AMAYA
AMAYA is Cymmetri's no-code/low-code provisioning tool designed to streamline and simplify the provisioning process for users. This tool allows administrators to create, manage, and automate user provisioning workflows without needing extensive coding knowledge.
The AMAYA application within Cymmetri is designed to facilitate the provisioning of users and groups to various target systems through a series of configurable operations. This application supports a variety of operations to manage the lifecycle of user identities, including testing a connection to target system, syncing, searching, creating, updating, deleting, and managing roles.
Application Provisioning
The Application Provisioning interface for AMAYA is divided into several tabs:
User Configuration
Lets you configure the various user identity operations quickly and without coding
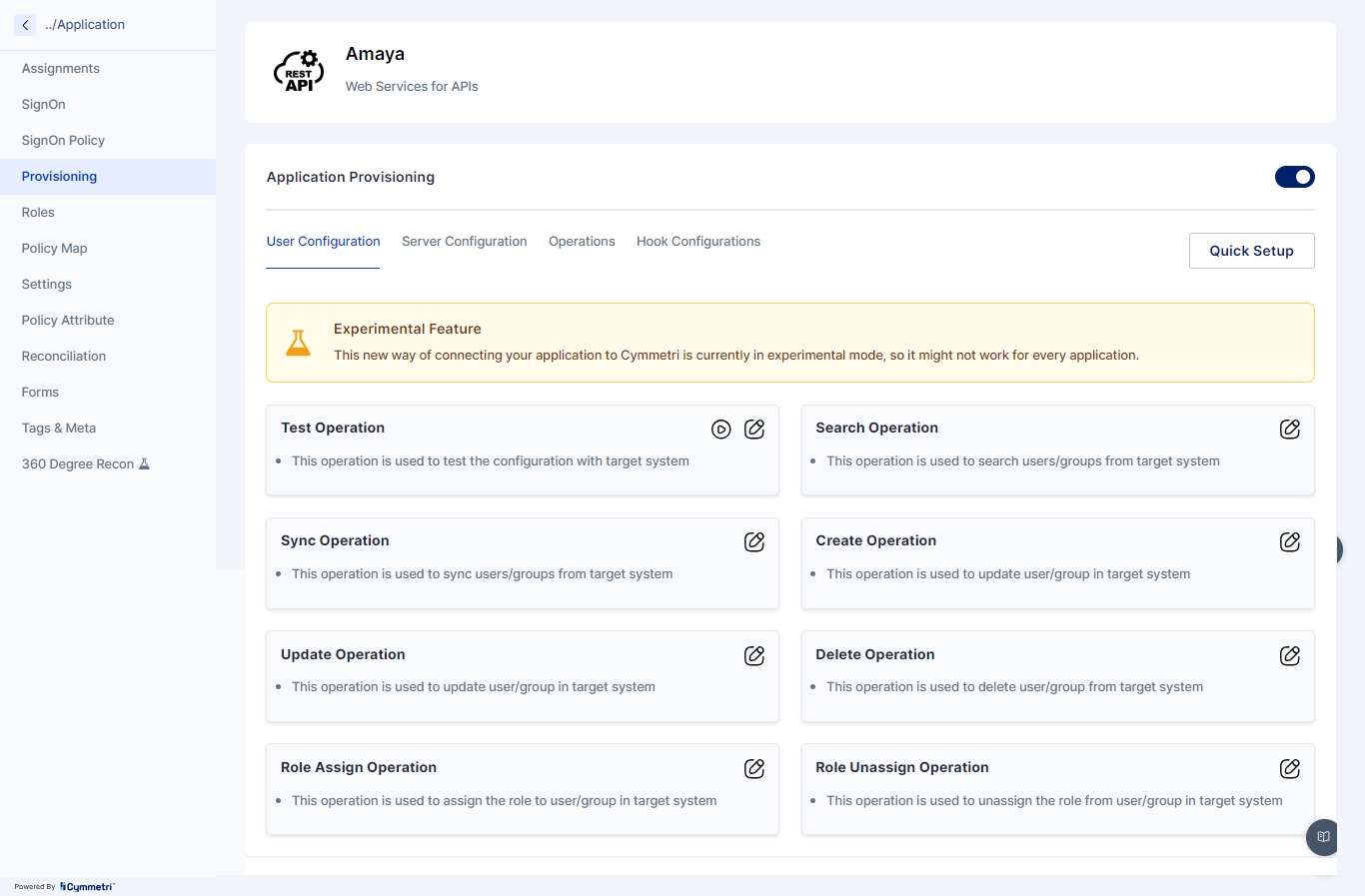
This interface allows administrators to configure and manage how users and groups are provisioned to or from target systems like Slack, Azure, ServiceNow, etc.
AMAYA Key Operations
Test Operation: This operation is used to test the configuration with the target system. It ensures that the setup is correct and that the AMAYA application can communicate with the target system.
Sync Operation: This operation is used to synchronize users or groups from the target system. It ensures that the user/group data in Cymmetri is consistent with the data in the target system.
Search Operation: This operation allows administrators to search for users or groups in the target system, making it easier to find specific entities.
Create Operation: This operation is used to create users or groups in the target system based on the information in Cymmetri.
Update Operation: This operation allows for updating the details of existing users or groups in the target system, ensuring that changes made in Cymmetri are reflected accurately.
Delete Operation: This operation is used to delete users or groups from the target system, removing access or decommissioning identities as required.
Role Assign Operation: This operation assigns roles to users or groups in the target system, helping to manage permissions and access levels.
Role Unassign Operation: This operation unassigns roles from users or groups in the target system, removing permissions as necessary.
Quick Setup with Predefined Templates
The second image shows the Quick Setup screen, which provides predefined templates for popular applications. These templates simplify the process of setting up provisioning by offering pre-configured settings for the following applications:
Slack
ServiceNow
HubSpot
Azure
AWS Identity Center
Administrators can quickly start with these templates, which have standard configurations, and customize them as needed to suit their specific requirements. The search function at the top allows users to find other applications if the needed one is not listed among the predefined templates.
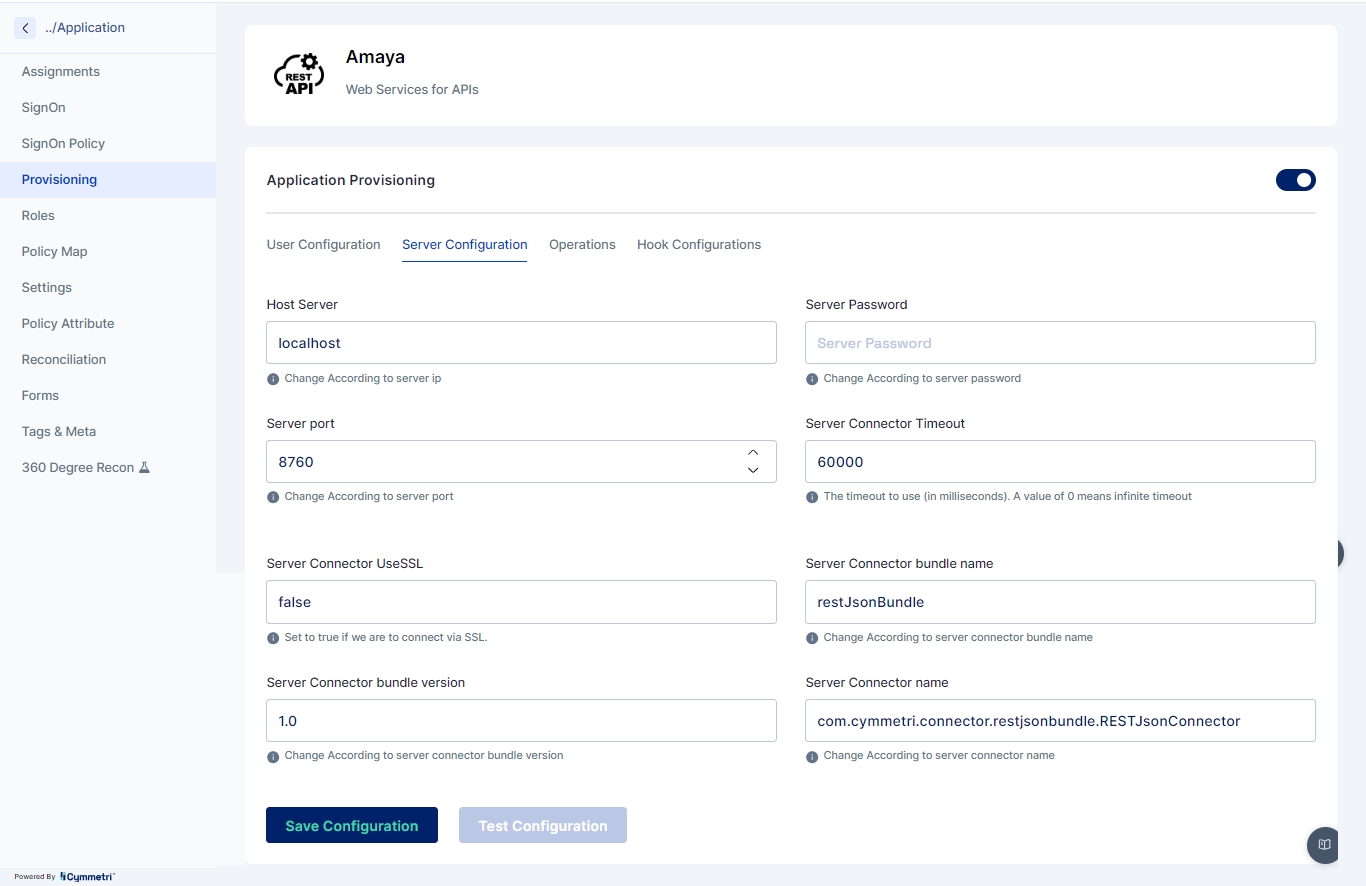
Server Configuration
Consists of configuring the connector server. Enter the IP address of the host server and its password. The rest of the fields come pre-filled with default values; you can change them according to your use case.
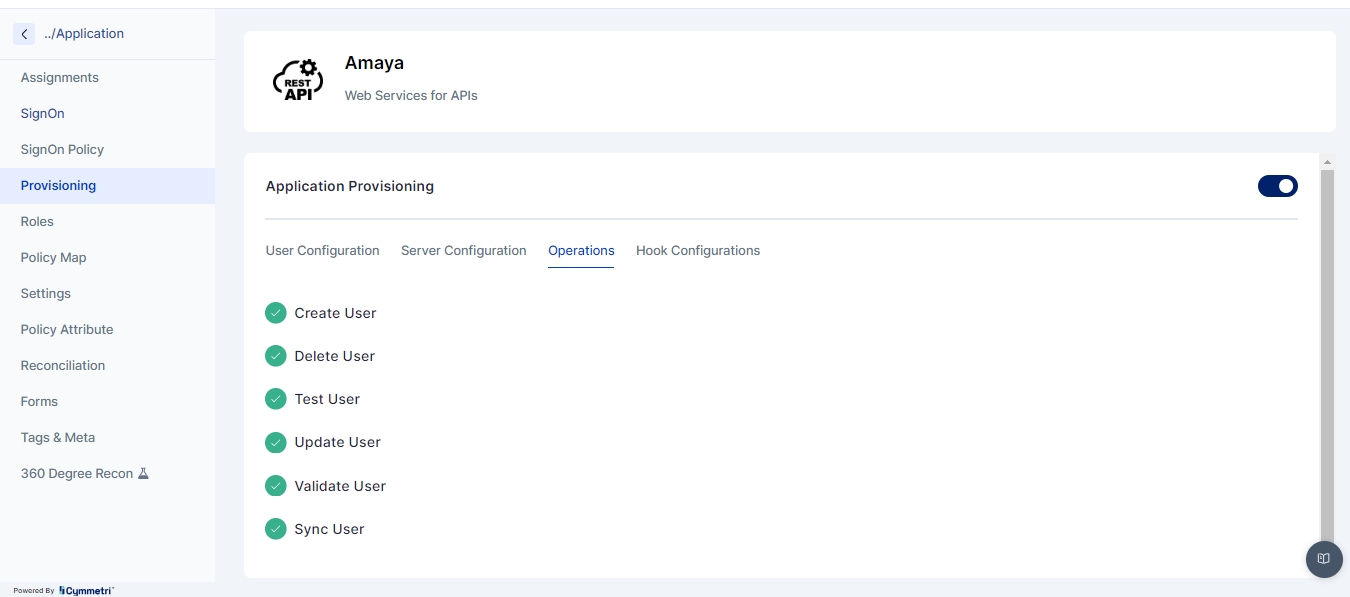
Operations
This tab shows the list of operations supported by AMAYA
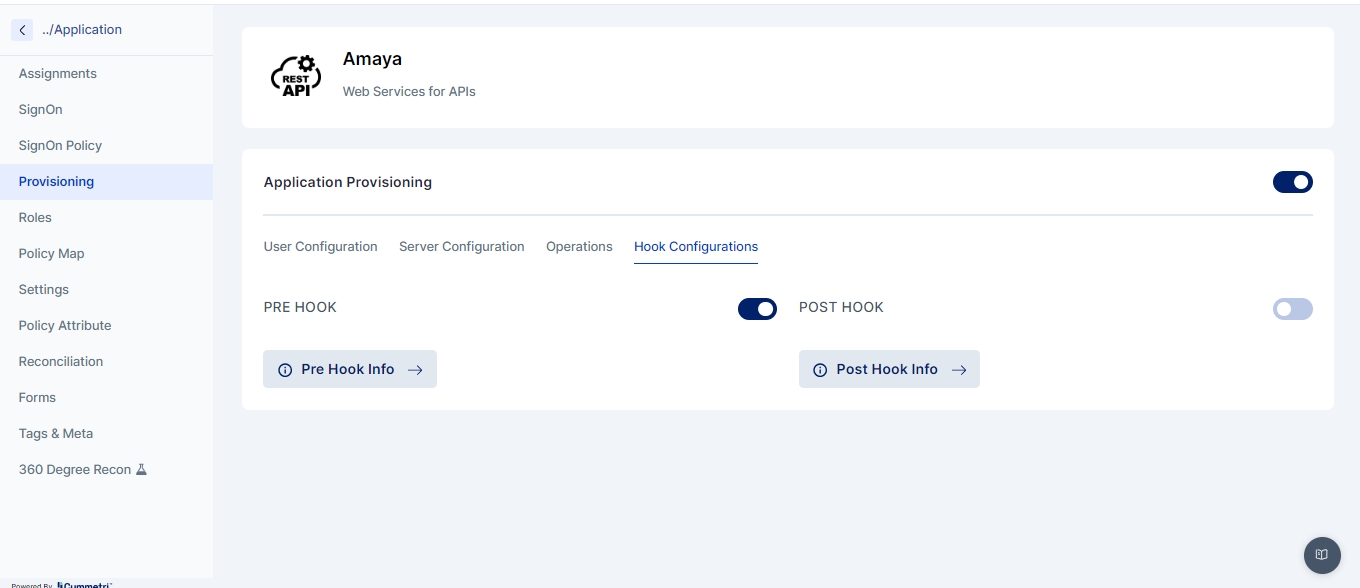
Hook Configurations If the administrator needs to write some custom action before and/or after provisioning the application, that can be enabled by configuring web hooks as shown in the Hook Configuration. The configuration supports a PRE and a POST HOOK for triggering custom code before and/or after provisioning of the application. Refer to webhooks here
Was this helpful?
