External Identity Provider Configuration - Azure IDP
Setting up Cymmetri Service Provider for External Identity Provider Configuration
The page here shows how to configure a Service Provider.
Navigate to External IDP in Identity Provider.
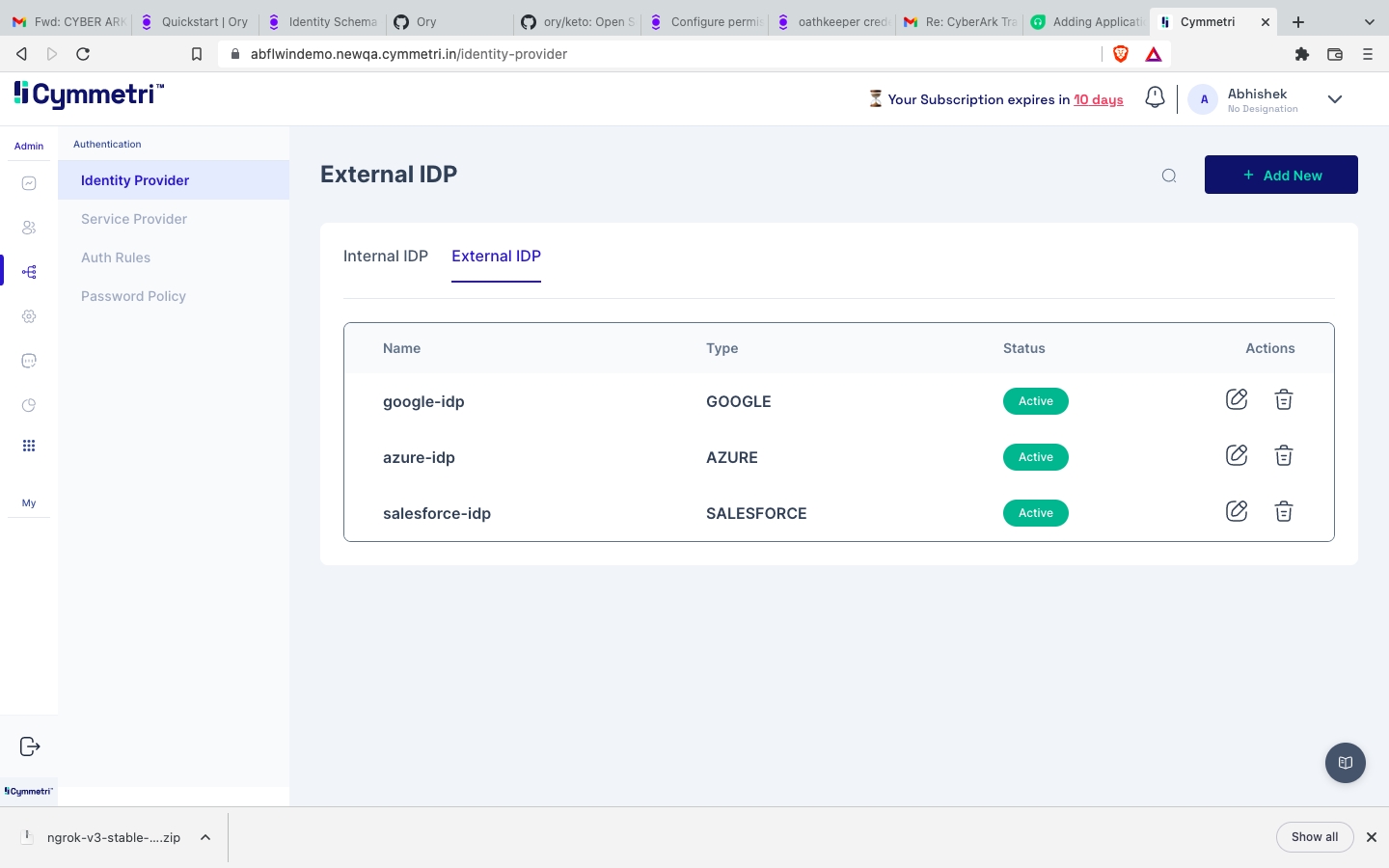
Select Azure-IDP.

Configure Azure AD for Creating Identity provider configuration
Now Login to the Azure portal and select Azure Active Directory.

Navigate to Enterprise applications and select New Application.

Create your own application and enter the name of the application.

Set up Single Sign On after creating the application using SAML.

Click on Edit basic SAML configuration.
Add Identifier (Entity ID) and Assertion Consumer Service URL from the XML file downloaded in step 3 (For Azure, Sign on and ACS URL are the same) and save the configuration.
Download the Certificate (Base64) from SAML Certificates.

Continue configuration of Identity Provider In Cymmetri Administration Console
Copy Azure AD Identifier from Set up, navigate to azure-idp in Cymmetri, and paste it in Entity ID. Similarly, copy the login URL and paste it into the Single Sign On Service URL in Cymmetri.
Replace the text "<host-name>" as the URL of the Cymmetri deployment (e.g., https://aktestidp.ux.cymmetri.in) "aktestidp.ux.cymmetri.in" in the destination field - "https://<hostName>/spsamlsrvc/samlSP/SingleSignOnService" as "https://aktestidp.ux.cymmetri.in/spsamlsrvc/samlSP/SingleSignOnService".
Open the Base64 certificate downloaded in step 12, copy it, and then paste it into the x509Certifcate field in Cymmetri.
Select the created service provider in the Service Provider Id field dropdown and save the changes.

For enabling Azure IDP to be used as an IDP for a specific set of users an Authentication Rule needs to be configured. Here you can see the steps on how to configure Authentication Rules.
Assigning Users
Assigning users to applications in Azure Administration Console to allow users to use Azure as an External Identity provider
Navigate to Enterprise applications and select the application you created in step 8.
Go to Users and Groups, and select Add user/group and add the user.

Configuring JIT provisioning in Cymmetri Administration Console
If JIT provisioning needs to be enabled for Azure AD as external Identity provider, we may set it up using the steps below.
Navigate to JIT in external identity provider and enable JIT Configuration.
The following fields are mandatory in Cymmetri - firstName, lastName, login, userType, displayName, and email.
For Azure JIT configuration, the following mapping needs to be done -
First Name -
Application Field - http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname
Cymmetri Field - firstName
Last Name -
Application Field - http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname
Cymmetri Field - lastName
Login (Username) -
Application Field - http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name
Cymmetri Field - login
User Type -
Application Field - any string
Cymmetri Field - userType
Default Value - <will be one of Employee, Vendor, Consultant>
Display Name -
Application Field - http://schemas.microsoft.com/identity/claims/displayname
Cymmetri Field - displayName
Email Address -
Application Field - http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name
Cymmetri Field - email

In Azure Administration Console
Login to cymmetri using Azure Email Address

The user will be redirected to the Azure portal to enter the Azure credentials.

Once the credentials have been entered properly in the Azure portal, the user will be redirected back to Cymmetri and will be logged in successfully.

Last updated
Was this helpful?
