Adaptive
Adaptive authentication is an advanced security measure that assesses various factors and context elements in real-time to determine the level of risk associated with a user's access attempt.
Based on this risk assessment, the authentication system can dynamically adapt its level of scrutiny and request additional verification steps if needed. This approach enhances security while minimizing disruption for legitimate users.
In Cymmetri there are various adaptive checks that the admin can enable for additional factor of authentication.
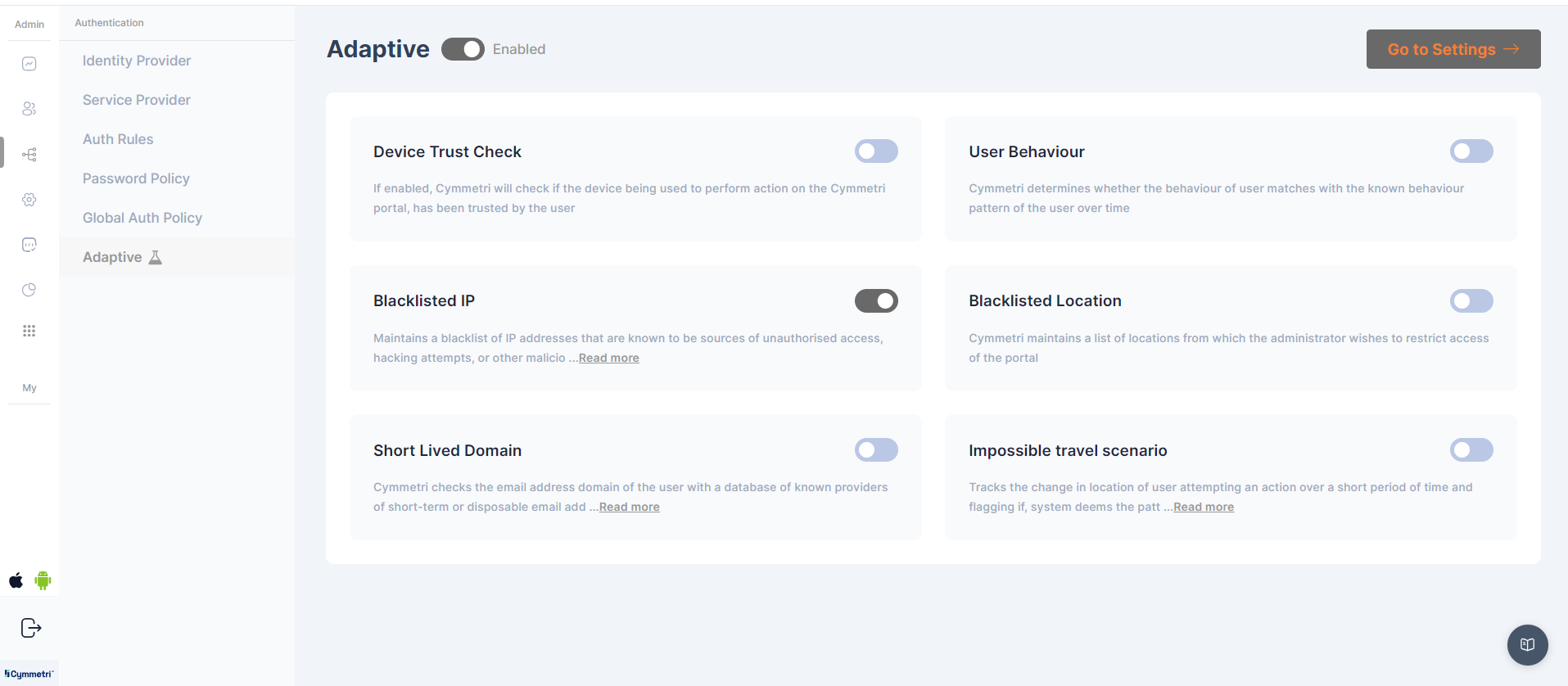
Device Trust Check - If enabled, Cymmetri will check if the device being used to perform action on the Cymmetri portal, has been trusted by the user
User Behavior - Cymmetri determines whether the behavior of user matches with the known behavior pattern of the user over time
Blacklisted IP - Maintains a blacklist of IP addresses that are known to be sources of unauthorized access, hacking attempts, or other malicious activities
Blacklisted Location - Cymmetri maintains a list of locations from which the administrator wishes to restrict access of the portal
Short Lived Domain - Cymmetri checks the email address domain of the user with a database of known providers of short-term or disposable email addresses
Impossible travel scenario - Tracks the change in location of user attempting an action over a short period of time and flagging if, system deems the pattern to be impossible.
The admin can enable these checks as per the business use case
To navigate to the adaptive settings page, click on the "Go to settings" button on the top right corner of the page.
IP Address Checks
Administrators can include an IP address in the blacklist by following these steps:
Enable the "IP address Check" radio button at the top of the page, input the IP address into the "Blacklisted IP address" field, and press enter. The specified IP will be added to the list. To synchronize the list with the database, click the "Sync Now" button.
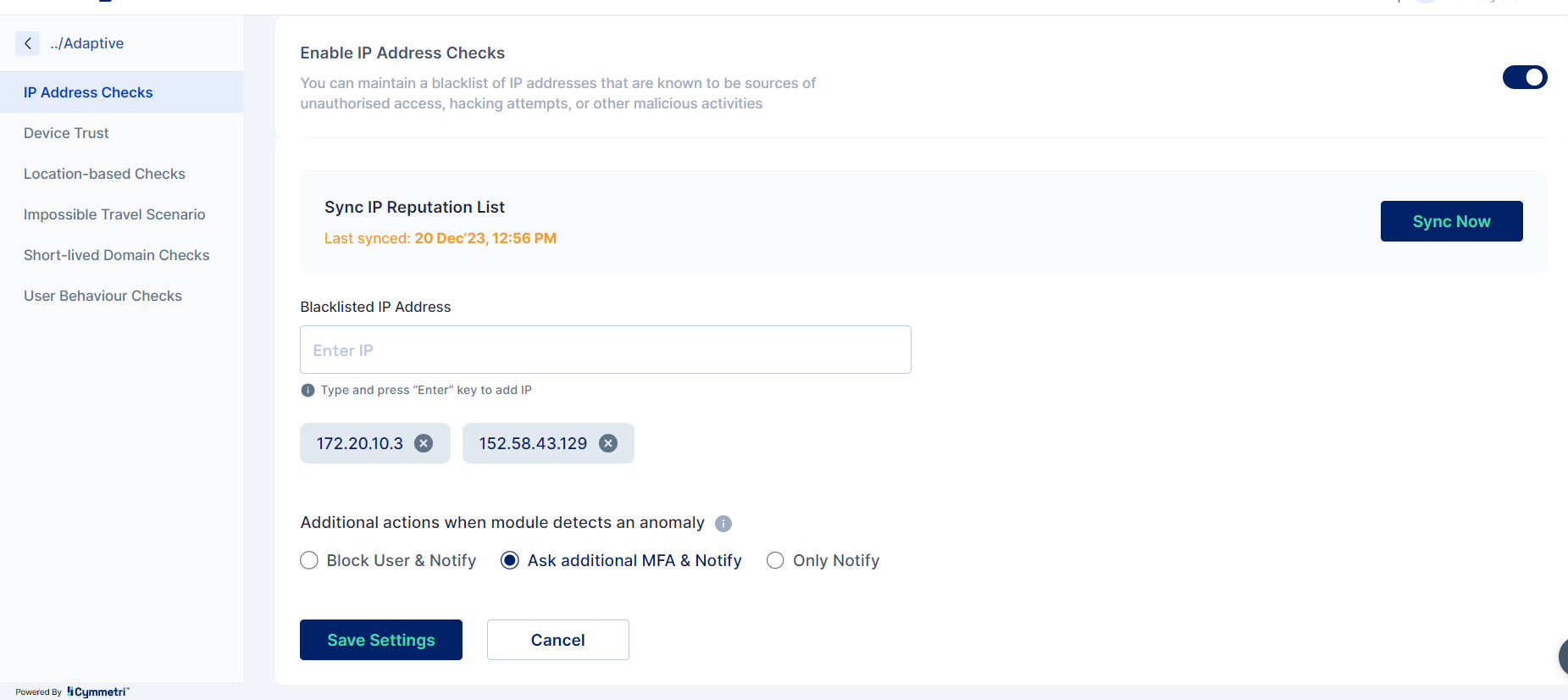
You can select additional actions when module detects an anomaly. They are the following:
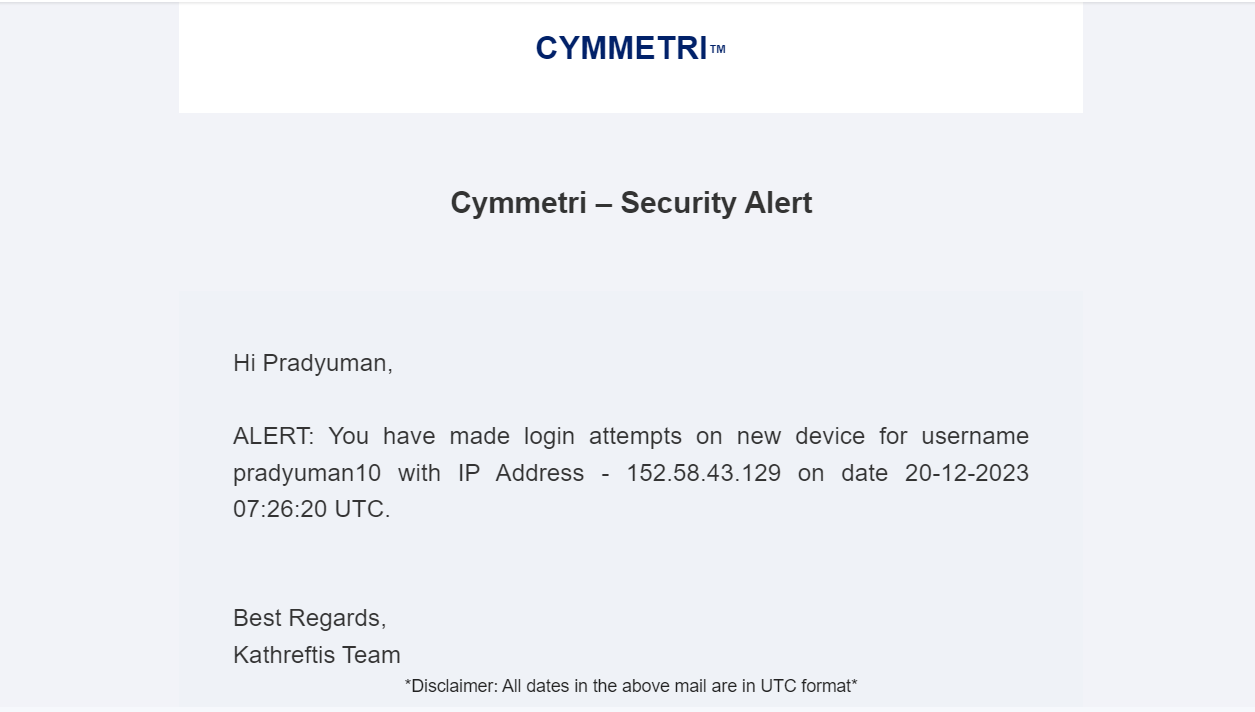
Ask additional MFA and notify - If an MFA rule has been established and adaptive authentication is activated for it in the MFA section, when a user attempts to log in with a blacklisted IP address, the user will be prompted for additional factor(s) for authentication as defined by the rule. Additionally, the user will receive email notifications regarding the login activity.
Only Notify - This option solely sends a notification to the user about the login activity.
Block user and notify - This option not only blocks the user upon a login attempt with a blacklisted IP but also notifies the user on their registered email ID.
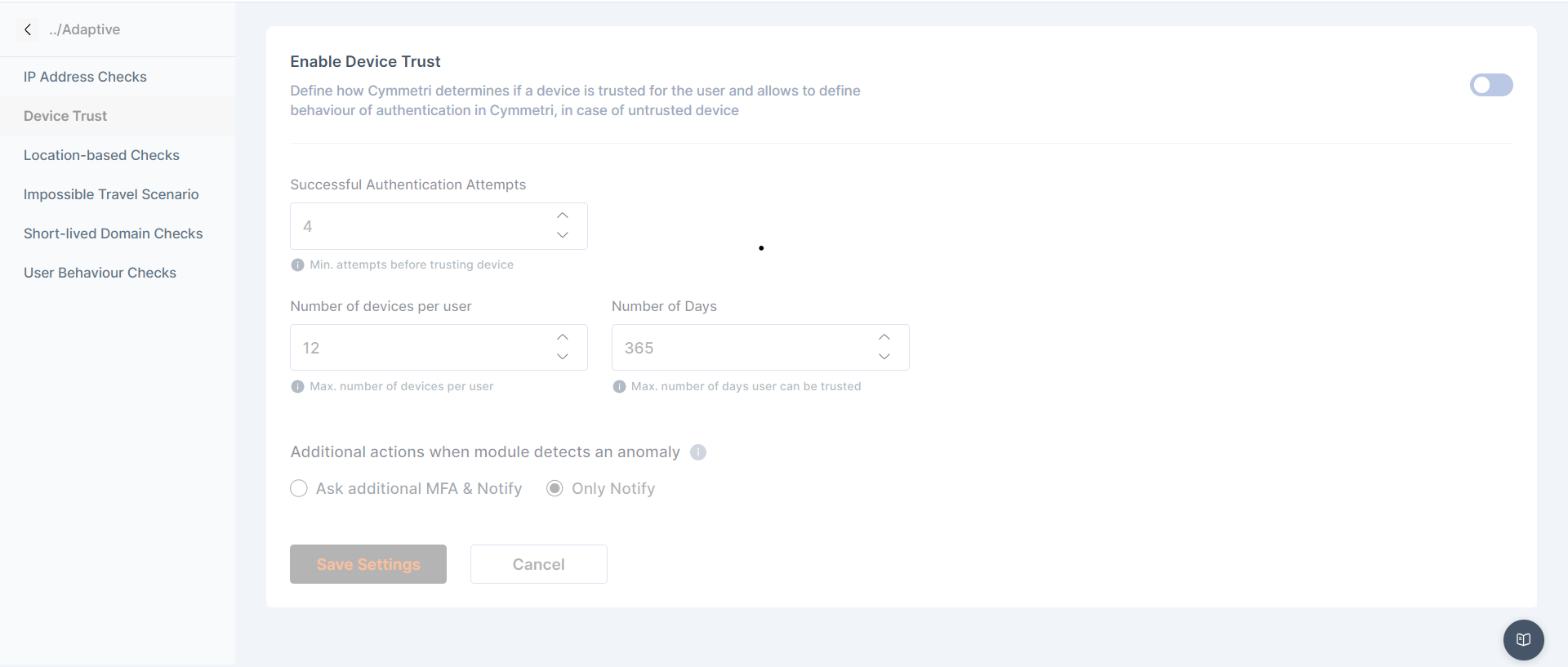
Device Trust
Define how Cymmetri determines if a device is trusted for the user and allows to define behavior of authentication in Cymmetri, in case of untrusted device
The admin can define
No of successful authentication attempts
Number of devices per user
Number of days
Additional action when module detects anomaly
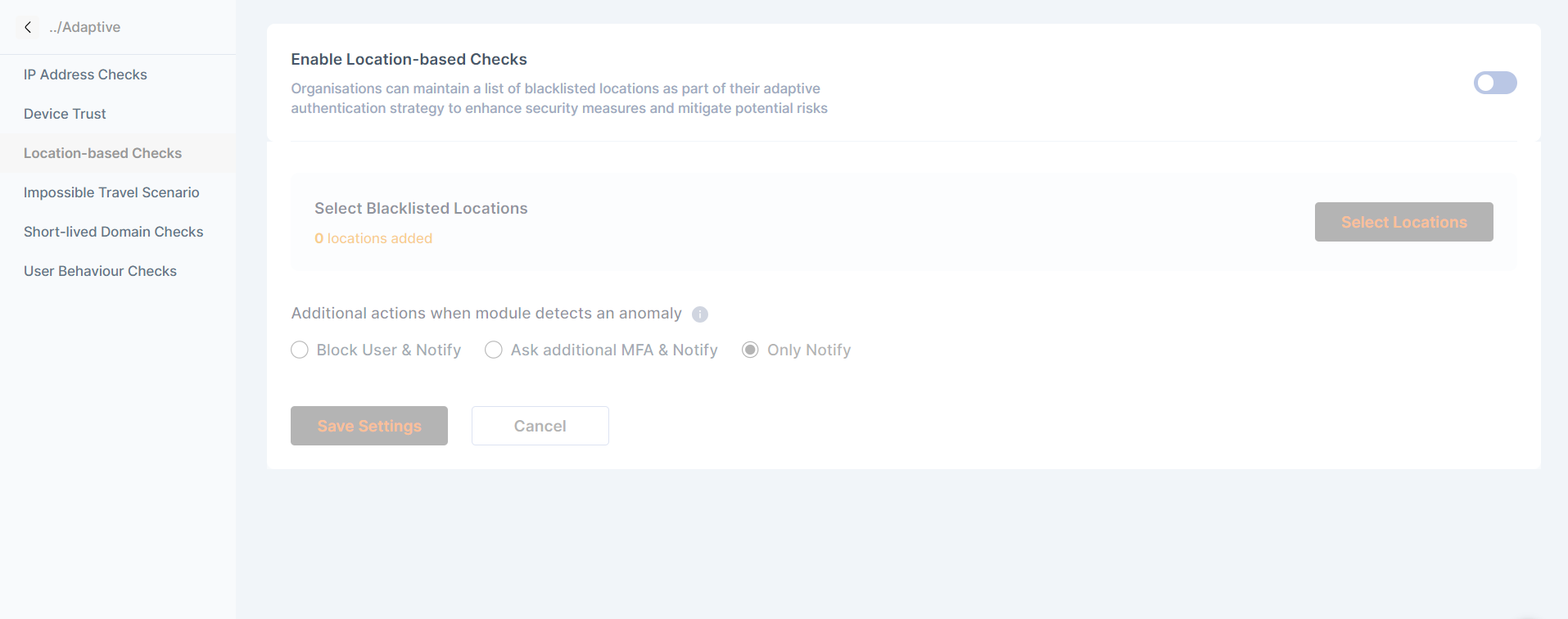
Location based checks
Organizations can maintain a list of blacklisted locations as part of their adaptive authentication strategy to enhance security measures and mitigate potential risks
The admin can select the blacklisted location on this page. Also additional actions on these checks can be selected.
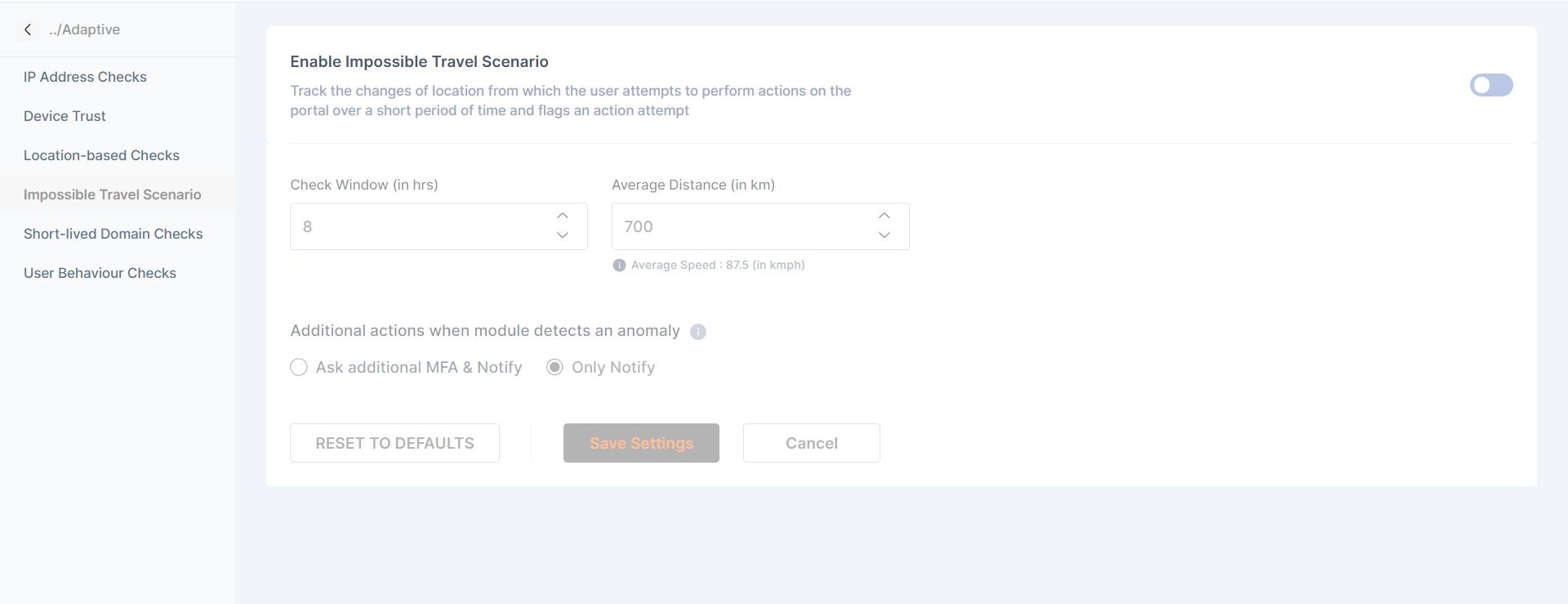
Impossible Travel Scenario
Track the changes of location from which the user attempts to perform actions on the portal over a short period of time and flags an action attempt
The admin can configure the:
Check Windows(in hrs)
Average Distance (in Km)
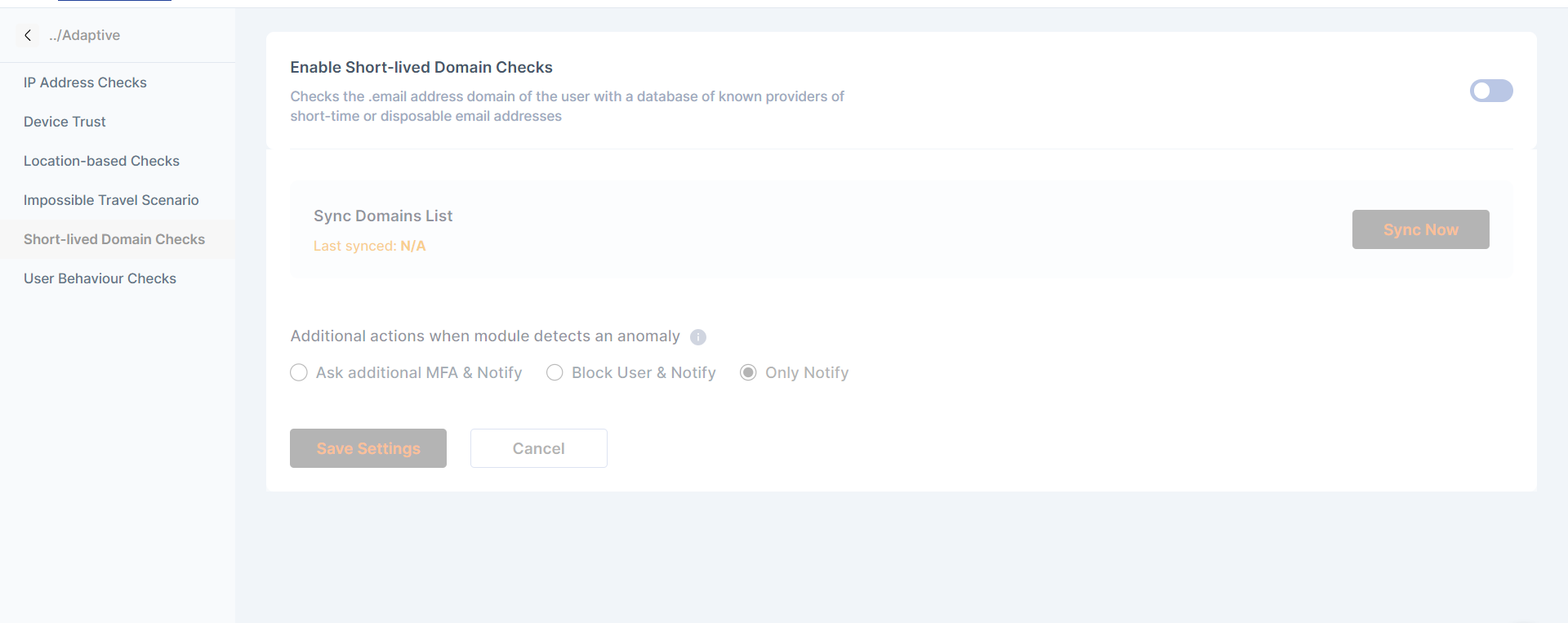
Short lived Domain Checks
Checks the .email address domain of the user with a database of known providers of short-time or disposable email addresses
The admin can Sync the database where the domains are stored and updated
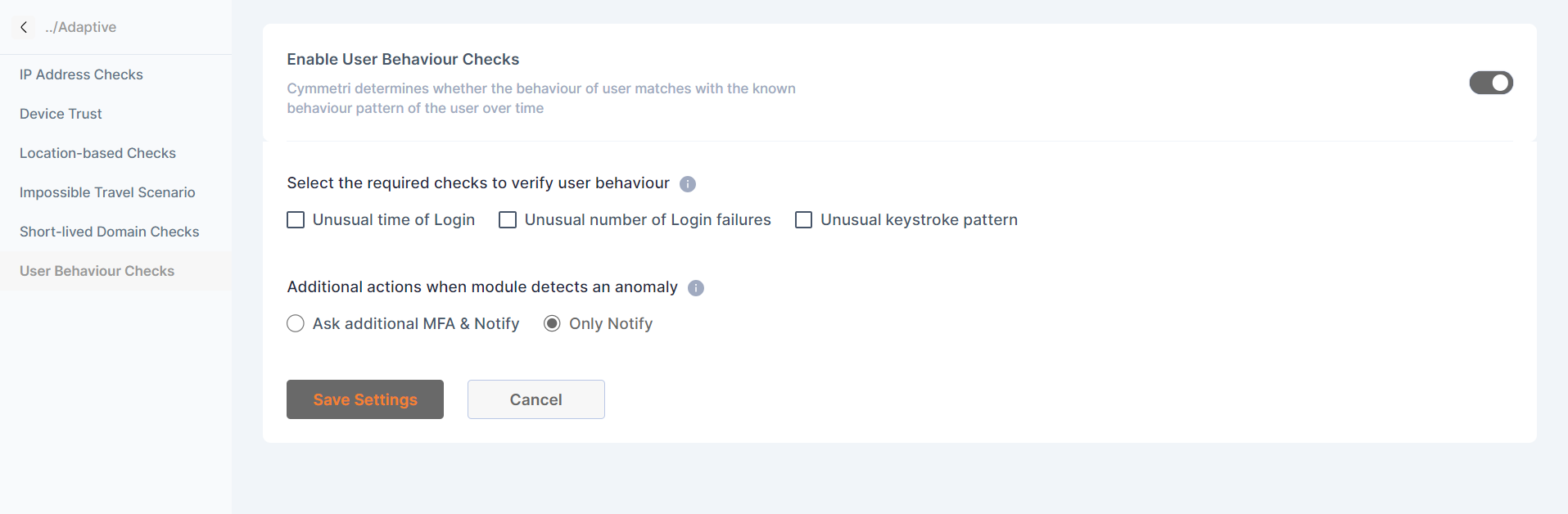
User behavior checks
Cymmetri determines whether the behavior of user matches with the known behavior pattern of the user over time
The admin can select the required checks to verify the consumer behavior:
Unusual time of Login
Unusual number of Login failures
Unusual keystrokes pattern
The admin can enable, configure and save these adaptive checks individually as and when required.