Active Directory (AD) Provisioning
Pre-requisites:
Make sure you have the following information before you proceed further:
Cymmetri login credentials
Access to IIS (Internet Information Services) to install certificates.
Access to Windows Certificate Services
Active Directory Essentials:
Server hostname and password
OU (Organisation Unit) name, if any
SSL ports need to be enabled on your side
Export the CA Certificate from Active Directory and import it into the Connector Server.
Make sure the certificate is installed on the Connector Server
Step 1 - Configure your Active Directory Certificate and export it to Connector Server
Exporting your Active Directory certificate to the Connector Server is a necessary and crucial step. This ensures that the Active Directory and Cymmetri Identity Server can communicate over LDAPS (LDAP over SSL). For this to happen, LDAPS requires a properly formatted certificate installed in your Active Directory Domain Controllers. Please refer to this link and follow the same steps: https://www.manageengine.com/products/active-directory-audit/kb/how-to/how-to-install-ssl-certificates-in-active-directory.html
Once the certificate has been imported per the above instructions, you must restart the application to apply the changes made.
Step 2 - Add a new Active Directory application to Cymmetri
Navigate to the Identity Hub on the left navigation bar and click the Applications tab. You will see a list of existing applications.
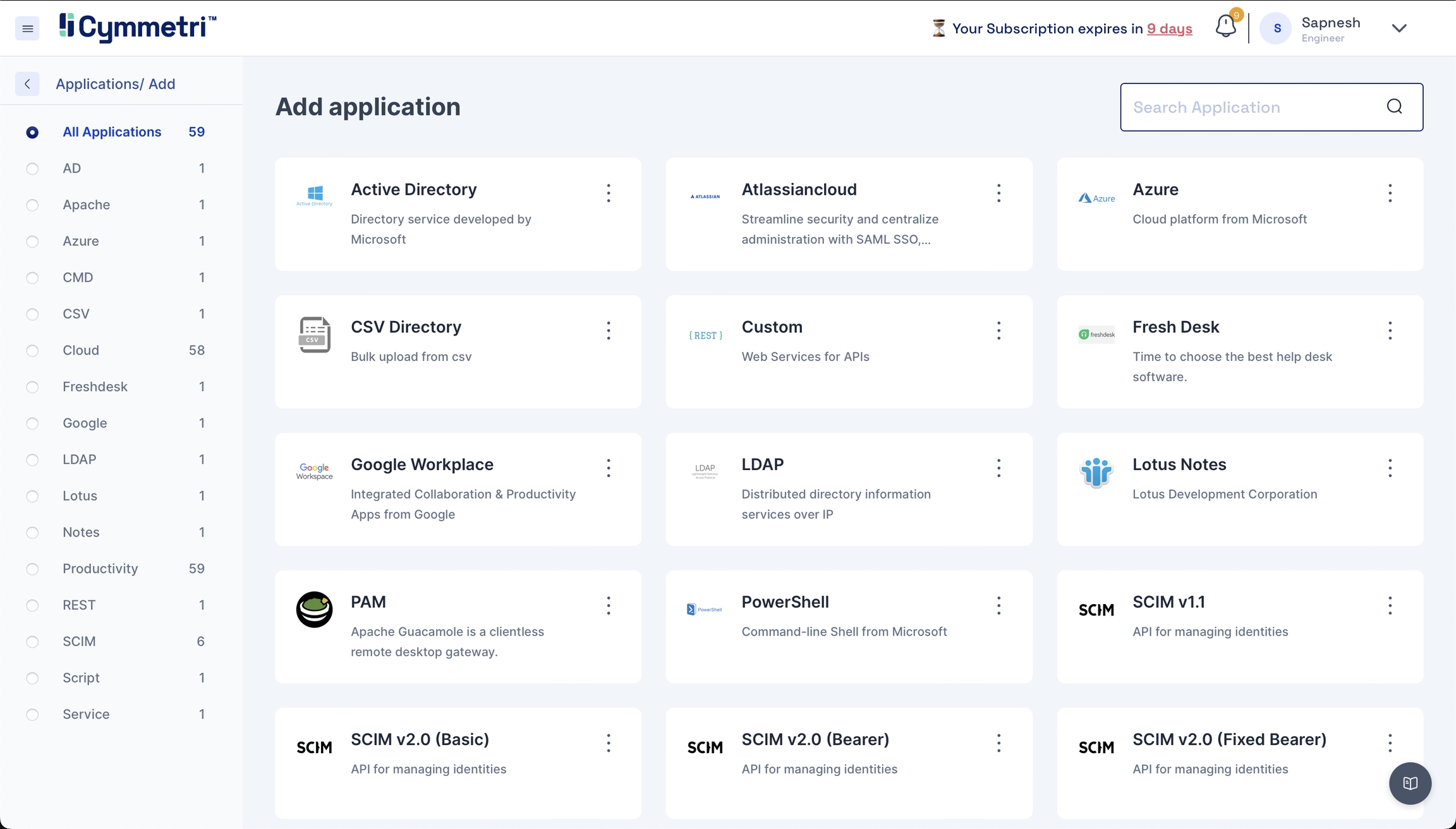
Click 'Add New', and you will find the entire list of all available applications.
Search for Active Directory on the top right and click on it. You should see the Active Directory application sidebar on the right.
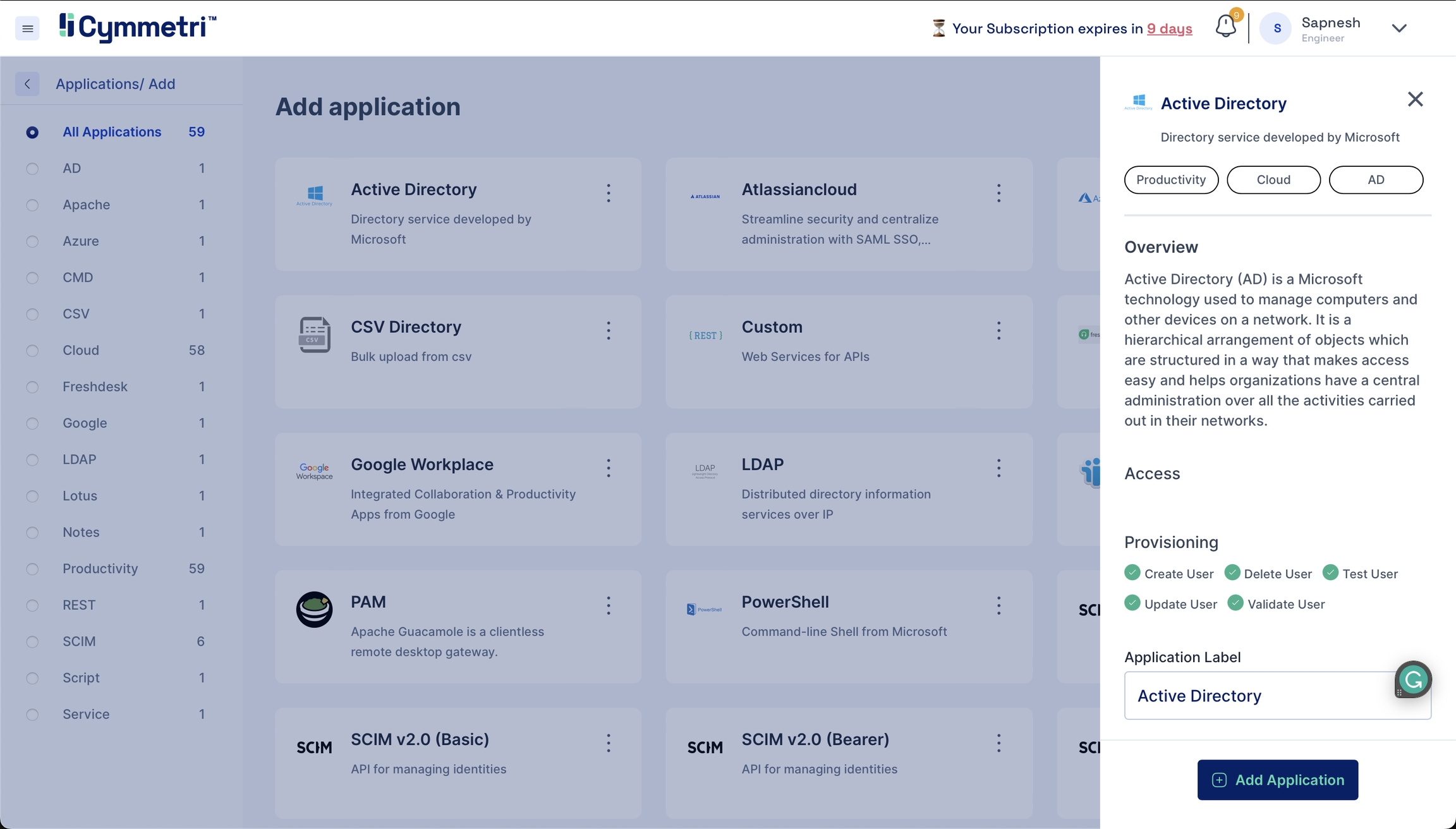
The
Application Labelhas a default name for the Active Directory application and can be changed according to your choice. Click 'Add Application' from the bottom right to add the Active Directory application to your Cymmetri profile.
You have now added an Active Directory application to Cymmetri.
Step 3 - Adding Policy Attributes
After adding the Active Directory, the 'Configure Now' button is enabled. Click this button to start setting up your Active Directory application.
Define which attributes should be fetched from your Active Directory. You can do that by going to the Policy Attribute section.
Here below are shown some Active Directory attribute descriptions
CN
Common Name/ Display Name
RDN
Relative Distinguished Name - An RDN is the relative portion of a Display Name (DN).
SN
Surname
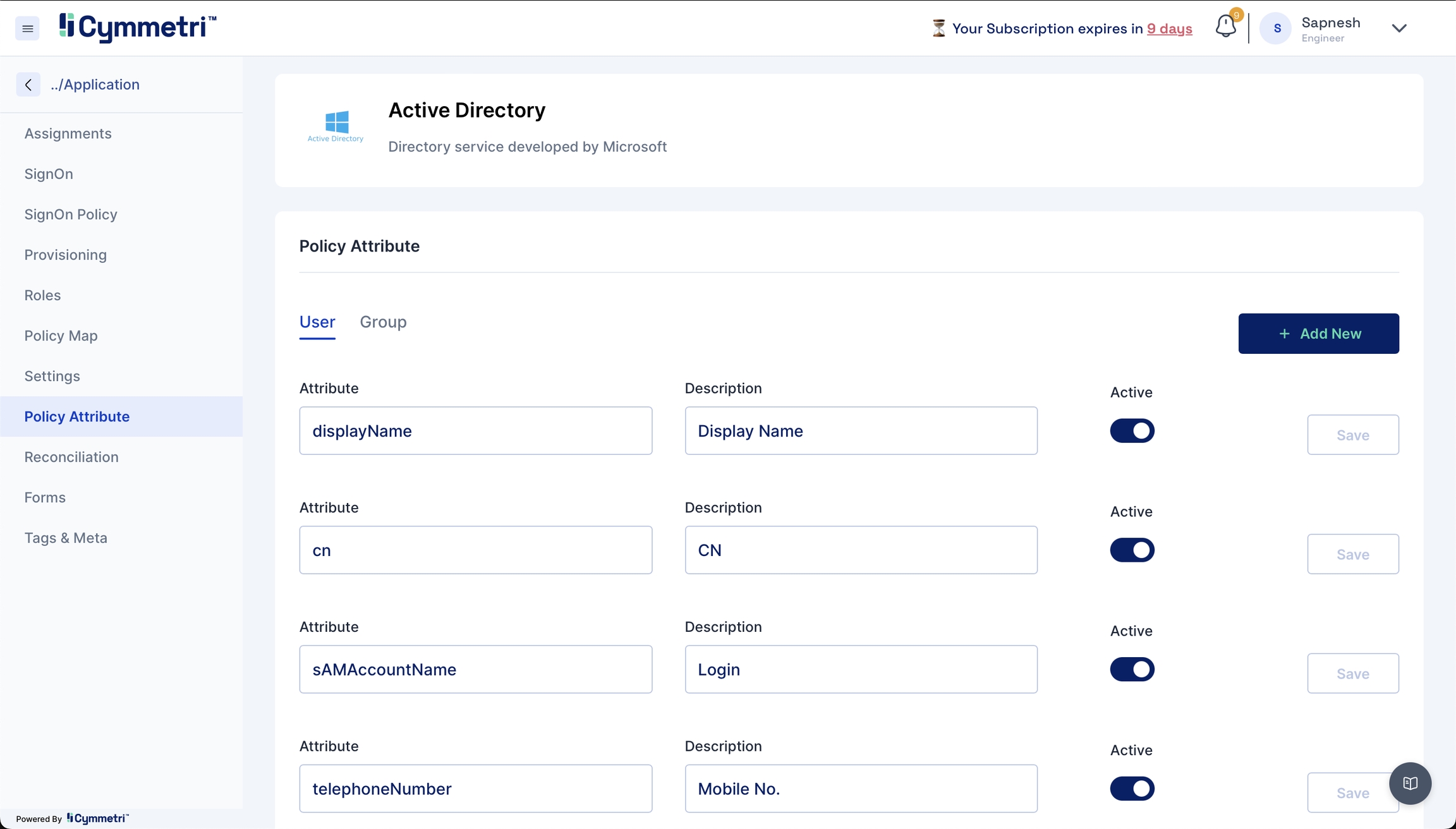
Policy Attributes - Policy attributes are user attributes (field names) in the Active Directory.
The policy attribute table is prefilled with standard Active Directory Attributes by default. Please verify if it works for you. If not, follow the below mappings for the provisioning to work.
telephoneNumber- mobilesAMAccountName- logingivenName- firstNamemail- emailsn- lastNamecn- firstName
2.1 Adding new attributes
If the standard list does not contain the attributes you want to include, you can add new attributes by clicking the 'Add new' button on the right.
Fill in the attribute name, and description and click Save.
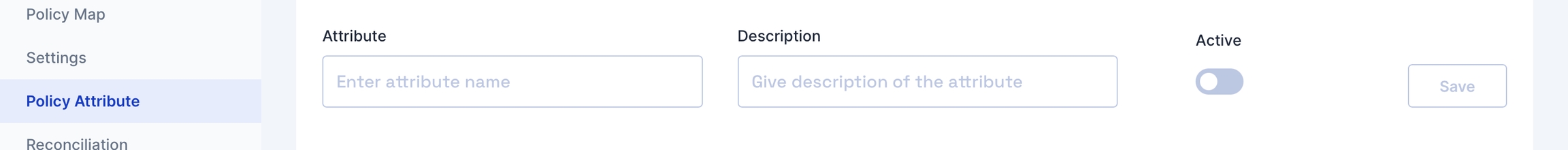
Also, toggle the Active switch to enable this new attribute.
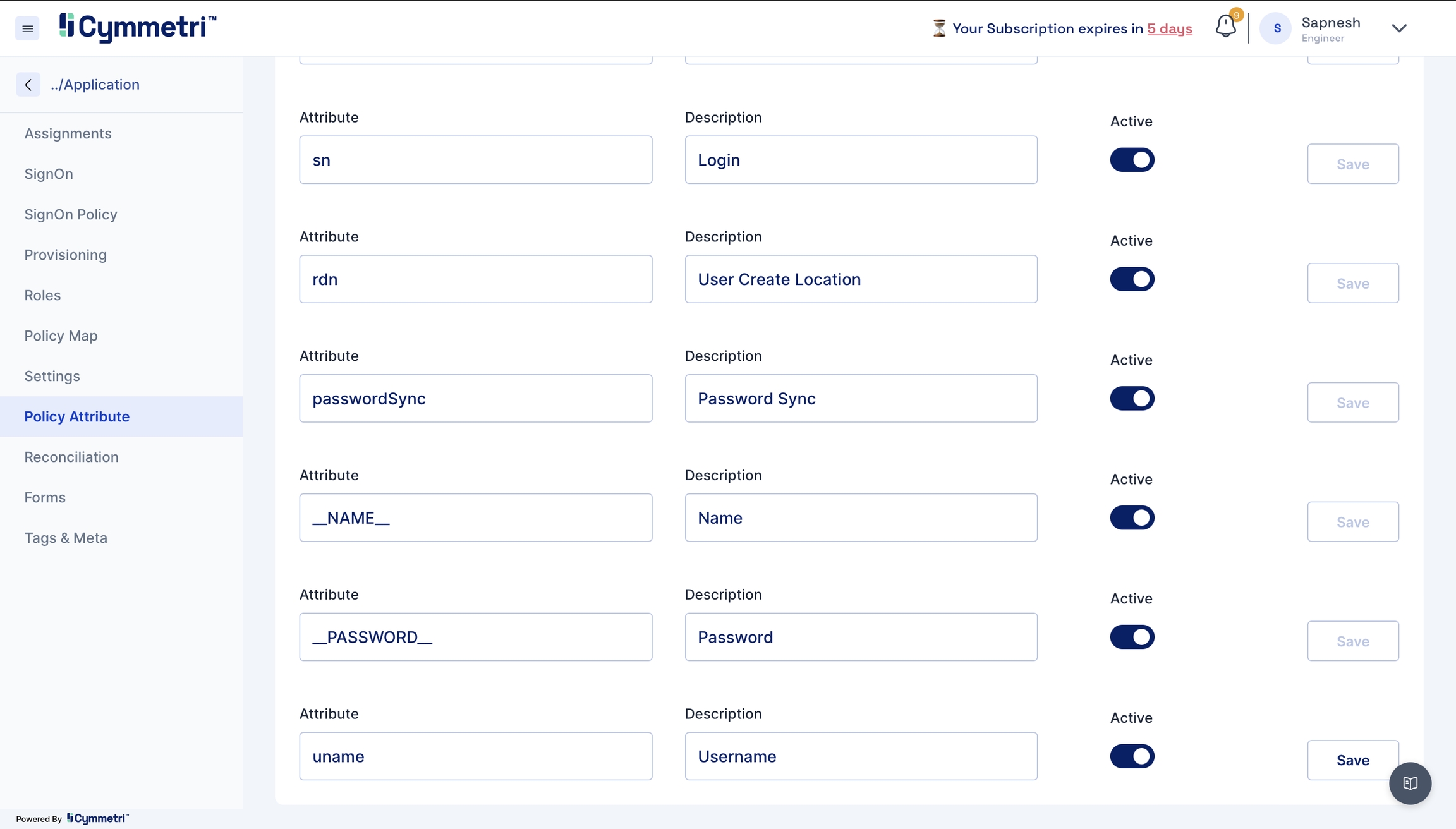
Besides the present policy attributes, you need to add a custom attribute in case you're going for group provisioning, i.e. memberOf attribute.
Step 4 - Map your Active Directory Attributes to Cymmetri
Now that you've defined what attributes to fetch from Active Directory, you will map these to Cymmetri user attributes.
On the same window, navigate to the policy map in the left navigation bar.
Policy Map - Mapping of Cymmetri and Active Directory attributes.
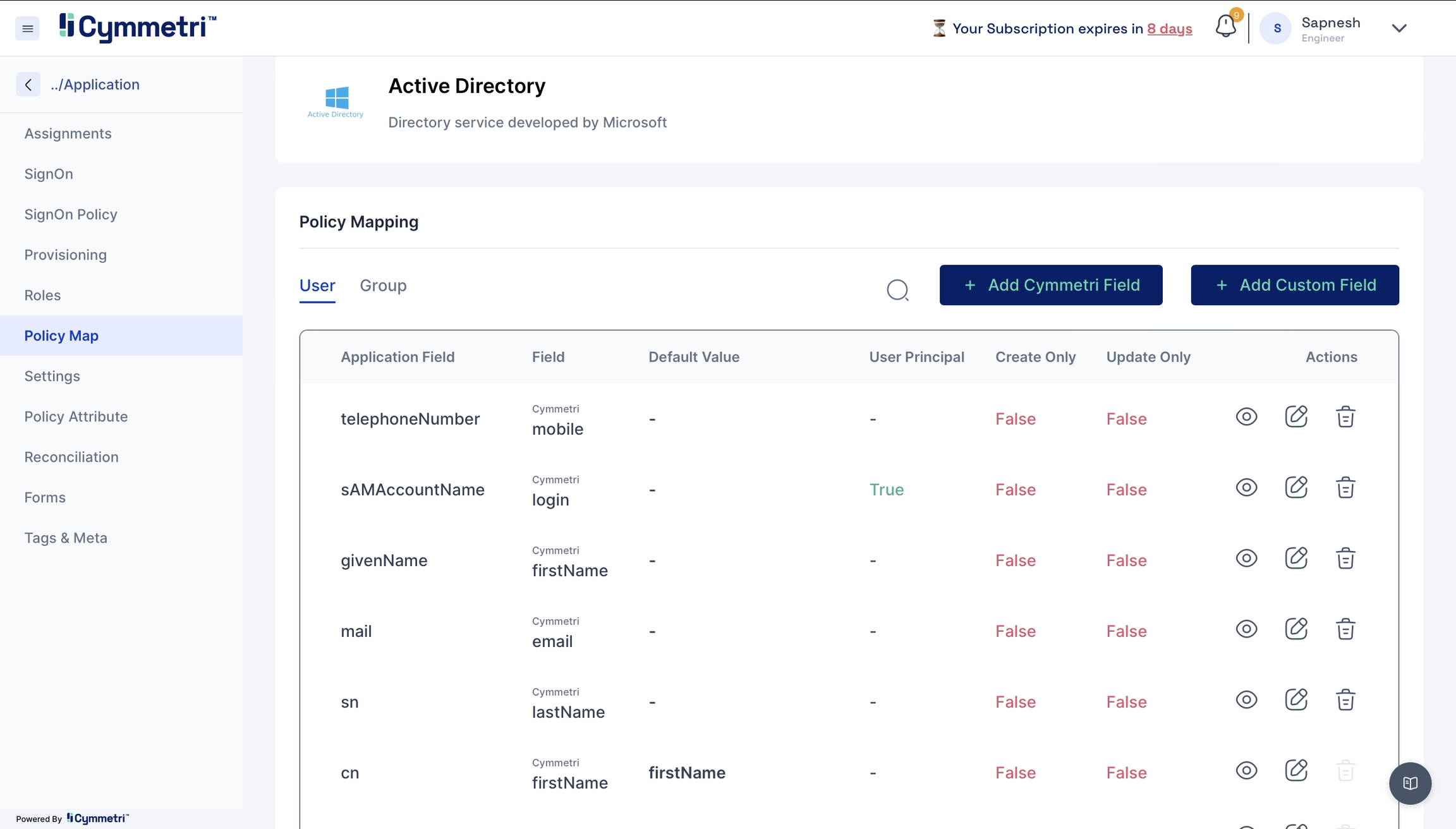
You will see that the attributes are set to
Falseby default. Our first step in the mapping process is to enable the attributes for syncing.Click on the edit button next to the 'Application Field' name.
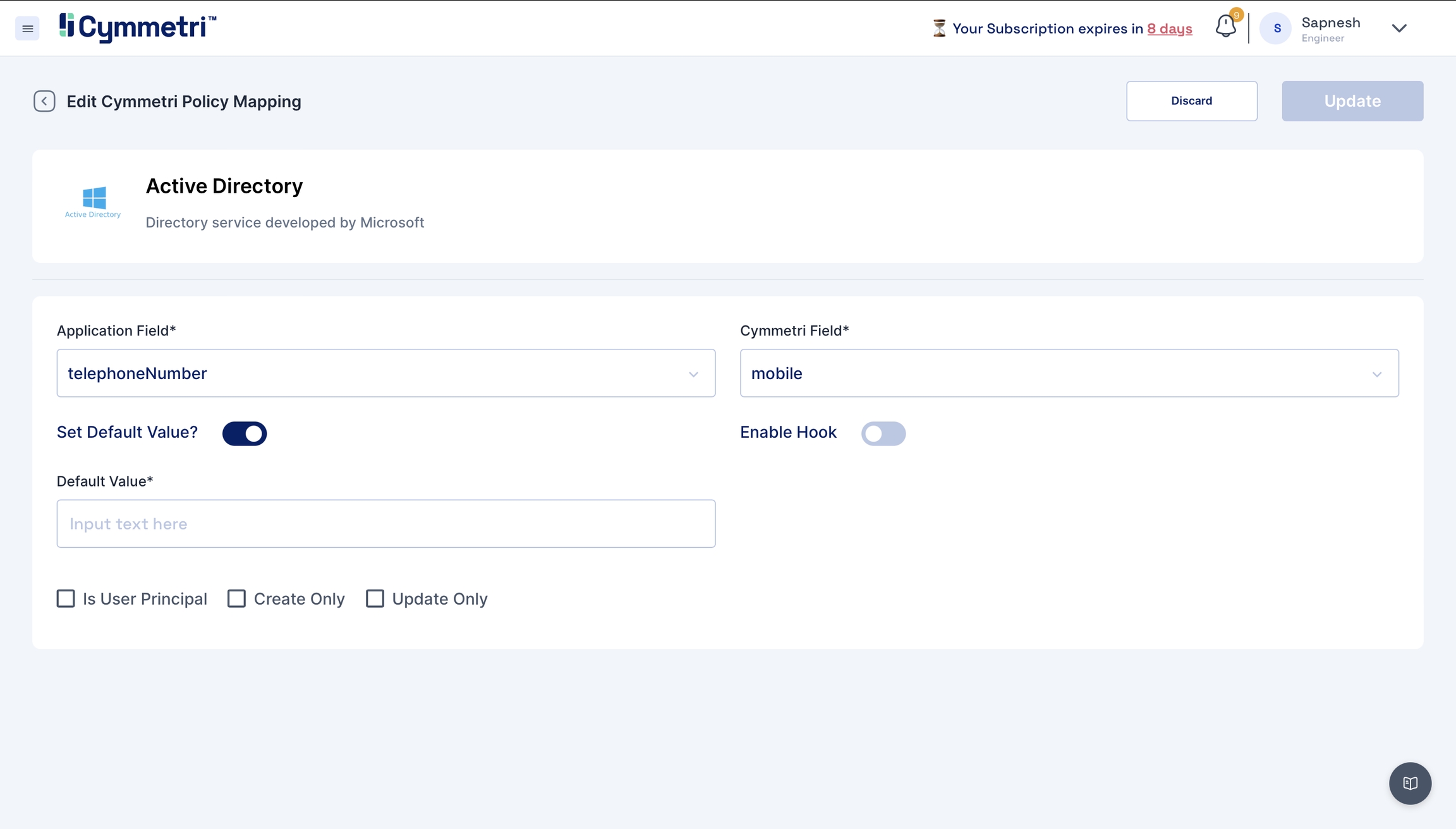
The 'Application Field' indicates the Active Directory field name, and the 'Cymmetri Field' indicates the Cymmetri field name.
To map the attributes, we need to sync the attributes on create and update only. Hence, these checkboxes need to be checked.
The 'Set default value' field accepts the default value you enter here if the field is empty in Active Directory.
Next, click on the 'Update' button.
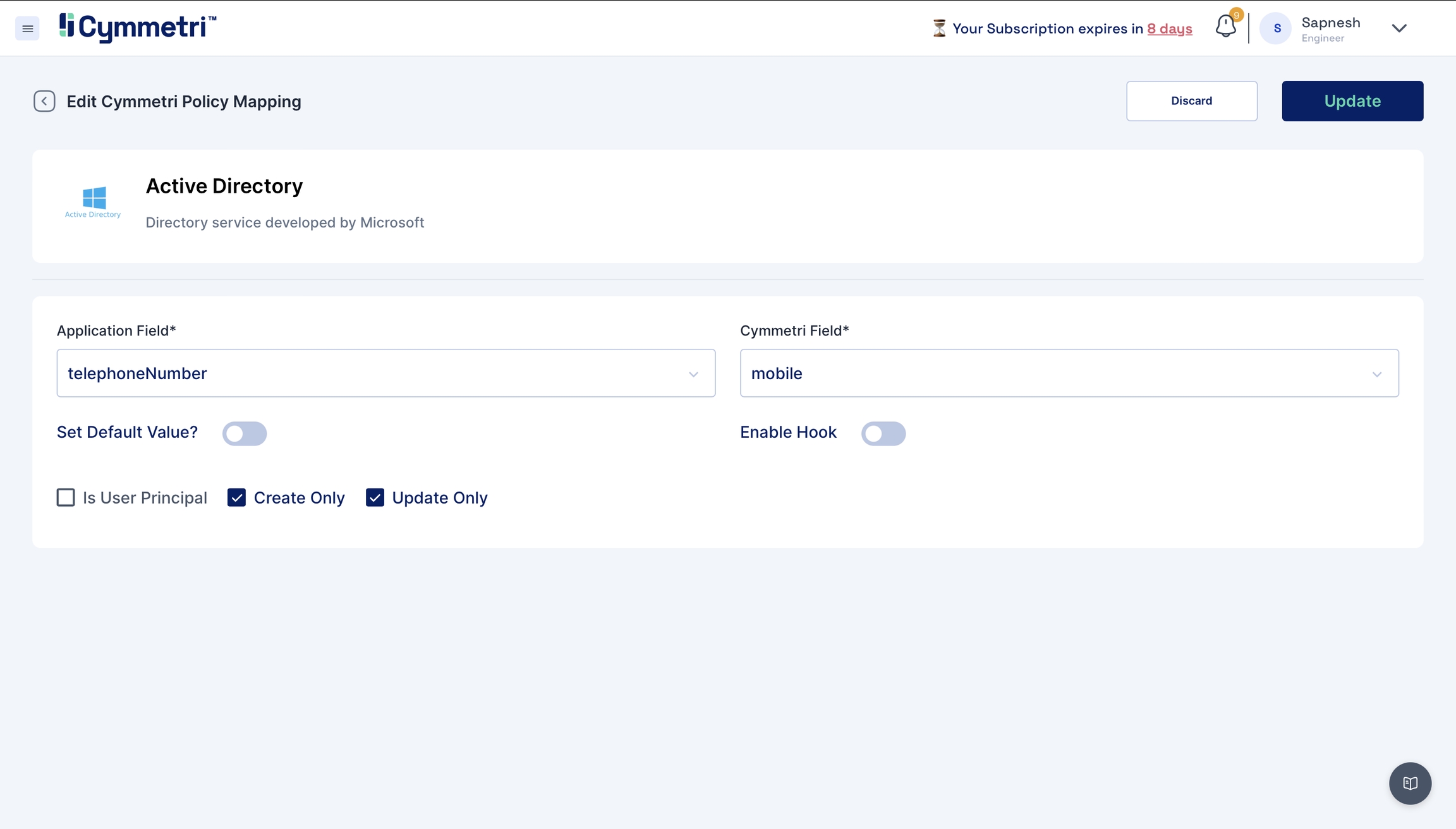
Similarly, repeat this for all attributes.
One exception is the
sAMAccountNamefield. The 'Is User Principal' checkbox is enabled by default because it is the primary key (unique data) on the Active Directory side, andloginis the primary key on Cymmetri side; leave it checked.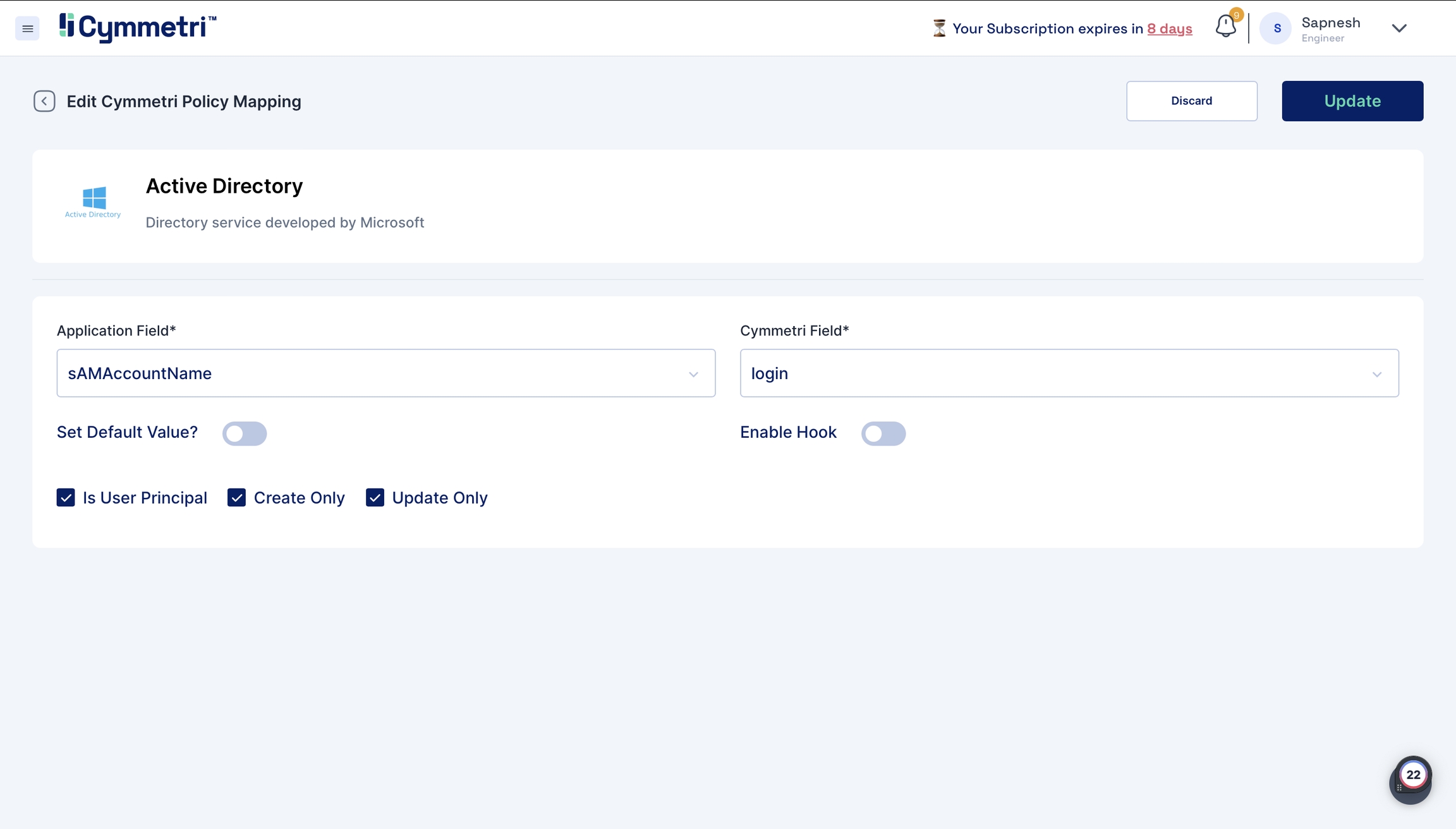
Some important policy map fields which need to be declared in the policy map are as follows.
__NAME__
Users Display Name
__PASSWORD__
Users password
sAMAccountName
Unique login attribute
cn
Unique login attribute (specific to user)
rdn
Used to pass the OU (Organization Unit) path
If any attribute is missing from the policy map but present in your policy attribute. Add it by clicking the 'Add Cymmetri Field' and follow the same steps to map it to the appropriate field.
If you want to add a new field that is not present even in Cymmetri, click on the 'Add Custom Field' button. For group provisioning, the
memberOfattribute must be configured with thememberOfattribute from the custom attribute.
Hook Configuration
Every organization has its own custom implementation scenarios such as duplicate checks for login id, emails and displaynames; similarly provisioning to specific AD OUs based on various conditions. Hooks allow to transform the data and execute the validation rules as per the custom implementation scenarios.
Step 5 - Configure the Connector Server
The connector server is a tool that provides different connectors that enable various provisioning operations from different sources to Cymmetri. Below you may see that Cymmetri supports all the various lifecycle operations needed to seamlessly perform various user operations.

In our case, we will prepare the connector server to work with the Active Directory source.
Click Provisioning from the left navigation bar and enable application provisioning by sliding the slider button.
Once you enable the application provisioning, you must take care of two configurations to successfully provision Active Directory data to Cymmetri.
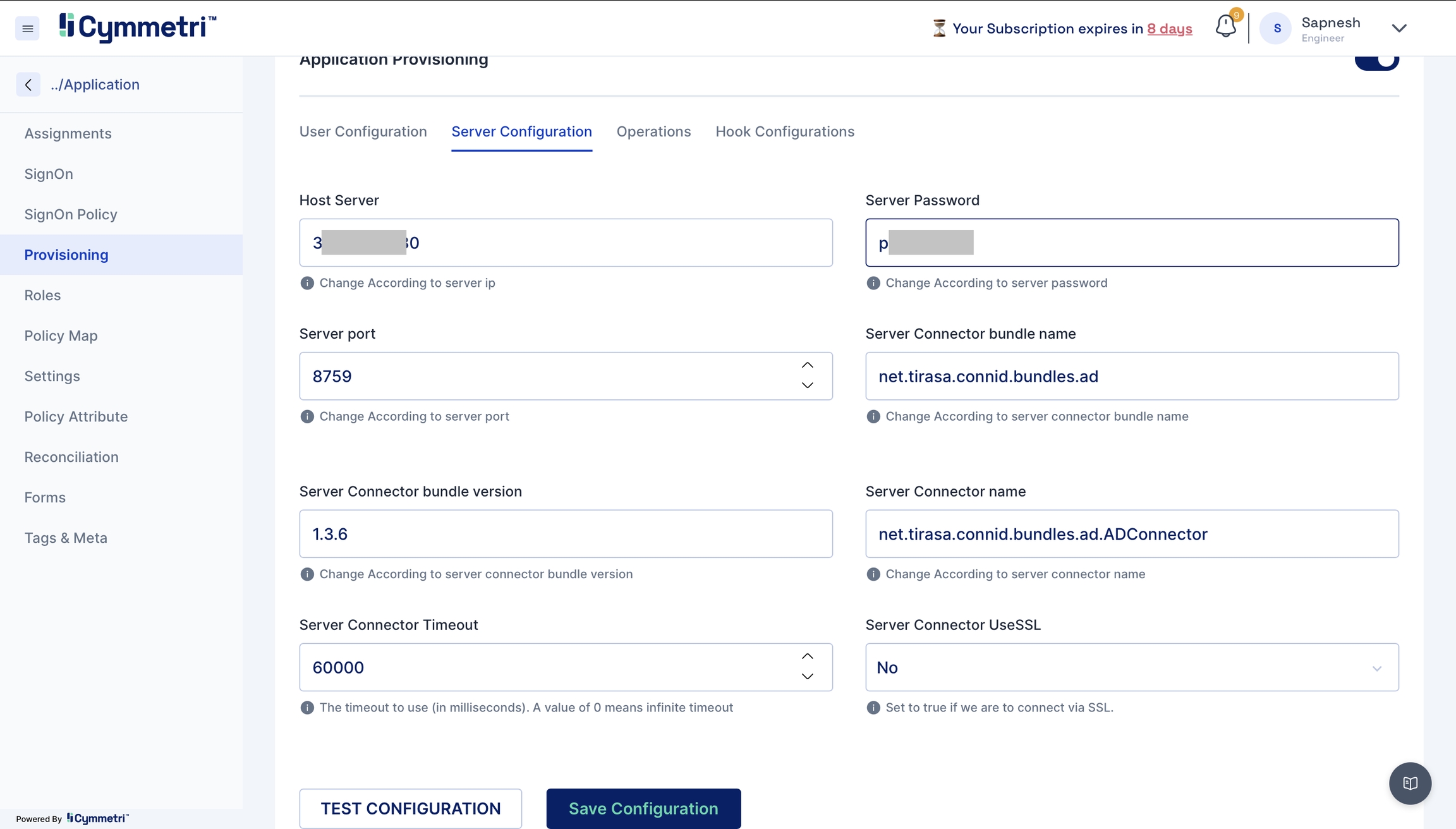
Server Configuration - Consists of configuring the connector server.
Enter the IP address of the host server and its password. The rest of the fields come pre-filled with default values; you can change them according to your use case. Next, click on the save configuration button.
Host server
The IP address of the host server
Server port
Port of the host server
Server Password
Host Server password
Server connector bundle version
Version number of the connector server bundle
Server connector bundle name
Name of the connector server bundle
Server connector name
Given name of the connector server
Server Connector Timeout
Timeout of the connector server in milliseconds
Server Connector UseSSL
Connector server SSL configuration
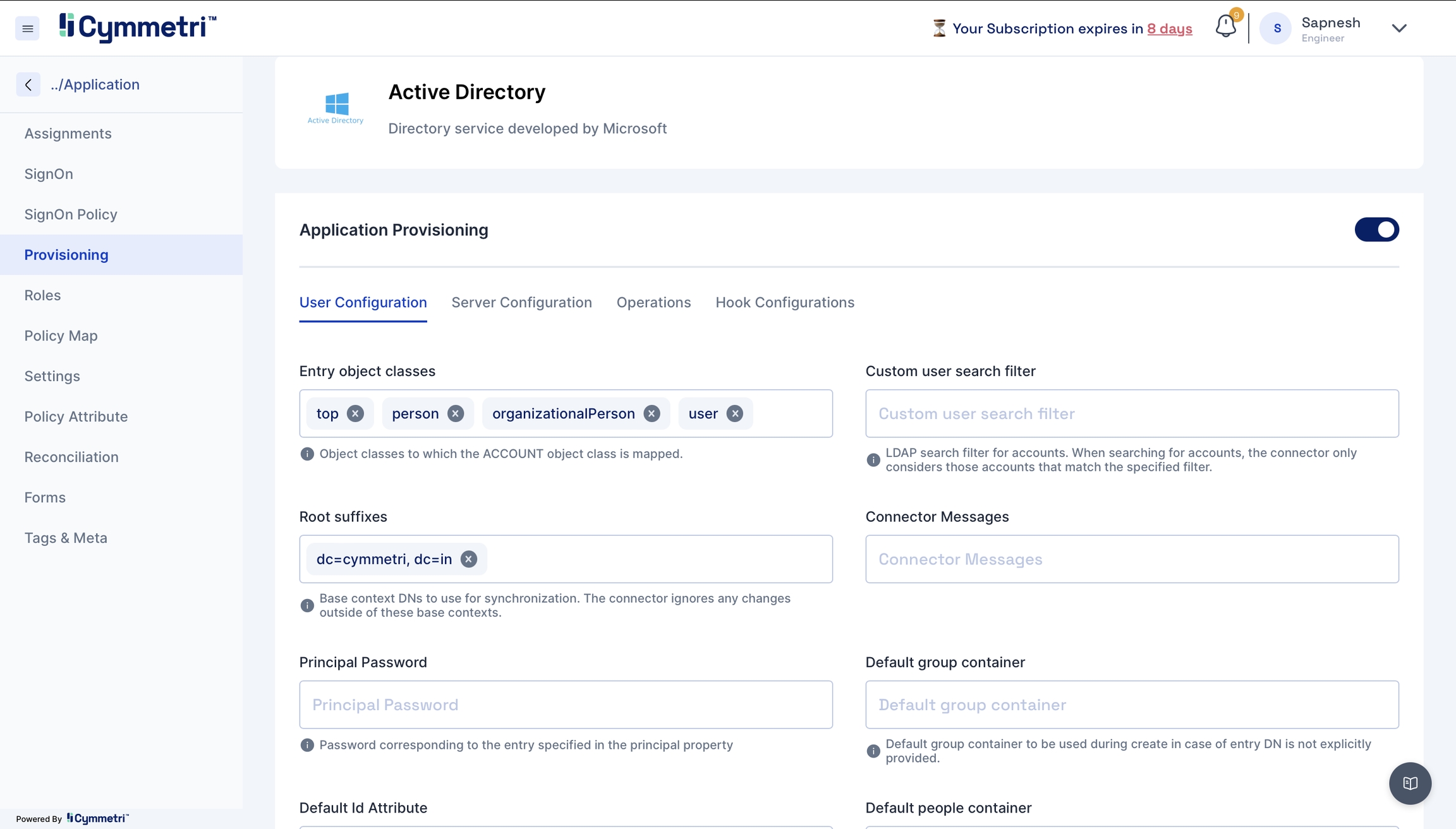
User Configuration - Consists of all user settings like domain name, search filter, etc. We can also configure an OU (Organisational Unit) in this window.
Entry object classes
Object classes to which the Account class is mapped
Root suffixes
Display names used for Active Directory synchronisation to Cymmetri, such as domain controller name
Principal password
Admin password to connect to Active Directory
Default id Attribute
Default attribute Id
Custom user search filter
Search filter used to search accounts
Connector messages
Custom connector messages
Default group container
Default group container can be used during create operation in case of entry DisplayName is not explicitly mentioned
Default people container
Default people container can be used during create operation in case of entry DisplayName is not explicitly mentioned
Group owner reference attribute
Group attribute referencing (by DisplayName) the users members of a group
Custom group search filter
User search filter for groups
Group search scope
Choose object, onlevel or subtree
Server hostname
Active Directory server hostname that would connect to Cymmetri
Conservative membership policy
Conservative management of assigned groups. The groups already assigned to an user on Active Directory will not be removed.
Memberships
Groups to identify users to synchronize. The connector ignores any changes about users not member of indicated groups.
Verify memberships in OR
Indicate if specified memberships must be verified using 'OR' logical operator.
Object classes to synchronise
User object classes to synchronise. The connector ignores any changes if it cannot find modified entry object classes in this property.
Page size
Get users from Active Directory with the provided size
Pageable result
Get users from Active Directory with the provided size pageable result
Server port
Port of the Active Directory connector server
Principal
Admin username of the Active Directory
Permit password update only
Permit password update only.
Create/delete operation will be denied, while other attributes update requests will be ignored.
Retrieve deleted groups
Indicate if deleted groups must be synchronized also.
Retrieve deleted users
Indicate if deleted users must be synchronised also.
SSL
True if the SSL certificate is configured
Trust all certs
Indicative if all server certificates can be trusted
UID attribute
Unique Identifier Attribute
Base context for user entry searches
Display the Name of OU (Organization Unit), Root domain or Root controller required for user entry search
User search scope
The scope could be a subtree or object for user search
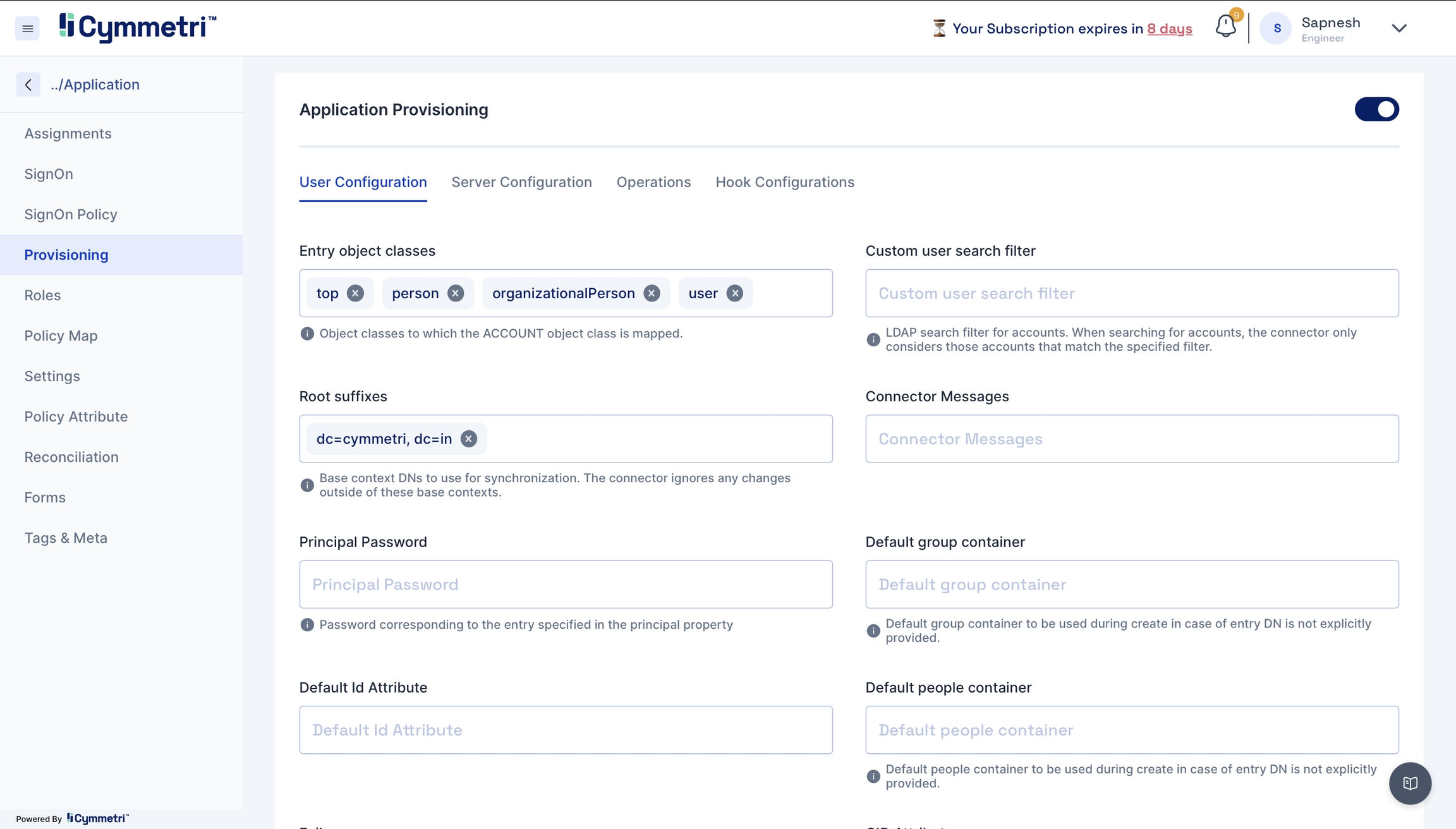
Note - You would need to change the below fields as per your organisation:
Root suffix - Add your domain name here.
Principal Password - Add your server password here.
Server Hostname - Add your server name here.
Principal - Add your admin Display Name of the Active Directory.
The base context for user search - You can add your Organisation Unit here.
The base context for group search - Add the base context to enable group search
Server port - Ensure that it is set to 636 for push
Page size- Define pageable result count for users
SSL - True is SSL is configured
Trust all certs - True.
Disable User OU Movement - Provide the path for disabling OU movement here.
Click on the save configuration button. Next, click on test configuration to see a successful toast message if your configuration is successful.
While configuring, you might encounter errors like:
Authentication exception - Failure due to incorrect username and password.
Solution - Keep all your necessary credentials handy and enter the details carefully
Socket timeout - Connection refusal by the target system
Solution - Please ensure your network connections are accurate to avoid socket timeout errors.
SSL issue - SSL issue occurs mainly if certificates are not configured correctly.
Solution - Follow the steps mentioned in Step 1 rigorously to import the Active Directory certificate to avoid SSL-related errors.
Step 6 - Start syncing users from Active Directory to Cymmetri
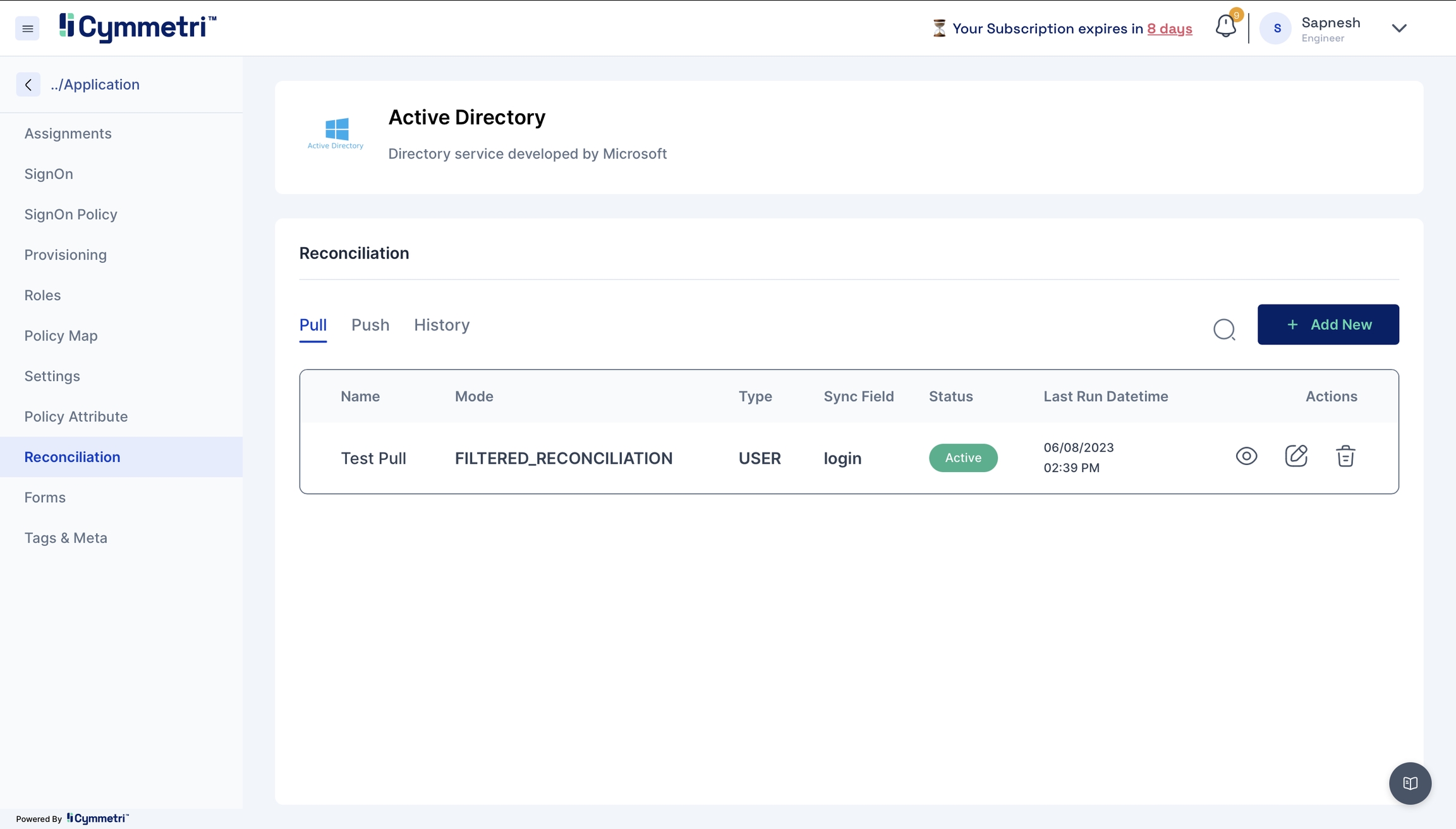
The last step of onboarding users is to add the users from Active Directory to Cymmetri by Reconciliation.
Pull Reconciliation
Pull users from your Active Directory to Cymmetri.
Click the 'Reconciliation' tab on the left navigation bar on the same page.
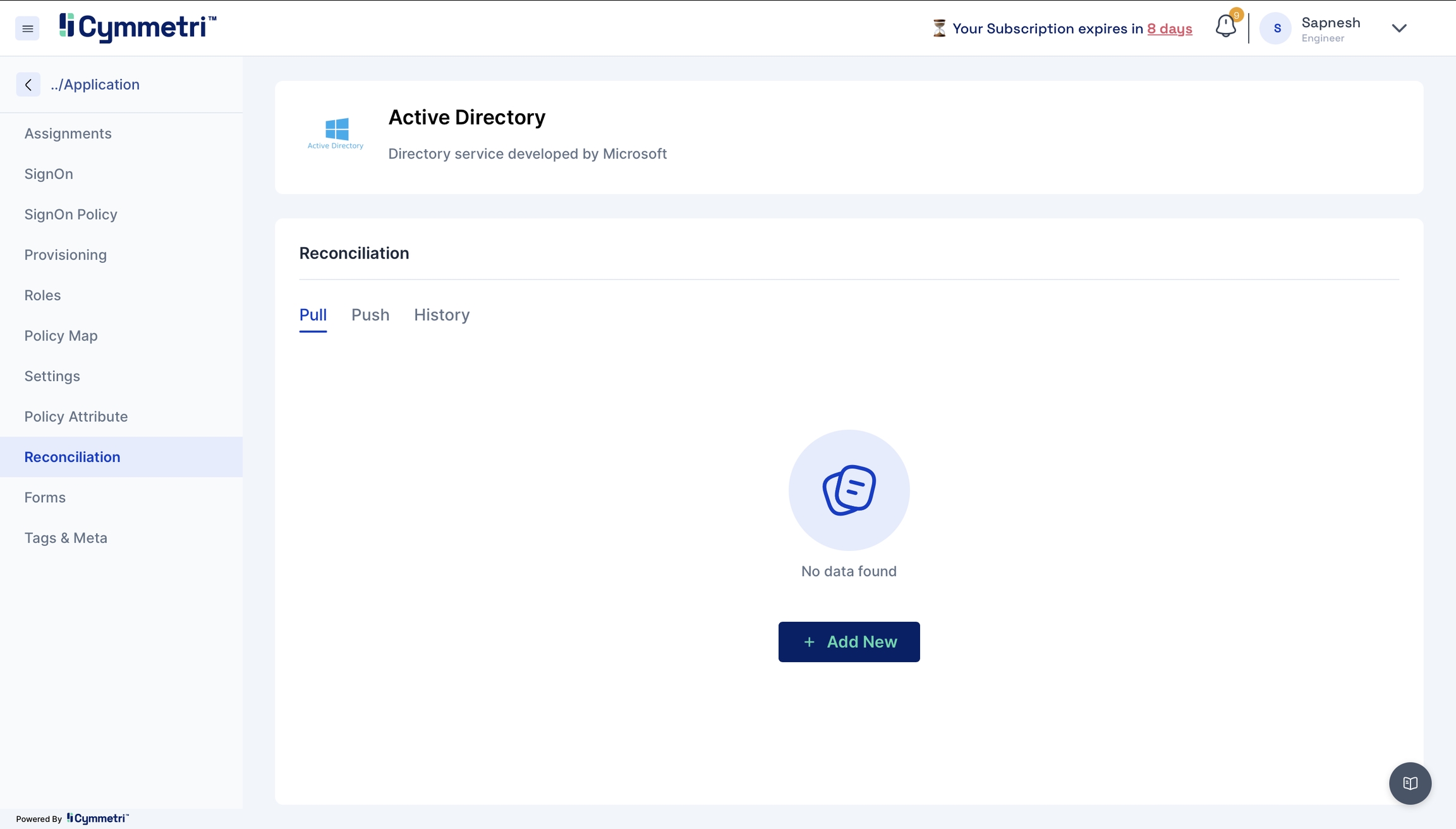
Next, click the 'Add New' button under the pull tab.
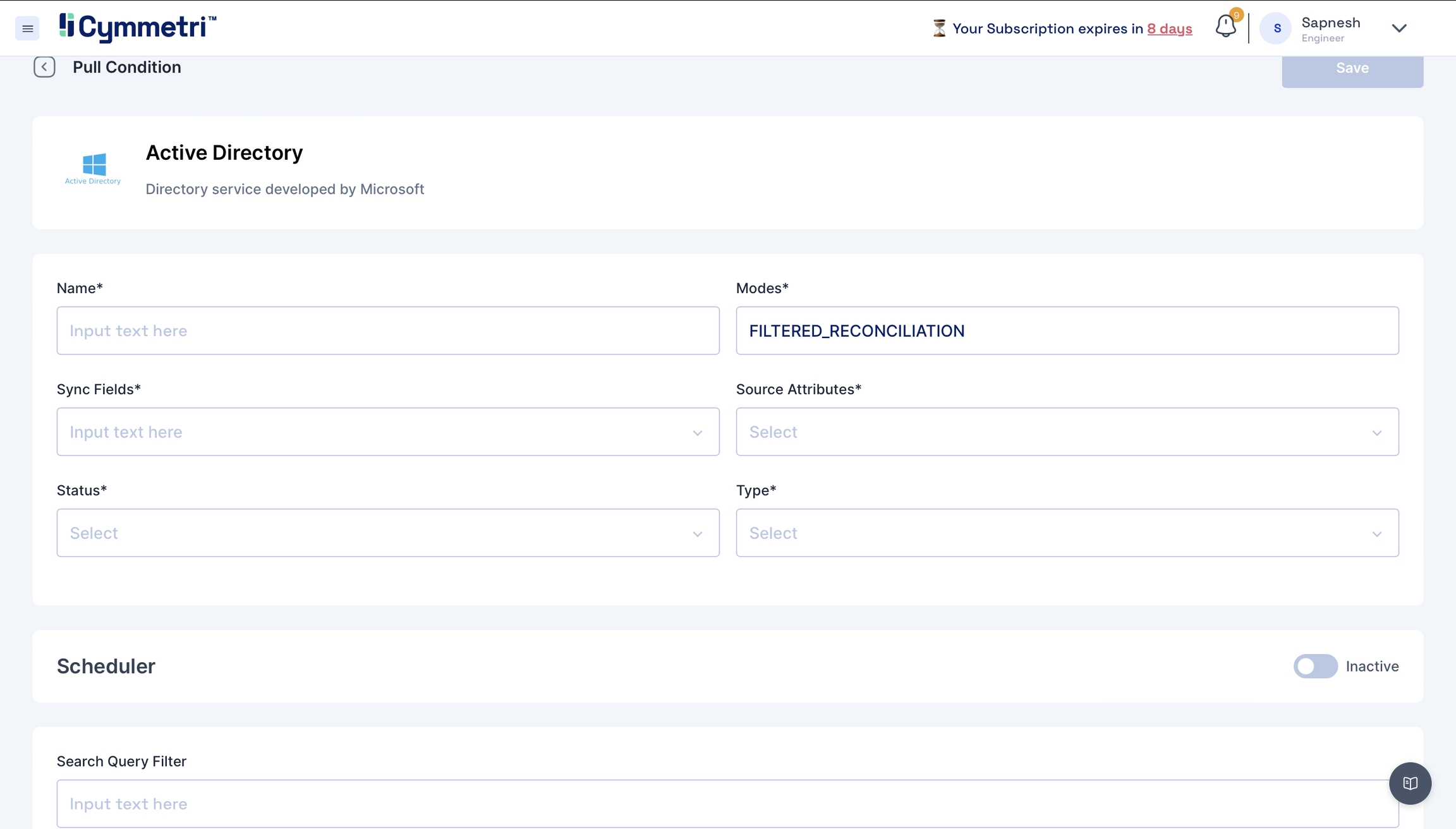
Add the field name details, and give a name to the pull reconciliation.
The modes field is prefilled with 'FILTERED_RECONCILIATION'; keep it as it is. It specifies the mode of Reconciliation.
The Sync fields are a drop-down menu with Cymmetri attributes that need to be mapped with the Source attributes, that is, your Active Directory attributes. Choose the correct mappings for these fields.
Keep the
Statusas Active.Typesare prefilled with theUser. Keep it as it is.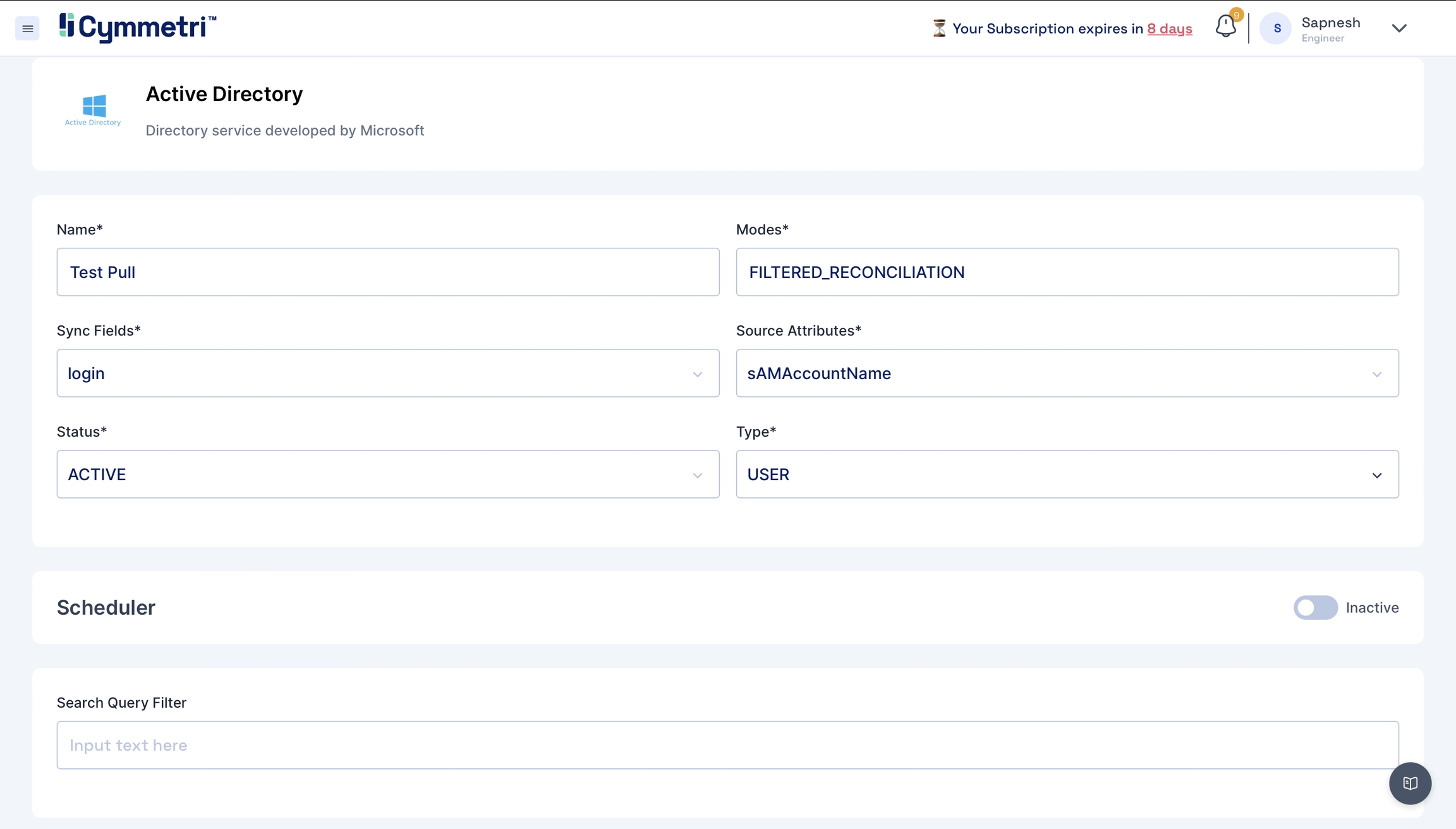
You can define the conditions for the Pull Reconciliation. It specifies the different scenarios of the Reconciliation. All the tabs have the same options in the dropdown:
IGNORE,UPDATE,DEPROVISION,PROVISION,UNLINK,LINK,ASSIGN,UNASSIGN.
IGNORE
You can skip the process by choosing this option.
UPDATE
It can be used when you want to modify or reflect new changes.
PROVISION
You can use this option to onboard the users.
DEPROVISION
You can use this option to remove the users.
LINK
You can use this option to link the users to Cymmetri
UNLINK
You can use this option to unlink the users to Cymmetri
ASSIGN
You can use this option to assign the users to Cymmetri
UNASSIGN
You can use this option to unassign the users to Cymmetri
Here is an example scenario:
UPDATE
IGNORE
PROVISION
Update user details in the target system, ignore if a user is present in both systems and provision users that do not exist in the target system.
The options to choose in a Reconciliation operation depend on your use case and change accordingly.
In this case, we have chosen to
IGNOREthe users that do not exist in your Active Directory but exist in Cymmetri. Also,IGNOREusers who are present in both the systems.PROVISIONthe users that exist in your Active Directory but do not exist in Cymmetri.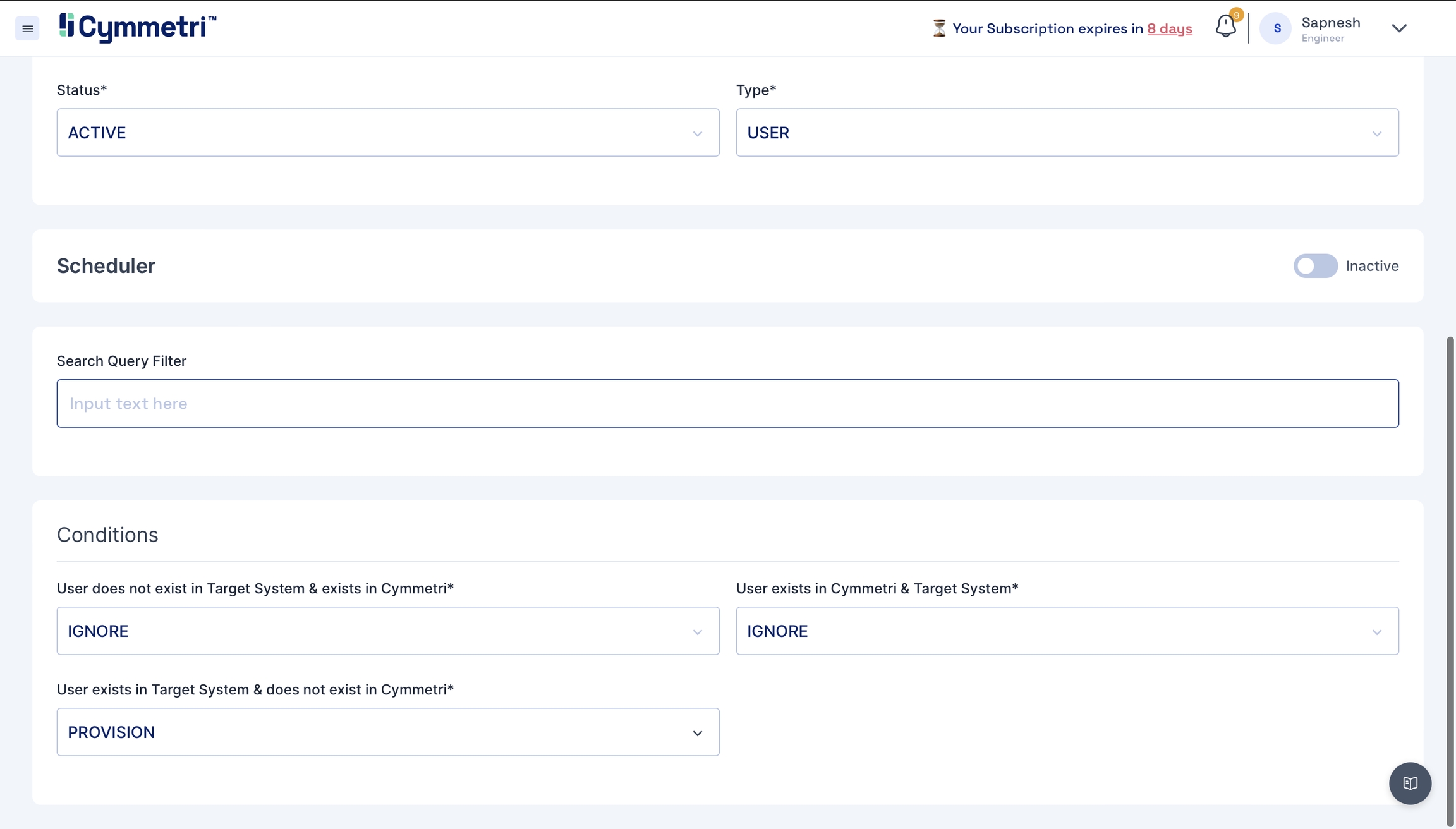
Hit the save button on the top left and click the 'Run now' button. The status of the recon changes to active.
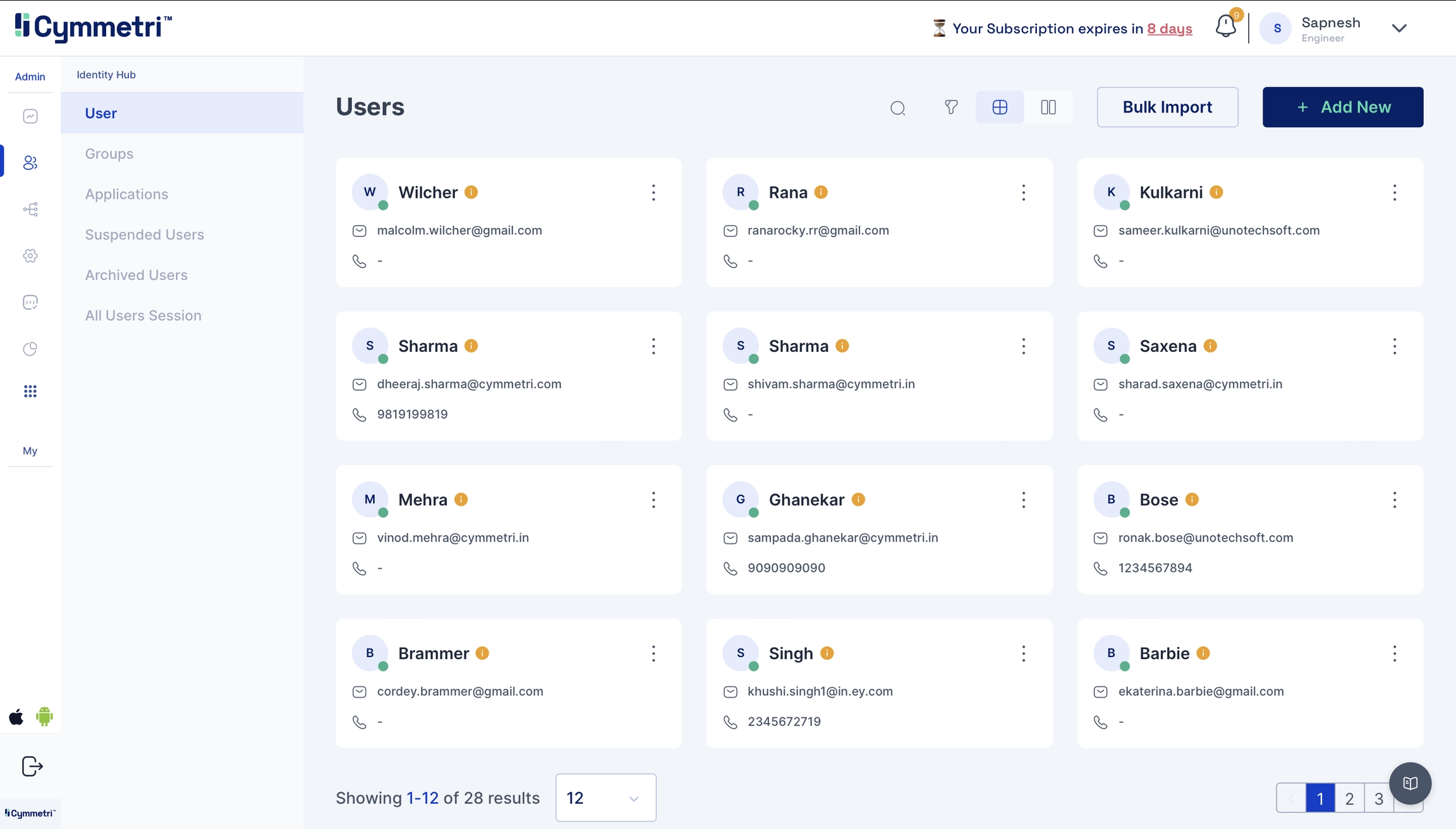
You can head to the users tab and check if users are synced. If the reconciliation is successful, the users start appearing in this tab.
Push Reconciliation
Sync your user data to Active Directory.
Navigate to the push tab and click on 'Add New'.
Repeat Steps 2 and 3 from Pull Reconciliation.
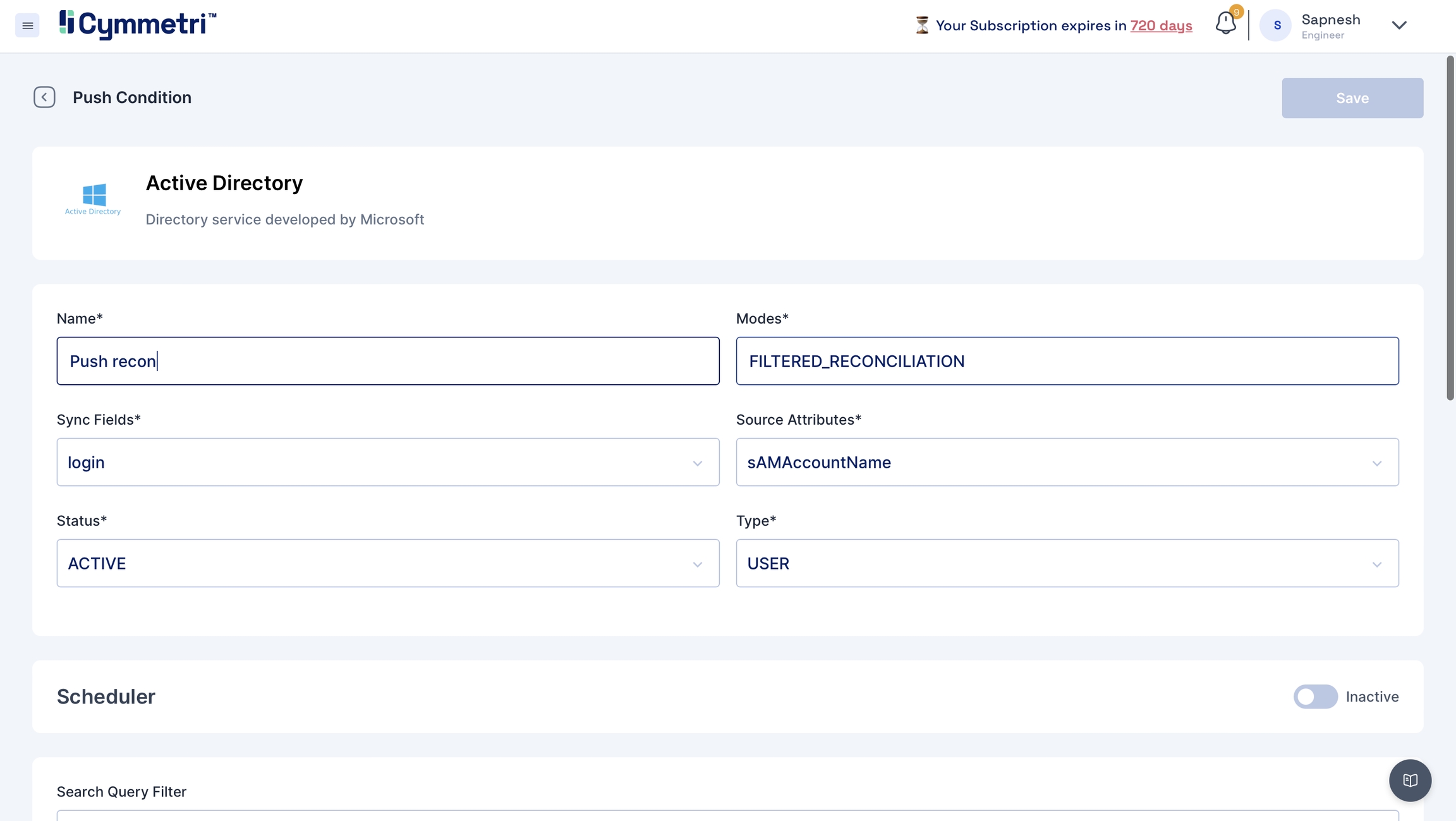
Move towards the Search Filter and Add Criteria section on the page.
Fill in all the user details like Department, Designation, User Type, Location, Manager, Group, if any, email and mobile number. Keep the account status slider in the unlocked option. Choose user status as 'Active'.
Set the conditions for the Push Reconciliation.
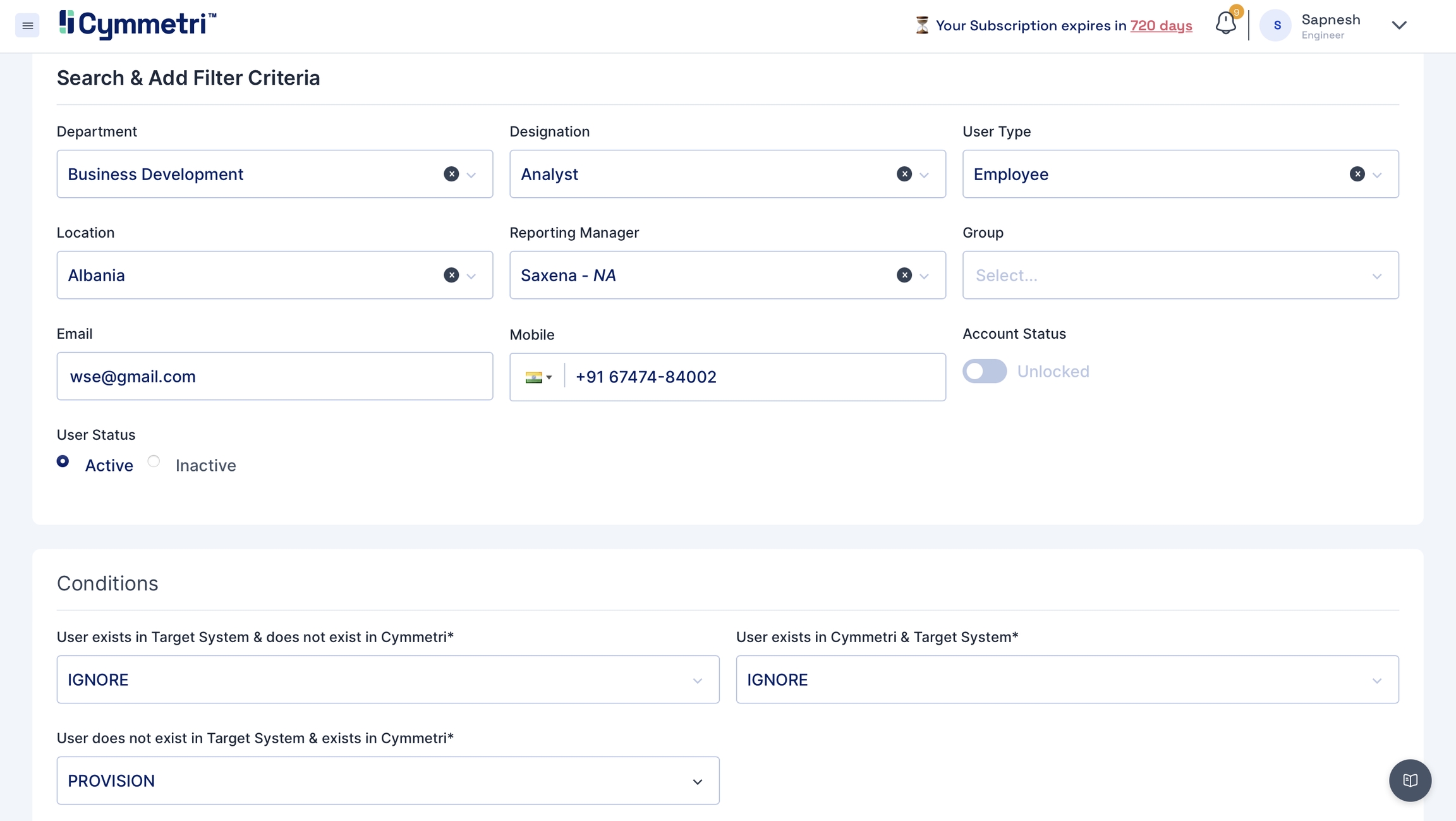
Click on Save at the top-right corner of the page.
Click on 'Run-now' to start the Push Reconciliation. You can check the status on the Reconciliation page.
Navigate to the users page to check the new users added to Cymmetri.
History
Navigate to the History tab to check and track the pull and push Reconciliation of the past.
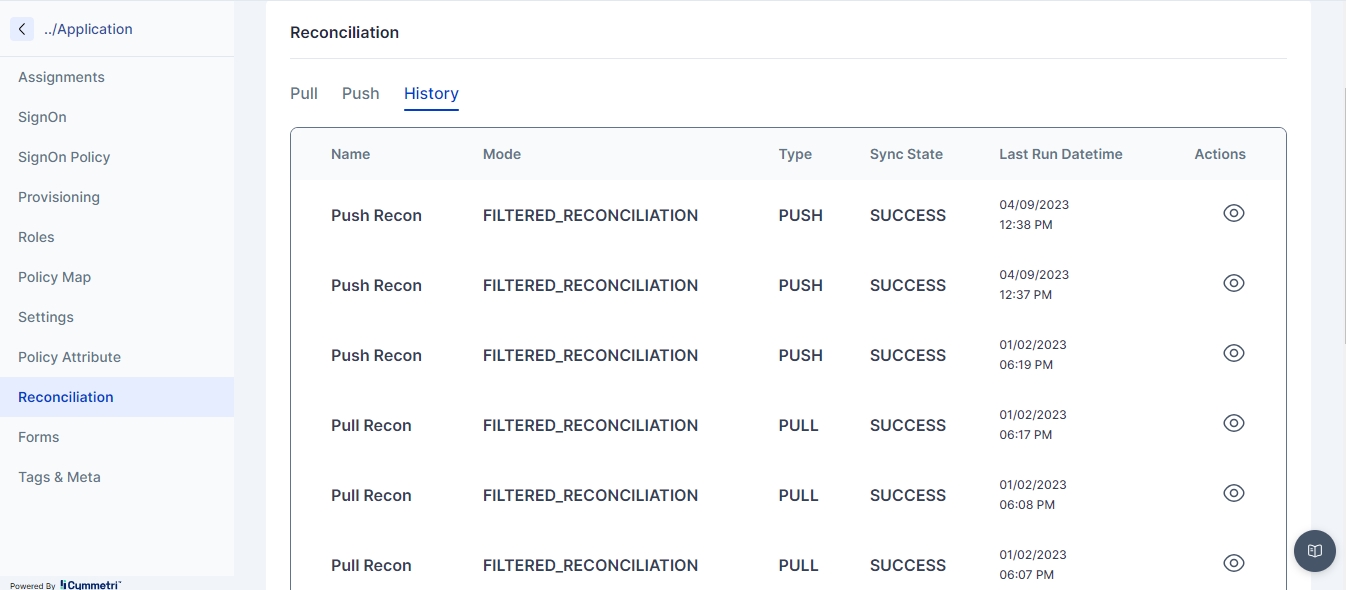
Click on the eye icon to view the Push/Pull reconciliation operation.
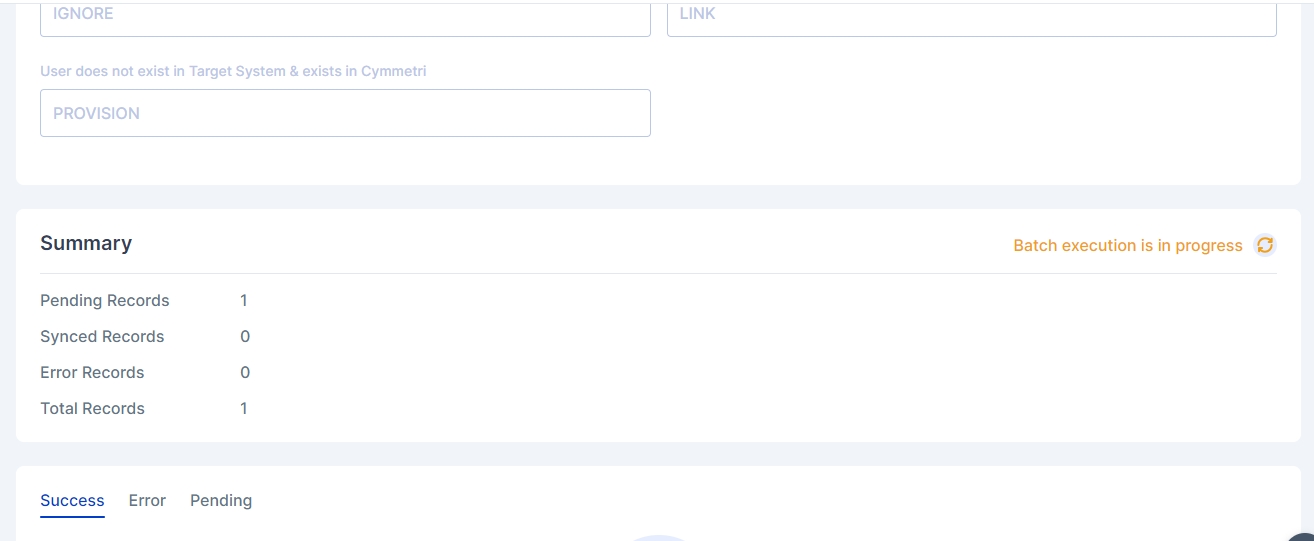
All the details configured in the Push/Pull Reconciliation can be seen here. It also displays the Summary of Pending, Synced and Error records.
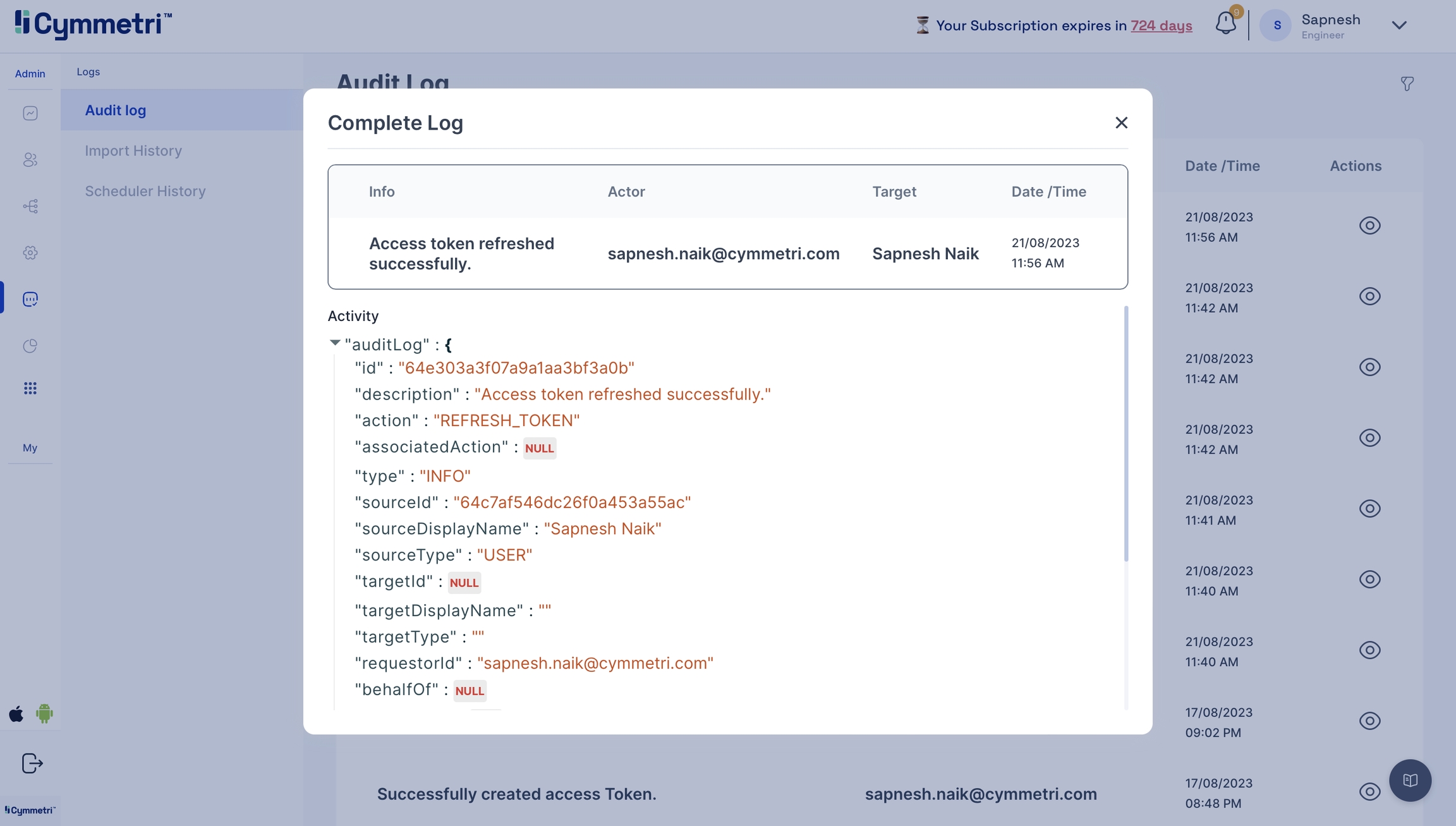
Logs
If, in any case, you're facing issues, head to the Logs->Audit Log to check for error logs.
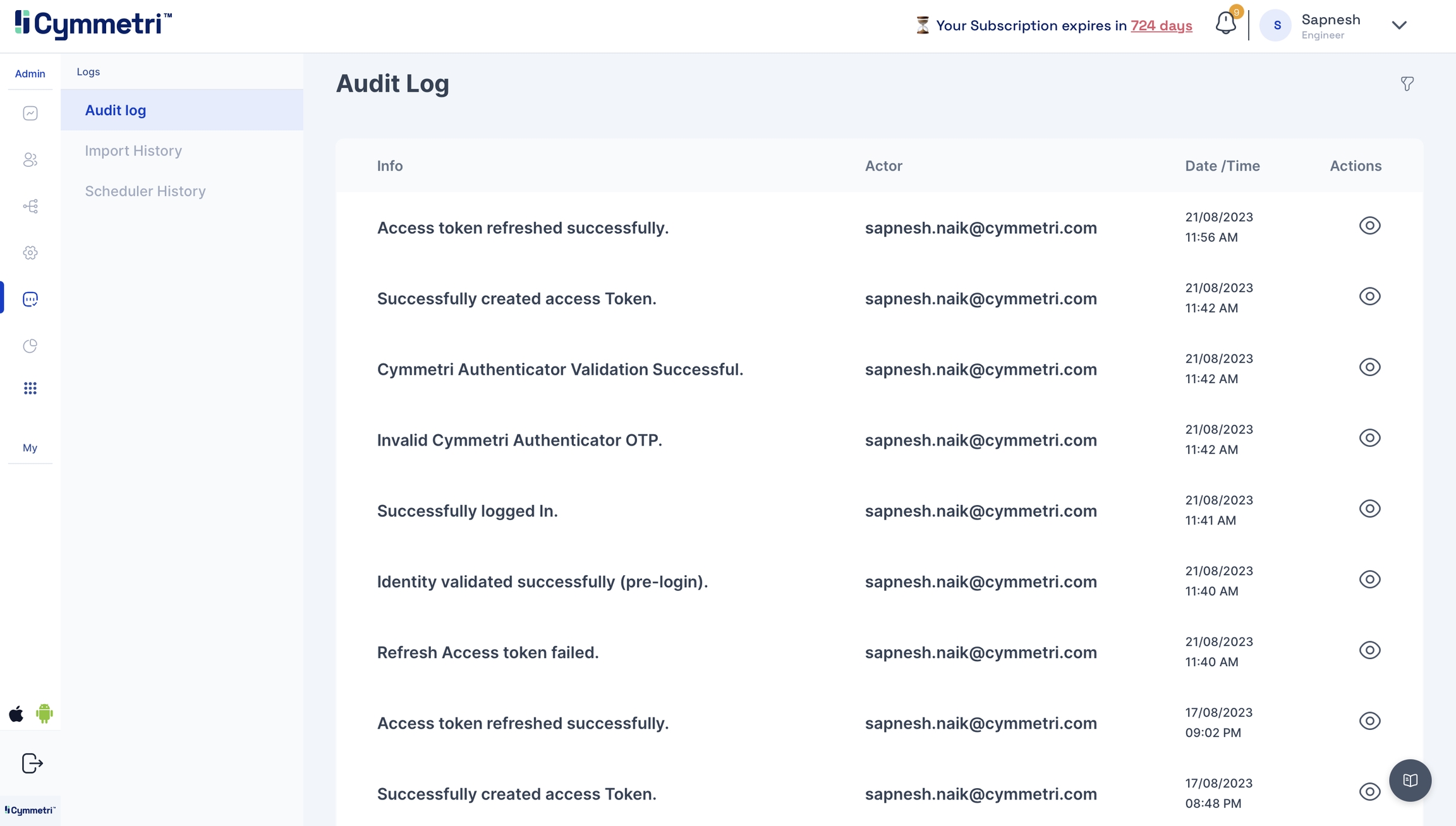
Click on the eye icon to check the event attributes in the audit log for errors.
Last updated
Was this helpful?
