Introduction
In our increasingly digitized world, safeguarding personal and sensitive information is of paramount importance. With cyber threats on the rise, traditional passwords alone are no longer sufficient to protect our digital identities and assets. This is where Multi-Factor Authentication (MFA) comes into play. MFA is a robust security measure that enhances online protection by requiring users to provide multiple forms of authentication before granting access to an account or system.
MFA typically involves three factors:
Something You Know: This is the traditional password or PIN that users have to enter. While passwords alone are susceptible to brute-force attacks or phishing, the combination with other factors adds an extra layer of security.
Something You Have: Users are also required to possess something physical, like a smartphone, smart card, or a security token. This device generates a one-time code, further authenticating the user.
Something You Are: This factor is based on biometric data, such as fingerprints, facial recognition, or retina scans. Biometrics add a high level of security as they are unique to each individual.
MFA offers several advantages:
Enhanced Security: By combining multiple authentication factors, MFA makes it significantly more challenging for cybercriminals to gain unauthorized access. Even if they have a password, they would still need physical access to a user's second-factor device or their biometric data.
Mitigation of Password Vulnerabilities: Since passwords are vulnerable to theft or hacking, MFA helps reduce the risks associated with compromised passwords.
Improved Compliance: In various industries, compliance standards require the implementation of MFA to protect sensitive data, reinforcing its importance in data protection and privacy.
User-Friendly: Modern MFA solutions are designed to be user-friendly, offering a seamless authentication experience through mobile apps or SMS verification.
Multi-Factor Authentication is a critical tool in our arsenal against the growing threats in the digital realm. By combining what we know, have, and are, MFA offers a robust defense, ensuring that only authorized individuals gain access to sensitive information and systems. It's a key element in the ongoing battle to safeguard our digital identities and data.
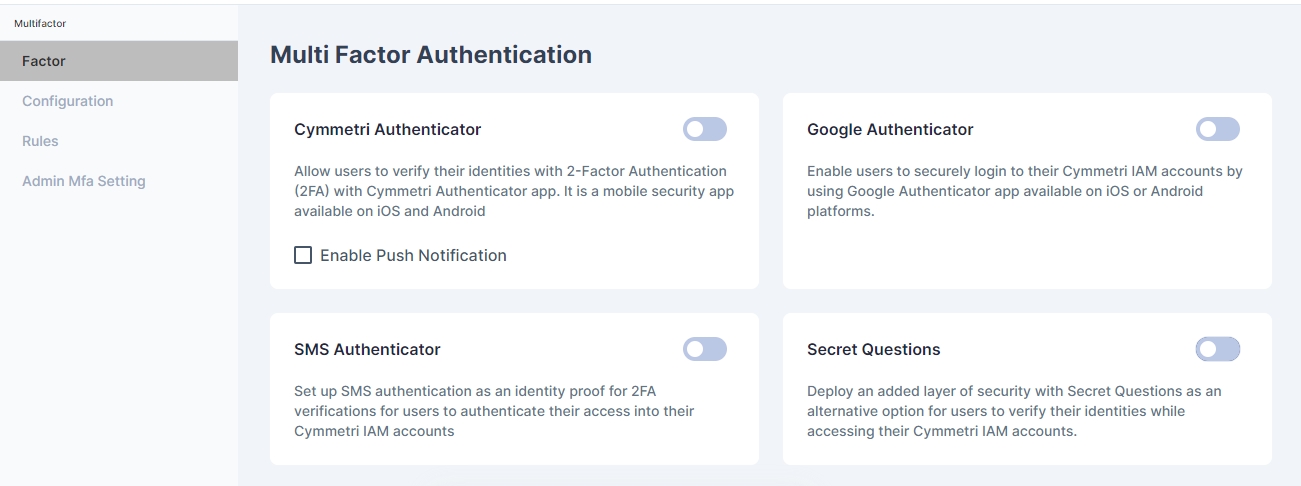
Multi-Factor Authentication is a mechanism used across the Cymmetri platform to deal with second level authentication.Typically employed using off-band mechanisms, Cymmetri allows flexibility by introducing both modern and traditional mechanisms, such as:
Cymmetri Authenticator
Push Authenticator
Google Authenticator
SMS Authenticator
Secret Questions
Accessing Multi-Factor Authentication
Access Multi-factor authentication by going to Products > Multifactor

Next, we select Factor sub-menu
In the upcoming sections we will explore each of these mechanisms.
Was this helpful?
