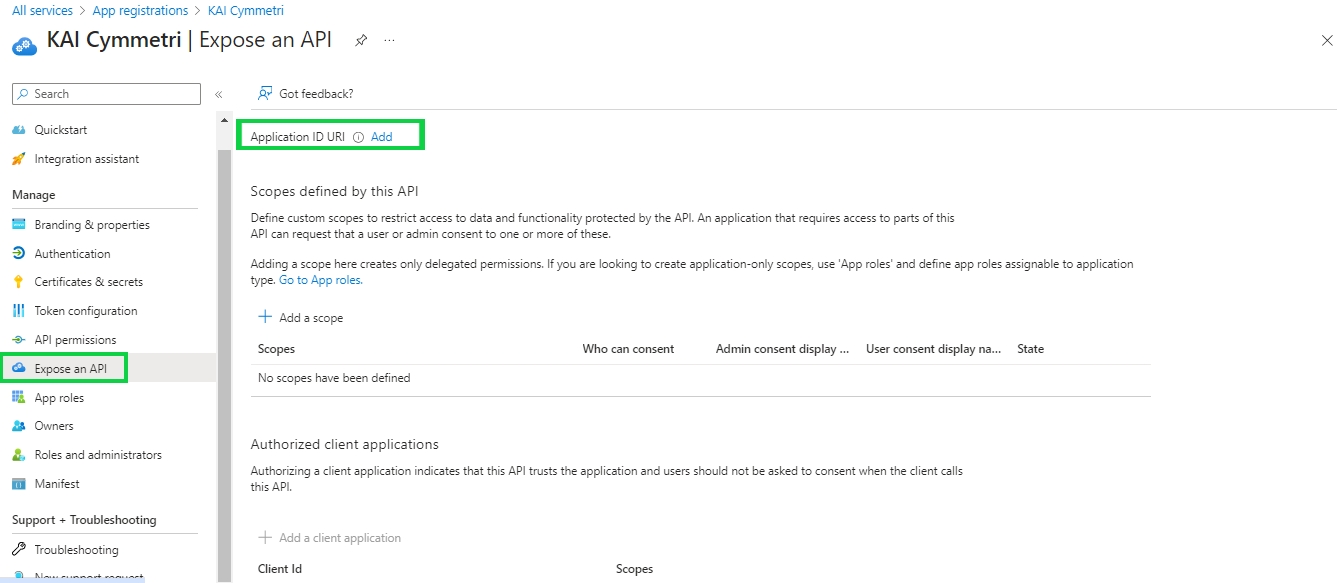
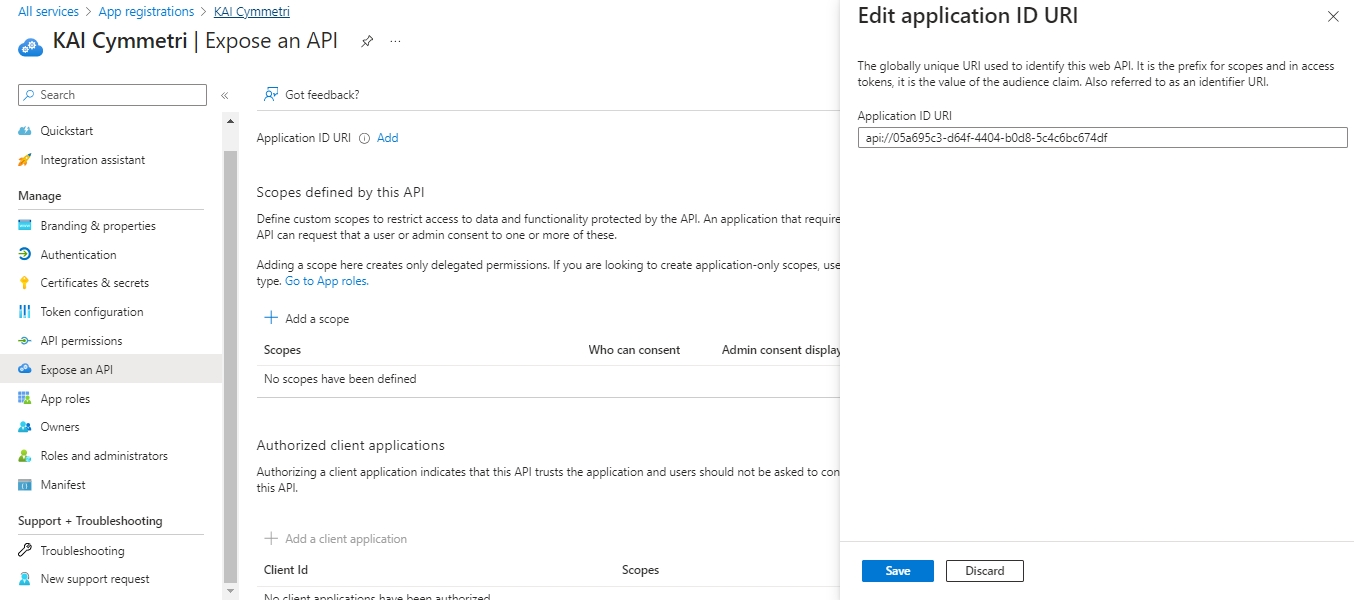
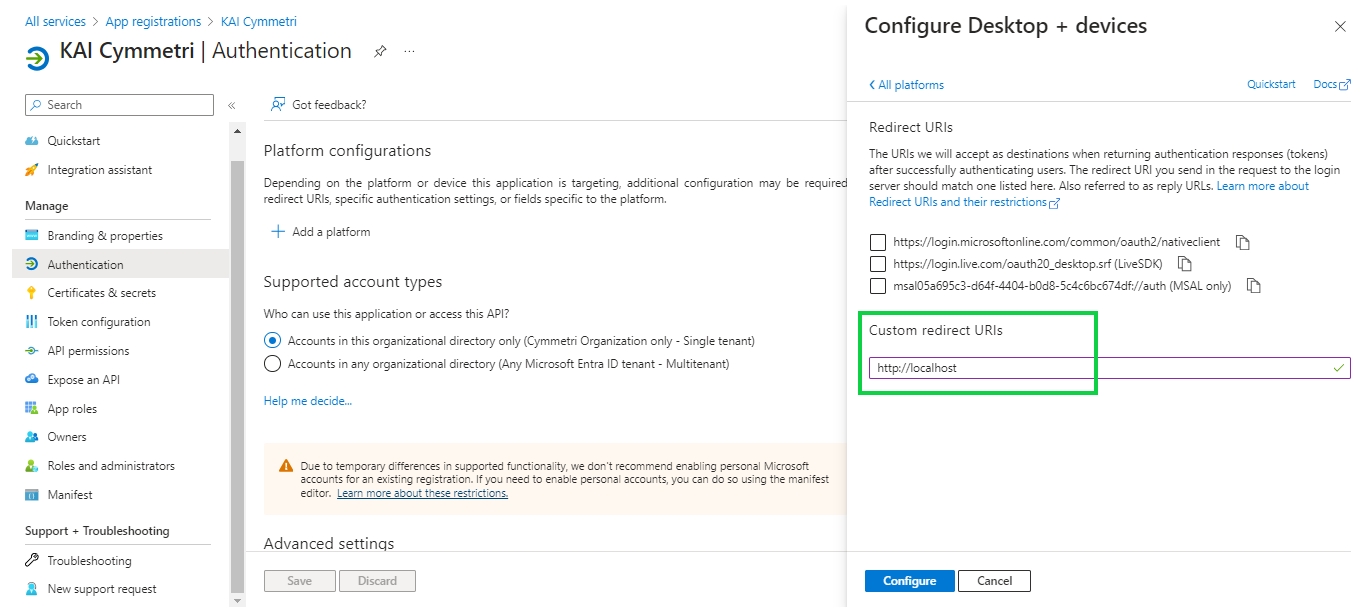




















Below is a list of Cymmetri connectors along with brief descriptions:
15Five
Employee engagement and performance management platform.
Active Directory
Directory service for managing users and resources in a Windows network.
Airbrake
Error tracking and performance monitoring tool.
Airtable
Collaborative database and spreadsheet tool.
Aiven
Managed cloud database services provider.
Akamai
Content delivery network (CDN) and cloud service provider.
AlertMediaCom
Communication and alerting platform for emergency situations.
AlertOps
Incident management and alerting system.
AlexisHR
Human resources management system.
Ally
Goal-setting and performance management tool.
AlphaSense
Market intelligence and research platform.
Alterdesk
IT service management and helpdesk software.
AlternativeInvestmentExchange
Platform for alternative investments.
Amadeus
Travel technology solutions provider.
Amazon AppStream
Desktop application streaming service.
Amazon AWS
Cloud computing services platform by Amazon.
Amazon AWS Redshift
Data warehousing service on Amazon AWS.
Amazon AWS SSO
Single Sign-On service by Amazon AWS.
Amazon Business
E-commerce platform for businesses.
AmazonManagedGrafanaSAML
Managed Grafana service with SAML support.
AmbientAI
AI-powered workplace safety and compliance solutions.
AMGTime
Time and attendance management software.
Anaplan
Cloud-based planning and performance management platform.
Anaqua
Intellectual property management software.
AndFrankly
Employee engagement and feedback platform.
Andromeda
Security and risk management solutions.
Anecdotes
Employee recognition and rewards platform.
AngelPoints
Employee rewards and recognition platform.
Animaker
DIY video-making platform.
Anodot
Real-time analytics and anomaly detection platform.
Anomalo
Data quality and anomaly detection tool.
AnswerHub
Enterprise Q&A platform.
Aon Hewitt
Human resources and benefits consulting services.
AperianGlobal
Talent management and recruitment solutions.
AppAegis
IT security and compliance solutions.
AppDynamicsEncrypted
Application performance management with encryption support.
AppDynamicsSSO
Single Sign-On support for AppDynamics.
Apperio
Legal spend management and analytics platform.
Appian
Business process management and automation platform.
AppianOnPrem
On-premises deployment of Appian's platform.
AppreciateHub
Employee recognition and rewards platform.
Apptio
IT financial management and optimization software.
Aprimo
Marketing operations and digital asset management platform.
AquaCloudSecurityPlatform
Cloud security management platform.
Arbitrip
Travel and expense management solution.
Arc GIS Online
Online geographic information system (GIS) service.
ArculessAML
Anti-Money Laundering compliance platform.
Area1Horizon
Security solution for email and phishing protection.
Area1Security
Advanced threat protection and security platform.
Ariba Network
Procurement and supply chain management platform.
AribaContractManagement
Contract management solutions by Ariba.
Articulate360
eLearning authoring and content creation suite.
Arxspan
Laboratory information management system (LIMS).
Asana
Work management and collaboration tool.
AskSpoke
IT support and service management platform.
AspenMesh
Service mesh solution for microservices.
Aspera
High-speed file transfer solutions.
AsperaV4
Updated version of Aspera's file transfer solutions.
AssemblaSAML
Single Sign-On (SSO) integration for Assembla.
Assembly
Employee engagement and performance management platform.
AssetBank
Digital asset management system.
AssetSonar
IT asset management and inventory system.
Atatus
Application performance monitoring and error tracking.
Atiim
Performance management and employee feedback platform.
Atipica
Talent acquisition and recruitment solutions.
Atlassian
Collaboration and productivity tools, including Jira and Confluence.
AtlassianCloud
Cloud-based solutions by Atlassian.
Attendease
Event management and planning software.
Aurion
HR and payroll management system.
Autodesk360
Cloud-based design and engineering tools.
Automox
Endpoint management and patching solution.
Auvik
Network management and monitoring solution.
AvidSecureInc
Security and compliance management services.
AvisoSAML
SAML integration for Aviso.
Avochato
Communication and messaging platform for sales teams.
Awardco
Employee recognition and rewards platform.
Axiom
Data management and analytics platform.
Axomo
IT management and automation solutions.
Axonius
Security asset management and visibility platform.
AxwayAmplify
Integration and API management platform by Axway.
Cloud computing services platform by Microsoft.
BakerHillNextGen
Loan origination and account management platform.
BambooHR
Human resources management and tracking software.
BambuSproutSocial
Social media management and marketing tools.
BanyanCommandCenter
Security and access management solution.
BasicOps
IT operations and incident management platform.
Beam
Employee engagement and performance management tool.
BeautifulAI
Presentation and slide design software.
BenchlingEnterprise
Life sciences research and data management platform.
BenefexRewardHub
Employee rewards and benefits management platform.
BenefitFocus
Benefits administration and management platform.
BenefitsolverSAML
SAML integration for Benefitsolver.
Beneplace
Employee benefits and discount programs.
Benetrac
Benefits administration and management software.
Benevity
Corporate social responsibility and employee giving platform.
BenSelect
Employee benefits selection and management tool.
Betterworks
Performance management and goal-setting platform.
BeyondTrust
Privileged access management and security solutions.
BigCenter
IT management and support platform.
BigID
Data privacy and protection platform.
BigPanda
IT operations and incident management platform.
BigTinCan
Sales enablement and content management solutions.
Birdeye
Customer experience and reputation management platform.
Birst
Business intelligence and analytics platform.
BitGlass
Cloud security and data protection platform.
BitlySAML
SAML integration for Bitly.
BitSightTech
Security ratings and risk management platform.
Biztera
IT management and service delivery platform.
Blackboard
Education technology and learning management system.
Blink
Employee communication and engagement platform.
BlissBook
Employee recognition and engagement tool.
Blissfully
SaaS management and vendor management platform.
BlocksEdit
Content management and editing tool.
BlogIn
Blog management and publishing platform.
BlueBoard
Employee recognition and rewards platform.
BlueJeans
Video conferencing and collaboration tool.
BlueOceanBrain
Employee learning and development platform.
BMCAtriumSSO
Single Sign-On integration for BMCAtrium.
BoardBookit
Board meeting and governance management tool.
BoardEffect
Board management and governance platform.
Bob
People management and HR platform.
Bonsai
Freelance management and invoicing software.
BoomiSAML
SAML integration for Boomi.
Boostr
Employee recognition and performance management tool.
BoxNet
Cloud storage and file sharing service.
Brainshark
Sales enablement and training platform.
BrainstormQuickHelp
Quick help and support tool for brainstorming.
BranchSAML
SAML integration for Branch.
BrandfolderSAML
SAML integration for Brandfolder.
BrandWorkzCom
Brand management and marketing platform.
Braze
Customer engagement and marketing automation platform.
Breezy
Recruitment and applicant tracking system.
BreezyHR
HR and recruitment software.
BridgeCrew
Cloud security and compliance platform.
BrightEdge
SEO and content performance platform.
CentrifyPrivilegeAccessService
Privileged access management and security solution.
CenturyLink
Telecommunications and cloud services provider.
CequenceSecurity
Security solutions for data and infrastructure.
Cerby
Security and compliance management platform.
Ceresa
Data protection and privacy management solution.
Ceridian
Human resources and payroll management software.
Cerner
Health information technology solutions provider.
Certify
Expense management and reporting tool.
Cezanne
HR software for small and medium-sized businesses.
CGRFoundation
Foundation for research and data management.
ChangePoint
Project and portfolio management software.
Chargebee
Subscription management and billing platform.
ChartHop
Org chart and employee directory tool.
ChartioSAML
SAML integration for Chartio.
ChatterSAML
SAML integration for Chatter.
ChatWork
Team communication and collaboration platform.
CheckpointInfinityPortal
Security management and threat detection solution.
Cherwell
IT service management and workflow automation platform.
ChorusAI
Conversation analytics and sales performance platform.
ChromeRiver
Travel and expense management software.
CSV Directory
Custom integration for CSV-based directories.
Custom
Custom integration solution for unique use cases.
DarwinBox
HR and talent management software.
FreshDesk
Customer support and ticketing system.
Freshservice
IT service management and helpdesk software.
Freshworks
Customer engagement and support platform.
Google services integration, including Google Workspace.
Google Workplace
Productivity and collaboration suite by Google.
hCaptcha
CAPTCHA service for protecting websites from bots.
Hive
Collaboration and project management tool.
Ingenium
Enterprise content management system.
Jedox
Performance management and business analytics platform.
Jenkins
Continuous integration and delivery tool.
Joomla
Content management system for websites.
LDAP
Lightweight Directory Access Protocol for directory services.
Liferay
Enterprise portal and content management system.
Lotus Notes
Email and collaboration software.
Lucid
Visual collaboration and diagramming tool.
Lucidchart
Diagramming and flowchart creation software.
ManageEngine AD Manager Plus
Active Directory management and reporting tool.
ManageEngine ServiceDesk Plus
IT service management and helpdesk solution.
NetSuite
Cloud-based ERP and business management software.
NextThink
IT operations analytics and end-user experience management.
oDesk
Freelance job platform (now Upwork).
Office365
Productivity suite by Microsoft.
OracleFusion
Oracle's suite of cloud-based enterprise applications.
OracleHCM
Human Capital Management solutions by Oracle.
PagerDuty
Incident management and response platform.
Paladin
Legal and compliance management software.
PaloAltoNetworksSAML
SAML integration for Palo Alto Networks.
PAM
Privileged Access Management solutions.
Pivotal
Application development and deployment platform.
Piwik
Open-source web analytics platform (now Matomo).
PowerShell
Task automation and configuration management framework.
Prezi
Presentation software with interactive and dynamic features.
ReadCube
Research management and document discovery tool.
SailPointIIQ
Identity governance and administration platform.
Salesforce
Customer relationship management (CRM) platform.
Samanage
IT service management and asset management software.
SAPNetWeaverSAML
SAML integration for SAP NetWeaver.
ScienceLogic
IT operations and management platform.
SCIM v1.1
System for Cross-domain Identity Management version 1.1.
SCIM v2.0 (Basic)
Basic implementation of SCIM v2.0 for user management.
SCIM v2.0 (Bearer)
SCIM v2.0 with Bearer token authentication.
SCIM v2.0 (Fixed Bearer)
SCIM v2.0 with Fixed Bearer token authentication.
SCIM v2.0 (Github)
SCIM v2.0 implementation for GitHub.
SCIM v2.0 (Salesforce)
SCIM v2.0 implementation for Salesforce.
Script Connector
Custom integration using scripting for unique requirements.
ServiceNow
IT service management and enterprise workflow solutions.
Shutterstock
Stock photo and image licensing platform.
Sisense
Business intelligence and analytics platform.
Slack
Team communication and collaboration tool.
Smartsheet
Work management and automation platform.
SNOW Commander
Snowflake data management and automation tool.
Snowflake
Cloud-based data warehousing platform.
Splunk
Data analysis and monitoring platform.
SplunkCloud
Cloud-based data analysis and monitoring by Splunk.
SuccessFactors
Human resources management and talent management solutions.
SugarCRM
Customer relationship management (CRM) software.
Tableau
Data visualization and business intelligence platform.
TeamViewer
Remote access and support software.
Vimeo
Video hosting and sharing platform.
Zendesk
Customer service and support ticketing system.
Zenduty
Incident management and response platform.
ZingHR
Human resources management and payroll solutions.




Cymmetri framework to extend the out of box use cases and support custom requirements from the platform
The following are the APIs calls.
Important Note:
Purpose: This API is used to create an application hook
URL: http://<tenant_domain>/api/user/listByApplication
Method: POST
Example Request:
Sample Response:
On success:
{
"success": true,
"data": {
"content": [
{
"id": "619ce9a69139ca14885a4717",
"displayName": "John Snow",
"firstName": "John",
"lastName": "Snow",
"email": null,
"mobile": null,
"designation": "Developer",
"status": "ACTIVE",
"profilePic": null,
"login": "john.snow",
"initialLoginPending": true,
"startDate": null,
"endDate": null,
"provStatus": {
"617253cc2fb4b2125b237b75": "SUCCESS_UPDATE"
}
}
],
"pageable": {
"sort": [
{
"direction": "ASC",
"property": "id",
"ignoreCase": false,
"nullHandling": "NATIVE",
"ascending": true,
"descending": false
}
],
"pageNumber": 0,
"pageSize": 10,
"offset": 0,
"paged": true,
"unpaged": false
},
"last": true,
"totalPages": 1,
"totalElements": 1,
"sort": [
{
"direction": "ASC",
"property": "id",
"ignoreCase": false,
"nullHandling": "NATIVE",
"ascending": true,
"descending": false
}
],
"first": true,
"number": 0,
"numberOfElements": 1,
"size": 10,
"empty": false
},
"timestamp": "02-Mar-2022 01:58:57",
"message": null,
"errorCode": null
}
On failure:
Response 1#
{
"data": null,
"success": false,
"errorCode": "PROVSRVC.APPLICATION_NOT_FOUND",
"message": null,
"timestamp": "02-Mar-2022 01:59:39"
}
Purpose: This API is used to get an application hook for the provided application id and type.
URL: http://<tenant_domain>/api/group/groupListByApplication
Method: POST
applicationId: Application id
Example Request:
Sample Response:
On success:
{
"success": true,
"data": {
"offset": 0,
"pageSize": 10,
"totalElements": 1,
"totalPages": 1,
"elements": [
{
"id": "621cdbb7776c95564c0313ab",
"name": "Gold",
"type": "LocalGroup",
"description": "Gold group",
"ouId": "",
"ouName": null,
"parentGroupIds": null,
"directParentGroupId": null,
"userCount": 0,
"appCount": 1
}
],
"pageNumber": 0,
"sort": {
"orders": [
{
"direction": "ASC",
"property": "name"
}
],
"sorted": true
}
},
"timestamp": "03-Mar-2022 05:29:23",
"message": null,
"errorCode": null
}
On failure:
Response 1#
{
"data": null,
"success": false,
"errorCode": "PROVSRVC.APPLICATION_NOT_FOUND",
"message": null,
"timestamp": "03-Mar-2022 05:29:49"
}
Purpose: This API is used to list reconciliation pulls for the provided application ID and keyword.
URL: https://<tenant_domain>/provsrvc/reconciliation/pull/search
Method: POST
applicationId: applicationId
keyword: keyword
Example Request:
Sample Response:
On success:
{
"success": true,
"data": {
"content": [
{
"id": "621cca3f9423002d41cbbed4",
"name": "AD-ADMIN-USERS",
"type": "USER",
"status": "ACTIVE",
"applicationId": "614b5d3489ad96554e89e2ab",
"targetSystemSearchQueryFilter": null,
"idmRepositoryField": "login",
"sourceAttributeName": "cn",
"reconType": "PULL",
"reconMode": "FILTERED_RECONCILIATION",
"reconConditions": {
"TARGET_DELETED_IDM_EXISTS": "IGNORE",
"TARGET_EXTSTS_IDM_EXISTS": "IGNORE",
"TARGET_EXTSTS_IDM_NOT_EXISTS": "PROVISION"
},
"lastRunDateTime": null,
"createdDateTime": "2022-02-28T13:12:31.07",
"updatedDateTime": "2022-03-02T12:45:31.069",
"version": 2
},
...
...
],
"pageable": {
"sort": [
{
"direction": "DESC",
"property": "updatedDateTime",
"ignoreCase": false,
"nullHandling": "NATIVE",
"ascending": false,
"descending": true
}
],
"pageNumber": 0,
"pageSize": 10,
"offset": 0,
"paged": true,
"unpaged": false
},
"last": true,
"totalPages": 1,
"totalElements": 3,
"first": true,
"sort": [
{
"direction": "DESC",
"property": "updatedDateTime",
"ignoreCase": false,
"nullHandling": "NATIVE",
"ascending": false,
"descending": true
}
],
"numberOfElements": 3,
"size": 10,
"number": 0,
"empty": false
},
"timestamp": "03-Mar-2022 08:41:03",
"message": null,
"errorCode": null
}
On failure:
Response 1#
{
"success": false,
"data": null,
"timestamp": "03-Mar-2022 09:06:43",
"message": null,
"errorCode": "INVALID_ARGUMENTS"
}
Response 2#
{
"success": false,
"data": null,
"timestamp": "03-Mar-2022 09:06:43",
"message": null,
"errorCode": "PROVSRVC.UNKNOWN"
}
Purpose: This API is used to list reconciliation push for provided application id and keyword.
URL: http://<tenant_domain>/reconciliation/push/search
Method: POST
applicationId: Application Id.
keyword : keyword
Example Request:
Sample Response:
On success:
{
"success": true,
"data": {
"content": [
{
"id": "62207b1655a2d10f525dc2bf",
"name": "AD-Admin",
"type": "USER",
"status": "ACTIVE",
"applicationId": "614b5d3489ad96554e89e2ab",
"idmSearchQueryFilter": {
"location": null,
"reportingManager": null,
"department": null,
"designation": null,
"group": null,
"email": null,
"mobile": null,
"status": [],
"userType": null,
"locked": false
},
"idmRepositoryField": "login",
"sourceAttributeName": "cn",
"reconType": "PUSH",
"reconMode": "FILTERED_RECONCILIATION",
"reconConditions": {
"IDM_DELETED_TARGET_EXISTS": "IGNORE",
"IDM_EXTSTS_TARGET_EXISTS": "IGNORE",
"IDM_EXTSTS_TARGET_NOT_EXISTS": "PROVISION"
},
"lastRunDateTime": null,
"createdDateTime": "2022-03-03T08:23:50.963",
"updatedDateTime": "2022-03-03T08:23:50.963",
"version": 0
}
…
…
],
"pageable": {
"sort": [
{
"direction": "DESC",
"property": "updatedDateTime",
"ignoreCase": false,
"nullHandling": "NATIVE",
"ascending": false,
"descending": true
}
],
"pageNumber": 0,
"pageSize": 10,
"offset": 0,
"paged": true,
"unpaged": false
},
"last": true,
"totalPages": 1,
"totalElements": 3,
"first": true,
"sort": [
{
"direction": "DESC",
"property": "updatedDateTime",
"ignoreCase": false,
"nullHandling": "NATIVE",
"ascending": false,
"descending": true
}
],
"numberOfElements": 3,
"size": 10,
"number": 0,
"empty": false
},
"timestamp": "03-Mar-2022 08:40:09",
"message": null,
"errorCode": null
}
On failure:
Response 1#
{
"success": false,
"data": null,
"timestamp": "03-Mar-2022 09:06:43",
"message": null,
"errorCode": "INVALID_ARGUMENTS"
}
Response 2#
{
"success": false,
"data": null,
"timestamp": "03-Mar-2022 09:06:43",
"message": null,
"errorCode": "PROVSRVC.UNKNOWN"
}
Purpose: This API is used to list application roles with provided application id and keyword.
URL: http://<tenant_domain>/applicationRole/findAppRolesByApplicationId
Method: POST
application id: applicationId
keyword: keyword
Example Request:
Sample Response:
On success:
{
"success": true,
"data": {
"content": [
{
"id": "621f2996a36e574d3e7ab4a7",
"roleId": "ROLE_ID_101",
"roleName": "ADMIN",
"roleDescreption": "This role is for admin users.",
"applicationId": "614b5d3489ad96554e89e2ab",
"cosoType": "Admin",
"active": false,
"mappedBusinessRoles": [],
"createdDateTime": "2022-03-02T08:23:50.608",
"updatedDateTime": "2022-03-02T13:48:54.189",
"version": 3
},
...
...
],
"pageable": {
"sort": [
{
"direction": "ASC",
"property": "id",
"ignoreCase": false,
"nullHandling": "NATIVE",
"ascending": true,
"descending": false
}
],
"pageNumber": 0,
"pageSize": 10,
"offset": 0,
"paged": true,
"unpaged": false
},
"last": true,
"totalPages": 1,
"totalElements": 3,
"first": true,
"sort": [
{
"direction": "ASC",
"property": "id",
"ignoreCase": false,
"nullHandling": "NATIVE",
"ascending": true,
"descending": false
}
],
"numberOfElements": 3,
"size": 10,
"number": 0,
"empty": false
},
"timestamp": "03-Mar-2022 09:20:03",
"message": null,
"errorCode": null
}
On failure:
Response 1#
{
"success": false,
"data": null,
"timestamp": "03-Mar-2022 09:06:43",
"message": null,
"errorCode": "INVALID_ARGUMENTS"
}
Response 2#
{
"success": false,
"data": null,
"timestamp": "03-Mar-2022 09:06:43",
"message": null,
"errorCode": "PROVSRVC.UNKNOWN"
}
Purpose: This API is used to search PolicymapTenant.
URL: http://<tenant_domain>/policyMapTenant/findAll
Method: POST
tenantApplicationId: Tenant Application Id
objectType: Mapping Object Type
internal: Internal Attribute
external: External Application Attribute
Example Request:
Sample Response:
On success:
{
"success": true,
"data": {
"content": [
{
"id": "61dd1da8db654e41881b5281",
"internal": "lastName",
"external": "sn",
"mandatory": false,
"script": null,
"createdDateTime": "2022-01-11T06:03:20.202",
"updatedDateTime": "2022-01-11T06:03:20.202",
"version": 0,
"default_val": "",
"tenant_applicationId": "61dd1da8db654e41881b5273",
"object_type": "USER",
"isCustom": false,
"scriptEnable": false
}
],
"pageable": {
"sort": [
{
"direction": "DESC",
"property": "internal",
"ignoreCase": false,
"nullHandling": "NATIVE",
"ascending": false,
"descending": true
}
],
"pageNumber": 0,
"pageSize": 10,
"offset": 0,
"paged": true,
"unpaged": false
},
"last": true,
"totalPages": 1,
"totalElements": 1,
"first": true,
"sort": [
{
"direction": "DESC",
"property": "internal",
"ignoreCase": false,
"nullHandling": "NATIVE",
"ascending": false,
"descending": true
}
],
"numberOfElements": 1,
"size": 10,
"number": 0,
"empty": false
},
"timestamp": "03-Mar-2022 07:13:09",
"message": null,
"errorCode": null
}
Purpose: This API is used to get paginated lists with filters.
URL: https://<tenant_domain>/selfservice/api/selfservice/applications
Method: POST
Example Request:
Sample Response:
On success:
{
"success": true,
"data": {
"offset": 0,
"pageSize": 16,
"totalElements": 5,
"totalPages": 1,
"elements": [
{
"endDate": null,
"deprovNotification": false,
"enabled": true,
"tagLine": "Directory service developed by Microsoft",
"id": "617253cc2fb4b2125b237b75",
"name": "Active Directory",
"appUrl": "",
"icon": "iVBORw0KGgoAAAANSUhEUgAAALoAAAC6CAYAAAAZDlfxAAAACXBIWXMAAAsSAAALEgHS3X78AAAgAElEQVR4nO2dCXQU17nnv1tb.....truncated"
}
],
"pageNumber": 0,
"sort": {
"orders": [
{
"direction": "ASC",
"property": "NAME"
}
],
"sorted": true
}
},
"timestamp": "03-Mar-2022 05:41:09",
"message": null,
"errorCode": null
}
Purpose: This API is used to get list of selfservice dashboard new Joiner list of logged in users.
URL: http://<tenant_url>/usersrvc/api/user/getSubOrdinates
Method: POST
Example Request: Need to pass filter as createdFrom and createdTo date time difference for seven day.
Sample Response:
On success:
{
"success": true,
"data": {
"content": [
{
"login": "nilesh",
"displayName": "Nilesh Dhepe",
"userId": "61e947c37dce7c5e40134f1f",
"profilePic": null,
"qualitativeRisk": null,
"sodViolations": null
},
{
"login": "workflow.one",
"displayName": "Test Workflow",
"userId": "61ee658de3a8361263cab0d1",
"profilePic": null,
"qualitativeRisk": null,
"sodViolations": null
},
{
"login": "workflow.two",
"displayName": "Test Workflow",
"userId": "61f7b3b50d84c22f79e1debd",
"profilePic": null,
"qualitativeRisk": null,
"sodViolations": null
},
{
"login": "mrunal",
"displayName": "Mrunal Chaple",
"userId": "61f8cda757a8e27934066a91",
"profilePic": null,
"qualitativeRisk": null,
"sodViolations": null
},
{
"login": "manoj.b",
"displayName": "Manoj Barapatre",
"userId": "61f8d81883126a511188e2ae",
"profilePic": null,
"qualitativeRisk": null,
"sodViolations": null
},
{
"login": "man.ba",
"displayName": "Manoj Bara",
"userId": "61f9160ed9800d4dbbc1baed",
"profilePic": null,
"qualitativeRisk": null,
"sodViolations": null
}
],
"pageable": {
"sort": [
{
"direction": "ASC",
"property": "id",
"ignoreCase": false,
"nullHandling": "NATIVE",
"ascending": true,
"descending": false
}
],
"pageNumber": 0,
"pageSize": 10,
"offset": 0,
"paged": true,
"unpaged": false
},
"last": true,
"totalElements": 6,
"totalPages": 1,
"first": true,
"number": 0,
"sort": [
{
"direction": "ASC",
"property": "id",
"ignoreCase": false,
"nullHandling": "NATIVE",
"ascending": true,
"descending": false
}
],
"numberOfElements": 6,
"size": 10,
"empty": false
},
"timestamp": "04-Mar-2022 10:39:22",
"message": null,
"errorCode": null
}
On failure:
Response 1#
{
"success": true,
"data": null,
"timestamp": "04-Mar-2022 10:39:22",
"message": null,
"errorCode": null
}
Purpose: This API is used to get count of onboard application config incomplete.
URL: http://<tenant_url>/provsrvc/applicationTenant/getApplicationIncompleteConfig
Method: GET
Example Request:
Sample Response:
On success{
"success": true,
"data": 3,
"timestamp": "07-Mar-2022 08:11:48",
"message": null,
"errorCode": null
}
On failure:
Response 1#
{
"success": true,
"data": 0,
"timestamp": "04-Mar-2022 10:39:22",
"message": null,
"errorCode": null
}
Purpose: This API is used to get count of application, admin and user.
URL: http://<tenant_url>/usersrvc/api/user/getOnboardCount
Method: GET
Example Request:
Sample Response:
On success:
{
"success": true,
"data": {
"appCount": 9,
"adminCount": 1,
"userCount": 25
},
"timestamp": "07-Mar-2022 08:11:27",
"message": null,
"errorCode": null
}
On failure:
Response 1#
{
"success": true,
"data": {
"appCount": 0,
"adminCount": 0,
"userCount": 0
},
"timestamp": "07-Mar-2022 08:11:27",
"message": null,
"errorCode": null
}
Purpose: This API is used to get the count of application,role,rule,workflow,password policy,active user,total user and unlogged user.
URL:https://<tenant_url>/usersrvc/api/user/getSystemKPICount
Method: GET
Example Request:
Sample Response:
On success:
{
"success": true,
"data": {
"appCount": 80,
"roleCount": 5,
"activeUserCount": 128,
"totalUserCount": 131,
"unloggedUserCount": 106,
"passwordPolicyCount": 2,
"workflowCount": 3,
"ruleCount": 6
},
"timestamp": "11-Mar-2022 12:42:30",
"message": null,
"errorCode": null
}
On failure:
Response 1#
{
"success": true,
"data": {
"appCount": 0,
"roleCount": 0,
"activeUserCount": 0,
"totalUserCount": 0,
"unloggedUserCount": 0,
"passwordPolicyCount": 0,
"workflowCount": 0,
"ruleCount": 0
},
"timestamp": "11-Mar-2022 12:42:30",
"message": null,
"errorCode": null
}
Purpose: This API is used to get count of requests, claims and my requests.
URL: https://<tenant_url>/workflowsrvc/api/workflowtaskassignment/user/request/claims/count
Method: GET
Example Request:
Sample Response:
On success:
{
"success": true,
"data": {
"requestCount": 12,
"clamisCount": 6,
"requestorCount": 0
},
"timestamp": "10-Mar-2022 07:07:48",
"message": null,
"errorCode": null
}
On failure:
Response 1#
{
"success": true,
"data": {
"requestCount": 0,
"clamisCount": 0,
"requestorCount": 0
},
"timestamp": "04-Mar-2022 10:39:22",
"message": null,
"errorCode": null
}
Purpose: This API is used to search application assigned to user.
URL: https://<tenant_url>/usersrvc/api/user/listApplications
Method: POST
Example Request:
Sample Response:
On success:
{
"success": true,
"data": {
"offset": 0,
"pageSize": 12,
"totalElements": 1,
"totalPages": 1,
"elements": [
{
"appId": "6226051994c38e414989eccd",
"appName": "ServiceNow",
"tagLine": "Workflow Automation Platform",
"status": "",
"appType": "GROUP",
"groupId": "61dea46ef515150ebe517b0d",
"endDate": null,
"provisionEnable": true,
"assignRoles": null
}
],
"pageNumber": 0,
"sort": null
},
"timestamp": "11-Mar-2022 01:06:33",
"message": null,
"errorCode": null
}
Purpose: This API is used to get assigned and unassigned application.
URL: https://<tenant_url>/provsrvc/applicationTenant/applicationListByPage
Method: POST
Example Request:
Sample Response:
On success:
{
"success": true,
"data": {
"content": [
{
"id": "61dbfdf6b30690468b0d4a79",
"appName": "Google Workplace",
"icon": null,
"tagLine": "Integrated Collaboration & Productivity Apps from Google",
"status": "ACTIVE",
"provisionEnable": false,
"ssoEnable": true,
"assigned": true
},
{
"id": "61dd1da8db654e41881b5273",
"appName": "Active Directory",
"icon": null,
"tagLine": "Directory service developed by Microsoft",
"status": "ACTIVE",
"provisionEnable": true,
"ssoEnable": false,
"assigned": true
},
{
"id": "6225f81edd7111640e094f8d",
"appName": "Google Workplace5",
"icon": null,
"tagLine": "Integrated Collaboration & Productivity Apps from Google",
"status": "ACTIVE",
"provisionEnable": true,
"ssoEnable": false,
"assigned": true
}
],
"pageable": {
"sort": [
{
"direction": "DESC",
"property": "displayName",
"ignoreCase": false,
"nullHandling": "NATIVE",
"ascending": false,
"descending": true
}
],
"pageNumber": 0,
"pageSize": 10,
"offset": 0,
"paged": true,
"unpaged": false
},
"totalPages": 2,
"totalElements": 12,
"last": false,
"first": true,
"sort": [
{
"direction": "DESC",
"property": "displayName",
"ignoreCase": false,
"nullHandling": "NATIVE",
"ascending": false,
"descending": true
}
],
"numberOfElements": 10,
"size": 10,
"number": 0,
"empty": false
},
"timestamp": "11-Mar-2022 02:10:38",
"message": null,
"errorCode": null
}
Purpose: This API is used to get list of application of user with there expiry days
URL: https://<tenant_url>/selfservice/api/selfservice/applicationswithexpiry
Method: POST
Example Request:
Sample Response:
On success:
{
"success": true,
"data": {
"offset": 0,
"pageSize": 10,
"totalElements": 3,
"totalPages": 1,
"elements": [
{
"id": "62220c747dab08061e00ba7b",
"name": "Active Directory",
"icon": "iVBORw0KGgoAAAANSUhEUgAAALoAAAC6CAYAAAAZDlfxAAAACXBIWXMAAAsSAAALEgHS3X78AAAgAElEQVR4nO2dCXQU17nnv1tb71q7BUJIzW7Jxo5N6zlOsPD2COBlEsnbiZFf,
"period": 20,
"tagLine": "Directory service developed by Microsoft"
},
{
"id": "62260e904f6c552b8b489c20",
"name": "Google Workplace",
"icon": "iVBORw0KGgoAAAANSUhEUgAAALoAAAC6CAIAAACWbMCmAAAACXBIWXMAAAsSAAALEgHS3X78AAAgAElEQVR4nO2dd3wURf/Ht1xLcnfpvUB6uRRSKFKl9w6C+KgPj2B57D6gD/o8iOVBEaQIiCiIgoBKNSAgVXoPISG910u5S0+u7/xed3vZ27vsXW6T4A+fZ97/ZLM7uzs7+9mZ73xn5nsoAACBQOwDg+UEsR8oFwgLoFwgLIBygbAAygXCAigXCAugXCAsgHKBsADKBcICKBcIC6BcICyAcoGwAMoFwgIoFwgLoFwgLIBygbAAygXCAigXCAugXCAsgHKBsADKBcICKBcIC6BcICyAcoGwAMoFwgIoFwgLoFwgLIBygbAAygXCAigXCAugXCAsgHKBsADKBcICKBcIC6BcICyAcoGwAMoFwgIoFwgLoFwgLIBygbAAygXYQGUC4QFUC4QFkC5QFgA5QKxFwRB/g+Z9ki2AOTkrgAAAABJRU5ErkJggg==",
"period": 5,
"tagLine": "Integrated Collaboration & Productivity Apps from Google"
},
{
"id": "62260e994f6c552b8b489c28",
"name": "PowerShell",
"icon": "iVBORw0KGgoAAAANSUhEUgAAALoAAAC6CAYAAAAZDlfxAT/gAAAABJRU5ErkJggg==",
"period": 4,
"tagLine": "Command-line Shell from Microsoft"
}
],
"pageNumber": 0,
"sort": {
"orders": [
{
"direction": "DESC",
"property": "plannedStart"
}
],
"sorted": true
}
},
"timestamp": "11-Mar-2022 01:42:30",
"message": null,
"errorCode": null
}
Purpose: This API is used to validate password against password policy
URL: https://<tenant_url>/authsrvc/passwordPolicy/pub/validate
Method: POST
Example Request:
Sample Response:
On success:
{"success":true,"data":null,"timestamp":"11-Mar-2022 01:40:38","message":null,"errorCode":null}
On failure:
Response 1#
{"success":false,"data":null,"timestamp":"11-Mar-2022 01:39:40","message":null,"errorCode":"AUTHSRVC.PASSWORD_COMPOSITION_RULE_VIOLATION"}
Purpose: This API is used to get count of application
URL: http://<tenant_url>/api/selfservice/newApplicationsCount
Method: GET
Example Request:
Sample Response:
On success:
{"success": true,"data": 1,"timestamp": "11-Mar-2022 02:13:39","message": null,"errorCode": null}
Purpose: This API is used to get list of campaign
URL: https://<tenant_url>/igsrvc/api/ig/campaign/execution/history/list-summary/reviewer
Method: POST
Example Request:
Sample Response:
On success:
{
"data": {
"content": [
{
"executionId": "61a865c69c60c83eb2d2cf0e",
"name": "Campaign For Bug_w8z89q",
"description": "",
"campaignId": "61a8657c9c60c83eb2d2cf0c",
"revision": 1,
"iteration": 1,
"status": "COMPLETED",
"remarks": "",
"startMode": "MANUAL",
"startDate": "2021-12-02",
"endMode": "MANUAL",
"endDate": "2021-12-02",
"plannedEnd": "2021-12-05",
"totalAssignments": 41,
"pendingAssignments": 41,
"approvedAssignments": 0,
"rejectedAssignments": 0
},
{
"executionId": "6225c00ab21ac3024d5a1d91",
"name": "Campaign For Bug_w8z89q",
"description": "",
"campaignId": "61a8657c9c60c83eb2d2cf0c",
"revision": 1,
"iteration": 2,
"status": "COMPLETED",
"remarks": "",
"startMode": "MANUAL",
"startDate": "2022-03-07",
"endMode": "AUTO",
"endDate": "2022-03-10",
"plannedEnd": "2022-03-10",
"totalAssignments": 40,
"pendingAssignments": 40,
"approvedAssignments": 0,
"rejectedAssignments": 0
}
],
"pageable": {
"sort": [
{
"direction": "ASC",
"property": "startDate",
"ignoreCase": false,
"nullHandling": "NATIVE",
"ascending": true,
"descending": false
}
],
"pageNumber": 0,
"pageSize": 10,
"offset": 0,
"paged": true,
"unpaged": false
},
"totalPages": 1,
"totalElements": 2,
"last": true,
"first": true,
"sort": [
{
"direction": "ASC",
"property": "startDate",
"ignoreCase": false,
"nullHandling": "NATIVE",
"ascending": true,
"descending": false
}
],
"numberOfElements": 2,
"size": 10,
"number": 0,
"empty": false
},
"errorCode": null,
"message": null,
"success": true,
"timestamp": "11-Mar-2022 02:38:11"
}
403
Forbidden
404
Not Found
Update API
200
OK
500
Internal Server Error
401
Unauthorized
403
Forbidden
404
Not Found
curl --location --request POST 'http://api.cymmetri.in/usersrvc/api/user/listByApplication' \
--header 'Content-Type: application/json' \
--header 'Authorization: Bearer eyJhbGciOiJIUzI1NiJ9.eyJzdWIiOiJhZG1pbiIsImRlbGVnYXRlZSI6bnVsbCwiZGVsZWdhdGVlSWQiOm51bGwsImZpcnN0TG9naW4iOmZhbHNlLCJyb2xlcyI6WyJPUkdfQURNSU4iLCJVU0VSIl0sInRlbmFudElkIjoiZ2s0MCIsImV4cCI6MTY0NzAxNzEwNywidXNlcklkIjoiNjE3MDE1YTNjMDQ4MTc1NmI3OThhY2EyIiwiaWF0IjoxNjQ3MDExMTA3fQ.8j711_L--eQHHfen2GPI1qWCmUWRd4n6O44HCZhuRSo' \
--data-raw '{
"keyword":"shu",
"pageNumber": "0",
"pageSize": "10",
"filter": {
"applicationId": "617253cc2fb4b2125b237b75"
},
"sortDirection": "ASC",
"sortOn": [
"id"
]
}'
curl --location --request POST 'http://localhost:9080/api/group/groupListByApplication' \
--header 'Tenant: gk16'
--data-raw '{
"filter": {
"applicationId": "617253cc2fb4b2125b237b75"
},
"keyword": "gold",
"pageNumber": 0,
"pageSize": 10,
"sortDirection": "ASC",
"sortOn": [
"name"
]
}'
curl --location --request POST 'https://mru18.cymmetri.in/provsrvc/reconciliation/pull/search' \
--header 'Tenant: mru18' \
--data-raw '{
"filter": {
"applicationId": "614b5d3489ad96554e89e2ab"
},
"keyword": "",
"pageNumber": 0,
"pageSize": 10,
"sortDirection": "DESC",
"sortOn": [
"updatedDateTime"
]
}'
curl --location --request POST 'https://mru18.cymmetri.in/provsrvc/reconciliation/pull/search' \
--header 'Tenant: mru18' \
--data-raw '{
"filter": {
"applicationId": "614b5d3489ad96554e89e2ab"
},
"keyword": "",
"pageNumber": 0,
"pageSize": 10,
"sortDirection": "DESC",
"sortOn": [
"updatedDateTime"
]
}'
curl --location --request POST 'https://mru18.cymmetri.in/provsrvc/applicationRole/findAppRolesByApplicationId' \
--header 'Tenant: mru18' \
--data-raw '{
"filter": {
"active": true,
"applicationId": "614b5d3489ad96554e89e2ab"
},
"keyword": "",
"pageNumber": 0,
"pageSize": 10,
"sortDirection": "ASC",
"sortOn": [
"id"
]
}'
curl --location --request POST 'api.cymmetri.in/provsrvc/policyMapTenant/findAll' \
--data-raw '{
"keyword": "lastName",
"pageNumber": 0,
"pageSize": 10,
"filter": {
"tenantApplicationId": "61dd1da8db654e41881b5273",
"objectType": "USER"
},
"sortDirection": "DESC",
"sortOn": [
"internal"
]
}'
curl --location --request POST 'https://gk40.cymmetri.in/selfservice/api/selfservice/applications' \
--header 'Connection: keep-alive' \
--header 'Pragma: no-cache' \
--header 'Cache-Control: no-cache' \
--header 'sec-ch-ua: " Not A;Brand";v="99", "Chromium";v="96", "Google Chrome";v="96"' \
--header 'Accept: application/json' \
--header 'content-type: application/json' \
--header 'Authorization: Bearer eyJhbGciOiJIUzI1NiJ9.eyJzdWIiOiJhZG1pbiIsImRlbGVnYXRlZSI6bnVsbCwiZGVsZWdhdGVlSWQiOm51bGwsImZpcnN0TG9naW4iOmZhbHNlLCJyb2xlcyI6WyJPUkdfQURNSU4iLCJVU0VSIl0sInRlbmFudElkIjoiZ2s0MCIsImV4cCI6MTY0NzAxNDY2NywidXNlcklkIjoiNjE3MDE1YTNjMDQ4MTc1NmI3OThhY2EyIiwiaWF0IjoxNjQ3MDA4NjY3fQ.jP2BgjiOVUcdxhImVvdwy18puEylWSSOVHnWA_2hhJU' \
--header 'sec-ch-ua-mobile: ?0' \
--header 'User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/96.0.4664.45 Safari/537.36' \
--header 'sec-ch-ua-platform: "Linux"' \
--header 'Origin: https://gk40.cymmetri.in' \
--header 'Sec-Fetch-Site: same-origin' \
--header 'Sec-Fetch-Mode: cors' \
--header 'Sec-Fetch-Dest: empty' \
--header 'Referer: https://gk40.cymmetri.in/' \
--header 'Accept-Language: en-GB,en-US;q=0.9,en;q=0.8' \
--header 'Cookie: deviceId=6e4caedd-beaf-444c-9312-21b219bb3709; Correlation=B194B86832FB4683ABC43EA6077944E2; Correlation=1E83B306404E4E46A2F6BE7D5A79C3BC; RefreshToken=fc6b1bcc-1c00-4663-b6ef-441051fb2e57; sessionId=75bdbb27-cf85-4102-9ba7-0cc5a84f8fb4' \
--data-raw '{
"direction": "ASC",
"keyword": "",
"pageNumber": 0,
"pageSize": 16,
"sort": "NAME"
}'
curl --location --request POST 'http://api.cymmetri.in/usersrvc/api/user/getSubOrdinates' \
--header 'Content-Type: application/json' \
--header 'Tenant: gk17' \
--header 'UserId: 61e81227aa505f4393b93405' \
--data-raw '{
"filter": {
"createdFrom": "2022-01-04T10:26:56.030Z",
"createdTo": "2022-03-04T10:26:56.030Z"
},
"keyword": "",
"pageNumber": 0,
"pageSize": 10,
"sortDirection": "ASC",
"sortOn": [
"id"
]
}'
curl --location --request GET 'http://api.cymmetri.in/provsrvc/applicationTenant/getApplicationIncompleteConfigCount' \
--header 'Tenant: gk17' \
--header 'Authorization: Bearer eyJhbGciOiJIUzI1NiJ9.eyJzdWIiOiJnazE3IiwiZGVsZWdhdGVlIjpudWxsLCJkZWxlZ2F0ZWVJZCI6bnVsbCwiZmlyc3RMb2dpbiI6ZmFsc2UsInJvbGVzIjpbIk9SR19BRE1JTiIsIlVTRVIiXSwidGVuYW50SWQiOiJnazE3IiwiZXhwIjoxNjQ2NjQ2NjQ0LCJ1c2VySWQiOiI2MWU4MTIyN2FhNTA1ZjQzOTNiOTM0MDUiLCJpYXQiOjE2NDY2NDA2NDR9.snwC7XVRWM5S-gCP53fXXObh9aROFtZDtfOXQCUDPps'
curl --location --request GET 'http://api.cymmetri.in/usersrvc/api/user/getOnboardCount' \
--header 'Content-Type: application/json' \
--header 'Tenant: n23' \
--header 'UserId: 6176c0b33c79f20dde6fd732' \
--header 'Authorization: Bearer eyJhbGciOiJIUzI1NiJ9.eyJzdWIiOiJnazE3IiwiZGVsZWdhdGVlIjpudWxsLCJkZWxlZ2F0ZWVJZCI6bnVsbCwiZmlyc3RMb2dpbiI6ZmFsc2UsInJvbGVzIjpbIk9SR19BRE1JTiIsIlVTRVIiXSwidGVuYW50SWQiOiJnazE3IiwiZXhwIjoxNjQ2NjQ2NjQ0LCJ1c2VySWQiOiI2MWU4MTIyN2FhNTA1ZjQzOTNiOTM0MDUiLCJpYXQiOjE2NDY2NDA2NDR9.snwC7XVRWM5S-gCP53fXXObh9aROFtZDtfOXQCUDPps'
curl --location --request GET 'https://macos.cymmetri.in/usersrvc/api/user/getSystemKPICount' \
--header 'Accept: application/json' \
--header 'Authorization: Bearer eyJhbGciOiJIUzI1NiJ9.eyJzdWIiOiJhZG1pbiIsImRlbGVnYXRlZSI6bnVsbCwiZGVsZWdhdGVlSWQiOm51bGwsImZpcnN0TG9naW4iOmZhbHNlLCJyb2xlcyI6WyJPUkdfQURNSU4iLCJVU0VSIl0sInRlbmFudElkIjoibWFjb3MiLCJleHAiOjE2NDcwMDg1MjUsInVzZXJJZCI6IjYxN2Y4YmIxZDE5MDViNjcyYzQ3N2QzMiIsImlhdCI6MTY0NzAwMjUyNX0.JzhcbfcQXxZoCYH5Mi_HmRCHZf_FVIr3OYrewl7vkjc'
curl --location --request GET 'https://gk40.cymmetri.in/workflowsrvc/api/workflowtaskassignment/user/request/claims/count' \
--header 'Tenant: gk40' \
--header 'Authorization: Bearer eyJhbGciOiJIUzI1NiJ9.eyJzdWIiOiJtcnUxOCIsImRlbGVnYXRlZSI6bnVsbCwiZGVsZWdhdGVlSWQiOm51bGwsImZpcnN0TG9naW4iOmZhbHNlLCJyb2xlcyI6WyJPUkdfQURNSU4iLCJVU0VSIl0sInRlbmFudElkIjoibXJ1MTgiLCJleHAiOjE2NDY2NzE2MTYsInVzZXJJZCI6IjYxNGI1Yjc1ODVmODU0NGYxY2RkOTcxNSIsImlhdCI6MTY0NjY2NTYxNn0.bViQdrikfQD1xdI6Waf_Sk6LOYQh-ilHVq4dMYfVt3E'
curl --location --request POST 'https://s3.cymmetri.in/usersrvc/api/user/listApplications' \
--data-raw '{
"pageNumber": 0,
"pageSize": 20,
"userId": "61d7f610dd92d761faa278f2",
"appName":"service"
}'
curl --location --request POST 'https://s3.cymmetri.in/provsrvc/applicationTenant/applicationListByPage' \
--data-raw '{
"displayName": "",
"order": "DESC",
"pageNo": 0,
"size": 10,
"sortBy": "displayName",
"tag": "",
"userId":"61d7f610dd92d761faa278f2"
}'
curl --location --request POST 'https://as100.cymmetri.in/selfservice/api/selfservice/applicationswithexpiry' \ --header 'Connection: keep-alive' \ --header 'Pragma: no-cache' \ --header 'Cache-Control: no-cache' \ --header 'sec-ch-ua: "Google Chrome";v="93", " Not;A Brand";v="99", "Chromium";v="93"' \ --header 'Accept: application/json' \ --header 'content-type: application/json' \ --header 'Authorization: Bearer eyJhbGciOiJIUzI1NiJ9.eyJzdWIiOiJhZG1pbiIsImRlbGVnYXRlZSI6bnVsbCwiZGVsZWdhdGVlSWQiOm51bGwsImZpcnN0TG9naW4iOmZhbHNlLCJyb2xlcyI6WyJPUkdfQURNSU4iLCJVU0VSIl0sInRlbmFudElkIjoiYXMxMDAiLCJleHAiOjE2NDcwMDk4NzgsInVzZXJJZCI6IjYyMTRkYjdiZDY2MWE1NzM4NmE3MWYxMCIsImlhdCI6MTY0NzAwMzg3OH0.LKZci0Yqeoyn4RHUIyYBFq7O5ATeDuCerZ0QdJ243gY' \ --header 'sec-ch-ua-mobile: ?0' \ --header 'User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/93.0.4577.63 Safari/537.36' \ --header 'sec-ch-ua-platform: "Linux"' \ --header 'Origin: https://as100.cymmetri.in' \ --header 'Sec-Fetch-Site: same-origin' \ --header 'Sec-Fetch-Mode: cors' \ --header 'Sec-Fetch-Dest: empty' \ --header 'Referer: https://as100.cymmetri.in/' \ --header 'Accept-Language: en-GB,en-US;q=0.9,en;q=0.8' \ --header 'Cookie: deviceId=48ba110c-c93c-45ac-92dc-3c6e04e74473; app_73e5c5f8-276b-47bb-a6a5-b6f82a779d79=e689a8da-faa7-46f5-9c7a-2800abdd206a; Correlation=C43A4277E7AB46178F0000BE4DD72F0C; RefreshToken=1ac7eea6-28a6-4bb8-997f-d7381a3dd7d1; sessionId=3417319f-789a-4849-8faa-bf180f4bec14; device=cf7bbf2a-161c-11ec-b3ec-39287c680726' \ --data-raw '{ "keyword": "", "pageNumber": 0, "pageSize": 10, "filter": {}, "sortDirection": "DESC", "sortOn": [ "plannedStart" ] }'
curl 'https://as100.cymmetri.in/authsrvc/passwordPolicy/pub/validate' \
-H 'Connection: keep-alive' \
-H 'Pragma: no-cache' \
-H 'Cache-Control: no-cache' \
-H 'sec-ch-ua: "Google Chrome";v="93", " Not;A Brand";v="99", "Chromium";v="93"' \
-H 'content-type: application/json' \
-H 'sec-ch-ua-mobile: ?0' \
-H 'User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/93.0.4577.63 Safari/537.36' \
-H 'tenant: as100' \
-H 'sec-ch-ua-platform: "Linux"' \
-H 'Accept: */*' \
-H 'Origin: https://as100.cymmetri.in' \
-H 'Sec-Fetch-Site: same-origin' \
-H 'Sec-Fetch-Mode: cors' \
-H 'Sec-Fetch-Dest: empty' \
-H 'Referer: https://as100.cymmetri.in/' \
-H 'Accept-Language: en-GB,en-US;q=0.9,en;q=0.8' \
-H 'Cookie: deviceId=fa83c4b1-7c85-467d-9b46-ffbc70efad97; Correlation=9928D5133AED419CBC01591B56483953; app_73e5c5f8-276b-47bb-a6a5-b6f82a779d79=e689a8da-faa7-46f5-9c7a-2800abdd206a; device=cf7bbf2a-161c-11ec-b3ec-39287c680726' \
--data-raw '{"password":"U2FsdGVkX191zbRQpSQz+rdxyAacEqD1G5Mx5wKtPV5ElwKZu7/TFHFLuCNH+v63G8k7sTFDa5gNYG9SQ+0ix4eZdTvLcJbELGm2yjUWjx2a6jH3JnP/USl2efCC9nDvufmqUhSbIPA0Nc1PZUqM+PPk+TpCFSoKtKwBPWeBa/LYjlYt11u++aTuVGsd/rOaWJxqINPRHIk6Ax89LfhM8+H6VKc4+ybfearoCJgHWCPE/X566hiYZJEKcMGe7u0OpUzGUMlyguBtfYlWlT7tcdP6x/rXlqs8vNTLk/HboYLv10UkB0ifsQ64c7fSQ/ofZKjQlqehpP4+SzIi4OiqRQikP9MOkKZWl9YJdGXZs+mUuzfEs9UGINMYBk1hSCq6xGb9mfE0vyFeVAyY/6oGgQ==","login":"totp","userId":"6214def0a251e06721ed8594"}' \
--compressed
curl --location --request GET 'http://localhost:8080/api/selfservice/newApplicationsCount' \
--header 'Connection: keep-alive' \
--header 'Pragma: no-cache' \
--header 'Cache-Control: no-cache' \
--header 'sec-ch-ua: " Not A;Brand";v="99", "Chromium";v="99", "Google Chrome";v="99"' \
--header 'Accept: application/json' \
--header 'content-type: application/json' \
--header 'Authorization: Bearer eyJhbGciOiJIUzI1NiJ9.eyJzdWIiOiJhZG1pbiIsImRlbGVnYXRlZSI6bnVsbCwiZGVsZWdhdGVlSWQiOm51bGwsImZpcnN0TG9naW4iOmZhbHNlLCJyb2xlcyI6WyJPUkdfQURNSU4iLCJVU0VSIl0sInRlbmFudElkIjoiZ2s0MCIsImV4cCI6MTY0Njc0OTkzMiwidXNlcklkIjoiNjE3MDE1YTNjMDQ4MTc1NmI3OThhY2EyIiwiaWF0IjoxNjQ2NzQzOTMyfQ.puFKgrNoHZtRl6P4LxzFd9KQM_-EB-45DqqP4zywws8' \
--header 'sec-ch-ua-mobile: ?0' \
--header 'User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/99.0.4844.51 Safari/537.36' \
--header 'sec-ch-ua-platform: "Linux"' \
--header 'Sec-Fetch-Site: same-origin' \
--header 'Sec-Fetch-Mode: cors' \
--header 'Sec-Fetch-Dest: empty' \
--header 'Referer: https://gk40.cymmetri.in/' \
--header 'Accept-Language: en-GB,en-US;q=0.9,en;q=0.8' \
--header 'Cookie: deviceId=6e4caedd-beaf-444c-9312-21b219bb3709; Correlation=B194B86832FB4683ABC43EA6077944E2; app_73e5c5f8-276b-47bb-a6a5-b6f82a779d79=e689a8da-faa7-46f5-9c7a-2800abdd206a; device=41b5bf50-9def-11ec-8665-953ee8af105c; Correlation=1B9449F921B043B9B513E99D253894CE; RefreshToken=b8ada8a1-d089-4a39-b3e1-72c04ce202fe; sessionId=130e95df-69a5-4462-a8b5-c04b53e97e64' \
--header 'Tenant: gk40' \
--header 'userId: 617015a3c0481756b798aca2'
curl --location --request POST 'https://gk40.cymmetri.in/igsrvc/api/ig/campaign/execution/history/list-summary/reviewer' \
--header 'Connection: keep-alive' \
--header 'Pragma: no-cache' \
--header 'Cache-Control: no-cache' \
--header 'sec-ch-ua: " Not A;Brand";v="99", "Chromium";v="99", "Google Chrome";v="99"' \
--header 'Accept: application/json' \
--header 'content-type: application/json' \
--header 'Authorization: Bearer eyJhbGciOiJIUzI1NiJ9.eyJzdWIiOiJhZG1pbiIsImRlbGVnYXRlZSI6bnVsbCwiZGVsZWdhdGVlSWQiOm51bGwsImZpcnN0TG9naW4iOmZhbHNlLCJyb2xlcyI6WyJPUkdfQURNSU4iLCJVU0VSIl0sInRlbmFudElkIjoiZ2s0MCIsImV4cCI6MTY0NzAxNDY2NywidXNlcklkIjoiNjE3MDE1YTNjMDQ4MTc1NmI3OThhY2EyIiwiaWF0IjoxNjQ3MDA4NjY3fQ.jP2BgjiOVUcdxhImVvdwy18puEylWSSOVHnWA_2hhJU' \
--header 'sec-ch-ua-mobile: ?0' \
--header 'User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/99.0.4844.51 Safari/537.36' \
--header 'sec-ch-ua-platform: "Linux"' \
--header 'Origin: https://gk40.cymmetri.in' \
--header 'Sec-Fetch-Site: same-origin' \
--header 'Sec-Fetch-Mode: cors' \
--header 'Sec-Fetch-Dest: empty' \
--header 'Referer: https://gk40.cymmetri.in/' \
--header 'Accept-Language: en-GB,en-US;q=0.9,en;q=0.8' \
--header 'Cookie: deviceId=6e4caedd-beaf-444c-9312-21b219bb3709; Correlation=B194B86832FB4683ABC43EA6077944E2; Correlation=C27A4466A21046309B58FD53AEF4A2C5; RefreshToken=4ec80313-bed3-44e5-9081-33eb9ba301f2; sessionId=32ceee83-781e-45d6-9c2c-2acc8741a944' \
--data-raw '{
"filter": {
"campaignName": "Campaign For"
},
"keyword": "",
"pageNumber": 0,
"pageSize": 10,
"sortDirection": "ASC",
"sortOn": [
"startDate"
]
}'
API
Status
Error Code
Message
Create API
200
OK
500
Internal Server Error
401
Unauthorized






A comprehensive list of all known Cymmetri error codes and their summary understanding:
CONNECTION_ERROR
Unable to connect. Please check your connection and try again.
USRSRVC.LAST_DATE_REACHED
The application's request end date is greater than the user's end date.
USRSRVC.MISSING_DATES
Incorrect dates Please ensure the selected date range is proper.
USRSRVC.EXPIRED_TIME_BOUND
Access request duration has ended
REGSRVC.UNKNOWN
Error. Please try again later or contact Cymmetri Administrator.
REGSRVC.USER_NOT_FOUND
User not found.
REGSRVC.INVALID_TOKEN
Token expired. Try again.
REGSRVC.OTP_EXPIRED
OTP expired. Please resend and try again.
REGSRVC.OTP_LIMIT_EXCEED
Otp limit exceeded.
REGSRVC.INVALID_OTP
OTP does not match. Please check & try again
REGSRVC.INVALID_ARGUMENTS
Error. Please correct input and try again.
REGSRVC.INVALID_DOMAIN
Invalid Domain. Please try again.
REGSRVC.INVALID_CREDENTIALS
Invalid Credentials. Please try again.
REGSRVC.TERMS_AND_CONDITIONS_NOT_FOUND
Invalid Terms & Conditions. Please try again.
REGSRVC.INVALID_ACCOUNT_VERIFICATION_TOKEN
Invalid request. Contact Cymmetri administrator.
REGSRVC.DATA_IS_NOT_VALID
Invalid data. Please try again.
REGSRVC.PASSWORD_NOT_VALID
Invalid password. Please try again
REGSRVC.EMAIL_EXISTS
Duplicate Email Address. Please try again.
REGSRVC.DOMAIN_EXISTS
Duplicate Domain.
REGSRVC.DB_CONFIG_EXISTS
Database already exists. Contact Cymmetri administrator.
REGSRVC.USER_ALREADY_ACTIVE
User status is active. Contact Cymmetri administrator.
USRSRVC.MANAGER_NOT_FOUND
No Manager Found
USRSRVC.UNSUPPORTED_FILE_TYPE
Unsupported File Type
USRSRVC.UNKNOWN
Error. Please try again later or contact Cymmetri Administrator.
USRSRVC.INVALID_ARGUMENTS
Error. Please correct input and try again.
USRSRVC.NONUNIQUE_GROUPNAME
Group name already exists. Please try again.
USRSRVC.GROUPTYPE_NOT_FOUND
Group type not found. Contact Cymmetri administrator.
USRSRVC.OU_NOT_FOUND
Organization Unit not found. Please try again.
USRSRVC.PARENTGROUP_NOT_FOUND
Parent Group not found. Please try again.
USRSRVC.GROUP_NOT_FOUND
Group not found. Please try again.
USRSRVC.USER_NOT_FOUND
User not found. Please try again.
USRSRVC.CYCLIC_UPDATE
Operation not allowed for current input.
USRSRVC.INHERITED_GROUP
Operation not allowed for current input.
USRSRVC.USERTYPE_NOT_FOUND
User type not found. Please try again.
USRSRVC.EXISTING_MOBILE
User mobile number in use. Please try again.
USRSRVC.EXISTING_EMAIL
User email address in use. Please try again.
USRSRVC.DEPARTMENT_NOT_FOUND
Department not found. Please try again.
USRSRVC.DESIGNATION_NOT_FOUND
Designation not found. Please try again.
USRSRVC.COUNTRY_NOT_FOUND
Country not found. Please try again.
USRSRVC.EXISTING_LOGIN
User Login ID in use. Please try again.
USRSRVC.APPLICATION_NOT_FOUND
Application not found. Please try again.
USRSRVC.APPLICATION_ROLE_NOT_FOUND
Application role not found. Please try again.
PROVSRVC.CYMMETRI_LOGIN_FIELD_NOT_CONFIGURED
Please configure Cymmetri Login field for Policy Mapping.
PROVSRVC.APPLICATION_TEST_FAILED
Provision Configuration failed.
USRSRVC.USER_NOT_PROVISIONED
User not provisioned. Please try again.
USRSRVC.CHILD_GROUP_FOUND
Cannot Delete as Child group found.
USRSRVC.GROUP_HAS_ASSIGNED_APPS
Group has assigned applications. Remove and try again.
USRSRVC.USER_ASSIGNED_GROUP
Cannot delete as User assigned to group.
USRSRVC.USER_MUST_PRESENT_IN_TARGET
User must present in target system before assign it to group.
USRSRVC.INACTIVE_USER
Inactive User cannot perform this action.
USRSRVC.INVALID_MANAGER
Invalid manager.
USRSRVC.MIN_ORG_ADMIN_RULE_VIOLATION
Admin role cannot be removed for this user.
USRSRVC.USER_ROLE_MAPPING_EXISTS
Role Already Exists.
USRSRVC.APPLICATION_ROLE_ALREADY_ASSIGNED
Application role is already assigned.
USRSRVC.APPLICATION_ALREADY_ASSIGNED
Application is already assigned.
USRSRVC.USER_ROLE_MAPPING_NOT_EXISTS
User role mapping does not exists.
USRSRVC.CANNOT_REMOVE_PROVISIONED_APPLICATION
Cannot remove already provisioned application.
USRSRVC.EMPTY_FILE
Empty file uploaded.
USRSRVC.SELF_STATUS_CHANGE_NOT_ALLOWED
This user cannot be deleted.
USRSRVC.MANAGER_ASSIGNMENT_REJECTED
Error. The manager assignment is invalid.
USRSRVC.INVALID_ENDDATE
The end date should be greater than start date.
USRSRVC.SELF_ROLE_CHANGE_NOT_ALLOWED
Self role change is not allowed.
USRSRVC.CUSTOM_ATTRIBUTE_MASTER_EXIST
Custom attribute already exist.
USRSRVC.CUSTOM_ATTRIBUTE_MASTER_NOT_FOUND
Custom attribute not found.
USRSRVC.DUPLICATE_NAME
Duplicate name record already exist.
USRSRVC.DUPLICATE_LABEL
Duplicate label record already exist.
USRSRVC.ATTRIBUTE_RIGHTS_NOT_FOUND
Attribute rights not found.
USRSRVC.REMOTE_GROUP_APPLICATION_NOT_FOUND
Application must present before assign user to remote group.
USRSRVC.REMOTE_GROUP_NAME_NOT_MODIFIED_EXCEPTION
Remote group name not able to update
USRSRVC.EMPTY_LOGIN
Something went wrong Please contact the administrator.
USRSRVC.TOO_LARGE_FILE
File size should not be more than {size}
USRSRVC.FORM_DEACTIVATED_EXCEPTION
Form is inactive
USRSRVC.ACTION_NOT_SUPPORTED
This action is not supported
AUTHSRVC.ACCESS_DENIED
Invalid Credentials.
AUTHSRVC.TENANT_EXPIRED
Free trial expired. Please contact Cymmetri administrator.
AUTHSRVC.UNKNOWN
Please contact system administrator.
AUTHSRVC.INVALID_TOKEN
Token is invalid.
AUTHSRVC.USER_NOT_FOUND
User not found.
AUTHSRVC.CANT_SET_FALSE_DEFAULT_PASSWORD_POLICY
Default password policy cannot be false.
AUTHSRVC.CONNECTION_FAILED
Connection failed.
AUTHSRVC.CANT_DELETE_DEFAULT_PASSWORD_POLICY
Cannot delete default password policy.
AUTHSRVC.INVALID_ARGUMENTS
Invalid argument.
AUTHSRVC.INVALID_AUTH_POLICY_CONFIG
Invalid auth policy config.
AUTHSRVC.ACCESS_DENIED_TOKEN
Session expired. Please login again
AUTHSRVC.ADAPTIVE_BLOCK_ACTION
Action blocked. Please contact administrator.
SESSION_EXPIRED
Session expired. Please refresh and try again
AUTHSRVC.NON_REMOVABLE_REFERENCED_ENTITY
Cannot modify IDP configuration till active under Authentication Policy.
AUTHSRVC.PASSWORD_POLICY_NAME_ALRAEDY_EXISTS
Password policy name already exists.
AUTHSRVC.PASSWORD_POLICY_CONDITION_ALRAEDY_EXISTS
Policy Conditions already exists.
AUTHSRVC.DEFAULT_POLICY_UPDATE_NOT_ALLOWED
Default password policy update not allowed.
AUTHSRVC.PASSWORD_COMPOSITION_RULE_VIOLATION
Password provided does not match the required guidelines.
AUTHSRVC.MOBILE_NOT_FOUND
Mobile number is not registered please contact Cymmetri Administrator.
AUTHSRVC.ALREADY_EXISTS
Name already exist. Please enter unique name.
AUTHSRVC.LDAP_ACCESS_DENIED
Access denied.
AUTHSRVC.CLIENT_EXISTS
API Client with same name already configured.
AUTHSRVC.USER_NOT_ACTIVE
Delegated user not active
AUTHSRVC.INVALID_AUTH_CONFIG
Invalid auth config
AUTHSRVC.PASSWORD_POLICY_NAME_ALREADY_EXISTS
Password policy name already exists.
AUTHSRVC.TRUST_DEVICE_MAX_DEVICE_EXCEPTION
Exceeded device trust max limit
AUTHSRVC.TRUST_DEVICE_EXPIRY_EXCEPTION
Exceeded expiration time for trust devices
AUTHSRVC.MULTIPLE_TRUST_DEVICE_CONFIG
Multiple trust device configuration found
AUTHSRVC.INVALID_GLOBAL_SESSION_CONFIGURATION
Invalid global auth configuration
AUTHSRVC.MULTI_SESSION_ACCESS_DENIED
Session(s) already in progress. Logout from all sessions to continue.
MFASRVC.UNKNOWN
Error. Please try again.
MFASRVC.USER_NOT_FOUND
User not found. Please try again.
MFASRVC.ALREADY_SENT_SMS_OTP
SMS OTP already sent.
MFASRVC.INVALID_SMS_OTP
Invalid SMS OTP provided.
MFASRVC.RESEND_COUNT_EXCEED
Allowed resend attempt exceed please try after some time
MFASRVC.PUSH_NOTIFICATION_FAILED
Failed to send the push notification. Please try again later or contact Cymmetri Administrator.
MFASRVC.MFA_CONFIG_NOT_FOUND
Multi Factor Authentication configuration not found.
MFASRVC.INVALID_ARGUMENTS
Error. Invalid request.
MFASRVC.QUESTION_NOT_FOUND
Question not found.
MFASRVC.DUPLICATE_QUESTION
Question field is duplicate. Please try again.
MFASRVC.INCORRECT_ANSWER
Answer field is incorrect. Please try again.
MFASRVC.INVALID_USERID
Invalid User. Please try again.
MFASRVC.INVALID_QUESTIONID
Question is invalid. Please try again.
MFASRVC.USER_NOT_REGISTERED
User is not registered for TOTP/Push Authentication
MFASRVC.EMPTY_QUESTION
Question field is empty. Please try again.
MFASRVC.FAILED_MINIMUM_CORRECT_ANSWER
Please provide correct answer for each question.
MFASRVC.INVALID_TOTP
Invalid Time based OTP provided.
MFASRVC.INVALID_ANSWER
Answer field is invalid. Please try again.
MFASRVC.QUESTION_NOT_REGISTERED
Question is not registered.
MFASRVC.NON_REMOVABLE_QUESTION
Question in use and cannot be removed.
MFASRVC.USER_RESPONSE_PENDING
User response is pending.
MFASRVC.USER_DENIED_ACCESS
User denied access.
MFASRVC.NOT_ABLE_TO_MODIFY
Not able to modify. Please try again
MFASRVC.INVALID_ANSWER_LENGTH
Invalid answer length
MFASRVC.DISPOSABLE_EMAIL
MFASRVC.FIREHOL_IP_REPUTATION
Ip reputation sync failed
MFASRVC.SYNC_PROCESS_RUNNING
Sync is in progress. Please wait
MFASRVC.IMPOSSIBLE_TRAVEL_NOT_FOUND
Config not found
MFASRVC.DEVICE_TRUST_NOT_FOUND
Config not found
MFASRVC.BLACKLISTED_LOCATION_NOT_FOUND
Config not found
MFASRVC.LOCATION_EMPTY
MFASRVC.BLACKLISTED_IP_NOT_FOUND
Blacklisted IP not found
MFASRVC.IP_ADDRESS_EMPTY
MFASRVC.MFA_NOT_FOUND
MFA not found
MFASRVC.INVALID_CONFIG
Invalid configuration
MFASRVC.SERVICE_NOT_SUPPORTED
MFASRVC.PLUGIN_REGISTRY_NOT_REGISTERED
MFASRVC.BLACKLISTED_IPADDRESS_CONFIG_NOT_FOUND
Config not found
MFASRVC.BLACKLISTED_LOCATION_CONFIG_NOT_FOUND
Config not found
MFASRVC.IMPOSSIBLE_TRAVEL_CONFIG_NOT_FOUND
Config not found
MFASRVC.BREACHED_PASSWORD_CONFIG_NOT_FOUND
Config not found
MFASRVC.COUNTRY_CODE_MISMATCH_CONFIG_NOT_FOUND
Config not found
MFASRVC.SHORT_LIVED_DOMAIN_CONFIG_NOT_FOUND
Config not found
MFASRVC.USER_BEHAVIOUR_CONFIG_NOT_FOUND
Config not found
MFASRVC.MULTIPLE_DEVICE_TRUST_FOUND
Multiple config found
MFASRVC.COMMON_CREDENTIAL_DOWNLOAD_FAILED
WKFLSRVC.UNKNOWN
Please contact system Administrator
WKFLSRVC.WORKFLOW_NOT_FOUND
No workflow available
WKFLSRVC.INVALID_ARGUMENTS
Please check input and try again.
WKFLSRVC.INVALID_LEVEL
Workflow Config issue
WKFLSRVC.EXCEEDED_REPORTING_MANAGER
Can not more than reporting manager
WKFLSRVC.WORKFLOW_SETUP_NOT_FOUND
No workflow config available
WKFLSRVC.REQUESTOR_NOT_FOUND
Requestor not found in the system.
WKFLSRVC.WORKFLOW_IN_PROGESS
Request is pending for approval.
WKFLSRVC.REPORTING_MANAGER_NOT_FOUND
Please assign approver's manager to complete workflow.
WKFLSRVC.LEVEL_NOT_IN_RANGE
Workflow level is not in range.
WKFLSRVC.WORKFLOW_SETUP_ALREADY_EXISTS
Workflow setup already exists.
WKFLSRVC.COMMON_REQ_ASSG_ID
Self-approval is not allowed Please contact the administrator for the reassignment.
WKFLSRVC.SAME_REQUESTOR_ASSIGNEE
Workflow cannot be assigned to same user.
WKFLSRVC.WORKFLOW_ALREADY_EXISTS
Workflow with same name already exists.
WKFLSRVC.DAYS_THRESHOLD_EXCEED_EXCEPTION
Max allowed TAT is {maxAllowedDays} days
WKFLSRVC.DELEGATE_COMMON_REQ_ASSG_ID
Approver and assignee can't be same.
WKFLSRVC.APPLICATION_DECOMMISSIONED
This application is decommissioned so the request can not be approved/rejected please refresh the page.
SSOCONFIGSRVC.UNKNOWN
Error. Please try again.
SSOCONFIGSRVC.SSO_CONFIG_NOT_FOUND
SSO config not found.
SSOCONFIGSRVC.SAML_CONFIG_NOT_FOUND
Saml config not found.
SSOCONFIGSRVC.OPENID_CLIENT_NOT_FOUND
OpenID config not found.
SSOCONFIGSRVC.DUPLICATE_OPENID_CLIENT_ID
Duplicate OpenID Client ID.
SSOCONFIGSRVC.API_CONFIG_NOT_FOUND
API config not found.
SSOCONFIGSRVC.INVALID_ARGUMENTS
Invalid Arguments.
SSOCONFIGSRVC.INVALID_CIDR
Not all CIDR are valid
SSOCONFIGSRVC.UNSUPPORTED_FILE_TYPE
Unsupported File Type
SSOCONFIGSRVC.ERROR_GENERATING_KEYS
Failed to generate keys.
SSOCONFIGSRVC.CERTIFICATE_PARSING_ERROR
Failed to read certificate. Please try again.
SSOCONFIGSRVC.ERROR_DEACTIVATING_KEYS
Failed to deactivate key. Please try again.
SSOCONFIGSRVC.KEY_GENERATION_FAILED
Failed to generate keys.
SSOCONFIGSRVC.METADATA_GENERATION_FAILED
Could not generate Metadata.
SSOCONFIGSRVC.ALRAEDY_EXISTS
Configuration for same Entity ID already exists.
SSOCONFIGSRVC.KEYS_CANNOT_BE_DISABLED
Key is being used in IDP or SP
SSOCONFIGSRVC.KEY_DOES_NOT_EXISTS
No related key found
SSOCONFIGSRVC.IDENTITY_PROVIDER_IS_DISABLED
Identity Provider is disabled
SSOCONFIGSRVC.DUPLICATE_POLICY_MAPPING
Policy mapping already exists
SSOCONFIGSRVC.USER_DOES_NOT_HAVE_ACCESS
User does not have access
SSOCONFIGSRVC.KEYS_IS_DISABLED
Keys Disabled
SSOCONFIGSRVC.IDENTITY_PROVIDER_DOES_NOT_EXISTS
Identity Provider does not exist
SSOCONFIGSRVC.IDENTITY_PROVIDER_KEY_IS_DISABLED
Identity Provider key disabled
SSOCONFIGSRVC.SERVICE_PROVIDER_IS_DISABLED
Service Provider disabled
SSOCONFIGSRVC.IDENTITY_PROVIDER_ALREADY_ENABLED
Identity Provider already enabled
SSOCONFIGSRVC.IDENTITY_PROVIDER_CANNOT_BE_DISABLED
Identity Provider can not be disabled
SSOCONFIGSRVC.KEYS_ALREADY_EXISTS
Keys already exists
SSOCONFIGSRVC.KEY_MINIMUM_EXPIRATION
Key Minimum expiration
SSOCONFIGSRVC.SERVICE_PROVIDER_ENABLED
Service provider enabled
SSOCONFIGSRVC.SERVICE_PROVIDER_DISABLED
Service provider disabled
SSOCONFIGSRVC.KEY_IS_BEING_USED
Key already used
SSOCONFIGSRVC.SERVICE_PROVIDER_CANNOT_BE_UPDATED
Service provider can not be updated
SSOCONFIGSRVC.SERVICE_PROVIDER_IS_BEING_USED
Service provider is being used
SSOCONFIGSRVC.INVALID_SAML_CONFIG
invalid saml configuration
SSOCONFIGSRVC.NOT_FOUND
SSO cofiguration not found
SSOCONFIGSRVC.CONNECTION_FAILED
SSO configuration connection failed
SSOCONFIGSRVC.FORBIDDEN
SSO configuration forbidden
SSOCONFIGSRVC.UNAUTHORIZED
SSO configuration unauthorized
SSOCONFIGSRVC.CERTIFICATE_EXPIRED
SSO configuration certificate is expired
SSOCONFIGSRVC.SAML_APP_CONFIG_NOT_FOUND
SSO configuration saml application configuration not found
SSOCONFIGSRVC.SAML_ATTR_CONFIG_NOT_FOUND
SSO configuration saml attribute configuration not found
SSOCONFIGSRVC.OPENID_SCOPE_NOT_FOUND
SSO configuration openid scope not found
SSOCONFIGSRVC.OPENID_CLAIM_NOT_FOUND
SSO configuration openid claim not found
SSOCONFIGSRVC.APPLICATION_NOT_FOUND
SSO configuration application not found
SSOCONFIGSRVC.DUPLICATE_POLICYATTRIBUTE
SSO configuration policy attribute is duplicate
SSOCONFIGSRVC.INVALID_POLICYATTRIBUTE_ID
SSO configuration policy attribute is invalid
SSOCONFIGSRVC.INAVLID_POLICYATTRIBUTE_APPLICATION
SSO configuration policy attribute application is invalid
SSOCONFIGSRVC.MANDATORY_ENTRY
SSO configuration policy field is mandatory
SSOCONFIGSRVC.INVALID_POLICY_MAP
SSO configuration policy map is invalid
SSOCONFIGSRVC.NO_MAPPING_FOUND
SSO configuration mapping is not found
SSOCONFIGSRVC.IDENTITY_PROVIDER_DOES_EXISTS
SSO configuration identity provider does not exist
SSOCONFIGSRVC.MULTIPLE_IDENTITY_PROVIDER_EXISTS
SSO configuration multiple identity provider exists
SSOCONFIGSRVC.SERVICE_PROVIDER_EXISTS
SSO configuration service provider already exists
SSOCONFIGSRVC.SERVICE_PROVIDER_DOES_NOT_EXISTS
Service provider does not exist
SSOCONFIGSRVC.DOMAIN_EXISTS
Domain doesn't exists
SAMLSRVC.KEY_DOES_NOT_EXISTS
Key doesn't exists
SAMLSRVC.INVALID_COOKIE
Invalid session. Re-login and try again
SAMLSRVC.IDENTITY_PROVIDER_IS_DISABLED
Identity Provider is disabled
SAMLSRVC.EXPIRED_TOKEN
Session Expired. Please re-login and try again
SAMLSRVC.KEYS_IS_DISABLED
Key is disabled
SAMLSRVC.KEYS_IS_EXPIRED
Key is expired
SAMLSRVC.KEYS_NOT_GENERATED
Public and private key is not generated
SAMLSRVC.SAML_TYPE_NOT_APPLICABLE
SAML type configured and SAML type received mismatched
SAMLSRVC.NAMEID_MISMATCH
SAML nameId configured and nameId received mismatched
SAMLSRVC.INVALID_SAML2_AUTHN_REQUEST_SIGNATURE
SAML authentication request signature is invalid
SAMLSRVC.ISSUE_INSTANT_MISMATCH
SAML authentication response is invalid with issue instant
SAMLSRVC.MESSAGE_REPLAY
SAML message is being sent again
SAMLSRVC.DESITNATION_MISMATCH
SAML destination configured and received mismatched
SAMLSRVC.VERSION_MISMATCH
SAML version does not match
SAMLSRVC.PROTOCOL_BINDING_MISMATCH
SAML protocol binding does not match
SAMLSRVC.REQUEST_ISSUER_URI_MISMATCH
SAML request issuer uri does not match
SAMLSRVC.ASSERTION_CONSUMER_SERVICE_URI_MISMATCH
SAML request assertion consumer service uri does not match
SAMLSRVC.INVALID_USER_SESSION
SAML user session is invalid
SAMLSRVC.USER_DOES_NOT_HAVE_ACCESS
User does not have access
SAMLSRVC.IDENTITY_PROVIDER_DOES_NOT_EXISTS
Identity Provider does not exist
SAMLSRVC.IDENTITY_PROVIDER_KEY_IS_DISABLED
Identity Provider key is disabled
SAMLSRVC.SERVICE_PROVIDER_IS_DISABLED
Service Provider is disabled
UTILSRVC.UNKNOWN
Error. Please try again.
UTILSRVC.INVALID_ARGUMENTS
Error. Please correct input and try again.
UTILSRVC.CONFIGURATION_EXIST
Hook already present.
UTILSRVC.ALREADY_EXISTS
Hook already present.
UTILSRVC.META_ATTRIBUTE_EXISTS
Name/Key or Value already exist.
UTILSRVC.MODULES_ENQUIRY_EXIST
Sales team is working on your request. We will get back to you soon.
UTILSRVC.LABEL_ALREADY_EXIST
Label Already Exists
UTILSRVC.EVENT_ALREADY_EXIST
Event Already Exists
UTILSRVC.BEHALF_CONFIG_NOT_FOUND
On Behalf configuration is not found.
UTILSRVC.MULTIPLE_BEHALF_CONFIG_FOUND
Multiple Behalf configurations found.
UTILSRVC.LENGTH_EXCEED_EXCEPTION
Length exceeded
UTILSRVC.SCRIPT_CUSTOM_ERROR-MOBILEALREADYEXIST
Mobile number already in use Try again with another number.
UTILSRVC.SCRIPT_CUSTOM_ERROR-EMAILALREADYEXIST
Email already in use Try again with another email.
USRSRVC.FORM_NOT_FOUND
Form not found
UTILSRVC.WEBHOOK_CALL_FAILED
Webhook test failed.
UTILSRVC.BATCH_TASK_EXECUTION_FAILED
Batch process execution failed.
UTILSRVC.BATCH_TASK_ALREADY_EXIST
Batch task already exists.
PROVSRVC.UNKNOWN
Error. Please try again later or contact Cymmetri Administrator.
PROVSRVC.USER_NOT_FOUND
User not found.
PROVSRVC.INVALID_ARGUMENTS
Error. Please correct input and try again.
PROVSRVC.APPLICATION_NOT_FOUND
Application not found. Please try again.
PROVSRVC.INVALID_USER_ACTION
User action not allowed. Please check configuration.
PROVSRVC.INVALID_GROUP_ACTION
Group action not allowed. Please check configuration.
PROVSRVC.INVALID_ROLE_ACTION
Role action not allowed. Please check configuration.
PROVSRVC.INAVLID_ACTION
Error. Please try again.
PROVSRVC.UID_NOT_FOUND
Record not found. Please try again.
PROVSRVC.Empty_Role_Id
Role not provided. Please try again.
PROVSRVC.Duplicate_GroupID
Duplicate Group association.
PROVSRVC.Invalid_GroupId
Invalid Group association.
PROVSRVC.CONNECTOR_NOT_FOUND
Connector not available. Please contact Cymmetri administrator.
PROVSRVC.UNSUPPORTED_OPERATION
Operation not supported.
PROVSRVC.APPLICATION_ALREADY_EXISTS
Application already exists.
PROVSRVC.INVALID_POLICYATTRIBUTE_ID
Invalid Policy configuration. Please try again.
PROVSRVC.DUPLICATE_POLICYATTRIBUTE
Duplicate Policy attribute selected.
PROVSRVC.INVALID_POLICY_MAP
Invalid Policy map.
PROVSRVC.INVALID_MASTER_AAPPLICATION_Id
Invalid master application reference.
PROVSRVC.NO_MAPPING_FOUND
Policy map not found.
PROVSRVC.DUPLICATE_POLICY_MAPPING
Duplicate Policy mapping.
PROVSRVC.INAVLID_POLICYATTRIBUTE_APPLICATION
Invalid Policy association. Please try again.
PROVSRVC.PROVISIONING_NOT_ENABLE
Provisioning not enable
PROVSRVC.DUPLICATE_ROLE
Role ID in use. Please try again.
PROVSRVC.DUPPLICATE_NAME
Name already in use.
PROVSRVC.IDENTITY_ALREADY_EXISTS_EXCEPTION
User principle is already checked Please reset and try again.
PROVSRVC.IDENTITY_NOT_CHECKED_EXCEPTION
At least one user principle should be checked.
RULESRVC.UNKNOWN
Error. Please try again.
RULESRVC.RULE_NOT_FOUND
Rule not found.
RULESRVC.RULE_CONDITION_NOT_FOUND
Rule condition not found.
RULESRVC.RULE_ACTION_GROUP_NOT_FOUND
No group associated with rule. Please try again.
RULESRVC.NON_REMOVABLE_REFERENCED_ENTITY
Cannot be modified as entity in use.
RULESRVC.ALRAEDY_EXISTS
Rule with same name already exists.
RULESRVC.RULE_CONFIGURE_ALREADY_EXIST
Rule with same condition configuration already exists.
RULESRVC.MULTIPLE_ZONES_FOUND
Multiple zones found.
RULESRVC.ZONE_NOT_FOUND
Zone not found.
RULESRVC.INVALID_ARGUMENTS
Please correct the input and try again.
RULESRVC.DEFAULT_RULE_NOT_FOUND
Default rule not found.
IGSRVC.UNKNOWN
Error. Please try again.
IGSRVC.INVALID_JWT
Error. Invalid JWT token.
IGSRVC.CAMPAIGN_COMPLETION_PERIOD_EXCEED
Error. Campaign Completion Period Exceeded.
IGSRVC.CAMPAIGN_STAGE_NOT_FOUND
Error. Campaign Stage Not Found.
IGSRVC.CAMPAIGN_SCOPE_NOT_FOUND
Error. Campaign Scope Not Found.
IGSRVC.CAMPAIGN_ALREADY_IN_DRAFT_STATE
Error. Campaign Already In Draft State.
IGSRVC.CAMPAIGN_ALREADY_IN_PUBLISHED_STATE
Error. Campaign Already In Published State.
IGSRVC.CAMPAIGN_EXECUTION_IN_PROGRESS
Error. Campaign Execution in Progress.
IGSRVC.CAMPAIGN_ASSIGNMENT_NOT_FOUND
Error. Campaign Assignment Not Found.
IGSRVC.CAMPAIGN_HISTORY_NOT_FOUND
Error. Campaign History Not Found.
IGSRVC.UNABLE_TO_PROCESS_RESPONSE
Error. Unable To Process Response.
IGSRVC.CAMPAIGN_ASSIGNMENT_APPLICATION_NOT_FOUND
Error. Campaign Assignment Application Not Found.
IGSRVC.CAMPAIGN_ASSIGNMENT_APPLICATION_ROLE_NOT_FOUND
Error. Campaign Assignment Application Role Not Found.
IGSRVC.APP_ROLE_ALREADY_PROCEED
Error. App Role Already Proceeded.
IGSRVC.INACTIVE_USER_FOUND
Error. Inactive User Found.
IGSRVC.NO_ACTIVE_EXECUTION_FOUND
Error. No Active Execution Found.
IGSRVC.INVALID_CRON_EXPRESSION
Error. Invalid Cron Expression.
IGSRVC.DUPLICATE_CAMPAIGNNAME
Error. Duplicate Campaign Name.
IGSRVC.CAMPAIGN_NOT_FOUND
Campaign not found.
IGSRVC.INVALID_ARGUMENTS
Error. Please correct input and try again.
IGSRVC.CAMPAIGN_STATE_STARTED
Error. Campaign State Already Started.
IGSRVC.STAGE_LIMIT_EXCEED
Error. Stage Limit Exceeded.
IGSRVC.DUPLICATE_STAGE
Error. Duplicate Stage.
IGSRVC.ASSIGNMENT_ALREADY_PROCEED
Error. Assignment Already Proceeded.
IGSRVC.INVALID_CAMPAIGN_ITERATION
Invalid Campaign Iteration.
IGSRVC.INVALID_CAMPAIGN_MANAGER_ASSIGNEE
Campaign manager or assignee configured in stages are not valid.
IGSRVC.INVALID_CAMPAIGN_STATUS
Campaign execution in progress operation not allowed.
IGSRVC.USER_WITH_NO_VALID_APPLICATION
No valid assignments found aborted execution.
IGSRVC.CONNECTION_FAILED
Please check your internet connection.
IGSRVC.ALRAEDY_EXISTS
Record already exists.
IGSRVC.FORBIDDEN
Please contact system administrator.
IGSRVC.UNAUTHORIZED
Please contact system administrator.
IGPROCESS.UNKNOWN
Error. Please try again.
IGPROCESS.INVALID_ARGUMENTS
Error. Please correct input and try again.
IGPROCESS.CAMPAIGN_NOT_FOUND
Error. Campaign Not Found.
IGPROCESS.NO_ACTIVE_EXECUTION_FOUND
Error. No Active Execution Found.
IGPROCESS.CAMPAIGN_HISTORY_NOT_FOUND
Error. Campaign History Not Found.
IGPROCESS.INVALID_CAMPAIGN_ITERATION
Error. Invalid Campaign Iteration.
IGPROCESS.CAMPAIGN_EXECUTION_IN_PROGRESS
Error. Campaign Execution In Progress.
IGPROCESS.MATCHING_ASSIGNMENTS_NOT_FOUND
Error. Matching Assignments Not Found.
SCHEDULER.UNKNOWN
Error. Please try again.
SCHEDULER.TASK_NOT_FOUND
Error. Task Not Found.
SCHEDULER.TASK_NOT_ACTIVE
Error. Task Not Active.
SCHEDULER.INVALID_ARGUMENTS
Error. Please correct input and try again.
SCHEDULER.INVALID_START_DATE
Error. Invalid Start Date.
SCHEDULER.TENANT_NOT_FOUND
Error. Tenant Not Found.
SCHEDULER.UPDATE_NOT_SUPPORTED
Error. Update Is Not Supported.
SCHEDULER.CRON_REPETITION_BELOW_ALLOWED_LIMIT
Error. Cron Repetition Is Below Allowed Limit.
SCHEDULER.INVALID_CRON_EXPRESSION
Invalid Cron Expression.
SODSRVC.ALREADY_EXISTS
Error. Value Already Exists.
SODSRVC.INVALID_ARGUMENTS
Error. Please correct the input and try again.
SAMLEXTIDPCONFIGSRVC.UNKNOWN
Error. Please try again.
SAMLEXTIDPCONFIGSRVC.IDENTITY_PROVIDER_WITH_NAME_EXISTS
Idenity Provider with same name already exist. Please enter unique name.
SAMLEXTIDPCONFIGSRVC.SERVICE_PROVIDER_WITH_NAME_EXISTS
Service Provider with same name already exists.
SAMLEXTIDPCONFIGSRVC.NON_REMOVABLE_REFERENCED_ENTITY
Cannot modify or remove service provider till active under external identity policy or rule.
SAMLEXTIDPCONFIGSRVC.INVALID_ARGUMENTS
Please correct the input and try again.
SAMLEXTIDPCONFIGSRVC.CERTIFICATE_PARSING_ERROR
Error occurred while parsing certificate.
SAMLEXTIDPCONFIGSRVC.AUTH_TYPE_CANNOT_BE_UPDATED
Identity provider type cannot be updated.
SAMLEXTIDPCONFIGSRVC.CONNECTION_FAILED
Please check your internet connection.
SAMLEXTIDPCONFIGSRVC.IDP_CONFIGURATION_NOT_FOUND
Identity provider configuration not found.
SAMLEXTIDPCONFIGSRVC.MULTIPLE_IDP_CONFIGURATION_FOUND
Multiple identity provider configuration found.
SAMLEXTIDPCONFIGSRVC.NAME_ID_POLICY_NAME_ID_VALUE_MISMATCH
NameIdPolicy and NameIdValue does not match.
SAMLEXTIDPCONFIGSRVC.SP_CONFIGURATION_NOT_FOUND
Service provider configuration not found.
SAMLEXTIDPCONFIGSRVC.UNAUTHORIZED
Please contact system administrator.
SAMLEXTIDPCONFIGSRVC.SERVICE_PROVIDER_NOT_FOUND
Service provider not found.
SAMLEXTIDPCONFIGSRVC.CERTIFICATE_NOT_FOUND
Certificate not found.
SAMLEXTIDPCONFIGSRVC.EAMIL_EXISTS
Email already exists.
SAMLEXTIDPCONFIGSRVC.CUSTOM_IDENTITY_TYPE_MUST_HAVE_ID
Custom identity type must have ID.
SAMLEXTIDPCONFIGSRVC.INACTIVE_CONFIGURATION_FOUND
Inactive configuration found.
SAMLEXTIDPCONFIGSRVC.INVALID_IDP_CONFIGURED
Invalid IDP configured.
SAMLEXTIDPCONFIGSRVC.NO_MAPPING_FOUND
No mapping found.
SAMLEXTIDPCONFIGSRVC.INVALID_POLICY_MAPPING
Invalid policy mapping.
SAMLEXTIDPCONFIGSRVC.POLICY_MAP_REQUIRED_FIELD_NOT_FOUND
Policy map required field not found.
SAMLEXTIDPCONFIGSRVC.MANDATORY_FIELD_EXCEPTION
Mandatory field exception.
SAMLEXTIDPCONFIGSRVC.MAPPING_ALREADY_EXISTS
Mapping already exists.
SAMLEXTIDPCONFIGSRVC.JIT_CONFIGURATION_NOT_FOUND
JIT configuration not found.
USRSRVC.INVALID_EXTENSION_ENDDATE
Extended end date should be less than current access end date.
MFASRVC.SMS_OTP_EXPIRED
SMS OTP expired.
MFASRVC.SHORT_ANSWER_LENGTH
Answer length is short.
MFASRVC.DEVICE_INFO_NOT_FOUND
Please scan the QR code.
AUTHSRVC.USER_LOCKED
User locked. Please Unlock your Account.
AUTHSRVC.EMAIL_NOT_FOUND
Email not found.
AUTHSRVC.INVALID_USER_ACCOUNT_STATE
Your account is expired/inactive. Please contact Cymmetri Administrator
AUTHSRVC.INVALID_DATE
Start/End date should be greater than current date and time.
AUTHSRVC.DELEGATE_CONSENT_NOT_FOUND
Error. Delegate consent not found.
AUTHSRVC.DELEGATE_USER_NOT_FOUND
Error. User doesn't have delegation access.
AUTHSRVC.NO_OPTION_AVAILABLE
Please contact Cymmetri Administrator for Password Reset.
AUTHSRVC.DELEGATION_DEACTIVATE
Error. Delegation is inactive.
AUTHSRVC.PASSWORD_EXPIRED
Your password has expired Please reset your password.
PROVSRVC.UNSUPPORTED_DELEGETE_MFA_SETUP
Delegatee can't setup MFA for application having additional authentication
PAMSRVC.UNSUPPORTED_DELEGETE_MFA_SETUP
Delegatee can't setup MFA for application having additional authentication
SLFSRVC.EXISITNG_APP_IN_TAG_FOUND
Application already available in tag.
AD-ADAPTER.FAILED_TO_PWD_CHANGE
Password change failed.
AUTHSRVC.INVALID_CONFIG
Invalid config for authentication policy or rule
PROVSRVC.UNAUTHORIZED
Unauthorized access.
REGSRVC.UNAUTHORIZED
Unauthorized access.
MFASRVC.INVALID_MFA_OTP_CONFIG
Invalid Otp config please contact admin
MFASRVC.EMAIL_NOT_FOUND
Email not registered please contact admin
MFASRVC.MOBILE_NOT_FOUND
Mobile not registered please contact admin
MFASRVC.EMAIL_MOBILE_NOT_FOUND
Mobile or email not registered please contact admin
MFASRVC.LARGE_ANSWER_LENGTH
Maximum answer lenght exceeded try with shorter length answer
SLFSRVC.EXISITNG_USER_TAG_FOUND
Tag with same name already exists
SLFSRVC.IMAGE_MAXSIZE_EXCEEDED
Maximum limit for file size exceeded.
SLFSRVC.IMAGE_TYPE_NOTALLOWED
Image Type not allowed
SLFSRVC.INVALID_ARGUMENTS
Invalid Arguments
REPORT.EMAIL_NOT_EXISTS_EXCEPTION
User Email Not Found. Please contact cymmetri administrator.
REPORT.CONNECTION_FAILED
Failed to send report.
SOME_ERROR_OCCURRED_WORKING_ON_IT
Please contact cymmetri administrator.
INVALID_IDENTITY_PROVIDER_STATUS
Invalid Identity Provider Status. Please contact cymmetri administrator.
INVALID_ARGUMENTS
Please correct Input and try again. Please contact cymmetri administrator.
INVALID_SERVICE_PROVIDER_STATUS
Invalid Service Provider Status. Please contact cymmetri administrator.
MANDATORY_FIELD_EXCEPTION
Mandatory Field is Missing. Please contact cymmetri administrator.
TENANT_OR_HOST_NOT_RECEIVED_FROM_NGINX
Please contact cymmetri administrator.
TENANT_OR_HOST_PROTO_NOT_RECEIVED_FROM_NGINX
Please contact cymmetri administrator.
SOME_IMPERSONATE_ACCESS
Unauthorized Access. Please contact cymmetri administrator.
SERVICE_PROVIDER_INBOUND_MESSAGE_ERROR
Invalid SAML Message Received. Please contact cymmetri administrator.
INVALID_SAML_RESPONSE_ASSERTION_VERSION
Invalid SAML Response Assertion version. Please contact cymmetri administrator.
INVALID_SAML_RESPONSE_ISSUE_INSTANT
Invalid SAML Response Issue. Please contact cymmetri administrator.
INVALID_SAML_RESPONSE_STATUS
Invalid SAML Response Status. Please contact cymmetri administrator.
INVALID_SAML_RESPONSE_STATUS_REQUESTER_URI
Invalid SAML Response Status Requester URI. Please contact cymmetri administrator.
INVALID_SAML_RESPONSE_STATUS_RESPONDER_URI
Invalid SAML Response Status Response URI. Please contact cymmetri administrator.
INVALID_SAML_RESPONSE_STATUS_VERSION_MISMATCH_URL
Invalid SAML Response Status Version Mismatch URI. Please contact cymmetri administrator.
INVALID_SAML_RESPONSE
Invalid SAML Response. Please contact cymmetri administrator.
INVALID_SAML_RESPONSE_DESTINATION
Invalid SAML Response Destination. Please contact cymmetri administrator.
INVALID_SAML_RESPONSE_VERSION_OR_ASSERTION_VERSION
Invalid SAML Response Version or Assertion Version. Please contact cymmetri administrator.
INVALID_SAML_RESPONSE_ASSERTION_SUBJECT
Invalid SAML Response Assertion Subject. Please contact cymmetri administrator.
INVALID_SAML_RESPONSE_ASSERTION_SUBJECT_NAMEID
Invalid SAML Response Assertion Subject NameId. Please contact cymmetri administrator.
INVALID_SAML_RESPONSE_ASSERTION_ISSUER
Invalid SAML Response Assertion Issuer. Please contact cymmetri administrator.
INVALID_SAML_RESPONSE_ASSERTION_CONDITION_AUDIENCE
Invalid SAML Response Assertion Condition Audience. Please contact cymmetri administrator.
INVALID_SAML_RESPONSE_ASSERTION_AUTHNSTATEMENT
Invalid SAML Response Assertion AuthNStatement. Please contact cymmetri administrator.
INVALID_SAML_RESPONSE_ASSERTION_ATTRIBUTE
Invalid SAML Response Assertion Attribute. Please contact cymmetri administrator.
MULTIPLE_ASSERTIONS_IN_RESPONSE_NOT_SUPPORTED
Multiple Assertion in Response Not Supported. Please contact cymmetri administrator.
INVALID_SAML_RESPONSE_ASSERTION_SIGNATURE
Invalid SAML Response Assertion Signature. Please contact cymmetri administrator.
INVALID_SAML_RESPONSE_SIGNATURE
Invalid SAML Response Signature. Please contact cymmetri administrator.
INVALID_SAML_RESPONSE_ASSERTION_CONDITION
Invalid SAML Response Assertion Condition. Please contact cymmetri administrator.
INVALID_SAML_RESPONSE_ASSERTION
Invalid SAML Response Assertion. Please contact cymmetri administrator.
INVALID_SAML_RESPONSE_ISSUER
Invalid SAML Response Issuer. Please contact cymmetri administrator.
IDP_CONFIGURATION_NOT_FOUND
Idp Configuration Not Found. Please contact cymmetri administrator.
SP_ID_IDP_ID_LOGIN_EMPTY
Service provider or identity provider login not provided. Please contact cymmetri administrator.
SERVICE_PROVIDER_CONFIGURATION_NOT_FOUND
Service Provider Configuration Not Found. Please contact cymmetri administrator.
ERROR_BUILDING_SAML_AUTHN_REQUEST
Failed To Build SAML Authentication Request. Please contact cymmetri administrator.
ERROR_PERSISTING_SAML_AUTHN_REQUEST
Failed To Persist SAML Authentication Request. Please contact cymmetri administrator.
ERROR_SENDING_SAML_AUTHN_REQUEST
Failed to Send SAML Authentication Request. Please contact cymmetri administrator.
USER_EMAIL_ADDRESS_NOT_PRESENT
User Email Not Found. Please contact cymmetri administrator.
USER_LOGIN_NOT_PRESENT
User Login Not Found. Please contact cymmetri administrator.
EMAIL_ADDRESS_DOES_NOT_MATCH
Email Address does not matching. Please contact cymmetri administrator.
LOGIN_DOES_NOT_MATCH
Login does not match. Please contact cymmetri administrator.
USER_NOT_AVAILABLE
User is not present. Please contact cymmetri administrator.
SERVICE_PROVIDER_NOT_FOUND
Service provider is not found. Please contact cymmetri administrator.
UNAUTHORIZED_ACCESS
Unauthorized Access. Please contact cymmetri administrator.
UNAUTHORIZED
Unauthorized Access. Please contact cymmetri administrator.
USER_NOT_FOUND
User Not found. Please contact cymmetri administrator.
DATA_NOT_PRESENT
Application configuration does not exist. Please contact cymmetri administrator.
ARGUMENT_IS_REQUIRED
Please correct Input and try again. Please contact cymmetri administrator.
APPLICATION_CONFIG_EXISTS
Application Configuration already exists. Please contact cymmetri administrator.
APPLICATION_CONFIG_NOT_PRESENT
Application configuration does not exists. Please contact cymmetri administrator.
INVALID_TOKEN
Invalid token Please contact cymmetri administrator.
TENANT_NOT_FOUND
Tenant detail not availaible. Please contact cymmetri administrator.
INVALID_APPLICATION_ID
Invalid application id. Please contact cymmetri administrator.
APPLICATION_WITH_ISSUER_NOT_FOUND
Application configuration with issuer not found. Please contact cymmetri administrator.
EXCEPTION_OCCURED_WITH_TENANT_JKS
Please contact cymmetri administrator.
EXCEPTION_OCCURED_WITH_TENANT_JKS_KEY_GENERATE
Please contact cymmetri administrator.
APPLICATION_NOT_ASSIGNED_TO_USER
Application is not assigned to the user. Please contact cymmetri administrator.
USER_NOT_ASSIGNED_SERVICE_PROVIDER_ERROR
User is not assigned to the service provider. Please contact cymmetri administrator.
SOMETHING_WENT_WRONG
Please contact cymmetri administrator.
SERVICE_PROVIDER_NAMEIDVALUE_MISMATCH_ERROR
Service provider nameId value does not match with configured application. Please contact cymmetri administrator.
SERVICE_PROVIDER_NAMEID_MISMATCH_ERROR
Service provider nameId value does not match with configured application. Please contact cymmetri administrator.
TENANT_HOST_NOT_FOUND
Please contact cymmetri administrator.
APPLICATION_CONFIG_NOT_FOUND
Application Configuration not found. Please contact cymmetri administrator.
SAMLREQUEST_NOT_PRESENT_IN_REQUEST
SAML Request is not present in Request. Please contact cymmetri administrator.
CONFIGURED_REQUEST_ISSUER_AND_SAML_REQUEST_NOT_ISSUER_NOT_MATCH
Application issuer Configuration does not match. Please contact cymmetri administrator.
INVALID_REQUEST_ISSUER
Invalid Request Issuer. Please contact cymmetri administrator.
IDENTITY_TOKEN_SAML_REQUEST_NOT_FOUND
Invalid Identity SAML Request Token. Please contact cymmetri administrator.
IDENTITY_REFRESH_SAML_REQUEST_NOT_FOUND
Invalid Refresh SAML Request Token. Please contact cymmetri administrator.
USER_NOT_ASSIGNED_TO_APPLICATION
User is not associated with the application. Please contact cymmetri administrator.
SSO_ERROR_SENDING_SAML_RESPONSE
Error Sending SAML Response. Please contact cymmetri administrator.
SSO_CONFIG_NOT_FOUND_APPLICATION_ID
SSO configuration not found for application. Please contact cymmetri administrator.
SSO_USER_NOT_FOUND
SSO user found for application. Please contact cymmetri administrator.
INTERNAL_SERVER_ERROR
Please contact cymmetri administrator.
IDP_SSO_JKS_MANAGER_FAILED
Please contact cymmetri administrator.
IDP_SSO_CUSTOM_JKS_FAILED
Please contact cymmetri administrator.
IDP_SSO_FAILED
SSO failed for identity provider. Please contact cymmetri administrator.
SERVICE_PROVIDER_SESSION_NOT_FOUND
Service provider session not availaible. Please contact cymmetri administrator.
INVALID_SP_INITIATED_REQUEST
Invalid service provider request. Please contact cymmetri administrator.
ERROR_PARSING_SAML_SLO
Error validating saml slo request. Please contact cymmetri administrator.
SERVICE_PROVIDER_ERROR
Failed with service provider. Please contact cymmetri administrator.
EXPIRED_REFRESH_TOKEN
Refresh token is expired. Please contact cymmetri administrator.
INVALID_REFRESH_TOKEN
Invalid refresh token. Please contact cymmetri administrator.
EMPTY_REFRESH_TOKEN
Empty refresh token. Please contact cymmetri administrator.
REFRESH_TOKEN_COOKIE_NOT_PRESENT
Refresh token cookie not present. Please contact cymmetri administrator.
APPLICATION_ID_NOT_PRESENT_IN_CONFIG
Application id not present. Please contact cymmetri administrator.
APPLICATION_ID_NOT_PRESENT_IN_REQUEST
Application id is not present in request Please contact cymmetri administrator.
EXPIRED_SSO_IDENTITY_TOKEN
SSO identity token is expired. Please contact cymmetri administrator.
EMPTY_SSO_IDENTITY_TOKEN
SSO identity token is invalid. Please contact cymmetri administrator.
REQUEST_ISSUER_FROM_SAML_REQUEST_NOT_PRESNETTITY_TOKEN
Request issuer is not present in saml request. Please contact cymmetri administrator.
INVALID_SSO_IDENTITY_TOKEN
Invalid SSO identity token. Please contact cymmetri administrator.
IDP_SLO_FAILED
Identity provider single logout failed. Please contact cymmetri administrator.
BUILD_SLO_REQUEST_FAILED
Build to failed single logout request. Please contact cymmetri administrator.
SLO_REQUEST_SEND_FAILED
Failed to send single logout request. Please contact cymmetri administrator.
SLO_RESPONSE_SEND_FAILED
Failed to send single logout response. Please contact cymmetri administrator.
ERROR_PERSISTING_SLO_REQUEST
Failed to persist single logout request. Please contact cymmetri administrator.
SLO_RESPONSE_SAML_ATTRIBUTE_VALIDATION_FAILED
Failed to validate single logout response attribute. Please contact cymmetri administrator.
INVALID_SAML_SLO_RESPONSE
Invalid saml single logout response. Please contact cymmetri administrator.
INVALID_SAML_SLO_MESSAGE
Invalid saml single logout message. Please contact cymmetri administrator.
SLO_REQUEST_VALIDATION_FAILED
Failed to validate single logout request. Please contact cymmetri administrator.
SLO_RESPONSE_VALIDATION_FAILED
Failed to validate single logout response. Please contact cymmetri administrator.
REMOVE_USER_BEFORE_APPLICATION
Users should get removed before removing the application.
PROVSRVC.REMOVE_USER_BEFORE_APPLICATION
Users should get removed before removing the application.
PAMSRVC.INVALID_ARGUMENTS
AD Parameter not found
PAMSRVC.IMPORT_DATA_TO_CSV_FILE_FAILED
CSV file not generated
PAMSRVC.UPDATE_AD_USER_PASSWORD_FAILED
Password update fail
PAMSRVC.VAULT_USER_ALREADY_AVAILABLE
Vault user already exist
PAMSRVC.BREAK_GLASS_NOT_FOUND
Break Glass Configuration Not Found
PAMSRVC.SERVER_ALREADY_EXISTS
Device Already Exists
DORMANCY_DISABLE_DAYS_EXCEEDED
Config days exceeded
PAMSRVC.DORMANCY_DISABLE_DAYS_EXCEEDED
Config days exceeded
SAMLSPSRVC.SOME_ERROR_OCCURRED_WORKING_ON_IT
Please contact cymmetri administrator.
SAMLSPSRVC.INVALID_IDENTITY_PROVIDER_STATUS
Invalid Identity Provider Status. Please contact cymmetri administrator.
SAMLSPSRVC.INVALID_ARGUMENTS
Please correct Input and try again. Please contact cymmetri administrator.
SAMLSPSRVC.INVALID_SERVICE_PROVIDER_STATUS
Invalid Service Provider Status. Please contact cymmetri administrator.
SAMLSPSRVC.MANDATORY_FIELD_EXCEPTION
Mandatory Field is Missing. Please contact cymmetri administrator.
SAMLSPSRVC.TENANT_OR_HOST_NOT_RECEIVED_FROM_NGINX
Please contact cymmetri administrator.
SAMLSPSRVC.TENANT_OR_HOST_PROTO_NOT_RECEIVED_FROM_NGINX
Please contact cymmetri administrator.
SAMLSPSRVC.SOME_IMPERSONATE_ACCESS
Unauthorized Access. Please contact cymmetri administrator.
SAMLSPSRVC.SERVICE_PROVIDER_INBOUND_MESSAGE_ERROR
Invalid SAML Message Received. Please contact cymmetri administrator.
SAMLSPSRVC.INVALID_SAML_RESPONSE_ASSERTION_VERSION
Invalid SAML Response Assertion version. Please contact cymmetri administrator.
SAMLSPSRVC.INVALID_SAML_RESPONSE_ISSUE_INSTANT
Invalid SAML Response Issue. Please contact cymmetri administrator.
SAMLSPSRVC.INVALID_SAML_RESPONSE_STATUS
Invalid SAML Response Status. Please contact cymmetri administrator.
SAMLSPSRVC.INVALID_SAML_RESPONSE_STATUS_REQUESTER_URI
Invalid SAML Response Status Requester URI. Please contact cymmetri administrator.
SAMLSPSRVC.INVALID_SAML_RESPONSE_STATUS_RESPONDER_URI
Invalid SAML Response Status Response URI. Please contact cymmetri administrator.
SAMLSPSRVC.INVALID_SAML_RESPONSE_STATUS_VERSION_MISMATCH_URL
Invalid SAML Response Status Version Mismatch URI. Please contact cymmetri administrator.
SAMLSPSRVC.INVALID_SAML_RESPONSE
Invalid SAML Response. Please contact cymmetri administrator.
SAMLSPSRVC.INVALID_SAML_RESPONSE_DESTINATION
Invalid SAML Response Destination. Please contact cymmetri administrator.
SAMLSPSRVC.INVALID_SAML_RESPONSE_VERSION_OR_ASSERTION_VERSION
Invalid SAML Response Version or Assertion Version. Please contact cymmetri administrator.
SAMLSPSRVC.INVALID_SAML_RESPONSE_ASSERTION_SUBJECT
Invalid SAML Response Assertion Subject. Please contact cymmetri administrator.
SAMLSPSRVC.INVALID_SAML_RESPONSE_ASSERTION_SUBJECT_NAMEID
Invalid SAML Response Assertion Subject NameId. Please contact cymmetri administrator.
SAMLSPSRVC.INVALID_SAML_RESPONSE_ASSERTION_ISSUER
Invalid SAML Response Assertion Issuer. Please contact cymmetri administrator.
SAMLSPSRVC.INVALID_SAML_RESPONSE_ASSERTION_CONDITION_AUDIENCE
Invalid SAML Response Assertion Condition Audience. Please contact cymmetri administrator.
SAMLSPSRVC.INVALID_SAML_RESPONSE_ASSERTION_AUTHNSTATEMENT
Invalid SAML Response Assertion AuthNStatement. Please contact cymmetri administrator.
SAMLSPSRVC.INVALID_SAML_RESPONSE_ASSERTION_ATTRIBUTE
Invalid SAML Response Assertion Attribute. Please contact cymmetri administrator.
SAMLSPSRVC.MULTIPLE_ASSERTIONS_IN_RESPONSE_NOT_SUPPORTED
Multiple Assertion in Response Not Supported. Please contact cymmetri administrator.
SAMLSPSRVC.INVALID_SAML_RESPONSE_ASSERTION_SIGNATURE
Invalid SAML Response Assertion Signature. Please contact cymmetri administrator.
SAMLSPSRVC.INVALID_SAML_RESPONSE_SIGNATURE
Invalid SAML Response Signature. Please contact cymmetri administrator.
SAMLSPSRVC.INVALID_SAML_RESPONSE_ASSERTION_CONDITION
Invalid SAML Response Assertion Condition. Please contact cymmetri administrator.
SAMLSPSRVC.INVALID_SAML_RESPONSE_ASSERTION
Invalid SAML Response Assertion. Please contact cymmetri administrator.
SAMLSPSRVC.INVALID_SAML_RESPONSE_ISSUER
Invalid SAML Response Issuer. Please contact cymmetri administrator.
SAMLSPSRVC.IDP_CONFIGURATION_NOT_FOUND
Idp Configuration Not Found. Please contact cymmetri administrator.
SAMLSPSRVC.SP_ID_IDP_ID_LOGIN_EMPTY
Service provider or identity provider login not provided. Please contact cymmetri administrator.
SAMLSPSRVC.SERVICE_PROVIDER_CONFIGURATION_NOT_FOUND
Service Provider Configuration Not Found. Please contact cymmetri administrator.
SAMLSPSRVC.ERROR_BUILDING_SAML_AUTHN_REQUEST
Failed To Build SAML Authentication Request. Please contact cymmetri administrator.
SAMLSPSRVC.ERROR_PERSISTING_SAML_AUTHN_REQUEST
Failed To Persist SAML Authentication Request. Please contact cymmetri administrator.
SAMLSPSRVC.ERROR_SENDING_SAML_AUTHN_REQUEST
Failed to Send SAML Authentication Request. Please contact cymmetri administrator.
SAMLSPSRVC.USER_EMAIL_ADDRESS_NOT_PRESENT
User Email Not Found. Please contact cymmetri administrator.
SAMLSPSRVC.USER_LOGIN_NOT_PRESENT
User Login Not Found. Please contact cymmetri administrator.
SAMLSPSRVC.EMAIL_ADDRESS_DOES_NOT_MATCH
Email Address does not matching. Please contact cymmetri administrator.
SAMLSPSRVC.LOGIN_DOES_NOT_MATCH
Login does not match. Please contact cymmetri administrator.
SAMLSPSRVC.USER_NOT_AVAILABLE
User is not present. Please contact cymmetri administrator.
SAMLSPSRVC.SERVICE_PROVIDER_NOT_FOUND
Service provider is not found. Please contact cymmetri administrator.
SAMLSPSRVC.UNAUTHORIZED_ACCESS
Unauthorized Access. Please contact cymmetri administrator.
SAMLSPSRVC.UNAUTHORIZED
Unauthorized Access. Please contact cymmetri administrator.
SAMLSPSRVC.USER_NOT_FOUND
User Not found. Please contact cymmetri administrator.
SAMLSRVC.SOME_ERROR_OCCURRED_WORKING_ON_IT
Please contact cymmetri administrator.
SAMLSRVC.DATA_NOT_PRESENT
Application configuration does not exist. Please contact cymmetri administrator.
SAMLSRVC.ARGUMENT_IS_REQUIRED
Please correct Input and try again. Please contact cymmetri administrator.
SAMLSRVC.APPLICATION_CONFIG_EXISTS
Application Configuration already exists. Please contact cymmetri administrator.
SAMLSRVC.APPLICATION_CONFIG_NOT_PRESENT
Application configuration does not exists. Please contact cymmetri administrator.
SAMLSRVC.INVALID_TOKEN
Invalid token Please contact cymmetri administrator.
SAMLSRVC.TENANT_NOT_FOUND
Tenant detail not availaible. Please contact cymmetri administrator.
SAMLSRVC.INVALID_APPLICATION_ID
Invalid application id. Please contact cymmetri administrator.
SAMLSRVC.APPLICATION_WITH_ISSUER_NOT_FOUND
Application configuration with issuer not found. Please contact cymmetri administrator.
SAMLSRVC.EXCEPTION_OCCURED_WITH_TENANT_JKS
Please contact cymmetri administrator.
SAMLSRVC.EXCEPTION_OCCURED_WITH_TENANT_JKS_KEY_GENERATE
Please contact cymmetri administrator.
SAMLSRVC.APPLICATION_NOT_ASSIGNED_TO_USER
Application is not assigned to the user. Please contact cymmetri administrator.
SAMLSRVC.TENANT_OR_HOST_PROTO_NOT_RECEIVED_FROM_NGINX
Please contact cymmetri administrator.
SAMLSRVC.USER_NOT_ASSIGNED_SERVICE_PROVIDER_ERROR
User is not assigned to the service provider. Please contact cymmetri administrator.
SAMLSRVC.SOMETHING_WENT_WRONG
Please contact cymmetri administrator.
SAMLSRVC.SERVICE_PROVIDER_NAMEIDVALUE_MISMATCH_ERROR
Service provider nameId value does not match with configured application. Please contact cymmetri administrator.
SAMLSRVC.SERVICE_PROVIDER_NAMEID_MISMATCH_ERROR
Service provider nameId value does not match with configured application. Please contact cymmetri administrator.
SAMLSRVC.TENANT_HOST_NOT_FOUND
Please contact cymmetri administrator.
SAMLSRVC.TENANT_OR_HOST_NOT_RECEIVED_FROM_NGINX
Please contact cymmetri administrator.
SAMLSRVC.APPLICATION_CONFIG_NOT_FOUND
Application Configuration not found. Please contact cymmetri administrator.
SAMLSRVC.SAMLREQUEST_NOT_PRESENT_IN_REQUEST
SAML Request is not present in Request. Please contact cymmetri administrator.
SAMLSRVC.CONFIGURED_REQUEST_ISSUER_AND_SAML_REQUEST_NOT_ISSUER_NOT_MATCH
Application issuer Configuration does not match. Please contact cymmetri administrator.
SAMLSRVC.INVALID_REQUEST_ISSUER
Invalid Request Issuer. Please contact cymmetri administrator.
SAMLSRVC.IDENTITY_TOKEN_SAML_REQUEST_NOT_FOUND
Invalid Identity SAML Request Token. Please contact cymmetri administrator.
SAMLSRVC.IDENTITY_REFRESH_SAML_REQUEST_NOT_FOUND
Invalid Refresh SAML Request Token. Please contact cymmetri administrator.
SAMLSRVC.USER_NOT_ASSIGNED_TO_APPLICATION
User is not associated with the application. Please contact cymmetri administrator.
SAMLSRVC.SSO_ERROR_SENDING_SAML_RESPONSE
Error Sending SAML Response. Please contact cymmetri administrator.
SAMLSRVC.SSO_CONFIG_NOT_FOUND_APPLICATION_ID
SSO configuration not found for application. Please contact cymmetri administrator.
SAMLSRVC.SSO_USER_NOT_FOUND
SSO user found for application. Please contact cymmetri administrator.
SAMLSRVC.INTERNAL_SERVER_ERROR
Please contact cymmetri administrator.
SAMLSRVC.IDP_SSO_JKS_MANAGER_FAILED
Please contact cymmetri administrator.
SAMLSRVC.IDP_SSO_CUSTOM_JKS_FAILED
Please contact cymmetri administrator.
SAMLSRVC.IDP_SSO_FAILED
SSO failed for identity provider. Please contact cymmetri administrator.
SAMLSRVC.SERVICE_PROVIDER_SESSION_NOT_FOUND
Service provider session not availaible. Please contact cymmetri administrator.
SAMLSRVC.INVALID_ARGUMENTS
Please correct input and try again. Please contact cymmetri administrator.
SAMLSRVC.INVALID_SP_INITIATED_REQUEST
Invalid service provider request. Please contact cymmetri administrator.
SAMLSRVC.ERROR_PARSING_SAML_SLO
Error validating saml slo request. Please contact cymmetri administrator.
SAMLSRVC.SERVICE_PROVIDER_ERROR
Failed with service provider. Please contact cymmetri administrator.
SAMLSRVC.EXPIRED_REFRESH_TOKEN
Refresh token is expired. Please contact cymmetri administrator.
SAMLSRVC.INVALID_REFRESH_TOKEN
Invalid refresh token. Please contact cymmetri administrator.
SAMLSRVC.EMPTY_REFRESH_TOKEN
Empty refresh token. Please contact cymmetri administrator.
SAMLSRVC.REFRESH_TOKEN_COOKIE_NOT_PRESENT
Refresh token cookie not present. Please contact cymmetri administrator.
SAMLSRVC.APPLICATION_ID_NOT_PRESENT_IN_CONFIG
Application id not present. Please contact cymmetri administrator.
SAMLSRVC.APPLICATION_ID_NOT_PRESENT_IN_REQUEST
Application id is not present in request Please contact cymmetri administrator.
SAMLSRVC.EXPIRED_SSO_IDENTITY_TOKEN
SSO identity token is expired. Please contact cymmetri administrator.
SAMLSRVC.EMPTY_SSO_IDENTITY_TOKEN
SSO identity token is invalid. Please contact cymmetri administrator.
SAMLSRVC.REQUEST_ISSUER_FROM_SAML_REQUEST_NOT_PRESNETTITY_TOKEN
Request issuer is not present in saml request. Please contact cymmetri administrator.
SAMLSRVC.INVALID_SSO_IDENTITY_TOKEN
Invalid SSO identity token. Please contact cymmetri administrator.
SAMLSRVC.IDP_SLO_FAILED
Identity provider single logout failed. Please contact cymmetri administrator.
SAMLSRVC.BUILD_SLO_REQUEST_FAILED
Build to failed single logout request. Please contact cymmetri administrator.
SAMLSRVC.SLO_REQUEST_SEND_FAILED
Failed to send single logout request. Please contact cymmetri administrator.
SAMLSRVC.SLO_RESPONSE_SEND_FAILED
Failed to send single logout response. Please contact cymmetri administrator.
SAMLSRVC.ERROR_PERSISTING_SLO_REQUEST
Failed to persist single logout request. Please contact cymmetri administrator.
SAMLSRVC.SLO_RESPONSE_SAML_ATTRIBUTE_VALIDATION_FAILED
Failed to validate single logout response attribute. Please contact cymmetri administrator.
SAMLSRVC.INVALID_SAML_SLO_RESPONSE
Invalid saml single logout response. Please contact cymmetri administrator.
SAMLSRVC.INVALID_SAML_SLO_MESSAGE
Invalid saml single logout message. Please contact cymmetri administrator.
SAMLSRVC.SLO_REQUEST_VALIDATION_FAILED
Failed to validate single logout request. Please contact cymmetri administrator.
SAMLSRVC.SLO_RESPONSE_VALIDATION_FAILED
Failed to validate single logout response. Please contact cymmetri administrator.
SAMLSRVC.UNAUTHORIZED
Unauthorized. Please contact cymmetri administrator.
INVALID_USER_SESSION
User login session is invalid
USER_NOT_CONFIGURED_FOR_EXTERNAL_LOGOUT
User is not configured for external identity provider logout
USER_DOES_NOT_HAVE_ANY_ACTIVE_SSO_SESSION
User does not have any active sso login session
ISSUE_INSTANT_EXCEPTION
Invalid user issue instant exception
NOT_ON_OR_AFTER_EXCEPTION
Saml attribute is not valid before and after timestamp
NAME_ID_FORMAT_EXCEPTION
Invalid user name id is not valid
SESSION_INDEX_EXCEPTION
User login session index is invalid
DESTINATION_EXCEPTION
Saml attribute destination is invalid
IDENTITY_PROVIDER_EXCEPTION
External identity provider is invalid
IN_RESPONSE_TO
Saml attribute in response attribute is invalid
ISSUER_EXCEPTION
Saml attribute issuer is invalid
DATALOGGER.ALREADY_ACTIVATED
Already activated
DATALOGGER.ALREADY_DEACTIVATED
Already deactivated
DATALOGGER.SYSLOG_CONFIG_TEST_FAILED
Syslog configuration test failed
DATALOGGER.SYSLOG_CONFIG_NOT_FOUND
Syslog configuration not found
PAM_CONFIG_DATA_NOT_FOUND
Pam Configuration data not found
PAM_INVALID_CONFIG
Invalid Pam Configuration found
PAMSRVC.INTERNAL_ERROR
Invalid password. Please try again
PAMSRVC.PAM_CONNECTION_FAIL
Connection Fail
PAMSRVC.CONNECTION_FAILED
Connection Fail
REPORT.INVALID_ARGUMENTS
Please correct the input and try again
PROVSRVC.PASSWORDFILTER_AND_APPLICATION_DOES_NOT_SAME
Filtered application and included/excluded cannot be the same
PROVSRVC.PASSWORDFILTER_ALREADY_CONFIGURED
Application is already configured for password filter
dagsrvc.INVALID_ARGUMENTS
Invalid argument.
dagsrvc.INVALID_ARGUMENTS
Invalid argument.
dagsrvc.SERVER_NAME_ALREADY_EXIST_EXCEPTION
Server name already exit.
dagsrvc.ROOT_LOCATION_NOT_FOUND
Server details not found.
DAGSRVC.DAG_SHARED_SERVER_ALREADY_EXISTS
Server Configuration already exist
DAGSRVC.DAG_SHARED_SERVER_NOT_FOUND
One or more shared servers not found
PROVSRVC.APPLICATION_ROLE_NOT_FOUND
Application Role not found
PORTAL.EXPIRY_DATA_NOT_FOUND
Expiry data not found
PORTAL.EXPIRED_LINK
Link has been expired
REGSRVC.ACCOUNT_NOT_ACTIVE
Tenant account inactive. Please contact support
USRSRVC.IMPORT_SCHEMA_NOT_FOUND
Import template not found
SLFSRVC.OPERATION_NOT_ACTIVE
Operation not configured
WKFLSRVC.WORKFLOW_PREFERENCE_CONFIG_NOT_FOUND
Workflow Preference Config not found
USRSRVC.GROUP_ALREADY_ASSIGN_TO_USER
Group Already Assigned to User.
USRSRVC.USER_INACTIVE_CONFIG_NOT_FOUND
Inactive User Config not found
UTILSRVC.TEAMS_CONFIG_ALREADY_EXIST
Teams Config already exist
UTILSRVC.TEAMS_CONFIG_NOT_FOUND
Teams Config Not Found
PAMSRVC.RULE_CONFIGURE_ALREADY_EXIST
Configuration already exists
PAMSRVC.EMPTY_CONDITION_EXCEPTION
Empty Condition exception
SLFSRVC.INVALID_MANAGER_EXCEPTION
Invalid Manager
SLFSRVC.INVALID_MANAGER
Invalid Manager
SLFSRVC.USER_NOT_FOUND
User not found. Please try again.
WKFLSRVC.SELF_APPROVAL_CONFIG_EXIST
Self Approval config already exists
WKFLSRVC.SELF_APPROVAL_CONFIG_NOT_FOUND
Self Approval config not found
MFASRVC.RESEND_PERIOD_NOT_ALLOWED
Please wait we are enabling resend operation
MFASRVC.RESEND_TIME_EXCEED
Allowed resend attempt exceed please try after some time
ANALYTICS.INVALID_LOG_ARGUMENTS
Invalid arguments
ANALYTICS.UNAUTHORIZED
Unauthorized. Please contact cymmetri administrator.
ANALYTICS.ALREADY_ACTIVATED
Already activated
ANALYTICS.ALREADY_DEACTIVATED
Already deactivated
DATALOGGER.ALREADY_EXISTS
Already exists
DATALOGGER.CONNECTION_FAILED
Connection Fail
DATALOGGER.FORBIDDEN
Please contact system administrator.
DATALOGGER.INVALID_ARGUMENTS
Invalid arguments
DATALOGGER.SYNC_NOT_SUPPORTED
Sync not supported
ANALYTICS.SYSLOG_CONFIG_NOT_FOUND
Syslog configuration not found
ANALYTICS.SYSLOG_CONFIG_TEST_FAILED
Syslog configuration test failed
DATALOGGER.UNAUTHORIZED
Unauthorized. Please contact cymmetri administrator.
REPORT.ALREADY_ACTIVATED
Already activated
REPORT.ALREADY_DEACTIVATED
Already deactivated
REPORT.ALREADY_EXISTS
Already exists
ANALYTICS.CONNECTION_FAILED
Failed to send report.
REPORT.CONTENT_NOT_FOUND
Content not found
REPORT.EMAIL_EXISTS
Email already exists
ANALYTICS.EMAIL_NOT_EXISTS_EXCEPTION
User Email Not Found. Please contact cymmetri administrator.
REPORT.FORBIDDEN
Please contact system administrator.
ANALYTICS.INVALID_ARGUMENTS
Please correct the input and try again
REPORT.INVALID_CRON_EXPRESSION
Invalid cron expression
REPORT.INVALID_FREQUENCY_CONFIG
Invalid frequency config
REPORT.INVALID_REPORT_CONFIG
Invalid report config
REPORT.INVALID_SCHEDULER_TASK_EXECUTION_ID
Invalid schedular task execution ID
REPORT.REPORT_BATCH_TASK_NOT_FOUND
Batch task not found
REPORT.REPORT_EXISTS_EXCEPTION
Report already exists
REPORT.REPORT_NOT_FOUND
Report not found
REPORT.SEND_EMAIL_FAILED_EXCEPTION
Email Sending failed
REPORT.UNAUTHORIZED
Please contact cymmetri administrator.
RISKENGINE.ALREADY_ACTIVATED
Already activated
RISKENGINE.ALREADY_DEACTIVATED
Already deactivated
RISKENGINE.ALREADY_EXISTS
Already exists
RISKENGINE.CONNECTION_FAILED
Connection Fail
RISKENGINE.CONNECTOR_NOT_AVAILABLE
Connector not available
RISKENGINE.FORBIDDEN
Please contact cymmetri administrator.
RISKENGINE.INVALID_ARGUMENTS
Invalid arguments
RISKENGINE.INVALID_RISK_SYNC_TASK_STATUS
Invalid risk sync task status
RISKENGINE.NO_MAPPING_FOUND
No mapping found
RISKENGINE.RISK_CONFIG_NOT_FOUND
Risk config not found
RISKENGINE.RISK_NOT_FOUND
Risk not found
RISKENGINE.RISK_SYNC_TASK_IN_PROGRESS
Risk sync task in progress
RISKENGINE.RISK_SYNC_TASK_NOT_IN_PROGRESS
Risk sync task not in progress
RISKENGINE.UNAUTHORIZED
Please contact cymmetri administrator.
RISKENGINE.UNSUPPORTED_FIELD
Field not supported
RISKENGINE.UNKNOWN
Please contact cymmetri administrator.


