IGA Policy Violations
Overview
This manual outlines the administration process for managing and handling policy violations within the Cymmetri Identity Governance and Administration (IGA) system. The system provides features such as maintaining a Library of Default Policy Violations, policy simulation, scheduled violation reporting, and autocorrection mechanisms. These features help ensure compliance, mitigate security risks, and maintain proper access control across the organization.
Functional Features
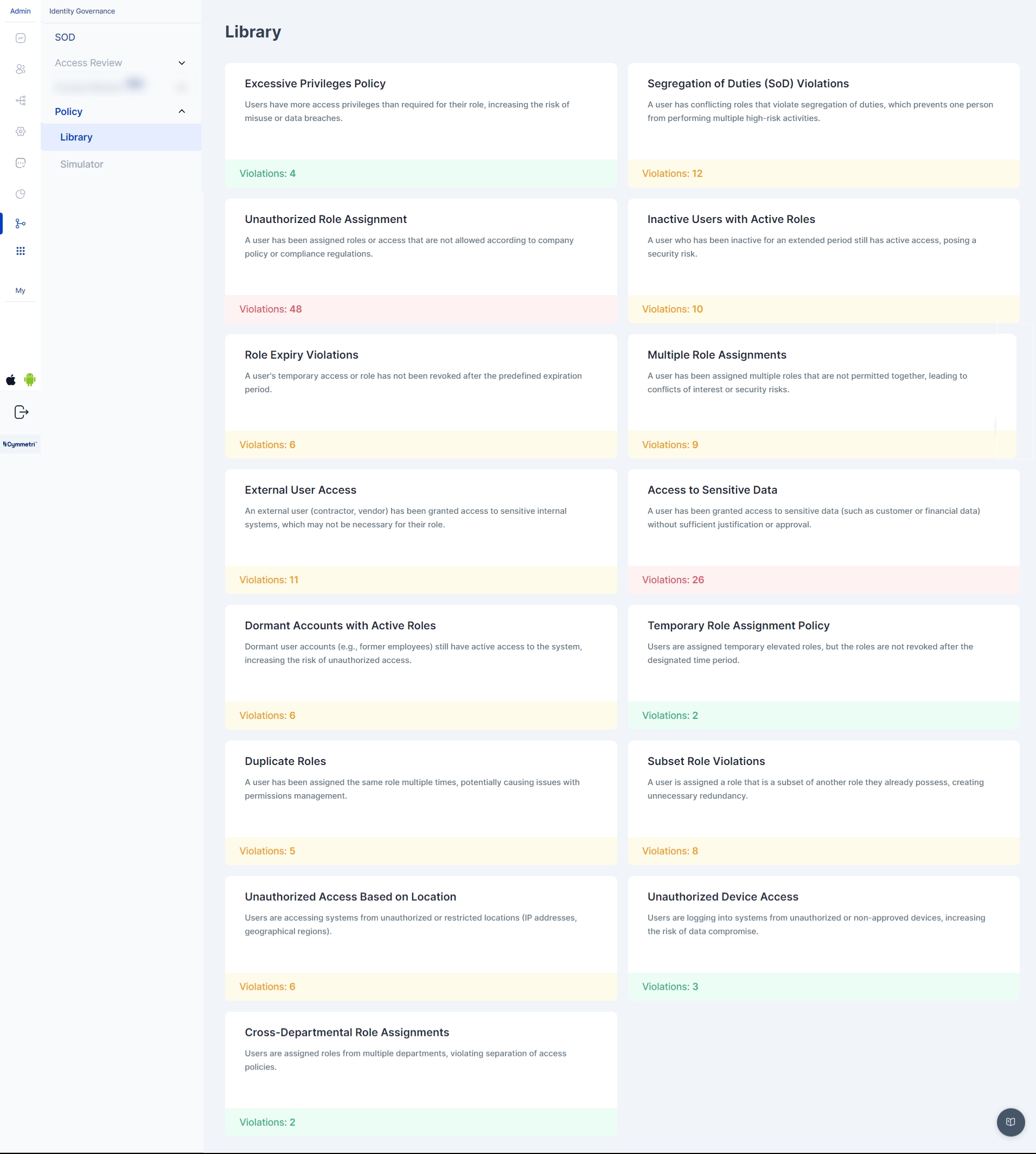
Library of Default Violations
The IGA system maintains a centralized Library of Default Violations, which includes predefined policy violations. These violations are categorized based on typical governance issues, such as excessive access, unauthorized role assignments, or segregation of duties (SoD) violations.
How to Access and Manage the Library
Navigate to the Policy Violations Library under the Governance section.
Review the list of predefined violations (e.g., Excessive Privileges, Segregation of Duties, Unauthorized Role Assignment).
View detailed descriptions of each violation type, including risk levels, sample records, and suggested remediation actions.
Administrator Actions
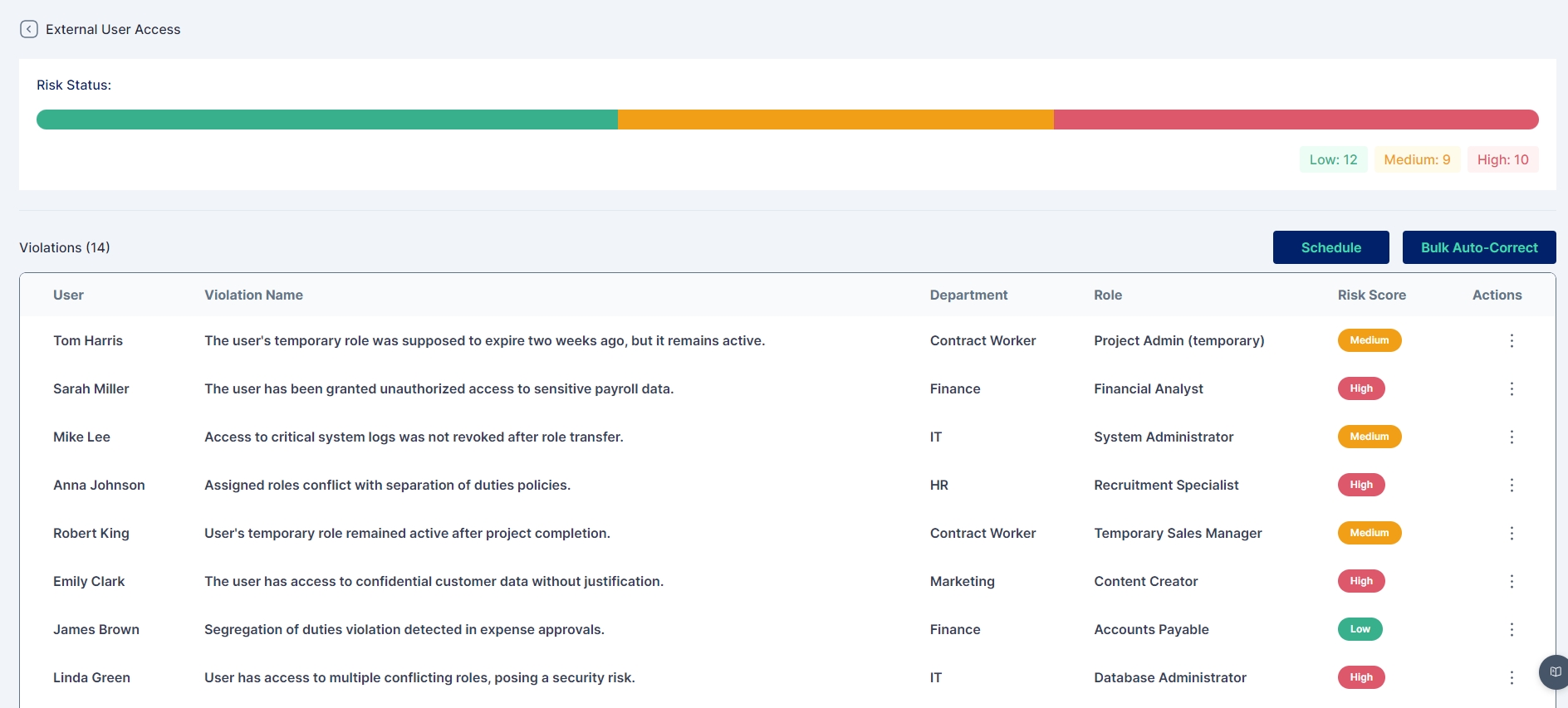
View or export reports detailing current violations.
Modify or update violation definitions based on changes in business requirements.
Add new policy violations to the library, if necessary (refer Designing Policy Violations for custom violations).
Designing New Policy Violations through Simulation
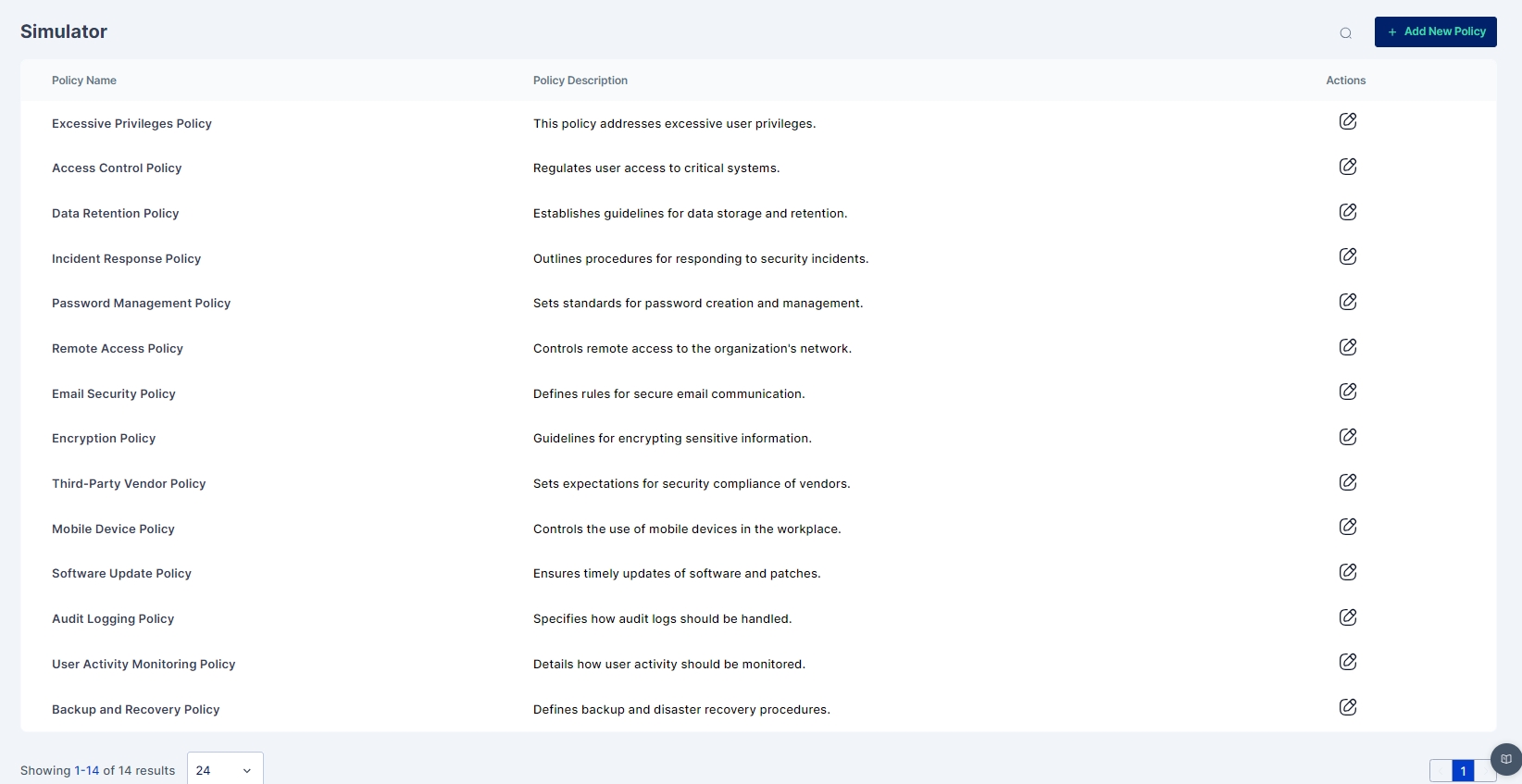
The system allows administrators to design custom policy violations using the built-in Policy Simulator. This feature helps assess potential risks before applying new policies system-wide.
Steps to Design a New Policy
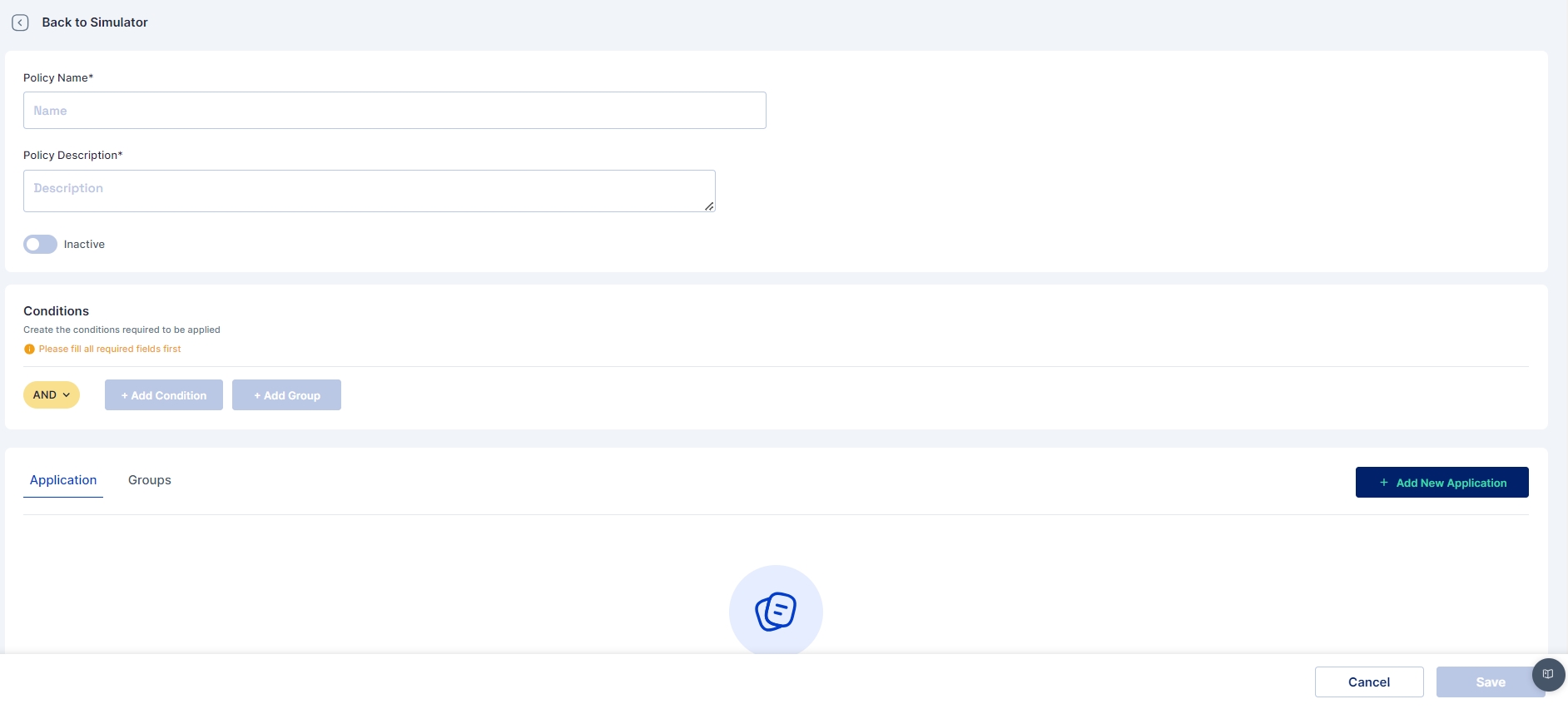
Access the Policy Simulator Navigate to the Policy Simulation section and click on Create New Policy.
Define Policy Conditions Provide a unique name, description, and select the target population. Define conditions like roles, data access, and compliance rules.
Assign Violation Severity Select a Severity Level (Low, Medium, High, Critical).
Simulate the Policy Click Simulate to apply the policy to the current system configuration and view results.
Modify and Re-Simulate Modify conditions and rerun the simulation if necessary.
Save and Enforce Save the policy to the Library of Default Violations and enforce it across the organization.
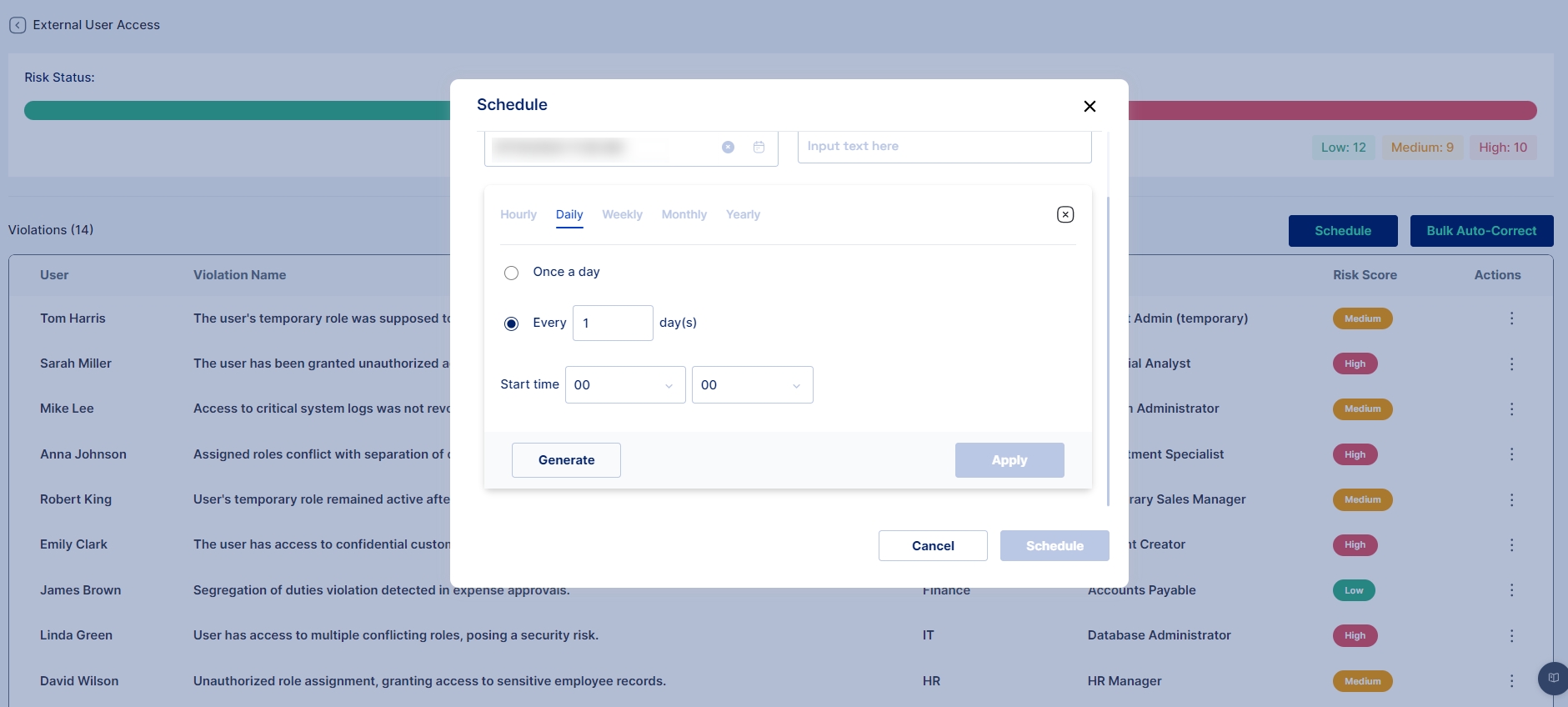
Scheduled Violation Reporting
Administrators can schedule regular reports to monitor policy violations across the organization. These reports provide detailed information on violations, risk levels, and affected users.
Steps to Schedule Reports
Navigate to the Scheduled Reports section under Governance.
Select the Create New Report option.
Choose the Violation Types and Risk Levels to include (e.g., Excessive Privileges, High-risk violations).
Set the report frequency (e.g., daily, weekly, monthly).
Define Email Recipients for the report (e.g., [email protected], [email protected]).
Save and activate the scheduled report.
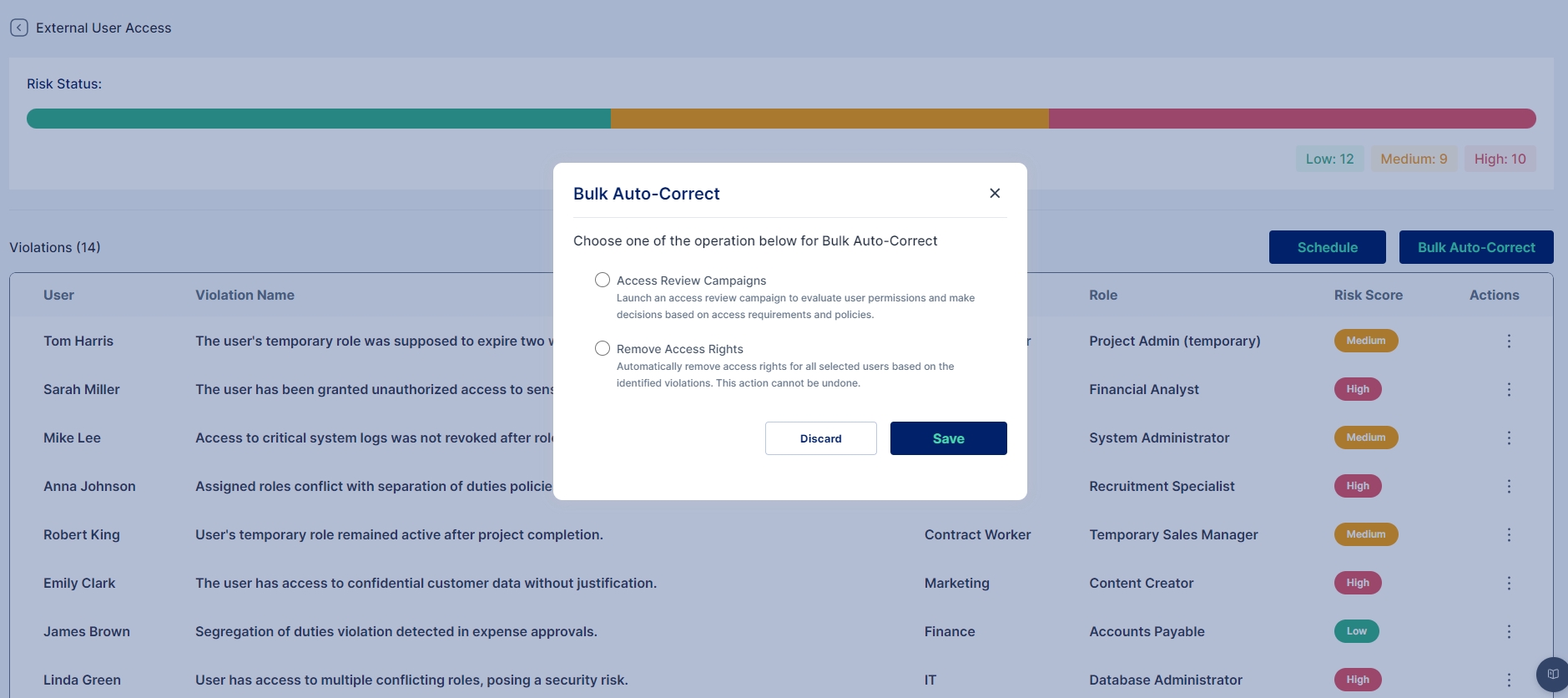
Auto-Correction of Violations
To ensure prompt remediation of critical violations, the IGA system offers an Auto-Correct feature. This feature automates the process of resolving violations by initiating corrective actions, such as access reviews or approval workflows.
How to Enable Auto-Correction
Navigate to the Auto-Correct Settings under the Policy Violations section.
Select the violations that require auto-correction.
Choose the appropriate remediation action (e.g., Access Certification Process, Approval Cycle).
Enable notifications for the administrator to receive updates on actions taken.
Ensure the Audit Log records all auto-correct actions for compliance and reporting purposes.
Was this helpful?
